

A user reported that he kept getting popup messages from Sysem Defender. He said they were occurring every few minutes. When I checked his system, I saw a gray wall icon in the taskbard and when I checked the running applications with the task manager, I saw "System Defender Firewall Alert" alert listed.
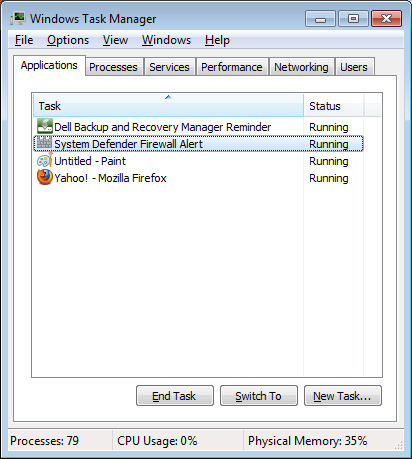
When I right-clicked on that entry in the task manager and
chose "Go to Process", I saw it was associated with a process named
rundll32.exe.
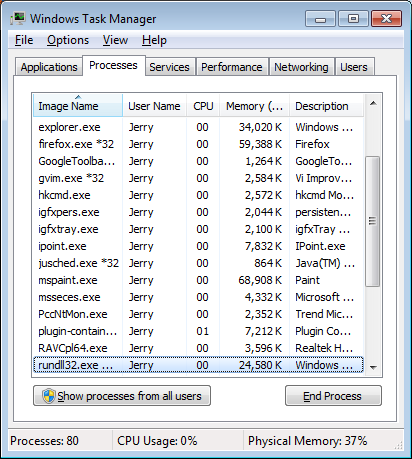
Every few minutes, I would see a balloon pop up at the lower right-hand side of the screen with "System Defender" at the top of it and below the name "Viruses have been found in your system. We highly recommend you to get license for System Defender to remove immediately harmful software." Apparently, the native lanaguage of the malware author is not English.
Clicking on the icon associated with that balloon, which was a gray wall with a red circle with a white "x" in it, would bring up the window shown below.
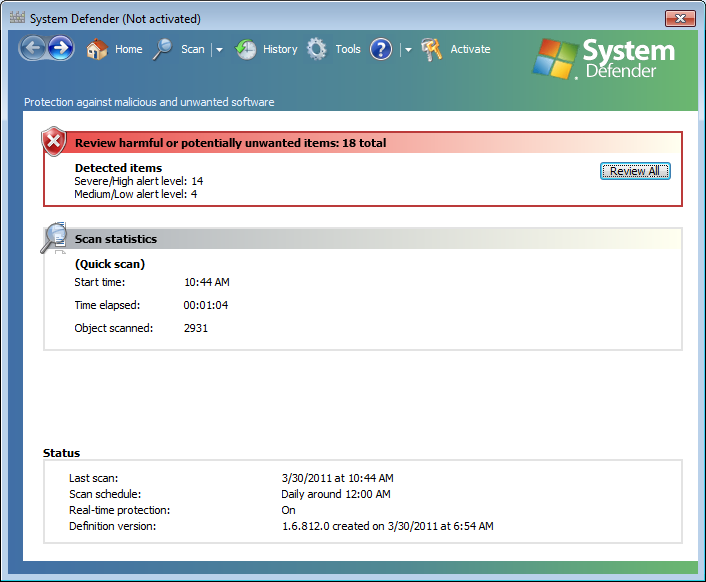
The window looks very similar to the one you would see for the legitimate antimalware software from Microsoft named "Windows Defender." The window was designed, apparently, to make people who might be familiar with Window Defender to think they were seeing warnings from that legitimate software rather than fake warnings from the rogue System Defender software. Clicking on the Review All button would, ostensibly show the malware infecting the system.
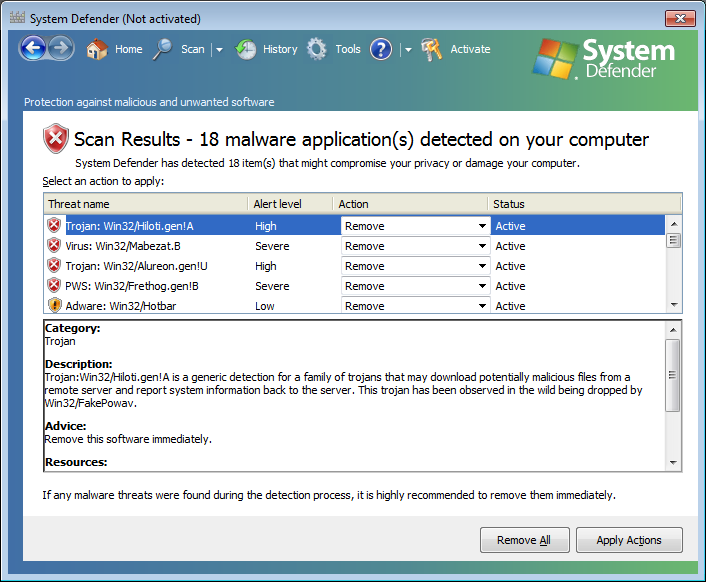
Funnily, when I scrolled to the bottom of the list, I saw "Trojan:Win32FakeXPA" listed.
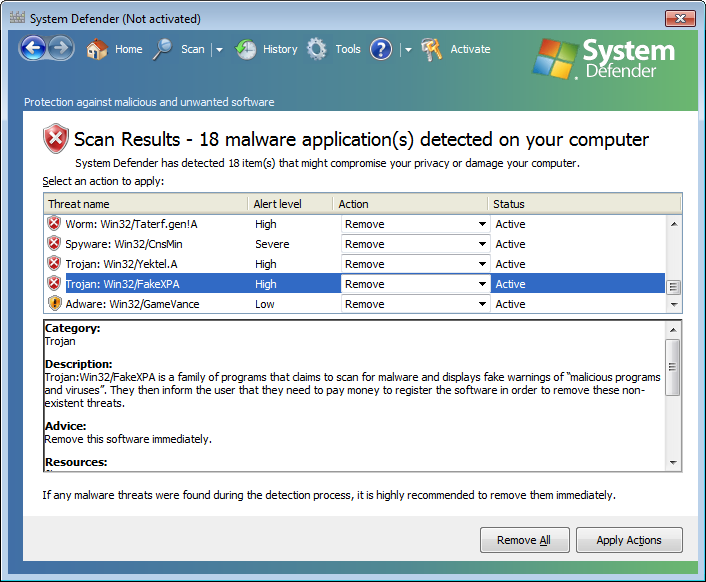
The alert level for it was "high" and it was listed with a category of "Trojan". The description for it was as follows:
Trojan:Win32/FakeXPA is a family of programs that claims to scan for malware and displays fake warnings of "malicious programs and viruses". They then inform the user that they need to pay money to register the software in order to remove these non-existent threats."
I was advised to "Remove this software immediately." Which was funny, because the description perfectly matches System Defender itself.
When I clicked on Remove All just to see what message it would produce, I saw an alert that "A valid activation key is required to remove all malicious and unwanted software found on your computer. Click OK to activate your personal copy of System Defender now.
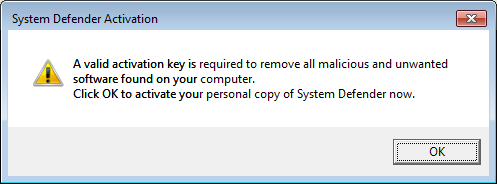
Clicking on OK brought up an activation window.
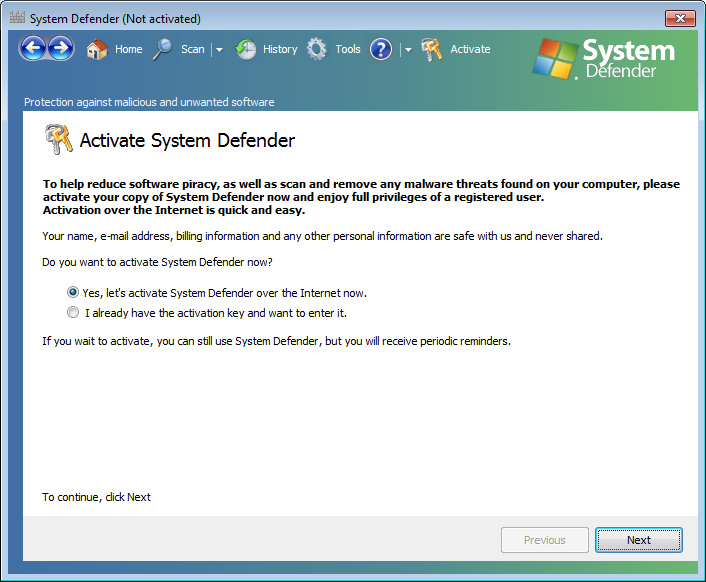
Choosing the option to activate it, to see where it would take me,
I found an Internet Explorer window open to
https://secure.isafebilling.com/purchase/get.php?i=spro&extern=1&advert=58, which showed a cost of $79.99 for the product. Needless to say,
I did not purchase the software.
That webpage showed the software, ostensibly, had a "Tucows 5 cows" rating from Tucows and an "excellent" 5 stars rating from Softpedia.
When I performed a search on Tucows for "System Defender", I saw "58 results for system + defender with a sponsored link at the top titled "System Defender" Hoax pointing to www.Removal-Tool.org with the following displayed:
"System Defender" is Rogue Spyware. Find Out How to Remove it Here...
There was no software listing for "System Defender" on that page, so, unsurpisingly the "5 cows" rating that was purportedly given to System Defender by Tucows appeared to be a lie.
I downloaded Malwarebytes' Anti-Malware free program and performed a quick scan of the system.
While that scan was occuring, I saw a Microsoft Security Essentials alert appear, stating that "Security Essentials deteced 1 potential threat and suspended it.
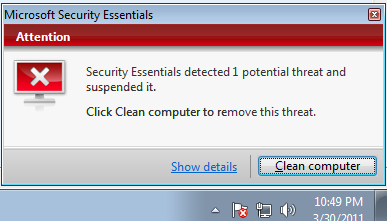
When I clicked on the "Show details" link, I saw the detected item listed
as Rogue:Win32/Defmid with the alert level listed as "severe"
and the status as "suspended".
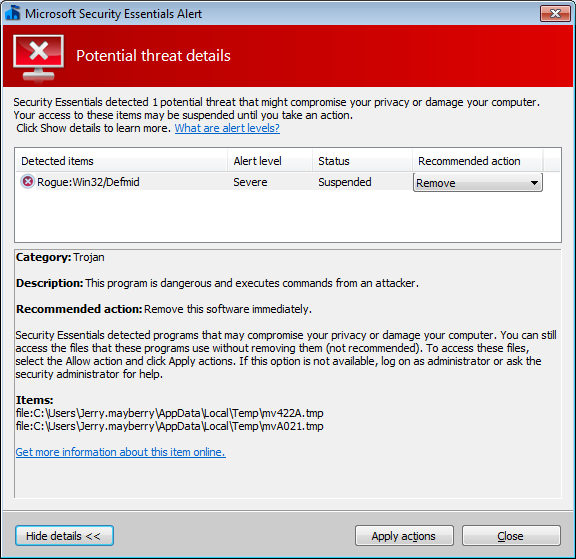
When I clicked on " Get more information about this item online, I was taken to Microsoft's Rogue:Win32/Defmid webpage which identified System Defender as the malware it had detected.
The Microsoft webpage on this malware stated it creates a registry
key HKCU\Software\Microsoft\Windows\CurrentVersion\Run
where it places the following:
In subkey: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Sets value: "<random name>"
With data: "<system folder>\rundll32.exe "%AppData%\<random name>.avi""
The entry I saw at HKCU\Software\Microsoft\Windows\CurrentVersion\Run
for the malware was slightly different in that it referred to a
.dat file, rather than a .avi file.
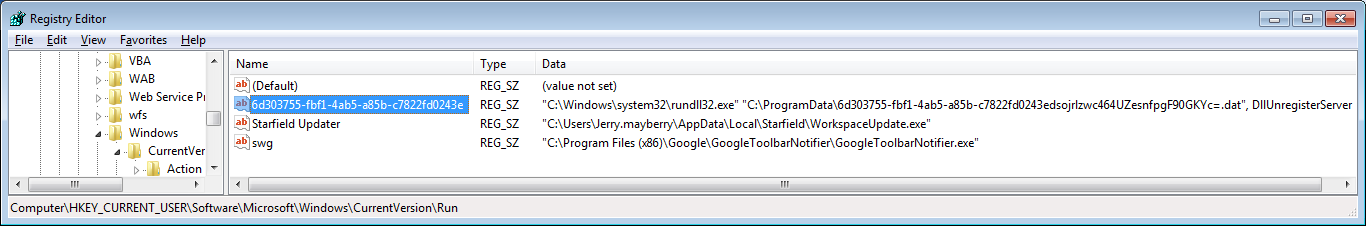
The file that was referenced was a hidden file; I had to use the
/ah option on the dir command to see it.
C:\>dir /ah "C:\ProgramData\6d303755-fbf1-4ab5-a85b-c7822fd0243edsojrlzwc464UZes
nfpgF90GKYc=.dat"
Volume in drive C is OS
Volume Serial Number is F2A6-EC39
Directory of C:\ProgramData
03/30/2011 06:53 AM 2,363,392 6d303755-fbf1-4ab5-a85b-c7822fd0243edsojr
lzwc464UZesnfpgF90GKYc=.dat
1 File(s) 2,363,392 bytes
0 Dir(s) 53,418,045,440 bytes freeMalwarebyte's Anti-Malware reported it detected 2 infected objects.
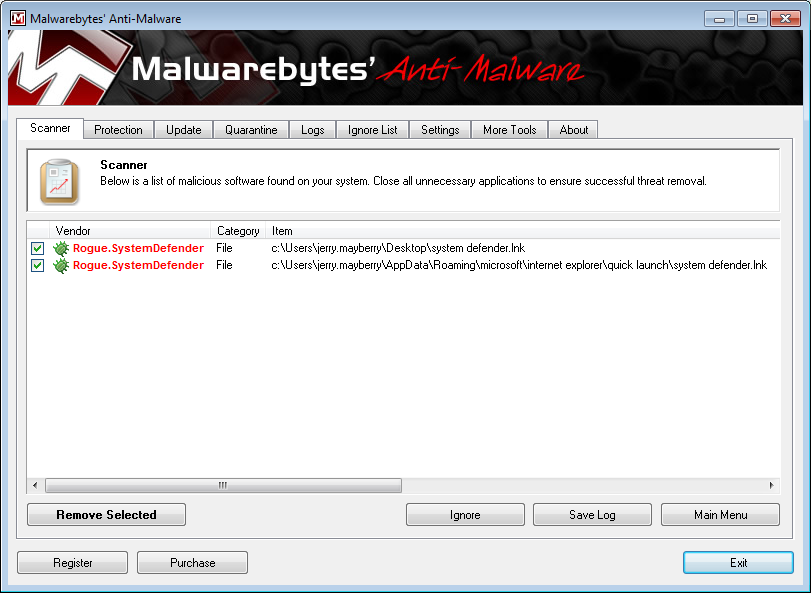
I checked on one of the files it reported, which was not hidden.
C:\>dir "\users\jerry.mayberry\appdata\roaming\microsoft\internet explorer\quick
launch\system defender.lnk"
Volume in drive C is OS
Volume Serial Number is F2A6-EC39
Directory of C:\users\jerry.mayberry\appdata\roaming\microsoft\internet explore
r\quick launch
03/30/2011 06:53 AM 1,991 System Defender.lnk
1 File(s) 1,991 bytes
0 Dir(s) 53,418,401,792 bytes freeI hadn't responded to the Microsoft Security Essentials Alert; when I checked its open window again, it reported it automatically removed the detected items, but I still saw System Defender in the taskbar and the baloon still continued to pup up every few minutes.
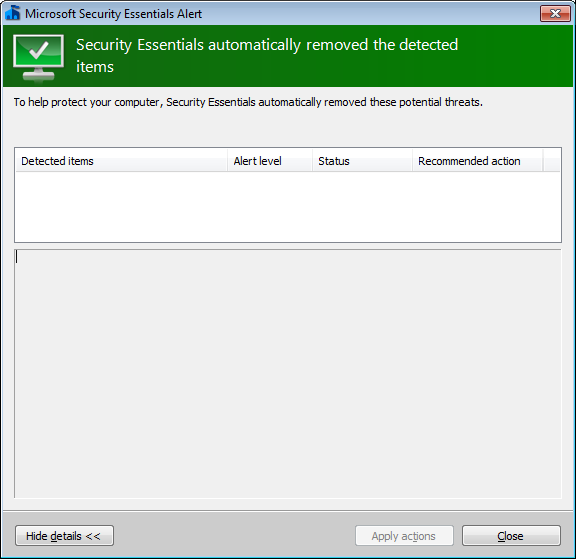
Having Malwarebytes' Anti-Malware remove what it found didn't result in those disappearing, either. It produced a log file and advised me to restart the system to complete the removal, which I did.
When I restarted and logged in, I found System Defender was still there and was purportedly scanning the system for malware, though it likely was just updating its own display. It reported finding malware as it was scanning. I stopped the scan.
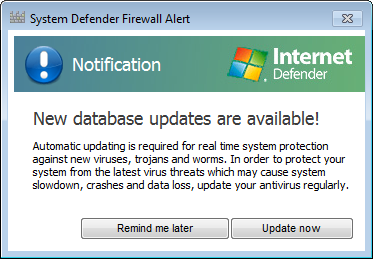
I then started a Microsoft Security Essentials full scan. As it was running, I saw a "Hamful software detected" window appear. The title of the window was "System Defender Firewall Alert", but it identified itself as "Internet Defender" in a logo beneath the title.
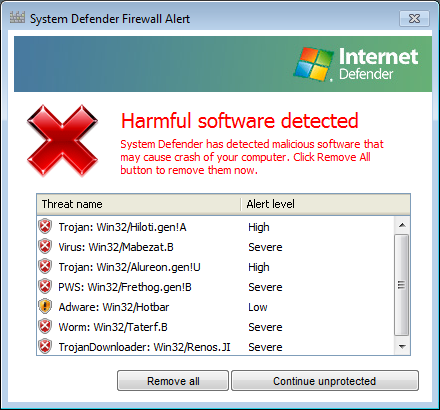
When I clicked on Continue unprotected in that window, I saw a "Are you sure you want to continue unprotected?" window appear with "Internet Defender" displayed in that window.
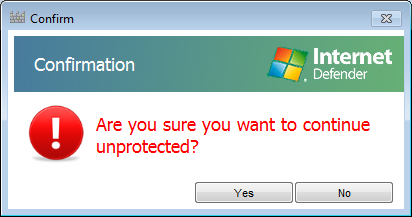
I chose "yes".
System Defender, a few minutes later, popped up a "Warning! 7 infections found!" window.
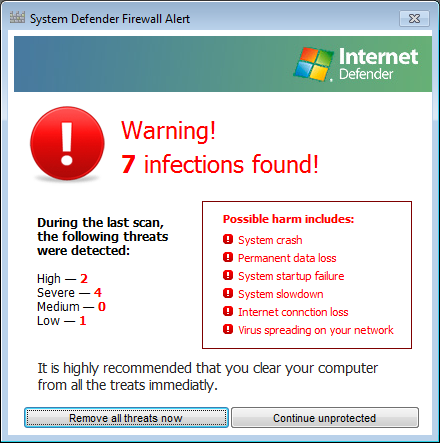
I again chose to "continue unprotected." The next window it popped up was a "Keylogger activity detected" one.
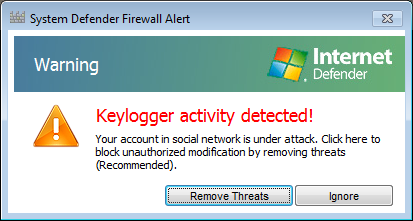
I chose the "ignore" option.
It was putting a different message in its balloon warning after I had rebooted.
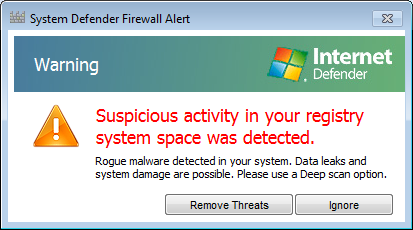
The next window to pop up warned me that "Suspicious activity in your registry system space was detected." Again, I chose "ignore."
The next tactic it tried was to claim the system was under attack from a remote macine with IP address 101.123.34.123.
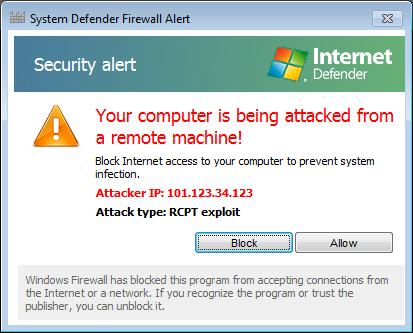
Knowing it was a fake alert, I chose "allow." Within a few minutes it then tried a "System Defender Firewall Alert."
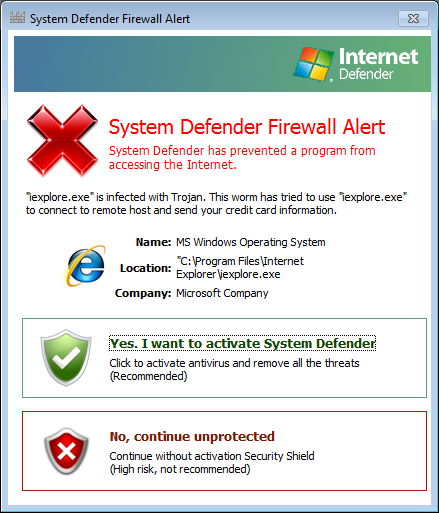
I chose the "No, continue unprotected" option.
I used IE HistoryView , which is free software that allows one to view Internet Explorer's history and see what webpages were accessed at specific times to see where the malware may have originated. The system is running Windows 7 Professional with Internet Explorer 9 Beta. IE HistoryView 1.60 worked fine with Internet Explorer 9 Beta.
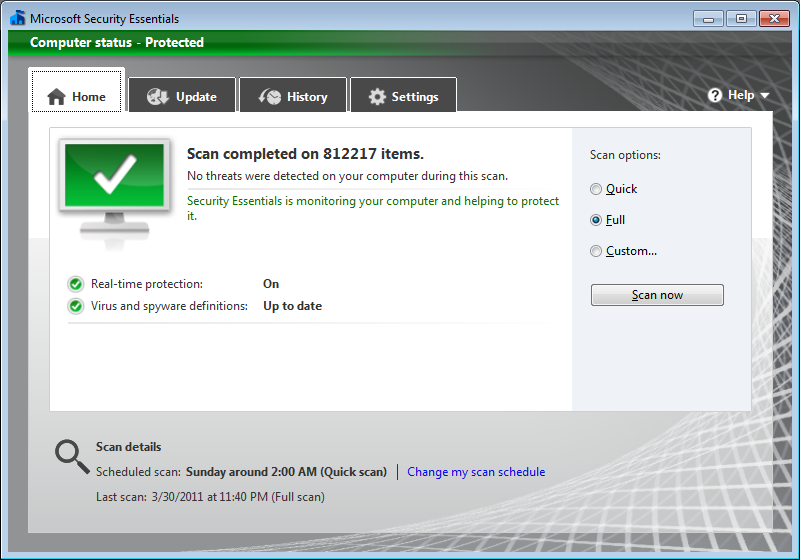
When the full scan by Microsoft Security Essentials completed, it reported it had not fund any malware.
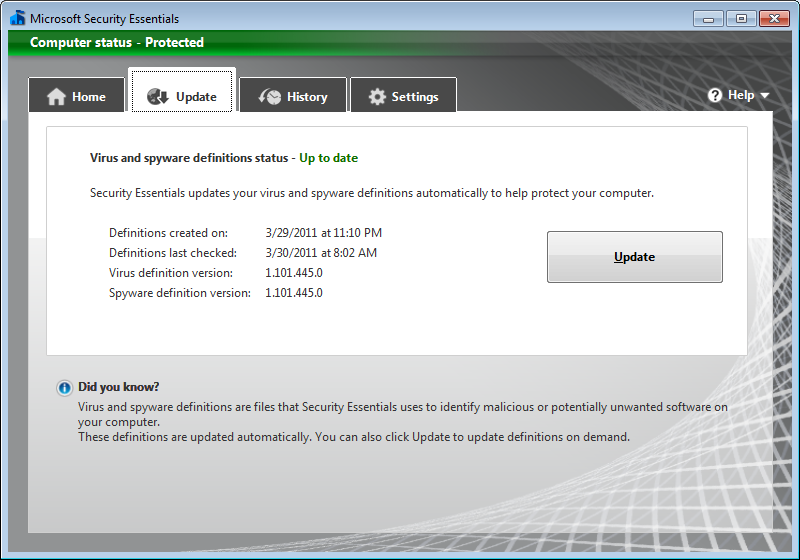
I checked its definitions; they were up-to-date.
If you right-click on the icon for System Defender in the system tray at the lower right-hand corner of the screen, there is a "game mode" option where you can opt to have it suspend alerts for various periods of time from 30 minutes up to 4 hours.
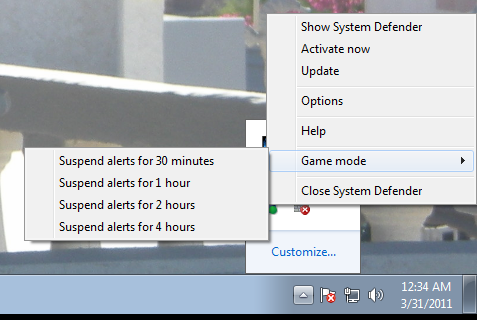
However, when opted to suspend alerts for 30 minutes, they still appeared. And I even saw a new alert in addition to ones I had seen before.
I ran a full scan of the system with Mawarebytes' Anti-Malware. The full scan reported 3 infected objects.
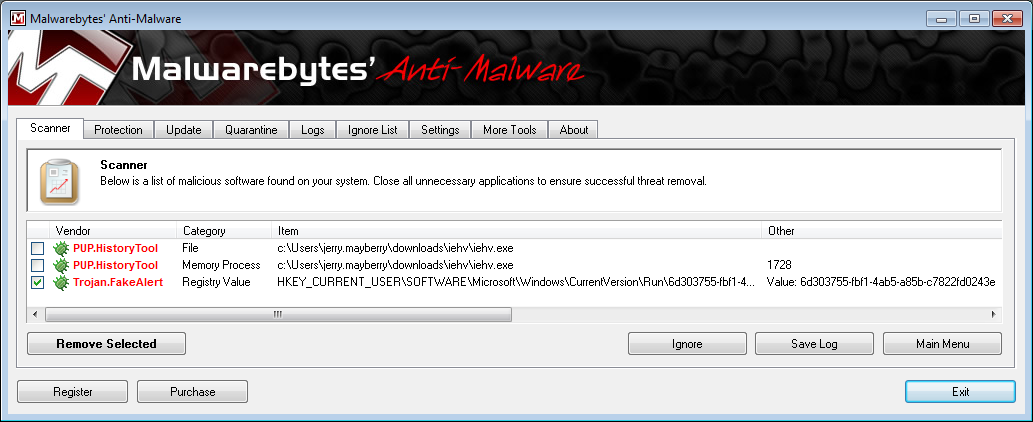
It reported System Defender as Trojan.FakeAlert. It also reported IE HistoryView (IEHV) as a "potentially unwanted program", i.e., "PUP". It didn't have the two entries related to it marked for removal and I didn't select those, since I wanted to be able to use that program to try to detect the source of infections. I had it remove Trojan.FakeAlert. It produced a new log file, but didn't suggest I needed to reboot the system. I rebooted anyway, since System Defender was still active. I didn't see the software running after I rebooted. I no longer saw alerts popping up every few minutes, either, minimizing all other windows when they did so to make System Defender even more annoyingly obtrusive.
Created: March 30, 2011