

I opened
HTTPNetworkSniffer, a packet capture tool developed by Nir Sofer and
available from his NorSoft site, today on
a Microsoft Windows system. While it was open I visited this website using
the Firefox browser on the system and happened to switch back to the
HTTPNetworkSniffer window where I noticed an unexpected connection to
gn.symcd.com.
I double-clicked on the entry to see the details for the connection and saw the following:
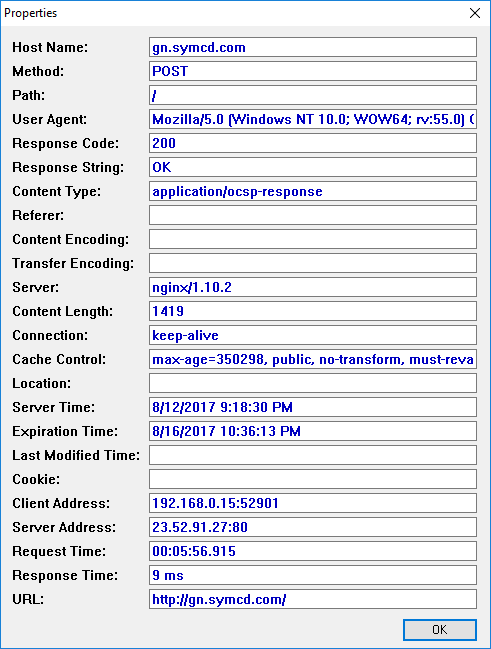
The HTTP method was listed as "POST" and the "content type" value listed was "applicaton/ocsp-response". "OCSP" stands for Online Certificate Status Protocol. OCSP is an internet protocol used to check the revocation status of X.509 digital certificates used by websites for HTTP over Transport Layer Security (HTTPS) connections.
All versions of Mozilla Firefox since at least version 1.5 support OCSP checking. And, as of Firefox 3, which was released in 2008, OCSP checking was enabled in Firefox by default.
I also noticed there were four similar OCSP connections to a google server, clients1.google.com, immediately preceding the one to the gn.symcd.com system.
Roger Karlsson, the developer of the FreeFixer utility, a free tool to help users delete potentially unwanted software, such as adware, spyware, trojans, viruses and worms, which I've used before to identify malware on systems - see Infected Gateway Laptop - December 2007 - reports that the symcd.com domain is owned by Symantec Corporation. After reading the article he posted regarding noticing an HTTP "application/ocsp-request" to gv.symcd.com while using a network monitoring tool, I performed an nslookup on gn.symcd.com and found that the IPv4 address listed for it is 23.4.187.27 and that one of the aliases for gn.symcd.com is ocsp-ds.ws.symantec.com.edgekey.net.
C:\Users\Pam>nslookup gn.symcd.com
Server: UnKnown
Address: 192.168.0.8
Non-authoritative answer:
Name: e8218.dscb1.akamaiedge.net.0.1.cn.akamaiedge.net
Addresses: 2600:1408:7:292::201a
23.4.187.27
Aliases: gn.symcd.com
ocsp-ds.ws.symantec.com.edgekey.net
e8218.dscb1.akamaiedge.net
C:\Users\Pam>I also found a Symantec webpage, Symantec_OCSP_FQDN_List.txt that lists many symcb.com and symcd.com hosts associated with the Symantec OCSP service. That list of fully qualified domain names (FQDNs) is referenced from Symantec's SSL Online Certificate Status Protocol (OCSP) Infrastructure Upgrade on January 13, 2014 web page, which states:
Important Service Announcement
We are upgrading our SSL Online Certificate Status Protocol (OCSP) infrastructure on January 13, 2014 to provide faster responses and a better experience for our customers.
Here's how you'll benefit
- Faster response time - OCSP requests will be served from the closest location to the user with dramatically improved average response times.
- 100+ additional new sites - more sites handling OCSP requests mean improved availability and reliability all over the globe.
What this means to youIt is strongly recommended that any firewall policies and/or access control devices use URLs and not IP addresses. Symantec can change these IP addresses at any time without notification. If possible white list the following entries on your firewall policies and/or access control devices to ensure seamless access to our OCSP services.
*.thawte.com
*.geotrust.com
*.ws.symantec.com
*.symcb.com
*.symcd.com
The reference to a faster response time due to many more servers being
available to respond to OCSP requests fits with the
e8218.dscb1.akamaiedge.net.0.1.cn.akamaiedge.net host name
associated with the IP address.
Akamai Technologies
is a
content delivery network (CDN) and
cloud services
provider that provides a variety of network services to other companies; in
this case it is likely providing the servers for Symantec's OCSP service.
I also found the relevant IP address, 23.4.187.27, in Symantec's Symantec_OCSP_IPs page. I've also saved a copy of that Symantec OCSP server list. Symantec has an article titled What is Online Certificate Status Protocol (OCSP)? that lists the following benefits of OCSP over using a Certificate Revocation List (CRL) for determining if a website's security certificate is still valid or has been revoked:
I installed Wireshark on the system and rebooted it. When I started Wireshark and set a filter for TCP traffic to port 80, the well-known port for HTTP traffic, I saw a lot of CRL traffic.
I opened Firefox and had it restore the previous session. I then checked
for any traffic to/from the 23.4.187.27 IP address with Wireshark by using
ip.addr == 23.4.187.27, but did not see any. However, when
I applied the filter ocsp.requestList
(see
Display Filter Reference: Online Certificate Status Protocol for
other OCSP-related filters), I did see an IP address,
23.52.91.27, in the Symantec OCSP IPs
list. When I looked at the information for the request by clicking on the
arrowhead next to Online Certificate Status Protocol in the middle pane
of the Wireshark window, I saw a Host: gp.symcd.com line.
In the HTTP/1.1 protocol, a host: fqdn header, where
fqdn is the
fully qualified domain name (FQDN) for a host, e.g., www.example.com, is
used to tell a web server which website on the server a browser wishes to
access, since a webserver may house multiple websites.
In an OCSP packet where the "info" field showed "Request", I saw a serial number for a certificate for a website that was being submitted to the OCSP server at the 23.52.91.27 address by clicking on Online Certificate Status Protocol, then tbsRequest, then requestlist, then Request, then reqCert, and then hashAlgorithm (SHA-1). SHA-1 is a cryptographic hash function.
I clicked on "SerialNumber:" to select the serial number and then hit Ctrl-C (the "ctrl" and "C" keys together) to copy the serial number to the clipboard. I then opened up Microsoft Notepad and pasted the serial number into the Notepad window with Ctrl-V. The serial number was the one below:
serialNumber: 0x4e43b6166e438e266b7968df879d6633
If you want to correlate the serial number that Wireshark shows for the OCSP certificate request with a website, in Firefox on a Microsoft Windows system, you can click on the 3 horizontal bars, one below the other, at the top, right-hand side of the Firefox window which will reveal a menu where you can select Options. On the Options window, click on Advanced , where, under Certificates you should see the check box checked for "Query OCSP responder servers to confirm the current validity of certificates". If you ever want Firefox to stop checking the validity of certificates with OCSP servers, you can uncheck that box.
If you click on the View Certificates button, you can then click on individual certificate entries to see the serial number for certificates stored on the system.
E.g., the one for addons.mozilla.org is shown below:
Firefox stores certificates in cert8.db which is
in the account's profile directory. The profile directory on a Microsoft
Windows system can be found at
C:\Users\acctname\AppData\Roaming\Mozilla\Firefox\Profiles\xxxxxxxx.default
where acctname is the name of the relevant account and xxxxxxxx
is a sequence of random chacters, e.g.,
C:\Users\Pam\AppData\Roaming\Mozilla\Firefox\Profiles\nnhb4be5.default.
C:\Users\Pam\AppData\Roaming\Mozilla\Firefox\Profiles\nnhb4be5.default>dir cert8.db
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pam\AppData\Roaming\Mozilla\Firefox\Profiles\nnhb4be5.default
08/13/2017 08:13 PM 671,744 cert8.db
1 File(s) 671,744 bytes
0 Dir(s) 861,926,846,464 bytes free
C:\Users\Pam\AppData\Roaming\Mozilla\Firefox\Profiles\nnhb4be5.default>Note: instructions written for Firefox 55.0.1 and Wireshark 2.4.0 on a Microsoft Windows 10 system.