

d2e24t2jgcnor2.webhostoid.com in the browser's address bar.
When I retyped the correct address, the page I wanted appeared. I tried
mistyping a few other domain names and putting in some site names I knew were
bogus since the domains had never been registered. Every time I did that I saw
a reference to the webhostoid system appear in the address bar. E.g., I tried
http://slowfood123.com and saw the following address appear in the address bar:
http://d2e24t2jgcnor2.webhostoid.com/Secure/Error?URL=http%3A%2F%2Fslowfood123.com%2F&ResponseCode=502&user_id=82f89196-4a1a-41ef-b50b-1e8517cdb788&uc=20150104&subid=20150104&source=&version=1.0.5476.25517&implementation_id=geniusbox-spigot&block_host=False®=False&redirectms=True&process=iexplore
And the error message below was displayed:
slowfood123.com
502 ErrorIt appears the website you are trying to visit is having technical difficulties or is no longer available.
Please go back and try your request again or try searching Google to find another website with what you're looking for!
I suspected some software on the system was now redirecting web traffic to the webhostoid.com site. When I checked the proxy server settings in Internet Explorer - see Checking Microsoft Windows proxy server settings - I found the system was now configured to route all HTTP and HTTPS traffic to a proxy server listening on the system local loopback address , i.e., 127.0.0.1, on port 55833. I.e., traffic to websites from the system was now being routed through proxy server software running on the system itself that had been installed on the system without my permission. Note: the port this malware uses for the proxy server it installs will vary; when I later rebooted the system I found the registry entry it uses to specify the proxy server port had been changed to 64696.
You can check the port the Genius Box malware is using for its proxy
server setting from a command with a reg query command.
C:\>reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v ProxyServer
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
ProxyServer REG_SZ http=127.0.0.1:64696;https=127.0.0.1:64696Since I had not knowingly granted any software the right to set itself up as a proxy server on the system, I blocked the system's access to the Internet at the firewall and began investigating this unwanted and suspicous alteration to the system's configuration.
After blocking access to the Internet by the system, I tried accessing another website through a browser on the system and saw the following:
[GeniusBox] The socket connection to d2e24t2jgcnor2.webhostoid.com failed.
ErrorCode: 10060.
A connection attempt failed because the connected party did not properly
respond after a period of time, or established connection failed because
connected host has failed to respond 54.225.130.198:80
I blocked access to the Internet by the system, but left its access to the DNS server on the LAN in place, so it could look up IP addresses for domain names, but couldn't access systems outside of the LAN.
Later, when I checked the IP address of the webhostoid host with nslookup, I saw the IP address below:
Name: d2e24t2jgcnor2.webhostoid.com
Address: 54.243.116.107
Checking both the 54.225.130.198 and 54.243.116.107 through the American Registry for Internet Numbers website, I found the IP addresses had been assigned to Amazon Technologies, so webhostoid appeared to be using Amazon Web Services .
Microsoft Windows systems store the IP address for a proxy server Windows has
been configured to use in the Windows Registry under
HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings.
If you check the value for ProxyServer there, you will see
the IP address and port number being used for a proxy server, if one is being
used. I wanted to know when that registry value had last been modified. The
Windows regedit tool doesn't display the time stamp for when a
registry value was last modified, so I searched for ProxyServer
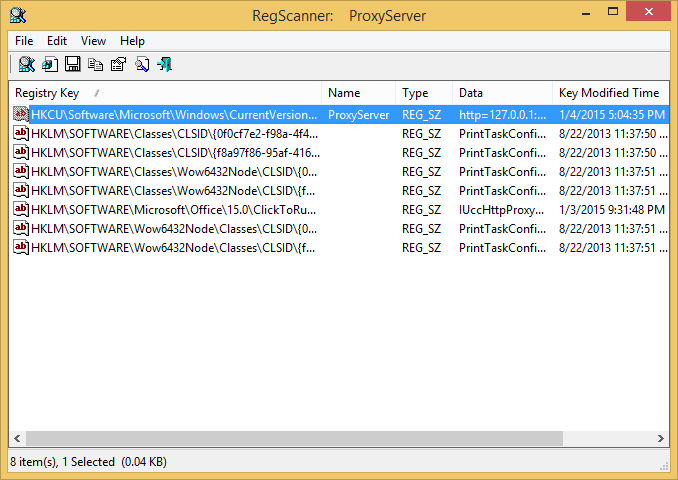
with RegScanner, a
free tool from NirSoft.
It indicated that the ProxyServer value had been set under
HKEY_USERS\S-1-5-21-3084690208-3888753220-1328190815-1115\Software\Microsoft\Windows\CurrentVersion\Internet Settings at 5:04:35 PM on January
4, 2015. The Security Identifier (SID) under HKEY_USERS, i.e.,
the id beginning with "S-1-5-21" was the SID for the currently logged on user.
I track the registry and file changes to a system when I install software
with Total Uninstall, so I examined its
log of the changes made when I installed Vuze
Bittorrent Client, which had been on the list of software my wife wanted
installed on the system, since Total Uninstall indicated the installation
of that program had completed at 5:06 PM on January 4, 2015, i.e., when
the installation of Vuze was completed and I indicated to Total Uninstall that
it should report on the changes, it had completed its assessment less than two
minutes after the proxy server value had been set in the registry. The Total
Uninstall report showed a GeniusBox directory was created during
the installation of Vuze with a settings.config file being created
in the GeniusBox directory at 5:04 PM. The contents of that directory are
listed below:
C:\>dir /ad %USERPROFILE%\AppData\Local | find /i "GeniusBox"
01/04/2015 05:04 PM <DIR> GeniusBox
C:\>dir /s %USERPROFILE%\AppData\Local\Genius
Box
Volume in drive C has no label.
Volume Serial Number is 5C60-1B61
Directory of C:\Users\JDoe\AppData\Local\GeniusBox
01/04/2015 05:04 PM <DIR> .
01/04/2015 05:04 PM <DIR> ..
12/18/2014 03:43 PM 8,704 certmanager.exe
12/29/2014 03:11 PM 872,672 Client.exe
12/18/2014 03:43 PM 55,632 makecert.exe
01/04/2015 05:04 PM <DIR> Resources
01/04/2015 05:04 PM 115 settings.config
12/29/2014 03:11 PM 18,656 Tasks.exe
01/04/2015 05:04 PM 913 TrustedRoot.cer
12/29/2014 03:11 PM 761,056 Uninstall.exe
12/29/2014 03:11 PM 750,304 Updater.exe
8 File(s) 2,468,052 bytes
Directory of C:\Users\JDoe\AppData\Local\GeniusBox\Resources
01/04/2015 05:04 PM <DIR> .
01/04/2015 05:04 PM <DIR> ..
12/18/2014 03:43 PM 90,112 certutil.exe
12/18/2014 03:43 PM 208,896 libnspr4.dll
12/18/2014 03:43 PM 28,672 libplc4.dll
12/18/2014 03:43 PM 24,576 libplds4.dll
12/18/2014 03:43 PM 364,544 nss3.dll
12/18/2014 03:43 PM 106,496 smime3.dll
12/18/2014 03:43 PM 372,736 softokn3.dll
7 File(s) 1,196,032 bytes
Total Files Listed:
15 File(s) 3,664,084 bytes
5 Dir(s) 3,916,020,883,456 bytes freeThe %USERPROFILE% environment variable points to the current user's
profile directory, usually C:\Users\Username where
Username is the account name for the user.
The presence of files named certutil, certmanager.exe
, makecert.exe, and TrustedRoot.cer looked
ominous, since at this point it appeared this "GeniusBox" software configured
the system so it could monitor HTTPS, i.e., the encrypted web traffic, as well
as the unencrypted HTTP traffic. Their presence made me wonder if this
dangerous digital ordure had positioned itself for a
man-in-the-middle attack by putting a
security certificate on the system that would allow it to decrypt and eavesdrop
on HTTPS traffic giving it access to login ids and passwords to otherwise secure
sites, with the potential to steal banking credentials, credit card numbers, as
well as other sensitive information. See
Viewing the Trusted
Root certificates on a Windows system for instructions on how to
view the trusted root
certificates on a Microsoft Windows system and for further information
on the trusted root certificate installed by the GeniusBox malware.
I right-clicked on the TrustedRoot.cer file in the GeniusBox directory and chose "Open", which on a Microsoft Windows system will provide details on the certificate. I saw the following:
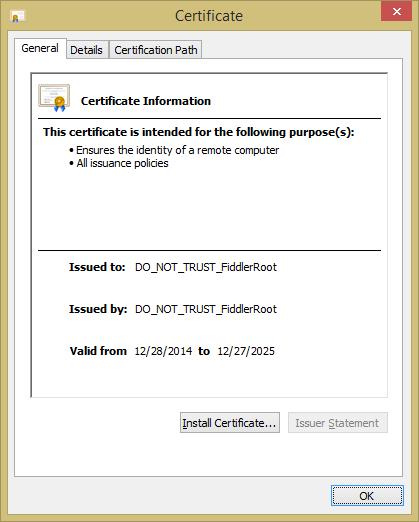
The details under the General tab were as follows:
| Issued to: | DO_NOT_TRUST_FiddlerRoot |
| Issued by: | DO_NOT_TRUST_FiddlerRoot |
| Valid from | 12/28/2014 to 12/27/2025 |
When I clicked on the Certification Path tab, the only entry I saw under "Certification path" was DO_NOT_TRUST_FiddlerRoot
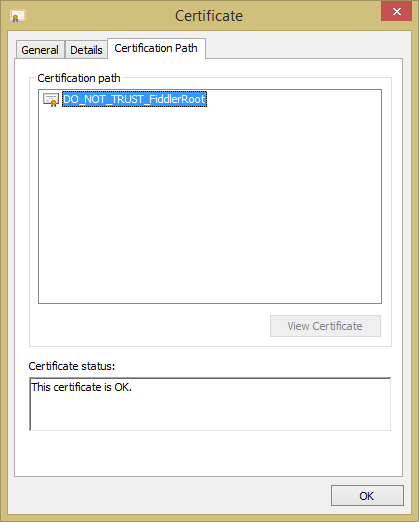
The starting date for the "Valid from" date range was December 28, 2014.
All of the files in the %USERPROFILE%\AppData\Local\GeniusBox\Resources
directory had a date stamp of December 18, 2014 and many of the files
in the %USERPROFILE%\AppData\Local\GeniusBox directory had
a date of December 29, 2014, making the starting date on the certificate
consistent with the installation of this malware during the installation
of Vuze.
It appears the Genius Box adware may have used the Microsoft
Makecert.exe (Certificate Creation Tool), since when I right-clicked
on the makecert.exe program in the GeniusBox directory and
chose Properties, and then clicked on the Details
tab, I saw Microsoft Corporation listed as the value for
"Copyright" - see Makecert.exe Properties
.
I didn't see Microsoft Corporation listed when I checked the properties
of the certmanager.exe file (see
image) in the GeniusBox directory.
Microsoft's command line tool is
Certmgr.exe (Certificate Manager Tool). There was no copyright information
displayed for Client.exe, either. When I checked the digital
signature on the file - see
Checking the digital signature for a file under Microsoft Windows - I found
it was signed by JoltLogic, a known adware purveyor.
When I checked the Details tab under Properties
for Tasks.exe, I saw "Copright © 2014", but no
company or invidual was identified. Checking its digital signature, I fond
it was also signed by JoltLogic.
C:\Users\JDoe\AppData\Local\GeniusBox>powershell
Windows PowerShell
Copyright (C) 2014 Microsoft Corporation. All rights reserved.
PS C:\Users\JDoe\AppData\Local\GeniusBox> Get-AuthenticodeSignature Tasks.exe | Format-List
SignerCertificate : [Subject]
CN=Joltlogic, O=Joltlogic, STREET=4600 Madison Ave
FL 10, L=Kansas City, S=Missouri, PostalCode=64112,
C=US
[Issuer]
CN=COMODO Code Signing CA 2, O=COMODO CA Limited,
L=Salford, S=Greater Manchester, C=GB
[Serial Number]
5EE011413A702F6705B25B34B674F3AB
[Not Before]
7/15/2014 8:00:00 PM
[Not After]
7/16/2015 7:59:59 PM
[Thumbprint]
16CE9D5ADE81FCA57EF3F545F631DFD7B6D6C01E
TimeStamperCertificate :
Status : Valid
StatusMessage : Signature verified.
Path : C:\Users\JDoe\AppData\Local\GeniusBox\Tasks.exe
PS C:\Users\Thorlack\AppData\Local\GeniusBox> exitLooking for text strings within it using the Sysinternals strings program, I saw the following included within it as well as others:
set_ResetProxy
client
BrowserSafeguard
software\browsersafeguardupdater
software\webinternetsecurity
software\webinternetsecurityinstalled
webinternetsecurity
geniusbox-dl
GeniusBox
www.geniusbox.net
d29ir131ce1iq8.cloudfront.net
aujiwvmoskdjlajksek.centde.com
geniusbox
dvfw75w58kcex.cloudfront.net
d2ebu295n9axq5.cloudfront.net
http://aujiwvmoskdjlajksek.centde.com/release/gb-installer.exe
Client.exe
Uninstaller
uninstall.exe /
Updater
Updater.exe /
Tasks
Tasks.exe
Updater.exe
http://www.geniusbox.net/home/thankyou
software\geniusboxinstalled
software\Search Extensions
software\GeniusBox
updater
uninstall
tasks
makecert.exe
resources\certutil.exe
resources\libnspr4.dll
resources\libplc4.dll
resources\libplds4.dll
resources\nss3.dll
resources\smime3.dll
resources\softokn3.dll
The nss3.dll file
in the GeniusBox subdirectory Resources has copyright information
for Netscape Communications
(image),
a company responsible for an early browser, Netscape Navigator, which released
its source code and created the
Mozilla Organization
, which now produces the free and open-source browser Firefox. All of
the other DLL files in
the GeniusBox\Resources directory display Netscape Communications
copyright information when the properties information is viewed.
The certutil.exe program in the GeniusBox\Resources
directory has no identifying copyright information nor is it digitally signed.
It uses the .dll files in the directory as can be seen by checking it with
the Sysinternals strings utility. You can see the arguments
it takes by running it from a command prompt with no arguments.
The certificate the adware inserted into the root certificates list refers to Fiddler. The Fiddler proxy server application was created by Eric Lawrence, who was formerly a Program Manager on the Internet Explorer development team at Microsoft. Fiddler can capture both HTTP and HTTPS traffic and log it for later examination by utilizing a man-in-the-middle system using a self-signed certificate. From its position in the middle of a web browser and a web server, Fiddler can also modify, or "fiddle" with the traffic, if you will, from one system to another without either of the end parties being aware that Fiddler has modified traffic from or to them. Further information on the tool is also available at Decrypting HTTPS-protected traffic. The FAQ on that site notes in regards to the decryption of HTTPS:
Q: The HTTPS protocol was designed to prevent traffic viewing and tampering. Given that, how can Fiddler2 debug HTTPS traffic?
A: Fiddler2 relies on a "man-in-the-middle" approach to HTTPS interception. To your web browser, Fiddler2 claims to be the secure web server, and to the web server, Fiddler2 mimics the web browser. In order to pretend to be the web server, Fiddler2 dynamically generates a HTTPS certificate.
At the Decrypting HTTPS-protected traffic page, you can see that Fiddler generates a certificate with the Certificate Authority (CA) listed as "DO_NOT_TRUST_FiddlerRoot".
Fiddler was subsequently acquired by another company, Telerik, a Bulgarian company which offers software tools for application development. The software can be downloaded for free from the company's website at Fiddler free web debugging proxy.
The "Key Features" section of the company's page for Fiddler notes that the software can "easily manipulate and edit web sessions", "decrypt HTTPS traffic and display and modify requests using a man-in-the-middle decryption technique", and "Fiddler is a free web debugging proxy which logs all HTTP(s) traffic between your computer and the Internet."
The Fiddler software has legitimate traffic analysis and debugging uses, but in this case, Genius Box appears to be using a similar technique for nefarious purposes. Using RegScanner to search through the Windows registry for references to Fiddler, I found the following:
| Registry Key | HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\RunOnce |
| Name | Import FF:0 |
| Type | REG_SZ |
| Data | "C:\Users\JDoe\AppData\Local\GeniusBox\Resources\certutil.exe" -A -n "DO_NOT_TRUST_FiddlerRoot" -t "TCu,TCu,TCu" -i "C:\Users\JDoe\AppData\Local\GeniusBox\TrustedRoot.cer" -d "C:\Users\JDoe\AppData\Roaming\Mozilla\Firefox\Profiles\l7fnkeja.default" |
| Key Modified Time | 1/4/2015 5:04:35 PM |
| Data Length | 261 |
Though the GeniusBox software may only be generating a similar root certificate as the one used by Fiddler, but not actually incorporating Fiddler code, the GeniusBox software does seem to be using a similar technique. It seems clear to me at this point that this adware/spyware has completely nullified any chance for security on the system on which Vuze and it were installed when the account under which Vuze was installed is used on the system for visiting websites, even ones that might otherwise be secure by the use of HTTPS to encrypt traffic between the client browser and the web server, since this software can intercept all traffic and could provide its own credentials to the brower in place of any from any site visited, even a banking site. It could intercept any userids, passwords, credit card numbers, etc. and could do with those whatever the developers of the software might choose to do with the information now accessible to them through giving their software man-in-the-middle attack capabilities.
I found that the software only runs when a login is made to the account under which Vuze, and thus the Genius Box software, was installed. But, if that account had more than standard user account access to the system, I would still be concerned about the safety of other accounts on the system, though I didn't see the proxy server not the assoicated Genius Box tasks in the Task Scheduler running.
Other system changes I noted from the installation of the Genius Box software include the creation of three scheduled tasks, which run when a logon occurs for the account under which the Vuze software is installed. When this adware is installed it creates scheduled tasks for itself in the Windows Task Scheduler. You can search on Schedule Tasks in Windows to locate and run the Task Scheduler. In the Task Scheduler Library, you will see a task named "GeniusBox". The security options for the task include "Run when user is logged on" and "Run with highest privileges". If you click on the Triggers tab, you will see a one time setting reflecting the day and time the adware was installed and then a scheduled rerunning of the software periodically after that as well as a trigger to run it "At log on of any user". E.g., on the infected system I checked, I saw the following in the "Details" field for the "One time" trigger (image):
At 5:04 PM on 1/4/2015 - After triggered, repeat every 06:00:00 indefinitely."
Under the Actions tab, I saw "Start a progam" listed as the action with the following under the Details tab:
cmd.exe /C start "" "C:\Users\JDoe\AppData\Local\GeniusBox\client.exe"
You can click on the History tab to see the history of the activation of the scheduled task.
Since this malware was installed, I've seen "Tasks has stopped working" windows appear (image), which I suspect may be the GeniusBox tasks.exe program crashing, perhaps because I've blocked any access from the system to the Internet.
Another scheduled task named "Check Updates" is also created by the
installation of GeniusBox (image)
It is also configured to "Run ony when user is logged on" and to "Run with
highest privileges". The triggers are the same as for the GeniusBox scheduled
task. The actions specified for it are to run the updater.exe
and tasks.exe files in the GeniusBox directory.
A third scheduled task created by the GeniusBox software is
"Validate Installation"
(image). The triggrs are
exactly the same as the other two tasks with the task scheduled to run
indefinitely. The actions are to run the updater.exe and
uninstall.exe programs in the GeniusBox directory.
You can uninstall the Genius Box software by going to Uninstall a program from the Programs section of the Control Panel. The entry for the software is named "GeniusBox 2.0"; the publisher is also listed as "GeniusBox 2.0". When I double-clicked on it, a GeniusBox Uninstall window opened.
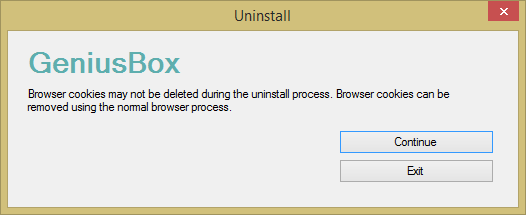
When I clicked on Continue in that window, I saw
an "Uninstall complete" window shortly afterwards. When I checked
the registry afterwards, I saw the ProxyServer value had
been removed from
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet
Settings and ProxyEnable was reset to 0
(image). I also saw the three scheduled
tasks were removed. It also removed the registry key under HKEY_USERS
at \Software\Microsoft\FiddlerCore it had created at
the installation of the software. It also deleted all files it had created in
the AppData\Local directory. Checking the entries listed
under the Logon tab with the Sysinternals
Autoruns utility, a program which shows which programs will run when
the system boots or a user logs into the system, I found that the
GeniusBox uninstall process had not removed Import FF:0
within the
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\RunOnce
registry key, which had a value of
"C:\Users\JDoe\AppData\Local\GeniusBox\Resources\certutil.exe" -A -n "DO_NOT_TRUST_FiddlerRoot" -t "TCu,TCu,TCu" -i "C:\Users\JDoe\AppData\Local\GeniusBox\TrustedRoot.cer" -d "C:\Users\JDoe\AppData\Roaming\Mozilla\Firefox\Profiles\l7fnkeja.default",
though. I manually deleted that entry from the registry using regedit by
right-clicking on it and choosing "delete". So GeniusBox does actually remove
itself itself and does a fairly good job of cleaning up after itself when
removed. But given the means it used to convey ads, by use of a proxy server
and the installation of its own security certificate into the root certificates
list, anyone with a system on which the software was installed appears to be at
the mercy of the JoltLogic developer(s), since their software appears to grant
them the capability to spy on all web traffic from the system when the account
under which it was installed is used. Do they only use the software to display
ads? Perhaps, but given that they appear to have the capability to engage in
much more nefarious activities would you want to make yourself so vulnerable by
allowing their software the capapbility to snoop on all web traffic for the
affected account on a system?
I am aware that some free software comes bundled with additional software from other companies/developers, sometimes adware like the GeniusBox software. When I install software, I always pick the "advanced" or "custom" install options when they are available to give me the chance to opt out of bundled software I don't want, avoid shortcuts being created on the desktop, and select the installation directory. I believed I had opted out of all of the bundled software that came with Vuze in this case. Perhaps I thought I had declined the installation of this bundled adware, but had failed to do so. Perhaps I hit Enter thinking I had declined it - see Avoiding the installation of adware when installing Vuze - when the window appears regarding the installation of GeniusBox during a custom installation. I'm willing to accept that as the explanation, but at this point I must conclude that one must be very careful when installing Vuze to avoid its bundled adware.
I certainly understand the need to cover development costs for software, but the fact that Vuze bundled the GeniusBox software with their software and the manner in which the GeniusBox software operates does not give me confidence that the Vuze software can be regarded as safe, unless care is taken by users when installing it to avoid its bundled adware. I feel the developers/publishers of Vuze must be regarded with some wariness, since they seem to have little regard for the privacy and security of the users of their product when they bundle such other software with their own. I.e., are they unaware of how this bundled software achieves its ends, or did they simply not even check on how it operates, or did they simply not care?
Created: Monday January 19, 2015