

When uou start the installation process, you will be able to choose between the default installation, which installs the most common features, and a custom installation. You will need 78 MB of free space on the hard disk drive where you will install the software.
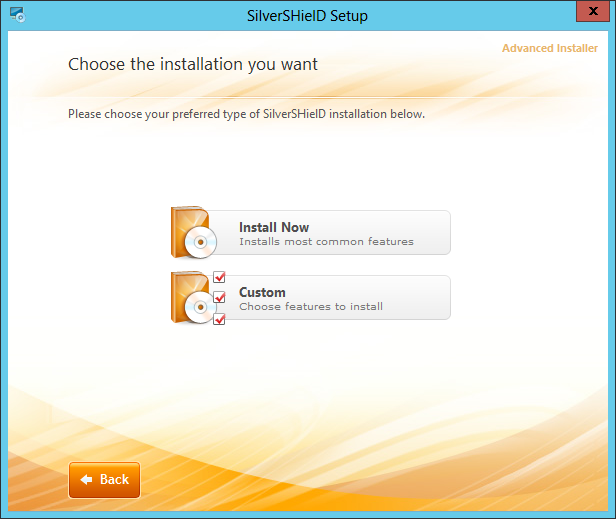
The options that you can uncheck, if you choose "Custom", are "Main Feature" and "64-bit". If you have a 64-bit version for your operating system, leave the 64-bit option checked. If you don't know whether you have a 32-bit or 64-bit version of Windows, see Microsoft's 32-bit and 64-bit Windows: frequently asked questions webpage.
At the next step, you will be prompted to accede to the
software license agreement
(PDF).
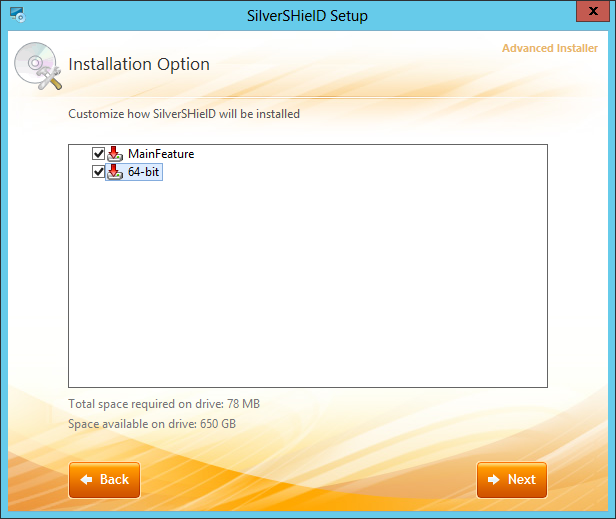
After accepting the software license, at the next step you can
choose the installation directory. The default location is
C:\Program Files\Extenua\SilverSHielD\.
At the next window, you can click install to commence the installation. After the installation has finished, you need to run the SilverSHielD Management Console.
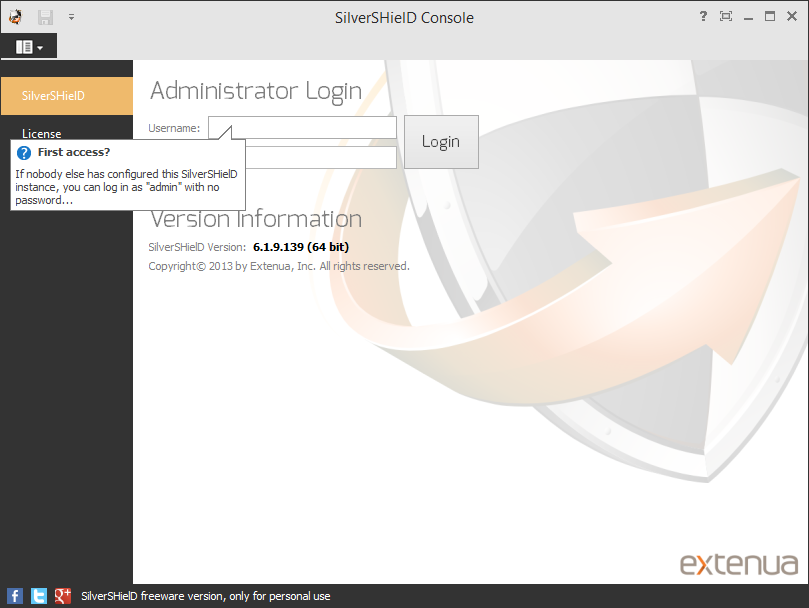
You can log into the console as admin with no password initially. A small Change Password window will then open where you will need to provide a new password; you will need to type the password twice in that window. The console window will then open where you can change settings.
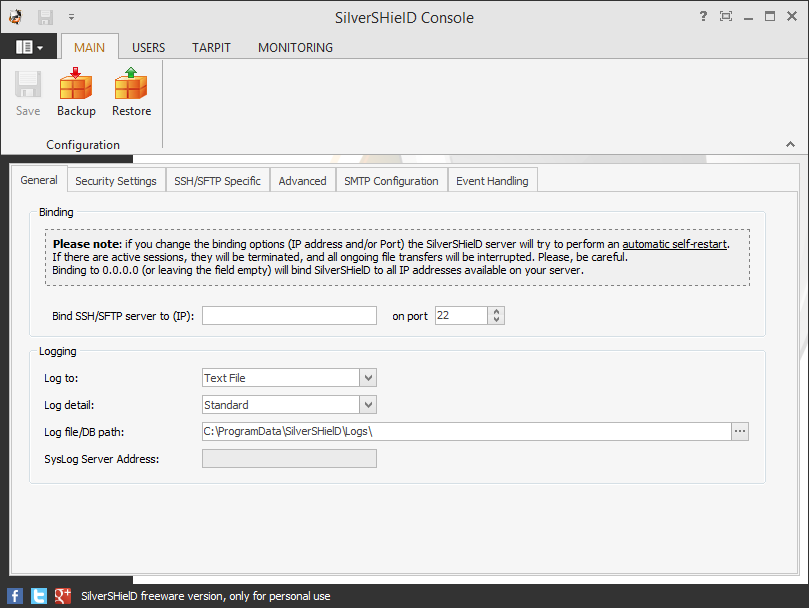
By default, the program listens on the default SSH port of 22, but you can
change the port, if you prefer. If you change the port, you will need to
restart the SilverSHielD service; you can do so from an
administrator command prompt window
using the net stop and net start commands.
C:\WINDOWS\system32>net stop SilverSHielD The SilverSHielD service is stopping. The SilverSHielD service was stopped successfully. C:\WINDOWS\system32>net start SilverSHielD The SilverSHielD service is starting. The SilverSHielD service was started successfully. C:\WINDOWS\system32>
You can also set a syslog server address under the General tab for the Main section of the console.
Under the Security Settings tab, you can control SSH access by IP address or subnet.
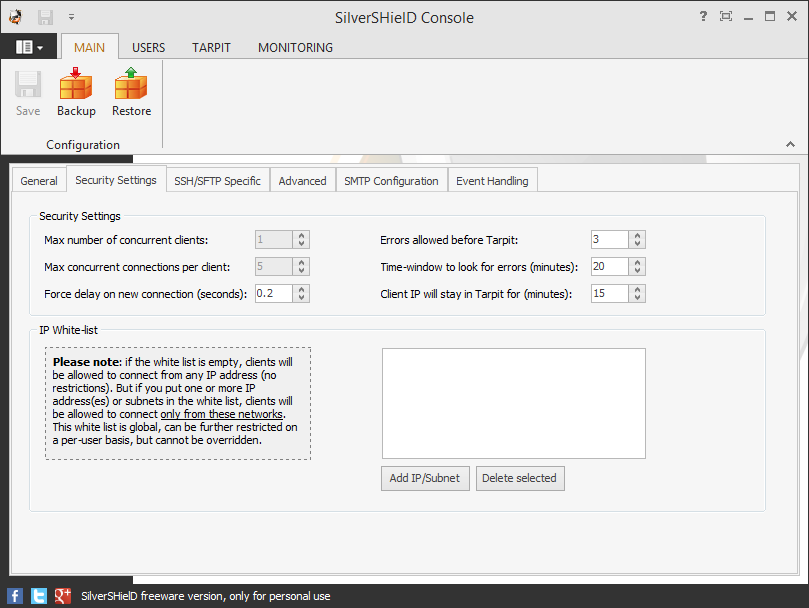
You can also control the maximum number of concurrent clients and the maximum number of connections here, though with the free version these options will be grayed out and you will be limited to one client connection with a maximum of five concurrent connections from that client.
At this tab, you can set the number of failed login attmpts that will be alowed before an IP address is blocked. The default number is 3. After 3 failed login attmpts, the IP address will be placed in the "tarpit". The IP address will remain there for 15 minutes by default. You can click on TARPIT at the top of the window to see the temporarily banned IP addresses.
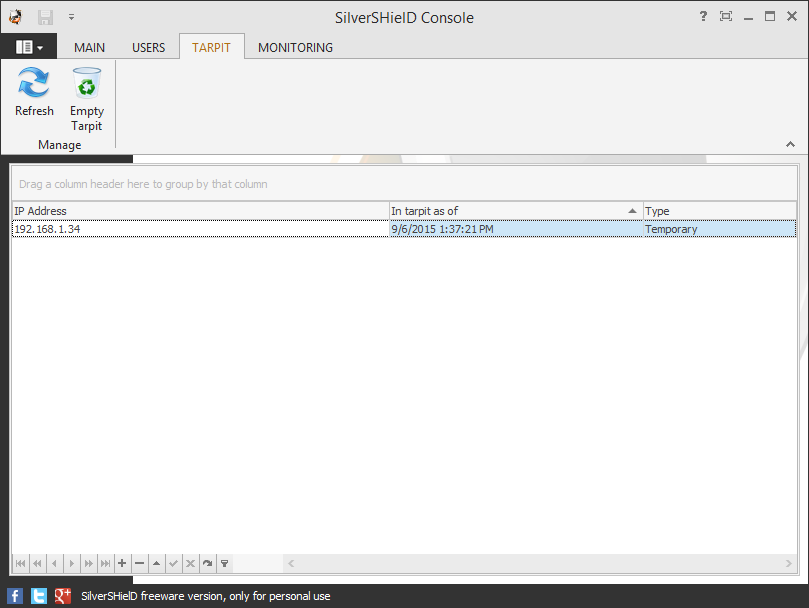
You can click on an entry to select it and then click on the minus sign at the bottom of the window to delete an IP address entry.
From the SSH/SFTP Specific tab in the Main area, you can control tunneling using a white list. If the white list is empty, clients will be allowed to create tunnels via SSH towards any destination (no restrictions). But if you put one or more IP address(es) or subnets in the white list, clients will be allowed to open tunnels only towards these networks. This white list is global, and can be overridden on a per-user basis as explained below.
You can click on USERS to add users that will be allowed to log in to the system by SSH. By default, no one will be allowed to log in, so you will need to make changes in this area before anyone can log in via SSH. You can control the file and directory permissions granted to the user. You can grant or withhold download upload, delete, modify, and rename permissions for files and list, create, delete, and rename permissions for directories.
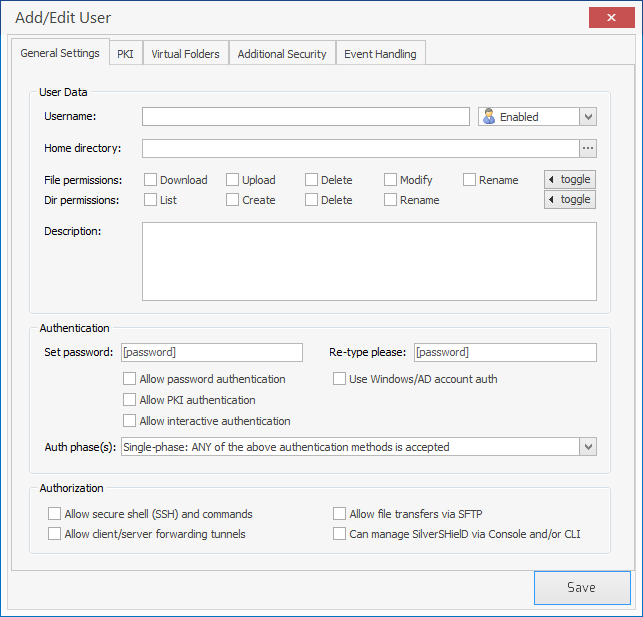
If you are adding a domain user, you can check the check box next to "Use Windows/AD account auth", "Allow password authentication, and "Allow interactive authentication" in the Authentication section to use the Active Directory credentials for the user, i.e., the user can use the same userid and password with which he/she logs into the Windows domain.
Be sure you also check the "Allow secure shell (SSH) and commands" check box in the Authorization section, otherwise login attempts will fail with a "shell request failed on channel 0" message at the SSH client end. Also check "Allow file transfers via SFTP", if you wish to allow SFTP file transfers, and check "Allow client/server forwaring tunnels", if you wish to permit the user to set up SSH tunnels. There is also a "Can manage SilverSHielD via Console and/or CLI" option in the Authorization section.
If you wish to restrict the destination IP addresses to which a user can establish an SSH tunnel, click on the Additional Security tab at the Add/Edit User window. In the "Allowed Tunnels" section, you can restrict the destination IP address(es) and/or network(s) towards which the specific user is allowed to crate forwarding tunnels. If this list is empty, which it is by default, all server-wide IP restrictions (if any) will still apply.
Note: this review was written for SilverSHielD 6.1.9.139, which is the current version as of September 6, 2015.