

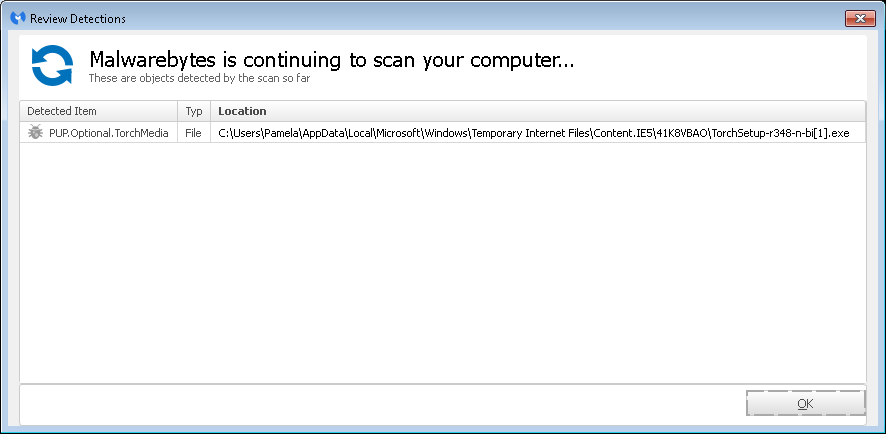
The file was located beneath the system user's
%LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5
directory. When I checked on the time stamp on the file, I found it
had a time stamp of October 29, 2014.
C:\Users\Administrator>dir "C:\Users\Pamela\AppData\Local\Microsoft\Windows\Tem
porary Internet Files\Content.IE5\41K8VBAO\TorchSet*"
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Microsoft\Windows\Temporary Internet
Files\Content.IE5\41K8VBAO
10/29/2014 04:38 PM 225,619 TorchSetup-r348-n-bi[1].exe
1 File(s) 225,619 bytes
0 Dir(s) 875,457,449,984 bytes freeI uploaded the file to Google's VirusTotal site, a site that checks uploaded files with multiple antivirus programs. Four of the fifty-four programs with which it scanned the file reported it as unsafe. Those four are listed below. The full report can be viewed here.
| Antivirus | Result | Update |
|---|---|---|
| Agnitum | Riskware.TorchMedia! | 20141205 |
| ClamAv | Win.Adware.Searchsuite-3 | 20141207 |
| ESET-NOD32 | a variant of Win32/TorchMedia | 20141207 |
| Malwarebytes | PUP.Optional.TorchMedia | 20141207 |
When I clicked on the File detail tab on the VirusTotal report, I saw the following:
| Copyright | Copyright (C) 2014 Torch Media Inc. |
| Publisher | Torch Media, Inc |
| Product | Torch |
| File version | 36.0.0.8226 |
| Description | Torch Browser |
When the scan completed, that item was the only one reported. I had Malwarebytes Anti-Malware quarantine the file and then reboot the system, though I wasn't expecting the removal of that file to resolve the performance issue with the system. I don't believe the user deliberately chose to download the file.
The Wikipedia article Torch (browser) notes the following regarding the Toch browser:
Torch Browser is a free, ad-supported, closed source, Chromium-based web browser and Internet suite developed by Torch Media.[1] The browser handles common Internet-related tasks such as displaying websites, sharing websites via social networks, downloading torrents, accelerating downloads and grabbing online media, all directly from the browser.[2] Torch Browser is commercial freeware.[3] ... Torch Media receives payments from companies like Conduit to bundle sponsor software with the browser. Users may be asked to install search toolbars or adware programs during installation. While this practice is deemed controversial by some, users are given a chance to opt out of sponsored software and Torch will work fine without it.[13]
When checking Malwarebytes Daily Protection Log, which is viewable by opening the program and clicking on "History" on the menu bar at the top of its window and then clicking on the "Application Logs" link which will appear on the left side of the window. You will then see a list of Application Logs. If you double-click on the one that has a type of "Protection Log", you will see a log similar to the following:
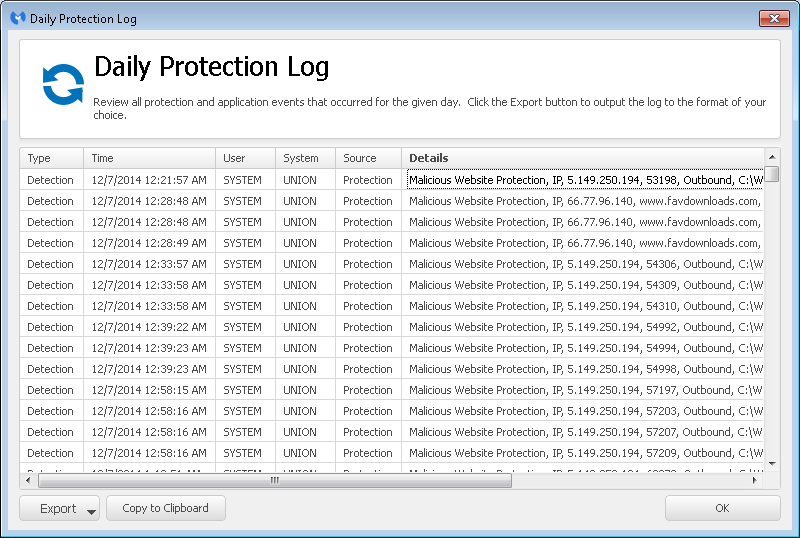
There is an "Export" button at the bottom of the window which will allow
you to export the log data to a .txt or .xml file. When I examined the
text log, I saw that the
attempts to access malicous websites were associated with
C:\Windows\explorer.exe. I thought something else was
causing explorer.exe to be associated with attempts to access those sites,
but I uploaded it to VirusTotal anyway. Someone else had uploaded the
same file a short while before I was going to upload it, so I viewed the
analysis from that upload, which showed 0 of the 55 antivirus programs
reporting it as malware - see
report.
Note: a file is judged to be the same no on the name, but on its
checksum.
I also examined the DNS log file on the server the system queries for DNS lookups and saw an enormous number of DNS lookups from the system today, a lot of which were to sites associated with advertising, even though the user had not used the system at all today, though her account was logged in. I don't believe the TorchMedia program was the cause of all of that activity, so eliminating it likely did not eliminate the cause of the slow performance and attempts to access websites Malwarebytes Anti-Malware identified as malicious.
Created: December 7, 2014