

The DOXDesk FavoriteMan webpage links calsdr.dll with the FavoriteMan parasite. Bazooka detects FavoriteMan, but doesn't, at least as of April 25, 2005, recognize calsdr.dll as being associated with that adware/spyware. There is a Bazooka webpage with instructions on how to manually remove FavoriteMan at http://www.kephyr.com/spywarescanner/library/favoriteman/index.phtml.
I used FileAlyzer to analyze the file. The file has a time stamp of Saturday, March 13, 2004 at 1:14:12 PM. FileAlyzer shows the following "Version" information:
| File version | 2,0,0,1 |
| Company name | 4 |
| Internal name | |
| Comments | |
| Legal copyright | |
| Legal trademarks | |
| Original filename | |
| Product name | |
| Product version | 2,0,0,1 |
| File description | Windows Help 4 Smart Browsing |
| Private build | |
| Special build |
It isn't unusual for adware/spyware not to place a company name in
a
The DOXDesk webpage provides the following information on the parasite:
FavoriteMan is a backdoor downloader implemented as an Internet Explorer Browser Helper Object (BHO) stored in the System32 folder. It periodically connects to its controlling server to download a control text file, which instructs it what software to install and where to download the control file from next.
It also has the facility to add web links to the desktop background and IE Favorites menu as directed by the control file.
Since the DOXDesk webpage states that "FavoriteMan is a backdoor downloader implemented as an Internet Explorer Browser Helper Object (BHO)", I switched Spybot to advanced mode and then clicked on "Tools" and then double-clicked on "BHOs" to see if it listed it as a BHO. The only BHO's it showed were the ones for Acrobat 5 and Spybot's own SDHelper. So I installed BHODemon version 2.0.0.22 and used it to view the BHO's installed. It also reported only the Acrobat and Spybot ones. Looking back through my notes on this system, I found that an Ad-aware scan over a year ago on March 28, 2004 had detected FavoriteMan, which I had it remove, so perhaps the calsdr.dll file is a remnant of previously removed FavoriteMan adware/spyware.
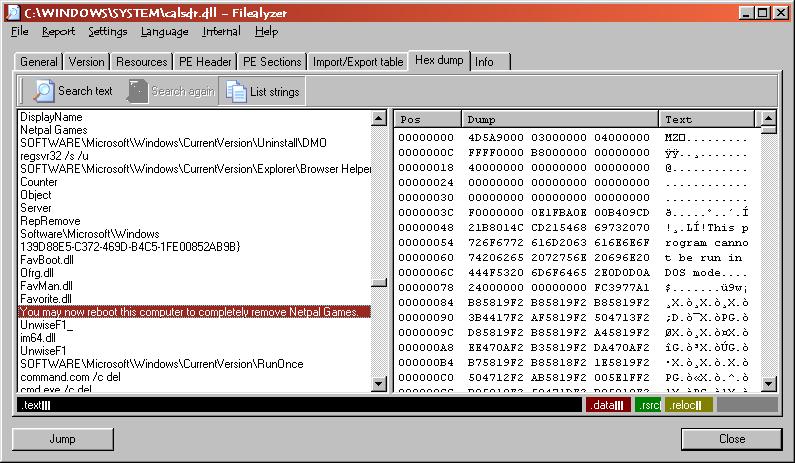
Using FileAlyzer to examine the strings within the file, I see "You may now reboot this computer to completely remove Netpal Games." Netpal Games wasn't something installed on the computer and doesn't appear under "Add/Remove Programs". Neither, of course does "FavoriteMan". The DOXDesk webpage states that Mindset Interactive (now Vista) used to call all its software ‘NetPal’, including the NetPal parasite and Transponder, which they previously controlled."
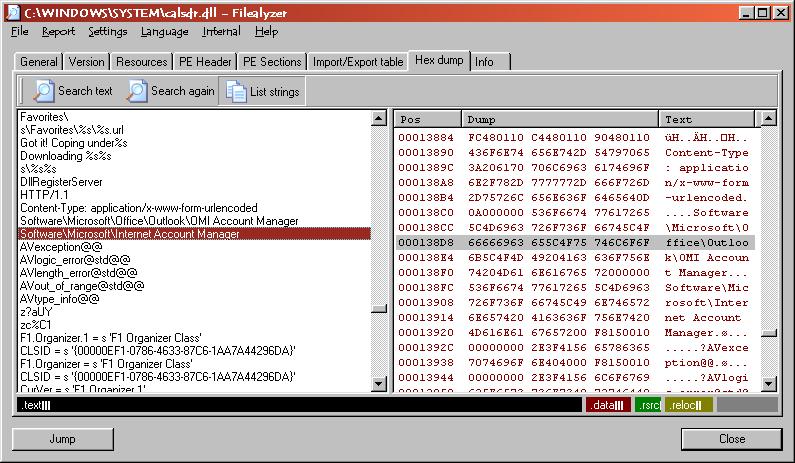
The DOXDesk webpage on FavoriteMan states "The Vista variants contain vestigial code that appears to want to read the user e-mail adress stored in Outlook and Outlook Express settings. However this has not been observed to actually work." And, indeed, when I look at the strings in the file with FileAlyzer by clicking on "Hex dump" and then selecting "List strings", I see "Software\Microsoft\Office\Outlook\OMI Account Manager" and "Software\Microsoft\Internet Account Manager".
I decided just to delete the file, but twice, when I right-clicked on the file in the Windows Explorer to delete it, Explorer crashed. I rebooted the system in safe mode and used regedit to search the registry for any references to calsdr.dll, but none were found. I also rescanned the system with Spybot, but again it found nothing. I rebooted into normal mode and then was able to right-click on the file in the Explorer and delete it.
The versions of programs I tested with and the definitions used with those programs are listed below. I used the update function in all of them prior to running the scans.
| Program | Version | Definitions |
| Bazooka Spyware Scanner | 1.13.03 | 25 Apr 2005 |
| BHODemon | 2.0.0.22 | 25 Apr 2005 |
| ClamWin | 0.83 | 25 Apr 2005 |
| PestPatrol | 4.4.4.81 | PestPatrol.exe: 12/27/04 4.4.4.81 PestPatrolCL.exe: 12/15/04 4.4.4.80 PPCLean.exe: 4/21/05 4.5.9.0 Pest Database: 4/21/05 |
| Spybot Search & Destroy | 1.3 | 2005-04-08 |
| Symantec Antivirus Corporate Edition | 8.00.9374 | 4/22/05 rev. 17 |
For anyone wishing to examine the file, I've provided a zip file containing the calsdr.dll file. The MD5 sum for the calsdr.dll file within it is 19342d732abac3e855aca6a2964f3b5a.
References: