

When she attempted to view the attachment, she received an "access denied" message, probably from the Symantec AntiVirus Corporate Edition client software on her system, but her system was still infected by malware. She said that her system rebooted and now she is seeing a message that her system is infected.
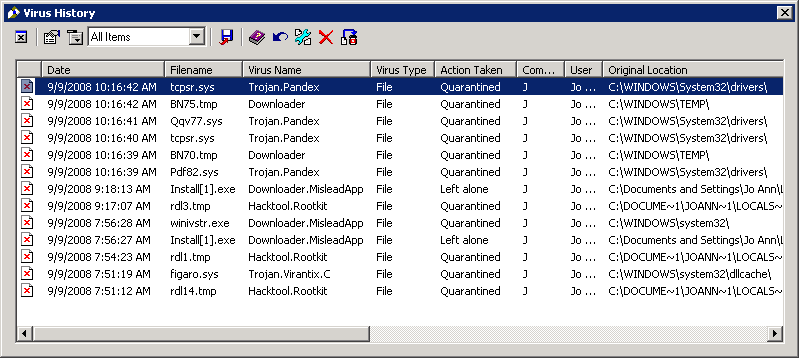
When I checked the status of her system with Symantec AntiVirus Corporate Edition on the server running the Symante System Center, it was reporting that it detected Trojan.Pandex as well as other malware [See SAV Virus History (CSV File)].
When I connected to her system, I saw the following popup warning at the lower right-hand corner of her screen.
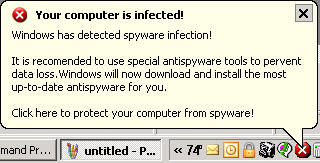
The fake warning message appearing on the system was as follows [Note: "prevent" is misspelled as "pervent"]:
Windows has detected spyware infection!
It is recommended to use special antispyware tools to pervent data loss. Windows will now download and install the most up-to-date antispyware for you.
Click here to protect your computer from spyware!
I brought up the Task Manager and clicked on the Processes
tab to look for processes I didn't recognize. I saw braviax.exe.
I didn't recognize it as a legitimate process on that system, so I searched
for it on the hard disk to see where it was located. I found the file
in C:\WINDOWS\system32. I then checked for the process ID of the
process and killed that process.
C:\>dir /s braviax.exe
Volume in drive C has no label.
Volume Serial Number is D8B5-E4AE
Directory of C:\WINDOWS\system32
09/09/2008 07:51 AM 9,216 braviax.exe
1 File(s) 9,216 bytes
Total Files Listed:
1 File(s) 9,216 bytes
0 Dir(s) 35,570,573,312 bytes free
C:\>tasklist /fi "imagename eq braviax.exe"
Image Name PID Session Name Session# Mem Usage
========================= ====== ================ ======== ============
braviax.exe 1916 RDP-Tcp#4 0 4,684 K
C:\>taskkill /f /pid 1916
SUCCESS: The process with PID 1916 has been terminated.
When I checked the registry with regedit, I found the following key
in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
| Name | Type | Data |
|---|---|---|
| braviax | REG_SZ | C:\WINDOWS\system32\braviax.exe |
I deleted the registry entry. I also found it in
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
I deleted it there as well.
I uploaded the braviax.exe file to
VirusTotal, which is a site
which will scan suspect files with multiple antivirus programs, for analysis.
Fifteen of the thirty-six programs it used reporated the file as malware
[See VirusTotal Report or
VirusTotal Compact Report].
The email message had passed through a Barracuda Spam Firewall, which uses ClamAV, undetected and wasn't stopped by the Symantec AntiVirus Corporate Edition 8.1 software on the user's system.
I decided to install Spybot Search & Destroy on the system. When I uninstalled the old 1.4 version of Spybot Search & Destroy already on the system in preparation for installing the 1.6.0 version, Symantec AntiVirus popped up a warning regarding an infected file detected on the system.
Scan type: Realtime Protection Scan
Event: Virus Found!
Virus name: Hacktool.Rootkit
File: C:\DOCUME~1\JOANN~1\LOCALS~1\Temp\rdlA5.tmp
Location: Quarantine
Computer: J
User: Jo Ann
Action taken: Quarantine succeeded : Access denied
Date found: Tuesday, September 09, 2008 7:33:03 PMI was prompted to reboot the system after uninstalling Spybot Search & Destroy 1.4, which I did.
When I logged into the system after rebooting, I saw the following message from Symantec AntiVirus Corporate Edition:
Scan type: Realtime Protection Scan
Event: Virus Found!
Virus name: Hacktool.Rootkit
File: C:\DOCUME~1\JOANN~1\LOCALS~1\Temp\rdl3.tmp
Location: Quarantine
Computer: J
User: Jo Ann
Action taken: Quarantine succeeded : Access denied
Date found: Tuesday, September 09, 2008 8:05:44 PM
When I brought up the Windows Explorer, I saw the message below from Symantec AntiVirus (SAV):
Scan type: Realtime Protection Scan
Event: Virus Found!
Virus name: Hacktool.Rootkit
File: C:\DOCUME~1\JOANN~1\LOCALS~1\Temp\rdl3.tmp
Location: Quarantine
Computer: J
User: Jo Ann
Action taken: Quarantine succeeded : Access denied
Date found: Tuesday, September 09, 2008 8:05:44 PM
When I closed the Explorer and reopened it, a similar message appeared only
referring to C:\DOCUME~1\JOANN~1\LOCALS~1\Temp\rdlAA.tmp this
time.
When I ran Spybot, it asked me if I wanted to uninstall 1100 temporary files. I chose "yes". It indicated it couldn't remove 276 temporary files, because they were in use. A second attempt to remove thos 276 files also failed.
Spybot found a lot of malware on the system [See
HTML or
TXT report]. For the malware for which
Spybot could provide further details, I've included those details
here. The braviax.exe
file in C:\WINDOWS\system32 was associated with Virantix
by Spybot. Spybot reported "no information available" for Virantix.
Spybot indicated for Premium Search that
"The trojan horse also uses rootkit functionality to hide some of its parts. Removal of this
trojan horse will require a reboot. After the reboot the explorer may not start anymore, this
will require to open Spybot via the taskmanager and fix the remaining parts of PremiumSearch."
Since I was running Spybot through a Remote Desktop Protocol (RDP) connection to the system
on which I installed it, I was afraid I might not be able to get back into the system
remotely after removing it, so I deselected it from the ones I would have Spybot fix.
I also deselected Virtumonde, for the same reason. For it, Spybot stated
"It also adds a randomly named dll to the Winlogon Notify, which will make it very resistable
to removal. Removal requires the computer to be disconnected from the internet and restarted
after first scan and fixing session."
When I had Spybot fix the other entries, I saw the following message:
Some problems couldn't be fixed; the reason could be that the associated files are still in use [in memory].
This could be fixed after a restart.
May Spybot-S&D run on your next system startup?
I chose "yes". Spybot indicated that CouponBar was the only one that
was not fixed.
For Delf.Spool.cn, Spybot had the description below:
This trojan horse replaces the orignal spoolsv.exe with its own to get started by the system and run in background. Variants may also connect to a chinese website in background. After fixing with Spybot-S&D please restore the original spoolsv.exe from the c:\windows\system32\dllcache folder to the c:\windows\system32 folder.
When I checked c:\windows\system32\dllcache, I did not find any
spoolsv.exe there. But Spybot didn't appear to have deleted the
spoolsv.exe file in c:\windows\system32 either, thougn.
I then decided that I should be able to establish a SSH connection to the system
even if there was problem with the GUI login, so I had Spybot remove Premium
Search and Virtumode as well. It indicated that it
fixed those without a problem. I then rebooted the system. When I logged
in afterwards, Spybot indicated it found 275 temorary files. It stated
it couldn't remove 271 of those, because they were in use. I then had
it scan the system. It reported "Congratulations! No immediate threats
were found!
Unfortunately, recently another support person had to install software on this user's system for a newly purchased Savin C6055 copier/printer/scanner to allow her to store documents scanned with the Savin C6055 in "file cabinets." Her system was the only one in the office on which this software was installed. For the others, I simply the C6055 "printer" from the server and had them connect to that shared printer to print to the unit. The copier support technician was not able to get the software to work under the user's account after it was installed under the local administrator account on the system. He said he believed the user's account had to be in the local administrator's group for it to work. Unfortunately, against my better judgment, I acquiesced and put her account in the local administrator's account. Which, of course, allowed the malware to install itself, since that account now had administrator privileges for the system.
When I questioned the copier technician about why the software should require administrative privileges to work, he told me that the software was developed for his company by a partner company of his company. Unfortunately, that developer apparently had no qualms about writing the software in such a way that it required the security of a system to be compromised in order for the software to work. In addition to the considerable amount of time spent disinfecting the system, I'll now have to try to figure out exactly what privileges and file and registry access the software actually needs to try and rectify that problem and allow me to limit the user account to the users group rather than have it in the administrators group. This is, unfortunately, not the first time I've run into this problem. I've encountered a similar problem with Intuit's QuickBooks softwaare, which, though it is designed specifically for business use, has, at least in versions I've installed, required more than normal user account privileges to be used under user accounts on the system.