

The laptop I was working on powered off without warning while I was researching a problem with software I wanted to use on a web server. I had a lot of tabs open in Internet Explorer (IE) 7 to webpages with information on the software. I hadn't stored the URLs for many of those webpages elsewhere, so wanted to recover the list of those visited URLs. Often I find that, if I reopen IE after an IE or system crash, the history list doesn't show many recently viewed pages.
So I decided to try the free IE HistoryView software from NirSoft. I've used other software from the same developer, Nir Sofer, and found it useful and easy to use.
No installation process is needed for the software. Simply extract the
3 files contained within the zip file. Place them wherever you want on
the system, e.g. \Program Files\IEHistoryView. The zip file
contains iehv.exe, iehv.chm, and a
readme.txt file. The
.chm file is a help file
for the software.
When started, IE History View shows a list of URLs visited using the Internet Explorer browser.
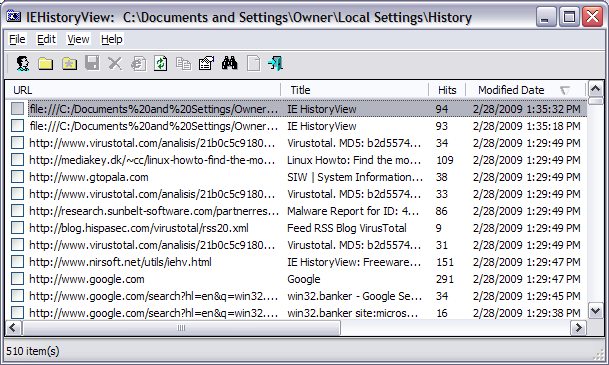
If you right-click on a URL, you will see a menu of options. If you select "Open Link", you can open the selected webpage in your default web browser. You can also choose "Copy URL" to copy the URL to the Windows clipboard.
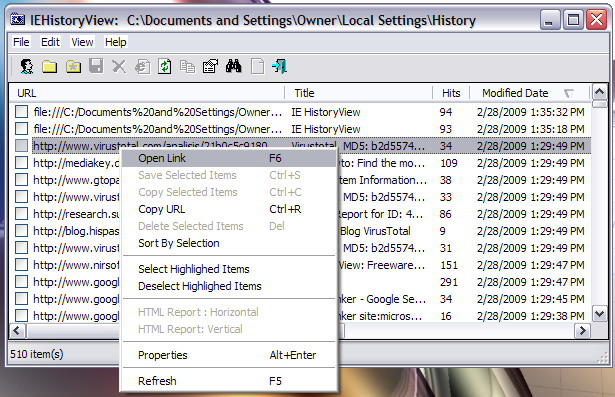
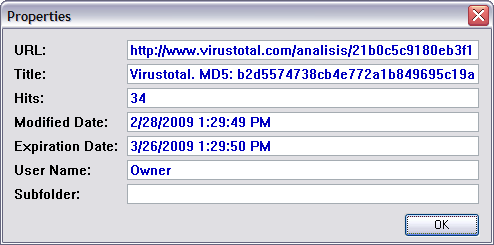
If you select "Properties", you can see further informaton regarding that URL within the IE history index file.
By default, when you start IE HistoryView, it will use the Internet Explorer history index file for the account under which you are logged in. But you can also view information within the history index file for other accounts on the system by clicking on File and then Select User Profile. You can then select other accounts on the system, if you have the proper privileges, e.g. you are logged into an account with administrator access.
If you want to view the history information of another computer on a network, connect to the desired network drive, and from the File menu, choose Select History Folder, and select the history folder in the remote drive.
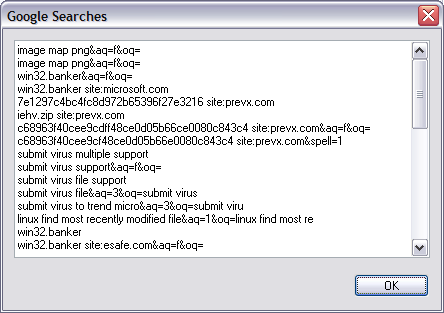
There is even the option to show all recent Google searches by clicking on File and selecting Show All Google Searches.
c:\win98,
the history folder is c:\win98\history. On Windows 2000/XP, the
History folder is located inside the "Local Settings" folder of your user
profile. For example, C:\Documents and Settings\Administrator\Local
Settings\History. The "Local Settings" folder is hidden by default, so
you won't see this folder unless your system is configured to display hidden
files and folders (see
Display Hidden Files and Folders and Operating System Files for
information on how to display such folders on a Windows XP system).
In most systems, IEHistoryView automatically identifies your current History
folder and uses it as default. However, you can always select History folder
from another location by using the Select History Folder option under
the File menu.
Be aware that when you watch the History folder from within the Windows environment, it doesn't show you the real files inside this folder, but instead it displays the history shell extension that provides limited information about the sites you visited.
[/Action] can be one of the following options:
|
| Saves the URLs list into a text file specified in ["Destination File"] parameter. |
|
| Saves the URLs list into tab-delimited text file specified in ["Destination File"] parameter. |
|
| Saves the URLs list into HTML file specified in ["Destination File"] parameter. |
|
| Saves the URLs list into vertical HTML file file specified in ["Destination File"] parameter. |
|
| Saves the URLs list into tabular text file specified in ["Destination File"] parameter. |
|
| Saves the URLs list into xml file specified in ["Destination File"] parameter. |
The {-Source Type} parameter is optional.
If you don't specify it, the URLs will be loaded from the default History folder on your system.
This parameter may contain one of the following values:
| -folder | Loads the URLs list from the folder specified in {"Source"} parameter. |
| -user | Loads the URLs list of the user specified in {"Source"} parameter. |
As I normally do for software that I download, I submitted the downloaded
file, iehv.zip to VirusTotal for analysis. The VirusTotal report is available
here. VirusTotal is a free online malware scanning site which allows you
to upload files for analysis by multiple malware detection programs. VirusTotal
scanned the file with 39 malware detection programs. It reported that two,
eSafe and
Sophos reported the file as potentially unsafe. eSafe identified
the file as being associated with Win32.Banker
while Sophos identified it as NirSoft.
I find eSafe reports a lot of false positives, so I generally discount any eSafe findings unless I find other antimalware products identifying files as malware. So I checked on why Sophos might be labelling the file as potentially unsafe. Sophos' webpage related to the designation is at NirSoft - Hacking Tool. Sophos labels the NirSoft software as a Potentially Unwanted Application (PUA), which it describes as "an application that is not inherently malicious, but is generally considered unsuitable for most business networks. Potentially unwanted applications include adware, dialers, remote administration tools and hacking tools." It assigns a type of Hacking Tool to the software. So in essence, Sophos is indicating that one wouldn't normally expect to find this software on a user's system, but that you shouldn't regard it as dangerous if you installed it purposefully. I.e., this should only concern you if the presence of the software on the system came as a surprise to you. One should remember that the original meaning of the word "Hacker" was a complimentary term indicating someone was knowledgeable about computer systems or was enthusiastic in the pursuit of knowledge about such systems. In this case Nir Sofer is providing a tool that gives one insight into software, specifically Internet Explorer, on the system.
I also submitted the file for analysis to Jotti's Malware Scan site. That site scanned the file with 19 antivirus programs, all of which reported that they found nothing of concern in the file (see Jotti report).
I also submitted the file for analysis to VirSCAN.org, another free multi-engine virus scanner. That site scanned the file with 37 antivirus programs. None detected any malware in the file (see VirSCAN report), even though VirSCAN.org also checks uploads with Sophos antivirus software.
| File Name: | iehv.zip |
| File Size: | 44526 byte |
| File Type: | Zip archive data, at least v2.0 to extract |
| MD5: | 7e1297c4bc4fc8d972b65396f27e3216 |
| SHA1: | c68963f40cee9cdff48ce0d05b66ce0080c843c4 |
| Scanner results: | All Scanners reported not find malware! |
| Time: | 2009/02/28 12:29:09 (EST) |
I also submitted the executable program, iehv.exe
(MD5: b2d5574738cb4e772a1b849695c19a2a), which is contained within the
zip file to ThreatExpert for
analysis. I didn't see anything of concern in the
ThreatExpert report. That report indicates that the program creates
the following registry keys when run:
HKEY_CURRENT_USER\Software\NirSoft
HKEY_CURRENT_USER\Software\NirSoft\IEHistoryView
It doesn't create any other files on the system nor does it start any other processes.
The VirusTotal report
for the iehv.exe program is available
here.
Sunbelt Malware Research
Labs is another service that analyzes file activity when a program is run.
Their CWSandbox info report for iehv.exe is available
here. That report also indicates that
the only registry key created by the program is
HKEY_CURRENT_USER\Software\NirSoft\IEHistoryView and that
the only file it observed iehv.exe opening when run was
C:\Documents and Settings\Sanbox\Local
Settings\History\History.IE5\index.dat, i.e. the
index.dat file for Internet Explorer for the user account under
which the program was run.
So I feel confident that the eSafe identification of iehv.zip
as containing Win32.Banker malware is yet another false positive from
eSafe. I couldn't find any information on the eSafe site about Win32.Banker.
Other sites with information on Win32.Banker are as follows:
Win32.Banker
avast! - antivirus protection
Win32/Banker
Microsoft Malware
Protection Center
Interestingly, 2-viruses.com, a site that provides information on how to remove fake antmalware programs, states at How to remove Trojan-Spy.Win32.Banker.aiw ? in regards to Trojan-Spy.Win32.Banker.aiw that such fake antimalware software often report Trojan-Spy.Win32.Banker.aiw.
Trojan-Spy.Win32.Banker.aiw is not a real trojan but it indicates serious problems. This threat is reported by fake security tools. Do not trust programs that supposedly detect Trojan-Spy.Win32.Banker.aiw trojan and offer removing it for a certain price. This trojan can not be deleted because it simply doesn't exist.
Though, perhaps, eSafe doesn't fall in the same category as those rogue antimalware programs, I don't give much credence to eSafe identification of files as containing malware without some corroborating evidence from other antimalware software, since whenever I submit files to VirusTotal, I find eSafe frequently identifies files as suspicious, though no other antimalware program does and I can't find any evidence that the designation is other than a false positive.
References: