

I installed Trend Micro™ RUBotted (Beta) on a system today as part of an effort to ensure the system wasn't being used to distribute spam. I had already run antivirus checks on the system with Symantec AntiVirus Corporate Edition and F-Secure Rescue CD 2.00, which is a free Linux-based boot CD that can be used to scan a system for malware. Neither one detected any malware on the system, but I wanted to run additional checks on the system to be certain it wasn't infected.
The system owner had been getting a lot of bounced spam messages. I was fairly certain that someone else's system was likely infected, but sending email using the email address of the person whose system I was checking. It isn't uncommon for malware to search for email addresses on an infected system and to randomly choose one that it finds as a "from" address when sending spam. I was fairly sure that was what was happening in this case, but wanted to do a thorough check on the system anyway, so I decided to try RUBotted.
RUBotted monitors a system to ensure it is not part of a botnet. A botnet is a collection of computers that are remotely controlled by someone who has taken over control of a system unbeknownst to its owner. Such compromised computers are known as "bots" and also known as "zombies". The term "bot" is shorthand for "robot". The malicious controller of such collections of compromised systems is often referred to as the " bot herder".
A bot herder may sell the services of the systems under his control. He may sell a spam service to spammers. I.e. he will use his collection of remotely controlled computers to send whatever email the spammer wishes to send. When a system sends spam to thousands of email addresses, the IP address of the sending system is usually quickly added to DNS Blacklists (DNSBL) maintained by various antispam organizations and companies. But if a spammer can use thousands of compromised systems to send his spam, it becomes much harder to block all sources of the spam.
By using software, such as RUBotted, one can reduce the chances that his or her system can be used for such nefarious purposes.
When the installation file for RUBotted is run, an installation wizard appears.
You are next asked to agree to the EULA
Once you agree the installation commences. There is no opportunity to specify the installation location.
When the installation completes, you are notified that the RUBotted icon will appear in the Windows system tray and given an opportunity to open the RUBotted console.
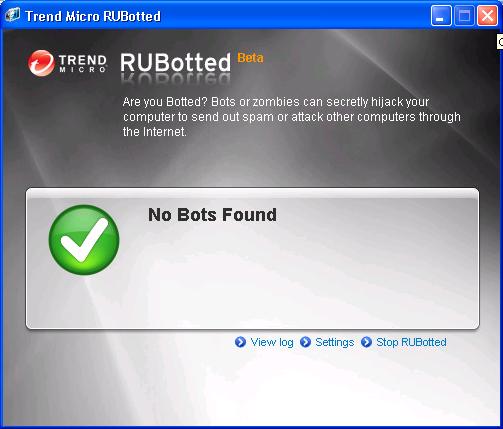
When you open the console to check the system, you will, hopefully, see a "No Bots Found" message.
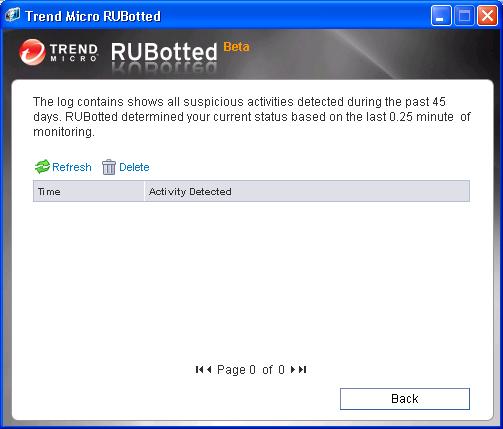
If you click on View log, you will see any suspicious activity that RUBotted has logged.
Clicking on Settings at the main console window allows you to specify a proxy server, if the system can only access the Internet via a proxy server. You can also turn off monitoring of the following traffic:
Http Incoming
Smtp Outgoing
Irc Request
Dns query
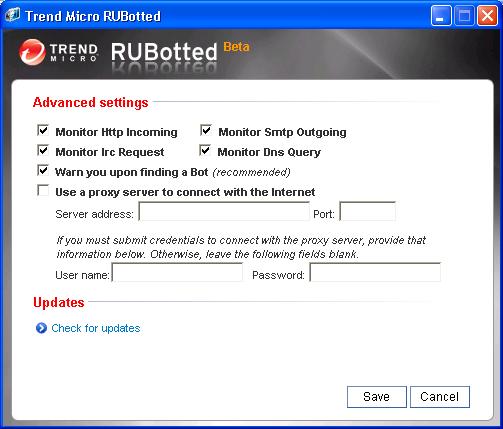
You also have the option of turning off warnings when RUBot detects a bot, but I would think you would almost always want to have such warnings.
Note: RUBotted cannot protect computers running Panda Internet Security 2008.
References:
Created: Saturday August 9, 2008