

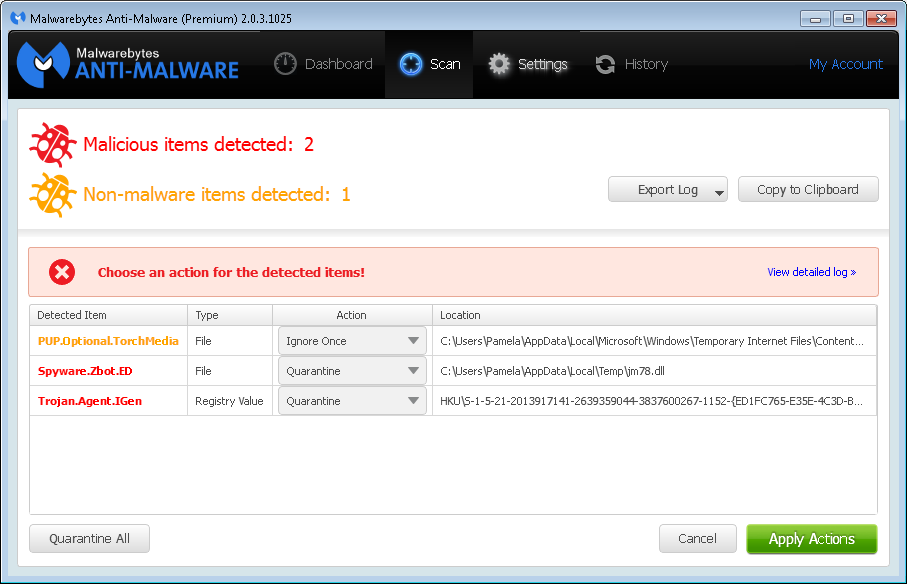
| Detected Item | Type | File | Location |
|---|---|---|---|
| PUP.Optional.TorchMedia | File | TorchSetup-r348-n-bi[1].exe | User's %LOCALAPPDATA%\Microsoft\Windows\Temporary Internet Files\Content.IE5\41K8VBAO\ directory |
| Spyware.Zbot.ED | File | jm78.dll | Users %TEMP% directory |
| Trojan.Agent.IGen | Registry Value | GoogleUpdate.exe | User's %APPDATA%\Roaming\FrameworkUpdate7\ directory |
For the Trojan.Agent.IGen registry entry, the registry entry was under the HKEY_USERS branch for the user's account:
\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\RUN|GoogleUpdate,
C:\Users\Pamela\AppData\Roaming\FrameworkUpdate7\GoogleUpdate.exe
When I looked for the file, it was not present, however. McAfee Total Protection may have removed it previously, though I didn't see it listed when I scanned through its history of what had been removed since the beginning of November, though it might have removed the file previously or perhaps I had removed it with Spybot Search & Destory or even Malwarebytes Anti-Malware previously.
When I right-clicked on jm78.dll and chose "Properties",
I did not see any product name, product version, nor copyright information
beneath the Details tab.
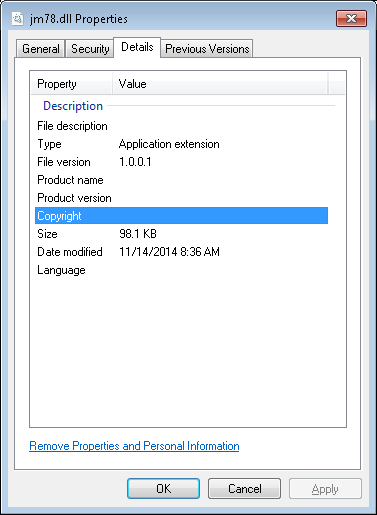
It appeared to have been placed on the system two days ago on November 14.
C:\>dir C:\Users\Pamela\AppData\Local\Temp\jm78.dll
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Temp
11/14/2014 08:36 AM 100,515 jm78.dll
1 File(s) 100,515 bytes
0 Dir(s) 886,562,205,696 bytes freeI uploaded the file to Google's VirusTotal site, which checks uploaded files with multiple antivirus programs. The site reported the file had been uploaded on the 14th and that 4 of its 54 antivirus/antispyware programs had detected it as malware. I chose to have the file reanalyzed. This time 20 of the 54 programs reported it as malware - see report. McAfee was one of those reporting it as safe. Since SUPERAntiSpyware is also installed on the system, but it was also reporting the file as safe, I opened that program, selected System Tools, then Submit Malware Samples to "Send suspected malware to our researches", and submitted the file for their analysis.
I installed BrowsingHistory View v1.60 to check the browsing history on the system. BrowsingHistoryView, which is free, reads the history data of four different web browsers: Internet Explorer, Mozilla Firefox, Google Chrome, and Safari. It displays the browsing history of all those Web browsers in one table.
After opening the program, under Advanced Options, which is presented by default when you open the program and which can be found under Options then Advanced Options, I changed the value for "Load history items from the last xx days" from 10 to 3. Since I only wanted to see the browsing history for the account that experienced the performance problems and which had the malware, I changed "Load history from" from "Load history from the current running system (All users) to "Load history from the specified profile (For example C:\users\admin)", then clicked on the button with three dots on it below that item to select the relevant user. I then clicked on Ok.
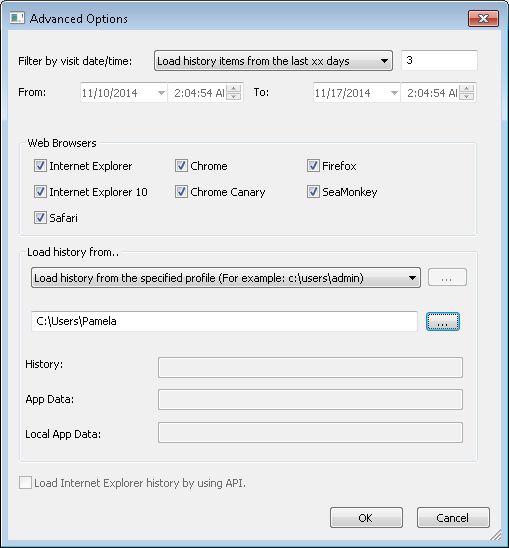
The URLs were ordered by URL by default, so I clicked on the Visit Time column header to order them by the time visited. I then looked for any URL with the time stamp of the jm78.dll file, which was Friday, November 14, 2014 8:36:45 AM, the time stamp available by right-clicking on the file and looking for the created and modified times under the General tab.
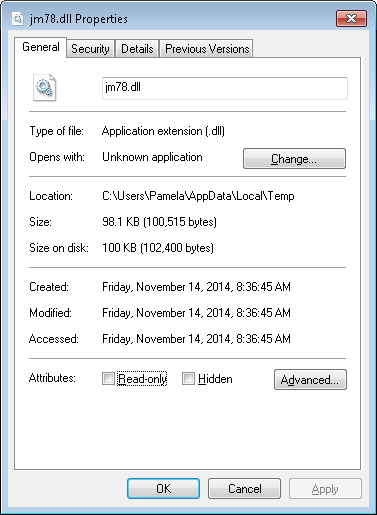
BrowsingHistoryView displayed URLs with visit times and visit counts for URLs accessed near the time for the dll file.
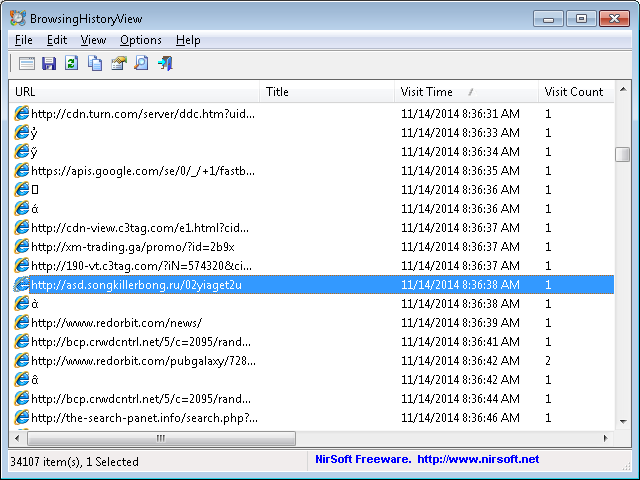
I right-clicked on some of the URLs that I saw that were visited a few seconds before 8:36:45 and then chose Copy URLs. I then pasted the URLs into the TrustedSource™ Query field at the McAfee TrustedSource™ site to check the reputation of the sites. I saw the following:
| Site | Web Reputation |
|---|---|
| 190-vt.c3tag.com | Minimal Risk |
| asd.songkillerbong.ru | Medium Risk |
| www.redorbit.com | Minimal Risk |
| bcp.crwdcntrl.net | Minimal Risk |
| the-search-panet.info | Unverified |
The last one I checked was visited a second after the creation time for jm78.dll, but I thought I would check it as well.
The one that McAfee TrustedSource™ rated as a medium risk was a suspiciously named Russian site; the ".ru" at the end of the fully qualified domain name (FQDN) is the country code for the Russian Federation.
I also went to the Trend Micro™ Site Safety Center and checked the site there. It reported it as untested and noted "Because you were curious about this URL, Trend Micro will now check it for the first time. Thanks for mentioning it!"
When I checked it at the AVG ThreatLabs Website Safety & Reviews site, it reported (link):
No active records found
We couldn't find a currently active record of this website. It may be currently unavailable or no longer exist.
I did find it listed at Malware-Traffic-Analysis.Net on 2014-11-14 - see 2014-11-14 - ANGLER EK FROM 131.72.138.141 - ASD.SONGKILLERBONG.RU where you can find a zip file of the malware the site author found associated with that suspicous domain.
The Malware-Traffic-Analysis.net blog is maintained by a security analyst in Texas whose blog "concentrates on network traffic related to malware infections. The focus is to establish a chain of events showing how the malware was delivered. Tools used for this blog include Wireshark and Security Onion. Hopefully, these blog entries will help other analysts who review events on intrusion detection systems (IDS) or security information and event management (SIEM) tools."
That suspicious Russian domain name no longer seems to exist, though. When I
performed an nslookup on the name, nslookup reported "*** UnKnown can't find
asd.songkillerbong.ru: Non-existent domain". So I didn't put the domain
name in C:\Windows\System32\drivers\etc\hosts associated with
the localhost address, 127.0.0.1, to block it. If you want to block
access to a known malevolent site, you can edit the file with Notepad and
put an entry such as the following in that file to block access to the site:
127.0.0.1 badsite.example.comIf you do that, if there is any attempt to access that domain name, Windows will check that file first to look up the IP address associated with the domain name. It will see the localhost address, 127.0.0.1, so will believe the name points to the system on which the hosts file resides and, since it doesn't won't be able to access it.
Though the VirusTotal report for the file I noted above reported the file as safe and McAfee Total Protection on the system hadn't previously detected it as malware, while I was writing up my notes on what I observed here, the file disappeared from the directory it had been in. When I checked the McAfee Total Protection Security History, I saw it detected it as malware about an hour ago at 9:25:30 PM on November 16, 2014. It reported it with a threat name of Artemis!810660921754. Clicking on the link provided for it in the Security History entry, took me to a McAfee webpage, but no information was listed for the malware there, which I often find to be the case when McAfee Total Protection reports malware and provides a link to their website for further information. Instead of further information, I often see "Sorry, we found 0 results matching your search criteria."
McAfee Total Protection didn't show the other file reported by Malwarebytes Anti-Malware as being detected as malware.