

I scanned a Windows 10 system used by a family member on July 2, 2017 with SUPERAntispyware Free Edtion, since the system was responding more slowly than I expected even for simple actions, though the system has other antivirus software on it. The first thing that SUPERAntispyware identified was the Ask Toolbar browser extension.
It showed the following information for Ask Toolbar:
Ask Toolbar
C:\ProgramData\ASKPARTNERNETWORK\TOOLBAR
HKLM\SYSTEM\CurrentControlSet\services\APNMCP
HKCU\Software\AskPartnerNetwork\Toolbar
C:\ProgramData\ASKPARTNERNETWORK
When I checked on when the software was installed, I found it appeared to have been placed on the system on June 25, 2017 at 5:57 PM.
C:\>dir /s C:\ProgramData\AskPartnerNetwork
Volume in drive C is OS
Volume Serial Number is D6DD-50D8
Directory of C:\ProgramData\AskPartnerNetwork
06/25/2017 05:57 PM <DIR> .
06/25/2017 05:57 PM <DIR> ..
06/25/2017 05:57 PM <DIR> Toolbar
0 File(s) 0 bytes
Directory of C:\ProgramData\AskPartnerNetwork\Toolbar
06/25/2017 05:57 PM <DIR> .
06/25/2017 05:57 PM <DIR> ..
06/25/2017 05:57 PM <DIR> WCL2-V7
0 File(s) 0 bytes
Directory of C:\ProgramData\AskPartnerNetwork\Toolbar\WCL2-V7
06/25/2017 05:57 PM <DIR> .
06/25/2017 05:57 PM <DIR> ..
06/25/2017 05:57 PM <DIR> Updater
0 File(s) 0 bytes
Directory of C:\ProgramData\AskPartnerNetwork\Toolbar\WCL2-V7\Updater
06/25/2017 05:57 PM <DIR> .
06/25/2017 05:57 PM <DIR> ..
06/25/2017 05:57 PM <DIR> Config
07/01/2017 02:38 PM <DIR> Response
0 File(s) 0 bytes
Directory of C:\ProgramData\AskPartnerNetwork\Toolbar\WCL2-V7\Updater\Config
06/25/2017 05:57 PM <DIR> .
06/25/2017 05:57 PM <DIR> ..
06/25/2017 05:57 PM 55,044 ConfigV1.33.11.0.8284-21.xml
1 File(s) 55,044 bytes
Directory of C:\ProgramData\AskPartnerNetwork\Toolbar\WCL2-V7\Updater\Response
07/01/2017 02:38 PM <DIR> .
07/01/2017 02:38 PM <DIR> ..
06/25/2017 05:57 PM 374 ResponseV1.33.11.0.8284-0.xml
06/30/2017 02:38 PM 244 ResponseV1.33.11.0.8284-4.xml
07/01/2017 02:38 PM 244 ResponseV1.33.11.0.8284-5.xml
3 File(s) 862 bytes
Total Files Listed:
4 File(s) 55,906 bytes
17 Dir(s) 219,318,169,600 bytes free
C:\>I had previously installed
RegScanner, which is a free software povided by Nir Sofer of
Nirsoft that provides capabilities
similar to those of the regedit program that comes with the Windows operating
system, but also provides additional capabilities, such as the ability to
show the last time a Windows registry key was modified. RegScanner showed the
HKCU\Software\AskPartnerNetwork\Toolbar was last modified on
December 13, 2016.
Perhaps the software had been present on the system previously and was recently updated or perhaps it had been removed, but not fully removed, previously, so there had been remnants on the system when it was reinstalled on the 25th of June.
When I used RegScanner to check on the
HKLM\SYSTEM\CurrentControlSet\services\APNMCP registry key, I saw
a last modified timestamp of July 1, 2017 at about 8:27 PM, which
corresponds to a time I had remotely logged into the system to check on the
status of a backup last night.
When I double-clicked on the entry in RegScanner, it opened the Microsoft Registry Editor program, which showed me the following information for the key.
The value for ImagePath was "C:\Program Files
(x86)\AskPartnerNetwork\Toolbar\apnmcp.exe". That file was dated
November 11, 2016. The date doesn't necessarily indicate the date the
program was placed on the system; it could have been placed on the system
within the last few days, but have that date if that's the last time the
developer updated that file.
C:\>dir "C:\Program Files (x86)\AskPartnerNetwork\Toolbar\apnmcp.exe"
Volume in drive C is OS
Volume Serial Number is D6DD-50D8
Directory of C:\Program Files (x86)\AskPartnerNetwork\Toolbar
11/09/2016 01:39 AM 201,800 apnmcp.exe
1 File(s) 201,800 bytes
0 Dir(s) 218,985,676,800 bytes free
C:\>When I right-clicked on the file in the Windows File Explorer and chose Properties then clicked on the Digital Signatures tab, I saw the file had been digitally signed by APN LLC.
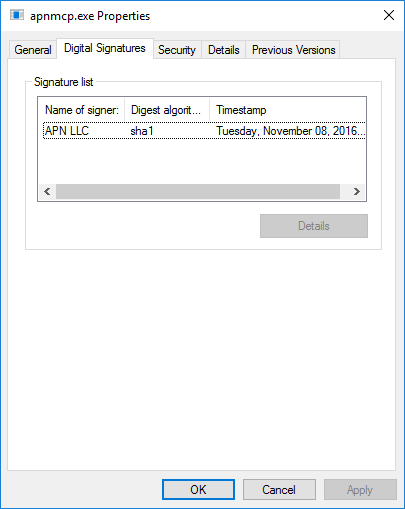
I opened a PowerShell window, which you can do on a Windows 10 system by typing powershell in the Cortana "Ask me anything" window, hitting Enter, and then clicking on Windows PowerShell, which should be returned as the best match, and used the Get-AutenticodeSignature cmdlet to get further information on the digital signature. It showed APN LLC to be a company in Oakland, California.
Windows PowerShell
Copyright (C) 2016 Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator> Get-AuthenticodeSignature "C:\Program Files (x86)\AskPartnerNetwork\Toolbar\apnmcp.exe" | For
mat-List
SignerCertificate : [Subject]
CN=APN LLC, O=APN LLC, L=Oakland, S=California, C=US
[Issuer]
CN=Symantec Class 3 SHA256 Code Signing CA, OU=Symantec Trust Network, O=Symantec
Corporation, C=US
[Serial Number]
76A1FC71CE00683A2B887A2CFA2F5D6B
[Not Before]
12/2/2015 7:00:00 PM
[Not After]
5/27/2018 7:59:59 PM
[Thumbprint]
B579DDDCFBFB60D9B7500C5A007E4E707055CDC0
TimeStamperCertificate :
Status : Valid
StatusMessage : Signature verified.
Path : C:\Program Files (x86)\AskPartnerNetwork\Toolbar\apnmcp.exe
SignatureType : Authenticode
IsOSBinary : False
PS C:\Users\AdministratorAsk.com has its headquarters in Oakland, California, U.S. The Wikipedia article on Ask.com currently notes:
Ask.com has been criticized for its browser toolbar, which has been accused of behaving like malware due to its bundling with other software and the difficulty of its uninstallation.
Checking on whether the file was present in a backup made with the
backup program Microsoft provides with Windows 10, I did not see it present
when I checked the backup from 6/18/2017, though the
C:\Program Files (x86)\AskPartnerNetwork\Toolbar directory existed
then. But the only file I saw in it was APNSetup.exe which had a
timestamp of January 9, 2014 12:09 PM. There were an Update and
WCL2-V7 subdirectories in the folder, also. But I saw the same
results when I checked the backup for July 1, 2017 9:42 PM.
I had SUPERAntiSpyware uninstall the Ask Toolbar by clicking on the white circle with a red "X" in it which appeared to the right of "Ask Toolbar".
At the conclusion of the SUPERAntiSpyware scan, it had found other Potentially Unwanted Programs/Settings including Adware.ConduitVariant, PUP.ConduitVariant, PUP.MyWebSearchVariant, PUPClientConnectVariant, PUPSearchProtectVariant, and Adware.PopCapVariant.
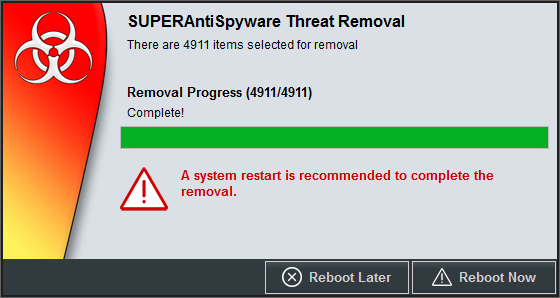
I had it remove everything it found, including the Tracking Objects, which were 4,871 tracking cookies. After SUPERAntispyware removed everything it found, I rebooted the system.
Related articles: