

Your computer is infected! Dangerous malware infection was detected on your PC The system will now download and install most efficient antimalware program to prevent data loss and your private information theft. Click here to protect your computer from the biggest malware threats.
When updates are available from Microsoft for the operating system, you will see a message associated with an icon in the system tray that looks like a globe with the Microsoft flag logo in its upper left-hand corner. This malware warning was associated with an icon that looked like the Microsoft updates icon. The logo flashed between that icon and a red circle with a white "X" in it. But the message certainly didn't look like it was from Microsoft.
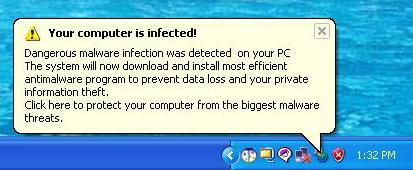
Someone else reporting this same message on a forum at Malware/porn popups/Spyaxe links stated that clicking on the message took him to http://spyaxe.net/?track_id=100064. The "track_id" at the end is likely an identifying number so that the SpyAxe distributor can pay an "affiliate" with that ID for directing a potential buyer to their website. Some software providers rely on disreputable affiliates to drive traffic to their website via spam or adware installations that popup windows directing a user of an infected system to the website of the software provider.
When I clicked on the message, a warning appeared from Microsoft AntiSpyware, which was running on the system.
| WARNING! Microsoft AntiSpyware Alert! |
| Warning, SpyAxe Potentially Unwanted Software is trying to install! |
| Microsoft AntiSpyware has detected the threat SpyAxe trying to install itself on your computer. If you would like to allow SpyAxe to run click the 'Allow' button below. |
SpyAxe had previously been removed by Microsoft AntiSpyware from this system on January 4, 2006 when Microsoft Antispyware ran automatically at 2:00:13 AM (see report). The spyware definitions were dated December 30, 2005 at 9:09:22 AM. SpyAxe was the only malware detected by Microsoft AntiSpyware at that time.
SpyAxe is listed at Spyware Warrior: Rogue/Suspect Anti-Spyware Products & Web Sites as "rogue" antispyware meaning that the product is of unknown, questionable, or dubious value as anti-spyware protection. The information provided by the Spyware Warrior site for SpyAxe, which is identified as being the same application as AdwareDelete, AntiVirus Gold, and SpywareStrike, is shown below.
| Product | Domains | Comments |
| AdwareDelete | adwaredelete.com qspyware.com |
deceptive advertising (1); false positives work as goad to purchase; uses inadequate scan/detection scheme; dubious corp. associations (1); same app as AntiVirus Gold, SpyAxe, & SpywareStrike [A: 6-14-05 / U: 1-4-06] |
A Dave's World noahdfear's page links the Trojan-Spy.HTML.Smitfraud.c malware infection to AntivirusGold, PSGuard Spyware Remover, SpySheriff, Spy Trooper, SpyAxe, Security Toolbar, WinHound and SpywareStrike. The page states that some of those may modify the Dynamic Link Library (DLL) wininet.dll, which is located in a Windows system directory. The webpage offers a SmitRem tool to remove Trojan-Spy.HTML.Smitfraud.c.
Removal instructions for SpyAxe are posted at How To Remove Spyaxe And Svchosts.dll/wbeconm.dll. Those instructions detail how you can use the smitRem tool to remove SpyAxe.
I uploaded the c:\windows\system32\wininet.dll file to Jotti's Online Malware Scan, but none of the 14 antivirus programs it uses detected any problem with the file. [ Scan Results ]. I also scanned the file with Symantec AntiVirus Corporate Edition 8.0 on another system, but it did not report it as infected either.
Either something remained of SpyAxe after Microsoft AntiSpyware removed it previously, which managed to resusitate the software or some other trojan, virus, etc. still on the system was attempting to reinstall SpyAxe.
I rebooted the system in Safe Mode and ran a quick scan with Microsoft AntiSpyware. The only malware detected was SpyAxe. No files were listed, but many registry entries related to SpyAxe were found (see AntiSpyware Found SpyAxe, which shows all of the registry entries found). One of the registry entries reported was "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run SpyAxe"
I ran regedit and checked the keys under
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
I saw the following key.
| Name | Type | Data |
|---|---|---|
| SpyAxe | REG_SZ | C:\Program Files\SpyAxe\spyaxe.exe /h |
I checked the virus definitions date for Symantec AntiVirus Corporate Edition 8.0, which is the antivirus software on the system. The definitions were 12/30/2005 rev. 4.
I don't see a SpyAxe folder beneath "C:\Program Files", however, even checking
for hidden and system files. I've seen malware often hide itself so that
files and directories aren't visible through the Windows Explorer and when
using the dir command at a command prompt, even when Windows
Explorer is set to display hidden and system files and folders and when the
dir /ah and dir /as are used at a command prompt
to show hidden and system files, but booting into safe mode usually reveals
those invisible files and folders. However, just to make sure a SpyAxe
directory under C:\Program Files didn't exist, I booted with
a PLoP Linux boot CD and
looked for such a directory. None existed.
I rebooted into safe mode again, but this time selected "Safe Mode with Networking". Unlike when I selected "Safe Mode" the previous time, this time I got the "Your computer is infected! Dangerous malware infection was detected on your PC" message again. I brought up Microsoft AntiSpyware again and had it remove SpyAxe. I then rebooted into "Safe Mode with Networking" again. Almost immediately after rebooting I saw the same "Your computer is infected" message again. Though I rebooted into "Safe Mode with Networking" mode, I had not connected the system to the network at any time since I received it from the user on January 5. So obviously something was escaping Microsoft AntiSpyware's notice.
I ran another quick scan with Microsoft AntiSpyware. This time Microsoft AntiSpyware did not detect anything.
A
How to Remove Spyaxe and Svchohsts.dll/wbeconm.dll webpage updated on
December 28, 2005 mentions the
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\C:\Program Files\SpyAxe\spyaxe.exe /h
registry key and states the SmitRem tool has been updated to include the removal
of c:\windows\system32\wbeconm.dll. I looked in the
c:\windows\system32 directory and found wbeconm.dll. Symantec
AntiVirus Corporate Edition 8.0 on the system did not report it as malware
when I scanned it nor did the same version of Symantec AntiVirus on another
system with 1/4/2006 rev. 6 virus definitions report it as malware. However,
when I uploaded it to Jotti's Online
Malware Scan for scanning by 14 different antivirus programs, five of the
fourteen reported it as malware [
Scan Results ].
| AntiVirus Program | Virus Reported |
|---|---|
| AntiVir | Adware-Spyware/NXegt.DLL adware |
| Dr.Web | Trojan.Fakealert |
| F-Prot Antivirus | W32/Adclicker.OZ |
| Kaspersky Anti-Virus | not-virus:Hoax.Win32.Renos.ak |
| Norman Virus Control | W32/Spywad.AG |
The Kapersky site indicates the malware was detected on December 29, 2005 by Kapersky Lab and states "Currently there is no description available for this program."
I checked to see what process had the wbeconm.dll module loaded with
tasklist /m wbeconm.dll. The process listed was explorer.exe.
Image Name PID Modules
========================= ====== =============================================
explorer.exe 1440 wbeconm.dllAn analysis of the file with FileAlyzer, a tool provided by the developer of Spybot Search & Destroy, showed the malware warning message inside the file when I used FileAlyzer's hex dump facility to search for strings inside the file (see FileAlyzer screen capture).
I downloaded the smitRem.exe tool using another system and then transferred it by floppy disk to the infected system, which was booted in "Safe Mode with Networking" mode, but unconnected from any network. I put the file on the desktop and then double-clicked on it. SmitRem.exe is a self-extracting file which created a smitRem folder on the desktop containing the following files.
delfiles.cmd
Process.exe
pv.exe
replace.cmd
RunThis.bat
swreg.exe
I then double-clicked on RunThis.bat in that folder to remove the malware. During the removal process a message appeared from the removal procedure that "Disk cleanup has been known to take up to 3 hours to complete. Please be patient and allow ample time for it do so so." The process then ran Windows Disk Cleanup procedure, which fortunately took only a few minutes on this system. After the process completed, I rebooted Windows XP normally. The user's background was changed to a plain blue background. The malware warning message no longer appeared.
I then updated Spybot Search & Destroy's spyware definitions to the latest ones available and checked the system with that antispyware program. It reported entries for both PSGuard and SpyAxe, as well as some other malware. But for PSGuard and SpyAxe, there were no files listed, just registry entries. SmitRem didn't remove registry entries used by PSGuard and SpyAxe, but, since it removed the files and folders associated with these suspect antispyware programs, they should no longer be a threat to the system. For a list of files and folders that smitRem checks, see List of Files and Folders Targeted by the smitRem Tool. I had Spybot remove everything it found (see Spybot Results).
| File | Description |
|---|---|
| SmitRem | malware removal tool |
| wbeconm.dll | malware DLL available for analysis (userid: zoo, password: malware |
References:
Created: Monday January 9, 2006 9:22 PM