|
| ←2026→| Months |
|---|
| Jan |
Feb | Mar |
| Apr |
May |
Jun |
| Jul |
Aug |
Sep |
| Oct |
Nov |
Dec |
|
Tue, Dec 27, 2011 6:14 pm
Spbyot - You are missing administrator rights
After installing
Spybot
Search & Destroy 1.6.2 through
allmyapps, I started Spybot and attempted to peform an immunization,
but saw the following error, even though I was logged into an account
in the administrator group when I started Spybot.
Error
You are missing administrator rights to perform this action.
If you need to do this, please run this application
elevated as an administrtor.
When I started Spybot by right-clicking on its shortcut and choosing
"Run as administrator", the immunization performed successfully.
[/security/spyware/spybot]
permanent link
Tue, Sep 16, 2008 9:27 am
CA Anti-Spyware Scan of J
I checked a Windows XP Professional Service Pack 3 system, J, with
CA Anti-Spyware 2008 LE. That version is free and will detect malware,
but not remove it. You can purchase a license to have the software remove
any malware it finds.
[ More Info ]
[/security/spyware]
permanent link
Sat, Sep 13, 2008 4:52 pm
Rootkit Checks on J on 2008-09-13
I had checked a system, J, that had malware on it earlier in the week with
the
rootkit detection
program,
BlackLight from
F-Secure. Today, I checked the
system with two other rootkit detection programs,
Rootkit Hook Analyzer
from
Resplendence Software
Projects and
RootkitRevealer from
Microsoft.
The software was originally developed by
Sysinternals; Microsoft acquired Sysinternals in 2006.
I did not find any rootkit software on the system with any of the 3 rootkit
revealers I used.
[ More Info ]
[/security/spyware]
permanent link
Wed, Sep 10, 2008 11:00 pm
Infection Checks on 2008-09-10
I ran further checks on September 10, 2008 on a system that I found infected
with
Virantix and other malware on September 9 (see
Infection by Virantix -
braviax.exe).
[ More Info ]
[/security/spyware]
permanent link
Wed, Sep 10, 2008 12:27 am
Infection by Virantix - braviax.exe
After a user attempted to open an attachment on an email message that
was ostensibly from Southwest Airlines, but which was really malware,
her system rebooted and kept popping up a ballon message from the system
tray that "It is recommended to use special antispyware tools to pervent
data loss. Windows will now download and install the most up-to-date
antispyware for you." The message, which misspelled "prevent" was really
coming from
rogue
antispyware software. Such messages are common to
rogue antispyware that attempts to trick users into buying the software after
the software has managed to surreptitiously install itself.
[ More Info ]
[/security/spyware]
permanent link
Mon, Jun 23, 2008 9:21 pm
PossibleHostsFileHijack
I scanned my laptop with Windows Defender version 1593. It reported
it found "Win32/PossibleHostsFileHijack.
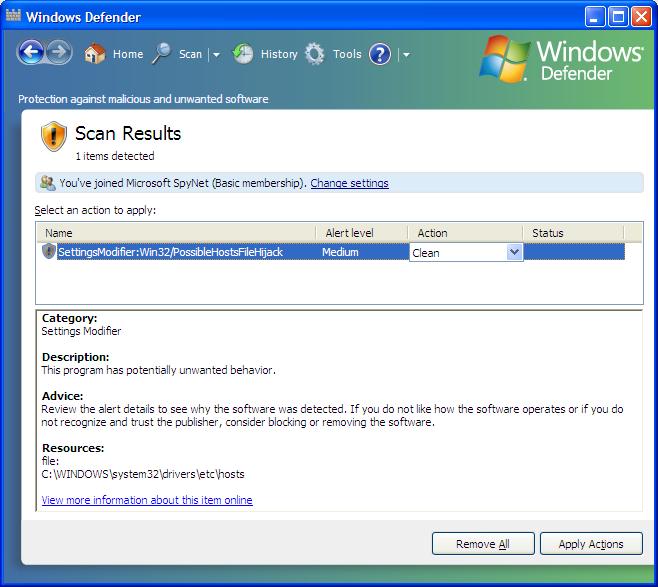
Scan Results
1 items detected
Select an action to apply:
| Name | Alert level | Action | Status |
|---|
| SettingsModifier:Win32/PossibleHostsFileHijack |
Medium | Clean | |
Category
Settings Modifier
Description:
This program has potentially unwanted behavior
Advice:
Review the alert details to see why the software was detected. If you do not
like how the software operates or if you do not recognize and trust the
publisher, consider, blocking or removing the software.
Resources:
file:
C:\WINDOWS\system32\drivers\etc\hosts
View more information about this item online
The link provided by Windows Defender to
SettingsModifier:Win32/PossibleHostsFileHijack provided the following
information:
Also Known As:
Trojan.Win32.Qhost (Kaspersky)
Qhosts.apd (McAfee)
Summary
A detection of Win32/PossibleHostsFileHijack is an indicator that your HOSTS
file may have been modified by malicious or potentially unwanted software.
Modifications to the HOSTS file can cause access to certain Internet domains
to be redirected or denied. This may prevent the computer from connecting to
certain Web sites.
Symptoms
Situations such as the following may be signs that your HOSTS file has been
modified without your consent:
-
You are unable to access a certain Web site that you believe is in operation,
such as a site that provides programs to help keep your computer secure.
-
Your browser connects to a Web site that does not appear to be appropriate,
given the Web address you entered.
The hosts file is at c:\windows\system32\drivers\etc\hosts.
In this case Windows Defender is flagging it because it has been modified.
Typically, it doesn't have much more in it than a reference to the
loopback address,
i.e. 127.0.0.1 localhost.
In the case of this laptop, Spy Sweeper added entries such as the following:
127.0.0.1 localhost
127.0.0.1 1.httpdads.com #SpySweeperCASS
127.0.0.1 207-87-18-203.wsmg.digex.net #SpySweeperCASS
127.0.0.1 a.mktw.net #SpySweeperCASS
127.0.0.1 a.tribalfusion.com #SpySweeperCASS
Many antispyware programs, such as Spy Sweeper or
Spybot Search & Destroy, will
add entries to the hosts file,
pointing the address to malicious sites or those that distribute adware/spyware
to the loopback address, 127.0.0.1, instead. That ensures that if
the the system attempts to contact one of those sites, such as
httpdads.com , which is listed by SpySweeper, which is antispyware
software produced by
Webroot Software, Inc., that instead of
going to the website distributing the malware, the system instead is directed
to the local loopback address on the system itself, preventing the system
from contacting the actual website.
So, in this case, I can consider the report a "false positive" and instruct
Windows Defender to ignore it.
[/security/spyware/defender]
permanent link
Wed, Nov 07, 2007 10:34 pm
Restart.Exe
When I scanned a system for malware,
BitDefender Free Edition v10 reported the presence of
Spyware.Destart.A in
Restart.exe, which was in
the directory
C:\Windows\System32\Tools. I submitted the file to
VirusTotal for analysis and also
to
Jotti's Online Malware Scan.
Other antimalware software used by those sites also reported the file
as malware. However, after further checking, I believe that the file
is actually innocuous.
[ More Info ]
[/security/spyware]
permanent link
Mon, Apr 30, 2007 11:13 pm
Charlene Infection
After a user complained of popup windows advising her to download
antivirus software, I checked the system with
Spybot Search & Destroy.
Spybot found the following malware on the system:
FunWeb
FunWebProducts
MyWay.MyWebSearch
MyWebSearch
TagASaurus
Zlob.VideoAccessActiveXObject
I also found that the popup ad was appearing whenever Internet Explorer was
opened. When Interenet Explorer was opened it would go immediately to
http://aprotectservice.com/, which
would result in a dubious W32.Myzor.FK@yf virus warning appearing.
[ More Info ]
[/security/spyware/funwebproducts]
permanent link
Mon, Jan 01, 2007 2:22 pm
Bazooka Update Failure
When attempting to update the malware database for
Bazooka ™ Adware and Spyware Scanner,
a free tool for detecting adware, spyware, trojans, keyloggers, etc. on a
system, which is compatible with Windows 95/98/ME/NT/2000/XP, I received the
message below:
Error updating database. Could not save the new database on the hard drive.
An error occurred when trying to open the file for writing.
Filename: 'system\bazooka_db.bdb'
Current Working Directory: C:\Program Files\Security\Spyware\Bazooka Scanner\
System error message: Access is denied.
C++ exception: ios::failbit set
Could not update the database. Please check the following:
1. Are you connected to the Internet?
2. Maybe it was a temporary error. Please try again later.
You can also update the database manually. Would you like to have instructions
how to update it manually?
When I checked the properties of the Bazooka database,
bazooka_db.bdb, which is under the system directory
of the Bazooka installation folder, by right-clicking on the file and
selecting Properties, I found it was marked as "read-only".
I unchecked the read-only option and then was able to update the database.
[/security/spyware/bazooka]
permanent link
Thu, Dec 28, 2006 9:33 pm
Fixing TeaTimer Window Problem with Resource Hacker
On several systems where I've installed
Spybot - Search
& Destroy 1.4, I've encountered problems with the
popup windows that appear when I've activated TeaTimer,
a Spybot application that monitors attempts to change
the registry. The buttons on the warning window that
appears won't have the correct description of their
function written on them, so it is hard to determine
what will happen when you click on a particular button.
The problem can be fixed with
Resource
Hacker.
[ More Info ]
[/security/spyware/spybot/teatimer]
permanent link

Privacy Policy
Contact



