Calculating a hash value for a file with Get-FileHash
The PowerShell cmdlet
Get-FileHash provides a
cryptographic hash function that will allow you to determine a
hash value of a file on a Microsoft Windows system. By default,
the cmdlet
uses the SHA-256 hash
function, but you can specify other functions, such as
MD5, using the
-Algorithm parameter. You can change the output to a list
format by
piping the output
of the cmdlet to Format-List.
PS C:\users\public\downloads> Get-FileHash ".\rel_x64_Xming-7-7-1-1-setup.exe"
Algorithm Hash Path
--------- ---- ----
SHA256 B7B4C0A191E315686A2481DCC8BBB27D6D7A156FBF689768E48CF08207B86560 C:\users\public\downloads\rel...
PS C:\users\public\downloads> Get-FileHash ".\rel_x64_Xming-7-7-1-1-setup.exe" | Format-List
Algorithm : SHA256
Hash : B7B4C0A191E315686A2481DCC8BBB27D6D7A156FBF689768E48CF08207B86560
Path : C:\users\public\downloads\rel_x64_Xming-7-7-1-1-setup.exe
PS C:\users\public\downloads> Get-FileHash -Algorithm MD5 ".\rel_x64_Xming-7-7-1-1-setup.exe"
Algorithm Hash Path
--------- ---- ----
MD5 BA200636A596A84E0877901CE89D1C2E C:\users\public\downloads\rel...
PS C:\users\public\downloads>
[ More Info ]
[/os/windows/PowerShell]
permanent link
NortonLifeLock Scam
Earlier this week, a user forwarded me an email she received purporting
to be a notification regarding an automatic renewal of a subscription to
"Norton Life-Lock" wondering if it was legitimate and she would be charged
$399 for the product.

The message included the following text:
This email confirms that your subscription has been renewed for another
1 year with Norton Life-Lock for $399.00 on April 11th,2024.
This subscription will Auto-Renew every year unless you turn it OFF. No
later than 24 hour before the end of the subscription period.
To cancel this subscription,
Call: +1(844)962-1087
An online search of the 844-962-1087 number showed it is not a number
associated with Norton LifeLock, a clear indication that the email was a
scam where the scammer attempts to get people to call a number to cancel an
expensive "subscription" for a well-known product or company. I assume those
who call the number will be asked to provide their credit or debit card
information, so someone pretending to be a customer service representative for
the company can supposedly look up the account information to "cancel" the
subscription. If credit card information is provided, the scammer can then use
it for fraudulent charges or sell the information to others. Another indicator
that a message such as this is fraudulent is poor English. E.g., "...unless you
turn if OFF. No later than 24 hour before the end of the subscription period."
Proper English would be "...unless you turn it OFF no later than 24 hours
before the end of the subscription period." I.e., there should not be
a period before "No later" and "hours" should be used rather than "hour."
Another indication that the email is a fraud attempt in this case is
that the sender hyphenated the product name, i.e., "Life-Lock" whereas if
you go to the Norton website and
look at their consumer products or visit the
NortonLifeLock website, you can
see that the name of the product is listed as "LifeLock" not "Life-Lock." The
Wikipedia LifeLock page
also shows the product name is not hyphenated. Such phishing
emails purporting to be notifications of upcoming charges for
NortonLifeLock have been prevalent for years — the NortonLifeLock
website has a January 11, 2022 article
"
Keep an eye out for Norton email scams" warning people about such
attempts and showing similar scam messages regarding their product.
Unfortunately, such scams can deceive enough people to make sending
such messages profitable for scammers. People anxious to avoid a
charge of several hundred dollars for a product they may not even be using
may call the number and provide credit/debit card or banking information
that the scammer may use to fraudulently charge their credit or debit card
or steal money from a banking account.
[/security/phishing]
permanent link
Casting a video stored on a Windows PC to an LG TV
If you have a movie, or other video, located on a PC running Microsoft Windows
and wish to view the movie on your
LG Electronics TV,
which runs the LG
webOS operating system,
if they are on the same
local area network
(LAN), you can "cast" the video to the TV.
If the LG TV is visible to other devices on the network, such as the PC,
you should see it within "Media Devices" under "Network" in the Windows
File Explorer.
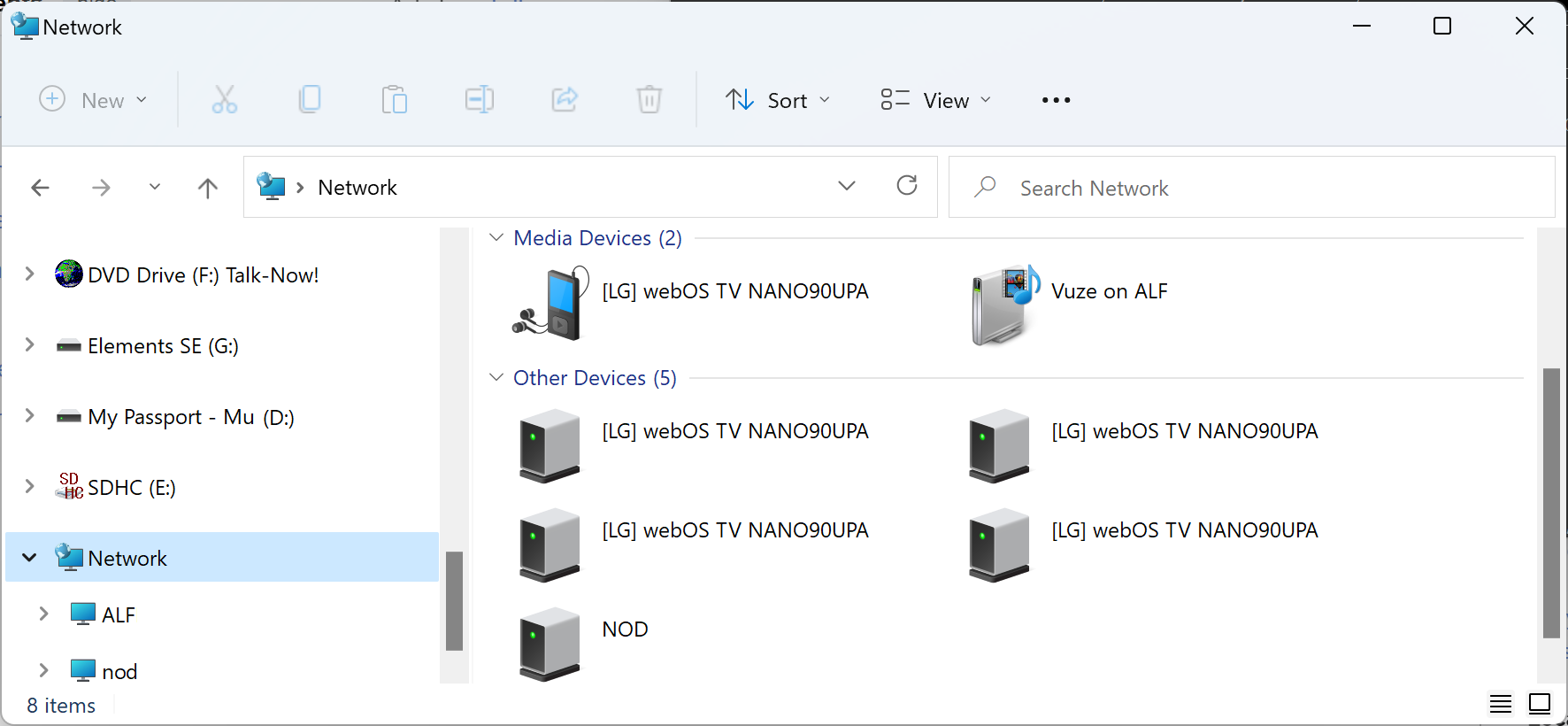
If you have an MPEG-4
(.mp4) or Audio Video Interleave (.avi) file on the PC, you can right-click
on video file, then choose "Show more options," and then
choose "Cast to Device" at which point you should see the LG TV as a
device to which you can stream the video.
[ More Info ]
[/video/lgtv]
permanent link
Blocking email from an envelope "from" address with Sendmail
For a mail server running
Sendmail email server
software, if you wish to block email from a particular "from" address to
any email address on the server, you can include the address you wish to
block in the /etc/mail/access file. E.g., if you wished to
block email from the address
spammer@example.com, you can include the following
line in that file:
# Block envelope "from" address of spammers
spammer@example.com REJECT
Any line beginning with a # is treated as a comment, so the
first line above isn't needed, but adding a comment line may help you
recognize why the reject statement is in the file. After you have
added the line, you need to regenerate the
/etc/mail/access.db file, or create a new one if there isn't
already one present, using the command shown below (you don't need to
restart sendmail):
# makemap hash /etc/mail/access </etc/mail/access
#
This will only work if you have a
FEATURE(`access_db')dnl line in /etc/mail/sendmail.mc.
E.g., a line like the one below:
FEATURE(`access_db', `hash -T<TMPF> -o /etc/mail/access.db')dnl
If you don't have such a line, you will need to add it. If the line begins
with dnl, you will need to remove the dnl at the
beginning of the line, since that "comments out" the line.
[ More Info ]
[/network/email/sendmail]
permanent link
Determining the default gateway and subnet mask from a Windows command prompt
From a command prompt on a
Microsoft Windows system, you can obtain details on the network configuration
by issuing the command ipconfig or ipconfig /all, if
you wish to see more details. If you are only interested in a specific value or
values, though, you can
pipe the output
of the command to the findstr
command. If you wish to see multiple values, e.g., the subnet mask and the
default gateway address, you can put text associated with both values,
separated by a space, within double quotes. Findstr will treat the space
between strings as instructing it to perform a
logical OR
operation, i.e., it will find any lines that contain either of the strings.
Findstr uses a case sensitive search, so you need to either match the case of
the text or use the /i option with findstr, which instructs it to
ignore the case of text and perform a case insensitive search.
C:\>ipconfig | findstr "Mask Gateway"
Subnet Mask . . . . . . . . . . . : 255.255.255.224
Default Gateway . . . . . . . . . : 192.168.1.1
C:\>ipconfig | findstr "mask gateway"
C:\>ipconfig /all | findstr /i "mask gateway"
Subnet Mask . . . . . . . . . . . : 255.255.255.224
Default Gateway . . . . . . . . . : 192.168.1.1
C:\>
You can also use a
Windows Management Instrumentation Command-line (WMIC) command to obtain
the same information.
C:\>wmic nicconfig get defaultIPGateway, IPSubnet
DefaultIPGateway IPSubnet
{"192.168.1.1"} {"255.255.255.224", "64"}
C:\>
[/os/windows/commands]
permanent link



