I scanned my laptop with Windows Defender version 1593. It reported it found "Win32/PossibleHostsFileHijack.
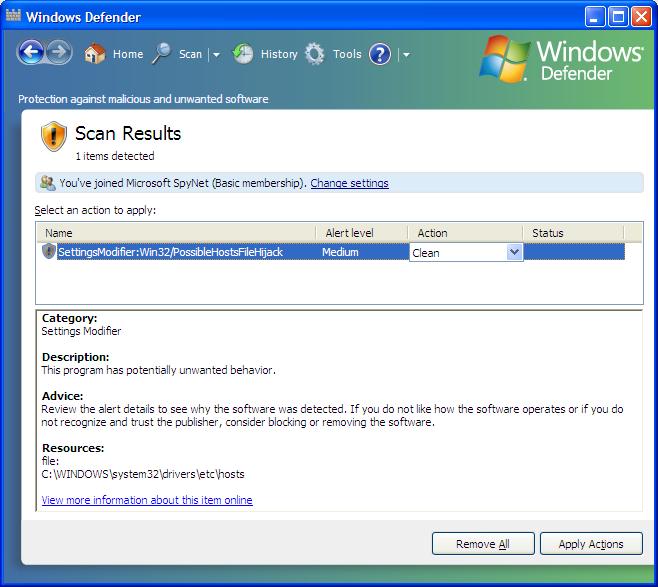
Scan Results
Select an action to apply:
1 items detected
Name Alert level Action Status SettingsModifier:Win32/PossibleHostsFileHijack Medium Clean Category Settings Modifier
Description:
This program has potentially unwanted behavior
Advice: Review the alert details to see why the software was detected. If you do not like how the software operates or if you do not recognize and trust the publisher, consider, blocking or removing the software.
Resources: file: C:\WINDOWS\system32\drivers\etc\hosts
View more information about this item online
Also Known As:
Trojan.Win32.Qhost (Kaspersky)
Qhosts.apd (McAfee)Summary
A detection of Win32/PossibleHostsFileHijack is an indicator that your HOSTS file may have been modified by malicious or potentially unwanted software. Modifications to the HOSTS file can cause access to certain Internet domains to be redirected or denied. This may prevent the computer from connecting to certain Web sites.
Symptoms
Situations such as the following may be signs that your HOSTS file has been modified without your consent:
- You are unable to access a certain Web site that you believe is in operation, such as a site that provides programs to help keep your computer secure.
- Your browser connects to a Web site that does not appear to be appropriate, given the Web address you entered.
The hosts file is at c:\windows\system32\drivers\etc\hosts.
In this case Windows Defender is flagging it because it has been modified.
Typically, it doesn't have much more in it than a reference to the
loopback address,
i.e. 127.0.0.1 localhost.
In the case of this laptop, Spy Sweeper added entries such as the following:
127.0.0.1 localhost
127.0.0.1 1.httpdads.com #SpySweeperCASS
127.0.0.1 207-87-18-203.wsmg.digex.net #SpySweeperCASS
127.0.0.1 a.mktw.net #SpySweeperCASS
127.0.0.1 a.tribalfusion.com #SpySweeperCASS
Many antispyware programs, such as Spy Sweeper or
Spybot Search & Destroy, will
add entries to the hosts file,
pointing the address to malicious sites or those that distribute adware/spyware
to the loopback address, 127.0.0.1, instead. That ensures that if
the the system attempts to contact one of those sites, such as
httpdads.com , which is listed by SpySweeper, which is antispyware
software produced by
Webroot Software, Inc., that instead of
going to the website distributing the malware, the system instead is directed
to the local loopback address on the system itself, preventing the system
from contacting the actual website.
So, in this case, I can consider the report a "false positive" and instruct Windows Defender to ignore it.

