

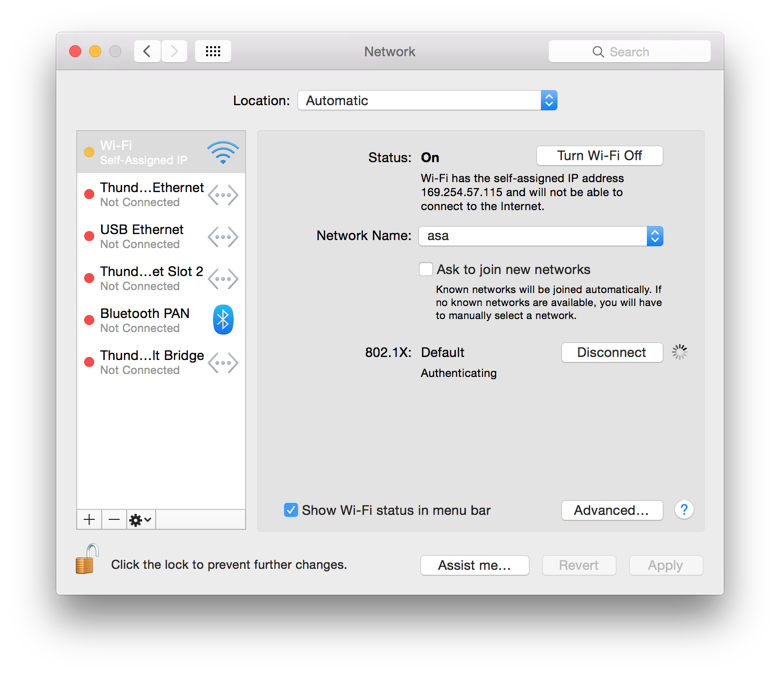
Eventually a message appeared stating "Authentication failed on network".
I clicked on the Disconnect button, the only option available in that window.
I can change the 802.1X password through the Keychain Access utility,
which is located in /Applications/Utilities. To find an 802.1X
entry, click on Edit then select Find and search for
802.1X. You should see an entry with a "Kind" of "802.1X Password".
You can change the password by double-clicking on the entry.
Then click on "Show password". Another window will appear stating "Keychain Access wants to use your confidential information stored in name_of_entry in your keychain." There will be three buttons: Always Allow, Deny, and Allow. If you want to allow the access type the login keychain password and click on "Always Allow" or "Allow".
You will then see the password displayed in the "Show password" field and can change it and click on the Save Changes button, if you wish to modify the password. After I modifed the password to be the currently valid password, I was able to successfully complete the 801.2X authentication.
If you wish to view the password from a
command line
interface (CLI), you can open a
Terminal
window and use the security
command with the find-generic-password parameter using the
-ga or -gD options as shown below:
$ security find-generic-password -ga "jasmith1" | grep "password:" password: "ASecretPassword" $ security find-generic-password -gD "802.1X Password" | grep "password:" password: "ASecretPassword" $
The meaning of those options is listed below - see the man page for the security command:
| -g | Display the password for the item found |
| -a | Match account string |
| -D | Match kind string |
You can change the password from the Terminal
shell prompt using a security add-generic-password command.
$ security add-generic-password
Usage: add-generic-password [-a account] [-s service] [-w password] [options...] [-A|-T appPath] [keychain]
-a Specify account name (required)
-c Specify item creator (optional four-character code)
-C Specify item type (optional four-character code)
-D Specify kind (default is "application password")
-G Specify generic attribute (optional)
-j Specify comment string (optional)
-l Specify label (if omitted, service name is used as default label)
-s Specify service name (required)
-p Specify password to be added (legacy option, equivalent to -w)
-w Specify password to be added
-A Allow any application to access this item without warning (insecure, not recommended!)
-T Specify an application which may access this item (multiple -T options are allowed)
-U Update item if it already exists (if omitted, the item cannot already exist)
By default, the application which creates an item is trusted to access its data without warning.
You can remove this default access by explicitly specifying an empty app pathname: -T ""
If no keychain is specified, the password is added to the default keychain.
Add a generic password item.
$E.g., assuming the settings in the example above which were:
| Name: | asa |
| Kind: | 802.1X Password |
| Account: | jasmith1 |
| Where: | com.apple.network.eap.user.item.wlan.ssid.asa |
I could use the second security command shown below to change the password from "ASecretPassword" to "ItsASecret".
$ security find-generic-password -gD "802.1X Password" | grep "password:" password: "ASecretPassword" $ security add-generic-password -a jasmith1 -s com.apple.network.eap.user.item.wlan.ssid.asa -l asa -D "802.1X Password" -U -w "ItsASecret" $ security find-generic-password -gD "802.1X Password" | grep "password:" password: "ItsASecret" $
The -a option, which specifies the account, is required.
The -D option specifies the entry "Kind", which is "802.1X
Password". The -s specifies the service name; I had to use
com.apple.network.eap.user.item.wlan.ssid.asa for that value
to update the existing entry, even though I used -U to specify
that I wanted to update an existing entry. Otherwise, a new keychain entry
would be created. To avoid that value also being inserted in the Name
field, I used the -l option to speify a label, which
goes into the Name field. Otherwise, whatever I put for the
value for the -s option would go into the Name field
as well.
Note: I can enter a password that contains an exclamation mark
(!) through the Keychain Access GUI, but I initially
had problems entering a password that contained an exclamation mark
through the command line interface using security. If I just
put in the exclamation mark without an
escape character preceding it, it was interpreted by the
Bash
shell and I saw the message -sh: !" event not found. But,
if I preceded it with a backslash (\) as an escape character, then
the backslash character was included in the stored password as shown below,
which was not what I needed.
$ security add-generic-password -a jasmith1 -s com.apple.network.eap.user.item.wlan.ssid.asa -l asa -D "802.1X Password" -U -w "ItsASecret!" -sh: !": event not found $ security add-generic-password -a jasmith1 -s com.apple.network.eap.user.item.wlan.ssid.asa -l asa -D "802.1X Password" -U -w "ItsASecret\!" $ security find-generic-password -gD "802.1X Password" | grep "password:" password: 0x497473415365637265745C21 "ItsASecret\134!" $
In the case above, when I queried the password with security
find-generic-password, I saw "\134!" as part of the password rather
than just the exclamation mark that I expected at the end of the password.
The number 134 is the octal representation of the backslash character as
can be seen in the ASCII Table and
Description. But, if I examined that password by double-clicking on the
relevant entry in Keychain Access and checking "Show password",
then I saw ItsASecret\!. I could change the password there to be
ItsASecret!, though and see what I expected when I quered the value
from the command line.
$ security find-generic-password -gD "802.1X Password" | grep "password:" password: "ItsASecret!" $
I found the solution was to to enclose the password in single quotes rather than double quotes, so I would recommend using those for any passwords containing non alphanumeric characters.
$ security add-generic-password -a jasmith1 -s com.apple.network.eap.user.item.wlan.ssid.asa -l asa -D "802.1X Password" -U -w 'AnotherSecret!' $ security find-generic-password -gD "802.1X Password" | grep "password:" password: "AnotherSecret!"
You can also delete the entry from the keychain using the
delete-generic-password parameter. You can issue the
command security delete-generic-password -h to see available
options:
$ security delete-generic-password -h
Usage: delete-generic-password [-a account] [-s service] [options...] keychain...]
-a Match "account" string
-c Match "creator" (four-character code)
-C Match "type" (four-character code)
-D Match "kind" string
-G Match "value" string (generic attribute)
-j Match "comment" string
-l Match "label" string
-s Match "service" string
If no keychains are specified to search, the default search list is used.
Delete a generic password item.
$For the example shown above where the SSID is "asa" and the account name is "jasmith1", I could use the command shown below. You will see a lot of information starting with "class" related to the entry you are deleting, but at the end of the output you should see "password has been deleted."
$ security delete-generic-password -a jasmith1 -D "802.1X Password"
keychain: "/Users/jasmith1/Library/Keychains/login.keychain"
class: "genp"
attributes:
0x00000007 <blob>="asa"
0x00000008 <blob>=<NULL>
"acct"<blob>="jasmith1"
"cdat"<timedate>=0x32303136303333303232343935305A00 "20160330224950Z\000"
"crtr"<uint32>=<NULL>
"cusi"<sint32>=<NULL>
"desc"<blob>="802.1X Password"
"gena"<blob>=<NULL>
"icmt"<blob>=<NULL>
"invi"<sint32>=<NULL>
"mdat"<timedate>=0x32303136303333303232343935305A00 "20160330224950Z\000"
"nega"<sint32>=<NULL>
"prot"<blob>=<NULL>
"scrp"<sint32>=<NULL>
"svce"<blob>="com.apple.network.eap.user.item.wlan.ssid.asa"
"type"<uint32>=<NULL>
password has been deleted.
$ If you delete the entry, either through the Keychain Access GUI or from the Terminal CLI, the next time you attempt to connect to the wireless network you should be prompted for the password to use, which is another alternative to fixing the problem for 802.1X authentication failure due to an old password being used.
References: