

When I booted the system into Windows XP Home edition, I saw a Norton Antivirus 2005 alert appear.
| Norton AntiVirus | |
| Virus Alert | |
| Object Name | C:\WINDOWS\system32\WININET.dll |
| Virus Name | W32.Desktophijack |
| Action Taken | Unable to repair this file. |
When I clicked on OK, I saw a similar window appear, except with "Action Taken" now listed as "Action to the file was denied". Clicking on OK on that window brought up the first window again. The sequence repeated multiple times before finally stopping.
The Symantec Security Response - W32.Desktophijack webpage states that, when When W32.Desktophijack is executed, it takes the following actions:
echo %windir% to
see the value for this folder.I don't see any uninstIU.exe file in c:\windows nor an oleadm32.dll in c:\windows\system32, though I do see an oleadm.dll file with a timesamp of 8/29/2002 06:00 AM in c:\windows\system32. That timestamp matches the timestamp on all of the other DLL files with names beginning with "ole", so it doesn't appear to be one created by this virus. However, when I submitted it to Jotti's Online Malware Scan, many of the antivirus programs used by Jotti reported it was associated with a trojan (see report), though not the same one as listed for wininet.dll. I also see a c:\windows\system32\wp.bmp file. It has a timestamp of 7/17/2005 12:31 AM.
| Name: | wp.bmp |
| Location | c:\windows\system32 |
| Size: | 97.3 KB (99,678 bytes) |
| Created: | Sunday, July 17, 2005 12:31:58 AM |
| MD5 Sum: | 87ee64e4c2b88cb8dfa39d87423a5a95 |
| Name: | oleadm.dll |
| Location | c:\windows\system32 |
| Size: | 19.0 KB (19,456 bytes) |
| Created: | Thursday, August 29, 2002 6:00:00 AM |
| MD5 Sum: | 1c8561853a71ea0c6795324336396f66 |
| File Version: | 4.71.2900.0 |
| Description: | Microsoft OLE Extensions for Windows |
| Company: | Microsoft Corporation |
| Name: | wininet.dll |
| Location | c:\windows\system32 |
| Size: | 585 KB (599,040 bytes) |
| Created: | Thursday, August 29, 2002 6:00:00 AM |
| MD5 Sum: | ce85639efdc549ac9507397645b2e0ff |
| File Version: | 6.0.2800.1106 |
| Description: | Internet Extensions for Win32 |
| Company: | Microsoft Corporation |
Searching for other wininet.dll files on the system, I see that the one in c:\windows\system32 matches the one in c:\i386 according to size and date, though that, of course, doesn't mean they are identical.
On September 20, 2005, I submitted the c:\windows\system32 copy of wininet.dll to Jotti's Online Malware Scan, which checks files with 14 different antivirus programs. The report it produced showed all but three of the antivirus programs reporting the file is infected.
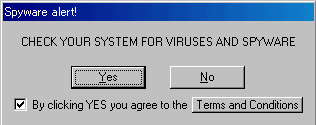
The wp.bmp file in c:\windows\system32 is an image that has a "Security warning" title at the top and then the following text. It has white text on a blue background to simulate a Windows Blue Screen of Death (BSOD) display.
| Security warning | ||
|
A fatal error in IE has occurred at 0028:C0011E36 in VXD VMM(01) + 00010E36. Error was caused by Trojan-Spy.HTML.Smitfraud.c * System can not function in normal mode. Please check you security settings. * Scan your PC with any available antivirus / spyware remover program to fix the problem. |
||
The fake message references Trojan-Spy.HTML.Smitfraud.c. There was a smitfraudinfo folder on the desktop. That folder was created on Sunday, July 17, 2005 at 4:33:09 PM. Looking in the folder I see a copy of the Symantec webpage dealing with W32.Desktophijack, so the folder was likely created by the user at that time when he tried to obtain information on the alert Norton AntiVirus 2005 was displaying regarding W32.Desktophijack.
I found another wininet.dll file with the same timestamp and exactly the same size in c:\i386. I submitted it to Jotti's Online Malware Scan for analysis. None of the 14 antivirus programs used there reported any infection in that file. Though it was the same size and had the same timestamp, it had an MD5 checksum of f3587750a7481dccbea13d473a0700be, while the checksum of the infected version is ce85639efdc549ac9507397645b2e0ff.
Download infected file found in c:\windows\system32 for analysis:
wininet.dll
Zip file containing infected wininet.dll
Download uninfected file found in c:\i386 for comparison:
Zip file containing uninfected wininet.dll
I wasn't able to work on the system again for a couple of days, but was able to work on it again on 9/25 when I replaced the infected copy of wininet.dll with the uninfected file in c:\i386. Since the file is needed by Windows, I couldn't simply delete it, which is likely why Norton AntiVirus on the system didn't quarantine it. When I first tried to overwrite the infected version with the uninfected one, I booted the system into Safe Mode (hit the F8 key before you see the Windows logon and choose "Safe Mode" as the boot option) and tried copying the the wininet file from the c:\i386 directory to the c:\windows\system32 directory, but that didn't work. I received the error message below:
Error Copying File or Folder
Cannot copy WININET: It is being used by another persorn or program.
Close any programs that might be using the file and try again.
Unfortunately, Microsoft has crippled the home version of Windows XP in
various ways to market it as a lower priced "home" version. One of the
ways they've crippled it, is to remove very useful utilities, such
as tasklist, which will show you a list of running processes and the modules,
such as DLL files, that
they have loaded. So I couldn't immediately determine what process or
processes had wininet.dll open. So I put tasklist.exe on the system
and used it to look for the processes using wininet.dll. You can copy
tasklist.exe from the c:\windows\system32 directory on a Windows XP
Professional system or download it from
http://www.computerhope.com/download/winxp/tasklist.exe. If you download
it from the Computer Hope's free
computer help site, you will get the file that is used on Windows XP
Professional systems (I compared that file to the one on a Windows XP
Professional system with fc /b a:\wininet.dll
c:\windows\system32\wininet and the binary file comparison by fc
reported they are identical). Alternatively, you can use
Process
Explorer from Sysinternals
to see the DLLs loaded by processes running on a system.
When I searched for processes that were using wininet.dll with
tasklist /fi "modules eq wininet.dll", I found that SVCHOST.EXE
was using it as well as EXPLORER.EXE. Unfortunately, since wininet.dll
contains Internet-related functions used by Windows applications, it was
loaded, even though I booted into Safe Mode without choosing the "Safe mode with
Networking" option. So I rebooted again, hit the F8 key prior to the Windows
logo appearing and then chose "Safe Mode with Command Prompt" instead. But
when I tried overwriting the file with the uninfected version using the
copy command, I again got an error message. This time I saw "The process
cannot access the file because it is being used by another process."
I thought I would likely need to boot the system using a boot CD such as ERD Commander, since I have ERD Commander 2002, or a Linux LiveCD, such as the Trinity Rescue Kit, which would allow me to boot into an alternative operating system, but still access the NTFS partition on which Windows XP Home resided to replace the infected version of wininet.dll with the noninfected version. However, while searching for information on the problem I found a forum thread on Computing.Net titled Subject: virus on wininet.dll - can't solve, that allowed me to resolve the problem while booted into "Safe Mode with Command Prompt". One of the respondents to a posting by someone who was suffering from the same infection of wininet.dll suggested renaming wininet.dll to wininet.dl.
I didn't think that would work. After all, if I couldn't copy a file over
it or delete it, why should I be able to simply rename it to resolve the
problem. But, lo and behold, when I typed rename wininet.dll
wininet.dl, it worked. I then was able to use the command copy
c:\i386\wininet.dll c:\windows\system32\. to copy the uninfected file
into the c:\windows\system32 directory where Windows expects to find it. The
respondent suggested one might also install Service Pack 2, which would
replace wininet.dll with an updated version (the system I was working on
had Service Pack 1 installed). When I then tried to delete wininet.dl, though
I got the message "Access is denied." But I then rebooted normally. I didn't
get the alert message from Symantec AntiVirus immediately after logging on.
Though when I went to c:\windows\system32 and selected the file to delete
it, Norton AntiVirus 2005 reported that wininet.dl was infected by
W32_Desktophijack and was repaired. The MD5 checksum of the repaired file
didn't match the one for the file I copied from \i386, though. Since I
didn't need a repaired wininet.dl as I was using the uninfected wininet.dll
from \i386, I removed wininet.dl
Interestingly, when I submitted my infected copy of wininet.dll to Jotti's Online Malware Scan, on September 20, 2005, AVG Antivirus on that system then didn't find any infection in the file nor did Norman Virus Control nor UNA, but the user posting the message to the forum reported that he was using AVG on a Windows XP Professional system. So I resubmitted the file to Jotti's Online Malware Scan and this time only Norman Virus Control did not report it as infected (see 9/25 report)