Turning on UltraVNC server service on a Windows system
If you installed
UltraVNC,
which is
free and open-source software, to provide
Virtual Network Computing (VNC) connectivity from/to
a system for remote administration capabilities, but haven't enabled
the UltraVNC server service to allow the system itself to be managed remotely,
you can enable that service by taking the following steps:
-
Run the
uvnc_settings.exe program, which you can find in
the directory where you installed UltraVNC. You will need to provide the
login credentials for an account with administrator-level access on the
system.
-
Click on the Service tab then click on the Install Service
button, which will install the software as a service, i.e. as a function
provided by a server, on the system.
-
Once the service is installed, you can click on the Start Service
button to run the service.
-
You can set the password to be used for VNC connections by clicking on
the Security tab. You can set two passwords. The "VNC Password"
will allow remote control of the system whereas the "View-Only Password"
will only allow viewing the display on the system, which is helpful if you
want to show someone what is happening on the system without giving the
person the ability to control the system. You can then click on the
OK button to close the UltraVNC settings window.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
UltraVNC not responding to connection attempts
A user reported he was unable to connect to a Microsoft Windows 8 system
functioning as a
VNC server using
UltraVNC.
The remote vncviewer program was reporting "Failed to connect to server !" I
logged into the system and verified that the system was listening on the
registered port for VNC, port 5900 using the
netstat
command.
C:\Users\Collen>netstat -a | find "5900"
TCP 0.0.0.0:5900 Speleologist:0 LISTENING
C:\Users\Collen>
I used windump,
a free
packet capture tool for Microsoft Windows systems, similar to
the tcpdump
tool found on
OS X/macOS and Linux systems, to verify that the system was seeing the
incoming connections to
network port 5900.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
Changing the UltraVNC passwords
To change the password used for connectivity to a system running
the
UltraVNC
free and open-source software that provides
remote-administration/
remote-desktop-software
functionality for
Microsoft Windows, select the icon representing
UltraVNC in
the system tray; it has an eye within it.
Right-click on it and select Admin Properties. At the Admin
Properties window, you can type a password in the "View-Ony Password"
that can be used to allow remote users access to the system via VNC. It
will only check the first 8 characters of a password.After making any
password change, click on the Apply button.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
Installing an encryption plugin for UltraVNC
An
encryption
plugin is available for the
UltraVNC
open source remote administration/
remote
desktop software. The
SecureVNC Plugin has the following specifications:
- Default configuration uses 2048-bit RSA keys and 256-bit AES keys.
- RSA public-key cryptography supports 512-, 1024-, 2048-, and 3072-bit keys.
- Configurable choice of symmetric ciphers and keys:
- AES: Supports 128-, 192-, and 256-bit keys.
- Blowfish: Supports 56-, 128-, 192-, 256-, and 448-bit keys.
- IDEA: Supports 128-bit keys.
- CAST5: Supports 56- and 128-bit keys.
- ARC4: Supports 56-, 128-, 192-, and 256-bit keys.
- Classic interface for older UltraVNC versions 1.0.8.2 or below uses 2048-bit RSA keys and 128-bit AES keys.
- All versions are threadsafe, allowing the UltraVNC server to host multiple simultaneous viewers.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
Installing RealVNC 4.1.2 under Windows
I installed the free edition of
RealVNC
4.1.2 on a Windows XP system.
Windows
Defender 1.1.1593 was installed on the system and popped up a warning
when I started the installation of RealVNC.
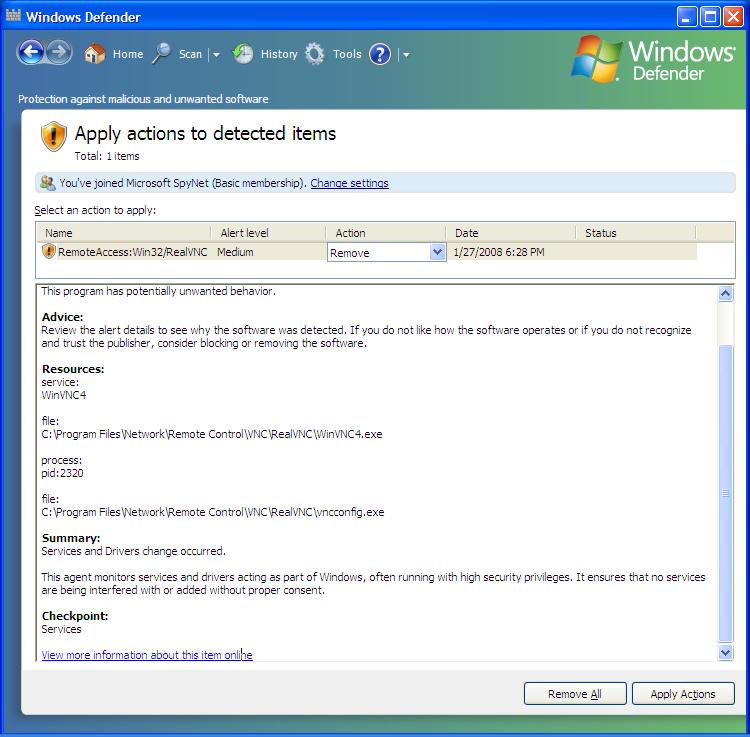
To get Windows Defender to accept RealVNC, select "always allow" for
the action and then click on "Apply Actions".
When you are configuring RealVNC during installation, under the
Connections tab in RealVNC, you can set the ports or retain the
default ports that will be used for listening for connections, if
you are installing the server portion of the software so you
can connect remotely to the system you are installing it on. The
default values are shown below:
Accept connections on port: 5900
Disconnect idle clients after (seconds): 3600
Serve Java viewer via HTTP on port: 5800
Under Access Control in the Connections section, you
can check "Only accept connections from the local machine", if you wnat
to require access to be through an SSH connection.
If you install the server portion of the software to run as a service
on the Windows system, but don't want it to start automatically, click
on the Windows Start button, select Run and type
services.msc. Find "VNC Server Version 4" within the services
list, double-click on it and change the startup type from "automatic" to
"manual", then click on OK.
References:
-
Malicious Software Encyclopedia: RemoteAccess:Win32/RealVNC
Published: September 12, 2006
Microsoft Corporation
[/os/windows/software/remote-control/vnc]
permanent link
VNC Local Loop-back Connections Disabled
I installed
TightVNC on a Windows
SBS 2003 server
in order to be able to remotely manage it from a Unix or Linux host.
I had previously installed
OpenSSH for Windows on the system so that I could login to the
system remotely and check on the system, but I also wanted to have
a
GUI connection to the
system so that I could run programs that can't be run from the command line
From a Unix workstation running Solaris, I entered the command
ssh -L 5901:localhost:5900 administrator@192.168.0.5 to
establish an SSH connection to
the system with port 5901 on the Unix workstation being forwarded to
port 5900 on the Windows SBS 2003 server. Port 5900 is the default port
for a VNC server and the one I used on the Windows system. However,
when I tried to connect to the Windows system with vncviewer by connecting
to port 5901 on the Unix system, which then should be forwarded over the
SSH connection to port 5900 on the Windows system, I saw the message
"Local loop-back connections are disabled."
bash-2.03$ vncviewer localhost:1
VNC viewer for X version 4.0 - built Jun 14 2004 12:04:05
Copyright (C) 2002-2004 RealVNC Ltd.
See http://www.realvnc.com for information on VNC.
Tue Nov 22 16:08:49 2005
CConn: connected to host localhost port 5901
CConnection: Server supports RFB protocol version 3.3
CConnection: Using RFB protocol version 3.3
Tue Nov 22 16:08:50 2005
main: Local loop-back connections are disabled.
Doing a Google search on the
error, I learned I needed to have the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3 on the Windows system set
to a DWORD value of "1". Since I had a command line prompt on the
Windows system via the SSH connection, I used the reg query
command to check the current value of that registry key. Sure enough,
its current value was "0".
C:\Documents and Settings\Administrator>reg query HKEY_LOCAL_MACHINE\SOFTWARE\OR
L\WinVNC3
HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3
ConnectPriority REG_DWORD 0x0
DebugMode REG_DWORD 0x0
DebugLevel REG_DWORD 0x2
LoopbackOnly REG_DWORD 0x0
EnableHTTPDaemon REG_DWORD 0x1
EnableURLParams REG_DWORD 0x0
AllowLoopback REG_DWORD 0x0
AuthRequired REG_DWORD 0x1
HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3\Default
Fortunately, the reg command can also be used to modify the
registry from the command line.
C:\Documents and Settings\Administrator>reg add HKEY_LOCAL_MACHINE\SOFTWARE\ORL\
WinVNC3 /v AllowLoopback /t REG_DWORD /d 1
Value AllowLoopback exists, overwrite(Yes/No)? yes
The operation completed successfully.
The REG ADD command uses the following syntax:
REG ADD KeyName [/v ValueName | /ve] [/t Type] [/s Separator] [/d Data] [/f]
In this case, the parameters used have the following meaning:
/v The value name, in this case "AllowLoopback", to
be added under the selected key.
/t Allows one to specify the data type, which can be
REG_SZ, REG_MULTI_SZ, REG_EXPAND_SZ, REG_DWORD, REG_BINARY, or REG_NONE.
If none is specified, REG_SZ is assumed. In this case REG_DWORD is needed.
/d The data to assign to the registry ValueName being
added, which is "1" in this case.
Another reg query HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3
shows the value was changed.
C:\Documents and Settings\Administrator>reg query HKEY_LOCAL_MACHINE\SOFTWARE\OR
L\WinVNC3
HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3
ConnectPriority REG_DWORD 0x0
DebugMode REG_DWORD 0x0
DebugLevel REG_DWORD 0x2
LoopbackOnly REG_DWORD 0x0
EnableHTTPDaemon REG_DWORD 0x1
EnableURLParams REG_DWORD 0x0
AllowLoopback REG_DWORD 0x1
AuthRequired REG_DWORD 0x1
HKEY_LOCAL_MACHINE\SOFTWARE\ORL\WinVNC3\Default
After modifying the registry value, you then must stop and restart the
VNC Server service.
C:\Documents and Settings\Administrator>net stop "VNC Server"
The VNC Server service is stopping..
The VNC Server service was stopped successfully.
C:\Documents and Settings\Administrator>net start "VNC Server"
The VNC Server service is starting.
The VNC Server service was started successfully.
You should then be able to use vncviewer localhost:1 to
access the remote system with VNC. After the message about the
protocol version, you should see a VNC Authentication window
open.
bash-2.03$ vncviewer localhost:1
VNC viewer for X version 4.0 - built Jun 14 2004 12:04:05
Copyright (C) 2002-2004 RealVNC Ltd.
See http://www.realvnc.com for information on VNC.
Tue Nov 22 17:07:42 2005
CConn: connected to host localhost port 5901
CConnection: Server supports RFB protocol version 3.3
CConnection: Using RFB protocol version 3.3
In this case, I was then able to enter the VNC authorization password
and then hit Ctrl-Alt-Del on the Solaris system to enter the user name
and password for the Windows SBS 2003 server.
References:
-
Cygwin ssh (OpenSSH), and Win98 - Use "crypt newpassword" to add a password
into /etc/passwd
[/os/windows/software/remote-control/vnc]
permanent link


