I installed NuBert version 2011.07.06.2 from Nucor Building Systems from an administrator account on a user's PC running Windows 7 Professional and entered the product key for the software. I was able to start the software from the domain administrator or local administrator account, but not the user's account, not even when I temporarily put the user's account in the domain users group. Putting the product code in when prompted to do so when the software was run under the user's account did not lead to the software running. It would simply terminate after the code was entered and the next time it was run I would be prompted for the code again.
In the registry, I found the following key associated with the software:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Nucor
When I right-clicked on the subkeys and checked their permissions, I saw that user accounts had read permissions for them.
I used Microsoft's free
Process
Monitor utiltity to check the file access and registry access
of the NBS.NuBert.Bootstrapper.Loader.exe process when
it was run from the domain administrator account and from the user's
account. I noticed that when it was run from the administrator's account,
it was accessing the directory
C:\Users\Administrator\AppData\Local\Nucor_Building_Systems.
I copied that directory to
C:\Users\useracct\AppData\Local\Nucor_Building_Systems
where useracct was the user's account name.
For the administrator account the following files were in the directory:
DefaultPerisssions
NuBertTreelistLayout
PermissionMetadata
There was also a directory with a name that began with
NBS.BERT.HostEnvironment._Url_ followed by a very long
string of digits and letters. There was a directory named
2011.7.7.1 within it and a file named
user.config within that directory.
For the users account, the following files were the only ones initially
in the Nucor_Building_Systems directory:
DefaultPerisssions
PermissionMetadata
I copied the directory and all of the files from the
Nucor_Building_Systems folder under the administrators
account into the same one under the user's account, replacing the files
already there.
I logged off the administrator's account and tested again from the user's account. Again, I was prompted for the product key, however.
I then logged into the administrator's account again. I right-clicked
on the NuBert shortcut on the desktop, chose Properties
then clicked on the Advanced button under the Shortcut tab.
Run as administrator was grayed out, so I could not select it.
So, from the administrator account,
I created a new shortcut on the desktop that pointed to
"C:\Program Files (x86)\NBS\BERT\NBS.NuBert.Bootstrapper.Loader.exe"
. I right-clicked on the NuBert shortcut on the desktop,
chose Properties then clicked on the Advanced button under
the Shortcut tab. I then checked Run as administrator and
clicked on OK.
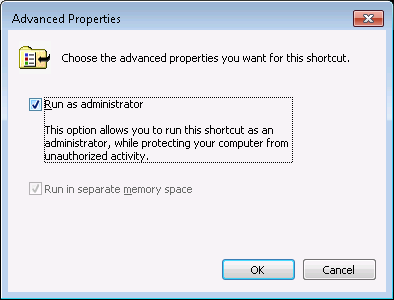
I then clicked on the Security tab, clicked
on the Edit button and added Domain Users, since the
user logs into a domain account. I then clicked on OK to close the
Properties window for the shortcut. I then copied the shortcut
from the domain administrator's desktop to the user's desktop at
C:\Users\useracct\Desktop, where useracct is
the username for the user's account.
Then when the user clicked on the shortcut, he would be prompted for a user name and password. I had him put in pcname\administrator, where pcname was the name of his computer, as the user name to use the local administrator account for his PC and the password for that account. I also created a .cmd file with just the following command in it and put a shortcut to it on his desktop as well:
runas /user:administrator "C:\Program Files (x86)\NBS\BERT\NBS.NuBert.Bootstrapper.Loader.exe
That would allow him to just put in the password for the local administrator account to save him a small amount of typing, if he preferred using it to the other shortcut.
Of course, running the software under the local administrator account is a poor solution, due to the security implications, but the only one I could get to work. Why do some software developers seemingly assume that their software will be run from an account with administrator privileges or that a system won't even employ the very minimum of security measures?

