←March→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| 1 |
2 |
3 |
4 |
5 |
6 |
7 |
| 8 |
9 |
10 |
11 |
12 |
13 |
14 |
| 15 |
16 |
17 |
18 |
19 |
20 |
21 |
| 22 |
23 |
24 |
25 |
26 |
27 |
28 |
| 29 |
30 |
31 |
|
|
|
|
|
|
Tue, Feb 26, 2019 9:28 pm
Monitoring directory changes with fswatch on OS X/macOS
If you want to monitor file changes in a directory on an Apple
OS X/macOS
system, one way to do so is using
fswatch, a cross-platform
file change monitor. The utility will allow
you to monitor which files in the directory have been changed, though it doesn't
report on the particular changes made to the content of the files. You can track
the addition and deletion of files or whether files in the monitored directory
are modified. On a Mac OS X system, you can install the software using the
Homebrew package management system - see
Installing Homebrew on Mac OS X for
instructions on installing the software. Once Homebrew is installed, you
can install fswatch using the command brew install fswatch in
a
Terminal window, which provides a
command-line interface (CLI). The program
will be installed in /usr/local/bin. Once it is installed, you
can view help information by typing fswatch -h at a Terminal
window shell prompt.
[ More Info ]
[/os/os-x/homebrew]
permanent link
Fri, Jul 27, 2018 11:07 pm
Determining if the system is connected to a VPN from the command line under OS X
I connect to a work
Virtual Private Network (VPN) from home using a
MacBook Pro
laptop running
OS X El
Capitan (10.11.6) and was curious if there was a way that I could determine
whether the system was connected to the VPN or disconnected from a VPN using a
command-line
interface (CLI), i.e., a
Terminal window, other than by checking the IP address that
external systems see for the system, e.g., by visiting
WhatIsMyIP.com. At
How can I tell if OS X is connected to a VPN network from the command line?,
I found someone suggesting using the
scutil command
scutil --nc list and
piping
the output to the grep command looking for the word "Connected", i.e.,
scutil --nc list | grep Connected. However, that didn't work
when I attempted to discern whether the laptop was connected to the VPN via
that method, since the scutil command always produced the following output
whether or not the system was connected to the VPN:
$ scutil --nc list
Available network connection services in the current set (*=enabled):
$
However, I was able to determine if the system was connected to the VPN by
using the method listed in the post by the person who posed the question. I.e.,
I could use the
ifconfig command and count the number of occurences of "utun0," since
the count was zero if the system was not connected to the VPN and one if it
was connected to the VPN. E.g., if the system was not connected to the VPN,
I would see the following output.
$ ifconfig | grep utun0
$ ifconfig | grep -c utun0
0
$
When the system was connected to the VPN, I would see the following output:
$ ifconfig | grep utun0
utun0: flags=8051<UP,POINTOPOINT,RUNNING,MULTICAST> mtu 1400
$ ifconfig | grep -c utun0
1
$
[ More Info ]
[/os/os-x]
permanent link
Wed, Jun 13, 2018 11:21 pm
Screen goes black with only mouse pointer visible on MacBook Pro laptop
I've been experiencing an intermittent issue on my
MacBook
Pro laptop, which is running
OS X El Capitan, where I find a black screen with only the mouse pointer
visible after I return to it from being away from it for some time. I can move the pointer by moving my finger about on the touchpad, but I get no visible
response to hitting any keys. I've tried hitting lots of different
key combinations to try to get the desktop to reappear or at least get
a login prompt, but none have worked. If I had music playing through
the headphones from
iTunes , I can hear it still playing if I put the
headphones back on, but when I hit any key or keys I simply hear a "bonk"
sound and see no response from the system. Initially, when I encountered
the problem the only way I could gain access to the system again was to
reboot, which might lead to a loss of unsaved work. I have found, though,
that if I simply close the lid of the laptop as I might if I wanted to put
it to sleep, wait about a minute, then reopen the lid and hit a key that most
of the times I've tried that, instead of rebooting, when the problem has
occurred, that I could get a login prompt allowing me to log back into the
system with everything apparently running as it was before I encountered
the problem.
[/os/os-x]
permanent link
Thu, May 24, 2018 11:10 pm
Using sox to record audio on OS X
I wanted to record a talk this week so I took my
MacBook Pro
laptop with me to the auditorium where the talk was being held. I
normally
use the QuickTime
Player to record audio in such cases. But this time when I attempted
to use the QuickTime Player, it wouldn't actually start recording.
The presenters had started talking when I attempted to begin recording
their presentation, so I opted to install
Sound eXchange
(SoX), which provides a
command-line interface (CLI) for recording and
editing audio on a variety of
operating systems, including
Microsoft Windows,
Linux, and
OS X. Since I had previously
installed Homebrew on OS X on the system, I
opened a
Terminal window and used it to install SoX.
[ More Info ]
[/os/os-x/audio]
permanent link
Thu, May 17, 2018 11:15 pm
Identifying Apple systems on the network
If you need to determine whether a system on the network is an
Apple
system, there are a number of means you can use to help identify whether
the system is, or is at least likely to be, manufactured by Apple. E.g.,
if the system is on the same
local area network (LAN) as a system from which you can
ping it, you can check the
media access control (MAC) address associated with the
IP address
you just pinged using the
Address Resolution Protocol (ARP), since the first 6
hexadecimal
digits of the MAC address can be used to identify the manufacturer of the
network interface controller (NIC) in the device pinged.
This technique won't work if there is an intervening
router between the device from which the ping is sent and the
receiving device, though, since the arp address you will see when there are
intervening
network hops is the one of the first hop device. You can see the number
of hops between the source and destination hosts using the
traceroute command (tracert is the equivalent command on
Microsoft Windows systems). E.g., in the example
below, I issued a ping command from a
Terminal window on my
MacBook
Pro laptop running OS X El Capitan (10.11.6). When I then peformed a
reverse DNS lookup on the IP address using
nslookup,
the fully qualified domain name (FQDN) identified the device
as an iPad.
The FQDN usually won't identify the type of device so clearly, but a check
of the MAC address may indicate the device was manufacturered by Apple. You
can get the MAC address using the
arp command.
$ ping -c 1 192.168.196.212
PING 192.168.196.212 (192.168.196.212): 56 data bytes
64 bytes from 192.168.196.212: icmp_seq=0 ttl=64 time=45.140 ms
--- 192.168.196.212 ping statistics ---
1 packets transmitted, 1 packets received, 0.0% packet loss
round-trip min/avg/max/stddev = 45.140/45.140/45.140/0.000 ms
$ nslookup 192.168.196.212
Server: 192.168.10.134
Address: 192.168.10.134#53
212.196.168.192.in-addr.arpa name = Margarets-iPad.abc.example.com
$ arp Margarets-iPad.abc.example.com
margarets-ipad.abc.example.com (192.168.196.212) at 78:7b:8a:55:bb:35 on en0 ifscope [ethernet]
$
[ More Info ]
[/os/os-x]
permanent link
Tue, Feb 27, 2018 11:10 pm
Error message "You don't have permission to access / on this server."
I had been running an Apache webserver under
OS X El Capitan on my
MacBook
Pro laptop. After an upgrade on the laptop, now running
OS X El Capitan (10.11.6), when I tried accessing the site
via http://localhost, I saw a page with the title "403 Forbidden"
and the following text displayed on the page:
Forbidden
You don't have permission to access /
on this server.
[ More Info ]
[/os/os-x/apache]
permanent link
Thu, Feb 22, 2018 11:01 pm
Installing GIMP on OS X
To install the
GNU Image Manipulation Program
(GIMP) on
OS X systems, take the following steps:
-
Download the GIMP installation file from
GIMP - Downloads. The
file is an Apple Disk Image .dmg file.
-
Double-click on the downloaded file to start the installation process.
-
When the GIMP installation window opens, you will see "GIMP.app" in the
window that opens. Click on "GIMP.app" and drag it over into a
Finder window with the Applications folder
displayed to complete the installation of the GIMP application into that folder.
[ More Info ]
[/os/os-x]
permanent link
Wed, Jan 17, 2018 11:01 pm
Renewing a DHCP lease under OS X
If you wish to renew a
Dynamic Host Configuration Protocol (DHCP) lease on a Mac
OS X
system, you can do so by clicking on the Apple icon in the upper, left-hand
corner of the screen, selecting System Preferences, and then Network
, and then the relevant network interface, e.g., Wi-Fi.
Then click on the Advanced button and then the TCP/IP tab.
You can then click on the Renew DHCP Lease button to have the system
attempt to renew its DHCP lease.
[ More Info ]
[/os/os-x]
permanent link
Wed, Oct 25, 2017 10:36 pm
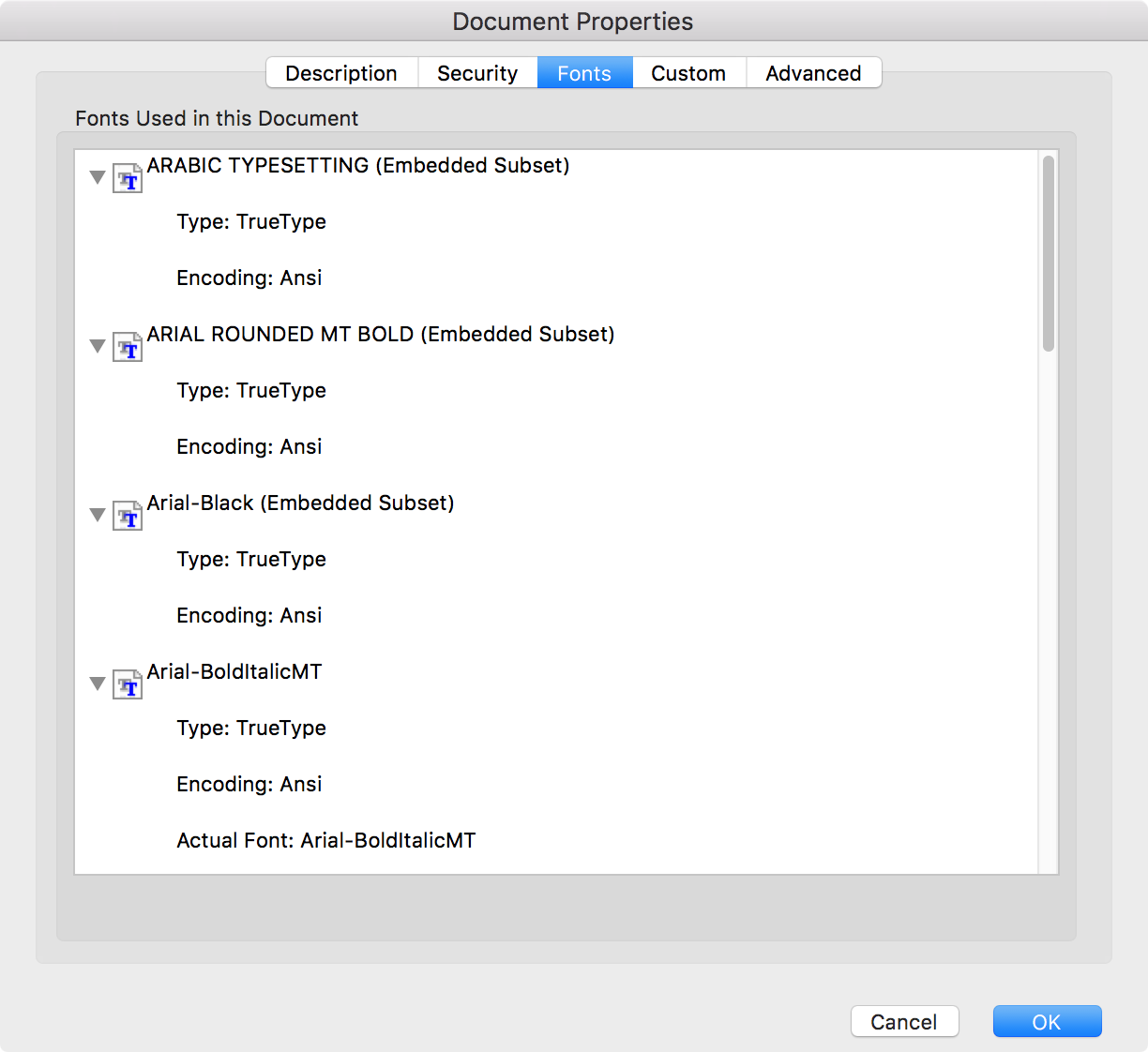
Viewing the fonts used in a PDF document on a Mac OS X system
To view the list of documents contained in a
PDF document with Adobe Acrobat Reader DC on a
Mac OS X
system, with the file open in Acrobat Reader DC, click on File then
select Properties and then click on the Fonts tab.
[ More Info ]
[/os/os-x]
permanent link
Sun, Oct 08, 2017 10:57 pm
Calculating file checksums on an OS X system
If you need to calculate a
checksum, aka
cryptographic hash value or digital fingerprint, on a
Mac
OS X
system, you can use the
md5
command to calculate a
MD5 checksum, which is equivalent to the
md5sum utility on Linux
systems, and the
shasum
command to calculate Secure Hash Algorithms (SHA). The default value for
shasum, if no
algorithm is specified, is
Secure Hash Algorithm 1 (SHA-1), but you can specify other
algorithms, such as
Secure Hash
Algorithm 2 (SHA-2), e.g. SHA-256, using the
-a option. E.g.
-a 256 for SHA-256.
[ More Info ]
[/os/os-x]
permanent link

Privacy Policy
Contact



