←February→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| 1 |
2 |
3 |
4 |
5 |
6 |
7 |
| 8 |
9 |
10 |
11 |
12 |
13 |
14 |
| 15 |
16 |
17 |
18 |
19 |
20 |
21 |
| 22 |
23 |
24 |
25 |
26 |
27 |
28 |
| ←2026→| Months |
|---|
| Jan |
Feb | Mar |
| Apr |
May |
Jun |
| Jul |
Aug |
Sep |
| Oct |
Nov |
Dec |
|
Thu, Mar 21, 2024 9:06 pm
Determining Excel's autosave value from the Windows registry
Microsoft Excel provides an autorecover feature that allows you to recover
updates to spreadsheets or other files that were open in Excel even if changes
were made since the last time the file was saved. Excel will automatically save
files at a specified time interval so that if Excel crashes or the system
crashes or loses power, you can recover the latest version of the file, or at
least the file as it was the last time Excel automatically saved it. For the
Office 365 version of
Excel, you can find the autosave interval by clicking on
File in
Excel then selecting
More, then
Options, and then
Save. The default value is 10 minutes but you can have
Excel save more or less frequently.
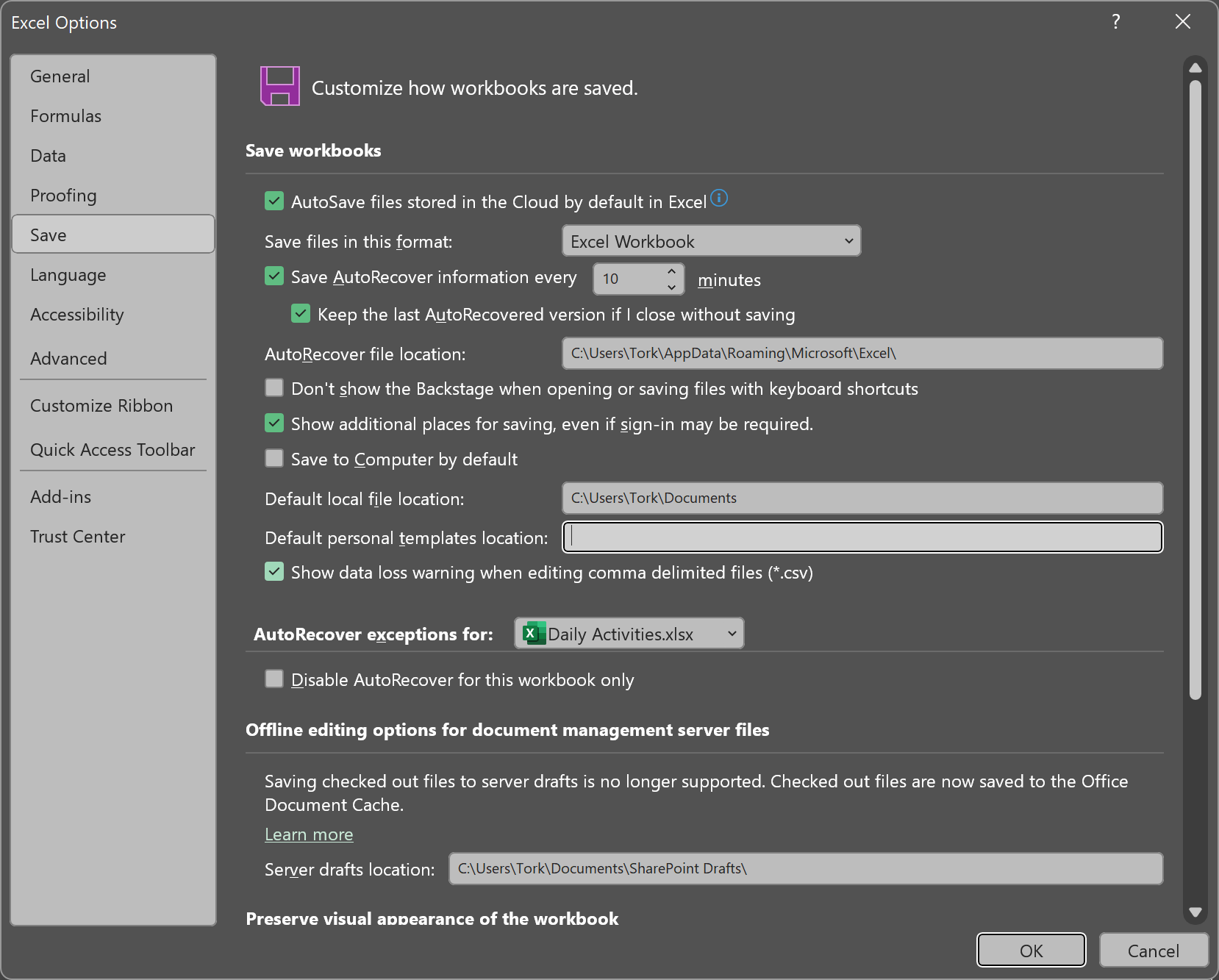
You can also find the value by checking the
Windows Registry,
which you can view or edit by using the Registry Editor program that
comes with Microsoft Windows. You can find the value by navigating to
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Excel\Options
and checking the value for AutoRecoverTime.
[ More Info ]
[/os/windows/registry]
permanent link
Tue, Jan 28, 2020 10:16 pm
Determining the time a registry key was last updated
When I ran a scan of a Windows System with
Spybot Search & Destroy 1.62, it reported it found a
Windows
registry key associated with GhostMail - it identified
GhostMail as adware. To check the registry key, I typed regedit in
the "Type here to search" field at the bottom of the screen and then selected
the "Registry Editor" app when it appeared in the list of returned results
(you can also open the application by typing regedit and hitting
enter at a command prompt. I then
navigated to the relevant key. I wanted to determine when the registry was
created or at least when it was last modified. You can't see that information
in the Windows
Registry Editor, but you can create a text file that will
contain that information by right-clicking on a key and choosing "Export" to
generate a text file - select "Text Files (*.txt)" in the "Save as type" field,
not the default value of "Registration Files (*.reg)."
The
text file will contain the key as well as
the time it was last written to:
| Key Name: | HKEY_USERS\S-1-5-21-3084690208-3888753220-1328190817-1115\Software\Albert Yale |
| Class Name: | <NO CLASS> |
| Last Write Time: | 8/16/2019 - 10:54 PM |
In this case, the date on the key was months ago, so didn't explain recent
problems on the user's PC and since Spybot - Search & Destroy didn't
locate anything else, the registry key may have been a remnant of something
removed many months ago.
[ More Info ]
[/os/windows/registry]
permanent link
Fri, Mar 25, 2016 9:45 pm
Creating a registry entry to run a program at login
If you wish to have a program run whenever a
user logs into the system, then you can add an entry to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
in the
Windows Registry, assuming you are logged into
the system as the user for which you wish to have the program run at logon at
the time you add the entry to the registry, so that
HKEY_CURRENT_USER (HKCU), which applies to the currently logged in user,
applies to that user's account.
One way you can add a new entry in the registry for a program to run when
the user logs in is to use the regedit program
that comes with the Windows operating system and which is normally found in the
C:\Windows directory.
[ More Info ]
[/os/windows/registry]
permanent link
Sun, Jan 24, 2016 9:45 pm
Using reg query to determine the last registry key accessed
You can determine the last
Windows Registry
key accessed in regedit by issuing a
reg query command from a
command prompt. E.g., suppose I ran regedit and viewed
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run and then
exited from regedit.

From a command line interface (CLI), i.e., a command prompt, I can issue
the command reg query HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Applets\Regedit /v LastKey, which will show me the last key
that was accessed while in regedit. If I reopen regedit, it will start with
that key selected, i.e., it will open from the key selected when I exited from
the program.
C:\>reg query HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Applets\Regedit /v LastKey
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Applets\Regedit
LastKey REG_SZ Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
C:\>Note: the command is querying a key in HKEY Current User (HKCU), so the
results apply to the account from which the command is run. If you run the
command from a different account on the system, you will get the LastKey
value for that account.
[/os/windows/registry]
permanent link
Fri, Jan 09, 2015 11:03 pm
Recovering information for the HKCU branch of the registry from a backup
Microsoft Windows stores information contained in the
HKEY_CURRENT_USER
branch of the registry, which is often abbreviated as
HKCU,
in the file
NTUSER.DAT. That file is stored in the user's
profile directory, which is usually
C:\Windows\Username,
where
Username is the account name. The location can be checked by
issuing the command
echo %USERPROFILE% from a command prompt
while logged into the account.
The file is a hidden and system file, so you would need to turn on
the display of hidden and system files in the Windows Explorer to see it,
but even then, if you are logged into the account for which you are trying
to access NTUSER.DAT it will be locked from
access. You can view the contents of the file for another account
or the contents of a backup copy of NTUSER.DAT
using the RegFileExport utility from NirSoft as explained in
Recovering information for the HKCU branch of the registry from a
backup.
[/os/windows/registry]
permanent link
Sun, Mar 22, 2009 10:52 am
Determining Device Driver Locations Used During Setup
To determine where Microsoft Windows will look for device driver
files during the Windows setup process, you need to examine
the registry key
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion.
[
More Info ]
[/os/windows/registry/devicepath]
permanent link
Sat, Apr 28, 2007 1:30 pm
Removing the Arrow from Windows Shortcuts
If you want to remove the arrow that appears on Windows shortcuts,
you can do so by using the following procedure.
- Click on Start.
- Select Run.
- Type regedit
- Click on Ok.
- Navigate to HKEY_CLASSES_ROOT\lnkfile.
- On the right side of the window, right-click on IsShortcut and
choose Delete.
Remember, you must be careful when editing the registry. Mistakes in
editing registry entries can cause significant problems.
As an alternative to the above method, you can use this
shortcut-arrow-removal.reg registry file,
which will delete the IsShortcut key from the registry. Download the
file (you can right-click on the link and choose "download", "save
link target as", or whatever your browser ues to initiate a download)
and then, once it is downloaded, double-click on the file on your system.
When prompted "Are you sure you
want to add the information in shortcut-arrow-removal.reg to the
registry?", select "Yes". That action will result in the key being
removed; the prompt about adding information is just the default
message that appears whenever you click on a
.reg file.
References:
-
Remove shortcut arrow from desktop icons
Free PC Tech Support -
Guides and FAQs
[/os/windows/registry]
permanent link
Mon, Sep 25, 2006 11:35 pm
Saving and Restoring Windows File Associations
To be able to restore Windows file associations, you need
to make a copy of two areas in the Windows registry:
HKEY_CURRENT_USER\Software\Classes and
HKEY_LOCAL_MACHINE\Software\Classes. Windows
stores information on what application should be used
to open a particular type of file, e.g. a file with
a .jpg association in those two areas. If you have made
a backup and some applications makes changes that you
would like to reverse, you can use your backup files
for those two branches of the registry to restore the
file associations to what they were previously.
[
More Info ]
[/os/windows/registry]
permanent link
Sat, Aug 13, 2005 1:06 pm
Registry P3P History Key
While troubleshooting an Internet access problem on a system, I noticed
a lot of entries for dubious sites in the registry under
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet
Settings\P3P\History\. There were a lot of keys for domain names
I know are associated with adware/spyware, such as 180solutions.com,
brilliantdigital.com, and exactsearchbar.com. There were a lot of
other dubious sounding domain names, such as casinoking.com, casinolasvegas.com,
and casinodelrio.com. When I checked the values of the keys, I noticed they
were all set as follows:
| Name | Type | Data |
| (Default) | REG_DWORD | 0x00000005 (5) |
At Microsoft's
WinInet Registry settings webpage, I found the following:
Per Site Cookie Handling
To handle site-by-site cookies, per-domain cookie decisions are stored under
the HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet
Settings\P3P\History\<domain> key. The domains are added to the
registry by WinInet when the user adds sites by using the Per Site Privacy
Actions dialog box.
The default value of the <domain> key stores the decision value. The
following table shows the possible values.
| Value | Description |
| REG_DWORD: 1 (COOKIE_STATE_ACCEPT) |
Accept all cookies from this site. |
| REG_DWORD: 5 (COOKIE_STATE_REJECT) |
Reject all cookies from this site. |
So a value of five in the key will block cookies from a site listed with
that value. The values were probably placed there by one of the antispyware
programs I previously installed on the system.
Internet Explorer 6 apparently checks the P3P keys to determine whether to
allow a site to place a cookie on the system as described in
IE6 and cookies. P3P stands for
Platform for Privacy Preferences.
References:
- WinInet Registry
Settings
-
IE6 and cookies
- P3P Public Overview
[/os/windows/registry]
permanent link

Privacy Policy
Contact




