A user reported that she saw a message on her system, which runs Windows 7 Professional, Friday morning December 19, 2014 indicating that malware had been detected on her system by Malwarebytes Anti-Malware
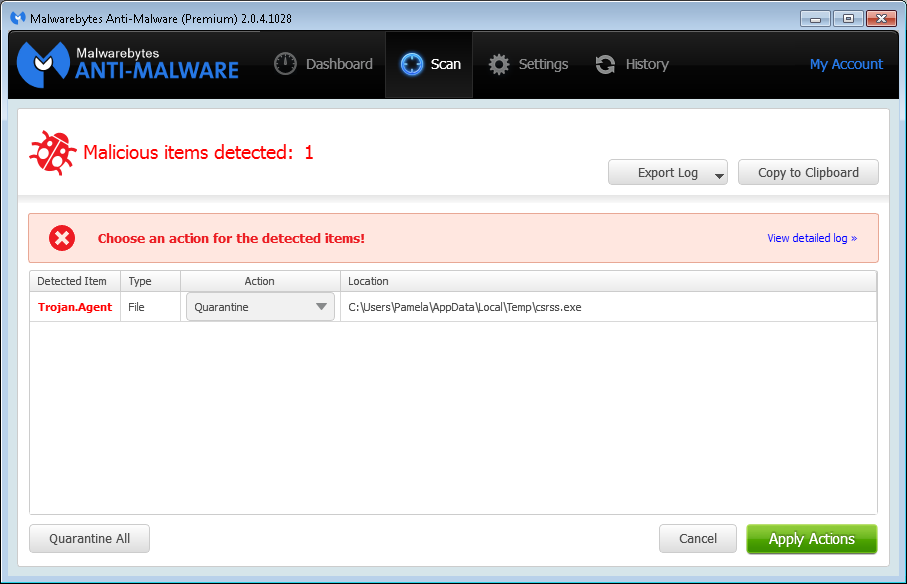
The file, which Malwarebytes identified as
Trojan.Agent, was csrss.exe was located in her
%TEMP% directory, i.e.,
C:\Users\Pamela\AppData\Local\Temp. There is a legitimate
Microsoft Windows file named csrss.exe, but that file is located in
C:\Windows\System32. The legitimate file on her system is
7,680 bytes in size and has a time stamp of 0/7/13/2009 08:39 PM. When
I checked the one Malwarebytes Anti-Malware was identifying as malware,
I saw it had the same size and time stamp.
C:\Windows>dir %TEMP%\csrss.exe
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Temp
07/13/2009 08:39 PM 7,680 csrss.exe
1 File(s) 7,680 bytes
0 Dir(s) 864,839,192,576 bytes freeI uploded the one Malwarebytes Anti-Malware flagged as malicious to
Google's VirusTotal site, which
analyzes uploaded files with many antivirus programs to determine if they
are safe or potentially dangerous. I had the site reanalyze the file, which
had been scanned previously. Zero of the fifty-four antivirus programs used
by the site to scan the file identified it as malware. The
SHA256 hash
listed for the file is
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a -
see the
report.
I ran a binary file comparison between the two files using the Microsoft
Windows fc utility. It found no differences between the two
copies of csrss.exe.
C:\Windows>fc /b %TEMP%\csrss.exe c:\windows\system32\csrss.exe Comparing files C:\USERS\PAMELA\APPDATA\LOCAL\TEMP\csrss.exe and C:\WINDOWS\SYSTEM32\CSRSS.EXE FC: no differences encountered
I had previously placed
md5deep, which can be downloaded from
md5deep and hashdeep, and its
associated utilities on the system. I used the 64-bit version, since
the system was running the 64-bit version of Microsoft Windows 7, of
sha256deep to check the SHA-256 hash for the version of the
csrss.exe file in C:\Windows\System32. It reported the same
SHA-256 hash as VirusTotal listed for the copy of the file I uploaded from
the users %TEMP% directory. I also checked the
MD5,
Tiger, and
Whirlpool
hashes for both files. For both files the MD5 hash was
60c2862b4bf0fd9f582ef344c2b1ec72 The Tiger hash function yieled a
hash of 42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b for both.
The Whirlpool hash was
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 for both files.
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>sha256deep64 %TEMP%\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 c:\windows\system32\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 %TEMP%\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 c:\windows\system32\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 %TEMP%\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 c:\windows\system32\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 %TEMP%\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 C:\Users\Pamela\AppData\Local\
Temp\csrss.exe
So I've no reason to suspect that the file in the %TEMP%
directory is any different than the one in the C:\Windows\Temp
directory. I thought that perhaps the only reason Malwarebytes
Anti-Malware flagged it to be quarantined is that it was an exe file in
the user's AppData\Local\Temp directory. It is possible that
I copied the file there previously when I was checking on various files
on the system when trying to eliminate a source of malware infection
on the system and that an update to Malwarebytes Anti-Malware now
has it mark any file in that directory as malware. I had Malwarebytes
Anti-Malware quarantine the file and then copied another legitimate
Microsoft Windows exe file, write.exe and also the
csrss.exe file from \C:\Windows\System32
into that directory just to see if Malwarebytes Anti-Malware would
flag them as malicious. It again detected csrss.exe as
malicious, but did not report the write.exe file I copied
into that directory from C:\Windows\system32 as malicious,
so it doesn't seem to be judging all .exe files in that folder as
potential threats, just certain ones.

