Malwarebytes Anti-Malware detection for csrss.exe
A user reported that she saw a message on her system, which runs Windows 7
Professional, Friday morning December 19, 2014 indicating that malware had
been detected on her system by
Malwarebytes Anti-Malware

.
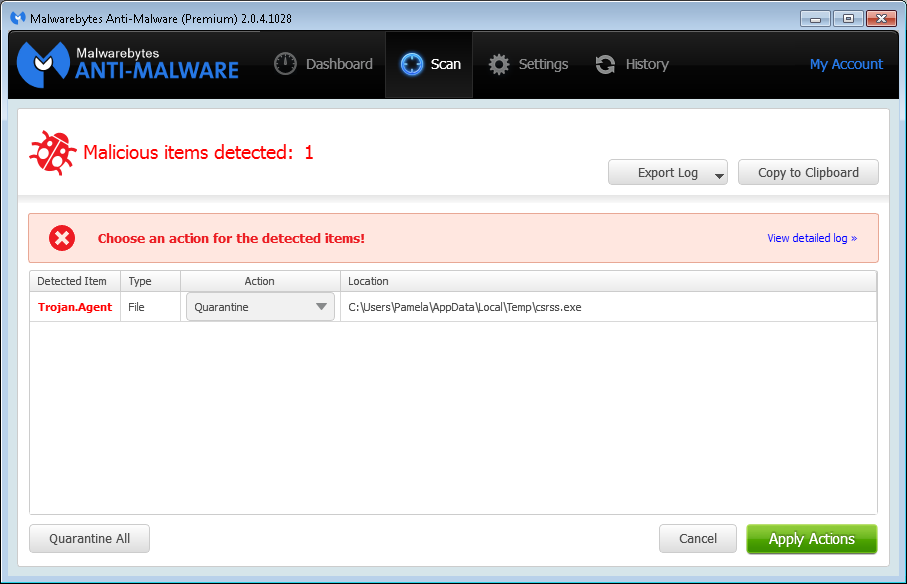
The file, which Malwarebytes identified as
Trojan.Agent, was csrss.exe was located in her
%TEMP% directory, i.e.,
C:\Users\Pamela\AppData\Local\Temp. There is a legitimate
Microsoft Windows file named csrss.exe, but that file is located in
C:\Windows\System32. The legitimate file on her system is
7,680 bytes in size and has a time stamp of 0/7/13/2009 08:39 PM. When
I checked the one Malwarebytes Anti-Malware was identifying as malware,
I saw it had the same size and time stamp.
C:\Windows>dir %TEMP%\csrss.exe
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Temp
07/13/2009 08:39 PM 7,680 csrss.exe
1 File(s) 7,680 bytes
0 Dir(s) 864,839,192,576 bytes freeI uploded the one Malwarebytes Anti-Malware flagged as malicious to
Google's VirusTotal site, which
analyzes uploaded files with many antivirus programs to determine if they
are safe or potentially dangerous. I had the site reanalyze the file, which
had been scanned previously. Zero of the fifty-four antivirus programs used
by the site to scan the file identified it as malware. The
SHA256 hash
listed for the file is
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a -
see the
report.
I ran a binary file comparison between the two files using the Microsoft
Windows fc utility. It found no differences between the two
copies of csrss.exe.
C:\Windows>fc /b %TEMP%\csrss.exe c:\windows\system32\csrss.exe
Comparing files C:\USERS\PAMELA\APPDATA\LOCAL\TEMP\csrss.exe and C:\WINDOWS\SYSTEM32\CSRSS.EXE
FC: no differences encountered
I had previously placed
md5deep, which can be downloaded from
md5deep and hashdeep, and its
associated utilities on the system. I used the 64-bit version, since
the system was running the 64-bit version of Microsoft Windows 7, of
sha256deep to check the SHA-256 hash for the version of the
csrss.exe file in C:\Windows\System32. It reported the same
SHA-256 hash as VirusTotal listed for the copy of the file I uploaded from
the users %TEMP% directory. I also checked the
MD5,
Tiger, and
Whirlpool
hashes for both files. For both files the MD5 hash was
60c2862b4bf0fd9f582ef344c2b1ec72 The Tiger hash function yieled a
hash of 42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b for both.
The Whirlpool hash was
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 for both files.
C:\Program Files\Utilities\File\md5deep>sha256deep64 c:\windows\system32\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>sha256deep64 %TEMP%\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 c:\windows\system32\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 %TEMP%\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 c:\windows\system32\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 %TEMP%\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 c:\windows\system32\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 %TEMP%\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 C:\Users\Pamela\AppData\Local\
Temp\csrss.exe
So I've no reason to suspect that the file in the %TEMP%
directory is any different than the one in the C:\Windows\Temp
directory. I thought that perhaps the only reason Malwarebytes
Anti-Malware flagged it to be quarantined is that it was an exe file in
the user's AppData\Local\Temp directory. It is possible that
I copied the file there previously when I was checking on various files
on the system when trying to eliminate a source of malware infection
on the system and that an update to Malwarebytes Anti-Malware now
has it mark any file in that directory as malware. I had Malwarebytes
Anti-Malware quarantine the file and then copied another legitimate
Microsoft Windows exe file, write.exe and also the
csrss.exe file from \C:\Windows\System32
into that directory just to see if Malwarebytes Anti-Malware would
flag them as malicious. It again detected csrss.exe as
malicious, but did not report the write.exe file I copied
into that directory from C:\Windows\system32 as malicious,
so it doesn't seem to be judging all .exe files in that folder as
potential threats, just certain ones.
[/security/antivirus/Malwarebytes]
permanent link
Seagate external USB drive part number 9SF2A4-500
I have a
Power Adapters page where
I list the power adapters that are needed for various devices. I started
the page years ago after repeated instances where I had to figure out what
power adapter went with what device when an adapter got disassociated from
a device and either lost or jumbled with other adapters. To make it easier
for me to immediately associate an adapter with a device, I listed the
model/part number for a device and the model/part number for its power
adapter. I also list, when I can find a source, a site where a suitable
replacement adapter can be purchased. Now, whenever I encounter a device,
I try to immediately enter the power adapter information for it on my
web page. But today, I found a couple of power adapters next to a couple of
devices that I had jumbled together. And when I checked my web page I found
that I hadn't entered the power adapter information for either device.
I was fairly certain that I could
associate the right adapter with each advice, assuming that since the adapters
were near the devices that they were indeed the ones that went with those
devices, but while double-checking
on the adapter for a Seagate USB external drive with part number
9SF2A4-500, I came across
Felix's Blog, a blog from another
person providing tech support, by Marcel "Felix" Giannelia of Terrace, BC,
Canada who provides
Disassembly instructions for Seagate 1 TB Expansion
External Drive (9SE2A4-571 or 9SF2A4-500).
I've copied his instructions to my own site
here,
so that I have a copy should the author's site, or even
just these instructions, disappear, since he states at
Welcome to Felix's little Knowledge Base
thing that "I've been even sloppier about copyright in the files
I've written myself. I intend the ones I wrote myself to be in the public
domain." According to his disassembly instructions, the drive inside the
Seagate External Expansion case is a Seagate Barracuda 7200.12 model
ST31000528AS

.
Checking other postings's to the author's site, I found
"Do NOT paraphrase when calling tech support", which links to
an email
he sent to a user regarding the user's paraphrasing an error message for
the Eudora email
client, a program I once used many years ago and which users
I supported once used.
I can certainly emphasize with his posting; many years ago when I was a sysadmin for
a Digital Equipment Corporation (DEC)
VMS system, a user
contacted me about a problem with one of her databases on the system. She
gave me the error message and, since DEC very nicely provided documentation
for the database software listing possible error messages and steps to take
to rectify the problem associated with a particular error message, I referred
to that documenation and found it listed an error message that was a very
close match to the one the user gave me. After spending a couple of hours
checking all of the possibilities listed for that error message, I contacted
the user and had her recreate the problem. When she then read me the exact
error message, I realized it was quite different than what she had paraphrased
from memory previously. Once I had the exact error message, it only took me
a few minutes to fix the problem, but I had wasted hours on the problem before
that because she hadn't written down the exact message, but gave me a
paraphrased version. One user takes snapshots of error messages on her
computer screen with her phone now and sends them to me; that's very helpful,
since I can see the window containing the error message and its exact
contents.
I also found his "Why cats save humans from house fires" amusing, though
the smoke alarm has almost never gone off in our house due to food
preparation. It did go off one time when I put the tea kettle on the stove
to heat water for tea and then went into another room to work on a
computer. I didn't hear the tea kettle whistling; when the smoke alarm
went off I went into the kitchen and found that all of the water in the
tea kettle had boiled off and there was a burning puddle of plastic next
to the tea kettle due to the plastic on the handle melting. Our cats
didn't like the blaring smoke alarms throughout the house.
In another posting by Felix, I found an adapter that will also be useful
to me, since it supports both IDE, aka PATA, drives as well as
SATA hard disk drives listed in his a "Product Plug!" posting
for a "Ultra USB 2.0 to IDE/SATA Cable for 2.5-Inch/ 3.5-Inch /
5.25-Inch Drive with Power Adapter", which he notes is a "a USB
to any-kind-of-hard-drive adapter. That is, it's got a USB plug on
one end, and all the kinds of hard drive connector mashed together
on the other end. I just ordered one, because this is going to
save me so much time disassembling USB enclosures". His link was to the ULT40112
on the TigerDirect.ca site, i.e., the Canadian site
for TigerDirect; it is available in the U.S. from
TigerDirect.com. I have devices that provide
USB connectivity for hard drives that aren't in an enclosure, but none that
support both IDE, aka PATA, and SATA drives.
Unfortunately, the plug on the Asian Power Devices WA-24E12 (output 12V 2A)
power adapter I found near the drive that I thought went with the drive
would not plug into the drive, even though according to information
I found elsewhere online it should have worked for that drive. Another
12V 2A adapter, model ADS-24F-12 1224GPCU, I tried from another Seagate
external USB disk drive enclosure did connect easily, though.
Seagate® Expansion™ External Data Sheet

[/hardware/storage/Seagate]
permanent link
Checking the warranty on a Segate drive
If you want to check whether a Seagate disk drive is still under warranty,
you can do so at either the
Warranty Validation or the
Customer Returns page. You can check the warranty for an internal
hard disk drive or an external USB drive.
You will need to complete fields on the form for the following information:
- Serial Number
- Product Number / Model Number
- Country
If the warranty is expired, you will see "Warranty is expired for the
entered Product/Serial". You won't see the date that the warranty expired on.
[/hardware/storage/Seagate]
permanent link
Viewing history of DNS server and IP Changes for a Domain
If you wish to view a history of
Domain Name System
(DNS) server changes for a domain name, you can do so through
the
WhoISrequest Domain History
Checker, which tracks nameserver changes since 2002 for all COM, NET, ORG,
INFO, BIZ and US domains.
E.g., if I put
sailormoonworld.com, which was registered in 1998, in the search field, I
can see a list of all of the DNS servers that translated the
fully
qualified domain name (FQDN) to an IP address since WhoISrequest began
tracking name server changes in 2002. The history information for that
particular domain shows that registration for the domain name lapsed in
2013 and the domain name was picked up by a
domain name squatter
then. The domain name squatter let the domain registration lapse in the
summer of 2014. I re-registered the domain name for the original owner, a
family member, in October.
You can also view such information through the
DNS History site, which notes
"Here at DNS History we have been crawling DNS records since 2009, our index
currently contains over 200 million domains and discovering over a billion DNS
records."
If I put sailormoonworld.com in the Doman Search field on that site,
though, it does not have any information on it, though it does have information
on moonpoint.com, though that information was last updated on 2010-08-11, so
that site's information does not appear to be as comprehensive nor as
up-to-date as the information provided through the WhoISRequest site.
You can also find past name server and registration information through
the who.is Search Domain DNS and Name Server
Information page. When you put a domain name in the search field,
and click on "Search DNS and Name Servers", you will see information
on the domain, such as name servers, SOA record, DNS records, including
the mail exchanger (MX) servers for the domain. If you click on the
History tab above that information, you will see past domain
name registrars and name servers associated with the domain.
If you wish to see prior IP addresses associated with a domain name,
you can use ViewDNSInfo IP
History. I noticed when I checked sailormoonworld.com with
its tool, though, that it is not showing a change made near the end of October
for that domain. The last change it shows was for 2014-07-05. The site also
has a lot of other tools, e.g.
Google Pagerank Checker, etc.
[/network/dns]
permanent link



