|
| ←2026→| Months |
|---|
| Jan |
Feb | Mar |
| Apr |
May |
Jun |
| Jul |
Aug |
Sep |
| Oct |
Nov |
Dec |
|
Fri, Aug 25, 2017 11:11 pm
Wireshark - bandwidth usage and bytes by protocol
The
free and open source
packet analysis
tool Wireshark provides
many capabilities for analyzing network traffic. Among its capabilities is
the capability to provide statistical information regarding captured network
traffic. Looking at a pcap
file with Wireshark for traffic captured during a data flow test, I saw what
seemed to be a fair amount of
Simple Network Management Protocol (SNMP) and
Secure Shell (SSH)
traffic with systems on an external network. I wanted to determine the
actual percentage that traffic represented within the overall traffic during
the test period. Fortunately, that is easy to do within Wireshark. One way to
view statistics on bandwidth utilization by protocol while viewing
captured data is by clicking on Statistics then selecting Protocol
Hierarchy. Note: you may need to wait a little while for the statistics
to be displayed if the amount of data to be processed is large.
[ More
Info ]
[/network/tools/sniffing/wireshark]
permanent link
Fri, May 05, 2017 10:46 pm
Using MTR for network diagnostics
Traceroute
and ping are commonly provided with operating systems as tools
to diagnose problems in network connectivity between systems. Another very
useful took, which combines the functionality of both those other tools is
My traceroute, which was originally know as Matt's traceroute,
aka
MTR. The software is available for
Linux systems
and also for Microsoft Windows sytems as
WinMTR.
The software can be installed via the
package
management system for some Linux distributions. E.g., it can be installed on a
CentOS Linux
system with yum using the command yum install mtr. You
can check on whether it is installed on a CentOS system with the command
rpm -qi mtr or you can just issue the command which mtr
on a Linux system.
[ More Info ]
[/network/tools]
permanent link
Wed, Jul 22, 2015 6:20 pm
Bopup Scanner
If you need to determine which IP address on your
LAN are in use and the
media access control (MAC) address associated with them,
Bopup Scanner from
B Labs is a handy free utility that
will quickly scan a range of IP addresses and provide the MAC addresses
for the systems within the specified IP address range. It can also tell
you if any of the systems are functioning as web servers listening on TCP
ports 80 or 8080.
[ More Info ]
[/network/tools/scanning/bopupscanner]
permanent link
Sat, Apr 25, 2015 10:41 pm
Using netcat to simulate a web server
If you have a Mac OS X system or a Linux system, you can listen for
connections from web browsers on the system by utilizing the
netcat utility,
which you can run by issuing the
nc command from a Terminal
window, i.e., a shell prompt. The Terminal application is found in
Applications/Utilities on a Mac OS X system.
You won't get the functionality provided by installing web server
software, such as the
Apache HTTP
Server, but you can use the command for testing or to provide
one page that is visible to thers from their browsers. As an example,
the command below instructs netcat to listen on port 8080 for
connections and display the file index.html when the system is
accessed on that port. If you pick a port above 1024, such as 8080
rather than 80, you don't need root (admin) privileges in order to
have the system listen on the port, but, if you don't use the default port
of 80, you need to specify the port used in the URL, e.g.,
http://www.example.com:80, when you try to connect with a browser.
nc -kl 8080 < index.html
In the above example, two options for netcat, -l
and -k are combined into -kl. Their meaning
and other options can be displayed by issuing the command nc -h.
-k Forces nc to stay listening for another connection after its cur-
rent connection is completed. It is an error to use this option
without the -l option.
-l Used to specify that nc should listen for an incoming connection
rather than initiate a connection to a remote host. It is an
error to use this option in conjunction with the -p, -s, or -z
options. Additionally, any timeouts specified with the -w option
are ignored.If you are running the command on an OS X system, you may see a
window appear asking whether you wish to allow netcat to receive
incoming connections.
To access the web page from a browser on the system on which you run the
command, or from another system, you will need to specify an appropriate IP
address for the system, which you can get
using the ifconfig -a command, or a fully
qualified domain name for it. If the system is accessible from
the Internet, you can determine what IP address others need to use by
visiting WhatIsMyIP.
E.g., suppose the IP address for the system is 192.168.1.5. That IP
address is
private IP address space, so wouldn't be accessible from the Internet, but
you would substitute whatever IP address others would see for the system, if
you had a system that was accessible from the Internet, e.g., whatever address
WhatIsMyIP would show if you visited
that website using a browser on the system. If you put in
http://192.168.1.5:8080, or substituting whatever port number
you picked instead of 8080, in a web browser, then you should
see the contents of index.html displayed.
If you only need access from a browser on the system itself, then you
can just put in the system's
localhost, aka, local loopback, address, which is 127.0.0.1. E.g., if you
had netcat listen for connections on ort 8080, you could use
http://127.0.0.1:8080.
You can use whatever file name you like, e.g., test123.html will work equally
as well. If you specified that file name, using http://192.168.1.5:8080
would display the contents of that file without it being specified
in the address bar of the browser.
Some browsers may expect the normal status returned by a web server when
a page is accessed, so you may want to include the following line at the top
of index.html or whatever file you specify. Follow the line with a blank line.
HTTP/1.1 200 OK
E.g., below is a sample index.html file that could be used.
HTTP/1.1 200 OK
<HTML>
<HEAD>
<TITLE>Testing</TITLE>
</HEAD>
<BODY>
<H1 align="Center">Test</H1>
<a href="http://support.moonpoint.com">Moonpoint Support</a><br>
</BODY>
</HTML>
If you don't include the "HTTP/1.1 200 OK" line followed by a blank line,
you may see a message such as "The connection was reset" or some other error
message, so I would recommend including it.
Until you hit Control-C at the command prompt window, netcat
will continue to listen for connections and you will see the HTTP commands
issued by browsers. E.g., I might see the following when
http://192.168.1.5:8080 is placed in the address bar of
Firefox.
GET / HTTP/1.1
Host: 192.168.1.5:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:31.0) Gecko/20100101 Firefox/31.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
GET /favicon.ico HTTP/1.1
Host: 192.168.1.5:8080
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.8; rv:31.0) Gecko/20100101 Firefox/31.0
Accept: image/png,image/*;q=0.8,*/*;q=0.5
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: keep-alive
Note: if the system on which you are running the netcat command is running
host-based firewall software, you may need to configure that software to
allow incoming connections on the port you specified in the netcat command
in order for connectivity to work. E.g., see
Opening a firewall port for Firewalld from the command line for
the command to use on a CentOS Linux system running FirewallD.
References:
-
One command line web server on port 80 using nc (netcat)
Date: August 31, 2011
commandlinefu.com
[/network/tools/netcat]
permanent link
Sat, Jan 05, 2013 9:10 pm
Creating a Filter to Display HTTP Cookies
To create a filter to display
HTTP cookies in
Wireshark, take the
following steps:
-
Open Wireshark and click on Analyze.
-
Select Display Filters.
-
Click on New.
-
For filter name, type
HTTP cookie or whatever name you would
like and for filter string type http.cookie.
-
Click on OK. You should then see only the packets containing
HTTP cookies displayed.
Note: written for Wireshark 1.8.4, but should apply to other versions
as well.
References:
-
cookie and query strings
Wireshark Q&A
[/network/tools/sniffing/wireshark]
permanent link
Sat, Jan 05, 2013 8:59 pm
Installing Wireshark 1.8.4 and WinPcap 4.1.2 on a Windows 8 System
I installed Wireshark 1.8.4. When I started it, I was
informed that I hadn't specified an interface on which to perform a
capture. When I tried specifying an interface, I was informed there were
no interfaces on which a capture could be done. I saw "(Unable to load
WinPcap (wpcap.dll); you will not be able to capture packets."
I needed to install WinPcap in order
to utilize Wireshark, so I downloaded
WinPcap 4.1.2. When I ran
the installation program, a Program Compatibility Assistant
window opened stating "This program has compatibility issues." There
were two options: (1) Get help online and (2) Run the program without
getting help. I chose the latter. That resulted in a WinPcap 4.1.2
Setup window opening with the message "This version of Windows is
not supported by WinPcap 4.1.2. The installation will be aborted."
To resolve the problem, the following steps can be taken.
- Right-click on the installation file,
WinPcap_4_1_2.exe and select Properties.
- Click on the Compatibility tab.
-
Check the box next to "Run this program in compatibility mode for" and select
"Windows 7".
- Check the box for "Run this program as an administrator"
under Privilege level.
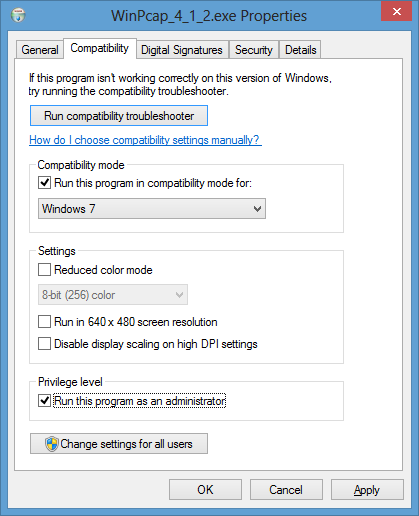
- Click on the OK button.
-
Run the installation program again and allow it to make changes to the system.
-
When the Program Compatibility Assistant window opens informing
you that "This program has compatibility issues", select "Run the program
without getting help". The WinPcap 4.1.2 Setup window should
then open allowing you to proceed with the installation.
References:
-
[Winpcap-users] Windows 8
By Andrew Stewart
Date: July 6, 2012
WinPcap
-
Installing WIRESHARK/WinPCap on Windows 8 RTM
By Kaushal Kumar
Panday
Date: August 7, 2012
Unleashed
[/network/tools/sniffing/wireshark]
permanent link
Sat, Apr 04, 2009 3:32 pm
Socat and Ncat
I needed to determine whether
User
Datagram Protocol (UDP) datagrams were being transmitted through a firewall
on specific ports. I had a Windows system behind the firewall and a
Linux system on the outside of the firewall. I intended to use
Ncat on both systems. I installed
Nmap on the Windows system, since it provides
the Ncat utility. But when I tried to install Ncat on the Linux system,
I
encountered problems, so I installed
socat, instead, since it
provides similar capabilities.
Since I needed to test whether UDP datagrams would reach the Windows
system on port 27900, I issued the command ncat -u 27900 -l
to have ncat listen (the "-l" argument) on UDP port 27900 (the -u 27900
argument). I then issued the command socat - udp-sendto:192.168.0.3:27900
on the Linux system. The - udp-sendto:192.168.0.3
allowed me to send data from the system socat was running on to
the the destination address 192.168.0.3. I was then able to type text,
e.g. the words "a test" on the Linux system. I saw them appear on the Windows
system indicating the firewall rule was functioning as needed.
Linux Sending System
$ socat - udp-sendto:192.168.2.3:27900
a test
Windows Listening System
C:\Program Files\Network\Nmap>ncat -u 27900 -l
a test
I then terminated the socat program on the Linux system with
Ctrl-D and the ncat program on the Windows system with
Ctrl-C.
References:
-
Nmap
-
socat
dest-unreach.org
-
socat - Multipurpose relay (SOcket CAT)
Linux Man Pages Manual
Documentation for Linux / Solaris / UNIX / BSD
[/network/tools/scanning/socat]
permanent link
Sat, Apr 04, 2009 3:01 pm
Ncat and Glibc
I wanted to install
Ncat on a CentOS
Linux system to test firewall rules. I intended to run Ncat on a Windows
system behind the firewall to listen for UDP connections while using
Ncat on the Linux system outside the firewall to send data to the Windows
system through the firewall. I downloaded the Windows version of
Nmap, which also provides the command line
Ncat tool. I had no problems installing and running it on the Windows system.
However, when I downloaded the Linux RPM for Ncat from the Nmap site and
tried to install it, I encountered problems.
# rpm --install ncat-4.85BETA7-1.x86_64.rpm
error: Failed dependencies:
libc.so.6(GLIBC_2.7)(64bit) is needed by ncat-4.85BETA7-1.x86_64Yet, when I checked the system for the presence of libc.so.6,
I found it was present.
# locate libc.so
/lib/libc.so.6
/lib/i686/nosegneg/libc.so.6
/lib64/libc.so.6
/usr/lib/libc.so
/usr/lib/i386-redhat-linux4E/lib/libc.so
/usr/lib/x86_64-redhat-linux4E/lib64/libc.so
/usr/lib64/libc.so
I checked to see what package provided the file.
# rpm -qf /lib/libc.so.6
glibc-2.5-24
# rpm -qf /lib64/libc.so.6
glibc-2.5-24
When I checked the package, there appeared to be two glibc-2.5-24 packages
present, since when I ran the command rpm -qi glibc-2.5-24,
I saw the package listed twice, but with different sizes
# rpm -qi glibc-2.5-24
Name : glibc Relocations: (not relocatable)
Version : 2.5 Vendor: CentOS
Release : 24 Build Date: Fri 23 May 2008 10:40:42 PM EDT
Install Date: Tue 29 Jul 2008 10:03:15 AM EDT Build Host: builder15.centos.org
Group : System Environment/Libraries Source RPM: glibc-2.5-24.src.rpm
Size : 11590290 License: LGPL
Signature : DSA/SHA1, Sun 15 Jun 2008 09:51:20 AM EDT, Key ID a8a447dce8562897
Summary : The GNU libc libraries.
Description :
The glibc package contains standard libraries which are used by
multiple programs on the system. In order to save disk space and
memory, as well as to make upgrading easier, common system code is
kept in one place and shared between programs. This particular package
contains the most important sets of shared libraries: the standard C
library and the standard math library. Without these two libraries, a
Linux system will not function.
Name : glibc Relocations: (not relocatable)
Version : 2.5 Vendor: CentOS
Release : 24 Build Date: Fri 23 May 2008 11:12:28 PM EDT
Install Date: Tue 29 Jul 2008 10:03:26 AM EDT Build Host: builder15.centos.org
Group : System Environment/Libraries Source RPM: glibc-2.5-24.src.rpm
Size : 12579066 License: LGPL
Signature : DSA/SHA1, Sun 15 Jun 2008 09:51:20 AM EDT, Key ID a8a447dce8562897
Summary : The GNU libc libraries.
Description :
The glibc package contains standard libraries which are used by
multiple programs on the system. In order to save disk space and
memory, as well as to make upgrading easier, common system code is
kept in one place and shared between programs. This particular package
contains the most important sets of shared libraries: the standard C
library and the standard math library. Without these two libraries, a
Linux system will not function.
I tried updating the package.
# yum upgrade glibc
Loading "priorities" plugin
Loading "fastestmirror" plugin
Loading mirror speeds from cached hostfile
* rpmforge: fr2.rpmfind.net
* base: mirror.anl.gov
* updates: ftp.lug.udel.edu
* addons: centos.aol.com
* extras: ftp.lug.udel.edu
338 packages excluded due to repository priority protections
Setting up Upgrade Process
Resolving Dependencies
--> Running transaction check
---> Package glibc.i686 0:2.5-34 set to be updated
--> Processing Dependency: glibc-common = 2.5-34 for package: glibc
--> Processing Dependency: glibc = 2.5-24 for package: glibc-devel
--> Processing Dependency: glibc = 2.5-24 for package: glibc-devel
--> Processing Dependency: glibc = 2.5-24 for package: glibc-headers
---> Package glibc.x86_64 0:2.5-34 set to be updated
--> Running transaction check
---> Package glibc-headers.x86_64 0:2.5-34 set to be updated
---> Package glibc-common.x86_64 0:2.5-34 set to be updated
---> Package glibc-devel.x86_64 0:2.5-34 set to be updated
--> Finished Dependency Resolution
Dependencies Resolved
=============================================================================
Package Arch Version Repository Size
=============================================================================
Updating:
glibc x86_64 2.5-34 base 4.7 M
glibc i686 2.5-34 base 5.2 M
glibc-common x86_64 2.5-34 base 16 M
Updating for dependencies:
glibc-devel x86_64 2.5-34 base 2.4 M
glibc-headers x86_64 2.5-34 base 589 k
Transaction Summary
=============================================================================
Install 0 Package(s)
Update 5 Package(s)
Remove 0 Package(s)
Total download size: 29 M
Is this ok [y/N]: y
Downloading Packages:
(1/5): glibc-devel-2.5-34 100% |=========================| 2.4 MB 00:04
(2/5): glibc-common-2.5-3 100% |=========================| 16 MB 00:32
(3/5): glibc-headers-2.5- 100% |=========================| 589 kB 00:01
(4/5): glibc-2.5-34.i686. 100% |=========================| 5.2 MB 00:09
(5/5): glibc-2.5-34.x86_6 100% |=========================| 4.7 MB 00:08
Running rpm_check_debug
ERROR with rpm_check_debug vs depsolve:
Package glibc-devel needs glibc = 2.5-24, this is not available.
Package glibc-devel needs glibc = 2.5-24, this is not available.
Package glibc-devel needs glibc-headers = 2.5-24, this is not available.
Package glibc-devel needs glibc-headers = 2.5-24, this is not available.
Complete!
When I ran rpm -qi glib afterwards, I saw version 2.5-24 still
listed. I tried yum update glibc as well, though I didn't
expect the results to be different; they weren't. I then checked for
glibc files in the yum cache. There appeared to be both 32-bit and 64-bit
versions present.
# ls /var/cache/yum/base/packages/glibc*
/var/cache/yum/base/packages/glibc-2.5-24.i686.rpm
/var/cache/yum/base/packages/glibc-2.5-24.x86_64.rpm
/var/cache/yum/base/packages/glibc-2.5-34.i686.rpm
/var/cache/yum/base/packages/glibc-2.5-34.x86_64.rpm
/var/cache/yum/base/packages/glibc-common-2.5-24.x86_64.rpm
/var/cache/yum/base/packages/glibc-common-2.5-34.x86_64.rpm
/var/cache/yum/base/packages/glibc-devel-2.5-24.i386.rpm
/var/cache/yum/base/packages/glibc-devel-2.5-24.x86_64.rpm
/var/cache/yum/base/packages/glibc-devel-2.5-34.x86_64.rpm
/var/cache/yum/base/packages/glibc-headers-2.5-24.x86_64.rpm
/var/cache/yum/base/packages/glibc-headers-2.5-34.x86_64.rpm
I removed all of them from the yum cache with rm -f
/var/cache/yum/base/packages/glibc*. When I tried
yum update glibc again, however, the results
were the same.
I checked the arch of the installed glibc packages.
# rpm -qa --qf '%{name}-%{version}-%{release}.%{arch}\n'|grep glibc
glibc-devel-2.5-24.x86_64
compat-glibc-headers-2.3.4-2.26.x86_64
compat-glibc-2.3.4-2.26.i386
glibc-devel-2.5-24.i386
compat-glibc-2.3.4-2.26.x86_64
glibc-2.5-24.x86_64
glibc-2.5-24.i686
glibc-common-2.5-24.x86_64
glibc-headers-2.5-24.x86_64I did have 32-bit and 64-bit versions installed. I decided to try
listing all of the glibc packages for the yum update command.
That worked much better.
# yum update glibc glibc-common glibc-devel glibc-headers
Loading "priorities" plugin
Loading "fastestmirror" plugin
Loading mirror speeds from cached hostfile
* rpmforge: fr2.rpmfind.net
* base: mirrors.rit.edu
* updates: ftp.lug.udel.edu
* addons: ftp.lug.udel.edu
* extras: ftp.lug.udel.edu
338 packages excluded due to repository priority protections
Setting up Update Process
Resolving Dependencies
--> Running transaction check
---> Package glibc.x86_64 0:2.5-34 set to be updated
---> Package glibc-headers.x86_64 0:2.5-34 set to be updated
---> Package glibc-devel.i386 0:2.5-34 set to be updated
---> Package glibc-common.x86_64 0:2.5-34 set to be updated
---> Package glibc-devel.x86_64 0:2.5-34 set to be updated
---> Package glibc.i686 0:2.5-34 set to be updated
--> Finished Dependency Resolution
Dependencies Resolved
=============================================================================
Package Arch Version Repository Size
=============================================================================
Updating:
glibc x86_64 2.5-34 base 4.7 M
glibc i686 2.5-34 base 5.2 M
glibc-common x86_64 2.5-34 base 16 M
glibc-devel i386 2.5-34 base 2.0 M
glibc-devel x86_64 2.5-34 base 2.4 M
glibc-headers x86_64 2.5-34 base 589 k
Transaction Summary
=============================================================================
Install 0 Package(s)
Update 6 Package(s)
Remove 0 Package(s)
Total download size: 31 M
Is this ok [y/N]: y
Downloading Packages:
(1/1): glibc-devel-2.5-34 100% |=========================| 2.0 MB 00:03
Running rpm_check_debug
Running Transaction Test
Finished Transaction Test
Transaction Test Succeeded
Running Transaction
Updating : glibc-common ####################### [ 1/12]
Updating : glibc ####################### [ 2/12]
Updating : glibc ####################### [ 3/12]
warning: /etc/ld.so.conf created as /etc/ld.so.conf.rpmnew
warning: /etc/localtime created as /etc/localtime.rpmnew
warning: /etc/nsswitch.conf created as /etc/nsswitch.conf.rpmnew
Updating : glibc-headers ####################### [ 4/12]
Updating : glibc-devel ####################### [ 5/12]
Updating : glibc-devel ####################### [ 6/12]
Cleanup : glibc ####################### [ 7/12]
Cleanup : glibc-headers ####################### [ 8/12]
Cleanup : glibc-devel ####################### [ 9/12]
Cleanup : glibc-common ####################### [10/12]
Cleanup : glibc-devel ####################### [11/12]
Cleanup : glibc ####################### [12/12]
Updated: glibc.x86_64 0:2.5-34 glibc.i686 0:2.5-34 glibc-common.x86_64 0:2.5-34 glibc-devel.i386 0:2.5-34 glibc-devel.x86_64 0:2.5-34 glibc-headers.x86_64 0:2.5-34
Complete!
I then checked the architecture for the installed packages again:
# rpm -qa --qf '%{name}-%{version}-%{release}.%{arch}\n'|grep glibc
glibc-devel-2.5-34.i386
glibc-2.5-34.x86_64
compat-glibc-headers-2.3.4-2.26.x86_64
compat-glibc-2.3.4-2.26.i386
glibc-headers-2.5-34.x86_64
glibc-common-2.5-34.x86_64
compat-glibc-2.3.4-2.26.x86_64
glibc-devel-2.5-34.x86_64
glibc-2.5-34.i686But when I tried to install ncat again, I got the same error as before.
# rpm --install ncat-4.85BETA7-1.x86_64.rpm
error: Failed dependencies:
libc.so.6(GLIBC_2.7)(64bit) is needed by ncat-4.85BETA7-1.x86_64When I checked on what was required for the ncat package,
I saw the following:
# rpm --requires -qp ncat-4.85BETA7-1.x86_64.rpm
libc.so.6()(64bit)
libc.so.6(GLIBC_2.2.5)(64bit)
libc.so.6(GLIBC_2.3)(64bit)
libc.so.6(GLIBC_2.3.4)(64bit)
libc.so.6(GLIBC_2.4)(64bit)
libc.so.6(GLIBC_2.7)(64bit)
rpmlib(CompressedFileNames) <= 3.0.4-1
rpmlib(PayloadFilesHavePrefix) <= 4.0-1
rtld(GNU_HASH)
I then tried installing the 32-bit version of ncat, but that
attempt failed as well.
# rpm --install ncat-4.85BETA7-1.i386.rpm
error: Failed dependencies:
libc.so.6(GLIBC_2.7) is needed by ncat-4.85BETA7-1.i386Since I had already expended far more time than I anticipated in trying
to install netcat, I decided to try an alternative program with
similar capabilities,
socat, instead. I didn't have any problems installing it.
# yum install socat
Loading "priorities" plugin
Loading "fastestmirror" plugin
Loading mirror speeds from cached hostfile
* rpmforge: fr2.rpmfind.net
* base: mirrors.rit.edu
* updates: ftp.lug.udel.edu
* addons: centos.aol.com
* extras: ftp.lug.udel.edu
338 packages excluded due to repository priority protections
Setting up Install Process
Parsing package install arguments
Resolving Dependencies
--> Running transaction check
---> Package socat.x86_64 0:1.7.1.0-1.el5.rf set to be updated
--> Finished Dependency Resolution
Dependencies Resolved
=============================================================================
Package Arch Version Repository Size
=============================================================================
Installing:
socat x86_64 1.7.1.0-1.el5.rf rpmforge 398 k
Transaction Summary
=============================================================================
Install 1 Package(s)
Update 0 Package(s)
Remove 0 Package(s)
Total download size: 398 k
Is this ok [y/N]: y
Downloading Packages:
(1/1): socat-1.7.1.0-1.el 100% |=========================| 398 kB 00:01
Running rpm_check_debug
Running Transaction Test
Finished Transaction Test
Transaction Test Succeeded
Running Transaction
Installing: socat ######################### [1/1]
Installed: socat.x86_64 0:1.7.1.0-1.el5.rf
Complete!
References:
-
Nmap
-
Ncat
MP: Weblog
-
Re: [rhelv5-list] Updating RHEL5.2 causes yum to loop infinitely...
The Mail Archive
-
Socat
Top 100 Nework Security Tools
-
socat - Multipurpose relay
dest-unreach.org
[/network/tools/scanning/nmap]
permanent link
Tue, Aug 05, 2008 9:58 pm
Installing Wireshark
I wanted to install Ethereal on a CentOS Linux system to sniff network traffic
to try to resolve a problem for a website. I have
tcpdump on the system,
but I wanted to have a
GUI
tool to make analyzing the packets a little easier for me.
I ran yum install ethereal, which installed wireshark
and its dependency, libsmi. Wireshark was installed, because
development of ethereal has stopped and the core development team is now
developing wireshark.
The FAQ for
wireshark offers the following explanation of the name change.
In May of 2006, Gerald Combs (the original author of Ethereal) went
to work for CACE Technologies (best known for WinPcap). Unfortunately,
he had to leave the Ethereal trademarks behind.
This left the project in an awkward position. The only reasonable way to
ensure the continued success of the project was to change the name. This
is how Wireshark was born.
Wireshark is almost (but not quite) a fork. Normally a "fork" of an
open source project results in two names, web sites, development teams,
support infrastructures, etc. This is the case with Wireshark except for
one notable exception -- every member of the core development team is now
working on Wireshark. There has been no active development on Ethereal
since the name change. Several parts of the Ethereal web site (such as the
mailing lists, source code repository, and build farm) have gone offline.
After the installation completed, I tried running wireshark by issuing
the command wireshark.
# wireshark
bash: wireshark: command not found
I then discovered that installing the wireshark
RPM only installs
a command line program, tshark. The program was installed in
/usr/sbin/tshark. You can obtain help on
tshark using man tshark or tshark -h.
There is also documentation installed in /usr/share/wireshark/help.
I had to install wireshark-gnome to get the GUI version, which
I did with yum -y install wireshark-gnome. I could then start
the GUI version from a shell prompt with wireshark or start it
by clicking on Applications, Internet, and then
Wireshark Network Analyzer.
Since I wanted to capture only HTTP
traffic, I typed HTTP in the Filter field and
then clicked on the Apply button. I then clicked on Capture,
Interfaces, and clicked on the Start button next to the
eth0 interface to start capturing all HTTP traffic.
[/network/tools/sniffing/wireshark]
permanent link
Sat, Feb 23, 2008 2:21 pm
Bopup Scanner
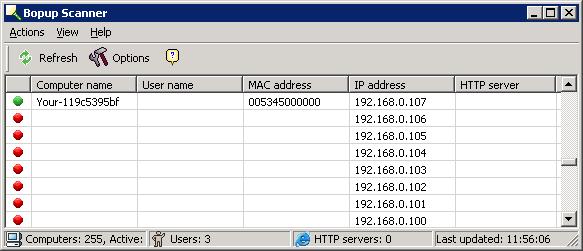
Bopup Scanner is a
freeware network scanner that displays active computers with user names
logged into the computers (NetBIOS), MAC and IP addresses. Bopup Scanner also
recognizes and shows HTTP (Web) servers running on remote computers (TCP ports
80, 8080), if you select the option to have it scan for webservers, quickly
detects online computers, and allows you to browse shared resources of a remote
computer. You can save the results of a scan to a text file.
Bopup Scanner will perform a NetBIOS scan of a network, which will
show Windows systems on the network. The program first tries to
ping an address it is scanning. So, if you were watching its
scan with a sniffer, you would see an
ARP request
for the IP address. If there is a reply to the ARP request, an
ICMP echo
request is sent to the IP address. If an echo reply is received,
Bopup Scanner will then check for a response from the scanned IP address on
UDP port 137.
Port 137 is associated with the NetBIOS Name Service commonly used
on systems running the Microsoft Windows operating system. The
NetBIOS Name Service is typically how Windows computers find out information
concerning the networking features offered by a computer, such as system name,
file shares, etc.
Because it is only scanning for responses to NetBIOS Name Service requests,
Bopup Scanner will show a red circle for IP addresses where it received no
response to a NetBIOS Name Service query, even though there may be a system
at that address. E.g. there may be a Linux system, networked copier, router,
etc. at the address.
Regarding installation of the software, there is no installation procedure for
the program. You simply run scanner.exe. When you first run it,
it will create the following registry entries:
Keys added: 5
-------------
HKEY_CURRENT_USER\Software\B Labs
HKEY_CURRENT_USER\Software\B Labs\Bopup Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner\Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner\Scanner\Settings
After starting the program, click on the Refresh button with
the green arrows next to it on the toolbar menu to begin a scan of the
subnet the system is on.
If you wish to check on whether a webserver is running on any of the
scanned IP addresses, click
on Options and check "Scan for HTTP servers (80, 8080 ports)".
You can save the results to a text file by clicking on Actions
and selecting Save list.
The developer, B-Labs Software,
also offers other
software that can be used for secure instant messaging.
Download Bopup Scanner
Developer Website
MoonPoint
Support (may not be the most current version)
[/network/tools/scanning/bopupscanner]
permanent link

Privacy Policy
Contact





