←March→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| 1 |
2 |
3 |
4 |
5 |
6 |
7 |
| 8 |
9 |
10 |
11 |
12 |
13 |
14 |
| 15 |
16 |
17 |
18 |
19 |
20 |
21 |
| 22 |
23 |
24 |
25 |
26 |
27 |
28 |
| 29 |
30 |
31 |
|
|
|
|
|
|
Wed, Feb 03, 2016 11:21 pm
eBay JavaScript block does not block all JavaScript
A number of sites that report on technology/computing issues carried reports
today regarding the possibility of malware being distributed via eBay custom
listings. E.g.,
TechWeek Europe UK
has the article
eBay 'Won't Fix' JavaScript Flaw That Exposes Users To Malware, Phishing
and
Ars Technica has the article
eBay has no plans to fix “severe” bug that allows malware
distribution. The articles state that eBay normally blocks sellers from
using
JavaScript code in
listings, but that malefactors can circument eBay's block by building their
JavaScript code with non-
alphanumeric characters, specifically the six characters . (,),[,],! and +.
According to the TechEurope UK article:
Security software firm
CheckPoint says eBay usually filters out scripts and iFrames from item
descriptions or online stores, but only strips alphanumeric characters
from these HTML tags.
CheckPoint claims that by using those non-alphanumeric characters,
malefactors could pull code from a remote server that would allow them to
trick an unsuspecting eBay user visiting a eBay store listing where the
nefarious JavaScript is posted into agreeing to install software that the
user may incorrectly assume is being provided by eBay.
CheckPoint stated it informed eBay of the potential issue on December 15,
but on January 16 was informed that eBay would not be providing a fix for
the issue because active content is allowed on eBay's website.
eBay's
HTML and JavaScript Policy page has the following guidelines on what
sellers aren't allowed to do on their listing pages:
You can't use HTML or JavaScript that:
-
Calls remote scripts and pages automatically, such as JavaScript
"includes" or "iframes."
-
Changes registry entries or otherwise writes to another person's computer
hard drive.
-
Creates automatic pop-ups except for links that open in a new window
when clicked on.
-
Is used to drop or read a cookie on any eBay page.
-
Loads any binary program on another person's computer automatically,
except for Flash content.
-
Launches a song or video when a listing is opened.
-
Overwrites any area in the listing outside of the item description area.
-
Manipulates areas outside the listing description, including changing
fonts, colors, and backgrounds in areas such as eBay headers and footers.
-
Posts to scripts on eBay automatically.
-
Redirects the user from eBay to another web page, such as using the
"replace" script.
I.e., the above guidelines do not seem to preclude the use of any
JavaScript on a listing page. And there are sites that provide scripts
to be used in eBay listings, e.g.,
Script Snips at Auction Repair
.
[/security/malware]
permanent link
Sun, Dec 21, 2014 5:38 pm
CoolYou
A friend was complaining that his laptop, which runs Microsoft Windows 7 Home
Premium, was very slow, so he was considering purchasing another laptop.
I suggested he download and install
Malwarebytes Anti-Malware

and scan the system with that software. One of the
items it detected was CoolYou
(
image),
which it classified as
Trojan.Dropper.
[ More Info ]
[/security/malware]
permanent link
Sun, Dec 07, 2014 10:45 pm
Scan of Windows system with Malwarebytes Anti-Malware on 2014-12-07
When I scanned a Windows 7 Professional system with Malwarebytes Anti-Malware
it reported a file associated with
PUP.Optional.TorchMedia, which I had it
remove.
[ More Info ]
[/security/malware]
permanent link
Sat, Nov 22, 2014 10:00 pm
Items detected by a ClamWin Scan on 2014-11-22
In continuance of an effort to ensure that all malware has been removed
from a Windows 7 Professional system, I scanned the system with
ClamWin Free Antivirus today.
It identified 12 suspect items, but I'm not sure any of those contributed
to excessive memory usage I saw at times on the system yesterday from
explorer.exe consuming more than 1/2 the 6 GB of memory on the system
for prolonged periods.
[ More Info ]
[/security/malware]
permanent link
Sun, Nov 16, 2014 11:28 pm
Malware Detected by Malwarebytes Anti-Malware 2014-11-16
A user who has been experiencing performance problems with her system
recently reported it was running particularly slowly on Friday, November
14. I checked the system this weekend. Malwarebytes Anti-Malware detected
some files associated with malware, but I'm not certain all problems
associated with the system are resolved yet. One of the files, jm78.dll,
it reported as associated with malware may have come from a no longer
existing website in Russia, but I'm not certain of that, either and don't
have time for futher investigation of the system tonight.
[ More Info ]
[/security/malware]
permanent link
Sun, Jan 29, 2012 7:59 pm
Redirection to Rogue rr.nu Site
While searching for a power adapter, I found a link for the part number of
the power adapter for which I was searching that redirected me to
www2.smartouholder.rr.nu. That site displayed a fake virus scan
(see
image),
which reportedly was finding malware on the system from which I was searching,
but was really just a ruse to try to lure unsuspecting users into buying
rogue antivirus software, i.e.,
scareware. If I tried
to navigate away from the site, I would receive a "Are you sure you want
to navigate away from this page?" message.
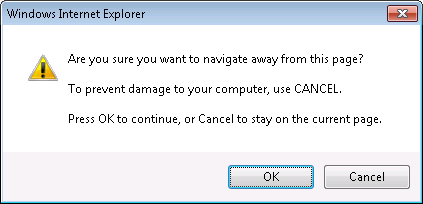
No matter which option I selected from "OK" or "Cancel", I was left at the
scareware webpage. After finally getting back to a prior Google search page,
I checked the site's reputation at
Norton™ Safe Web.
It did not list the site www2.smartouholder.rr.nu, stating it had not
been tested yet, but
it did list rr.nu.
Norton Safe Web reported the following for the rr.nu site:
rr.nu
Summary
| •Computer Threats: |
|
1 |
| •Identity Threats: |
|
0 |
|
•Annoyance factors:
|
|
0
|
|
|
|
| Total threats on this site: |
|
1 |
| |
|
|
|
•Community Reviews:
|
|
5
|
Norton Safe Web listed "Drive-By Downloads" as the threat from the site.
After I was able to navigate away from the site, I added an entry to
the /Windows/system32/drivers/etc/hosts file to ensure that
the system would not be able to contact the site again. I put the following
2 lines at the bottom of that file:
# Inserted on 2012-01-29. Site is attempting to download rogue antivirus software
127.0.0.1 www2.smartouholder.rr.nu
When a Windows system attempts to find an IP address for a website name,
such as www.example.com, it will first check the hosts file
to see if an IP address is listed there for the
fully qualified domain name. If
not, then it will perform a
Domain Name System (DNS) query to obtain the IP address associated with
the name. By associating the name with 127.0.0.1, which is the
loopback address
for the local system, you can ensure that a system on which the entry has
been put in the hosts file will see the name as pointing to its own address and
thus will never be able to reach the actual site.
Note: if you edit the hosts file with the Windows Notepad
editor, be sure you save the file as hosts, not
hosts.txt. The file may be marked as read-only, also, so in
order to save the file. you will need to take off the read-only attribute
temporarily and put the attribute back on after you have saved the file.
You can do so by right-clicking on the hosts file, choosing
Properties and unchecking the read-only attribute. Or you can
use the following two commands from the command line to take the attribute
off the file and put it back on after you've edited the file.
attrib -r C:\Windows\System32\drivers\etc\hosts
attrib +r C:\Windows\System32\drivers\etc\hosts
You will need to run the commands from an administrator account to do so.
You will also need to run Notepad from an administrator account to edit the
file. If you are logged in as another user, you can use the "runas" command
from the command line to run Notepad or the attrib command from the
administrator account.
E.g., you can use
runas /user:administrator cmd to open another command prompt
under the administrator account to run the attrib commands or
runas /user:administrator notepad to run Notepad from the
administrator account. Alternatively, for the attrib command you could use
runas /user:administrator
"attrib -r C:\Windows\System32\drivers\etc\hosts". If you are using a
domain administrator account you would use
runas /user:domainname\administrator.
[/security/malware]
permanent link
Tue, Nov 15, 2011 10:40 pm
AV Security 2012v121.exe Rogue Antivirus Program
I removed
rogue antivirus software associated with
AV Security 2012v121.exe from a user's system. The
AV Security 2012 "security" software was declaring other
programs on the system as infected and preventing other
programs from running.
[More Info ]
[/security/malware]
permanent link
Wed, Mar 30, 2011 11:59 pm
System Defender Infection
A user reported that annoying messages kept popping up on his sysetm
every few minutes from System Defender stating his system was infected.
When I checked his system, I found the
rogue
anti-spyware/anti-virus software named System Defender on the system.
I was able to remove it with
Malwarebytes' Anti-Malware, which has a free version of the software that
can be used to remove spyware and viruses. The commercial version will run
continually while the free version can be used to manually scan a system.
[More Info]
[/security/malware]
permanent link
Tue, Jan 05, 2010 11:00 pm
Malware Scanning on Dell Inspiron 1526
The owner of a Dell Inspiron 1526 laptop running Microsoft Windows Vista
with Service Pack 2 installed was seeing popups warning the system was
infected with malware. When I logged into the system, I saw one such
warning. The Task Manager would not run nor could I get a command prompt
at the time.
When I checked the system, I didn't find any rogue antivirus/antispyware
software on it, though that I could link to the warning. I did find
a .wmv file masquerading as an .mp3 file that Symantec Security Scan
identified as Trojan.Wimad, however.
[ More Info ]
[/security/malware]
permanent link
Tue, Sep 08, 2009 9:53 pm
Hello Kitty Online - Trojan.Win32.Generic!BT
A family member got an offer to become a beta tester for
Hello Kitty Online
today. The email message she received provided a link to download
a setup program
HKO_Downloader.exe. After she downloaded
the file, I had her submit it to
Virustotal
, a site that checks files for malware with multiple antivirus programs.
The
Virustotal analysis of the file showed 2 of the 41 programs it used
to check the file reporting a potential issue with the file. Note: someone
else had uploaded a file named
HKO_Island_of_Fun.exe on
September 3, 2009 that Virustotal identified as being an identical file
because that file had an identical
hash
value.
File HKO_Island_of_Fun.exe received on
2009.09.03 20:55:55 (UTC)
Current status: finished
Result: 2/41 (4.88%)
The two that identified the file as potentially being malware were as
follows:
| Antivirus | Version | Last Update | Result |
|---|
| McAfee+Artemis | 5730 | 2009.09.03 |
Suspect-29!4A5CA8AF0ECD |
| Sunbelt | 3.2.1858.2 | 2009.09.03 |
Trojan.Win32.Generic!BT |
Information on Mcafee+Artemis is available at
McAfee Artemis Technology. An evaluation of McAfee+Artemis is available
at
Anti-Virus Comparative Technology Preview Report McAfee Artemis.
Sunbelt's
Trojan.Win32.Generic!BT Information and Removal webpage shows the following:
| Threat Name | Trojan.Win32.Generic!BT |
| Summary |
Trojan.Win32.Generic!BT is a downloader associated with rogue security
programs (also called “scareware.”) Once downloaded, the rogues
pretend to scan a victim.s computer for malware then display false warnings
that the machine is infected. It tries to convince victims to purchase useless
security software. |
| Category |
Trojan
|
| Level |
High
|
| Advice | Remove |
| Description |
Other names: F-Secure: Trojan-Downloader.Win32.FraudLoad.ffz
Kaspersky: Trojan-Downloader.Win32.FraudLoad.ffz
Microsoft: TrojanDownloader:Win32/FakeVimes |
| Release Date | Apr 7 2009 |
| Last Updated | Aug 7 2009 |
| File Traces | - No traces available. |
The HKO_Downloader.exe file downloads the actual software needed to participate
in Hello Kitty Online, which is
a site run by Aeria Games. I
concluded that they may have licensed a downloading program that some others
may use for nefarious purposes, but I didn't see sufficient reason to be
concerned in this case and told her she could download the software and
participate in the beta testing.
[/security/malware]
permanent link

Privacy Policy
Contact



