←January→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| |
|
|
|
|
|
1 |
| 2 |
3 |
4 |
5 |
6 |
7 |
8 |
| 9 |
10 |
11 |
12 |
13 |
14 |
15 |
| 16 |
17 |
18 |
19 |
20 |
21 |
22 |
| 23 |
24 |
25 |
26 |
27 |
28 |
29 |
| 30 |
31 |
|
|
|
|
|
|
|
Mon, Jan 24, 2005 12:32 pm
Changing the Port Used by LapLink
LapLink has a mechanism for
changing the port number used for establishing connections.
It is a more cumbersome mechansm than that provided by some
other Windows remote control programs, such as
Symantec's pcAnywhere,
but it is possible to change the port.
LapLink uses UDP and TCP ports 1547 by default. But,
if you edit the LLW.INI file, that will be in the directory
C:\Windows\TSI32\LLW, you can get it to use another port.
In LLW.INI, in the [TCPIP] section, add
ListenPort= followed by the port
number you wish to use as below:
[TCPIP]
Enabled=Yes
ListenPort=5549
What makes this approach more cumbersome is that if you
need to connect to systems listening on different ports with
LapLink, you need to edit the file, save your changes, and then
restart LapLink to get it to use the port you want to use. If
you want to go back to the default port, you can just put in
"1547" for the ListenPort value.
[/os/windows/software/remote-control]
permanent link
Sun, Jan 23, 2005 6:16 pm
Setting up a Windows Server 2003 for Small Business Server (SBS) as an FTP Server
To set up a Windows Small Business Server 2003 server as a File Transfer Protocol
(FTP) server, take the following steps:
- Click on Start.
- Click on Control Panel.
- Click on Add or Remove Programs.
- Click on Add/Remove Windows Components.
- Click on Application Server to highlight it then click on
Details.
- Click on Internet Information Services (IIS) to highlight
it then click on Details.
- Click on File Transfer Protocol (FTP) Service, so that
it has a checkmark next to it.
- Click on OK.
You can configure the FTP service by taking the followng steps:
- Click on Start.
- Click on Control Panel.
- Click on Admimistrative Tools.
- Click on Internet Information Services (IIS) Manager.
- Click on the plus sign to the left of the server name to expand
the list of services under it.
- Click on the plus sign to the left of FTP Sites to expand
the list.
- Right-click on Default FTP Site and select Properties.
By default anonymous FTP connections are allowed. If you wish to disallow
anonymous FTP connections, click on the
Security Accounts tab and
uncheck
Allow anonymous connections. If you wish to permit only
anonymous connections, checck the
Allow only anonymous connections
check box under this tab.
To change the directory FTP users are connected to when they logon,
click on the Home Directory tab under Default FTP Site
Properties. Change the Local path to whatever directory
you wish to be the default directory when users login. You can
control the type of access allowed through Windows Explorer by
right-clicking on a folder name in the Explorer then selecting
Properties and clicking on the Security tab.
[/os/windows/iis]
permanent link
Sun, Jan 23, 2005 12:07 am
Internet Information Servier (IIS) Won't Permit File Download
I placed the Bazooka Spyware Scanner executable file, bazookasetup.exe, in
a downloads directory on my website along with the latest spyware database
for the program, bazooka_db.bdb. I was able to download both files from my
webserver running Apache, but I was not able to download the .bdb file
from a webserver running Microsoft's Internet Information Server (IIS).
When I tried clicking on the link to download it, I would get an error
page that included the information below:
The page cannot be found
The page you are looking for might have been removed, had its name changed, or is
temporarily unavailable.
...
HTTP Error 404 - File or directory not found.
Internet Information Services (IIS)
I renamed the file to have different extensions, such as .bak, .txt, and
.rtf and saw that IIS would recognize the file was there and allow me to
download it if it had an extension for a file type the system recognized,
such as .txt or .rtf, but not one it didn't recognize, such as .bak or
.bdb. To allow the download of this file from IIS, I took the following
steps:
- Clicked on Start
- Clicked on All Programs
- Selected Administrative Tools
- Selected Internet Information Services (IIS) Manager
- Right-clicked on Default Web Site and selected
Properties
- I then clicked on the HTTP Headers tab
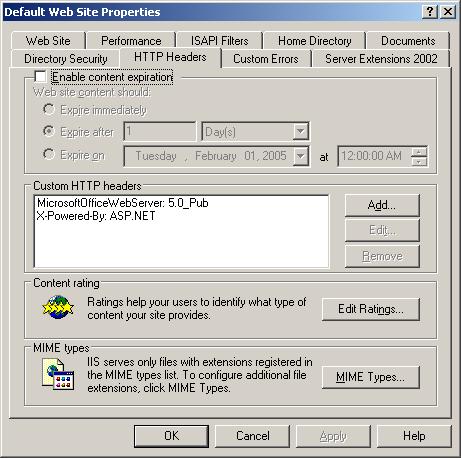
- Clicked on the MIME Types button
- Clicked on New
- Put bdb in the Extension field and
application/x-msdownload in the MIME type field
- Clicked on OK twice
- When I clicked on OK at the Default Web Site Properties
window, another window appeared titled Inheritance Overrides, which
stated the following:
The following child nodes also define the value of the "UNCPassword" property,
which overrides the values you have just set. Please select from the list below
those nodes which should use the new value.
-
I didn't select any, just clicked on OK. I don't know why the change
I made should have an effect on "UNCPassword".
I was then able to get a download window when I clicked on the
bazooka_db.bdb file, though.
[/os/windows/iis]
permanent link
Wed, Jan 19, 2005 12:15 am
Problem Printing AOL Email and Webpages with Internet Explorer
A user reported that he was unable to print his email from within AOL on
his Dell Dimension XPS R350 system running Windows 98 Second Edition and
Internet Explorer 6.0. He could
print from within Microsoft Word and I found that I could print from Notepad
also, but I couldn't print webpages from within AOL nor from within Internet
Explorer. This occurred after I removed adware/spyware from the system. I
thought perhaps some adware/spyware hadn't been fully removed or some damage
had been done in removing some deeply embedded adware/spyware, but I could find
nothing that I could identify as the source of the problem.
I updated Ad-aware SE Personal,
Bazooka Adware and Spyware Scanner,
BHODemon,
and Spybot Search & Destroy, but
when I scanned the system with those antispyware programs, they did not
find anything else. I installed another antispyware program,
PestPatrol. It found additional
adware/spyware that the others hadn't detected. Though much of what it
found were just cookies, which I didn't regard as more than a privacy
vulnerability. It also found remnants that Ad-aware and Spybot had left, i.e.
some registry entries. But, even removing everything PestPatrol found had
no impact on the problem. I've seen odd behavior on systems due to problems
with Layered Service Provider (LSP) software after I've removed adware/spyware,
so I even checked the system with
LSP-Fix and Ad-aware's
LSP
Explorer add-on, but found no LSP problems either.
I also updated
ClamWin Antivirus and scanned the
system for viruses, but found none.
I checked the system for updates by opening Internet Explorer and
choosing "Tools" and then "Windows Update". I scanned for updates and
found that there were 23 Critical Updates and Service Packs needed. I
clicked on "Review and Install Updates", which showed me the updates I
was about to install, but when I clicked on the "Install Now" button
nothing appeared to happen. Trying it several times, I noticed the
title bar for Internet Explorer did change color briefly each time
I clicked on "Install Now".
Examing the source code for the page showed that Microsoft used javascript
on the page, but when I checked the page using various browser test tools, such
as BrowserHawk,
BrowserInfo, and BrowserSpy,
showed that Internet Explorer on the system did have javascript support enabled
(another test page that just verifies javascript support is
JSsupport), plus all of the other support that I would expect from the
browser. None of those test tools showed anything unusual.
It appeared that the "Install Now" button would open another window and,
since the title bar was changing color briefly when I clicked on it, I
thought some popup blocking software was causing the problem. But
when I used the Windows 98 System Information tool (click on "Start",
"Programs, "Accessories", "System Tools", then "System Information", then
select "Tools", "System Configuration Utility" and click on the "Startup"
tab) to see what processes were starting when Windows 98 started, I didn't
see any popup blocking software listed. I installed
WinTasks Pro 4.3 to show me
all of the running tasks, but didn't see anything unusual. Nor did
ending almost all of the running processes make any difference.
Yet something was definitely stopping popup windows from appearing.
I went to PopupTest.com and
ran various popup tests that one could use to test popup blocking software.
Normally users don't want annoying popup ads appearing, but there are
occasions where the opening of a popup window is desireable. For instance,
if you click on a link in a webpage that would open another window or
right-click on a link in Internet Explorer and choose "Open in New Window",
you want a new window to open. Good popup blocking software should allow
windows to open in those cases, but some popup blocking programs may block
those as well, though they shouldn't. You can test whether the latter
type of popup windows are blocked at
http://www.popuptest.com/goodpopups.html. I found those popup windows
were blocked as well. And running checks at another popup blocker test
site, PopupCheck.com also showed
that all popup windows were blocked, even the kind that should be allowed.
I ran a Google search and found others
reporting similar problems with popup windows not opening when clicking on
links that should open a new window or when selecting "Open in New Window"
for a link displayed in Internet Explorer.
-
Internet Explorer won't open in a new window
-
Internet explorer won't display anything in a new window
I found suggestions advising one to use regsvr to register DLL's
as suggested on a Microsoft Knowledgebase article, "
You
cannot open a new Internet Explorer window or nothing occurs after you click a
link. That page suggested entering the following regsvr32 commands at
a command prompt, aka MS-DOS prompt, to resolve the problem.
regsvr32 Shdocvw.dll
regsvr32 Msjava.dll
regsvr32 Oleaut32.dll
regsvr32 Mshtml.dll
regsvr32 Browseui.dll
You should close all open programs before doing so and I found I had to
change the working directory to C:\Windows\System first. I've created
a batch file,
RegSvr32-FixIE.bat to enter the commands.
When the commands were executed, all were executed successfully, except the
one for Oleaut32.dll. I saw windows appear with the following information
displayed.
- DllRegisterServer in Browserui.dll succeeded.
- DllRegisterServer in Mshtml.dll succeeded.
- DllRegisterServer in Shdocvw.dll succeeded.
- DllRegisterServer in Oleaut32.dll failed.
Return code was 0x80029c4a
- DllRegisterServer in Msjava.dll succeeded.
An "
Explanation of Regsvr32 Usage and Error Messages" provides
some information on the errors regsvr32 will return, but you
need to check the "Error List from WINERROR.H" section of
INFO: Translating Automation Errors for VB/VBA (Long) for
the meaning of the "0x80029c4a" hexadecimal error code.
Unfortunately, the only explantion is that the code
80029c4a means "Error loading type library/DLL". WinTasks did
show a couple of processes running using that module, but I wasn't
able to close all of them, so perhaps the problem was due to one
of those processes having the oleaut32.dll module in use.
I thought the oleaut32.dll file might have become corrupted, altered, or
replaced by some other program, so I also compared
oleaut32.dll against a copy I obtained from
DLL-files.com. A binary comparison using the Windows fc command, i.e. "fc /b", showed that the copy of oleaut32.dll on the system was exactly the same
as the one I downloaded.
The Microsoft Knowlegebase article also suggested checking entries
in the registry.
If the problem is still not resolved, verify that the following registry values are present and correct:
HKLM\SOFTWARE\Classes\Interface\{00020400-0000-0000-C000-000000000046}
Name: (Default)
Value: IDispatch
HKLM\SOFTWARE\Classes\Interface\{00020400-0000-0000-C000-000000000046}\ProxyStubClsid
Name: (Default)
Value: {00020420-0000-0000-C000-000000000046}
HKLM\SOFTWARE\Classes\Interface\{00020400-0000-0000-C000-000000000046}\ProxyStubClsid32
Name: (Default)
Value: {00020420-0000-0000-C000-000000000046}
I checked all of the listed registry entries and found they were present and
correct, however. The next step listed in the Knowledgebase article, if
the problem was still not resolved, was to reinstall Internet Explorer. I
did reinstall Internet Explorer 6.0. While doing so, I encountered the
error message below.
An error has occurred while setting up "C:\WINDOWS\SYSTEM\oleaut32.dll".
This error has been logged, the installation will continue.
Afterwards nothing appeared to be different. I still had the same
problem as before. After the sentence about reinstalling Internet Explorer,
the Knowledgebase article stated "If you are using the version of Internet
Explorer that is included with your operating system, reinstall or repair your
operating system." I used the Windows 98 "System File Checker", which can be
run by clicking on "Start", "Programs", "Accessories", "System Tools", "System
Information" and then choosing "Tools" and "System File Checker". It indicated
that a couple of files should be restored, but those didn't appear to be
related to the problem nor did restoring them from the Windows 98 Second Edition
CD change the problem. So after that I reinstalled Windows 98 Second Edition
and that finally resolved the problem. I was then able to click on links that
open popup windows or right-click on a link and select "Open in New Window" and
have windows actually open. And I could print webpages by going to "File" and
"Print" in Internet Explorer and could also print AOL email from the system.
[/network/web/browser]
permanent link
Mon, Jan 17, 2005 8:40 pm
Determining if a Task is a Legitimate Process
If you have a question about whether a process you see running under Task
Manager, or something listed in a "Startup" group, is a legitimate process
there are a number of websites that provide informaton on processes you might
see running.
-
I Am Not A Geek - Startup DB
-
CastleCops - StartupList
-
WinTasks Process Library
-
Windows Files Database
[/security/spyware]
permanent link
Sat, Jan 15, 2005 2:17 pm
Using PHP to Upload Files to a Website
You can use PHP to provide the capability for users to upload files
to your website. First create an HTML file with a form for
uploading a file. Specify the PHP file that will handle the
uploads in the "action" part of the form.
For the form portion of the HTML file, I've named the PHP file
I will use as "upload.php". You must specify "POST" rather
than "GET" for "action". PHP on the server you are using is
likely to have a maximum size for POST data of 8 MB. Look
for the following lines in your php.ini file, which should
be in the /etc directory on a Linux system, and adjust the
size to what you consider to be an appropriate number.
; Maximum size of POST data that PHP will accept.
post_max_size = 8M
There is also another limiting factor, the maximum size for a file to be
uploaded, which is controlled by upload_max_filesize, in php.ini. The
default value is likely to be 2 MB. When you are transmitting a file via
POST using a form on a webpage, there may be other data transmitted for
other fields on the form as well plus MIME headers as well. So,
if you wanted to be able to transmit a file of 8 MB, you would need to
set the value of upload_max_filesize to 8M, and make post_max_size
slightly larger. But for this example, I'm simply going to set them
both to 8M, since the other data I'm transmitting is fairly small.
To adjust the maximum allowed size for file uploads, look for the
following lines in php.ini. You can specify the number in bytes or in
KiloBytes (KB) or MegaBytes (MB) by putting a "K" or "M" immediately after
the number in the latter two cases. Keep in mind a KiloByte is 1,024 bytes
and a MegaByte is 1,024 KiloBytes, so to determine the number of bytes
equivalent to a certain number of MB use Bytes = MB * 1024 *
1024.
; Maximum allowed size for uploaded files.
upload_max_filesize = 2M
There are also other parameters to consider when using a form that
calls a PHP script to upload files to your website. There is also a
memory_limit value, which will be a factor if the enable-memory-limit is
set. In my case, using Apache 2.0.40 and PHP 4.2.2 on a Fedora Linux
system, the only parameters I needed to set in php.ini were
upload_max_filesize (you can determine the versions by apachectl
-v and php -v. For a complete discussion of the
parameters to consider see
How to optimize your PHP installation to handle large file uploads.
Once you have adjusted the upload_max_filesize and post_max_size to
the desired values, you may need to restart your webserver software. If
you are using Apache on a Linux system you will need to do so. Use
apachectl restart to restart Apache. You will need to have
root access to do so. If you are using Apache, you will also need to put
the following lines in Apache's httpd.conf, likely located in
/etc/httpd/conf, before restarting Apache.
<Files *.php>
SetOutputFilter PHP
SetInputFilter PHP
LimitRequestBody 8388608
</Files>
The reason you will need to add the lines above to httpd.conf is that
Apache has a default limit for LimitRequestBody that restricts the size of
all POST data for any scripting language used on a webpage. Some Redhat
Package Manager (RPM) installations may set this value at 512 KB.
The HTML code you should use for the form portion of your HTML file
is shown below.
<!-- The data encoding type, enctype, MUST be specified as below -->
<form enctype="multipart/form-data" action="upload.php" method="POST">
<!-- Name of input element determines name in $_FILES array -->
Send this file: <input name="userfile" type="file">
<input type="submit" value="Send File">
</form>
See
upload.html for a complete HTML file
to perform the upload.
For the PHP file, you can use the following code:
<?php
// In PHP versions earlier than 4.1.0, $HTTP_POST_FILES should be used instead
// of $_FILES.
$uploaddir = "../../uploads/";
$uploadfile = $uploaddir . basename($_FILES['userfile']['name']);
if (move_uploaded_file($_FILES['userfile']['tmp_name'], $uploadfile)) {
echo "File is valid, and was successfully uploaded.<br><br>";
echo "<b>Name:</b> " . $_FILES['userfile']['name'] . "<br>";
echo "<b>Type:</b> " . $_FILES['userfile']['type'] . "<br>";
printf ("<b>Size:</b> %.2f KB ", $_FILES['userfile']['size'] / 1024);
echo "(" . $_FILES['userfile']['size'] . " bytes)<br>";
}
else {
echo '<pre>';
echo "Possible file upload attack!\n\n";
echo "Here is some more debugging info:\n";
print_r($_FILES);
print "</pre>";
}
?>
Be sure to put a "/" at the end of the directory name for the
upload directory.
When a user uploads a file, it will go into whatever directory is
specified as the temp directory in php.ini. If no temp directory
is specified in php.ini, the files will go into the default
temp directory for the system. When the PHP program
completes, it will be moved into whatever directory you specified
for the upload directory. You should change the permission of the
upload directory to 733, e.g. chmod 733 uploads or grant
permission for the user account under which your webserver software
runs, e.g. Apache, to write to this directory. I would strongly
advise you to use a directory outside the document root for your website,
e.g. if all of your website HTML files go under a directory named "www"
under your home directory, create another directory, e.g. "uploads"
at the same level as the www directory, but not underneath the "www"
directory. Otherwise, if some malicious user guesses where you are
placing the uploaded files, he can store a file with executable code
in that directory and then use a URL which includes the name of
the file he just uploaded to execute its contents.
For example, let's suppose that you are putting the uploaded files
in a directory called "uploads" that lies directly beneath the
one where your upload.php file resides. Someone knows or guesses
that you are using a directory with that name underneath the one
containing the upload.php file. He then creates a file with PHP
code within it and uploads it to your webserver. Let's suppose
your upload.html file is at http://somewhere.com/files/upload.html
and the upload.php file is at http://somewhere.com/files/upload.php.
The malicious user puts the code below in showinfo.php and then
uploads it. He knows it went into a directory called "uploads" beneath
the "files" directory He can then use the URL
http://somewhere.com/files/showinfo.php to execute the PHP file he
just put on the site.
<?
$files = `ls -la`;
$users = `who`;
echo "<pre>";
echo "Directory \n";
echo $files . "\n";
echo "Users \n";
echo $users . "\n";
echo "</pre>";
?>
The code above is relatively innocous. On a Unix or Linux system,
it will only display all files
in the directory where it is located and a list of the users logged
into the system. But code could just as easily be inserted to replace
or delete files, including system files, so it is important to
protect yourself against malicious individuals wishing to do damage
to your system or compromise it. So put the uploaded files in a
location where no one can execute the files.
You may also wish to password protect the directory where the upload.php
file is located, so that you can limit who will be able to upload
files.
References:
-
Chapter 38. Handling file uploads
-
File Uploads (tutorial)
-
How do I do html form file uploads
-
How to optimize your PHP installation to handle large file uploads
-
ini_get (finding post_max_size)
[/languages/php]
permanent link
Fri, Jan 07, 2005 10:33 pm
Browser Information
For information on the system and browser you are using, such as the
browser version, monitor resolution, number of colors supported, whether
Flash and Java support are enabled, etc., use one of the webpages listed
below.
-
BrowserHawk
-
BrowserInfo
-
BrowserSpy
[/network/web/browser]
permanent link

Privacy Policy
Contact



