Wed, Dec 31, 2014 4:45 pm
Determining the version of Microsoft Word used to edit a .docx Document
I sent someone a Microsoft Word document that contained a network diagram I had
created in PowerPoint and then copied and pasted into the Word document.
I created the file on an Apple MacBook Pro laptop using
Microsoft® Word 2008 for Mac and saved it in "Word Document (.docx)" format.
The diagram I pasted into the Word document was created with
Microsoft® PowerPoint® 2008 for Mac. The recipient informed me that
some of the text in boxes in the diagram was cropped, so he edited the
diagram and sent me a copy of the document with his edited diagram. When
I viewed his version, I saw text missing that had been present in my version
and some of the double-headed arrows I had on the diagram now looked
odd to me when viewed in Word on the Mac. I presumed the issue was due
to the different versions of Microsoft Word we are using, since I had
encountered issues before where diagrams created in a Microsoft Office
application on a Windows-based PC looked different when viewed in the
same application on a Mac.
I thought he was likely using Office 2013, but I wanted to verify that
was the version he was using. The .docx files we were exchanging became
a standard Word format starting with Office 2007. They are in an
Office Open XML
format, which is a
zipped, XML-based file
format developed by Microsoft; information about the
formats can be found in the Microsoft Office 2007 article
Introducing the Office (2007) Open XML File Formats. Prior to
Office 2007, Microsoft used proprietary file formats based on the OLE
Compound File Binary Format.1
You can check the version of Word that was last used to edit a
document by unzipping the docx file; you can use the unzip
command from a shell prompt on a Mac OS X system. If your unzip program
isn't opening it, you may have to rename it changing the .docx
extension to .zip, but that's not needed for the OS X unzip utility.
When you unzip the docx file, there will be a docProps
directory with an app.xml file within it. In that file
you will see a number between AppVersion tags, e.g., as
shown below:
<AppVersion>15.0000</AppVersion>
To translate that number into the commonly used version number, the
table below can be used:
| Number | Office Version |
|---|
| 12.0000 | 2007 or Office 2008 for Mac |
| 14.0000 | 2010 |
| 15.0000 | 2013 |
If you are interested in the usage for the other documents within the
.docx container file, see the ForensicsWiki article
Word Document (DOCX). The contents of the Word document can be
found in word/document.xml when you examine the files
within the .docx file.
Since I saw 15.0000 as the AppVersion in the file he sent,
I could tell that he was, indeed, using Office 2013. In .docx files
I saved from Word 2008, I saw 12.0000 as the AppVersion
number within app.xml.
To resolve the problem, instead of copying and pasting the
diagram from PowerPoint into the Word document, I saved it as a JPEG image
from within PowerPoint. Then chose "Insert", then "Picture", then "From File"
within Word to insert the diagram as a picture instead. When I viewed the
document with embedded diagram afterwards in Word for Office 2007 and 2010 it
looked the same as it did in Word 2008 on the Mac, though it had also looked
ok in those Microsoft Windows applications when I used the pasted PowerPoint
version. The embedded JPG file also looked the same in Apache OpenOffice
Writer 4; it had not appeared when I viewed the document there
previously and when I had viewed the PowerPoint file in OpenOffice
Impress, the diagram looked quite different with most of the text
missing and small circles beneath the network clouds in the diagram.
References:
-
Microsoft Office: File formats and metadata
Date accessed: December 31, 2014
Wikipedia, the free encyclopedia
-
Which Version of Microsoft Word created a given document?
Date: August 25, 2013
By: Gergely
Herendi
Super User
-
Word Document (DOCX)
ForensicsWiki
[/os/windows/office/word]
permanent link
Tue, Dec 30, 2014 1:24 am
PHP script displaying wrong time
I include the following PHP code in web pages on this system to display the
last time that a file was updated.
<?php
$thisfile = pathinfo($_SERVER['PHP_SELF']);
echo "Last modified: ".date("l F j, Y g:i A",
filemtime($thisfile["basename"]));
?>
After I replaced the hard drive recently and installed
CentOS 7 as a fresh install, the times displayed have been ahead 5 hours, i.e.,
the PHP code was displaying a time stamp matching
Universal
Coordinated Time (UTC), also commonly referred to as
Greenwich Mean
Time, rather than
Eastern Standard Time (EST)
I verified the time zone was set correctly at the operating system level
with the timedatectl
command, so I realized the issue must be with PHP itself. I checked the
location of the PHP configuration file, php.ini and found it was
located at /etc/php.ini.
$ locate php.ini
/etc/php.ini
/usr/share/doc/php-common-5.4.16/php.ini-development
/usr/share/doc/php-common-5.4.16/php.ini-production
I logged into the root account and checked the contents of the
/etc/php.ini file. I found that the timezone was not
set in the file:
[Date]
; Defines the default timezone used by the date functions
; http://php.net/date.timezone
;date.timezone =
So I removed the semicolon which was making the date.timezone
line into a comment and set the time zone to be the appropriate one for
Eastern Time (ET).
[Date]
; Defines the default timezone used by the date functions
; http://php.net/date.timezone
date.timezone =America/New_York
I then restarted the Apache web server software with the
apachectl restart command, which fixed the problem.
[/languages/php]
permanent link
Tue, Dec 30, 2014 12:51 am
Setting the time zone on a CentOS 7 system
You can see the time zones a CentOS 7 system recognizes by entering the
command
timedatectl list-timezones while logged into the root
account.
[root@localhost ~]# timedatectl list-timezones
Africa/Abidjan
Africa/Accra
Africa/Addis_Ababa
Africa/Algiers
Africa/Asmara
Africa/Bamako
Africa/Bangui
Africa/Banjul
Africa/Bissau
Africa/Blantyre
Africa/Brazzaville
Africa/Bujumbura
Africa/Cairo
Africa/Casablanca
<text snipped>
Pacific/Pitcairn
Pacific/Pohnpei
Pacific/Port_Moresby
Pacific/Rarotonga
Pacific/Saipan
Pacific/Tahiti
Pacific/Tarawa
Pacific/Tongatapu
Pacific/Wake
Pacific/Wallis
For a system in the Americas, the following time zones are recognized:
[root@localhost ~]# timedatectl list-timezones | grep America
America/Adak
America/Anchorage
America/Anguilla
America/Antigua
America/Araguaina
America/Argentina/Buenos_Aires
America/Argentina/Catamarca
America/Argentina/Cordoba
America/Argentina/Jujuy
America/Argentina/La_Rioja
America/Argentina/Mendoza
America/Argentina/Rio_Gallegos
America/Argentina/Salta
America/Argentina/San_Juan
America/Argentina/San_Luis
America/Argentina/Tucuman
America/Argentina/Ushuaia
America/Aruba
America/Asuncion
America/Atikokan
America/Bahia
America/Bahia_Banderas
America/Barbados
America/Belem
America/Belize
America/Blanc-Sablon
America/Boa_Vista
America/Bogota
America/Boise
America/Cambridge_Bay
America/Campo_Grande
America/Cancun
America/Caracas
America/Cayenne
America/Cayman
America/Chicago
America/Chihuahua
America/Costa_Rica
America/Creston
America/Cuiaba
America/Curacao
America/Danmarkshavn
America/Dawson
America/Dawson_Creek
America/Denver
America/Detroit
America/Dominica
America/Edmonton
America/Eirunepe
America/El_Salvador
America/Fortaleza
America/Glace_Bay
America/Godthab
America/Goose_Bay
America/Grand_Turk
America/Grenada
America/Guadeloupe
America/Guatemala
America/Guayaquil
America/Guyana
America/Halifax
America/Havana
America/Hermosillo
America/Indiana/Indianapolis
America/Indiana/Knox
America/Indiana/Marengo
America/Indiana/Petersburg
America/Indiana/Tell_City
America/Indiana/Vevay
America/Indiana/Vincennes
America/Indiana/Winamac
America/Inuvik
America/Iqaluit
America/Jamaica
America/Juneau
America/Kentucky/Louisville
America/Kentucky/Monticello
America/Kralendijk
America/La_Paz
America/Lima
America/Los_Angeles
America/Lower_Princes
America/Maceio
America/Managua
America/Manaus
America/Marigot
America/Martinique
America/Matamoros
America/Mazatlan
America/Menominee
America/Merida
America/Metlakatla
America/Mexico_City
America/Miquelon
America/Moncton
America/Monterrey
America/Montevideo
America/Montserrat
America/Nassau
America/New_York
America/Nipigon
America/Nome
America/Noronha
America/North_Dakota/Beulah
America/North_Dakota/Center
America/North_Dakota/New_Salem
America/Ojinaga
America/Panama
America/Pangnirtung
America/Paramaribo
America/Phoenix
America/Port-au-Prince
America/Port_of_Spain
America/Porto_Velho
America/Puerto_Rico
America/Rainy_River
America/Rankin_Inlet
America/Recife
America/Regina
America/Resolute
America/Rio_Branco
America/Santa_Isabel
America/Santarem
America/Santiago
America/Santo_Domingo
America/Sao_Paulo
America/Scoresbysund
America/Sitka
America/St_Barthelemy
America/St_Johns
America/St_Kitts
America/St_Lucia
America/St_Thomas
America/St_Vincent
America/Swift_Current
America/Tegucigalpa
America/Thule
America/Thunder_Bay
America/Tijuana
America/Toronto
America/Tortola
America/Vancouver
America/Whitehorse
America/Winnipeg
America/Yakutat
America/Yellowknife
For a system on the east coast of the U.S., the appropriate time zone
would be "America/New_York". You can see the current timezone setting with the
command timedatectl with no parameters.
[root@localhost ~]# timedatectl
Local time: Tue 2014-12-30 00:15:02 EST
Universal time: Tue 2014-12-30 05:15:02 UTC
RTC time: Tue 2014-12-30 05:15:02
Timezone: America/New_York (EST, -0500)
NTP enabled: yes
NTP synchronized: yes
RTC in local TZ: no
DST active: no
Last DST change: DST ended at
Sun 2014-11-02 01:59:59 EDT
Sun 2014-11-02 01:00:00 EST
Next DST change: DST begins (the clock jumps one hour forward) at
Sun 2015-03-08 01:59:59 EST
Sun 2015-03-08 03:00:00 EDTIf you need to change the time zone, you can enter the command with
a set-timezone parameter, e.g.,
timedatectl set-timezone America/New_York.
You can use the ntpdate package to synchronize your
system with a
Network Time Protocol (NTP) server. You can check if the package is
installed with the command rpm -qi ntpdate. You will see
details on the package, if it is installed. If it is not installed, you
will see "package ntpdate is not installed".
References:
-
How To Configure Server Timezone In CentOS 7
By: Richard W
Date: September 14, 2014
Liberian Geek
[/os/unix/linux/centos]
permanent link
Mon, Dec 29, 2014 9:38 pm
Colasoft Ping Tool 1.2
If you want a graphical version of the ping tool that comes with most
operating systems, the
Colasoft Ping Tool provides a
GUI tool that, in addition to providing the standard
information provided by ping tests, such as minimum, maximum, and average
response times, also puts the information into a chart, which can be
viewed in several formats, e.g., bar chart, line chart, and area chart.
As ping packets are sent, the program updates a graph showing how ping
response times are varying over time with response times in milliseconds
on the y axis and the x axis showing time. The program also allows you to
save an image of the chart it produces as a BMP file, which can be viewed
by a variety of image viewing programs on a Microsoft Windows system.
[ More Info ]
[/reviews/software/windows/network/icmp]
permanent link
Mon, Dec 29, 2014 12:09 am
PowerShell Server 6.0
I installed PowerShell Server software on a Windows 8.1 Professional system to
enable the system to function as an SSH server. I've used Bitvise's SSH
server software and
Copssh with recent operating
systems, but hadn't used the PowerShell Server software before. The
software allows a system to function as an SSH and SFTP server. I had
hoped to be able to allow domain accounts to log into the system as well
as local accounts, but so far I've only been able to log into the system
via SSH after installing the software with local accounts on the system.
[ More Info ]
[/reviews/software/windows/network/ssh]
permanent link
Sat, Dec 27, 2014 11:01 pm
EFI System Partition
PCs now have UEFI firmware rather than the BIOS they once had. Hard disk
drives in systems with UEFI firmware may have an "EFI System Partition",
which will be fairly small, e.g. about 100 MB, which may be a third partition
on drives that may have an operating system, such as Microsoft Windows on
one partition and system recovey software on another partition. The
EFI partition must be formatted with the FAT12, FAT16, or FAT32 file
system. The partiton will store boot loader code for operating systems, such as
Windows, installed on other partitions and may also store device drivers
needed by the firmware.
[ More Info ]
[/hardware/pc/UEFI]
permanent link
Sat, Dec 27, 2014 3:20 pm
Windows Server 2012 - Folders located on the system hard drive
After I set up a Windows Server 2012 Essentials server, I noticed the dashboard
indicated two alerts were pending. One of them was just to reboot the server
since updates had been recently installed that required a reboot, but the
other alert was "One or more server folders are located on the system hard
drive". The folders referenced were as follows:
- Client Computer Backups
- Folder Redirection
- File History Backups
- Users
- Company
If you have a second internal drive or another partition on the primary
drive you can move the
folders with these steps.
[/os/windows/server2012]
permanent link
Thu, Dec 25, 2014 9:29 pm
Windows Server 2012 Essentials Product Key
I needed to install Microsoft
Windows Server 2012
Essentials on a system. Windows Server 2012 is the server version of
Windows 8 and the successor to Windows Server 2008 R2. I had the product key for
Windows Server 2012, but not the media. I downloaded an ISO file for Windows
Server 2012 R2 Essentials from Microsoft at
Windows Server Evaluations. The evaluation version allows you to try the
software for 180 days before purchase. I burned the .iso file to a DVD
and started the installation of the software. When I got to the "Enter
the product key to activate Windows" step, I put in the product key I had,
but received the message "We couldn't verify the product key. Please check
your installation media." After triple-checking the product key, I had to
conclude it wasn't going to work with the latest version of the software I
downloaded from Microsoft's site. Someone provided me with a link where I
could download an ISO file to use with the legitimate product key, but I was
concerned about the possibility of tampering with the contents of that ISO
file. So I checked the
MD5 and
SHA-1 hashes for the ISO file
with
digestIT 2004, which
gave me the following hashes for
en_server_install_disc_windows_server_2012_essentials_x64_dvd_1022281.iso:
MD5: 5ee4c7ad57248b5e791dcfd39d9e54e3
SHA-1: 1f3fbf9cd23f864a2acc6b7a6a8e6a9eb94b5c52
I was then able to verify those hashes with postings from
Server 2012 Essentials RTM (SHA-1 from October 11, 2012) and
Server 2012 Essentials RTM Page 2 (MD5 and SHA-1 from December 8, 2012)
postings at My Digital Life Forums
, which gave me the confidence to use that .iso file for the installation
of the server software, since the hashes matched ones posted for the 2012
version of the software distributed by Microsoft. Such hashes are
commonly used to verify that a file is exactly the same as it was when
provided by the original software developer and has not been modified.
When I installed Windows Server 2012 from the DVD I burned from that
ISO file, I was able to use the product key I had.
[/os/windows/server2012]
permanent link
Thu, Dec 25, 2014 6:20 pm
Cloning a drive with Clonezilla
Clonezilla,
which is a
live
CD based on Debian Linux, provides the capability to clone one disk
drive to another. You can boot a system from the live CD and copy an
entire drive, including Microsoft Windows partitions, to a new drive.
[ More Info ]
[/os/unix/linux/Clonezilla]
permanent link
Mon, Dec 22, 2014 11:59 pm
Allow file downloads in Internet Explorer 11
A user reported she received the following message when attempting to download
an attachment to email she was viewing while logged into her GoDaddy email
account through Internet Explorer 11.
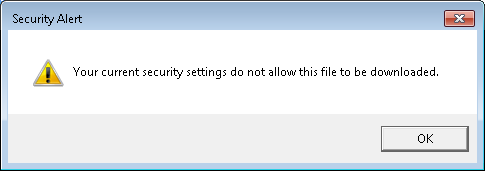
I tried downloading a Microsoft Word .docx attachment to an email and
saw the same Security Alert window, which stated "Your current security
settings do not allow this file to be downloaded."
The setting, which applies to all files rather than a particular type of
file such as a Microsoft Word document, can be changed through the
following steps in Internet Explorer (IE) 11:
- Click on Tools.
- Select Internet Options.
- Click on the Security tab.
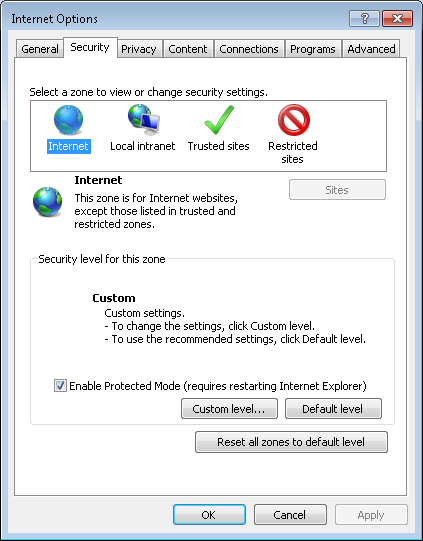
-
Select the Internet zone, which is the left-most zone in the row of icons
representing the four zones: Internet, Local intranet, Trusted sites, and
Restricted sites.
-
Click on the Custom level button.
-
In the Security Settings - Internet Zone window that opens, scroll
down through the settings list until you see Downloads. For
the File download option, change it from "Disable" to "Enable"
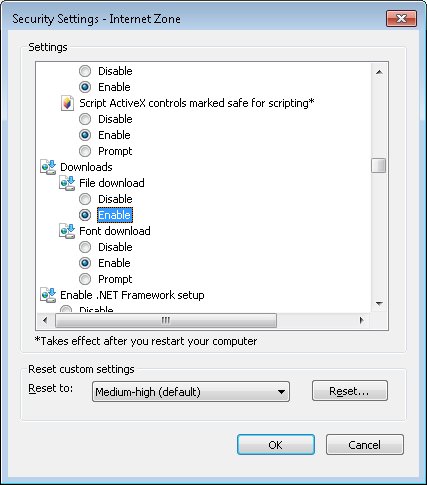
-
Click on the radio button next to "Enable".
- Click on OK.
- When asked "Are you sure you want to change the
settings for this zone?", click on Yes.
- Click on the OK button to close the
Internet Options window.
[/network/web/browser/ie]
permanent link
Sun, Dec 21, 2014 5:38 pm
CoolYou
A friend was complaining that his laptop, which runs Microsoft Windows 7 Home
Premium, was very slow, so he was considering purchasing another laptop.
I suggested he download and install
Malwarebytes Anti-Malware

and scan the system with that software. One of the
items it detected was CoolYou
(
image),
which it classified as
Trojan.Dropper.
[ More Info ]
[/security/malware]
permanent link
Sat, Dec 20, 2014 10:46 pm
Malwarebytes Anti-Malware detection for csrss.exe
A user reported that she saw a message on her system, which runs Windows 7
Professional, Friday morning December 19, 2014 indicating that malware had
been detected on her system by
Malwarebytes Anti-Malware

.
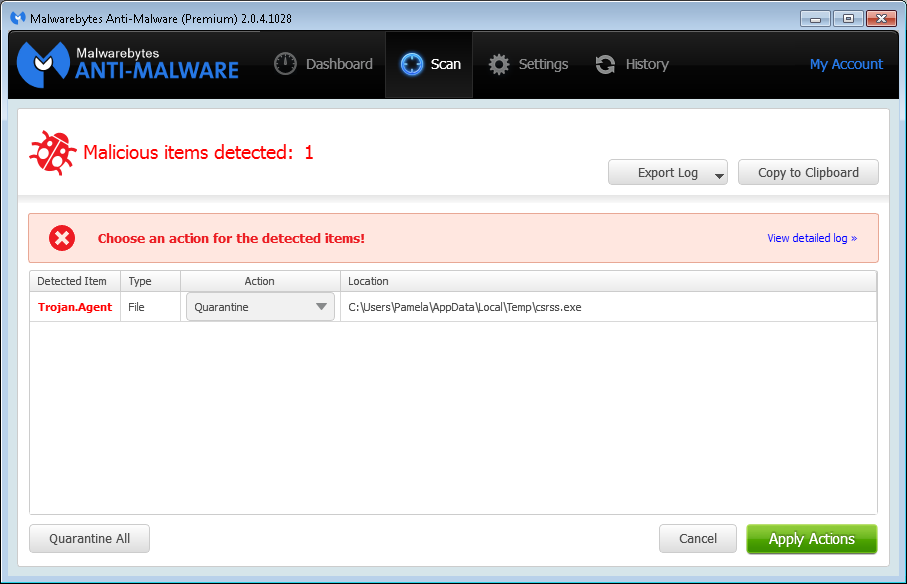
The file, which Malwarebytes identified as
Trojan.Agent, was csrss.exe was located in her
%TEMP% directory, i.e.,
C:\Users\Pamela\AppData\Local\Temp. There is a legitimate
Microsoft Windows file named csrss.exe, but that file is located in
C:\Windows\System32. The legitimate file on her system is
7,680 bytes in size and has a time stamp of 0/7/13/2009 08:39 PM. When
I checked the one Malwarebytes Anti-Malware was identifying as malware,
I saw it had the same size and time stamp.
C:\Windows>dir %TEMP%\csrss.exe
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Temp
07/13/2009 08:39 PM 7,680 csrss.exe
1 File(s) 7,680 bytes
0 Dir(s) 864,839,192,576 bytes freeI uploded the one Malwarebytes Anti-Malware flagged as malicious to
Google's VirusTotal site, which
analyzes uploaded files with many antivirus programs to determine if they
are safe or potentially dangerous. I had the site reanalyze the file, which
had been scanned previously. Zero of the fifty-four antivirus programs used
by the site to scan the file identified it as malware. The
SHA256 hash
listed for the file is
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a -
see the
report.
I ran a binary file comparison between the two files using the Microsoft
Windows fc utility. It found no differences between the two
copies of csrss.exe.
C:\Windows>fc /b %TEMP%\csrss.exe c:\windows\system32\csrss.exe
Comparing files C:\USERS\PAMELA\APPDATA\LOCAL\TEMP\csrss.exe and C:\WINDOWS\SYSTEM32\CSRSS.EXE
FC: no differences encountered
I had previously placed
md5deep, which can be downloaded from
md5deep and hashdeep, and its
associated utilities on the system. I used the 64-bit version, since
the system was running the 64-bit version of Microsoft Windows 7, of
sha256deep to check the SHA-256 hash for the version of the
csrss.exe file in C:\Windows\System32. It reported the same
SHA-256 hash as VirusTotal listed for the copy of the file I uploaded from
the users %TEMP% directory. I also checked the
MD5,
Tiger, and
Whirlpool
hashes for both files. For both files the MD5 hash was
60c2862b4bf0fd9f582ef344c2b1ec72 The Tiger hash function yieled a
hash of 42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b for both.
The Whirlpool hash was
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 for both files.
C:\Program Files\Utilities\File\md5deep>sha256deep64 c:\windows\system32\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>sha256deep64 %TEMP%\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 c:\windows\system32\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 %TEMP%\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 c:\windows\system32\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 %TEMP%\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 c:\windows\system32\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 %TEMP%\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 C:\Users\Pamela\AppData\Local\
Temp\csrss.exe
So I've no reason to suspect that the file in the %TEMP%
directory is any different than the one in the C:\Windows\Temp
directory. I thought that perhaps the only reason Malwarebytes
Anti-Malware flagged it to be quarantined is that it was an exe file in
the user's AppData\Local\Temp directory. It is possible that
I copied the file there previously when I was checking on various files
on the system when trying to eliminate a source of malware infection
on the system and that an update to Malwarebytes Anti-Malware now
has it mark any file in that directory as malware. I had Malwarebytes
Anti-Malware quarantine the file and then copied another legitimate
Microsoft Windows exe file, write.exe and also the
csrss.exe file from \C:\Windows\System32
into that directory just to see if Malwarebytes Anti-Malware would
flag them as malicious. It again detected csrss.exe as
malicious, but did not report the write.exe file I copied
into that directory from C:\Windows\system32 as malicious,
so it doesn't seem to be judging all .exe files in that folder as
potential threats, just certain ones.
[/security/antivirus/Malwarebytes]
permanent link
Sat, Dec 20, 2014 9:13 pm
Seagate external USB drive part number 9SF2A4-500
I have a
Power Adapters page where
I list the power adapters that are needed for various devices. I started
the page years ago after repeated instances where I had to figure out what
power adapter went with what device when an adapter got disassociated from
a device and either lost or jumbled with other adapters. To make it easier
for me to immediately associate an adapter with a device, I listed the
model/part number for a device and the model/part number for its power
adapter. I also list, when I can find a source, a site where a suitable
replacement adapter can be purchased. Now, whenever I encounter a device,
I try to immediately enter the power adapter information for it on my
web page. But today, I found a couple of power adapters next to a couple of
devices that I had jumbled together. And when I checked my web page I found
that I hadn't entered the power adapter information for either device.
I was fairly certain that I could
associate the right adapter with each advice, assuming that since the adapters
were near the devices that they were indeed the ones that went with those
devices, but while double-checking
on the adapter for a Seagate USB external drive with part number
9SF2A4-500, I came across
Felix's Blog, a blog from another
person providing tech support, by Marcel "Felix" Giannelia of Terrace, BC,
Canada who provides
Disassembly instructions for Seagate 1 TB Expansion
External Drive (9SE2A4-571 or 9SF2A4-500).
I've copied his instructions to my own site
here,
so that I have a copy should the author's site, or even
just these instructions, disappear, since he states at
Welcome to Felix's little Knowledge Base
thing that "I've been even sloppier about copyright in the files
I've written myself. I intend the ones I wrote myself to be in the public
domain." According to his disassembly instructions, the drive inside the
Seagate External Expansion case is a Seagate Barracuda 7200.12 model
ST31000528AS

.
Checking other postings's to the author's site, I found
"Do NOT paraphrase when calling tech support", which links to
an email
he sent to a user regarding the user's paraphrasing an error message for
the Eudora email
client, a program I once used many years ago and which users
I supported once used.
I can certainly emphasize with his posting; many years ago when I was a sysadmin for
a Digital Equipment Corporation (DEC)
VMS system, a user
contacted me about a problem with one of her databases on the system. She
gave me the error message and, since DEC very nicely provided documentation
for the database software listing possible error messages and steps to take
to rectify the problem associated with a particular error message, I referred
to that documenation and found it listed an error message that was a very
close match to the one the user gave me. After spending a couple of hours
checking all of the possibilities listed for that error message, I contacted
the user and had her recreate the problem. When she then read me the exact
error message, I realized it was quite different than what she had paraphrased
from memory previously. Once I had the exact error message, it only took me
a few minutes to fix the problem, but I had wasted hours on the problem before
that because she hadn't written down the exact message, but gave me a
paraphrased version. One user takes snapshots of error messages on her
computer screen with her phone now and sends them to me; that's very helpful,
since I can see the window containing the error message and its exact
contents.
I also found his "Why cats save humans from house fires" amusing, though
the smoke alarm has almost never gone off in our house due to food
preparation. It did go off one time when I put the tea kettle on the stove
to heat water for tea and then went into another room to work on a
computer. I didn't hear the tea kettle whistling; when the smoke alarm
went off I went into the kitchen and found that all of the water in the
tea kettle had boiled off and there was a burning puddle of plastic next
to the tea kettle due to the plastic on the handle melting. Our cats
didn't like the blaring smoke alarms throughout the house.
In another posting by Felix, I found an adapter that will also be useful
to me, since it supports both IDE, aka PATA, drives as well as
SATA hard disk drives listed in his a "Product Plug!" posting
for a "Ultra USB 2.0 to IDE/SATA Cable for 2.5-Inch/ 3.5-Inch /
5.25-Inch Drive with Power Adapter", which he notes is a "a USB
to any-kind-of-hard-drive adapter. That is, it's got a USB plug on
one end, and all the kinds of hard drive connector mashed together
on the other end. I just ordered one, because this is going to
save me so much time disassembling USB enclosures". His link was to the ULT40112
on the TigerDirect.ca site, i.e., the Canadian site
for TigerDirect; it is available in the U.S. from
TigerDirect.com. I have devices that provide
USB connectivity for hard drives that aren't in an enclosure, but none that
support both IDE, aka PATA, and SATA drives.
Unfortunately, the plug on the Asian Power Devices WA-24E12 (output 12V 2A)
power adapter I found near the drive that I thought went with the drive
would not plug into the drive, even though according to information
I found elsewhere online it should have worked for that drive. Another
12V 2A adapter, model ADS-24F-12 1224GPCU, I tried from another Seagate
external USB disk drive enclosure did connect easily, though.
Seagate® Expansion™ External Data Sheet

[/hardware/storage/Seagate]
permanent link
Sat, Dec 20, 2014 5:38 pm
Checking the warranty on a Segate drive
If you want to check whether a Seagate disk drive is still under warranty,
you can do so at either the
Warranty Validation or the
Customer Returns page. You can check the warranty for an internal
hard disk drive or an external USB drive.
You will need to complete fields on the form for the following information:
- Serial Number
- Product Number / Model Number
- Country
If the warranty is expired, you will see "Warranty is expired for the
entered Product/Serial". You won't see the date that the warranty expired on.
[/hardware/storage/Seagate]
permanent link
Sat, Dec 20, 2014 1:58 pm
Viewing history of DNS server and IP Changes for a Domain
If you wish to view a history of
Domain Name System
(DNS) server changes for a domain name, you can do so through
the
WhoISrequest Domain History
Checker, which tracks nameserver changes since 2002 for all COM, NET, ORG,
INFO, BIZ and US domains.
E.g., if I put
sailormoonworld.com, which was registered in 1998, in the search field, I
can see a list of all of the DNS servers that translated the
fully
qualified domain name (FQDN) to an IP address since WhoISrequest began
tracking name server changes in 2002. The history information for that
particular domain shows that registration for the domain name lapsed in
2013 and the domain name was picked up by a
domain name squatter
then. The domain name squatter let the domain registration lapse in the
summer of 2014. I re-registered the domain name for the original owner, a
family member, in October.
You can also view such information through the
DNS History site, which notes
"Here at DNS History we have been crawling DNS records since 2009, our index
currently contains over 200 million domains and discovering over a billion DNS
records."
If I put sailormoonworld.com in the Doman Search field on that site,
though, it does not have any information on it, though it does have information
on moonpoint.com, though that information was last updated on 2010-08-11, so
that site's information does not appear to be as comprehensive nor as
up-to-date as the information provided through the WhoISRequest site.
You can also find past name server and registration information through
the who.is Search Domain DNS and Name Server
Information page. When you put a domain name in the search field,
and click on "Search DNS and Name Servers", you will see information
on the domain, such as name servers, SOA record, DNS records, including
the mail exchanger (MX) servers for the domain. If you click on the
History tab above that information, you will see past domain
name registrars and name servers associated with the domain.
If you wish to see prior IP addresses associated with a domain name,
you can use ViewDNSInfo IP
History. I noticed when I checked sailormoonworld.com with
its tool, though, that it is not showing a change made near the end of October
for that domain. The last change it shows was for 2014-07-05. The site also
has a lot of other tools, e.g.
Google Pagerank Checker, etc.
[/network/dns]
permanent link
Thu, Dec 18, 2014 10:53 pm
Finding files by modification date in Windows
If you need to search a Microsoft Windows for files modified on a
particular date or within a specific time span, you can use the
datemodified qualifier within the Windows Explorer.
[ More Info ]
[/os/windows/explorer]
permanent link
Sun, Dec 14, 2014 6:05 pm
Determining the accounts in the administrators group form a command prompt
To determine the accounts in the administrators group for a Microsoft
Windows system, you can use the command
net localgroup administrators
C:\Users\Administrator>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
JDoe
mayberry\Administrator
mayberry\Domain Admins
SvcCOPSSH
The command completed successfully.
[/os/windows/commands]
permanent link
Sun, Dec 14, 2014 5:45 pm
Copssh Connection Issues
When I tried connecting to a Windows 7 Professional system running Copssh 5.0.1 from
PuTTY
0.58 on a Windows Small Business Server (SBS) 2003 system, a "PuTTY Fatal Error"
window appeared with the message "Couldn't agree a client-to-server cipher
(available: aes128ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com)".
I tried connecting from the same system with an OpenSSH_3.8.1p1 SSH client
that is part of
OpenSSH for
Windows and received the message "no kex alg", which may mean "no
key-exchange algorithm". When I tried specifying the encryption cipher using
the OpenSSH client, I received an error message similar to the one I saw
with PuTTY.
C:\Program Files\SSH\OpenSSH\bin>ssh -c 3des jdoe@192.168.0.15
no matching cipher found: client 3des-cbc server aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
C:\Program Files\SSH\OpenSSH\bin>ssh -c blowfish jdoe@192.168.0.15
no matching cipher found: client blowfish-cbc server aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
When I tried connecting from the SBS 2003 system to another system, to
which I could successfully connect with the OpenSSH SSH client, when I
specified the -v option for debugging output with ssh -v
jdoe@example.com, I saw the following:
debug1: Remote protocol version 2.0, remote software version OpenSSH_6.4
debug1: match: OpenSSH_6.4 pat OpenSSH*
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_3.8.1p1
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: server->client aes128-cbc hmac-md5 none
debug1: kex: client->server aes128-cbc hmac-md5 none
I upgraded PuTTY on the client system from version 0.58 to 0.63. I then no
longer received the message about no matching cipher being found, but, instead
saw another "PuTTY Fatal Error" window open, this time with the message
"Network error: Software caused connection abort". I saw the same error
message when I used PuTTY's plink utility from the command line.
C:\Program Files\Network\SSH\PuTTY>plink -ssh jdoe@192.168.0.15
Using username "jdoe".
jdoe@192.168.0.15's password:
FATAL ERROR: Network error: Software caused connection abort
I installed Bitvise
SSH Client (Tunnelier) 6.08 and tried connecting with
that client. Like with PuTTY, after I authenticated with the SSH server, I
was immediately disconnected. I saw the following from Tunnelier:
First key exchange completed using ecdh-sha2/nistp521. Session encryption:
aes256-ctr, MAC: hmac-sha2-256, compression: none.
Attempting password authentication.
Authentication completed.
The SSH2 session has terminated with error. Reason: FlowSocketReader: Error
receiving bytes. Windows error 10054: An existing connection was forcibly closed
by the remote host.
When I was able later to connect to the system running Copssh via
RDP for
troubleshooting after the user had left for the day, I
checked its status log, which you can do on a Windows 7 system by the following
steps:
- Click on Start.
- Select All Programs.
- Select Copssh.
- Select Copssh Control Panel.
- Under the Status tab, you will see
an icon that looks like a piece of paper with one edge folded down. You
may also see something like "6 events last 15 minutes" next to it.
Double-click on that icon.
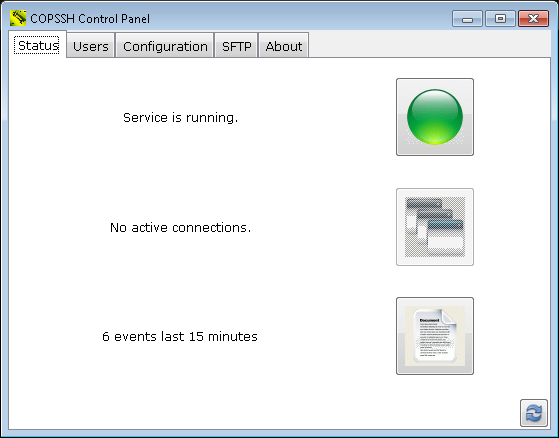
When I checked the log, I saw many "fatal: mm_request_receive: read: Connection reset by peer" messages. There was a "Received SIGHUP; restarting" entry
hours later.
2014.12.12 23:26:23 - Received SIGHUP; restarting.
2014.12.12 18:30:02 - fatal: mm_request_receive: read: Connection reset by peer
Seeing that, I tried establishing a connection with PuTTY again
and was then able to log in by SSH successfully.
But then when I tried logging in remotely by SSH two days later the problem
was back. I restarted the service within the Copssh Control Panel by clicking
on the green button next to "Service is running" to stop the service. When
the button turned red, I clicked on it again to restart the service, but that
didn't resolve the problem; I still got the "Network error: Software
caused connection abort" message when I tried connecting via PuTTY 0.63 and
I saw the "fatal: mm_request_receive: read: Connection reset by peer" message
in the Copssh log for evey connection attempt. Though I didn't expect it
to resolve the problem, I tried the "net stop" and "net start" commands from
a command prompt.
C:\Users\Administrator>net stop "OpenSSH SSHD"
The Openssh SSHD service is stopping.
The Openssh SSHD service was stopped successfully.
C:\Users\Administrator>net start "OpenSSH SSHD"
The Openssh SSHD service is starting.
The Openssh SSHD service was started successfully.
But that did work. I was then able to successfully log into the system
via SSH.
[/os/windows/network/ssh/copssh]
permanent link
Sun, Dec 14, 2014 5:10 pm
Ripping a CD with Microsoft Windows Media Player 12
To rip a CD to the music libary stored on your system, i.e., to copy the music
from the CD to the hard drive on a Windows sytem, using Windows Media Player
12, take the following steps:
-
Insert the CD in the CD/DVD drive in the system.
-
Start the Windows Media Player application.
-
On the left pane of the Windows Media Player window, navigate
to the location of the CD/DVD drive, which should be displaying the
album as shown below where the album is identified as "unknown album"
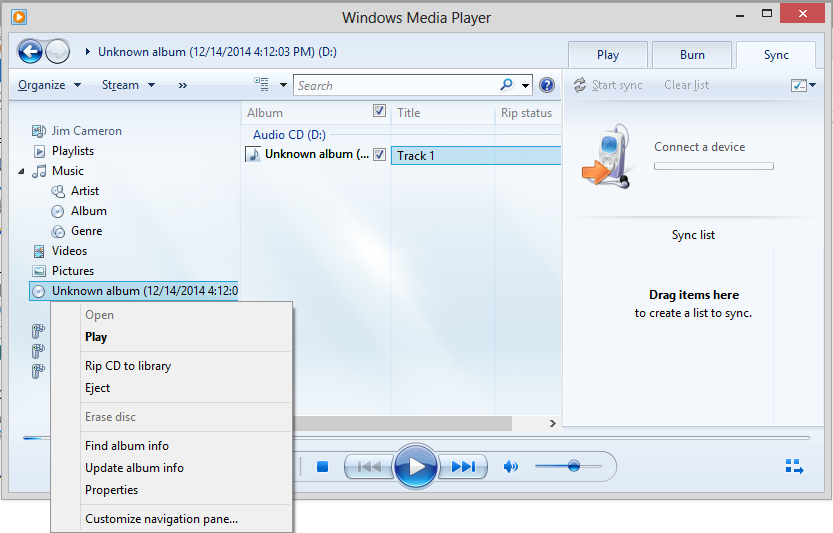
-
Right-click on the CD in the left pane of the window and choose "Rip CD to
library. As the CD is "ripped", you should see the status displayed
under "Rip status" near the top of the window; status information is
also displayed in the lower, right-hand side of the window.
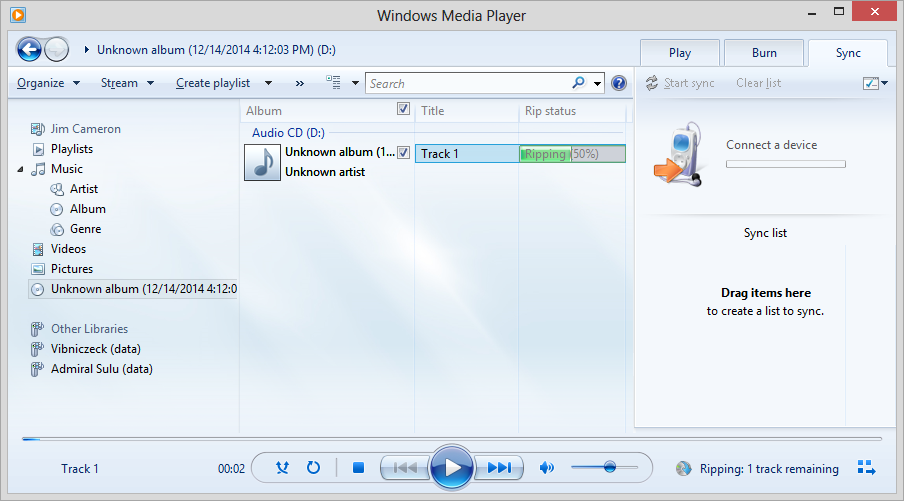
The status under "Rip status" should change to "Ripped to library" at
the completion of the rip process.
On a Microsoft Windows 7 system, you should then see the name of the
album in your music folder under Libraries\Music or
C:\Users\Username\Music\, where Username is
the name for the account under which you logged into the system, if you
look for it using the Windows Explorer. If the
album/artist could not be identified by Windows Media Player, you may
see an "Unknown artist" folder with an "Unknown album" folder within it.
From the Windows Explorer, you can right-click on the folder names and
change them, if you wish.
[/os/windows/software/audio-video/WMP]
permanent link
Fri, Dec 12, 2014 11:54 pm
DNSQuerySniffer v1.35
I installed DNSQuerySniffer v1.35 on a Microsoft Windows Professional
system which has been generating a lot of unusual DNS and HTTP traffic
even when the owner of the system is not using the system. E.g., I've seen
a lot of such traffic overnight, far more than can be accounted for by
normal processes running and checking on available updates, etc. And the
websites being contacted are not ones I would expect to be contacted.
DNSQuerySniffer allows the DNS queries and responses from DNS servers to
the system on which the software is installed to be monitored and captured for
later analysis.
[
More Info ]
[/os/windows/software/network/dns]
permanent link
Wed, Dec 10, 2014 11:53 pm
SysRescueCd
If you need to boot a system outside of the operating system residing on its
hard disk drive, a
live CD or
DVD provides a means to boot the system from an optical drive with an
operating system that is on the CD or DVD. There are many Linux-based live CDs,
which can be used to boot and troubleshoot systems running Microsoft Windows as
well as those running Linux. Many Linux-based live CDs have antivirus, backup
utilities, etc. that facilitate troubleshooting and maintenance of Windows
systems. One such live CD is
SystemRescueCd.
[ More Info ]
[/os/unix/linux]
permanent link
Tue, Dec 09, 2014 11:32 pm
Microsoft Visual C++ Runtime Error from Dell Stage
On a Dell desktop system running Microsoft Windows 7 Professional,
for awhile now whenever the user logged into her account, a Microsoft Visual
C++ Runtime Library window opened with the following information displayed:
Runtime Error!
Program: C:\...
This application has requested the Runtime to terminate it in an
unusual way.
Please contact the application's support team for more information.
[ OK ]
Checking on the application that was creating the window, I found it
to be "Dell Stage", which was software preinstalled on the system, which
I uninstalled.
[ More Info ]
[/os/windows/software]
permanent link
Sun, Dec 07, 2014 10:45 pm
Scan of Windows system with Malwarebytes Anti-Malware on 2014-12-07
When I scanned a Windows 7 Professional system with Malwarebytes Anti-Malware
it reported a file associated with
PUP.Optional.TorchMedia, which I had it
remove.
[ More Info ]
[/security/malware]
permanent link
Sun, Dec 07, 2014 7:30 pm
Rotate the DNS server log file on a Windows server
For a site where a
Windows Small Business Server (SBS) 2003 system serves as a
DNS server, I
wanted to rotate the DNS log file every night at midnight. The log file is
named
DNS.log and I'd like to close the current log at
midnight renaming it to
DNS_YYYYMMDD.log where YYYY is the 4-digit
year, MM, the month (1-12) and DD the day (1-31). The system date can be put in
the format
YYYYMMDD using substring extraction as explained at
Appending a date to a filename in
batch files.
Renaming the log file requires stopping the DNS server service, which
can be done with the command net stop "DNS Server". If
you try to move the file without stopping the service, you will receive
the message below:
D:\Logs\DNS>move dns.log dns_old.log
The process cannot access the file because it is being used by another process.
0 file(s) moved.After the file is moved/renamed, the DNS server service can be restarted
with net start "DNS Server".
The location of the DNS log file is stored in the Windows Registry. A
REG QUERY command can be used to obtain the current location for
the file as explained at
Determing the location of a Microsoft Windows DNS log file from a command prompt. After the location and name of the file is determined, the DNS server
service can be stopped, then the current log file can be renamed, and the
DNS server service can be restarted, creating a new log file with the name
and at the location indicated by the registry entry.
The batch file is shown below and is available
here.
@echo off
REM Name: rotatednslog.bat
REM Version: 1.0
REM Created: December 6, 2014
REM Last Modified: December 6, 2014
REM
REM: Location of latest version:
REM: http://support.moonpoint.com/downloads/computer_languages/mswin_batch/rotatednslog.bat
REM
REM Description: When scheduled to run at the end of each day, this batch
REM file will roate the DNS server log. The DNS server service will be
REM stopped temporarily, so the current DNS log can be renamed to a log file
REM with the name DNS_YYYYMMDD.log, where YYYY is the year, MM the month, and
REM DD the day. The DNS server service will then be restarted creating a
REM new DNS log file. The current location of the DNS log file is obtained
REM from the Windows Registry.
REM Required for substituting the contents of a variable in string subsitution
REM employed to insert the contents of the date variable YYYYMMDD in the log
REM file name.
SETLOCAL ENABLEDELAYEDEXPANSION
REM Windows Registry key holding the location of the DNS log file
SET regkey="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters"
REM Registry value needed from the above key
SET regvalue="LogFilePath"
REM Extract only the file location from the output of the reg query command
FOR /F "tokens=3" %%G IN ('reg query %regkey% /v LogFilePath ^| find %regvalue%') DO set logfile=%%G
REM Set the variable YYYYMMDD to today's date in YYYYMMDD format where
REM YYYY = 4-digit year, MM is month (1-12), and DD is day (1-31)
SET YYYYMMDD=%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%
REM Set the name for the rotated log file to have "_YYYYMMDD.log" at the
REM end of the file name. Need to use delayed expansion.
SET renamedlog=!logfile:.log=_%YYYYMMDD%.log!
REM Stop the DNS server service
NET STOP "DNS Server"
REM Move the log file to its new location with its new name.
REM Since you cannot specify a new drive or path for your destination file with
REM the RENAME command, I'm using the MOVE command, instead, in case I may
REM wish to update this batch script to move the file to another drive and/or
REM directory.
MOVE %logfile% %renamedlog%
REM Restart the DNS server service
NET START "DNS Server"
If it is run from a command prompt, you will see the following output:
C:\Program Files\Utility\Scripts>rotatednslog
The DNS Server service is stopping.
The DNS Server service was stopped successfully.
1 file(s) moved.
The DNS Server service is starting.
The DNS Server service was started successfully.Since I would like the batch file to execute at the end of each day, I
scheduled it to run at 23:59 (11:59 PM) Monday through Sunday with the command
at 23:59 /every:m,t,w,th,f,s,su
"C:\program files\utility\scripts\rotatednslog.bat (specify the location
for the batch file).
C:\Program Files\Utility\Scripts>at 23:59 /every:m,t,w,th,f,s,su "C:\program files\utility\scripts\rotatednslog.bat"
Added a new job with job ID = 5
I could have used 00:00 to run the batch job at midnight, but
I set it to run 1 minute before midnight to be sure that the date inserted
in the name of the file is the one for the day that has just ended rather than
the date of the new day.
If you want to see the details of scheduled batch jobs, you can just
enter at without any parameters at the command line and hit
return. You will then see all the scheduled batch jobs. There may be gaps
in the ID numbers if some batch jobs have been deleted.
C:\Documents and Settings\Administrator>at
Status ID Day Time Command Line
-------------------------------------------------------------------------------
1 Each M T W Th F S 7:30 PM d:\backups\daily.bat
2 Each Su 7:30 PM d:\backups\weekly.bat
5 Each M T W Th F S Su 11:59 PM "C:\program files\utility\scripts\rotatednslog.bat"If you wish to delete a scheduled batch job you can use
at id /delete, where id is the numeric
ID assigned to a batch job. E.g., the rotatednslog batch job above could
be deleted with at 5 /delete.
[/network/dns/windows]
permanent link
Fri, Dec 05, 2014 11:27 pm
Determine the file name and extension from a string containing path and filename
For Microsoft Windows systems, if you have a string or variable holding the
complete path to a file and the file name and extension, but you wish to have
just the file name and the extension of the file you can use
%~nx1
which will expand the batch parameter expansion variable
%1 to a
file name and extension.
Other modifiers you can use in expansion are as follows:
| Modifier | Description |
|---|
| %~1 |
Expands %1 and removes any surrounding quotation marks (""). |
| %~f1
| Expands %1 to a fully qualified path name. |
| %~d1 |
Expands %1 to a drive letter. |
| %~p1 |
Expands %1 to a path. |
| %~n1 |
Expands %1 to a file name. |
| %~x1 |
Expands %1 to a file extension. |
| %~s1 |
Expanded path contains short names only. |
| %~a1 |
Expands %1 to file attributes. |
| %~t1 |
Expands %1 to date and time of file. |
| %~z1 |
Expands %1 to size of file. |
| %~$PATH:1 |
Searches the directories listed in the PATH environment variable and
expands %1 to the fully qualified name of the first one found. If the
environment variable name is not defined or the file is not found, this
modifier expands to the empty string. |
Combinations of modifiers and qualifiers that you can use to get compound
results are shown in the table below:
| Modifier | Description |
|---|
| %~dp1 |
Expands %1 to a drive letter and path. |
| %~nx1 |
Expands %1 to a file name and extension. |
| %~dp$PATH:1 |
Searches the directories listed in the PATH environment variable for %1
and expands to the drive letter and path of the first one found.
|
| %~ftza1 |
Expands %1 to a dir-like output line. |
In the examples above, you can use other batch paramters besides
%1 and PATH. Cmd.exe provides the batch parameter
expansion variables %0 through %9.
Batch parameters can't be manipulated in the same manner that you can
manipulate environment variables. You can't search and replace values or
examine substrings within them. You can, however, assign the parameter to an
environment
variable and then manipulate the environment variable.
So, if I wanted just the file name dns.log from
d:\logs\dns.log, I could use the following in a batch file:
@echo off
call :getfilename "d:\logs\dns.log"
exit /b
REM Determine just the file name
:getfilename
echo %~nx1
If I have the above batch commands in a file called test.bat,
I would see the following when I ran it.
C:\Users\JDoe>test.bat
dns.log
If there is a
Windows Registry key containing the file location and I want to query
that key and extract just the file name, I could use commands such as
the following if the file location was stored in LogFilePath
for the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters:
@echo off
REM Regkey is set to the registry key containing the location of the DNS log
REM file
set regkey="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters"
REM Regvalue is set to the value that is desired from the above registry key
set regvalue="LogFilePath"
REM log_file_location is set to contain the complete path to the log file nad
REM its name, e.g., d:\logs\dns\dns.log
FOR /F "tokens=3" %%G IN ('reg query %regkey% /v LogFilePath ^| find %regvalue%') DO set log_file_location=%%G
call :getfilename %log_file_location%
exit /b
REM Determine just the file name
:getfilename
echo %~nx1
References:
-
Using batch parameters
Microsoft Corporation
-
Determing the location of a Microsoft Windows DNS log file from a command prompt
Date: November 22, 2014
MoonPoint Support
[/os/windows/commands]
permanent link
Fri, Dec 05, 2014 12:45 pm
Using tcpdump on OS X
When I tried running
tcpdump
on a MacBook Pro laptop running Mac OS X 10.8.5 from an account that
was configured to "Allow user to administer this computer" in System
Preference/Users & Groups, I received a "no suitable device found" message.
$ tcpdump
tcpdump: no suitable device found
The problem can be addressed by changing the ownership or permissions
of the Berkeley Packet Filter (BPF) file in /dev. The default
permissions and ownership are shown below:
$ ls -l /dev/bpf*
crw------- 1 root wheel 23, 0 Nov 30 22:42 /dev/bpf0
crw------- 1 root wheel 23, 1 Dec 4 21:45 /dev/bpf1
crw------- 1 root wheel 23, 2 Dec 4 15:39 /dev/bpf2
crw------- 1 root wheel 23, 3 Nov 30 22:41 /dev/bpf3
To resolve the problem, I changed the ownership of the bpf0
file to the account I was using:
$ sudo chown jdoe /dev/bpf0
Password:
I also checked to see what the designation was for the wireless adapter
in the system. It was en1.
$ networksetup -listallhardwareports
Hardware Port: Bluetooth DUN
Device: Bluetooth-Modem
Ethernet Address: N/A
Hardware Port: Ethernet
Device: en0
Ethernet Address: d4:9a:20:0d:e6:cc
Hardware Port: FireWire
Device: fw0
Ethernet Address: d4:9a:20:ff:fe:0d:e6:cc
Hardware Port: Wi-Fi
Device: en1
Ethernet Address: f8:1e:df:d9:2b:66
VLAN Configurations
===================
I then tried again to run tcpdump specifying the wireless interface; this
time I received a "You don't have permission to capture on that
device message with a reference to bfp1, so I changed
the ownership on that file as well. I was then able to observe
traffic with tcpdump.
$ sudo chown jdoe /dev/bpf0
$ tcpdump -i en1
tcpdump: en1: You don't have permission to capture on that device
((no devices found) /dev/bpf1: Permission denied)
$ sudo chown jdoe /dev/bpf1
$ tcpdump -i en1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on en1, link-type EN10MB (Ethernet), capture size 65535 bytes
I changed the ownership back to root on /dev/bpf0 to see if I could still run
tcdump, but when I did so I was no longer able to observe network traffic with
tcpdump.
$ sudo chown root /dev/bpf0
$ tcpdump -i en1
tcpdump: en1: You don't have permission to capture on that device
((no devices found) /dev/bpf0: Permission denied)
I could have just changed ownership of all of the bpfx files
in /dev initially with sudo chown jdoe /dev/bbf*, but
I wanted to determine if I only needed to change a specific one for the wireless
interface, en1. Alternatively one can expand the
permissions on those files, e.g., one can use sudo chmod 644
/dev/bpf*. When the system is rebooted the permissions/ownership
will be reset, so you will have to take the same steps to run tcpdump
subsequent to a reboot of the system.
I specifically wanted to check on
DNS
queries, so, after changing the ownership for the bpf file back to the account
I was using, I specified port 53, but saw no data.
$ tcpdump -i en1 'port 53'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
I wasn't able to observe the DNS traffic until I ended the
VPN connection I was using
when I ran the command. Once I disconnected from the VPN, I was able
to check on the DNS queries from the system and the responses from a DNS
server.
References:
-
Tcpdump Permission Denied on OS-X
Date: June 12, 2007
MoonPoint Support
-
Managing Wi-Fi from the terminal command line under OS X
Date: February 28, 2014
MoonPoint Support
-
No Interfaces Available In Wireshark Mac OS X
Date: January 31, 2010
langui.sh Languishing since 2008.
[/os/os-x]
permanent link
Tue, Dec 02, 2014 9:45 pm
Shellshock Vulnerability on OS X Systems
You can test a system to determine if it may be vulnerable to being
exploited through the
shellshock, aka bashdoor, vulnerability using the command
env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'.
If it is vulnerable, you will see the commands executed that appear after
the semicolon. On vulnerable systems,
Bash is
executing commands that are concatenated at the end of function
definitions stored in the contents of environment variables.
When I checked a MacBook Pro running, OS X 10.8.4, I saw output indicating
it was vulnerable, i.e., I saw "vulnerable" displayed when the command was run.
The check can be performed by opening a Terminal window and entering the code.
The terminal application is in Applications/Utilities.
$ env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'
vulnerable
this is a testA bash shell prompt could be otained by a malicious remote user
if Remote Login was enabled and Guest Access was also enabled,
though, hopefully, if Remote Login was enabled, Guest Access would
not be enabled. Of course, a malicious person could also gain access to the
system remotely if Remote Login is enabled and a weak password is present
for an account on the system that is allowed remote access.
A OS X system could also be vulnerable if it is functioning as a web
server and there are scripts present on the server that would allow an
attacker to provide any input he wishes that could be executed as code by the
script.
Apple released a fix for the vulnerability for OS X systems on September
29, 2014.
After the laptop was upgraded to OS X 10.8.5 and security updates were
applied, I didn't see "vulnerable" displayed when the code was executed.
$ env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'
this is a testAnd when I tested the related vulnerability
CVE-2014-7169, the date was no longer displayed.
$ env X='() { (a)=>\' sh -c "echo date"; cat echo
date
cat: echo: No such file or directory
A system that has been patched for both
CVE-2014-6271 and CVE-2014-7169 will simply echo
the word "date" and the file "echo" will not be created, as shown above.
References:
-
Shellshock Vulnerability: What Mac OS X users Need to Know | The Mac
Security Blog
By
Derek Erwin
Date: September 26, 2014
Intego - Mac Antivirus & Security
-
Shellshock (software bug)
Wikipedia
[/security/vulnerabilities/multios]
permanent link
Mon, Dec 01, 2014 10:32 pm
Searching for messages in Outlook 2010
Microsoft Outlook 2010 provides a means to quickly search through email
for particular messages by specifying multiple criteria in its search
field. It also provides the means to use
logical operators,
such as
NOT to exclude some messages that you deem not pertinent.
[ More Info ]
[/network/email/clients/outlook]
permanent link

Privacy Policy
Contact










