Anomalous Windows XP Firewall Rules
When checking the firewall settings on a Windows XP Service Pack 2
system tonight, I found several anomalous firewall rules. The system
is running the Windows XP firewall.
When I checked the firewall openings with the netsh firewall show
state command, I didn't see anything unusual.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Enable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
135 TCP IPv4 (null)
137 UDP IPv4 (null)
139 TCP IPv4 (null)
138 UDP IPv4 (null)
9370 UDP IPv4 C:\Program Files\Logitech\Desktop Messenger\8876480\Pr
ogram\LogitechDesktopMessenger.exe
3389 TCP IPv4 (null)
445 TCP IPv4 (null)
22 TCP IPv4 C:\Program Files\Network\OpenSSH\usr\sbin\sshd.exe
Nor did I see anything unusual when I issued the command
netsh firewall show portopening.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
22022 TCP Enable OpenSSH
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
However, when I went to the
GUI for configuring the
firewall to correct an mistake I noticed in the firewall configuration, I
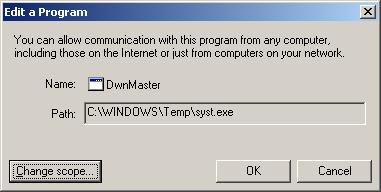
saw DwnMaster listed. I didn't know what that program was
nor why it needed a firewall rule.

Double-clicking on DwnMaster showed that the program
associated with the firewall rule was syst.exe in
C:\WINDOWS\Temp.
When I checked to see if syst.exe was running, I didn't
see evidence of it running.
C:\>tasklist /fi "imagename eq syst.exe"
INFO: No tasks running with the specified criteria.
And when I checked for the existence of the file, however, though
I found it, it was only zero bytes in length. I am presuming
that it was nullified during an antivirus or antispyware
scan of the system.
C:\>dir c:\windows\temp\syst.exe
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\windows\temp
02/02/2007 03:32 AM 0 syst.exe
1 File(s) 0 bytes
0 Dir(s) 57,556,082,688 bytes free
Looking at the "allowed programs" list for the firewall, I noticed another
unusual entry, C:\win.com.
C:\>netsh firewall show allowedprogram
Allowed programs configuration for Domain profile:
Mode Name / Program
-------------------------------------------------------------------
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable DwnMaster / C:\WINDOWS\Temp\syst.exe
Enable TCP / C:\WIN.COM
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
Allowed programs configuration for Standard profile:
Mode Name / Program
-------------------------------------------------------------------
Enable restorea0 / c:\windows\system32\restorea0.exe
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
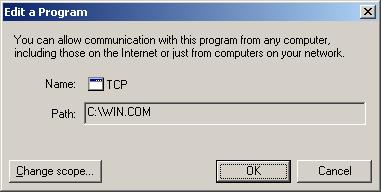
The name given to it was TCP, apparently in an attempt to
make it less likely to stand out as possible malware.
But I wouldn't expect to find a win.com file in the
root directory of a Windows XP system.
It was also a zero byte file when I checked for its existence, however, so
may also have been nullified by a previous scan of the system with antivirus
or antispyware software.
C:\>dir c:\win.com
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\
02/09/2007 02:47 AM 0 WIN.COM
1 File(s) 0 bytes
0 Dir(s) 57,555,771,392 bytes free
Another allowed program that looked suspicious was
restorea0 in
c:\windows\system32\.
But when I looked for it, I did not see it on the system. So
it may have been removed completely by antivirus or antispyware software
previously. At
FKIYY.EXE
Spyware Remove, I found it listed as one of many alternative names
associated with malware detected by Prevx.
At
SYST.EXE Spyware Remove, Prevx lists syst.exe as being
associated with Trojan Downloader Small yt. At
WIN.COM
Spyware Remove, win.com is linked to
Adware Virtumonde
[/os/windows/xp/firewall]
permanent link
RPC Server Unavailable Because of XP Firewall
If you get an "RPC server unavailable" error message when attempting
to remotely query or administer a Windows XP
SP 2 system, even though the
RPcSs service is running on the remote XP system, you may need to
adjust the group firewall policy for the domain.
[ More Info ]
[/os/windows/xp/firewall]
permanent link
Obtaining Information About the Windows XP Firewall from the Command Line
If you wish to check the state of the Microsoft Windows XP firewall software,
you can issue the following command from a command line prompt.
C:\Documents and Settings\Administrator>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Standard
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = None
Remote admin mode = Disable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
10243 TCP IPv4 (null)
10280 UDP IPv4 (null)
10281 UDP IPv4 (null)
10282 UDP IPv4 (null)
10283 UDP IPv4 (null)
10284 UDP IPv4 (null)
20099 TCP IPv4 C:\Program Files\Network\SSH\OpenSSH\usr\sbin\sshd.exe
3389 TCP IPv4 (null)
42599 TCP IPv4 C:\Program Files\Network\pcAnywhere\awhost32.exe
42600 UDP IPv4 C:\Program Files\Network\pcAnywhere\awhost32.exe
2869 TCP IPv4 (null)
1900 UDP IPv4 C:\WINDOWS\system32\svchost.exe
The command also shows the open ports and applications that have opened
particular ports.
You can also request information just on open ports with netsh
firewall show portopening as below.
C:\Documents and Settings\Administrator>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
20099 TCP Enable SSH
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
3389 TCP Enable Remote Desktop
You may notice that the second example doesn't list the two ports
opened by pcAnywhere, TCP port 42599 and UDP port 42600 (the system is
using non-standard pcAnywhere ports), which are listed in the first
example. That is because those ports were allowed to be open in the
firewall not by designating the specific ports as allowed, but by
specifying the program that opens them as an "allowed program". You
can see the allowed programs by using the command netsh firewall
show allowedprogram.
C:\Documents and Settings\Administrator>netsh firewall show allowedprogram
Allowed programs configuration for Domain profile:
Mode Name / Program
-------------------------------------------------------------------
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Allowed programs configuration for Standard profile:
Mode Name / Program
-------------------------------------------------------------------
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable pcAnywhere Main Executable / C:\Program Files\Network\pcAnywhere\Winaw32.exe
Enable pcAnywhere Host Service / C:\Program Files\Network\pcAnywhere\awhost32.exe
Enable pcAnywhere Remote Service / C:\Program Files\Network\pcAnywhere\awrem32.exe
Enable proxy / C:\Program Files\Network\Proxy\proxy.exe
In the above example, the AnalogX
Proxy program, proxy.exe, is allowed to open ports, though it was not running
at the time the command was issued and therefore hasn't opened any ports.
If you just want to know whether the firewall is enabled, you can use
the netsh firewall show service command.
C:\Documents and Settings\Administrator>netsh firewall show service
Service configuration for Domain profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No UPnP Framework
Service configuration for Standard profile:
Mode Customized Name
-------------------------------------------------------------------
Enable No UPnP Framework
Enable No Remote Desktop
Other firewall "show" commands that are available are listed below.
C:\Documents and Settings\Administrator>netsh firewall show
The following commands are available:
Commands in this context:
show allowedprogram - Shows firewall allowed program configuration.
show config - Shows firewall configuration.
show currentprofile - Shows current firewall profile.
show icmpsetting - Shows firewall ICMP configuration.
show logging - Shows firewall logging configuration.
show multicastbroadcastresponse - Shows firewall multicast/broadcast response configuration.
show notifications - Shows firewall notification configuration.
show opmode - Shows firewall operational configuration.
show portopening - Shows firewall port configuration.
show service - Shows firewall service configuration.
show state - Shows current firewall state.
[/os/windows/xp/firewall]
permanent link
Configuring Windows XP Firewall for OpenSSH
If you want to set up a Windows system as an SSH server, you can use
OpenSSH for Windows.
OpenSSH for Windows can be installed on Windows NT, 2000, XP, or Small
Business Server (SBS) 2003 systems. If you are installing it on a
Windows XP system with the Windows firewall activated, which will likely
be the case if Service Pack 2 has been installed on the system, then
you will need to create a firewall rule to allow SSH connectivity.
[ More Info ]
[/os/windows/xp/firewall]
permanent link
Remotely Disabling Windows XP Firewall
The Windows XP Firewall, which is turned on by default on systems
running Windows XP Service Pack 2, unless they are in a domain with
a Windows SBS 2003 server with an early version of Windows SBS 2003,
can be turned off from another machine in the domain by using
"Computer Management".
[
More Info ]
[/os/windows/xp/firewall]
permanent link





