←September→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| |
1 |
2 |
3 |
4 |
5 |
6 |
| 7 |
8 |
9 |
10 |
11 |
12 |
13 |
| 14 |
15 |
16 |
17 |
18 |
19 |
20 |
| 21 |
22 |
23 |
24 |
25 |
26 |
27 |
| 28 |
29 |
30 |
|
|
|
|
|
|
Fri, Sep 26, 2008 12:51 pm
Maillog Not Rotating
The
maillog file in
/var/log had been rotated
every night to produce
maillog.1,
maillog.2, etc.
on a
CentOS Linux server. But the
log file rotation stopped at some point and the
maillog file
has been growning huge. The file contains entries related to messages
processed by sendmail on the system.
In email from the Cron Daemon to the root account, I found messages with the
following within them:
/etc/cron.daily/logrotate:
error: syslog:1 duplicate log entry for /var/log/maillog
I checked /etc/logrotate.conf, but didn't find any references
to rotation of the maillog file there.
Contents of /etc/logrotate.conf:
# see "man logrotate" for details
# rotate log files weekly
weekly
# keep 4 weeks worth of backlogs
rotate 4
# create new (empty) log files after rotating old ones
create
# uncomment this if you want your log files compressed
#compress
# RPM packages drop log rotation information into this directory
include /etc/logrotate.d
# no packages own wtmp -- we'll rotate them here
/var/log/wtmp {
monthly
minsize 1M
create 0664 root utmp
rotate 1
}
# system-specific logs may be also be configured here.
I then checked the /etc/logrotate.d directory. I found
maillogrotate there.
Contents of /etc/logrotate.d/maillogrotate:
# Begin maillogrotate control file
/var/log/maillog {
daily
rotate 14
sharedscripts
create 0600 root root
missingok
postrotate
/bin/kill -HUP `cat /var/run/syslogd.pid 2> /dev/null` 2> /dev/null || true
endscript
}
# End maillogrotate control file
I also checked the /etc/logrotate.d/syslog file, since syslog
may rotate the file.
Contents of /etc/logrotate.d/syslog:
/var/log/messages /var/log/secure /var/log/maillog /var/log/spooler /var/log/boot.log /var/log/cron {
sharedscripts
postrotate
/bin/kill -HUP `cat /var/run/syslogd.pid 2> /dev/null` 2> /dev/null || true
/bin/kill -HUP `cat /var/run/rsyslogd.pid 2> /dev/null` 2> /dev/null || true
endscript
}
So it appears that both
the /etc/logrotate.d/maillogrotate and the
/etc/logrotate.d/syslog files were attempting to rotate
the maillog file on a daily basis.
Checking notes posted on my blog, I found I resolved the problem on another
email server, a Redhat Linux server, on Friday, September 17 of 2004, almost
exactly 4 years ago, and had
posted my notes in
Daily Rotation of Mail Logs. In that case, I had removed the
/var/log/maillog reference from
/etc/logrotate.d/syslog, so I did the same thing in this case
as well. But this time, I decided to leave the maillogrotate file
in /etc/logrotate.d.
Checking my notes for the CentOS email server, I see that I had in the past
removed the /var/log/maillog reference from
/etc/logrotate.d/syslog. Some installation or upgrade must of
led to the version of the file I created then being overwritten.
References:
-
[Rocks-Discuss] /var/log/maillog in syslog.conf vs. /var/log/mail in
logrotate.d/rocks
Date: September 13, 2006
SDSC Mailing List Server
-
Pflogsumm issues
Date: July 16, 2008
HowtoForge - Linux Howtos and Tutorials
-
Configuration: centos50
System Configuration Collector
(SCC)
-
What the hell is rotating my mail.log?
Date: February 23, 2007
Stephan Paukner
-
Rotating Linux Log Files - Part 1: syslog
Date: Nisan 22, 2007
Netlojik
-
Logging, Log File Rotation, and Syslog Tutorial
Wayne Pollock's Home Page
-
Daily Rotation of Mail Logs
Date: September 17, 2004
MoonPoint Support
[/network/email/sendmail]
permanent link
Tue, Sep 16, 2008 11:45 am
Did Al Gore Say He Invented The Internet?
The answer is "no". He did make a statement in an interview with Wolf Blitzer
of CNN about his role in the creation of the Internet, but that statement
was taken out of context to be used as a political attack tool. I've heard
Al Gore mocked many times for his supposed statement and found someone else
making what appeared to be a sarcastic comment in a post today to an
article "
The
Web back in 1996-1997"
As I posted there, I would like to point out that he never claimed to have
invented the Internet
(see the Snopes article "Internet of Lies"). For
a much fuller discussion of the topic and some history on
the Internet’s development and Gore’s role in
supporting advanced networking initiatives, I would recommend
“
Al Gore and the Creation of the Internet”
His early vision of its potential and his support for funding
of advanced networking activities was important. Vint Cerf,
who has, I think appropriately, been dubbed the “father
of the Internet” for his technical contributions, along
with Bob Kahn, in designing the Internet Protocol, has credited
Gore’s early support for advanced networking efforts (see "Vint Cerf responded to MSNBC").
I see the same tactic of taking an opponent’s statements
out of context being widely used in the current campaign by both
parties. Unfortunately, I suspect many Americans will make up their minds
based on what they see in political ads that are designed to mislead
them. The tactic used so successfully against Gore still works.
[/network/Internet]
permanent link
Tue, Sep 16, 2008 9:27 am
CA Anti-Spyware Scan of J
I checked a Windows XP Professional Service Pack 3 system, J, with
CA Anti-Spyware 2008 LE. That version is free and will detect malware,
but not remove it. You can purchase a license to have the software remove
any malware it finds.
[ More Info ]
[/security/spyware]
permanent link
Sun, Sep 14, 2008 7:55 pm
CopSSH Installation on Windows Vista
I installed
copSSH 1.4.6
on a Windows Vista Ultimate system. The software is an implementation of an
SSH server and client
for Windows systems. I had been using
OpenSSH for Windows 3.8.1p1
on Windows 2000 and XP systems, but I haven't been able to get it to work
under Windows Vista. I haven't had any problems getting copSSH to function
as an SSH server under Vista.
At the end of the installation,
the installation software displays the message below:
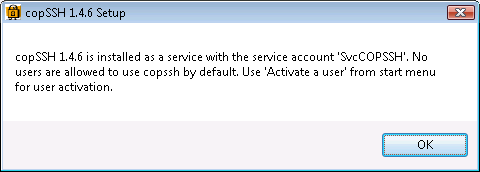
After the installation, I clicked on Start, selected All
Programs, then COPSSH, then Activate a User.
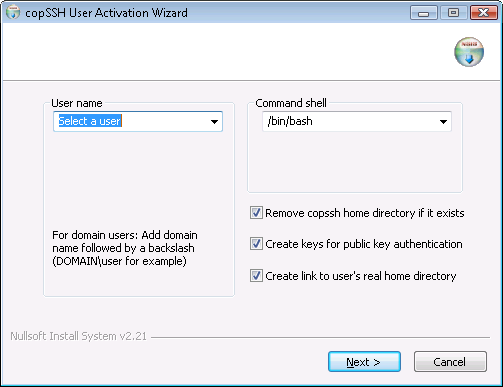
I selected a user and then proceeded to the next step where I typed in
a passphrase, which is used to protect the private key for the account.
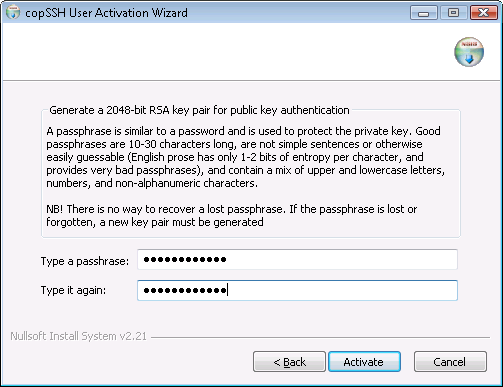
I then clicked on the Activate button, which produced the message
below.
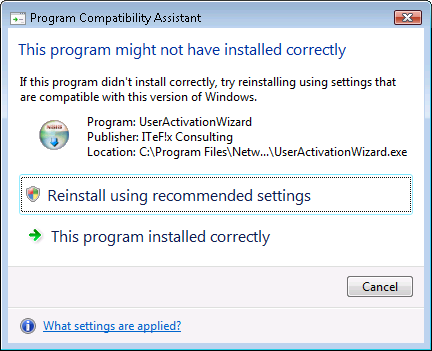
I selected the "This program installed correctly" option.
Since the system was using the firewall capability built into Windows Vista,
I then clicked on the Start button, selected Control Panel,
then Security then Windows Firewall, and then
Change Settings.
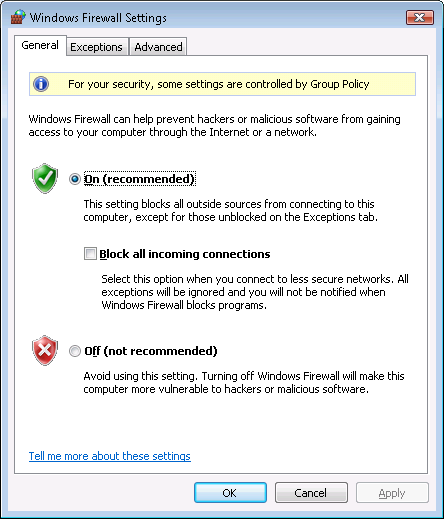
I clicked on the Exceptions tab and then selected Add Port.
At the Add Port window, I specified copSSH as the name
for the firewall port and the default SSH port, which is port 22. SSH uses
the TCP protocol.
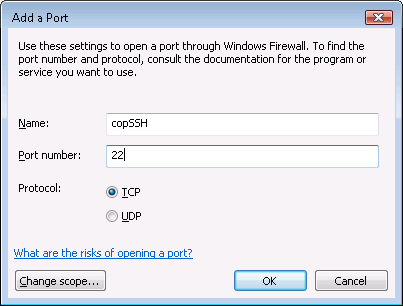
I clicked on Ok and then OK again to create the firewall rule
for copSSH. I was then able to use
PuTTY to log
into the system from another system.
If you would like to use another port other than the default port of 22,
you need to edit the sshd_config file, which you will find within
the etc directory beneath the directory in which you installed
copSSH, e.g. \Program Files\copSSH\etc\sshd_config.
I suggest
editing the file with WordPad rather than Notepad, because WordPad can handle
the end of line characters used in the file so that each line appears one
beneath the other rather than all lines appearing as one long line as they
will in Notepad. WordPad can deal with the end of line character used on Unix
and Linux systems better than Notepad. The file uses the linefeed character
common for files on Unix and Linux systems rather than the combination of
carriage return and linefeed characters that Microsoft Windows uses.
To change the port, locate the line below. Remove the "#" from the beginning
of the line, which turns the line into a comment line. Then replace 22 with
whatever number you wish to use for the port.
#Port 22
When you've changed the port, you will need to restart the SSH server service,
which you can do by rebooting or simply stopping and restarting the service.
To stop and restart the service from the command line, obtain a command prompt.
If you aren't logged into an administrator account, you can use the command
runas /user:administrator cmd from a command prompt to open
another command prompt window under the administrator account.
C:\>net stop "Openssh SSHD"
The Openssh SSHD service is stopping.
The Openssh SSHD service was stopped successfully.
C:\>net start "Openssh SSHD"
The Openssh SSHD service is starting.
The Openssh SSHD service was started successfully.
You can verify copSSH is listening on the new port using the
netstat command. E.g., if you set the port to 5622, you
could use the command below:
C:\>netstat -an | find "5622"
TCP 0.0.0.0:5622 0.0.0.0:0 LISTENING
[/os/windows/network/ssh/copssh]
permanent link
Sun, Sep 14, 2008 1:38 pm
Setting F-Secure Resce CD to Automatically Reboot
I needed to scan a system with an F-Secure Rescue CD 2.00. I started
the scan late at night and wanted to go home to sleep before the scan
completed. But I wanted the system to reboot into Microsoft Windows
after the scan was completed. Since the results of the scan are
stored in
/tmp, which exists only in the system's memory
when the system is booted from the F-Secure Rescue CD, I also wanted
the output log files produced by the scanning process to be stored
somewhere where I could access them after the reboot.
When a scan is started, the following is displayed:
Scanning
Scanning all filesystems mounted under /mnt/scan/ directory.
The results of the scan will be saved in /tmp/scan_results.txt
Alt-F1 This screen.
Alt-F5 To see details of files being scanned.
Alt-F6 To see any malware found.
Ctrl-C TO cancel scanning.
You can also use Alt-F2, Alt-F3, or Alt-F4 to
get a shell prompt. I used Alt-F2 to obtain a shell prompt.
When a system is booted from the rescue CD, the hard drive on the system
is mounted under /mnt/scan. In this case, the hard drive is an
IDE
drive designated as hda2 by Linux, which is the operating system
used on the F-Secure Rescue CD. So I could store the log files, which are as
follows, somewhere under /mnt/scan/hda2.
scan_error.txt
scan_log.txt
scan_results.txt
On this system there was a C:\TEMP directory, so I decided
to store them there. You can see the directories on the hard drive using
the ls command, e.g. ls /mnt/scan/hda2/.
Using the pico editor on the CD, I created a script,
which I named rebootwin in the
/tmp directory to automatically reboot the system after 9 hours,
presuming that the scan of the system should certainly be completed within
that time (it took about 3 hours).
root@tty2[/]# cd /tmp
root@tty2[tmp]# pico rebootwin
I put the following commands in the script:
#!/bin/bash
date
sleep 9h
cp scan*.txt /mnt/scan/hda2/TEMP/.
reboot
The script prints the date and time and then "sleeps" for 9h. When that
amount of time has elapsed, it copies the log files from the scanning
process from the /tmp directory to the C:\TEMP
directory on the system's hard drive. The system is then rebooted. If
the system is set to boot from the hard drive first, rather than a CD-ROM
drive, it will boot into Windows from the hard drive. If the system's BIOS
is set to attempt to boot the system first from a CD in a CD-ROM drive, it will
reboot from the F-Secure Rescue CD, but, unless a key is hit within a few
seconds, it will not continue with a reboot into the antivirus scanning
software, but will instead boot from the system's hard drive.
I saved the script with Ctrl-X and then made the script executable
with the chmod command. I then started the script with
./rebootwin.
root@tty2[tmp]# chmod 755 test
root@tty2[tmp]# ./rebootwin
Sat Sep 13 23:52:46 UTC 2008
The next morning, I was able to check the results of the scanning process
by examing the log files on the system's hard drive.
[/security/antivirus/f-secure]
permanent link
Sat, Sep 13, 2008 11:31 pm
Scan of J with AVG and F-Secure Rescue CDs
I've been continuing to check a Windows XP Pro system, J, which became
infected on September 8, with programs to detect any malware that might
remain on the system. I used
AVG Rescue CD
and an
F-Secure Resce CD 2.00 to check the system tonight.
[
More Info ]
[/security/antivirus/f-secure]
permanent link
Sat, Sep 13, 2008 4:52 pm
Rootkit Checks on J on 2008-09-13
I had checked a system, J, that had malware on it earlier in the week with
the
rootkit detection
program,
BlackLight from
F-Secure. Today, I checked the
system with two other rootkit detection programs,
Rootkit Hook Analyzer
from
Resplendence Software
Projects and
RootkitRevealer from
Microsoft.
The software was originally developed by
Sysinternals; Microsoft acquired Sysinternals in 2006.
I did not find any rootkit software on the system with any of the 3 rootkit
revealers I used.
[ More Info ]
[/security/spyware]
permanent link
Wed, Sep 10, 2008 11:00 pm
Infection Checks on 2008-09-10
I ran further checks on September 10, 2008 on a system that I found infected
with
Virantix and other malware on September 9 (see
Infection by Virantix -
braviax.exe).
[ More Info ]
[/security/spyware]
permanent link
Wed, Sep 10, 2008 12:27 am
Infection by Virantix - braviax.exe
After a user attempted to open an attachment on an email message that
was ostensibly from Southwest Airlines, but which was really malware,
her system rebooted and kept popping up a ballon message from the system
tray that "It is recommended to use special antispyware tools to pervent
data loss. Windows will now download and install the most up-to-date
antispyware for you." The message, which misspelled "prevent" was really
coming from
rogue
antispyware software. Such messages are common to
rogue antispyware that attempts to trick users into buying the software after
the software has managed to surreptitiously install itself.
[ More Info ]
[/security/spyware]
permanent link
Wed, Sep 03, 2008 6:27 pm
Remembering Text for a Regexp Replacement in Vi
I needed to insert a space between months and years
in text in a document while using
Vim, a version of
the Vi editor for Windows systems. The text was as
shown below:
December1999 Edition
November1999 Edition
October1999 Edition
...
March1996 Edition
February1996 Edition
January1996 Edition
With Vi,
regular expressions
can be used to search for and replace text. In this case I could use
:.,$ s/199\(\d) Edition/ 199\1/ to perform the substitution.
To search from the line I was on to the end of the document I can use
.,$. With the substitute s command, you can search
and replace text with commands of
the form s/old text/new text. You can use the i
option, if you don't want the case of letters to be considered, i.e. if you
wish "A" and "a" to be treated the same, then you can use s/old text/new
text/i. You can use the g option, if you wish to replace
all occurrences of old text on the line, for cases where the
text may occur multiple times on the same line, e.g. s/old text/new
text/g. You can use whatever delimiter you wish to separate the
parts of the command, e.g. you can use s:old text:new text:.
The \d in the command indicates that I am only looking for
digits, i.e. 0 to 9. By enclosing the \d in parentheses, i.e.
by using (\d), I can have the editor "remember" whatever it
found between the parentheses. Then I can have it insert what it has
remembered in the replacement text by using \1. If I had
used multiple parentheses at various parts in the search text, then the
second string I wanted remembered would be indicated with a \2.
In this case the last digit of the year was all I wanted the editor to
remember and insert appropriately in the substitutiong text.
If you wish to search an entire document, you can use 1,$
to represent the first line of the file through the last line, or you
can just use % to represent the entire file.
:% s/199\(\d) Edition/ 199\1/
References:
-
Vim Regular Expressions - Substitute Command
[/software/editors/vi]
permanent link
Mon, Sep 01, 2008 3:34 pm
Rootkit Detection Software
Rootkits allow
a malefactor to take control of another's system. There are
free programs to help detect rootkits on a Windows system.
Two such programs are
BlackLight from
F-Secure and
RootkitRevealer from
Sysinternals,
which has been acquired by
Microsoft.
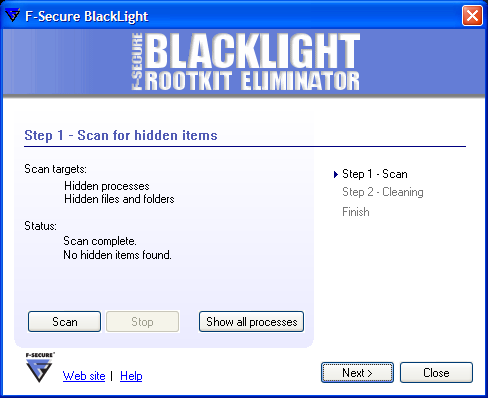
To use BlackLight, simply
download it and run the downloaded file. There is no installation process.
When the scan is completed, BlackLight will report whether it found any
hidden processes, files, or folders that may be part of a rootkit.
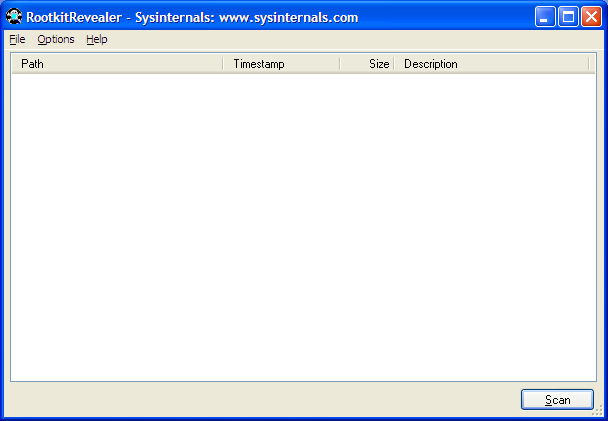
Analysis of the results of a RootkitRevealer scan requires more technical
competence as some of the entries you see listed in its report may be
normal for Windows systems and not necessarily a sign that the system
has been "rootkitted".
[/os/windows/software/security/antimalware/rootkit]
permanent link

Privacy Policy
Contact










