

|
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
But when I tried establishing a VNC connection to the system from another system on the same LAN, I could not establish the connection. Yet I could establish a VNC connection when I attempted to do so through an SSH tunnel, which led me to believe that the firewall software running on the eMac was blocking the connection.
I went to Sharing again on the system and selected Apple Remote Desktop and then clicked on the Firewall tab. I clicked on the padlock icon so I could edit the firewall settings. I then saw a message telling me that I couldn't change the settings when I clicked on Edit.
You cannot change the firewall settings for this service.
When you turn on Apple Remote Desktop in the Services pane, you also allow the service access through the firewall on TCP port(s) 3238 and UDP port(s) 3238. To stop access through the firewall you must turn off this service through the Services pane.
I didn't see a reference to the default VNC port of 5900, so
I opened a terminal window to check the firewall rules (Applications -
Utilities - Terminal) using the ipfw command. The
command has to be issued while logged into an account that
has administrator access on the system.
Maroon-Apple:~ JDoe$ sudo ipfw list Password: 02000 allow ip from any to any via lo* 02010 deny ip from 127.0.0.0/8 to any in 02020 deny ip from any to 127.0.0.0/8 in 02030 deny ip from 224.0.0.0/3 to any in 02040 deny tcp from any to 224.0.0.0/3 in 02050 allow tcp from any to any out 02060 allow tcp from any to any established 02065 allow tcp from any to any frag 02070 allow tcp from any to any dst-port 3238 in 02080 allow tcp from any to any dst-port 22 in 02090 allow tcp from any to any dst-port 548 in 02100 allow tcp from any to any dst-port 427 in 02110 allow tcp from any to any dst-port 139 in 02120 allow tcp from any to any dst-port 631 in 02130 allow tcp from any to any dst-port 515 in 12190 deny tcp from any to any 65535 allow ip from any to any
I could see that connections to port 3238 were
allowed, but there was no entry for port 5900, though
the system was listening on port 5900 as a
netstat -an command verified.
Haroon-Apple:~ Jim$ netstat -an | grep 5900 tcp4 0 0 *.5900 *.* LISTEN
To resolve the problem, with the Firewall tab selected under Sharing, I clicked on the New button. I then selected VNC for Port Name, which automatically selected TCP ports 5900-5902 and UDP port 5900.
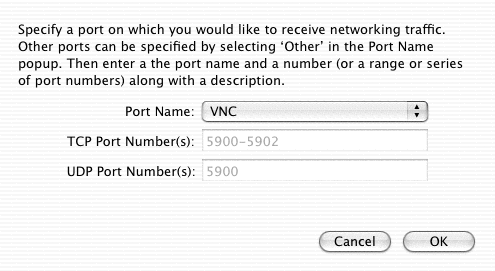
VNC then appeared in the list of services in the firewall
window with a checkmark next to it. When I checked the
firewall rules with the ipfw list command, I also
saw ports 5900 to 5902 listed.
$ sudo ipfw list Password: 02000 allow ip from any to any via lo* 02010 deny ip from 127.0.0.0/8 to any in 02020 deny ip from any to 127.0.0.0/8 in 02030 deny ip from 224.0.0.0/3 to any in 02040 deny tcp from any to 224.0.0.0/3 in 02050 allow tcp from any to any out 02060 allow tcp from any to any established 02065 allow tcp from any to any frag 02070 allow tcp from any to any dst-port 3238 in 02080 allow tcp from any to any dst-port 22 in 02090 allow tcp from any to any dst-port 548 in 02100 allow tcp from any to any dst-port 427 in 02110 allow tcp from any to any dst-port 139 in 02120 allow tcp from any to any dst-port 5900-5902 in 02130 allow tcp from any to any dst-port 631 in 02140 allow tcp from any to any dst-port 515 in 12190 deny tcp from any to any 65535 allow ip from any to any
I was then able to successfully connect to
the system from another Mac by putting
vnc://192.168.0.103 in the
address bar of Safari (192.168.0.103 was the
address of the system functioning as a VNC
server). When prompted for login credentials,
I could put in the userid and password
of an account on the system functioning
as the VNC server and log into it.
When I used it to connect to a Mac OS X system, I was warned that the connection would not be encrypted.
Unencrypted Connection
This connection will not be encrypted. Your authentication credentials will be transmitted securely, but all subsequent data exchanged while the connection is in progress may be susceptible to interception by third parties.
That's not a significant concern for me when both systems are on a Local Area Network (LAN) I control, but I normally tunnel VNC connections through an SSH connection when connecting over the Internet to ensure transmissions are encrypted.
Chrome OS on a Chromebook contains
A Secure Shell
(SSH) client application. To access it, hit the Ctrl-Alt-T
keys simultaneously, which will open a terminal window as a tab in the
Chrome browser. Type ssh at the "crosh>" prompt to access
the ssh client.
Welcome to crosh, type 'help' for a list of commands. crosh> ssh
Within the ssh application, typing help will show you a
list of the available commands.
ssh> help connect - connect dynamic-forward port - dynamic socks proxy (-D) forward port:host:port - static port forward (-L) help - this host <hostname> - remote hostname key <file> - sets private key to use (-i) nocmd - don't execute command (-N) port <num> - port on remote host (-p) server-alive-interval <num> - set ServerAliveInterval option exit - exit ssh subsystem user <username< - username on remote host Note that this program can only bind local ports in the range 8000-8999, inclusive. ssh>
If you wish to encrypt a Virtual Nework Computing (VNC) connection by tunneling it through an SSH connection, you will need to specify a port from 8000 to 8999 as the port to be used for forwarding the VNC traffic when using SSH under Chrome OS. You can do so using a forward command such as the following:
crosh> ssh ssh> user JDoe ssh> host my.example.com ssh> forward 8000:127.0.0.1:5900 ssh> connect
Then using the RealVNC
client for Chrome OS, you can specify 127.0.0.1:8000
or localhost::8000 as the address through
which to establish the VNC connection. You could also have
used forward 8000:localhost:5900 for the SSH
forwarding command. The address 127.0.0.1 is the
localhost
address and with the port number of 8000 tells VNC to try
establishing the VNC connection by connecting to port number 8000 on
the system on which VNC is running, i.e., the Chromebook. Because there
is an SSH tunnel through that port, SSH will route any traffic to TCP
port 8000 through its connection to port 5900 on the remote system.
You will still get the warning from the VNC Viewer about transmissions not being encrypted when you tunnel the traffic through the SSH tunnel, but you no longer have to worry about the warning, since the traffic is going through an encrypted SSH tunnel. The VNC Viewer does not know that its transmissions are going through an encrypted tunnel; it only knows that it isn't performing any encryption.
I checked Google Drive, but the particular Scratchpad note I had been editing wasn't there. Though Scratchpad had at one time been synchronizing between my Chromebook and Google Drive, it appeared it hadn't done so for quite some time.
I opened the Scratchpad app (version 3.1.0), which opened a new browser tab. On the left-hand side where a list of the notes I had created appeared there was also a "Scratchpad tips and tricks" note. I clicked on it; one of the options that appeared in the note was "Connect your Scratchpad to Google Docs." When I clicked on Connect, I saw that, under Options, "Sync with Google Docs" was set to "Off". I clicked on the option to change it and gave the application access to the Google Docs for my Gmail account. I then saw the option was set to "On". Hopefully, now I will have a copy of my notes on Google Docs should the problem reoccur. I recall once previously being asked what version of a note I wanted, the one stored locally or the one on Google Docs.
Note: you can also get to the setting to change the synchronization option by taking the following steps in the browser: