Sun, Jan 26, 2014 11:40 am
Downloading Video Clips with Offliberty
If you wish to download a video clip from a website, such as a news site
or
YouTube, to archive it should it
ever disappear from the Web,
Offliberty,
which provides "evidence of offline life", offers a means to download
the video to your hard drive by simply putting in the URL for the webpage
where it is found and then clicking on the
Off button below the
field where you enter the URL.
[ More Info ]
[/video/offliberty]
permanent link
Sat, Jan 25, 2014 10:22 pm
Turning Off Automatic Updates in Windows 8
By default, a Windows 8 system will automatically install updates and
reboot the system, if it deems it is necessary. You will be warned a
few days beforehand that a reboot will be necessary within a few days,
but when the time arrives, you will get only 15 minutes to save your work
before the system automatically updates. If you are someone like me who
tends to have a lot of windows open at once and who may be working on
many tasks concurrently, 15 minutes may not be enough to save all work
in progress, even if you are sitting at the computer at the 15-minute
warning so have the full amount of time to save work in progress. And,
if the 15-minute warning comes late at night, you may not even be awake
at the time and may find when you first check the system after you have
awakened that it rebooted over night and you have lost a lot of work in
progress in applications that don't autosave. To download the updates, but
control the timing of their installation yourself, take
these steps.
[/os/windows/win8]
permanent link
Sun, Jan 19, 2014 12:00 pm
Conditional Formatting in a Google Docs Spreadsheet
You can use conditional formatting in Google Docs spreadsheets to change
the color of text in a cell or the background color of a cell just as you
can in Microsoft Excel. E.g., if I had a cell that contained an expiration
date and wanted the background color of the cell to be red if the date
had been reached or had passed, I could click in the cell and take the
following steps:
- Click on Format.
- Select Conditional formatting....
- I could then select "Date is before" in the first
field and "today" in the next field. I could then check "Background" and
select the color red for the background color for the cell once the date
in the cell has been passed.
- Once you've set up the rule or rules for the cell or range of cells,
clik on Save rules.
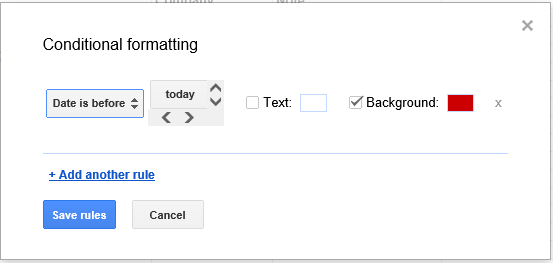
The cell will then have the normal color as long as the date stored in the
cell is before today's date. Once the date in the cell matches today's date
or is before the date of viewing, the cell background color will turn red.
Note: You can ensure that Google knows the cell contains a date by clicking
on Format, selecting Number, and then More formats,
which will allow you to pick a particular format you wish to use for dates,
such as 2008-09-26, 9/26/08, etc.
[/network/web/services/google]
permanent link
Sun, Jan 19, 2014 10:34 am
Kindle Fire Won't Power On
Yesterday, I found my Kindle Fire would not power on. I had used it a few
hours earlier without seeing any message about the battery charge being
low. But repeated attempts to turn it on by hitting the power button did
no good. So I plugged it into a charger. Hours later when I attempted to
power it on, I still was unable to do so. Following advice posted at
My kindle won't turn on, I found that holding in the power button for
30 seconds then releasing the button and then tapping the power button again
resulted in it powering on again. When it powered on, I saw the battery had
a full charge.
[/ebook]
permanent link
Sat, Jan 18, 2014 11:13 pm
Kindle App Invalid Item
I've been getting an "Invalid Item" message stating "Please remove the item
from your device and go to All Items to download it again", when I try
to read some books I've purchased through Amazon on my Android phone.
I've tried suggestions I've found elsewhere for resolving the problem,
but there are still a few books that I've been unable to download and
read with the Kindle app on my phone.
[ More Info ]
[/ebook]
permanent link
Tue, Jan 14, 2014 10:30 pm
Setting up a Cisco DPC3827 Router
I needed to configure a Cisco DPC3827 DOCSIS 3.0 Gateway provided by
an Internet Service Provider (ISP) for a home local area network (LAN)
today, so I've placed some notes
here on steps for
configuring that router.
[/hardware/network/router/cisco]
permanent link
Sun, Jan 12, 2014 12:31 pm
Using an Email Alias in Thunderbird
When I register an email address for a website, I normally create a new
email alias unique to that website or the company associated with the
website. Unfortuately, many companies and websites sell their email lists
to other companies, ususally labelled as their "partners" in their privacy
policies, seeing that as a way to make additional revenue from their
customers or website visitors. Even if a company states they won't do so, most
reserve the right to change their privacy policy at any time and there is also
the possibility that the company will go out of business at some point and
all assets, including its mailing lists, will be sold to others.
I receive an inordinate amount of spam every day and waste a lot of time
purging it from my inbox, so by creating an email alias, which I can
easily do, since I manage the email server that processes my email, I can
simply invalidate any alias when I notice I'm receiving a lot of spam with
a particular alias I created in the "to" field. E.g., if I created an
alias Acme_2014@example.com that points to Me@example.com and start receiving
spam to Acme_2014@example.com, I know that the Acme Corporation sold my
email address to a spammer or had a compromise of their server holding my
account information.
Since Acme_2014 is not an email address that a spammer who employs name
dictionaries to distribute spam might use, I can be sure that
the source of the email is using the email address I gave to the Acme
Corporation. If I used an address such as abe, bill, or zachary@example.com,
I couldn't be certain, since some spammers try sending email to a
domain using every name from a name dictionary. I also wouldn't use
acme@example.com, since that is a word in an English language dictionary,
so spammers using a dictionary for building email addresses might use it.
I can easily create aliases on my email server, but there are a number
of online services that will allow you to create such aliases to thwart
spammers. E.g., with such a service you might be able to create an
alias acme_2014@spamblock1.com that points to me@example.com, if
me@example.com is the email address you normally use.
If you wanted to communicate with Acme Corporation by email, you
might need to use the alias you used in the "from" field of email you
send to them. To do so in Thunderbird 24.2.0, right-click on your
account, which should be located at the top of the left pane of the
Thunderbird window. E.g., you may see me@example.com there. Select
Settings, then put the alias in the Email Address field
and, if needed, set the Your Name field appropriately, then
click on OK. Once you have sent the email you needed to send
to the Acme Corporation you can change the settings back to those you
normally use.
[/network/email/clients/thunderbird]
permanent link
Sat, Jan 11, 2014 4:38 pm
Disk Management Under Windows 7 from a Regular Windows Account
If you are logged into a Windows 7 system as a regular user without
administrator privileges, you can still access the disk management
function without logging off and on again as administrator or switching
to the administrator account via the
Switch User feature. To
do so, take the following steps.
-
Click on the Start button.
-
Type
cmd and hit enter to open a command prompt window.
-
At the command prompt window, type
runas /user:administrator mmc. Note: if the system is part
of a Microsoft
Windows domain and you wish to use the domain administrator account,
put the domain name followed by a backslash after user: and
before administrator. E.g., runas
/user:mydomain\administrator mmc.
-
When prompted for the administrator password, enter it.
-
In the Console Root window that opens, click on File
and select compmgmt.
-
In the Computer Management window that opens, you
will then see Disk Management under Storage.
[/os/windows/win7]
permanent link
Tue, Jan 07, 2014 2:56 pm
Telemarketing or scammer call from 717-203-8889
At 2:12 PM, I received another annoying telemarketing/scammer credit card
call. When I answered the phone I heard a message about reducing
credit card interest rates. There was a mention that the call was from
"Cardmember Services". Since there was no mention of my credit union
nor bank, it was obvious that it was not a call from my
bank nor credit union. I hit "1" to speak to a representative so I could
ask that the calls be stopped. When I was finally connected to a person,
I asked her what company she represented in a friendly tone; the person
immediately hung up without answering, so I couldn't ask to be removed
from any calling list used.
I then used *69 to get the calling number, which was 7172038889. When
I called I heard the message "Please leave a message for. That mailbox
is full." There was no person or company identified after the word "for".
I've received many telemarketing calls where the caller is identified as
"Cardmember Services" and don't know how many telemarketing companies
or credit card scammers use that identification. If it was a telemarketing
number, there was not a way for me to get the actual name of the company.
As I usually do in such cases, I reported the calling number to the
U.S. Federal Trade Commission's National
Do Not Call Registry website, since my home phone number is in that
registry, thus telemarketers shouldn't be calling my number. Unfortunately,
many telemarketers ignore the list, apparently feeling that nothing will be
done to them if they ignore the list. Perhaps that is true; I don't know
how limited the FTC's resources may be for pursuing such companies. I can
only hope that if enough complaints are filed for a particular number that
the FTC will investigate and at least fine a few of them, though I'd like
to see such companies put out of business.
I think anyone who would answer such a call and provide a credit card
number to the caller is either a fool or extremely naive, since providing
credit card information to an unknown caller may provide an opportunity to
a scammer to use that information to use the credit card information for
nefarious purposes. But since I've frequently received such calls, apparently
such telemarketers/scammers find a fair number of people willing to do so.
[/phone]
permanent link
Fri, Jan 03, 2014 9:50 pm
Altering a browser's display of a webpage by zooming in and out
Many browsers, e.g., Internet Explorer, Firefox, and Safari, provide a
feature to zoom in and out, i.e., to magnify the display of a webpage to
make text and images larger or smaller through the use of
Ctrl-key
combinations.
Ctrl-+, i.e., the
Ctrl and
+ (plus)
keys hit simultaneously, will permit you to "zoom in" to enlarge the display
of text and images on a page. Hitting the
Ctrl and
- (minus)
keys simultaneously will reverse the process allowing you to zoom
back out, i.e., reduce the size of text and images. If you wish to return
to the default display, use
Ctrl-0, i.e., the
Ctrl
and zero keys struck simultaneously.
[/network/web/browser]
permanent link
Thu, Jan 02, 2014 7:30 pm
Juniper VPN software not working with Safari for Mac OS X
I haven't been able to use Safari on my MacBook Pro laptop running OS X
version 10.8.3, aka "
Mountain Lion, to start a VPN connection from home to the office
network for some time. When I attempt to establish the VPN connection,
by going to the website address that worked in the past from within
Safari 6.1, I am asked about running a Juniper Networks application.
Do you want to run this application?
Name: NCAppController
Publisher: Juniper Networks, Inc.
When I run it, a "Setup Control - Warning" message then appears
containing the following information:
Do you want to download, install, and/or execute software
from the following server?
Product Name: Network Connect
Software Name: NetworkConnect.app
When I click on "Yes", I see a "[Network Connect] Error" window
open stating "An error occurred while extracting one of the Network
components." The only option available is "OK" and the VPN connection
is not established.
According to
Connections to Juniper Network Connect VPN failing in Safari 6.1 and Safari
7, this problem also occurs with Safari 7 on OS X 10.8 (Mountain Lion).
The author of that article states:
Based on what I’m seeing, it looks like Safari 6.1 and Safari 7
introduced a new sandbox for browser plug-ins, replacing the previous
Java whitelist. At this time, it does not appear that Juniper’s
software is able to work with this sandbox.
I can establish the VPN connection by going to the Applications
directory in the Finder and double-click on Network
Connect, which starts the Network Connect 7.4.0 application,
then put in my username and password for the VPN and establish a
connection by that means without a problem.
[/os/os-x]
permanent link
Thu, Jan 02, 2014 11:40 am
Choosing a country for the Tor exit node
If you use the
Tor Browser Bundle
for web browsing, you may sometimes see "This service is not available in
your location" or similar messages when you attempt to use some online
services when a service is not available to residents of some countries, if
the exit node, i.e., the last hop in the Tor network, for your browser
session happens to be in a country for which the oline service is
unavailable. You can see the location of the exit node, i.e., the IP address
that websites see for your location when you visit them by visiting
WhatIsMyIP.com or similar websites
that provide geolocation information.
If you wish to specify an exit node in a particular country, you
can use the country code
for the country established by the
International Organization for Standardizaton. Two characters are used
to represent the country code in an online address, e.g. us for
the United States, dk for Denmark, gb for
Great Britain, etc. You can find the complete list of country codes
at
ISO 3166-1-alpha-2 code. The country code to be used for the exit
note must be placed in the
torrc
configuration file used by the Tor browser bundle. Look
for the torrc file in the Data/Tor directory
beneath the directory in which you installed the Tor Browser Bundle. You
can edit it with a text editor, such as Notepad on a Microsoft Windows
system. Put the following line at the end of the file where cc
represents the country code:
ExitNodes {cc}
E.g., for a United States exit node, you would use:
ExitNodes {us}
To confirm the exit node location, restart the Tor browser, if
it is running, and visit a site such as
WhatIsMyIp. Note: if there is a problem accessing an exit node in
the selected country or if you entered an invalid country code, you may find
that you don't get past the "Connecting to the Tor network" window
when you start the Tor browser. In that case, you may need to select
a different country code. Also, some online services may block access
from all known Tor exit nodes, since some people use Tor for malicious
purposes rather than simply for online privacy. E.g., Wikipedia does not
allow editing of articles when an editor is accessing Wikipedia via the
Tor network.
Also note that the Tor Project does not recommend specifying
an exit node. At
Tor FAQ: Can I control which nodes (or country) are used for entry/exit?
you will find:
We recommend you do not use these — they are intended for testing and
may disappear in future versions. You get the best security that Tor can
provide when you leave the route selection to Tor; overriding the entry /
exit nodes can mess up your anonymity in ways we don't understand.
But that option is available, if you wish to use it, at least as of
version 3.5 of the Tor Browser Bundle.
[/network/web/browser/tor]
permanent link
Wed, Jan 01, 2014 3:45 pm
Tor reports Firefox is already running
If you install the
Tor browser
bundle for online privacy and see a "Close Firefox" window appear
when you attempt to start the Tor browser with the message below, then you
may need to change the location where you placed the Tor browser bundle:
Firefox is already running, but it is not responding. To open a new window,
you must first close the existing Firefox process, or restart your system.
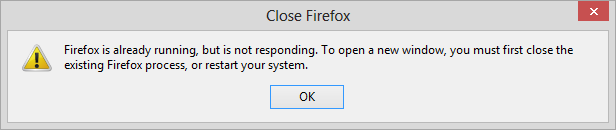
This message can appear even when the Firefox browser provided with the
Tor browser bundle isn't running as you can see by using the Windows Task
Manager to check for running processes, if the the software was placed
under the C:\Program Files (x86) directory, even if you run
the software from an account with administrator privileges. The
software apparently needs to write to files in the directory where it
has been installed, but can't do so. If you install it to the Desktop
or under the Documents directory for the account from which you will be
running it, you won't see the message.
[/network/web/browser/tor]
permanent link

Privacy Policy
Contact





