Fri, Aug 31, 2007 11:33 am
Setting Savin C3535 Printer for Folding and Stapling
A client was having problems printing a brochure from Microsoft Publisher to a
Savin C3535 copier/printer. She wanted to have the document folded and stapled.
Folding and stapling worked for tabloid pages, but not letter-size pages.
The company providing support for the Savin 3535 printer suggested the
following steps be taken at the server from which the printer was being
shared.
- Click on Start.
- Select Printers and Faxes.
- Right-click on the printer, in this case SAVIN C3535 PCL 6, and
select Properties
- Click on the Accessories tab.
- Check Tray 3 (LCT) and Finisher SR3020
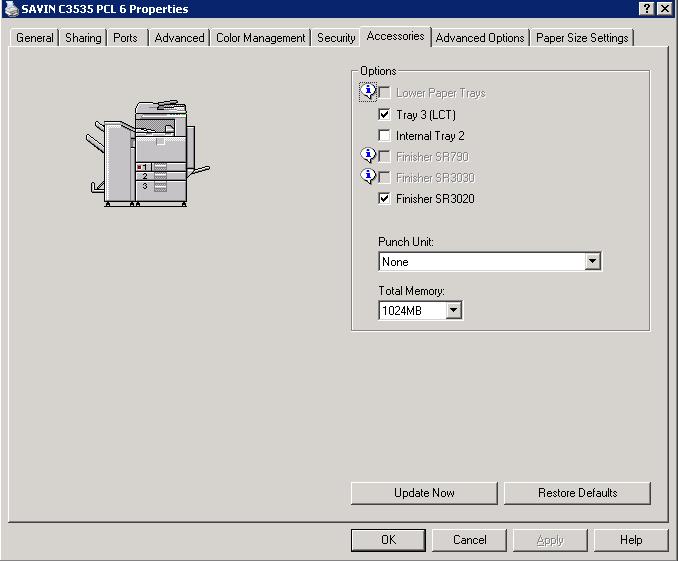
- Click on the Paper Size Settings tab.
- Select Tray 1 under Input Tray.
- For Paper Size, select Letter (8.5" x 11") then
click on Update
- For Tray 2, select 11" x 17" as the paper size
and click on Update.
- For Tray 3 (LCT), select 8.5" x 11" as the paper size
then click on Update.
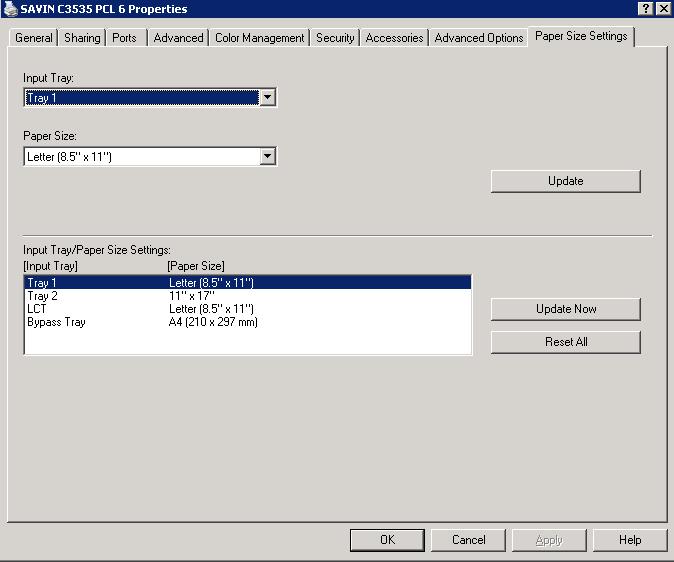
- Click on OK.
When that didn't resolve the problem, the tech support person I spoke to
suggested deleting the shared printer from the system on which the print
job was being generated and then adding the share for the printer again.
[/os/windows/printers]
permanent link
Thu, Aug 30, 2007 10:11 pm
Print Last Page First in Adobe Acrobat
To reverse page printing order, i.e. to print the last page of a document
first, in Adobe Acrobat 6.0, take the following steps:
- Click on File.
- Select Print.
- Check Reverse pages.
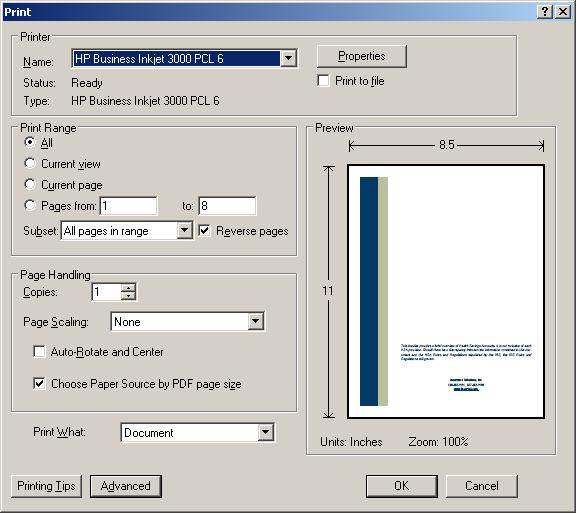
- Click on OK.
References:
-
Options in the Print dialog box
Adobe Systems Incorporated
[/os/windows/software/pdf]
permanent link
Tue, Aug 28, 2007 11:04 pm
Forwarding Email to Another Exchange User
For an Exchange 2003 server, If you need to forward email to another Exchange
user when an employee leaves, take the following steps.
- Go to Active Directory Users and Computers.
- Select the account for the user who left and right click on it.
- Select Properites.
- Under the Exchange General tab, click on the Delivery
Options button.
- Click on the Modify button at the Delivery Options
window that opens.
- In the "Enter object name to select" field, type the account name of the
user to whom email should be forwarded, e.g. jsmith.
- Click on the Check names button to verify the account name and
then click on OK when it has been verified.
- Click on OK again to close the Delivery Options window.
- Click on OK to close the Properties window.
If you need to forward email to an external address instead of an internal
Exchange address,
see
Forwarding an Exchange User's Email to an External Address.
References:
-
Forwarding an Exchange User's Email to an External Address
November 5, 2006
MoonPoint Support
-
Redirect mail from old staff and reply to senders with new instructions
November 11, 2005
TechRepublic
[/network/email/exchange]
permanent link
Mon, Aug 20, 2007 11:35 pm
Premature EOM in Sendmail Log File
A user reported that she had been unable to receive email from two email
addresses. The server processing her incoming email is running
sendmail. When I looked in the
/var/log/maillog files, where entries related to successful
and unssuccessful email delivery attempts for sendmail are stored, for
any entries related to one of the email addresses she mentioned, I did
not see any, but I saw many entries similar to the following for
the domain name used in that email
address, which mentioned
collect: unexpected close on connection.
Aug 16 23:37:57 frostdragon sendmail[3738]: l7H3ak69003738: collect:
premature EOM: unexpected close
Aug 16 23:37:57 frostdragon sendmail[3738]: l7H3ak69003738: collect: unexpected close on connection from mail6.tcusa.com,
sender=<orders@example.com>
I had also been receiving reports from others that sending even small messages
sometimes takes a long time. A couple of times when I checked the number of
SMTP connections to
the server with netstat -a | grep smtp | wc -l, I found over
60 connections from other email servers. Previously, I would find that there
would usually be no more than a dozen such connections at any give time. And,
if I connected to the SMTP port with telnet mail.example.com 25,
I would sometimes see fairly slow responses.
In searching for information on the problem, I found
Sendmail ‘collect: premature EOM: unexpected close’ solution
. The author was encountering the same problem, which he traced to the use
of a defunct DNSBL,
relays.ordb.org. Like the author, I have been using relays.ordb for a long
time to block incoming spam to the server. In the /etc/mail/sendmail.mc
file on the server, I have the following line.
FEATURE(`dnsbl', `relays.ordb.org', `"550 Mail from " $`'&{client_addr} " refused due to sending server misconfiguration - see http://www.ordb.org/faq/\#why_rejected"')dnl
I removed the above line from /etc/mail/sendmail.mc, but added
another DNSBL in its place, the Abusive
Hosts Blocking List (AHBL), which I found listed at
HOWTO: Sendmail tips for Ensim, by adding the following line to
/etc/mail/sendmail.mc.
FEATURE(dnsbl,`dnsbl.ahbl.org', `"550 Host is on the AHBL - Please see [url]http://www.ahbl.org/tools/lookup.php?ip=[/url]"$&{client_addr}')dnl
I then took the following steps to update sendmail's configuration information
so that it no longer checks the relays.ordb.org blocklist, but uses the AHBL
list instead.
- I issued the command below
m4 /etc/mail/sendmail.mc > /etc/mail/sendmail.cf
-
I then stopped and restarted sendmail with the command below
/etc/init.d/sendmail restart
According to
DNS Blacklist ORDB.org is shutting down the relays.ordb.org DNSBL
has been shut down since December 18, 2006. When I tried pinging it, I don't
get a response and an nslookup on the name returns an error message as well.
# nslookup relays.ordb.org
Note: nslookup is deprecated and may be removed from future releases.
Consider using the `dig' or `host' programs instead. Run nslookup with
the `-sil[ent]' option to prevent this message from appearing.
;; connection timed out; no servers could be reached
I'm using 5 other blocklists as well, so I checked all of them by pinging
them to ensure that no other blocklists that I am using have disappeared.
I got responses for all of them, but that just verifies that a system is
functioning at the address pinged. To check whether a system is actually
functiong as a DNSBL at that address, you should issue use the nslookup,
host, or dig commands to query the system using a query in the form
2.0.0.127.blacklist.example.com.
All of the commands should result in the address 127.0.0.2 being
displayed as the IP address for
the query. This is because DNSBL's normally work by storing the IP address
of systems to be blocked as reversed mappings so that queries are submitted
akin to how you would do a reverse lookup for an in-addr.arpa
query (see
Chapter 9: Howto Create a DNSBL (DNS Black List), if
you wish further details on how DNSBL's work). Since the convention is
for DNSBL's to always have the address 127.0.0.2 in the list, querying
for that address allows for easy testing. E.g. for AHBL, I could use
2.0.0.127.dnsbl.ahbl.org with nslookup, host, or dig.
# nslookup 2.0.0.127.dnsbl.ahbl.org
Note: nslookup is deprecated and may be removed from future releases.
Consider using the `dig' or `host' programs instead. Run nslookup with
the `-sil[ent]' option to prevent this message from appearing.
Server: 207.233.128.10
Address: 207.233.128.10#53
Non-authoritative answer:
Name: 2.0.0.127.dnsbl.ahbl.org
Address: 127.0.0.2
# host 2.0.0.127.dnsbl.ahbl.org
2.0.0.127.dnsbl.ahbl.org has address 127.0.0.2
# dig +short 2.0.0.127.dnsbl.ahbl.org
127.0.0.2
Note: this won't work for all DNSBL's, e.g. performing an nslookup for
2.0.0.127.dnsrbl.swinog.ch returns
** server can't find 2.0.0.127.dnsrbl.swinog.ch: NXDOMAIN, even
though the DNSBL is working.
For checking whether a particular IP address is in one of the blacklists,
you would reverse the address and then put a period and the name of
the blacklist after it when issuing an nslookup, host, or dig query.
E.g., if I wanted to find out whether the addresses
62.30.35.75 and 62.30.35.76 are in the
Composite Blocking List (CBL), I could use
the commands below.
# host 75.35.30.62.cbl.abuseat.org
75.35.30.62.cbl.abuseat.org has address 127.0.0.2
# host 76.35.30.62.cbl.abuseat.org
Host 76.35.30.62.cbl.abuseat.org not found: 3(NXDOMAIN)
From the results, I see that the first address is in the CBL DNSBL, but
the second address is not in the blacklist.
Checking other blacklists, aka blocklists, I'm using by querying for
the presence of 127.0.0.2 in the lists, I found that opm.blitzed.org
is no longer functioning either.
# host 2.0.0.127.opm.blitzed.org
;; connection timed out; no servers could be reached
At OPM status, I learned
that opm.blitzed.org has also been shut down. It was shut down in May 2006.
Details on the shutdown have been posted at
[opm-announce] opm.blitzed.org has shut down.
So I removed the line below from /etc/mail/sendmail.mc.
FEATURE(`dnsbl', `opm.blitzed.org', `"550 Mail from " $`'&{client_addr} " refused - see http://opm.blitzed.org"')dnl
After verifying all of the other blacklists I was using in sendmail.mc still
worked, I then rebuilt the sendmail.cf file with the m4 command as above and
then restarted sendmail again.
References:
-
Sendmail ‘collect: premature EOM: unexpected close’ solution
Posted by plattapuss
on February 28th, 2007
Out of Control Image
-
DNSBL
Wikipedia, the free encyclopedia
-
Abusive Hosts Blocking List
-
HOWTO: Sendmail tips for Ensim
Posted By: pblinux
Posted: December 1, 2003
The Planet Forums
-
DNS Blacklist ORDB.org is shutting down
Article ID: KBID002925
GFI Knowledge Base
-
Chapter 9: Howto Create a DNSBL (DNS Black List)
ZyTrax, Inc.
-
Composite Blocking List
-
OPM Status
Blitzed Wiki
-
[opm-announce] opm.blitzed.org has shut down
Posted By: Andy Smith grifferz at blitzed.org
Posted: May 7, 2006
lists.blitzed.org Mailing Lists
[/network/email/sendmail]
permanent link
Fri, Aug 17, 2007 9:43 pm
DNS Server Listening on All Addresses
I removed the line
listen-on { 127.0.0.1; };
from
/etc/named.conf
to enable a Solaris server to listen on all IP addresses for the server, not
just the loopback address, making it usable as a
DNS server by other systems
on the LAN.
[/os/unix/solaris]
permanent link
Fri, Aug 17, 2007 9:23 pm
Start Named Service under Solaris
I had configured a Solaris 10 system to function as a name server
(see
Configuring a
Solaris System as a DNS Server), but when I rebooted the system
it was no longer functioning as a DNS server and since the only name server
I had listed in
/etc/resolv.conf was the system itself, i.e.
its loopback address, I could not resolve system names to IP addresses.
# svcs | grep 'named'
# nslookup cisco.com
;; connection timed out; no servers could be reached
# cat /etc/resolv.conf
domain example.com
nameserver 127.0.0.1
I could run named to start the named daemon again, so that
I could resolve names, but I wanted it to start automatically when the
system boots. To do so, I created the file /etc/init.d/named
with the following lines in the file:
#!/sbin/sh
#
# named
#
case "$1" in
start)
# Start daemon.
echo "Starting named"
/usr/sbin/named
;;
stop)
# Stop daemon.
echo "Shutting down named"
pkill named
;;
*)
echo "Usage: $0 { start | stop }"
exit 1
;;
esac
exit 0
I then changed the group ownership for the file to sys to make
it consistent with the other files in that directory and made it executable.
# chgrp sys /etc/init.d/named
# chmod 744 /etc/init.d/named
# ls -l /etc/init.d/named
-rwxr--r-- 1 root sys 284 Aug 17 20:07 /etc/init.d/named
To have it start automatically, I also needed to add it to
/etc/init.d/rc3.d. You need to prefix the name with
"S" and then a number to have it start automatically. You will see other
files with names beginning with Sxx where "xx" is some number. You must
pick a number that is different from any already used. I picked the next
higher number, 91, in this case.
# cp -p /etc/init.d/named /etc/rc3.d/S91named
When you reboot, you can check that the service is running with
the ps or svcs commands or do an nslookup
.
# ps -ef | grep named
root 537 1 0 20:42:16 ? 0:00 /usr/sbin/named
# svcs | grep named
legacy_run 20:42:18 lrc:/etc/rc3_d/S91named
# nslookup cisco.com
Server: 127.0.0.1
Address: 127.0.0.1#53
Non-authoritative answer:
Name: cisco.com
Address: 198.133.219.25
References:
-
Configuring a Solaris
System as a DNS Server
MoonPoint Support
-
Building
and configuring BIND 9 in a chroot jail
By Steve Friedl
Unixwiz.net - Software Consulting Central
[/os/unix/solaris]
permanent link
Mon, Aug 13, 2007 6:10 pm
Deleting a User Under Solaris 2.7
To delete a user on a system running Solaris 2.7, run
admintool,
select the user's account by clicking on it, then click on
Edit
then
Delete. You will be prompted as to whether you really want
to delete the user's account and can choose to delete the home directory
when the account is deleted. You may have to manually delete a mail file for the
user from /var/mail, e.g.
rm /var/mail/jsmith.
[/os/unix/solaris]
permanent link
Sun, Aug 12, 2007 6:22 pm
Too Many Partitions for Norton Ghost
I tried to backup a system with four primary partitions across the network
with Norton Ghost 7.5 using the Symantec Ghost Console, but was unable to do so,
since Ghost was unable to set up the virtual partition it needed on the client
system. When I deleted one of the partitions on the client system, I was able
to successfully backup the system.
[ More
Info ]
[/os/windows/utilities/backup/ghost]
permanent link
Fri, Aug 10, 2007 9:01 pm
mii-tool
If you want to know the speed at which a system has connected to the
LAN, e.g. the system can
autonegotiate its speed and you need to know which speed it is using, you can
use the
mii-tool
command to check the status of Ethernet devices in the system.
# mii-tool
eth0: no autonegotiation, 10baseT-HD, link ok
From the above output from the command on a Linux system, I can see that
the Ethernet device, eth0, is not using autonegotiation to determine its
speed and is set to 10 Mbs half duplex.
If you want more details for Ethernet devices in the system, you can
use -v or --verbose as a parameter to the command.
# mii-tool -v
eth0: no autonegotiation, 10baseT-HD, link ok
product info: vendor 00:10:18, model 23 rev 7
basic mode: autonegotiation enabled
basic status: autonegotiation complete, link ok
capabilities: 100baseTx-FD 100baseTx-HD 10baseT-FD 10baseT-HD
advertising: 100baseTx-FD 100baseTx-HD 10baseT-FD 10baseT-HD flow-control
From the above, I can see that eth0, though it is set for a 10baseT connection,
i.e. 10 Mbs, can support a 100baseTx, i.e. 100 Mbs, connection.
The device is capable of the following port speeds:
| Port Speed | Description |
|---|
| 10baseT-HD |
10 megabits/s half duplex |
| 10baseT-FD |
10 megabits/s full duplex |
| 100baseTx-HD |
100 megabits/s half duplex |
| 100baseTx-FD |
100 megabits/s full duplex |
mii-tool manpage
References:
-
B.5. mii-tool
Guide to IP Layer Network Administration
with Linux
[/os/unix/commands]
permanent link
Thu, Aug 09, 2007 9:56 pm
Configuring Outlook Express 6 For TLS
Outlook Express can be configured to use
TLS to authenticate
with an email server and to transmit messages securely, i.e. in
encrypted form between Outlook Express and the server set to be its
SMTP server.
Note: TLS doesn't gurantee end-to-end encryption of the message, just
the encrypted transmission of the message from the client email program, such
as Outlook Express, to the SMTP server to which it hands off the message.
That server may in turn transmit the message to other servers in unencrypted
form.
[
More Info ]
[/network/email/clients/outlook-express]
permanent link
Tue, Aug 07, 2007 11:19 pm
Expired sendmail.pem Security Certificate
I had been getting reports from users of one domain handled by my
Linux email server
that email from/to a particular client they deal with had been getting
delayed. When I checked the maillog files, I found references to
"TLS errors" for that domain. When I discussed the problem with a tech
support person for the other company, he said his company is using Exchange
with a
TLS connector and
would prefer my server communicate using
TLS
with their server. He told me that the security certificate for my server
had expired.
I didn't know how to check the expiration date until I found instructions
for checking the expiration at
Renew SSL certificate in RedHat 9.
Sugree, the author of
that webpage, suggested running the command openssl x509 -in
sendmail.pem -text | grep Not. The instructions were written for
a RedHat 9 system. When I ran the command, I saw the following
results.
# cd /usr/share/ssl/certs
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Not
Not Before: Nov 9 21:26:57 2003 GMT
Not After : Nov 8 21:26:57 2004 GMT
The author then recommended using the command openssl x509 -in
sendmail.pem -text | grep Subject. It produced the following
results on my server.
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Subject
Subject: C=US, ST=Maryland, L=Annapolis, O=MoonPoint, CN=frostdragon.com/emailAddress=support_999@frostdragon.com
Subject Public Key Info:
X509v3 Subject Key Identifier:
The information above will be needed when you generate a new certificate.
I deleted the /usr/share/ssl/certs/sendmail.pem file and generated
a new one with make sendmail.pem, which I ran from
/usr/share/ssl/certs. The bold text items are the responses I entered
to queries and repeat the information I saw when I ran openssl x509 -in
sendmail.pem -text | grep Subject.
[root@frostdragon certs]# make sendmail.pem
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req -newkey rsa:1024 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 ; \
cat $PEM1 > sendmail.pem ; \
echo "" >> sendmail.pem ; \
cat $PEM2 >> sendmail.pem ; \
rm -f $PEM1 $PEM2
Generating a 1024 bit RSA private key
...........++++++
..............................................++++++
writing new private key to '/tmp/openssl.Ipeqjd'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:US
State or Province Name (full name) [Berkshire]:Maryland
Locality Name (eg, city) [Newbury]:Annapolis
Organization Name (eg, company) [My Company Ltd]:MoonPoint
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:frostdragon.com
Email Address []:support_999@frostdragon.com
When I then checked the expiration of the sendmail.pem certificate,
I saw the following.
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Not
Not Before: Aug 8 02:41:22 2007 GMT
Not After : Aug 7 02:41:22 2008 GMT
So now I've got a certificate that is good for another year.
References:
-
Transport
Layer Security
Wikipedia, the free encyclopedia
-
Renew SSL certificate in RedHat 9
By Sugree
howforge.com | Share Know-How
[/network/email/sendmail/tls]
permanent link
Sun, Aug 05, 2007 10:19 pm
Norton Ghost 7.5 - Broadcom 57xx Integrated Controller
If you want to backup a Dell system with a Broadcom NetXtreme 57xx
integrated network controller using Norton Ghost 7.5, then you will
need to create a template for that network interface card (NIC) using
an NDIS2 driver.
[ More Info ]
[/os/windows/utilities/backup/ghost]
permanent link

Privacy Policy
Contact





