Fri, May 29, 2015 9:29 pm
Counting cells that aren't blank in Google Sheets
To count the number of cells containing content, i.e., those that aren't
blank, in Google Sheets, which is part of
Google Docs and is
Google's online equivalent of Microsoft Excel you can use
COUNTIF
or
COUNTA. E.g., suppose you wish to count the number of cells
in column A from A2 to A64 which contain data, ignoring any cells that are
blank. You could use
COUNTIF(A2:A64,"<>"). The
"<>", instructs Google Sheets to only count cells that
don't have a null value, i.e., ones containing some data. Alternatively,
you could use
COUNTA(A2:A64). If you wanted the number that
were blank, you could use
COUNTBLANK(A2:A64).
[/network/web/services/google]
permanent link
Thu, May 28, 2015 9:58 pm
Copying command output to the clipboard under Microsoft Windows
When you are using the Microsoft Windows command line interface, you may need
to copy the output of commands somewhere else, such as notepad or some
other text editor. You can copy and paste the output of commands by
right-clicking on the Command Prompt title bar and selecting
Edit,
then
Mark and then highlighting the text you wish to copy in the
command prompt window and hitting
Enter to copy it to the Windows
clipboard. Or you can click within the Command Prompt window below the title
bar which will give you the option to select
Mark without selecting
Edit first. Either method will then allow you to use
Edit
and
Paste or
Ctrl-V to paste the text into other applications.
Another alternative is to redirect the output of a command to a file using
the redirect character, >. E.g., if you wished to put
the output of the dir command in file example.txt,
you could use dir > example.txt.
If you wish to see the output in the command window and also have it
copied to the clipboard at the same time, another alternative is to use
the "pipe" character, | followed by clip. E.g.,
if you wanted to see all the files in a directory with many files and also
have the output of the command placed in the Windows clipboard, you could
use dir | clip. You could then paste the contents of
the clipboard into other applications.
[/os/windows/commands]
permanent link
Tue, May 19, 2015 9:10 pm
Determining if a package is installed under Ubuntu
To determine if a package is installed on a Ubuntu Linux system, you can
use the command
dpkg -s packagename where
packagename
is the name of the package.
$ dpkg -s python-software-properties
Package: python-software-properties
Status: install ok installed
Priority: optional
Section: python
Installed-Size: 196
Maintainer: Michael Vogt <michael.vogt@ubuntu.com>
Architecture: all
Source: software-properties
Version: 0.82.7.5
Depends: python2.7, python (>= 2.7.1-0ubuntu2), python (<< 2.8), python-apt (>= 0.6.20ubuntu16), lsb-release, python-gnupginterface, unattended-upgrades, iso-codes, python-pycurl
Description: manage the repositories that you install software from
This software provides an abstraction of the used apt repositories.
It allows you to easily manage your distribution and independent software
vendor software sources.
If a package isn't installed, you will see output similar to the following:
$ dpkg -s linssid
Package `linssid' is not installed and no info is available.
Use dpkg --info (= dpkg-deb --info) to examine archive files,
and dpkg --contents (= dpkg-deb --contents) to list their contents.
You can use the dpkg-query -l command with the wild card
character, *, to see a list of packages that match a specified
pattern. E.g., to see all packages that begin with python-py:
$ dpkg-query -l 'python-py*'
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Description
+++-==============-==============-============================================
un python-pyatspi <none> (no description available)
ii python-pyatspi 2.4.0+dfsg-0ub Assistive Technology Service Provider Interf
ii python-pycurl 7.19.0-4ubuntu Python bindings to libcurl
un python-pycurl- <none> (no description available)
un python-pygment <none> (no description available)
un python-pyicu <none> (no description available)
ii python-pyinoti 0.9.2-1 simple Linux inotify Python bindings
un python-pyinoti <none> (no description available)
un python-pylons <none> (no description available)
An asterisk, "*", can represent one or more characters. You can also
use a question mark, "?", to represent just one instance of any character.
E.g.:
$ dpkg-query -l 'xin*'
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Description
+++-==============-==============-============================================
ii xinit 1.3.1-1 X server initialisation tool
ii xinput 1.5.99.1-0ubun Runtime configuration and test of XInput dev
jim@lancelot:~/Documents/blog$ dpkg-query -l 'xin??'
Desired=Unknown/Install/Remove/Purge/Hold
| Status=Not/Inst/Conf-files/Unpacked/halF-conf/Half-inst/trig-aWait/Trig-pend
|/ Err?=(none)/Reinst-required (Status,Err: uppercase=bad)
||/ Name Version Description
+++-==============-==============-============================================
ii xinit 1.3.1-1 X server initialisation tool
To get a list of all packages on the system, use dpkg-query -l.
[/os/unix/linux/ubuntu]
permanent link
Sun, May 17, 2015 10:51 pm
Tools for Cutting Craft Sticks
My wife asked me to help her cut a large number of
Woodsies Craft Sticks for floorboards for a doll house project she has
started. The wooden craft sticks, which look like large popsicle sticks or
tongue depressers, have rounded ends, but she needed square ends for some
and others with a 45-degree angle at the ends. I thought I could simply
cut them with a pair of electrician's scissors, which worked well for
the first couple of craft sticks I cut; it was easy to cut through them
with the scissors and the scissors left fairly smooth edges, but I found
after the first couple of sticks that subsequent cuts through other sticks
tended to splinter the cut ends. My saws were too large, but she had a
Revell Razor Saw designed
for craft projects which worked well, but, since I had to go to the local
True Value hardware store for some C-clamps anyway, I looked for something
there that might help speed cutting through a large number of the craft
sticks. I found a
Master Mechanic
Mult Cutter there, which uses blades similar to what you might find
in a box cutter. I found it was easy to put a stick on its anvil and
then cleanly and easily cut through the craft sticks by squeezing its
handle, which pressed the blade through the stick and against the anvil.
I thought I'd note the tools used here, so I'd know what to buy should
I need to replace the blades in the tools in the future or should anyone
else possibly be looking for tools to cut those craft sticks, since I've
seen others noting problems cutting similar items without frayed/splintered
ends, e.g.,
What is the best way to cut popsicle sticks?
[/info/tools]
permanent link
Sat, May 16, 2015 10:31 pm
Configuring SNMP on a Windows 7 System
The Simple Network Management Protocol (SNMP) provides a mechanism
for managing network-connected devices using a standard protocol for a
wide variety of networked devices, such as routers, switches, servers,
workstations, printers, etc. Microsoft Windows systems support SNMP, but they
are not configured by default to support SNMP. But once you've installed and
configured SNMP on a Windows system you can monitor a variety of system
parameters on it from an SNMP network management system. Steps for configuring
SNMP on a Microsoft Windows 7 system are detailed
here.
Instructions for installing SNMP on systems running Windows XP are at
Installing SNMP
Under Windows XP.
[/os/windows/win7]
permanent link
Fri, May 15, 2015 8:23 pm
Determining the Office 2013 Product Key
If Microsoft Office 2013 is installed on a PC and you need to know
the product key, but there is no product key sticker on the system,
you can obtain the product key from a command prompt using the command
cscript “C:\Program Files (x86)\Microsoft Office\Office15\OSPP.VBS”
/dstatus for the 32-bit version or
cscript “C:\Program Files\Microsoft Office\Office15\OSPP.VBS” /dstatus
for the 64-bit version. If Microsoft Office is installed beneath
Program Files (x86) that indicates you have the 32-bit version,
since that is where 32-bit versions of applications are installed.
But you will only be shown the last 5 characters of the 25-character
product key, because, unlike with prior versions of Microsoft Office, Microsoft
is no longer storing the entire product key in the registry where it can be
retrieved. So the product key you obtain is only likely useful to you if
you have multiple Microsoft Office 2013 product keys and need to determine
which one is used on which system. Or if you purchased the software online
and received the product key by email, you could use those last 5 characters
to search your email or your system for any message or file containing the
full product key.
When you run the commands, you will see output similar to the following:
C:\>cscript "\Program Files\Microsoft Office\Office15\OSPP.VBS" /dstatus
Microsoft (R) Windows Script Host Version 5.8
Copyright (C) Microsoft Corporation. All rights reserved.
---Processing--------------------------
---------------------------------------
SKU ID: 064383fa-1538-491c-859b-0ecab169a0ab
LICENSE NAME: Office 15, OfficeProPlusR_Retail edition
LICENSE DESCRIPTION: Office 15, RETAIL channel
LICENSE STATUS: ---LICENSED---
Last 5 characters of installed product key: B96XY
---------------------------------------
---------------------------------------
---Exiting-----------------------------
If the software was preinstalled on the system, there is likely a sticker
with the full Microsoft Office 2013 product key. But, if it wasn't and you
need the full product key, but can't find it via a search through email
or files on the system, if you registered and activated the software,
you may be able to log into a Microsoft account that you have via Microsoft Office:
My Account. You should be able to see the product key there and
redownload the software, also, if needed. A last resort might be to
contact Microsoft support using contact information from Microsoft's Contact Us page.
But you will likely need some way of proving that you purchased the
software to have any chance of being issued another product key.
References:
-
How to find your Office 2013 product key after installation
Support - support.office.com
[/os/windows/office]
permanent link
Thu, May 14, 2015 11:03 pm
Checking and setting the NTP server on a Mac OS X System
The
systemsetup -getnetworktimeserver command can be used on
a Mac OS X system to determine the time server with which the system's
clock is being synchronized.. You need administrator access to utilize the
command; you can use sudo to run it if your account has administrative
privileges.
$ systemsetup -getnetworktimeserver
You need administrator access to run this tool... exiting!
$ sudo systemsetup -getnetworktimeserver
Password:
Network Time Server: ntp.example.com
You can set the
Network
Time Protocol (NTP) server with which the system will
synchronize its clock by specifying -setnetworktimeserver,
instead. E.g.:
$ systemsetup -setnetworktimeserver us.pool.ntp.org
You can query an NTP server with the sntp command.
$ sntp us.pool.ntp.org
2015 May 14 22:50:29.664176 +4.438430 +/- 0.099854 secs
[/os/os-x]
permanent link
Wed, May 13, 2015 9:07 pm
Monitoring Interface Bandwidth Utilization on a NetScreen Firewall
While checking on a performance problem at a site using a NetScreen 5GT
firewall, I found that when I accessed the Interface Bandwidth report from
the web-based management interface that the report was showing zero Kbps
for the utilized bandwidth on all interfaces, which was obviously wrong, since
data was flowing through the firewall. I found that I needed to enable traffic
shaping mode on the firewall to get that report to actually show the bandwidth
being used for the interfaces on the firewall.
Traffic shaping is a mechanism to give certain types of data flows
precedence over others with lower priority traffic being buffered. In this
case I didn't actually "shape" the traffic, but just enabled traffic shaping
mode so that I could see the current bandwidth being used on interfaces.
[ More Info ]
[/security/firewalls/netscreen]
permanent link
Tue, May 12, 2015 11:22 pm
Checking and setting NTP information on a NetScreen firewall
While checking the configuration of a Juniper Networks netscreen-5gt
firewall, I noticed that the time was incorrect and that it was not
set up to query a Network Time Protocol (NTP) server to ensure its time was
accurate. To check or set the NTP configuration on a Juniper Networks
NetScreen firewall, From the web management interface, you can check and
set the Network Time Protocol (NTP) information for a Juniper NetScreen
firewall, such as the NetScreen-5GT firewall, by clicking on Date/Time
beneath the Configuration option on the menu.
The NTP configuration can also be viewed and set from a command line
interface accessible by SSH using get ntp and set ntp
commands. Up to three NTP servers can be configured. The time interval for
NTP queries can be specified.
[ More Info ]
[/security/firewalls/netscreen]
permanent link
Mon, May 11, 2015 9:52 pm
Adding Plugins Folders to Corel PaintShop Pro X7
In Corel PaintShop Pro X7, select
File,
Preferences then
File Locations. In the
File Locations window, click on
Plug-ins, which will show the current plug-in file folders. Click
on the
Add button and browse to the directory where plugins are
located that you wish to add to PaintShop Pro. Click on
OK once you've
located the directory, then click on
OK again to close the
File Locations window.
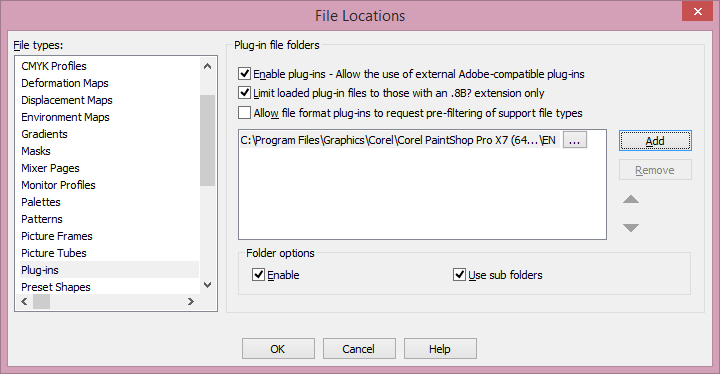
Make sure Enable is checked in the File Locations window
and Use sub folders, if the plug-ins are within a subfolder of a
selected folder.
To use an added plugin, click on Effects, then Plugins, then
select the plugin you wish to use.
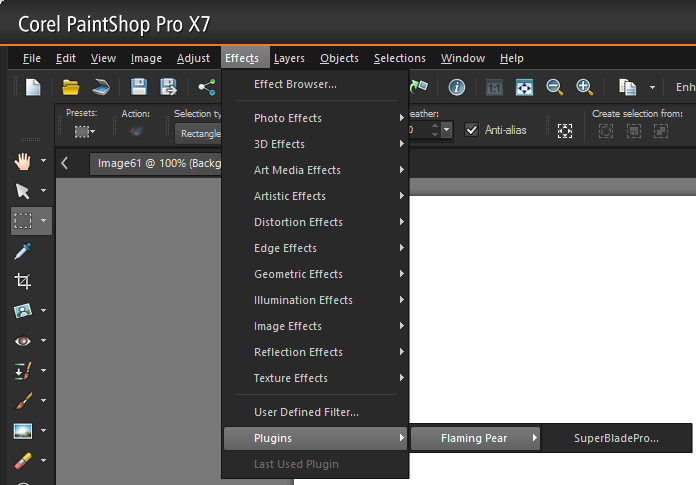
[/os/windows/software/graphics/corel/psp]
permanent link
Sun, May 10, 2015 5:55 pm
Google Index Status and Crawl Errors
If you use
Google
Analytics to monitor your site, Google provides a number of reports
that can be used to find issues related to Google's
crawling of your
site, such as
Google Index Status and
Crawl
Errors.
For instance, I often use Google to find articles on my own site when
I encounter a problem that I resolved previously while working on someone's
computer when I can't remember exactly what I did previously or the cause
of the same issue when I previously encountered it. I go to google.com and
spcify some keywords I know would be on the page or blog posting I created
and follow the keywords with site:support.moonpoint.com so
Google returns only results from my site. But I've recently found that
Google is reporting it has found no results for my site when I know it should
be finding them since I know the Googlebot has crawled the site subsequent
to my posting the entries on the site, some of which I posted quite some
time ago, and since it has shown me results that indicate it has
indexed material from the site only the day before. Checking the
Index Status report for my site, I found that the number
of pages indexed has declined considerably since this time
last year, whereas I haven't deleted pages and have added over
one hundred pages/blog entries since that time. Checking the Crawl Errors
report, I see quite a few "Not found" entries I need to fix,
but they don't explain the decline in the number of indexed entries,
so I know I need to do further investigation.
[/network/web/services/google/analytics]
permanent link
Sat, May 09, 2015 8:12 pm
Quicken 2015 Mortgage Balance Discrepancy
I use Quicken 2015 Home & Business to manage our finances. One annoyance
I encountered recently was that when I viewed the details for the mortgage
account, the balance was listed correctly, but on the left side of the screen
where the balances are listed for all accounts, the balance shown for the
mortgage account under the
Property section was wrong. The amount
that was displayed was the amount shown for the current balance when I looked
at the transaction display for the account plus the original balance when
we purchased the house. The two balances had matched previously; I think the
incorrect amount under the
Property section of
Accounts
started appearing with an incorrect amount after I reconciled all of the
transactions in the mortgage account. But even after I unchecked entries to
make them unreconciled to see if that would eliminate the discrepancy, the
discrepancy remained. And that discrepancy resulted in an incorrect
equity being shown when I clicked on
Equity when viewing the
mortgage account. The equity was being shown as a negative value, i.e.,
Quicken was claiming I owed more on the house than the house was worth.
I exited from the program then restarted it, but the discrepancy remained.
So I decided to backup the Quicken data file and then perform a repair
operation. So I backed up our data by going to File, Backup and
Restore, then Backup Quicken File. Then, to run a repair
operation, I clicked on File then File Operations. From
that option I could select Validate and Repair, but before I selected
it, I noticed that now the amount shown for the balance owed on the mortgage
was correct under Property in the listing of accounts. It seems
that just performing the backup resulted in the discrepancy being resolved. I
certainly didn't expect that to resolve the problem, but I was glad just doing
that apparently resolved the problem. Quicken was also now showing a correct
positive equity value based on what I had estimated for our home's
current value minus what we still owed on the mortgage.
[/financial]
permanent link
Fri, May 08, 2015 10:11 pm
High Chrome memory utilization
Checking on the cause for slow performance on a Microsoft Windows system, I
opened the
Task Manager and saw that memory utiilization was high.
Clicking on the
Memory column header to order the list of processes
by memory utilization, I saw that the Google Chrome web browser was consuming
most of the memory; there were many Chrome tabs open in the browser.
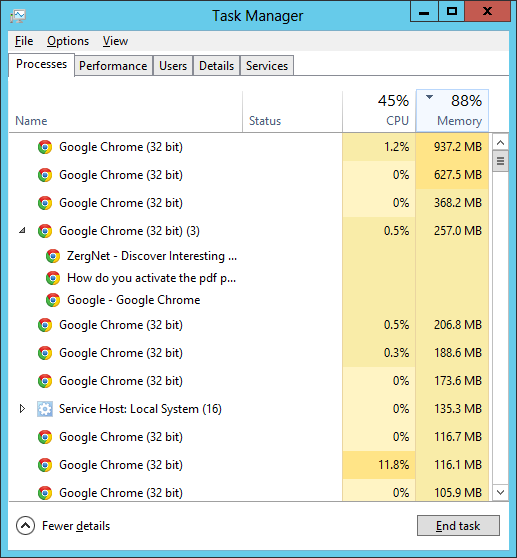
I could see that the Chrome tab consuming the most memory was one consuming
937.2 MB of memory.
To determine what webpages associated with tabs open in Chrome are
consuming excessive amounts of memory or CPU time, put
chrome://memory in the address bar of the browser. That will
provide information on the amount of memory consumed by each tab open in
the browser as can be seen in this
example. Since the entries aren't ordered by memory utilization, you
will need to scroll through the list to find the tabs consuming the most
memory.
In this case, when I scrolled through the list I saw the tab that was
consuming 937.2 MB of memory had a CNN.com article open in it. When I went
to that tab I saw a "Shockwave Flash has crashed" message at the top of the
tab. When I clicked on "Reload", I saw that memory utilization for that tab
inreased slightly. Moving back to a prior page in the tab with the back arrow
resulted in the Task Manager then showing the highest memory
utilization for a Chrome process to be about half the 937.2 MB shown previously.
I closed the tab to free memory.
[/network/web/browser/chrome]
permanent link
Thu, May 07, 2015 10:32 pm
Increasing disk space for a VM under VMWare Fusion 5.0.5
If you find that the disk drive space you originally allocated for a
Virtual Machine (VM) under VMWare is now inadequate, the process for
increasing the size of the drive allocated to the VM is fairly simple, but
you will have to delete any existing snapshots before you can increase the
size of the disk drive for the VM, which, though easily done, can take take
some time - I found it took an hour on my MacBook Pro to delete a snapshot for
a Windows XP VM. Once you've deleted existing snapshots, you can then
expand the disk drive size to accomodate your needs. Files with a .vmdk
extension are created to hold the VM's disk drive.
[ More Info ]
[/VM/vmware]
permanent link
Wed, May 06, 2015 9:29 pm
Curl SSL certificate problem
When attempting to download a file via HTTPS from a website using curl, I
saw the error message "SSL3_GET_SERVER_CERTIFICATE:certificate verify failed".
$ curl -o whitelist.txt https://example.com/BLUECOAT/whitelist.txt
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
0 0 0 0 0 0 0 0 --:--:-- --:--:-- --:--:-- 0c
url: (60) SSL certificate problem, verify that the CA cert is OK. Details:
error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify fail
ed
More details here: http://curl.haxx.se/docs/sslcerts.html
curl performs SSL certificate verification by default, using a "bundle"
of Certificate Authority (CA) public keys (CA certs). If the default
bundle file isn't adequate, you can specify an alternate file
using the --cacert option.
If this HTTPS server uses a certificate signed by a CA represented in
the bundle, the certificate verification probably failed due to a
problem with the certificate (it might be expired, or the name might
not match the domain name in the URL).
If you'd like to turn off curl's verification of the certificate, use
the -k (or --insecure) option.When I added the -k option, I was able to download the file
successfully.
$ curl -o whitelist.txt -k https://example.com/BLUECOAT/whitelist.txt
But I wanted to know what the issue was with the
public key
certificate and I wanted to get that information from a Bash shell prompt.
You can get the certificate from a website using the command
openssl s_client -showcerts -connect fqdn:443, where
fqdn is the
fully qualified domain name for the website, e.g. example.com. Port
443 is the standard port used for HTTPS. The certificate should be stored as a
.pem file. When I used openssl s_client -showcerts -connect
example.com:443 >example.pem, I saw the message
"verify error:num=19:self signed certificate in certificate chain"
displayed, which revealed the source of the problem.
A self-signed
certificate is one that has been signed by the same entity whose
identity it certifies. For a site using a self-signed certificate, your
traffic to and from that site is protected from eavesdroppers along the path
of the traffic, but the certificate doesn't offer validation that the site
belongs to the entity claiming to own it. But, if you have other reasons to
trust the site or are only concerned about third parties eavesdropping on your
communications with the site, then a self-signed certificate may be adequate.
E.g., the site could be your own site or belong to someone or an entity you
know is in control of the website. Some organizations use self-signed
certificates for internal sites with the expectation that members/employees
will ignore browser warnings for the internal websites, though if people
become accustomed to ignoring such errors there is the danger that they
will also be more prone to ignore such warnings for external sites where
a site's true controlling entity isn't the one they expect.
$ openssl s_client -showcerts -connect example.com:443 >example.pem
depth=1 /C=US/ST=Maryland/L=Greenbelt/O=ACME/OU=EXAMPLE/CN=EXAMPLE CA
verify error:num=19:self signed certificate in certificate chain
verify return:0
read:errno=0
The s_client parameter uses a generic SSL/TLS client to
establish the connection to the server.
s_client This implements a generic SSL/TLS client which can establish
a transparent connection to a remote server speaking SSL/TLS.
It's intended for testing purposes only and provides only
rudimentary interface functionality but internally uses
mostly all functionality of the OpenSSL ssl library.
The certificate is stored in example.pem in this case. You
would need to edit the file to remove everything but the "BEGIN CERTIFICATE"
and "END CERTIFICATE" lines below and the lines that lie between those two
lines.
-----BEGIN CERTIFICATE-----
-----END CERTIFICATE-----
Or you can use a Bash script
retrieve_certifcate to obtain the certificate; it will stip off the
extraneous lines. The code for the script is shown below:
#!/bin/sh
#
# usage: retrieve-cert.sh remote.host.name [port]
#
REMHOST=$1
REMPORT=${2:-443}
echo |\
openssl s_client -connect ${REMHOST}:${REMPORT} 2>&1 |\
sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p'
You can obtain information for the certificate from the PEM file
using the command openssl x509 -text -in example.pem. If
-issuer is appended, then only the issuer information will be
displayed, so I could see that the cerificate was self-signed with the
following command:
$ openssl x509 -noout -in example.pem -issuer
issuer= /C=US/ST=Maryland/L=Greenbelt/O=ACME/OU=EXAMPLE/CN=EXAMPLE CA
If you just want to verify the status of a certificate from the
command line without storing the certificate locally, you can add
the -verify 0 option.
-verify depth - turn on peer certificate verification
E.g.:
$ openssl s_client -showcerts -verify 0 -connect example.com:443
verify depth is 0
CONNECTED(00000003)
depth=1 /C=US/ST=Maryland/L=Greenbelt/O=ACME/OU=EXAMPLE/CN=EXAMPLE CA
verify error:num=19:self signed certificate in certificate chain
verify return:0
88361:error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed:/SourceCache/OpenSSL098/OpenSSL098-52.6.1/src/ssl/s3_clnt.c:998:
You can ignore all output from the command but the "verify error" line
with commands like the following:
$ openssl s_client -showcerts -verify 0 -connect example.com:443 2>&1 | grep "verify error"
verify error:num=19:self signed certificate in certificate chain
For another internal website, when I accessed the site in Firefox
with https://cmportal, Firefox reported the following:
This Connection Is Untrusted
You have asked Firefox to connect securely to cmportal,
but we can't confirm that your connection is secure.
Normally, when you try to connect securely, sites will present
trusted identification to prove that you are going to the right
place. However, this site's identity can't be verified.
What Should I Do?
If you usually connect to this site without problems, this error
could mean that someone is trying to impersonate the site, and you
shouldn't continue.
When I viewed the technical details for the certificate, Firefox informed
me that:
code760cmportal uses an invalid security certificate. The
certificate is only valid for the following names: 192.168.160.242,
servera.example.com (Error code: ssl_error_bad_cert_domain)
When I tried downloading the home page for the site with curl, I saw
the message below:
$ curl https://cmportal
curl: (51) SSL peer certificate or SSH remote key was not OK
I was able to get past that error with the -k or
--insecure parameter to curl, though then the page returned
reported I was being denied access to the requested web page due
to invalid credentials.
I downloaded the certificate for that site with openssl; since openssl
would wait for input after verify return:0, I used an
echo "" | to get it to complete.
$ echo "" | openssl s_client -showcerts -connect cmportal:443 >example.pem
depth=2 /C=US/O=Acme/OU=Anvils/OU=Certification Authorities/OU=Anvils Root CA
verify error:num=20:unable to get local issuer certificate
verify return:0
DONE
I removed all the lines before "BEGIN CERTIFICATE" and all those after
"END CERTIFICATE" and then checked the certificate for that .pem file with
the openssl command. That showed me a reference to servera
whereas I had accessed the site using cmportal..
$ openssl x509 -noout -in example.pem -subject
subject= /C=US/O=Acme/OU=Anvils/OU=Services/CN=servera.example.com
If you've accepted a self-signed certificate, or a certificate
with other issues, in Firefox, you can view the certificate following
the steps noted in Forgetting a certificate
in Firefox.
References:
-
Retrieving Password Protected Webpages Using HTTPS With Curl
Date: September 8, 2011
MoonPoint Support
-
How To Verify SSL Certificate From A Shell Prompt
Date: May 23, 2009
nixCraft
-
Example sites with broken security certs [closed]
Asked: November 9, 2009
Stack Overflow
-
Command line tool for fetching and analyzing SSL certificate
Asked: April 17, 2014
Server Fault
-
OpenSSL Command-Line HOWTO"
Published: June 13, 2004
Most recent revision: June 25, 2014
By: Paul Heinlein
madboa.com
-
x509 - Certificate display and signing utility
OpenSSL: The Open Source toolkit for SSL/TLS
[/network/web/tools/curl]
permanent link
Tue, May 05, 2015 10:32 pm
Checking WiFi status on Mac OS X
To check the status of a WiFi connection on a Mac OS X system, you can click
on the wireless networking icon, which is a series of curved lines one
beneath the other, at the top of the screen while holding down the
Option
key. You will then see the currently connected WiFi network with a
check mark next to it and details regarding the wireless connection.
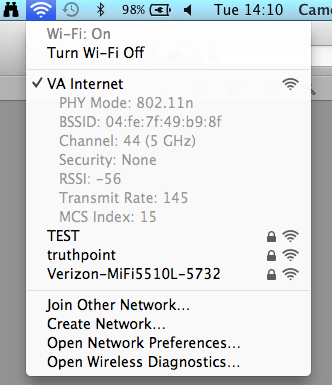
The following parameters will be displayed for the wireless connection
currently in use:
-
PHY Mode, e.g.
802.11n or one of the other wireless standards, such as a, b, g, etc.
-
Basic service set identification
(BSSID)
-
Channel
-
Security, e.g., the
wireless security
method employed, or "None" if no security mechanism is emmployed, such
as for a wireless network that is intended to be available for public
access.
-
Received signal strength indicator (RSSI), which provides a numeric
value indicating the strength of the signal. For Apple OS X systems, the value
will range from -100 as the worst value to 0 as the best. So a value of
-56 as shown above is about at the midpoint for signal strength.
-
Transmit Rate, which indicates the maximum transmission rate you might
achieve through the wireless access point or router, though you likely
won't be able to actually achieve that maximum rate.
-
Modulation and Coding Scheme (MCS) Index
For information on checking signal stength and other wireless parameters
from the command line on an OS X system, see
Checking WiFi signal
strength from the command line on OS X.
[/os/os-x/wireless]
permanent link
Mon, May 04, 2015 10:24 pm
Outlook 0x800ccc0f error message
I had a user on a Windows 7 system contact me today to report that he
was unable to check email from his system, but others at his location
were not experiencing problems. He was able to get to websites with his
browser, so there didn't appear to be an issue with Internet access. He
told me that Outlook was displaying a 0x800ccc0f error message, but he
didn't know what version of Outlook was present on his system, so I had
him check in Outlook by going to
Help then
About Microsoft
Office Outlook. He reported the version number was 14.0. I had
to look up the version name corresponding to that number. The name to
version number correlation is shown below:
| Version Name | Version Number |
|---|
| Outlook 97 | 8.0 |
| Outlook 98 | 8.5 |
| Outlook 2000 | 9.0 |
| Outlook XP/2002 | 10.0 |
| Outlook 2003 | 11.0 |
| Outlook 2007 | 12.0 |
| Outlook 2010 | 14.0 |
| Outlook 2013 | 15.0 |
So that version corresponded to Outlook 2013. With the version number,
I was able to provide instructions on how to determine what
POP3 server
was handling his email. It was pop3.firespring.com, so I had him run
a traceroute to it, i.e., tracert pop3.firespring.com. He
told me that was not completing successfully and some of the lines had values
of over 100 ms for the time for a response from the system at that particular
hop, so I at first thought there might be a congestin issue with the network
path to the mail server. If other systems on the same
LAN weren't experiencing the
problem, then perhaps his system was more sensitive to delays, perhaps with
a lower timeout value. But when I tried a traceroute from a Mac system, I
saw the same traceroute issue, but a telnet connection to the POP3 mail
server on the POP3 port, port 110, i.e., telnet pop3.firespring.com 110
resulted in an immediate OK response from the server
which seemed to rule out that hypothesis. So I suggested he contact his
mail service provider which found that he had an unusually large message
on the server. When that message was deleted from the server by the email
server provider his problem went away; apparently Outlook on his system
was timing out when it couldn't download that message in a reasonable
amount of time and then displaying the 0x800ccc0f error message.
References:
-
Outlook versions and
trivia
MSOutlook.info
[/os/windows/office/outlook]
permanent link
Fri, May 01, 2015 10:16 pm
Telemarketers spoofing calling numbers
The
U.S. Federal Communications Commission (FCC) in conjuction with the
Federal Trade
Commission (FTC) estabilshed a
Do Not Call
List. U.S. residents who don't want to receive calls from telemarketers
can add their phone numbers to the FCC's Do Not Call Registry. Once a number
has been added to the registry, telemarketers are not supposed to call the
number unless one of the following conditions applies:
- the calling organization has an established business relationship with you
- you have given prior written permission for calls from the caller
- the calls are not commercial or do not include unsolicited advertisements
- the calls are being made by or on behalf of a tax-exempt non-profit
organizations
I've had our phone numbers on the registry for years. I believe adding the
numbers may have reduced the telemarketing calls, but many telemarketers
ignore the Do Not Call Registry. I have been filing a complaint through the
FTC National Do Not Call Registry
website whenever I receive such calls. I fill out the
Submit a Complaint form after receiving such calls in hopes that if many
others are submitting complaints regarding the same calling number that the
telemarketing company will be fined for its disregard of the regulations
that apply to them.
Lately, though, I've been finding that a large number of such
calls are from "spoofed" numbers. E.g., today I received a robocall with a spiel
that began with "This is Rachel at Card Holder Services". The spiel
ended with a note that this would be my final notice, but I've been
receiving such telemarketing calls from "Rachel at Card Holder Services"
for months, each ending with the reference to a "final notice". The only
option at the end of the spiel was to hit 9 to speak to someone. The
person remarked about my desire to reduce my credit card rate; I said
"No, I want to be removed from the calling list". I asked very politely,
but the person immediately disconnected. I called the number that appeared
as the calling number on my cell phone. After several rings, I received
a recorded message typical of what you would find on someone's personal
voicemail. I figured the telemarketer had spoofed the calling number and
didn't leave a message, but a short while later I received a call from the
person who had that number who was wondering who had called him and why. I
told him about the telemarketing call and said I suspected when I heard
his voicemail that a telemaketer had spoofed his number. He understood
and mentioned he finds telemarketing calls annoying as well. The area
code and first 3 numbers of his number matched those for my cell phone,
likely because the telemarketer by using a number that would seem to be
local to me would be more likely to have someone answer the robocall.
Some people may avoid the plague of telemarketing calls by only answering
numbers they recognize, but I use my cell phone for work and can't tell
by looking at an incoming number whether it is a work-related call or
an annoying telemarketer, since I can't know the number for everyone
who may call me on a work-related matter and those calling on work-related
matters may be in other parts of the country. Nor can one even
reliably assume today that an area code reveals the geographical area
of the caller.
As long as a significant percentage of people buy whatever a telemarketer
is selling, telemarketers won't stop calling no matter how annoying most
people find such calls. But someone would be exceedingly foolish to provide
a credit card number and other personal information to some unknown caller
offering to reduce one's credit card rate in return for providing such
information to the caller. Since I've been getting such calls for months,
I can only assume that a significant number of people do so, though.
When I know the caller is ignoring the Do Not Call Registry, I assume that
the caller's business practices are dubious at best. And certainly when the
calling number has been spoofed, it would be prudent to assume that the caller
is a scammer who may use any credit card number you provide for his own
nefarious ends or sell it to others.
According to the FCC
Caller ID and
Spoofing page a telemarketer must:
-
Transmit or display its telephone number or the telephone number of the
seller on whose behalf the telemarketer is calling, and, if possible,
its name or the name and telephone number of the company for which it
is selling products or services.
-
Display a telephone number that you can call during regular business
hours to ask to no longer be called. This rule applies even to companies
that already have an established business relationship with you.
Under the Truth in Caller ID Act, violators can be subjected to a penalty of
up to $10,000 for each violation of the rules.
So what can you do in such cases? I filed a complaint for the above
mentioned call via the
FTC Do Not Call Registry complaint form. You can also
file a complaint through the FCC's
consumercomplaints.fcc.gov
site by submitting a
Phone Complaint.
For the "Phone Issues" field, you can select "Telemarketing (including
do not call and spoofing". It only takes a few minutes to complete the
complaint forms and I filed a complaint in this case there as well.
Will filing such complaints do any good? The
Rachel With Cardholder Services’ Coughs Up Refunds article published
on January 19, 2015 on the ABC News site notes:
The Federal Trade Commission, the nation’s consumer watchdog, has
reached a settlement with a collection of companies it says used that
ploy. And now a special administrator is preparing to mail out checks
to victims.
The total amount available to repay consumers is $700,000. The FTC says
it is mailing out 16,590 checks this week. Each check will be for $42.95
and must be cashed within 60 days.
But that article also notes:
In fact, after the FTC took its first action against “Rachel,”
investigators were frustrated when the calls continued, likely placed
by other sketchy companies.
I'm not looking for a remuneration for the disruption to my work and
wasted time from such calls, but I would like to see companies that ignore
the Do Not Call Registry and use spoofed numbers fined and, hopefully, put out
of business. I hope that others will also file complaints and that an
accumulation of such complaints will lead the FTC or FCC to track down at
least some of these companies and take action against them.
[/phone]
permanent link
Fri, May 01, 2015 6:11 pm
How to fix a problem with Entourage 2008 not indexing all email
After an issue with my MacBook Pro a few weeks ago that resulted in Microsoft
Entourage 2008 for Mac crashing, I found that searches for email would not
return all pertinent messages. I could search on subject, "from" addresses,
etc. and see results, but not all messages I knew were in the inbox or
other folders. E.g., if I searched by subject for daily logs I
receive, the search would not return any messages between December 31, 2014
and March 31, 2015, though I could see they were in the inbox if I ordered it
by subject.
To correct the problem, I clicked on the Apple icon in the upper,
left-hand corner of the screen, chose System Preferences and then
Spotlight from the Personal group. I confirmed that
Messages & Chats was checked (all entries were checked by
default).

I then clicked on the Privacy button.
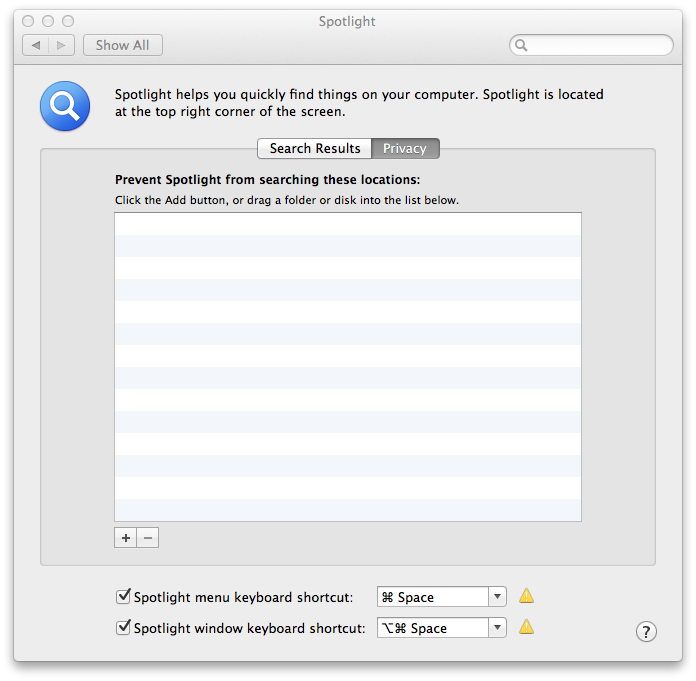
Within the Privacy window, I clicked on the plus sign, "+",
and addeded my home directory, e.g., jdoe, to the list of directories that
should not be searched. When you do so, a warning window will open with
a message similar to the one below:
Are you sure you want to prevent Spotlight from searching in "jdoe"?
If you exclude this location from Spotlight searches, the search feature
won't work in some applications.
Clicking on OK will add the directory and its subdirectories
to the exclusion list. After adding the home directory, I clicked on it
to highlight and select it, then clicked on the minus sign, "-" to remove the
directory from the exclusion list and cause a reindexing of that directory.
I then closed the Spotlight window.
I don't know how long the reindexing process took to complete. I didn't
peform any further searches in Entourage until the following day; at that
time searches did return all messages.
[/network/email/clients/entourage]
permanent link

Privacy Policy
Contact








