Tue, Jan 31, 2017 11:10 pm
Creating a rescue configuration for a Juniper SRX Firewall
You can create a rescue configuration to be used in the event you make some
change to a
Juniper Networks SRX
router/
firewall, which runs
Junos OS,
that makes the device inaccessible. With a
rescue configuration saved
on the device, you can return the router/firewall to a known operational
state. The rescue configuration saved on the device can provide a last resort
means of quickly restoring the device to operational status. You can use
either the web-based
graphical user interface (GUI) method to create a saved rescue configuration
via a web browser connection to the system or a
command line interface (CLI)
method.
[ More Info ]
[/security/firewalls/SRX]
permanent link
Mon, Jan 30, 2017 10:49 pm
Checking a website's security certificate with OpenSSL
You can use
OpenSSL, which is commonly installed on Mac OS X and Linux systems and which
is also available for other operating systems (the source code can be downloaded
from
OpenSSL Downloads and
a Windows implementation is available at
OpenSSL for
Windows), to check the security certificate of a website using an
openssl command in the
form
openssl s_client -showcerts -connect fqdn:port where
fqdn is the
fully qualified domain name (FQDN) of the website and
port is the
port that the website is listening on for
HTTPS
connections, which is usually
well-known port 443, though it may sometimes be another port, such as the
registered port 8443. The
showcerts option instructs openssl
to show all certificates in the
public key certificate chain.
[
More Info ]
[/security/encryption/openssl]
permanent link
Sun, Jan 29, 2017 7:52 pm
Setting up the Windows Subsystem for Linux on Windows 10
With the
Anniversary Edition of the Microsoft Windows 10
operating system (OS), Microsoft provides a an
Ubuntu-based
Bash shell that
will allow you to run
Linux software on your Microsoft Windows 10 system. If you
are unsure whether the Anniversary Edition update to Windows 10 is installed
on a system, you can follow the steps listed at
Determining which version of Windows 10
is installed. You can also use the instructions at
Determining the version of
Microsoft Windows from the command line. The Anniversary Edition is version
1607 of Windows. Or just checking the
software build will
reveal whether the Anniversary Edition is installed; if you see "build 14393"
or later, then the Anniversary Edition is installed on the system.
The Windows system will also need to be using the 64-bit version of Windows
10 rather than the 32-bit version - see
Determining if your version
of Windows is a 32-bit or 64-bit version for methods that can be used
to determine if the installed version of Windows is a 32-bit or 64-bit
version.
If the version of Windows is appropriate, then you can
follow these step by step
instructions to install the Linux subsystem.
[/os/windows/win10]
permanent link
Sat, Jan 28, 2017 9:46 pm
Setting the default mail application on Windows 10
If you wish to set or change the default mail app on a Microsoft Windows 10
system, you can take the following steps:
-
Click on the Windows Start button.
-
Click on Settings.
-
Click on System.
-
Click on Default apps.
-
Click on "Choose a default" under Email.
-
You should then see a list of email applications on the system;
click on the one you wish to be the default mail application.
-
Once you've chosen an email program, you can click on the "X" at
the upper, right-hand corner of the window to close it.
[ More Info ]
[/os/windows/win10]
permanent link
Fri, Jan 27, 2017 10:29 pm
Changing the UltraVNC passwords
To change the password used for connectivity to a system running
the
UltraVNC
free and open-source software that provides
remote-administration/
remote-desktop-software
functionality for
Microsoft Windows, select the icon representing
UltraVNC in
the system tray; it has an eye within it.
Right-click on it and select Admin Properties. At the Admin
Properties window, you can type a password in the "View-Ony Password"
that can be used to allow remote users access to the system via VNC. It
will only check the first 8 characters of a password.After making any
password change, click on the Apply button.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
Thu, Jan 26, 2017 10:56 pm
You can't open the application "Firefox.app" because it is not responding
I killed Firefox on my MacBook Pro laptop running OS X Yosemite (10.10.5)
by clicking on the Apple icon at the upper, left-hand corner of the screen then
selecting
Force Quit and then selecting
Firefox and clicking on
the
Force Click button. But when I tried to reopen Firefox,
I saw the message 'You can't open the application "Firefox.app" because
it is not responding.'
I clicked on OK and used Force Quit Applications again. I saw
Firefox in the list and again forced it to quit. I then clicked on the Firefox
icon in the
Dock at the bottom of the screen again, but Firefox didn't appear to open.
I double-clicked on it again, but it still didn't appear to open, though it
appeared in the Force Quit Applications list again with "not responding"
appearing next to its entry in the list of open apps. I tried clicking on the
Firefox icon in the Dock a third time and this time saw the 'You can't open
the application "Firefox.app" because it is not responding' message again,
though reopening Force Quit Applications again did not show "not
responding" next to the Firefox entry in its list. Nor was any other
application listed as being unresponsive. I tried the Force Quit
step again. Firefox remained in the list until I closed and reopened
Force Quit Applications. Though Firefox wasn't in the Force Quit
Applications list, I did see a process associated with Firefox
when I used the ps command to view processes running on the system.
$ ps -ef | grep -i Firefox | grep -v grep
723184451 6861 1 0 8:46AM ?? 0:00.03 /Applications/Firefox.app/Conte
nts/MacOS/plugin-container.app/Contents/MacOS/plugin-container /Library/Internet Plu
g-Ins/JavaAppletPlugin.plugin -greomni /Applications/Firefox.app/Contents/Resources/
omni.ja -appomni /Applications/Firefox.app/Contents/Resources/browser/omni.ja -appdi
r /Applications/Firefox.app/Contents/Resources/browser 1635 gecko-crash-server-pipe.
1635 org.mozilla.machname.776527788 plugin
$
[ More Info ]
[/os/os-x]
permanent link
Wed, Jan 25, 2017 11:08 pm
Extracting information from a pem file
The
X.509
standard is used to manage
digital certificates used for
public key encryption. One of the
filename extensions used for X.509 certificates is .pem,
which stands for
"
Privacy
Enhanced Mail". These certificates are
Base64
encoded
DER certificates. If you have a .pem certificate and want to
view information about the contents of the certificate, you can do so with
OpenSSL
software, which is commonly found on Linux and Mac OS X systems, but is
available for other operating systems as well. If you just want to view the
expiration date for a certificate you can use an
openssl command like the one
below:
$ openssl x509 -enddate -noout -in cacert.pem
notAfter=Aug 13 23:59:00 2018 GMT
$
[ More Info ]
[/security/encryption/openssl]
permanent link
Tue, Jan 24, 2017 9:28 pm
Viewing available upgrades in Radia Client Automation Application Self-Service Manager
If the
Radia Client Automation Self-Service Manager is in use on a Mac OS X system,
the app may be found in the
Applications/HPCA/Agent
folder on the system's disk drive. You can double-click on
Application Self Service Manager.app to see what
software updates are available for the system. If the system isn't
connected to the corporate network, e.g., if you need to establish
a
virtual private network (VPN) connection to be
able to connect to the server, and you see the message "Error code 769
encountered during the connect. Do you want to work offline?", you can
click on
Yes to still see available updates stored on the system
which you can install.
[ More Info ]
[/software/hpca]
permanent link
Mon, Jan 23, 2017 10:07 pm
Firefox Profile Location on an Apple OS X System
The
Firefox
web browser stores information about its user settings and state in a "profile"
directory for each user. On a Mac
OS X system (now macOS), such as my MacBook Pro laptop, you
can have Firefox open a
Finder window showing you the relevant profile folder or you
can find it from a command line interface (CLI), i.e., a shell prompt, by
opening a
Terminal window (you can find the Terminal program in the
Applications/Utilities folder). For the latter method, you can see the location
of the profile directory by issing the command
ls -l ~/Library/Application\ Support/Firefox/Profiles.
(you need to put a
backslash before the space in the directory path)
$ ls -l ~/Library/Application\ Support/Firefox/Profiles
total 0
drwx------ 53 jasmith1 ABC\Domain Users 1802 Jan 23 11:56 bgq13udo.default
$
[ More Info ]
[/network/web/browser/firefox]
permanent link
Sun, Jan 22, 2017 9:32 pm
Minecraft memory usage
You can control the amount of memory used by
Java for the
Minecraft
sandbox
video game by setting parameters in the
server_start.bat file located in the directory where the Minecraft software
was installed. To reduce the contention of the Minecraft server with
other software running on the system for the system's memory, you can specify
the maximum memory it will consume with a
Xmx parameter.
E.g., the following example uses a
server_start.bat
file where the maximum of memory that Java will use for running the
game software is 1
gigabyte (GB)
java -Xmx1G -Xms1G -jar forgeserver.jar nogui
PAUSE
[ More Info ]
[/os/windows/software/games/minecraft]
permanent link
Sat, Jan 21, 2017 11:33 pm
Error occurred message when upgrading freeSSHd
I needed to upgrade
freeSSHd, which
is free
Secure Shell (SSH) server software for Microsoft Windows systems, on a
Windows 8 system. The software allows remote users to log into a command line
interface on the Windows system via SSH and provides the capability to transfer
files via the
SSH File Transfer Protocol (SFTP). When I attempted to
install the latest version of the software over a prior version, however, the
installation was unsuccessful. If you see the following error message, you may
need to stop the SSHD service prior to performing the upgrade:
An error occurred while trying to replace the existing file:
DeleteFile failed; code 5.
Access is denied.
Click Retry to try again, Ignore to skip this file (not recommended), or
Abort to cancel installation.
[ More Info ]
[/os/windows/network/ssh/freeSSHd]
permanent link
Fri, Jan 20, 2017 10:02 pm
Installing an encryption plugin for UltraVNC
An
encryption
plugin is available for the
UltraVNC
open source remote administration/
remote
desktop software. The
SecureVNC Plugin has the following specifications:
- Default configuration uses 2048-bit RSA keys and 256-bit AES keys.
- RSA public-key cryptography supports 512-, 1024-, 2048-, and 3072-bit keys.
- Configurable choice of symmetric ciphers and keys:
- AES: Supports 128-, 192-, and 256-bit keys.
- Blowfish: Supports 56-, 128-, 192-, 256-, and 448-bit keys.
- IDEA: Supports 128-bit keys.
- CAST5: Supports 56- and 128-bit keys.
- ARC4: Supports 56-, 128-, 192-, and 256-bit keys.
- Classic interface for older UltraVNC versions 1.0.8.2 or below uses 2048-bit RSA keys and 128-bit AES keys.
- All versions are threadsafe, allowing the UltraVNC server to host multiple simultaneous viewers.
[
More Info ]
[/os/windows/software/remote-control/vnc/ultravnc]
permanent link
Thu, Jan 19, 2017 11:06 pm
Setting up a Juniper Networks SRX100 Router/Firewall
You can configure a Juniper Networks router/firewall, such as a
Dell J-SRX100H, which is manufacturered by Juniper Networks by connecting a
network cable between one of the 0/1 through 0/7 ports on the SRX100; don't use
the 0/0 port, because that is the default port for the "untrusted" side of the
device, i.e., for connections on the "outside" or Internet-facing side of the
device. If you have the connected device set to obtain an IP address by the
Dynamic Host Configuration Protocol (DHCP), it will be assigned an address from
the 192.168.1.1/24 subnet, 192.168.1.2. You can then log into the router
by opening a browser window and pointing the browser to http://192.168.1.1.
[ More Info ]
[/security/firewalls/SRX100]
permanent link
Wed, Jan 18, 2017 10:46 pm
Allowing inbound connectivity for an application under Windows 8
To permit inbound access to an application through the Microsoft
Windows Firewall
on a Windows 8 system, you can take the following steps:
-
Move the mouse pointer to the lower, left-hand corner of the window until
you see the Windows Start button appear. When you see it, right-click on it
and select Control Panel.
-
From the Control Panel, select System and Security.
-
Click on Windows Firewall.
-
Click on Allow an app or feature through Windows Firewall.
-
Click on the Change settings button.
Once you do so, the "Allow another app" button will no longer be grayed out and
you can click on it.
-
Find the application for which you wish to allow access through the firewall
and click on it to highlight and select it.
-
Click on the Add button. You should then see the program added to the
list of apps allowed to communicate through Windows Firewall.
By default access is allowed on "private" networks, such as your home or
work network. If you also want to allow access on "public" networks, such as
you would find at a coffe shop or airport, you can also click the check box
for "public".
-
Click on the OK button. You can then close the Windows Firewall
window. You should be able to connect to whatever port or ports the application
opens now from another system on the same
local area network (LAN).
[ More Info ]
[/os/windows/win8]
permanent link
Tue, Jan 17, 2017 10:30 pm
prisoner.iana.org
While using
Wireshark to
troubleshoot a
Domain Name System (DNS) issue for a server that sits
behind a firewall that performs
Network Address Translation (NAT), I noticed a DNS
response coming back where Wireshark showed the following in the "Info"
field for a packet:
Standard query response 0x21e1 No such name PTR 5.1.168.192.in-addr.arpa SOA
prisoner.iana.org
The server for which I was performing the troubleshooting has an IP
address of 192.168.1.5, which is a
private
IP address. There are 3 private IP address ranges; these ranges are also
sometimes referred to as "RFC 1918 addresses", since the private IP address
space is defined in RFC 1918
. A Request for Comments (RFC) is a document published by the
Internet Engineering Task Force (IETF). Some RFCs, such
as RFC 1918 become Internet Standards.
[ More Info ]
[/network/dns]
permanent link
Mon, Jan 16, 2017 10:35 pm
Selecting records containing a string in a MySQL or MariaDB database
If you wish to select only the records containing a particular
string, e.g., some word, etc., from a
MySQL
or
MariaDB
database table then
you can use
LIKE in the
SQL SELECT command. E.g., if I have a table named
Books that contains book information and one of the
columns in the database is
Title, I can select any books from
the database where the title contains "Unix" with the command below:
SELECT * FROM Books WHERE Title LIKE "%Unix%";
The percent sign (%) serves as a
wildcard character indicating that any number of other charcters will
match it. So by putting the percent sign before and after the word
Unix, the expression will find any books with titles that have "Unix"
anywhere in the title, e.g., at the beginning, middle, or end of the title.
If I only wanted to find those records in the Books table where the
title began with the word Unix, I could use the command below:
SELECT * FROM Books WHERE Title LIKE "Unix%";
Any characters that came after the word Unix would match, but the title
would need to start with "Unix". To find only those books where the word
appears at the end of the title, I could use the following command:
SELECT * FROM Books WHERE Title LIKE "%Unix";
If I wanted, instead, to find all of the records where the title doesn't
contain the word "Unix", I could put NOT before LIKE.
SELECT * FROM Books WHERE Title NOT LIKE "%Unix%";
[/software/database/mysql]
permanent link
Sun, Jan 15, 2017 10:30 pm
Turning on network discovery and file sharing on a Windows 8 system
If you wish to see folders from other Microsoft Windows systems on a
local area network (LAN) or those shared from Linux systems via
Samba, you may need to turn on network discovery on the Windows system(s)
in order to see the shared folder. E.g., if you double-click on
Network
in the Windows
File Explorer and see "Network discovery and file sharing
are turned off. Network computers and devices are not visible. Click to
change...", click on the message to enable network discovery.
[ More Info ]
[/os/windows/win8]
permanent link
Sat, Jan 14, 2017 11:07 pm
Determining or changing the system name for a computer running Windows 8
To determine the system name for a computer running the Microsoft Windows 8
operating system, you can right-click on the Windows
Start Button at the lower, left-hand corner of the
screen. If you don't see it, hit the
Esc key and move the mouse
pointer to the lower, left-hand corner of the screen where it should appear.
You will see the system's name listed in the "Computer name, domain,
and workgroup settings" section. If you want to give the system a new name,
click on
Change settings and then click on the
Change button.
If you want to obtain the information through a
command-line interface (CLI) method, instead, you can do so either
at a
command prompt or
PowerShell prompt.
[ More Info ]
[/os/windows/win8]
permanent link
Fri, Jan 13, 2017 10:27 pm
Deleting up to a word or back to a word in the Vi or Vim editor
In the
vi or
Vim
text editor, you can delete all characters on a line up to a specified
word by placing the cursor on the line at the point where you wish to
start the deletion then hit the
d key followed by the slash
key followed by the word up to which you wish to remove the characters
on the line. E.g., suppose you have the following line:
If you can force your heart and nerve and sinew To serve your turn long after they are gone, And so hold on when there is nothing in you Except the Will which says to them: “Hold on”;
From the poem
If—
by Rudyard Kipling (1865-1936)
If you wished to delete all of the text on the line from the word "To" up
until, but not including the word "And" in "And so hold on...", while in command
mode, not insert mode, you could move the cursor to the "T" in "To" and then
hit the d key followed by the
forward slash key (/) and then type And (make
sure you use the matching capitalization). The line would then appear as shown
below.
If you can force your heart and nerve and sinew And so hold on when there is nothing in you Except the Will which says to them: “Hold on”;
Suppose, instead, you had the cursor at the word "To" as before, but wanted
to delete backwards through the word "If", i.e., all the way to the beginning
of the line, instead. You could then hit the d key while in command
mode, then hit the question mark (?) key and type If.
You would then have the text below.
To serve your turn long after they are gone, And so hold on when there is nothing in you Except the Will which says to them: “Hold on”;
For the backwards deletion, the word you type after the question mark is
included in the deletion. In this case, if you wished to delete
backwards to the beginning of the line, you could also have hit the
d key followed by the ? key and then hit the
caret
(^) key, which represents the beginning of the line. Likewise,
you could hit the dollar sign ($) key to delete forward
to the end of the line, which it represents, or you could just hit the
D key, instead of the lower-case "d" to delete from the
current cursor position to the end of the line.
[/software/editors/vi]
permanent link
Thu, Jan 12, 2017 10:13 pm
Whitelisting email from a sender or domain using GoDaddy's email service
If you are using
Godaddy's email service and email sent from a particular sender isn't
showing up in your inbox, check the
bulk mail
folder, since there is a possibility that the mail was treated as junk email
and placed there. To keep email from a particular sender from being
subjected to checks that may result in email from that sender going into the
bulk mail folder or never appearing in any folder in your account, you can add the sender's email address to a list of
whitelisted
email addresses, i.e., ones that won't undergo the normal checks to ascertain
if the email is
email spam, which can sometimes result in
false positives, i.e., a legitimate email
you would want to receive is mistakenly classified as spam by a
software
algorithm that checks all incoming email. To whitelist an email address
or an entire
domain,
e.g., all email from any email address at example.com, take the following
steps while logged into your GoDaddy email account through the web interface
to your email account.
[ More Info ]
[/network/email/godaddy]
permanent link
Wed, Jan 11, 2017 10:36 pm
tar extraction errors - Cannot utime: Operation not permitted
I needed to copy the contents of one directory belonging to a user from one
Linux system to another. While logged into her account on the source system, I
created a
tar file, aka a "tarball", of the directory with the command
tar -cvf game.tar game to copy the contents of her "game"
directory and all of its subdirectories to the tar file. The tar file was about
20 MB in size, so I compressed it with the
gzip
command
gzip game.tar resulting in a game.tar.gz file about 5 MB
in size, which I transferred to the destination system. While logged
into her account on the destination system, I uncompressed the .gz file
with
gunzip game.tar.gz and then attempted to extract the
contents of the tar file into the same directory on the destination system as
on the source system. The directory already existed on the destination server
because I had many months ago copied everything in her home directory from the
source to the destination system. When I ran the command
tar -xvf
game.tar to extract the contents of the tar file, I saw files
extracted, but I also saw several "Cannot open: File exists" lines
in the output from the command, which terminated prematurely with the
following lines:
game/Update
tar: game/Update: Cannot open: File exists
game/FAQ
tar: game/FAQ: Cannot open: File exists
game/CONVERT.22
tar: game/CONVERT.22: Cannot open: File exists
game/BETA
tar: game/BETA: Cannot open: File exists
tar: game: Cannot utime: Operation not permitted
tar: Exiting with failure status due to previous errors
[ More Info ]
[/os/unix/commands]
permanent link
Tue, Jan 10, 2017 10:47 pm
Determining which version of Windows 10 is installed
There have been various iterations of Microsoft Windows 10 since it was
first released. Though you might think of Windows 10 as one version
compared to Windows XP, Vista, 7, 8, etc., but there are versions of
Windows 10 itself and "builds" within those versions.
You can determine which version of Microsoft Windows 10 is installed on a
system running Windows 10 by typing
winver in the
Cortana "Ask me anything" field. You will then see a window, such as the
one below, displaying the version and build number of the operating system.
In the example shown below from a Dell laptop, the system is running Version
1511 build 10586.713 of the Windows 10
operating system (OS), which is the
"November Update" to the OS.

[ More Info ]
[/os/windows/win10]
permanent link
Mon, Jan 09, 2017 10:32 pm
Thunderbird and Proxy Server Settings
When attempting to check email after installing
Mozilla Thunderbird on a Windows 10 system and configuring an email account
in Thunderbird, instead of email being downloaded, Thunderbird would show
"Connecting to pop3.example.com" and seemed to be indefinitely stuck at that
point. When I opened
Wireshark to observe the network traffic between the
Windows 10 laptop and the email server, I didn't see any traffic whether
Thunderbird was configured to use the
Post Office Protocol version 3 (POP3) port 110 or the secure
version of the protocol POP3S on
port 995. I set the Wireshark filter to be
tcp.port eq 110 || tcp.port
eq 995. I didn't see any traffic between to/from the server when I
changed the filter to look for traffic to/from the
IP address
of the server with
ip.addr == xxx.xxx.xxx.xxx where
xxx.xxx.xxx.xxx was the IP address of the server. After puzzling over the matter
for awhile, it finally dawned on me that I had prevoiusly configured the
Microsoft Edge browser to use a
SOCKS proxy server
via a
Secure Shell (SSH) tunnel set up with
PuTTY. I had disconnected the PuTTY connection to the
SSH
server, but hadn't changed the
proxy
server settings for the system so I realized the was likely the cause of
the problem, though I hadn't expected Thunderbird to use the system proxy
server setting by default.
[More Info]
[/network/email/clients/thunderbird]
permanent link
Sun, Jan 08, 2017 10:50 pm
Altering the contents of a file using sed
On Unix, Linux, and OS X systems, the
sed (stream
editor) utility can be used to modify the contents of a file replacing one
string, i.e., sequence of characters, with another.
E.g., suppose the file named
myfile contains the following
lines:
pink blue
red Blue
orange
blue purple blue
blue
If I want to replace all occurrences of the word "blue" with "green", I
could issue the following
sed command at a
Bash
shell prompt.
$ sed -i -e 's/blue/green/g' myfile
[ More Info ]
[/os/unix/commands]
permanent link
Sat, Jan 07, 2017 11:12 pm
Day of the week for dates in Excel and Calc
If you wish to display the day of the week, i.e, Monday, Tuesday, Wednesday,
etc., that corresponds to a particular date in
Microsoft Excel you can simply format the display of the date using
a custom format of
ddd. E.g., in Microsoft Excel 2013,
if I have dates in column A displayed in mm/dd/yyyy format, but I also
want the day of the week corresponding to those days to appear in column
B as shown below.
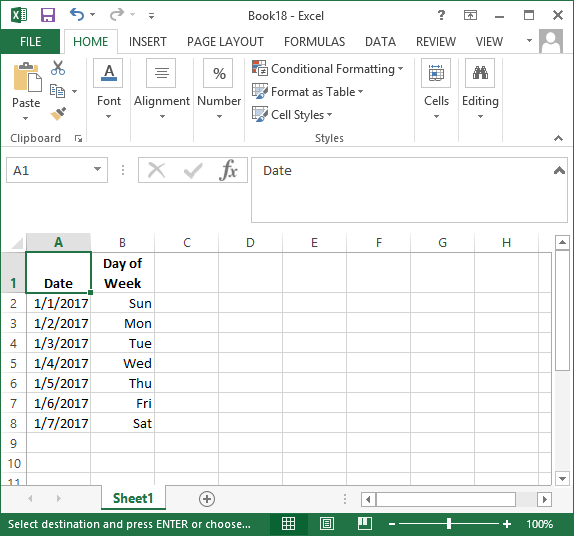
[ More Info ]
[/os/windows/office/excel]
permanent link
Fri, Jan 06, 2017 8:44 pm
Wireshark showing RST packets when unable to access website
I was unable to access a website on a webserver I frequently access.
When I examined the network traffic to and from the server with
Wireshark
network
analyzer software, I could see a repeating sequence of
SYN packets from the IP address of the Windows laptop from which I was
attempting to access the web server followed immediately by RST, ACK packets
from the IP address of the server. That sequence repeated over and over
again. E.g.:
130 2.766497 TCP 74 44970?80 [SYN] Seq=0 Win=14600 Len=0 MSS=1460 SACK_PERM=1 TSval=1029178963 TSecr=0 WS=16
131 2.768022 TCP 60 80?44970 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
132 2.800200 TCP 74 27779?80 [SYN] Seq=0 Win=14600 Len=0 MSS=1460 SACK_PERM=1 TSval=1029178972 TSecr=0 WS=16
133 2.801724 TCP 60 80?27779 [RST, ACK] Seq=1 Ack=1 Win=0 Len=0
[More Info ]
[/network/web/server]
permanent link
Thu, Jan 05, 2017 4:02 pm
Email stuck in the sendmail queue
A user repoted that she didn't receive an email someone sent her today.
I checked the
/var/log/maillog file to see if the mail server,
which is running
Sendmail, received the email. When I searched on part of the
sender's email address, I saw the message had been received by the mail
server:
# grep sbear /var/log/maillog
Jan 5 14:08:08 moonpoint sendmail[6276]: v05IxmvR006276: from=<sbearab1@y0hoo.c
om>, size=2339942, class=0, nrcpts=1, msgid=<1226622358.574156.1483642780691@mai
l.y0hoo.com>, proto=ESMTP, daemon=MTA, relay=omp1011.mail.ne1.y0hoo.com [98.138.
87.11]
So I checked Sendmail's queue with the
mailq command and saw
the message was stuck there. Note: Mailq is identical to sendmail -bp
.
# mailq
/var/spool/mqueue (1 request)
-----Q-ID----- --Size-- -----Q-Time----- ------------Sender/Recipient-----------
v05IxmvR006276 2338155 Thu Jan 5 14:08 <sbearab1@y0hoo.com>
(host map: lookup (yahoo.com): deferred)
<abad_kitty@moonpoint.com>
Total requests: 1
#The sendmail queue can be flushed with the command sendmail -q -v
.
# sendmail -q -v
Running /var/spool/mqueue/v05IxmvR006276 (sequence 1 of 1)
<abad_kitty@moonpoint.com>... aliased to ann
ann... Connecting to local...
ann... Sent
# mailq
/var/spool/mqueue is empty
Total requests: 0
#The meaning of the -q and -v options to the
sendmail command are
shown below:
-q[time]
Process saved messages in the queue at given intervals. If time
is omitted, process the queue once. Time is given as a tagged
number, with `s' being seconds, `m' being minutes (default), `h'
being hours, `d' being days, and `w' being weeks. For example,
`-q1h30m' or `-q90m' would both set the timeout to one hour
thirty minutes. By default, sendmail will run in the back-
ground. This option can be used safely with -bd.
-v Go into verbose mode. Alias expansions will be announced, etc.
[/network/email/sendmail]
permanent link
Wed, Jan 04, 2017 10:32 pm
SSH brute-force break-in attempts from 49.116.40.31
While troubleshooting a problem with a Linux system this evening, I opened
Wireshark
and noticed a
Secure Shell (SSH) packet from an unexpected source
address,
49.116.40.31. When I checked the
fail2ban log on
the system, I noticed that the
IP address
had been banned temporarily several times today, but break-in attempts resumed
whenever the timeout period for the ban expired.
# grep '49.116.40.31' /var/log/fail2ban.log | grep 'Ban\|Unban'
2017-01-04 17:20:46,190 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 17:30:47,135 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 17:31:15,276 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 17:41:16,250 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 17:41:43,390 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 17:51:44,299 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 17:52:14,441 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:02:15,243 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:02:43,383 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:12:44,182 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:13:13,323 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:23:14,227 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:24:23,414 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:34:24,183 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:35:33,368 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:45:34,148 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:46:44,331 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 18:56:45,126 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 18:57:14,282 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 19:07:15,124 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 19:07:44,270 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 19:17:45,043 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 19:18:14,190 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 19:28:15,111 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 19:29:23,297 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 19:39:23,304 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 19:39:51,441 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 19:49:52,326 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 19:50:21,472 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:00:22,251 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 20:00:49,390 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:10:50,192 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 20:11:19,338 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:21:20,121 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 20:21:49,263 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:31:50,036 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 20:33:38,258 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:43:39,059 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
2017-01-04 20:44:37,358 fail2ban.actions [25142]: NOTICE [sshd] Ban 49.116.40.31
2017-01-04 20:54:37,372 fail2ban.actions [25142]: NOTICE [sshd] UnBan 49.116.40.31
#
[ More Info ]
[/security/attacks/ssh]
permanent link
Tue, Jan 03, 2017 10:23 pm
Executing a JavaScript function when a browser window is resized
Sometimes you may want to have a certain event take place if a visitor to
your website resizes his or her browser window. With HTML 5, you can use the
onresize Event Attribute. You can apply the event attribute to
the body tag, e.g.:
<body onresize="someFunction()">
The event that would occur when the browser window is resized will depend
upon the code you place in the
JavaScript
function referenced, which in this case I've named
someFunction.
Note: the onresize attribute is new to
HTML5 and
isn't supported in
HTML 4.01 and older versions oF HTML. You can expect current
versions of browsers to support it, but if a visitor has an outdated browser
version, the function may not work for the visistor.
[ More Info ]
[/network/web/html]
permanent link
Mon, Jan 02, 2017 10:42 pm
Determining the program that is connecting to specific IP addresses
While troubleshooting a network issue using the
free and open source (FOSS)
network analyzer Wireshark, I noticed connections to
IP addresses that I thought might be associated with adware sites. The
connections were occurring from a Microsoft Windows 10 system. I suspected
that the connections were occuring via a browser tab that was open to a
website within the
K-Meleon
web browser, but I wanted to confirm that was the case and then, if it was,
to attempt to identify the particular tab open in the browser and the web page
that was responsible for the traffic, since there were several tabs open in
the browser. There were also other browsers open on the system with multiple
windows and tabs, so I might also need to check the tabs open in those
browsers.
To see all of the connections to websites on the
HTTP port, which is the
well-known port 80, I can
open a command prompt window and
use the netstat
command netstat -an and then
pipe its output into the
find
command, looking for ":80". The -a option shows all connections
and the -n option converts
IP addresses
and application layer protocols, such as HTTP, to numeric form.
[ More Info ]
[/os/windows]
permanent link
Sun, Jan 01, 2017 8:45 pm
Determining if a directory exists in a Bash script
I have a
Bash script that copies the prior day's mail log file
from
/var/log/maillog.1 to another directory for archiving.
The archive directory contains a subdirectory for each year's mail logs.
Today is the first day of a new year, so I needed to create a 2017 directory.
I could manually create the directory, but I thought I'd modify the Bash
script that runs from
Cron to check on whether the current year's directory exists
and, if it doesn't create it, so, if I forget in future years to create a
new year's directory the script will create it for me.
You can check if a directory exists with code similar to what is shown below:
if [ -d "$DIRECTORY" ]; then
# Insert code to be executed
fi
Or, to check if a directory doesn't exist and execute commands if it
doesn't:
if [ ! -d "$DIRECTORY" ]; then
# Insert code to be executed
fi
Note: putting the $DIRECTORY
variable
in double quotes allows for cases where the directory name may contain a space.
Though that won't be the case for my yearly subdirectories, it is something
you can allow for by enclosing the variable name in double quotes.
[ More Info ]
[/os/unix/bash]
permanent link

Privacy Policy
Contact




