Sun, Feb 24, 2008 11:22 pm
Memory Upgrade for Gateway PC Model Number MFATXPN1 ESX 500S P04
I upgraded the memory in a Gateway PC model number MFATXPN1 ESX 500S P04
(that is the model number listed on the back of the computer).
The system, which was running Windows XP Professional, had only 256 MB of
memory installed.
The following memory module was already in the system:
| MT8VDDT3264AG-265C4, PC2100U-25330-A1 |
US BZABW72029 200303 |
| 256MB, DDR, 266MHz, CL2.5V |
The BIOS memory information was as follows:
BIOS Settings
| BIOS Version | RG84510A.15A.0021.P11 |
| |
| Processor Type | Intel (R) Pentium (R) 4 |
| Processor Speed | 2 GHz |
| System Bus Speed | 400 MHz |
| System Memory Speed | 266 MHz |
| |
| Cache RAM | 512 KB |
| |
| Total Memory | 255 MB |
| Memory Bank 0 | 256 MB (DDR 266) |
| Memory Bank 1 | Not Installed |
I installed the following PNY
memory module in the second of the two memory slots in the system.
PNY 512MB
DDR
PC2700
333MHz / 266 MHz
OPTIMA&trade Memory
The following information was on a sticker on the module:
| 512MB,DDR DIMM,Q |
ASSY. IN TAIWAN |
| 64WQD-T PO135492 |
The package had "MD0512SD1-333-BB" on it above the
UPC. The
UPC was 7 51492 34983 1.
When I booted into Windows and ran winver, it showed
"Physical memory available to Windows: 784,176KB".
I ran a 30 minute test of the memory with
Windows Memory Diagnostic
Beta. No errors were found in the 3 passes of the diagnostic program that
were run.
[/hardware/pc/memory]
permanent link
Sun, Feb 24, 2008 10:44 pm
Memory Upgrade and Sound Card installation in Gateway E2300 PC
I upgraded the memory in a Gateway PC model number
MATXHDS MDW E 2300 (that is the model number listed on
the back of the computer; a sticker on the side of the
computer lists the model number as E2300). The system, which was running
Windows XP Professional, had only 256 MB of memory installed.
BIOS Utility - Main
| |
| BIOS Version | BF86510A.15A.0080.P18 |
| |
| Processor Type | Intel(R) Celeron(R) CPU |
| Processor Spped | 2.8 GHz |
| Systm Bus Speed | 533 MHz |
| System Memory Speed | 333 MHz |
| |
| L2 Cache RAM | 256 KB |
| Total Memory | 256 MB |
| Memory Mode | Single Channel |
| Memory Channel A Slot 0 | 256 MB (DDR333) |
| Memory Channel A Slot 1 | Not Installed |
| Memory Channel B Slot 0 | Not Installed |
| Memory Channel B Slot 1 | Not Installed |
I also needed to install a sound card, since the on-board audio stopped
working. I changed the BIOS settings for the on-board audio support from
"enabled" to "disabled". The option is listed under Advanced then
Peripheral Configuration in the BIOS Setup Utility.
I checked the Crucial Memory site
for information on the memory that the system will support.
| Manufacturer | Gateway |
| Product Line | E Series |
| Model | E2300 (4 DIMM slots) |
The Crucial Memory site providded the following information at
Computer memory upgrades for Gateway E-2300 Series (4 DIMM Slots)
| Maximum Memory: | 4096MB |
| Standard Memory | 256 or 512 removable |
| Slots: | 4 (2 banks of 2) |
Although the memory can be installed one module at a time, the best
performance comes from using matched pairs of modules.
Each memory slot can hold DDR PC3200, DDR PC2700 with a maximum of
1 GB per slot.*
*Not to exceed manufacturer supported memory.
The Crucial Memory site also had the following series of questions and
answers regarding memory for the system:
Q: Will my system recognize the maximum upgrade?
A: Possibly
How much memory your Windows OS will recognize depends on which version of
Windows you are running. 32-bit versions of Windows will see (and utilize)
only 3GB or 3.5GB. To utilize more memory, install a 64-bit version of your OS.
More information about OS memory maximums can be found at
http://www.crucial.com/kb/answer.aspx?qid=4251.
Q: What memory goes into my computer, and will a
faster speed be backward-compatible?
A: DDR memory with support for DDR PC3200,DDR PC2700 speeds.
Because DDR memory is backward-compatible, you can safely upgrade your system
with any of the guaranteed-compatible DDR speeds listed below, even if your
manual calls for PC1600 or PC2100 speeds. [DDR PC3200 and DDR PC2700 modules
were listed below the statement]
Q: How much memory can my computer handle?
A: 4096MB
Adding the maximum amount of memory will improve performance and help extend
the useful life of your system as you run increasingly demanding software
applications in the future.
Q: Do I have to install matching pairs?
A: Yes
Your system requires that you install memory in pairs.
The system had a 256 MB memory module in Channel A DIMM0. That module
had the following information on a sticker on it.:
| Hynix |
KOREA 03 |
| PC2700U | 0430 |
| 256MB DDR 333MHz CL2.5 |
| HYMD232646B8J-J AA-A |
I put the following memory in the system:
Kingston Technology
Value RAM
KVR333/1GR
The module had a sticker on it with the following information:
Kingston
Technology |
KVR |
| KVR333/1GR |
| 740617072662 | 2.5V |
| Warranty Void if Removed |
The Crucial Memory site indicated that memory must be installed in
matching pairs, but I wasn't sure if that applied just to modules inserted
in the same channel, i.e., I wasn't sure if I could install the 1 GB module
in Channel B, since the 256 MB module was in channel A.
I put the new module in Channel B DIMM0. When I powered on the system,
I saw "1264MB System RAM" but then received the error message
"Dual-channel operation requires identical paired
DIMMs installed across both memory channels." I then tried the new
1 GB module in Channel A DIMM1. Again I saw "1264MB System RAM" and
the same error message, so I removed the 256 MB module and moved
the 1 GB module to Channel A DIMM0. This time when I powered on the
system I saw "1008 System RAM" followed by "Keyboard Error" and then
"Memory Size Decrease". I powered the system off and on and didn't
see the keyboard or "memory size decrease" messages again, though
the system did display "1008 System RAM" again.
When I checked the BIOS configuration, I saw the following:
BIOS Utility - Main
| |
| BIOS Version | BF86510A.15A.0080.P18 |
| |
| Processor Type | Intel(R) Celeron(R) CPU |
| Processor Spped | 2.8 GHz |
| Systm Bus Speed | 533 MHz |
| System Memory Speed | 333 MHz |
| |
| L2 Cache RAM | 256 KB |
| Total Memory | 1024 MB |
| Memory Mode | Single Channel |
| Memory Channel A Slot 0 | 1024 MB (DDR333) |
| Memory Channel A Slot 1 | Not Installed |
| Memory Channel B Slot 0 | Not Installed |
| Memory Channel B Slot 1 | Not Installed |
When I selected the Advancecd tab in the BIOS Setup Utility
and then chose Video Configuration, I saw the following:
| Video Configuration |
| Primary Video Adapter |
[AGP] |
| Frame Buffer Size |
[ 16MB] |
Presumably, the remaining 16 MB of the 1024 MB module is being allocated
to the frame buffer, which is why the system is reporting 1,008 MB during
the Power-on
Self-test (POST) process.
When I booted into Windows and ran winver, I saw
"Physical memory available to Windows: 1,030,896 KB".
I had also installed a Dynex model DX-SC51 sound card in PCI slot 1
at the same time I installed the memory.
When I checked on the sound card, Windows Media Player reported
"Windows Media Player cannot play the file because there is a problem
with your sound device. There might not be a sound device installed
on your computer, it might be in use by another program, or it might not be
functioning properly."
Under the Device Manager, I saw "Unknown device" listed under
display adapters, but no new audio device listed. When I tried
to install the Dynex driver, I saw the warning message "Undetermine Card!
Please do not click cancel on device manager!" Clicking on OK
there produced another warning message "OS not support!"
I opened the case and checked the sound card. I found it wasn't
seated fully in its slot. I reseated the card. When I rebooted and logged
in as the adminsitrator, the Found New Hardware Wizard appeared.
I inserted the CD that came with the sound card. The wizard indicated it
found a Multimedia Audio Controller, an Envy24 Family Audio Controller WDM.
After the sotware was installed, I was able to play music files on the
system and hear sound from the speakers.
I ran a memory test on the new memory module with
Windows Memory Diagnostic
Beta. I let the test run for an hour and 30 minutes. The diagnostic program
completed 22 passes with no errors found.
[/hardware/pc/memory]
permanent link
Sun, Feb 24, 2008 11:51 am
Switching Rdesktop from Full-Screen to Windowed Mode
Rdesktop is free, open-source,
software that provides the capability for remotely controlling a
Microsoft Windows system from a Linux or Unix system.
I sometimes encounter a problem where I can't see the taskbar at the
bottom of the Windows display or the bottom of windows displayed on the
remote Windows system due to differences in the resolution for the
screen on the Linux/Unix system and the resolution of the Windows system.
The problem can be resolved by specifying the -f option when
starting rdesktop, so that you get a full screen display., e.g.
rdesktop -0 -f -u jsmith 192.168.0.44. But what do you do
when you wish to put the remote session in a window rather than have it
occupy the full screen without disconnecting? You can hit the
Ctrl-Alt-Enter keys simultaneously to switch to a windowed
view. You can also use Ctrl-Alt-Enter to switch to a full-screen
view, if you didn't start redesktop with the -f
option.
References:
- Rdesktop
Rdesktop.Org
-
Controlling a Windows System from a Linux System
January 12, 2006
MoonPoint Support
[/os/windows/software/remote-control/rdp]
permanent link
Sat, Feb 23, 2008 11:34 pm
Ghost Console Waiting for Console Services
On a system with Symantec Ghost 7.5,
I tried starting the
Ghost Console, but it hung
with the following message:
| Wait... |
Waiting for console services to start |
Cancel
|
When I checked the Ghost services (click on Start, select
Run, type services.msc and hit Enter),
I found the Symantec Ghost COnfiguration Server was
started, but not the Symantec Ghost Database Service,
which had a manual startup type. I double-clicked on
Symantec Ghost Database Service and clicked on the
Start button to start it. I received the error message below:
| Services |
 |
Could not start the Symantec Ghost Database Service service on Local
Computer.
Error 2: The system cannot find the file specified.
OK
|
The "path to executable" value was C:\Program Files\Symantec\Ghost\bin\dbserv.exe. When I
checked, I found there was no C:\Program
Files\Symantec\Ghost directory. I believe
it wasn't recovered when a disk drive problem
occurred previously. To correct the problem, I reinstalled
Symantec Ghost. I chose the Repair option
during the installation. At the end of the repair operation,
I saw the error message below:
| Symantec Ghost Configuration
Server |
 |
08001 [Sybase][ODBC Driver][Adaptive Server
Anywhere]Unable to connect to
database server: Database server not running
Error 2: The system cannot find the file specified.
OK
|
So I tried the Remove option to "Remove
Symantec Ghost Corporate Edition from your computer".
After deinstalling the software, I reinstalled it.
The Symantec Ghost Console then started
without a problem. And when I checked the running
services, I saw that both Symantec Ghost
Configuration Server and Symantec
Ghost Database Service were started.
I didn't see the client systems in the default machine
group, so thought I had to add the client systems back into the
console. When I tried to reinstall the client
software on a system, the installation failed.
When I checked the
RemoteInstall.log, I saw the reason listed
as "Remotely Installed Client is installed on this
machine."
To resolve the problem I restored the
privkey.crt, pubkey.crt,
and C:\Program Files\Symantec\Ghost
directory from a Ghost backup I had from some time ago.
To backup those files and that directory or restore
over them, you should close the Ghost Console,
if you have it open, and stop the running Ghost services.
You can stop the Ghost services by clicking on
Start, then selecting Run
and typing the following command and hitting
Enter. You need to include the double
quotes where shown below.
"c:\program files\symantec\ghost\ngserver.exe" -stop
If you check the running services, you should then see
both Symantec Ghost Configuration Server and
Symantec Ghost Database Service are stopped.
I then restored the privkey.crt,
pubkey.crt, and C:\Program
Files\Symantec\Ghost directory from the backup.
Afterwards, I ran the command
"c:\program files\symantec\ghost\ngserver.exe" -start
to restart the Symantec Ghost services. I then saw the
systems in the default machine group I had been using
previously for the Ghost backups.
References:
-
How to move the Symantec Ghost Solution Suite 1.x Console to a different computer
or retain Console settings during a reinstall
Document ID: 2001050812540225
Last Modified: 11/08/2007
Date Created: 05/08/2001
Operating System(s): DOS, Windows 95, Windows 98, Windows NT,
Windows 2000, Windows ME
Product(s): Symantec Ghost 7.0, Symantec Ghost 7.5,
Symantec Ghost 8.0, Symantec Ghost 8.2, Symantec Ghost Solution Suite 1.0,
Symantec Ghost Solution Suite 1.1
Release(s): Ghost 7.0 [All Releases], Ghost 7.5 [All Releases],
Ghost 8.0 [All Releases], Symantec Ghost 8.2 [All Releases], Symantec
Ghost Solution Suite 1.0 [All Releases], Symantec Ghost Solution Suite 1.1
Symantec Corporation
[/os/windows/utilities/backup/ghost]
permanent link
Sat, Feb 23, 2008 2:21 pm
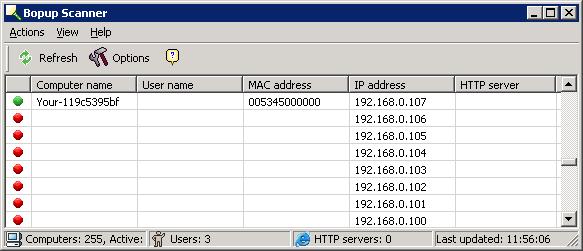
Bopup Scanner
Bopup Scanner is a
freeware network scanner that displays active computers with user names
logged into the computers (NetBIOS), MAC and IP addresses. Bopup Scanner also
recognizes and shows HTTP (Web) servers running on remote computers (TCP ports
80, 8080), if you select the option to have it scan for webservers, quickly
detects online computers, and allows you to browse shared resources of a remote
computer. You can save the results of a scan to a text file.
Bopup Scanner will perform a NetBIOS scan of a network, which will
show Windows systems on the network. The program first tries to
ping an address it is scanning. So, if you were watching its
scan with a sniffer, you would see an
ARP request
for the IP address. If there is a reply to the ARP request, an
ICMP echo
request is sent to the IP address. If an echo reply is received,
Bopup Scanner will then check for a response from the scanned IP address on
UDP port 137.
Port 137 is associated with the NetBIOS Name Service commonly used
on systems running the Microsoft Windows operating system. The
NetBIOS Name Service is typically how Windows computers find out information
concerning the networking features offered by a computer, such as system name,
file shares, etc.
Because it is only scanning for responses to NetBIOS Name Service requests,
Bopup Scanner will show a red circle for IP addresses where it received no
response to a NetBIOS Name Service query, even though there may be a system
at that address. E.g. there may be a Linux system, networked copier, router,
etc. at the address.
Regarding installation of the software, there is no installation procedure for
the program. You simply run scanner.exe. When you first run it,
it will create the following registry entries:
Keys added: 5
-------------
HKEY_CURRENT_USER\Software\B Labs
HKEY_CURRENT_USER\Software\B Labs\Bopup Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner\Scanner
HKEY_CURRENT_USER\Software\Bopup Scanner\Scanner\Settings
After starting the program, click on the Refresh button with
the green arrows next to it on the toolbar menu to begin a scan of the
subnet the system is on.
If you wish to check on whether a webserver is running on any of the
scanned IP addresses, click
on Options and check "Scan for HTTP servers (80, 8080 ports)".
You can save the results to a text file by clicking on Actions
and selecting Save list.
The developer, B-Labs Software,
also offers other
software that can be used for secure instant messaging.
Download Bopup Scanner
Developer Website
MoonPoint
Support (may not be the most current version)
[/network/tools/scanning/bopupscanner]
permanent link
Thu, Feb 21, 2008 12:34 pm
Internet Explorer Crash Recovery
An area in which
Opera is far superior
to Internet Explorer as a web browser is crash recovery. Internet Explorer,
even in version 7.0, does not provide any crash recovery features. In
Opera, should the browser or system crash, when you reopen the browser,
you can go back to exactly where you were prior to the crash. You can
have all of your tabs reopened and even move backwards through the prior
URLs you visited
in each tab. In contrast, Internet Explorer offers no crash recovery
features. Since I've often encountered probelms with Internet Explorer
crashing or hanging, I find the lack of any crash recovery features in the
browser to be a major drawback to using Internet Explorer.
So, I decided to look for an add-on that might add similar
functionality for Internet Explorer. I found a free add-on, IE7Pro, that offers that functionality
as well as other enhancements for Internet Explorer. The developer states
"IE7Pro includes Tabbed Browsing Management, AD Blocker, Flash Block,
Super Drag Drop, Crash Recovery, Proxy Switcher, Mouse Gesture, Tab
History Browser, Inline Search, User Agent Switcher, Webpage Capturer,
Greasemonkey like User Scripts platform, User Plug-ins and many more
power packed features. You can customize not just internet Explorer, but
even your favorite web site according to your need and taste using IE7Pro."
During the installation, which uses a Nullsoft Install System v2.33
installation program, you are given the option to select default settings,
which are shown below:
Please select default settings:
[x] Enable ADblock
[ ] Enable Userscripts
[ ] Enable Plugins
[X] Enable Spelling Checker
[ ] Set EasyHome as Homepage
At the end of the installation, you are requested to set the default
search engine to be IEPro's Google based search, to help finance
further development of the software, but you don't have to
do so. Selecting that option is certainly a small measure that you can
take to make continued development of the software possible.
To simulate a system crash, I powered off the system. When I
restarted the system and opened Internet Explorer, I saw a "Crash
Recovery" window stating "Your last session crashed, Please review and
open last URLs. All of the Internet Explorer 7 tabs I had open previously
were listed and checked to be reopened. I could deselect tabs I didn't
want reopened, if I wished. There were also Select All and
Select None buttons. I chose to reopen all of the tabs I had
open previously. Unfortunately, unlike Opera's crash recovery feature,
I couldn't click on the backwards arrow button in Internet Explorer
to view my history of previously visited sites in any tab. So, IE7Pro
definitely offered an improvement over the total lack of crash recovery
features in Internet Explorer, but also falls far short of the built-in
crash recovery features of Opera.
References:
-
IE7Pro User Guide
IE7Pro.com
-
IE7Pro FAQ
IE7Pro.com
[/network/web/browser/ie]
permanent link
Tue, Feb 19, 2008 11:27 pm
Counting Non-Blank Cells in a Spreadsheet and Using Multiple Criteria for Counting
Either the
counta or
countif functions can
be used to count the number of cells that are not blank in
a spreadsheet.
E.g., suppose you have the following information in a spreadsheet
| | A | B |
| 1 |
apple | maple |
| 2 |
| oak |
| 3 |
plum | birch |
| 4 | | birch |
| 5 | apricot | |
The function counta(A1:A5) would count those cells that
aren't empty in cells A1 to A5 yielding 3.
The function countif(B1:B5,"*") would also count those
cells that contain text in cells B1 to B5, yielding 4
as well.
Note: counta will count cells that have formulas
in them even though those formulas may amount to nothing appearing
in the cell, i.e. they evaluate to "".
If you wanted to count the number of cells that contained specific
text, e.g. birch, you could use
countif(B1:B5,"birch"), which would yield 2.
The count is case insensitive, i.e., if one of the cells contained "BIRCH",
instead of "birch", the count would still be equal to two.
If you wanted to count the number of cells that contained "birch" in
column B and "plum" in column A, then countif won't work, since
you can only specify one criteria with it. You could use sum
instead. E.g. sum((B1:B5="birch")*(A1:A5="plum")), which
yields 1. The * in this case "ands" the two
conditions. Note: You have to hit the Ctrl, Shift, and Enter keys
simultaneously when you've typed the formula in order to enter it. If you
don't, you will see a #value appear in the cell. This type of
formula is considered to be an "array" formula or CSE formula, since it
requires the Ctrl-Shift-Enter keys to be hit to enter it. When it is entered,
you will see {} appear around the formula.
References:
-
Excel -- Worksheet Functions -- Count Cells
Last updated: November 11, 2006
Contextures -- Microsoft Office
Consulting
-
Excel Developer Tip: Summing and Counting Using Multiple Criteria
Excel Developer Tip Archives
[/os/windows/office/excel]
permanent link
Mon, Feb 18, 2008 8:30 am
Symantec AntiVirus Server Could Not Collect Log Data From Client
On a Symantec AntiVirus Corporate Edition 8.1 server, I tried checking the
logs for a client system through the Symantec System Center by unlocking
the server group, right-clicking on a client system, selecting
All
Tasks,
Symantec AntiVirus,
Logs, and
Scan
History. I received a message that the log data couldn't be
collected from the selected computer.
| Symantec AntiVirus Management Snap-In |
Symantec AntiVirus could not collect all the log
data from the selected computer(s).
Please verify that Symantec AntiVirus is running on these computers.
OK
|
I received the same message if I tried viewing any log.
Symantec has a knowledgebase article on the problem at
Error: "Symantec AntiVirus could not collect all the log data from the
selected computer(s) . . ." when viewing client logs in Symantec System Center
. I followed the steps listed in that article.
I could ping the IP address of the system and ping -a 192.168.0.7
showed the hostname associated with the address. I could also ping the server
from the client system using ping and ping -a,
which confirmed network connectivity and the ability to do reverse lookups
on the IP addresses to get host names.
I checked for the presence of any .cer server group root certificate on
the server and the client. I didn't see any .cer file on either system, but
nor did I see a certificate on a client for which I could successfully check
log files from the antivirus server, so I didn't think that was the source
of the problem.
I could successfully start the Symantec AntiVirus Client program on
the client system. It showed the correct server name. Though nothing
was listed for "group", nothing was listed for "group" on a system I could
successfully query from the server, either.
And from the server, I could query the client and see that the
Symantec rtvscan.exe program was running.
C:\>tasklist /s 192.168.0.7 /fi "imagename eq rtvscan.exe"
Image Name PID Session Name Session# Mem Usage
========================= ======== ================ =========== ============
Rtvscan.exe 1760 0 46,604 K
When I checked the Windows XP firewall settings on a system I could successfully
query from the antivirus server, I saw a firewall rule listed for
User Datagram
Protocol (UDP) port 2967, which the Symantec RTVScan program uses.
I checked the firewall rules on the system
I couldn't successfully query with the command netsh firewall show
portopening. I did not see a rule for RTVScan, so I created one from
the command line using the command netsh firewall set portopening
protocol = UDP port = 2967 name = "Symantec AntiVirus Client Management"
mode = ENABLE scope = CUSTOM 192.168.0.33 (IP address 192.168.0.33
corresponds to the IP address of the antivirus server).
When I tried checking the antivirus log files from the server again, I
still could not do so. Looking at the firewall rules on the client
with netsh firewall show portopening verbose = enable (you
have to specify the verbose option to see the scope of
rules), I saw that I had mistyped the IP address of the server when I
created the RTVScan rule with the netsh command. So I re-entered the
netsh firewall set portopening protocol = UDP port = 2967 name =
"Symantec AntiVirus Client Management" mode = ENABLE scope = CUSTOM
192.168.0.33 command exactly as before with the exception that this
time I specified the IP address correctly.
I was then able to check the virus history and other logs on the client
from the Symantec System Center.
References:
-
Error: "Symantec AntiVirus could not collect all the log data from the
selected computer(s) . . ." when viewing client logs in Symantec System Center
Document ID: 2003032010404748
Last Modified: 11/15/2006
Date Created: 03/20/2003
Operating System(s): Windows 2000, Windows Server 2003 32-bit Edition,
Windows 98, Windows Me, Windows NT 4.0 SP6a, Windows 2000 Professional, Windows
XP Professional
Product(s): Symantec AntiVirus Corporate Edition 10.0, Symantec
AntiVirus Corporate Edition 8.0, Symantec AntiVirus Corporate Edition 9.0,
Symantec Client Security 3.0, Symantec AntiVirus 10.1, Symantec Client Security
3.1
Release(s): SAV 10.0 [All Releases], SAV 8.0 [All Releases], SAV 9.0
[All Releases], Symantec Client Security 3.x [All versions], Symantec AntiVirus
10.1, Symantec Client Security 3.1
Symantec Corporation
-
Allow Rtvscan Access Through Windows XP Firewall
April 9, 2007
MoonPoint Support
-
Configuring Windows XP Firewall for Symantec Antivirus Client
April 9, 2007
MoonPoint Support
[/security/antivirus/symantec]
permanent link
Sun, Feb 17, 2008 11:45 pm
Unable to Unlock Symantec AntiVirus Server Group
I was unable to unlock the server group on a Symantec AntiVirus Corporate
Edition 8.1 server. I was also unable to start the Symantec AntiVirus
Server service or update the virus definitions on the server.
I discovered the problem was due to corrupt virus definitions.
[ More Info ]
[/security/antivirus/symantec]
permanent link
Sun, Feb 17, 2008 8:18 pm
Encoding Spaces in URLs
If you have a filename that includes spaces, you should encode the URL that you
use for any links to the document, i.e.
%20 should be used wherever
a space occurs in the filename.
You can go to
URL Encoding to see a list of characters that should be encoded, such as the
space character. You can also plug in a URL there and have it converted to a browser
safe version.
[/network/web/browser]
permanent link
Sun, Feb 17, 2008 5:41 pm
IP and Domain Name Reputation Sites
An
IP address may be added to a
DNS Blacklist (DNSBL), if spam
is detected as emanating from that IP address. You can check for the presence
of an IP address on various blacklists using the
MxToolBox Email Blacklist
Check, which currently checks 124 blacklists, or at individual
blacklist sites, such as
MAPS.
You can check on whether an IP address has been associated with attacks
on other systems at DShield
or myNetWatchman by
performing an IP lookup.
You can also obtain information on the "reputation" for a site
at Barracuda
Central by performing a lookup on either an IP address or a domain name.
Barracuda Networks sells widely used spam firewall devices, so a poor
reputation listing at Barracuda Central may lead to email from an IP address
listed there, or with a domain name in the body of email messages being found
there, being blocked by those using Barracuda Networks security devices.
Another reputation site is
TrustedSource. You can lookup an IP address there and see a graph
of activity associated with that site. If you see red bars on the
graph, those represent malicious activity associated with the IP address
on the days for which those bars appear.
[/network/Internet/domains]
permanent link
Sun, Feb 17, 2008 4:46 pm
Locating Cybersquatters Capitalizing on a Variant of Your Domain
Cybersquatters
may buy domains similar to yours hoping to take advantage
of someone mistyping your domain name or to mislead someone into thinking
a domain name in a URL belongs to a legitimate company or organization.
For instance many people might visit microsoft.com, so a cybersquatter might
buy micrsoft.com, which has a missing "o", so that someone making a typo that
left out that "o" would be directed to the cybersquatter's site instead, where
the cybersquatter may have nothing but ads, hoping to get money generated
from those viewing those ads. If millions of people visit microsoft.com every
week, the cybersquatter will probably get a signifiant amount of traffic
from such a typo.
Or perhaps you own example.com. The cybersquatter may purchase example.net,
if it is available. Someone seeing example.net in an email may think the
domain belongs to your company and visit a site that might have nothing but ads,
perhaps even risque ones, or the site might try to infect visitors with
adware/spyware, which might harm your company's reputation, even though you
don't own the domain name and have no control over the site.
CitizenHawk helps you locate
potential cybersquatter sites for your domain name.
[/network/Internet/domains]
permanent link
Sun, Feb 17, 2008 12:54 pm
Configure Sendmail to Listen on All Addresses
If you can't connect to the
SMTP port on a system, i.e.
port 25, from external hosts, but you can connect from the system itself,
then you need to comment out a line in
sendmail.mc that
restricts connections to the local loopback address, 127.0.0.1.
I.e., if you can use telnet 127.0.0.1 25 and see the sendmail
banner, but when you use telnet 192.168.0.44 25 (presuming
192.168.0.44 is the IP address for the mail server), you get "connection
refused" messages, then the default configuration option in
sendmail.mc is likely preventing the connection by causing
sendmail to only listen on the loopback address.
# telnet 192.168.0.44 25
Trying 192.168.0.44...
telnet: connect to address 192.168.0.44: Connection refused
telnet: Unable to connect to remote host: Connection refused
To resolve the problem, look for the following lines in sendmail.mc
, which on a Linux system will likely be in the /etc/mail
directory.
dnl #
dnl # The following causes sendmail to only listen on the IPv4 loopback address
dnl # 127.0.0.1 and not on any other network devices. Remove the loopback
dnl # address restriction to accept email from the internet or intranet.
dnl #
DAEMON_OPTIONS(`Port=smtp,Addr=127.0.0.1, Name=MTA')dnl
Edit the sendmail.mc file from the root account. Put a
dnl # at the beginning of the DAEMON_OPTIONS
line to comment out the line.
dnl # DAEMON_OPTIONS(`Port=smtp,Addr=127.0.0.1, Name=MTA')dnl
Then issue the following commands:
m4 /etc/mail/sendmail.mc > /etc/mail/sendmail.cf
/etc/init.d/sendmail restart
The first command rebuilds the .cf configuration file from the modified
.mc file. The second restarts sendmail so that it is using the new
configuration file.
[/network/email/sendmail]
permanent link
Fri, Feb 15, 2008 7:02 pm
216-115-223-200.expertcity.com HTTPS Access
While monitoring a
LAN
with
Show Traffic, a
network monitoring application for Windows systems, I noticed two
systems contacting 216.115.223.200 [ 216-115-223-200.expertcity.com ]
on port 443 (HTTPS).
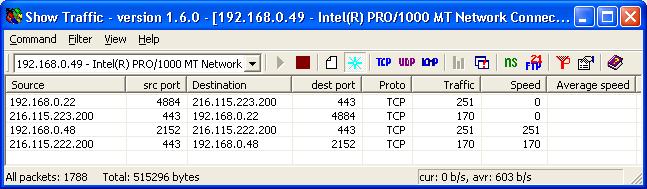
Since the communications occurred at 18:30 when the
employees using those systems would have gone home, I did a
Google search on the
FQDN,
216-115-223-200.expertcity.com, which was associated with that address.
A
McAfee SiteAdvisor webpage linked the site with
GoToMeeting, i.e.
legitimate software on the users' systems. That webpage stated "When we
installed and ran GoToMeeting 2.0.0.127 (gotomeeting.exe), the following
network servers were contacted." It then listed the following addresses:
216-115-222-200.expertcity.com
216-115-223-200.expertcity.com
[/os/windows/network/monitoring/show_traffic]
permanent link
Fri, Feb 15, 2008 5:08 pm
Wed, Feb 13, 2008 10:53 pm
Configuring SNMP on a Netopia R7220-T Router
To configure
SNMP
on a Netopia R7220-T router, take the following steps:
- From the main menu, select System Configuration.
Netopia R7220-T v4.6.2
Easy Setup...
WAN Configuration...
System Configuration...
Utilities & Diagnostics...
Statistics & Logs...
Quick Menus...
Quick View...
Return/Enter displays options for the system.
You always start from this main screen.From the System Configuration menu, select SNMP
(Simple Network Management Protocol)....
System Configuration
Network Protocols Setup...
Filter Sets...
IP Address Serving...
Date and Time...
Console Configuration...
SNMP (Simple Network Management Protocol)...
Security...
Upgrade Feature Set...
Logging...
Return/Enter to set up basic SNMP options (Community Strings, Traps, etc.).From the SNMP Setup window, specify the desired SNMMP configuration.
SNMP Setup
System Name:
System Location:
System Contact:
Read-Only Community String: public
Read/Write Community String:
Authentication Traps Enable: Off
IP Trap Receivers...
Configure optional SNMP parameters from here.
You can put in whatever name you would like to use for the router in the
System Name field, e.g. Netopia Router and then hit
Enter to advance to the next field, where you can specify the location,
e.g. 1020 Maple Street. Hit Enter to fill in the
System Contact field. The default read-only community string is
public. To prevent others from accessing information from the
router, you can provide another community string. You can provide a
read/write community string as well, if you like. If you want authentication
traps sent to another device, enable authentication traps and specify IP
trap receivers. Otherwise, you can leave these as is.
You can return to the main menu, if you wish, by hitting the
Escape key until to back up through the menus.
If you want a free program to monitor the router via SNMP from a Windows
system, try PRTG Traffic Grapher.
It is fairly straight-forward to set up and can even install its own
webserver on the system on which you install it. If you already have webserver
software running on the system on which you install it using port 80, PRTG
will automatically set up its own webserver at port 8080. Or you can choose
a different port, if you prefer. You can specify userids and passwords granted
access to the webserver, where the PRTG graphs are displayed.
[/hardware/network/router/netopia]
permanent link
Wed, Feb 13, 2008 9:25 pm
FTP Attacks from 221.130.187.49 and 202.57.128.159
The system became unresponsive for a time. I ran
kripp and found two systems conducting FTP brute-force
password guessing attempts.
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: poiuyt [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: purple [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: ranger [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: 111111 [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: purple [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: ranger [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: 111111 [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: 123go [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: 000000 [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: Airhead [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: oracle [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: Braves [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: library [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: Sparky [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: linux [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: angela [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: unix [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: brandy [F]
ftp password :: frostdragon.com -> 202.57.128.159.sta.isp-thailand.com :: anna :: amanda [F]
ftp password :: frostdragon.com -> 221.130.187.49 :: james :: cindy [F]
I blocked the 221.130.187.49 system with route add 221.130.187.49 reject
. I then checked DShield to
learn if it has been observed attacking other systems. The
DShield report
for 221.130.187.49 showed it was first reported engaged in hostile
activity on 2008-02-11 and the last reported incident was today
2008-02-13. The IP address is a Chinese address. When I checked the
IP Details
for the ports the system was attacking, I found it was listed only
for port 21 attacks, i.e. FTP
attacks.
It was also listed at myNetWatchman.
The Incident
Detail report for that IP address at myNetWatchman showed the system
had been attacking other systems on port 21 and port 22 (SSH) as well from
February 5, 2008 onwards.
I then checked the second system attacking, which was
202.57.128.159.sta.isp-thailand.com. The IP address for it is 202.57.128.159.
Note: a reverse lookup on 202.57.128.159 yields a Fully Qualified Domain Name
(FQDN) of 202.57.128.159.sta.isp-thailand.com, but a forward lookup on
202.57.128.159.sta.isp-thailand.com does not yield an IP address.
I ran an nmap scan of it to see what operating system it was running. I got
the following results:
# nmap -P0 -O 202.57.128.159
Starting nmap V. 3.00 ( www.insecure.org/nmap/ )
Insufficient responses for TCP sequencing (1), OS detection may be less accurate
Interesting ports on 202.57.128.159.sta.isp-thailand.com (202.57.128.159):
(The 1588 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
80/tcp open http
111/tcp open sunrpc
135/tcp filtered loc-srv
137/tcp filtered netbios-ns
199/tcp open smux
443/tcp open https
445/tcp filtered microsoft-ds
3306/tcp open mysql
4444/tcp filtered krb524
8009/tcp open ajp13
8080/tcp open http-proxy
10000/tcp open snet-sensor-mgmt
Remote operating system guess: Linux Kernel 2.4.0 - 2.5.20
Nmap run completed -- 1 IP address (1 host up) scanned in 173 seconds
Visting http://202.57.128.159/ with
a browser showed "Welcome to web4.thaibestserver.net".
When I checked DShield for any reports
on hostile activity for that IP address, which is a Thai address,
I found it was first reported
engaged in hostile activity on 2008-02-08 with the most recent report
dated 2008-02-09 (see
IP Info
(202.57.128.159)). The
IP Details
202.57.128.159 report showed all of the incidents to be FTP attacks.
There was also an
Incident Detail report for it at
myNetWatchman, which also showed the system engaged in FTP attacks from
February 6 onwards.
I blocked it with route add 202.57.128.159 reject.
I also turned off the FTP service on the system, since it isn't needed
at the moment.
[/security/attacks]
permanent link
Wed, Feb 13, 2008 3:41 pm
PrimoPDF Producing Zero Byte Files
I installed
PrimoPDF 3.0 on a system.
PrimoPDF provides free PDF converter software that will allow you to
"print" documents to a PDF file. After installing the software,
I could print to PDF files without a problem from the administrator account
from which I installed the software, but when I printed to a PDF file using
the PrimoPDF "printer", I would receive the error message below:
| Adobe Reader |
Adobe Reader could not open 'http.pdf' because it
is either not a supported file
type or because the file has been damaged (for example, it was sent as an
email attachment and wan't correctly decoded).
OK
|
When I checked the PDF files produced by PrimoPDF, I found they were always
zero bytes in size. When the files were being produced I would hear an
error beep.
An
Error after converting posting at the
PrimoPDF Forums, suggested giving the
Users group on the system full control of the directory into which PrimoPDF
is installed.
From the Windows Explorer, I right-clicked on the directory under
Program Files into which I had installed PrimoPDF and chose
Properties. I saw that the Users group had only read access, i.e. only
the read & execute, list folder contents, and read permissions were granted
to the Users group for that folder.
Note: you can use the cacls command to check permission from
the command line, e.g. cacls "\program files\primopdf", if
the installation directory was \program files\primopdf. You
will see BUILTIN\Users:(OI)(CI)R. The R at the
end indicates that the Users group on the system, to which all normal user
accounts belong, has only read access to that directory.
If you are logged into an account that is a member of the Administrators
group on the system, you can right-click on the directory and choose
Properties to reset the security permissions. Click on the
Security tab, then select the Users group under "group or user
names", then grant Full Control.
Since I was logged into a normal user account at the time I encountered
the problem and had a lot of windows open and didn't want to have to close
all of them, logoff, logon as an administrator, logoff, logon to my user
account again, and then reopen all of the applications and files I previously
had open, I used the cacls command to reset the permissions.
To use that method, you need to take the following steps, if you are currently
logged into an unprivileged user account.
- Open a command prompt window as the Administrator. On Windows XP systems,
you can do so by going to
C:\WINDOWS\system32\ and right-clicking
on cmd.exe while holding down the shift key (if you don't hold
down the shift key at the same time, you won't see the "run as" option). Then
select Run as. Click on The following user and put in
Administrator, or some other account with administrator access, for
the user name, and enter the appropriate password. Then hit Enter
or click on OK. A command prompt window will open with Administrator
credentials.
- Enter the command
cacls "\program files\primopdf" /E /G Users:F
to give all users of the system full control of the directory where you
installed PrimoPDF, presuming that you installed it in \program
files\primopdf. Granting full control of the directory means
they can add or delete files in that directory. The Users group will still
only have "read" access to the dll and exe files in the directory, though.
The /E means "edit the existing Access Control List (ACL)
rather than creating a new one and the /G grants access
for the account or accounts specified as a parameter. The F
at the end grants "full" access. You can enter cacls /?
for help with the cacls command. You will see something
like "processed dir: C:\program files\PrimoPDF", if the
command is successfully executed.
[/os/windows/software/pdf]
permanent link
Tue, Feb 12, 2008 9:43 pm
Smart Network Data Services for Tracking Email to Hotmail.com Addresses
Microsoft offers
Smart Network Data Services, which allows someone to view data
on email transmitted from IP addresses for which he or she is resonsible
to hotmail.com email addresses. Microsoft describes the service as
follows:
Smart Network Data Services (SNDS) is a revolutionary Windows Live Mail
initiative designed to allow everyone who owns IP space to contribute to the
fight against spam, malware, viruses, and other internet evils, and to protect
e-mail and the internet as a valued communications, productivity and commerce
tool. Windows Live Mail and MSN Hotmail, with over 250 million active user
accounts world-wide, is in a unique position to collect and analyze e-mail
activity data. By providing that data to service providers, most of whom
wouldn.t otherwise have access to any such data, they are empowered to use
their relationship with their customers to react and take repair actions, such
as preventing spam from originating within their IP space. The overarching
goal of SNDS is to make the Internet a better, safer place. Working together,
Windows Live Mail and service providers can make their respective customers
happier and more satisfied with the various services we all provide.
To request a Smart Network Data Services account, go to
SNDS - Request
Access. Enter the IP address or address range for which you are
responsible and for which you wish to track email being sent to Hotmail.com
addresses.
When you click on Submit you will see the message "We've determined
that the following email addresses are associated with the specified network
in an appropriately authoritative way. Please choose one that you can receive
mail at and we will send instructions for completing the signup process to that
address." You may then see 4 addresses similar to those below:
abuse@yourdomain.com
noc@isp1.net
noc@isp2.net
postmaster@yourdomain.com
Two of the addresses will be of the form abuse@yourdomain.com and
postmaser@yourdomain.com, assuming that a reverse DNS lookup on
a provided IP address yields "yourdomain.com".
A "whois" lookup will also be done on a provided IP address using the
relevant registrar, which, if you are in the U.S. will likely be
the American Registry for Internet Numbers
(ARIN). The "OrgTechEmail" address listed for the IP address may
be used as one of the possible addresses, e.g. noc@isp1.net, if that
was the "OrgTechEmail" listed for the
ISP.
You can see further information on how the email addresses are derived
at
SNDS - FAQ.
If you have PTR record in DNS that points back to yourdomain.com,
and wish to use one of those email addresses, make sure that you have valid
abuse@yourdomain.com and postmaster@yourdomain.com email addresses.
What data does SNDS provide?
The data provided by SNDS is meant to provide as broad a picture of an IP's
mail sending behavior as necessary for the system's consumers to be
able to stop spam. It reports on a variety of characteristics of mail
traffic. The data points provided are designed to be difficult
or impossible for spammers to avoid differentiating themselves from
well-behaved mailers. Similarly however, data isn't provided on IPs that
send very little mail because they (currently) account for a negligible amount
of spam. For each IP within the ranges that the user has been authorized,
the following data is provided:
Virus-infected emails
Malware
hosting
Open proxy
status
An email message is sent to the address you specified. You will need to go
to a link provided in that email message to grant access to the data to a
Windows Live ID account, such as a hotmail.com email address,
you specified when you requested an account.
Once you have confirmed access, you can view data at
SNDS - View Data
There you will see a calendar where you can select dates for which to view
data. You have the option to change your settings to allow access your data as
a .CSV file without the need for browser-based authentication technologies such
as Windows Live™ ID. This
facilitates access to your data via your own automated scripts or programs.
I didn't see any data listed for an IP address I specified. I know email is
sent from that address to hotmail.com users, but the volume of traffic is
fairly low. The
SNDS - FAQ
states that "data isn't provided on IPs that send very little mail because
they (currently) account for a negligible amount of spam."
[/network/email/spam]
permanent link
Tue, Feb 12, 2008 8:42 pm
Viewing Exchange Logs in Excel
The email log files for a Microsoft Exchange server can be analyzed with
Microsoft Excel. Exchange stores the log entries in a text file, which can
be imported in Excel for analysis.
[
More Info ]
[/network/email/exchange]
permanent link
Tue, Feb 12, 2008 12:30 pm
IP on LASHBACK DNS Blocklist
An IP address for a site had gotten on some blocklists, apparently
due to an infected system at the site.
I went to the
MxToolBox Email Blacklist Check page, which currently checks for the
presence of an IP address on 124 blacklists. I checked on whether the IP
address was present on any of the lists queried by the MxToolBox blacklist
check tool. It was on the
LASHBACK blacklist, with the
reason listed as "Sender has sent to LashBack Unsubscribe Probe accounts
Return codes were: 127.0.0.2", but no others.
I requested a delisting from their
Unsubscribe Blacklist
Support page. When I looked up the address at LASHBACK, I found it was
listed. When I requested it be delisted at 12:30 PM, I was notified that it
would be removed within 1 hour. When I had checked for the address on
the
MxToolBox Email Blacklist Check page, I had seen a
TTL
value of 3594, which is 59.9 minutes, listed for it for the LASHBACK list.
[/network/email/blacklist]
permanent link
Mon, Feb 11, 2008 9:03 pm
System Not Recognizing EasyShare printer dock plus
A user told me that she was no longer able to communicate
with her Kodak EasyShare C340 camera, which she plugs into
a Kodak EasyShare printer dock plus.
The following steps can be taken to see if the system is
recognizing the presence of the printer dock.
- Click on Start.
- Select All Programs.
- Select Kodak.
- Select Kodak EasyShare printer dock.
- Select Kodak printer dock firmware updater.
When the application opens, you should see the printer
name listed along with the current firmware version number
as shown below.
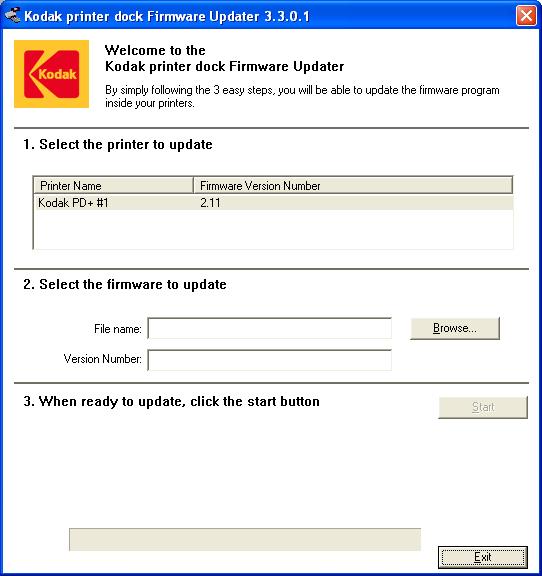
In this case nothing was listed under "Printer Name" nor under
"Firmware Version Number". I unplugged the
USB cable
from the computer and plugged it back in. I then saw the
message below:
USB Device Not Recognized
One of the USB devices attached to this computer has
malfunctioned, and Windows does not recognize it.
For assistance in solving this problem, click this message.
I tried plugging the device into two other USB ports
with the same results. I unplugged the cable from the
printer dock and powered it off. I plugged the cable
back in and powered it on. I then heard noises from
the unit and when I exited the Kodak printer dock firmware
updater program and restarted it, I saw entries listed
under "Printer Name" and "Firmware Version Number"
[/hardware/camera]
permanent link
Sun, Feb 10, 2008 9:45 pm
Use Custom Filter with Netopia R7220-T Router
A Netopia R7220-T router has built-in firewall capabilities.
It comes with two filter sets preconfigured, "Basic Firewall"
and "NetBIOS", but you can create your own custom filters.
To use a custom filter you have created, take the following steps.
- From the main menu, select Quick Menus and hit Enter.
Netopia R7220-T v4.6.2
Easy Setup...
WAN Configuration...
System Configuration...
Utilities & Diagnostics...
Statistics & Logs...
Quick Menus...
Quick View...
Return/Enter displays options for the system.
You always start from this main screen.
- From the Quick Menu, select Change Connection Profiles
and hit Enter.
Quick Menu
Connection Profiles Line Configuration IP Setup
Add Connection Profiles IP Address Serving Setup
Change Connection Profiles IP Filter Sets
Delete Connection Profiles Backup Config Static Routes
WAN Default Profile Network Address Translation
IPX Setup
IPX Filters & Filter Sets
Console Configuration TFTP
SNMP Setup
This menu allows you to visit most configuration screens.
- When your connection profile, e.g. Easy Setup Profile, appears
hit enter to accept it for editing.
Quick Menu
+-Profile Name---------------------IP Address----IPX Network-+
Connecti+------------------------------------------------------------+
Add Conn| Easy Setup Profile 192.168.6.25 | Setup
Change C| |
Delete C| |
WAN Defa| |anslation
| |
| |
| |er Sets
| |
| |
| |
| |
Console | |
SNMP Set| |
| |
| |
| |
+------------------------------------------------------------+
Up/Down Arrow Keys to select, ESC to dismiss, Return/Enter to Edit.
- Select IP Profile Parameters... and hit Enter.
Change Connection Profile
Profile Name: Easy Setup Profile
Profile Enabled: Yes
Data Link Encapsulation... RFC1483
IP Enabled: Yes
IP Profile Parameters...
IPX Enabled: No
Interface Group... Primary
Return accepts * ESC cancels * Left/Right moves insertion point * Del deletes.
Modify Connection Profile here. Changes are immediate.
- Select Filter Set... and hit Enter.
IP Profile Parameters
Address Translation Enabled: Yes
IP Addressing... Numbered
NAT Map List... Easy-PAT List
NAT Server List... Easy-Servers
Local WAN IP Address: 192.168.6.25
Local WAN IP Mask: 255.255.254.0
Filter Set... NetBIOS Filter
Remove Filter Set
Receive RIP: Both
Return/Enter to select Filter Set (Firewall) for this profile.
Configure IP requirements for a remote network connection here.
- Select the custom filter set you created, e.g. "Custom", if that was the
name you used, and hit Enter.
IP Profile Parameters
+-----------------------------------+
Address Translati+-----------------------------------+
IP Addressing... | Basic Firewall |
| NetBIOS Filter |
NAT Map List... | Custom |
NAT Server List..| |
| |
Local WAN IP Addr| |
Local WAN IP Mask| |
| |
+-----------------------------------+
Filter Set... NetBIOS Filter
Remove Filter Set
Receive RIP: Both
Up/Down Arrows to select, then Return/Enter; ESC to cancel.
- Hit Esc to go back to the prior IP Profile Parameters
menu. You should now see whatever name you used for your custom filter listed
on the same line as Filter Set....
IP Profile Parameters
Address Translation Enabled: Yes
IP Addressing... Numbered
NAT Map List... Easy-PAT List
NAT Server List... Easy-Servers
Local WAN IP Address: 66.159.76.25
Local WAN IP Mask: 255.255.254.0
Filter Set... Custom
Remove Filter Set
Receive RIP: Both
Toggle to Yes if this is a single IP address ISP account.
Configure IP requirements for a remote network connection here.
- You can then keep hitting Esc until you get back to the main
menu or just disconnect from the router
[/hardware/network/router/netopia]
permanent link
Sun, Feb 10, 2008 4:39 pm
Colasoft MAC Scanner 1.1
If you need to determine the
Media Access
Control (MAC) addresses on a
LAN using a Windows system,
Colasoft provides a tool,
MAC Scanner,
which you can use to scan all IP addresses in a subnet to obtain a list
of the MAC, aka hardware addresses, associated with those IP addresses.
The
results
can be exported to a text or Comma Separated Value (CSV) file.
[/os/windows/software/network/scanner]
permanent link
Sun, Feb 10, 2008 2:02 pm
Dell PowerConnect 3024 - Finding MAC Addresses
To determine the
Media Access Control (MAC) addresses of devices connected to a Dell
PowerConnect 3024 switch, take the following steps:
- Select Address Manager from the main menu.
PowerConnect 3024
Main Menu
a. System Manager
b. Port Manager
c. Address Manager
d. Spanning Tree
e. VLAN and CoS Setup
f. Port Trunking
g. Port Mirroring
h. SNMP Management
i. Multimedia Support
j. Statistics
k. Save Configuration
Hit to configure Static Address Table or Address Aging Time
<Ctrl-L> Refresh <Ctrl-W> Save
- Select Dynamic Addresses from the Address Manager menu.
PowerConnect 3024
Address Manager
a. Static Addresses
b. Dynamic Addresses
c. Address Aging
d. Static Multicast Groups Administration
e. Static Multicast Groups Membership
Hit <Enter> to view Dynamic Addresses
<ESC> Back <Ctrl-L> Refresh <Ctrl-W> Save
You will then see the MAC addresses that have been seen by the switch for each
port. Ports with no device attached will not be listed. If nothing is listed
for a port at the time you check, though, that does not necessarily mean that
no device is attached to that port, only that no activity has been seen on
that port recently. A system could be attached to the port, but turned off, or
may be on, but has not communicated with another device over the network
recently.
If the switch is seeing multiple MAC addresses on a port, as it would
if there is another switch or hub plugged into the port, which itself
has multiple systems plugged into it, it will show all of the MAC addresses. In
the example below, 5 addreses are listed for port 6 and 4 addresses
are listed for port 16. There is another switch connected to port 6
and a hub connected to port 16.
PowerConnect 3024
Address Manager/Dynamic Addresses
Dynamic Address Learning is: Enabled
Port: VLAN ID: MAC Address: Query Next Prev
Port VLAN MAC Address Port VLAN MAC Address
--------------------------------------------------------------------------------
1:3 1 00:0c:f1:c8:99:09 1:16 1 00:09:6b:19:38:a5
1:4 1 00:13:20:97:de:e4 1:20 1 00:16:01:41:72:3b
1:5 1 00:1d:09:0a:5d:55
1:6 1 00:11:11:64:ec:bc
1:6 1 00:13:20:97:e2:cf
1:6 1 00:13:72:3b:4a:b6
1:6 1 00:16:76:96:cb:1e
1:6 1 00:17:a4:26:88:d5
1:7 1 00:11:11:5e:b5:90
1:8 1 00:11:11:a8:9c:b0
1:15 1 00:30:18:aa:70:a5
1:16 1 00:00:74:ad:e8:c6
1:16 1 00:00:c5:7c:08:7c
1:16 1 00:06:25:b5:b4:62
Hit <Space> to Enable or Disable Dynamic Address Learning
<ESC> Back <Ctrl-L> Refresh <Ctrl-W> Save
If you see a MAC address which you don't recognize, you can lookup up the
manufacturer of the network adapter associated with that address at
Vendor/Ethernet MAC Address
Lookup and Search, which may help you identify what type of device
is connected on the port showing that MAC address. For instance, when I look
up 00:09:6b:19:38:a5, I see the vendor listed as
"IBM Corporation". When I look up 00:17:a4:26:88:d5, I see
"Global Data Services (may now be Hewlett-Packard, HP)" listed and, in
this case, the device is an HP K5400 printer.
References:
-
Vendor/Ethernet MAC Address Lookup and Search
Coffer.com
[/hardware/network/switch/dell]
permanent link
Sat, Feb 09, 2008 8:22 pm
Setting IP Information From the Command Line
On a Windows system, you can use the
netsh interface ip set
command to configure IP parameters for the system from the command line.
E.g. the command netsh interface ip set address name="Local Area
Connection" static 192.168.0.66 255.255.255.0 192.168.0.1 1 could
be used to set the IP address to a static value of 192.168.0.66
with a subnet mask of 255.255.255.0 and a default gateway of
192.168.0.1.
[ More Info ]
[/os/windows/commands]
permanent link
Fri, Feb 08, 2008 10:16 pm
Uploading Blocked Files to a SharePoint Server
On a Windows Small Business Server (SBS) 2003 system, I tried uploading an
exe file to the SharePoint
server, but saw the following displayed when I attempted to upload it.
Form Validation Error
Please correct the information you provided by following these steps, then
submit the information again:
- The following file(s) have been blocked by the administrator:
Downloads/Security/clamwin-0.92-setup.exe
The following steps can be taken to allow the upload of an .exe file.
Similar steps can be followed to allow the upload of other blocked
files.
- Click on Start.
- Select All Programs.
- Select Administrative Tools.
- Select SharePoint Central Administration.
- Under Security Configuration, click on Manage blocked
file types.
- Delete
exe from the list and click on OK.
[/os/windows/sharepoint]
permanent link
Thu, Feb 07, 2008 8:01 pm
Determining Version of Microsoft Exchange
To determine what version of Microsoft Exchange is running on
a system, you can take the following steps:
- Click on Start.
- Select All Programs.
- Select Microsoft Exchange.
- Select System Manager. Note: the System Manager
is applicable if you have Exchange Server 2000 and later. For
Exchange Server 5.5 and earlier, you will need to run
Exchange Administrator.
- Click Servers. You will then see the version
displayed. For Exchange Server 2000, the version is 6.0;
for Exchange Server 2003, the version is 6.5.
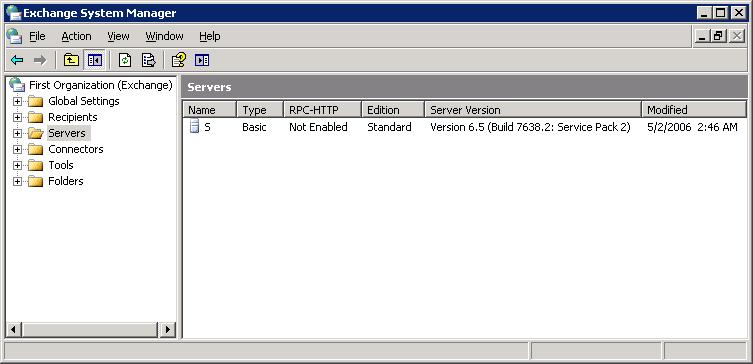
You can also determine the version number, by going to
C:\Program Files\Exchsrver\bin, right-clicking on
store.exe, selecting Properties, and
clicking on the Version tab.
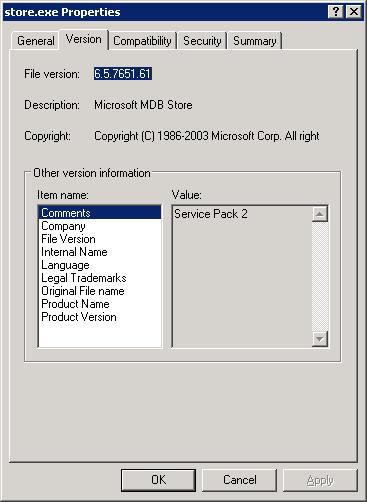
Clicking on Product version will show the version
of the Exchange software. In the case shown above, the
file version is listed as 6.5.7651.61 while the product version
is 6.5. The digits after the 6.5 in the file version don't
necessarily match the build version displayed using the first
method.
Note: the version number you see using the above methods
may not necessarily be the same version number you would
see displayed if you telnet to port 25 on the Exchange server. E.g.
the above method of determining the version of Exchange running
on a system shows it to be 6.5 (Build 7638.2: Service Pack 2), but
if I telnet to port 25 on that same Exchange server, I see the
following:
220 example.com Microsoft ESMTP MAIL Service, Version: 6.0.3790.3959 ready at
Wed, 13 Feb 2008 19:07:30 -0500
I.e. the "ESMTP MAIL Service" version is not the same as the version number
for the Exchange server software on the system, so you can't infer that
the version number you see displayed when you connect to port 25 on the
system is the Exchange server version number.
References:
-
How to tell which software version your computer is using
Published: June 18, 2004
Microsoft Corporation
[/network/email/exchange]
permanent link
Wed, Feb 06, 2008 9:38 pm
HPProduct Assistant Installation Failure
While checking a user's Windows XP system, I found that every time
I logged into it a window opened for the installation of
HPProductAssistant.
| HPProductAssistant |
Please wait while Windows configures HPProductAssistant
Cancel
|
Then another HPProductAssistant window would appear stating "The feature
you are trying to use is on a CD-ROM or other removalable disk that is not
available" and asking me to "Insert the 'HPProductAssistant' disk and click OK"
with "1" appearing in the "use source" field. When I clicked on the browse
button, I saw it was looking for hpproductassistant.msi.
If I clicked on the Cancel button, I would see the error message below:
| HPProductAssistant |
Error 1706.No valid source could be found for product
HPProductAssistant. The Windows Installer cannot
continue.
OK
|
If I clicked on OK, which was the only option, the process would
just repeat. Clicking on the Cancel button at the point where it
prompted for the HPProductAssistant installation file, just kept the process
repeating as well. I had to kill the application through the Task Manager to
stop it.
When I checked on what process was associated with the HPProductAssistant in the
Task Manager by right-clicking on HPProductAssistant under the Applications
tab in the Task Manager and selecting Go To Process , I found it was
hpqtra08.exe That file is associated with
"HP Digital Imaging Monitor" software and is located in
C:\Program Files\HP\Digital Imaging\bin\hpqtra08.exe
When I went to Start, All Programs, and Startup, I
found "HP Digital Imaging Monitor" listed there. It was probably put there
during the installation of software for the user's printer. HP will install
a lot of other software in addition to a printer driver when you use the
HP-provided installation disc for one of their printers. Since it wasn't working
and I doubted the user had any need for it, I clicked on Start,
All Programs and Startup then right-clicked on "HP Digital
Imaging Monitor and selected Delete to get rid of the entry
from the startup group. I rebooted the system to verify that the problem would
no longer occur; it did not.
References:
-
Wait while Windows configures HPProductAssistant???
Yahoo! Answers
-
How to remove hpqtra08 error
file.net
[/os/windows/processes]
permanent link
Sun, Feb 03, 2008 7:36 pm
Determing the Package to Which a File Belongs
If you wish to determine what package a file belongs to under Solaris,
you can use the command
pkgchk -l -p /path/file. E.g.
to determine the package to which the
openssl program located
in
/usr/sfw/bin belongs, the following command could be used:
# pkgchk -l -p /usr/sfw/bin/openssl
Pathname: /usr/sfw/bin/openssl
Type: regular file
Expected mode: 0555
Expected owner: root
Expected group: bin
Expected file size (bytes): 318668
Expected sum(1) of contents: 16493
Expected last modification: Jan 26 21:01:01 2006
Referenced by the following packages:
SUNWopenssl-commands
Current status: installed
From the above information, I can see the file belongs to the package
SUNWopenssl-commands. I can get further information on that
package, such as the date the package was installed with the command
pkginfo -l SUNWopenssl-commands.
# pkginfo -l SUNWopenssl-commands
PKGINST: SUNWopenssl-commands
NAME: OpenSSL Commands (Usr)
CATEGORY: system
ARCH: i386
VERSION: 11.10.0,REV=2005.01.21.16.34
BASEDIR: /
VENDOR: Sun Microsystems, Inc.
DESC: OpenSSL Commands (Use)
PSTAMP: on10-patch-x20060126144406
INSTDATE: Jul 08 2006 23:31
HOTLINE: Please contact your local service provider
STATUS: completely installed
FILES: 5 installed pathnames
3 shared pathnames
3 directories
2 executables
634 blocks used (approx)
References:
-
Solaris find out a package which a file belongs to
nixCraft - Insight Into Linux Admin
Work
[/os/unix/solaris/commands]
permanent link
Sun, Feb 03, 2008 11:08 am
Internet Explorer Shortcut Keys
I use
Furl to save copies of webpages
I've found interesting. Furl creates an online bookmarks or "favorites"
list for you. If you make your Furl archive public, others can also
have access to your links. You also get an online archived copy of the webpage
you've "furled". So if the webpage disappears or the website where it resided
is inaccessible for some other reason the next time you want to view it,
you have a stored copy at Furl.
But sometimes I run into difficulty with multi-page news articles. I don't
want to have to furl each page individually. Some websites offer a "print"
function, so that you can display a copy of all pages of the article at
once to send them to the printer at once. But often, when the window opens
that displays the entire article for printing, I don't see the Internet
Explorer (IE) menubar with "File, Edit, View, Favorites, Tooks, and Help" on it.
The link to furl pages is under "Favorites", so I don't then have access
to that link.
One alternative is to right-click on the "print" version of the webpage,
choose "Properties" and then copy the URL for the webpage, which you can
paste into another IE window with the menubard displayed to access the page.
Another method is to hit the Ctrl and "I" keys simultaneously, which will
bring up the IE Favorites box.
Other IE shortcut keys to view and explore web pages are listed below:
To do this Press this key
----------------------------------------------------------------------
Display Internet Explorer Help or to F1
display context Help about an item in
a dialog box
Toggle between full-screen and other F11
views in the browser
Move forward through the items on a TAB
Web page, the Address box, or the
Links box
Move through the items on a Web page, SHIFT+TAB
the Address box, or the Links box
Go to your Home page ALT+HOME
Go to the next page ALT+RIGHT ARROW
Go to the previous page ALT+LEFT ARROW or BACKSPACE
Display a shortcut menu for a link SHIFT+F10
Move forward between frames CTRL+TAB or F6
Move back between frames SHIFT+CTRL+TAB
Scroll toward the beginning of a UP ARROW
document
Scroll toward the end of a document DOWN ARROW
Scroll toward the beginning of a PAGE UP
document in larger increments
Scroll toward the end of a document PAGE DOWN
in larger increments
Move to the beginning of a document HOME
Move to the end of a document END
Find on this page CTRL+F
Refresh the current Web page F5 or CTRL+R
Refresh the current Web page, even if CTRL+F5
the time stamp for the Web version and
your locally stored version are the same
Stop downloading a page ESC
Go to a new location CTRL+O or CTRL+L
Open a new window CTRL+N
Close the current window CTRL+W
Save the current page CTRL+S
Print the current page or active frame CTRL+P
Activate a selected link ENTER
Open the Search box CTRL+E
Open the Favorites box CTRL+I
Open the History box CTRL+H
In the History or Favorites boxes, CTRL+click
open multiple folders
References:
-
Internet Explorer Keyboard Shortcuts
Article ID : 306832
Last Review : May 7, 2007
Revision : 2.3
Microsoft Help and Support
[/network/web/browser/ie]
permanent link
Fri, Feb 01, 2008 9:41 pm
Removing a Package
Removing a package that has been installed on a Solaris system is handled
by the
pkgrm command, which must be run from the root account.
E.g.
pkgrm SMCx11vnc would remove the previously installed
x11vnc package from a system. The output produced from
running the command appears below.
# pkgrm SMCx11vnc
The following package is currently installed:
SMCx11vnc x11vnc
(sparc) 0.7
Do you want to remove this package? [y,n,?,q] y
## Removing installed package instance <SMCx11vnc>
## Verifying package <SMCx11vnc> dependencies in global zone
## Processing package information.
## Removing pathnames in class <none>
/usr/local/share/x11vnc/classes/index.vnc
/usr/local/share/x11vnc/classes/VncViewer.jar
/usr/local/share/x11vnc/classes
/usr/local/share/x11vnc
/usr/local/share <shared pathname not removed>
/usr/local/man/man1/x11vnc.1
/usr/local/man/man1
/usr/local/man
/usr/local/doc/x11vnc/TODO
/usr/local/doc/x11vnc/README
/usr/local/doc/x11vnc/NEWS
/usr/local/doc/x11vnc/INSTALL
/usr/local/doc/x11vnc/ChangeLog
/usr/local/doc/x11vnc/COPYING
/usr/local/doc/x11vnc/AUTHORS
/usr/local/doc/x11vnc
/usr/local/doc <shared pathname not removed>
/usr/local/bin/x11vnc
/usr/local/bin <shared pathname not removed>
## Updating system information.
Removal of <SMCx11vnc> was successful.
References:
-
Remove a Solaris package with pkgrm
November 28, 2005
tech-recipes - Your cookbook of
tech-tutorials
[/os/unix/solaris/commands]
permanent link
Fri, Feb 01, 2008 8:40 pm
Pkginfo Command
On Solaris systems, the
pkginfo command can be used to obtain
information on installed packages. It is somewhat aking to the
rpm and similar commands on Linux systems.
usage:
pkginfo [-q] [-pi] [-x|l] [options] [pkg ...]
pkginfo -d device [-q] [-x|l] [options] [pkg ...]
where
-q #quiet mode
-p #select partially installed packages
-i #select completely installed packages
-x #extracted listing
-l #long listing
-r #relocation base
and options may include:
-c category, [category...]
-a architecture
-v version
If you just issue the command pkginfo, you will see list of
all of the installed packages on the system with a one-line listing per
package.
# pkginfo
system CADP160 Adaptec Ultra160 SCSI Host Adapter
Driver
application CFWWine WINE
system HPFC Agilent Fibre Channel HBA Driver
system NCRos86r NCR Platform Support, OS Functional
ity (Root)
system SK98sol SysKonnect SK-NET Gigabit Ethernet
Adapter SK-98xx
system SKfp SysKonnect PCI-FDDI Host Adapter
application SMChtdig htdig
<text snipped>
system SUNWzlib The Zip compression library
system SUNWzoner Solaris Zones (Root)
system SUNWzoneu Solaris Zones (Usr)
system SUNWzsh Z shell (zsh)
system SYMhisl Symbios 895A, 896 and 1010 SCSI driver
If you are just interested in a particular package, you can use pkginfo
pkgname where pkgname is the relevant package. But you need
to bear in mind that the name assigned to the package may have SUNW
in front of it or may not otherwise be exactly what you expect. E.g., suppose
I want to know whether the zlib package is installed, because
I want to install some other package that lists the zlib software
as a dependency. If I use the command pkginfo zlib, I see the
following:
# pkginfo zlib
ERROR: information for "zlib" was not found
Using pkginfo | grep -i pkgname will likely be better, unless
you are certain of the package name.
# pkginfo | grep -i zlib
system SUNWzlib The Zip compression library
Now I see the package name for the zlib package is SUNWzlib
and I could use that command with the pkginfo command, but
I want see any more information unless I use the -l option to
get a long listing.
# pkginfo SUNWzlib
system SUNWzlib The Zip compression library
# pkginfo -l SUNWzlib
PKGINST: SUNWzlib
NAME: The Zip compression library
CATEGORY: system
ARCH: i386
VERSION: 11.10.0,REV=2005.01.08.01.09
BASEDIR: /
VENDOR: Sun Microsystems, Inc.
DESC: The Zip compression library
PSTAMP: sfw10-x20050108014620
INSTDATE: Jul 08 2006 23:00
HOTLINE: Please contact your local service provider
STATUS: completely installed
FILES: 13 installed pathnames
4 shared pathnames
4 directories
2 executables
424 blocks used (approx)
The long listing shows me the version of zlib installed, which
in this case is version 11.10.0. I also see the installation date was
July 8, 2006 at 11:00 P.M.
References:
-
Solaris: list installed packages with pkginfo
November 28, 2005
tech-recipes - Your cookbook of
tech-tutorials
[/os/unix/solaris/commands]
permanent link

Privacy Policy
Contact







