Mon, Apr 30, 2007 11:13 pm
Charlene Infection
After a user complained of popup windows advising her to download
antivirus software, I checked the system with
Spybot Search & Destroy.
Spybot found the following malware on the system:
FunWeb
FunWebProducts
MyWay.MyWebSearch
MyWebSearch
TagASaurus
Zlob.VideoAccessActiveXObject
I also found that the popup ad was appearing whenever Internet Explorer was
opened. When Interenet Explorer was opened it would go immediately to
http://aprotectservice.com/, which
would result in a dubious W32.Myzor.FK@yf virus warning appearing.
[ More Info ]
[/security/spyware/funwebproducts]
permanent link
Mon, Apr 30, 2007 12:39 am
Remotely Enabling Remote Desktop Protocol
If you need to enable Remote Desktop support on a system in a
domain from the domain controller, you can do it by editing
the
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server
key in the registry of the remote system. By changing the
value of
fDenyTSConnection from 1 to 0 and
then rebooting the system, you can enable Remote Desktop
support.
[
More Info ]
[/os/windows/software/remote-control/rdp]
permanent link
Sun, Apr 29, 2007 9:30 pm
Updating NVIDIA Driver Fixed GoPets and Second Life Problem
When I updated the driver for the NVIDIA GeForce 6150 LE video adapter
in a Windows XP PC earlier today from version 8.2.08 (driver date:
5/9/2006) to version 6.14.10.9371 (driver date: 10/22/2006),
the update corrected a problem with
GoPets and a problem with
Second
Life.
A family member has many fruit trees on GoPets from which she harvests
fruit regularly. However, whenever she put the fruit in her inventory,
GoPets would randomly crash. Sometimes it would crash after she put only
1 piece of fruit in her inventory. At other times, she could put 3 or 4
pieces of fruit in her inventory before it crashed. And sometimes even 10 or
more pieces of fruit in her inventory. Upgrading the driver for the NVIDIA
video card stopped those crashes altogether.
When she was in Second Life, her avatar would continually turn to the right,
as if she was clicking the arrow to turn to the right. The only way she
could stop the behavior was to switch to full-screen mode, which she
preferred not to do. Updating the video driver resolved that problem, also.
For anyone experiencing either problem, you can check the version of the
driver for the video adapter in your system by the following steps on a
Windows XP system:
- Click on Start.
- Click on Settings. If you don't see Settings,
look for Control Panel instead.
- Click on Control Panel.
- Within the Control Panel, double-click on System.
- Click on the Hardware tab.
- Click on the Device Manager button.
- Double-click on Display Adapters to expand the list of
display adapters.
- Right-click on a display adapter (for most systems there will be only 1)
and choose Properties.
- Click on the Driver tab. You should then see the driver
provider, driver date, and driver version listed.
- You can then click on Cancel and close the window.
If you are experiencing any of the above problems a driver update may help.
If your system has an NVIDIA adapter, you can get the latest drvier from
the NVIDIA
software download webpage.
[/os/windows/software/games]
permanent link
Sun, Apr 29, 2007 3:31 pm
GoPets and Second Life Won't Run After Nvidia Hardware Acceleration Turned Off
I turned off hardware acceleration for an Nvidia GeForce 6150 LE
video adapter in a Windows XP Media Center PC, but then the family member using
the system found that neither GoPets nor Second Life would start.
For
GoPets, the following
window appeared.
| Initialize Error |
Your video card could not support the requested 3D function.
This error may occur if your video card is not supported by GoPets.
Please view the Download page at the GoPets website for a list of
unsupported video cards.
OK
|
When she clicked on OK, another error window appeared.
| Error |
 Failed to
initialize the rendering engine.: 0 Failed to
initialize the rendering engine.: 0
OK
|
Clicking OK on that window closed the
application.
When she started Second Life
the message "detecting hardware" appeared followed by the error
window below.
| Error |
Second Life is unable to run because your video card drivers
are out of date or unsupported. Please make sure you have
the latest video card drivers installed.
If you continue to receive this message, contact customer service.
OK
|
I had turned video acceleration off for the Nvidia graphics adapter
when Paint Shop Pro 9 would not start with it turned on. To turn
it back on I tried the following steps.
- Right-click on desktop.
- Select Properties.
- Click on Settings.
- Click on the Advanced button.
But then the following message appeared.
| NVIDIA Display |
The NVIDIA Display Panel extension cannot be created.
Possible reasons include:
Disabled graphics hardware acceleration. To enable Hardware
Acceleration:
- Right click on your desktop, select Properties, the Settings
tab, and click Advanced.
- Click the Troubleshoot tab and move the 'Hardware
acceleration' slider all the way to Full.
- Click OK.
- If prompted, restart your computer.
OK
|
I clicked on the Troubleshoot tab instead, clicked
on the hardware acceleration slider and dragged it down
to the "Full" end. GoPets and Second Life then started
when I tried to open them. Paint Shop Pro 9 wouldn't
start again, though. It hung while starting up (see
Paint Shop Pro Hangs at Startup).
I checked the version of the driver installed for the
NVIDIA GeForce 6150 LE through the device manager.
I saw the following.
| Driver Provider: | NVIDIA |
| Driver Date: | 5/9/2006 |
| Driver Version: | 8.2.0.8 |
| Digital Signer: | Microsoft Windows Hardware Compatibility
Publisher |
I went to the NVIDIA
software download page. I didn't find a driver listed specifically for
the NVIDIA GeForce 6150 LE adapter, but I found that the GeForce 6 Series
driver supports the GeForce 6150 LE adapter.
The "Driver Installation Hints" for the new driver stated the following.
Before installing new drivers make sure you uninstall all NVIDIA display drivers
from the Windows Control Panel. Browse to the Start Menu > Windows Control Panel >
Add/Remove Programs and search for "NVIDIA Windows Display Drivers" or "NVIDIA
Display Drivers" and select remove.
I removed the existing NVIDIA drivers through "Add or Remove Programs".
I chose to "Remove all NVIDIA drivers, including Display". I also opted
to remove the nView profiles. After rebooting, GoPets, Second Life, and
Paint Shop Pro 9 all started without problems.
[/os/windows/software/games]
permanent link
Sat, Apr 28, 2007 1:30 pm
Removing the Arrow from Windows Shortcuts
If you want to remove the arrow that appears on Windows shortcuts,
you can do so by using the following procedure.
- Click on Start.
- Select Run.
- Type regedit
- Click on Ok.
- Navigate to HKEY_CLASSES_ROOT\lnkfile.
- On the right side of the window, right-click on IsShortcut and
choose Delete.
Remember, you must be careful when editing the registry. Mistakes in
editing registry entries can cause significant problems.
As an alternative to the above method, you can use this
shortcut-arrow-removal.reg registry file,
which will delete the IsShortcut key from the registry. Download the
file (you can right-click on the link and choose "download", "save
link target as", or whatever your browser ues to initiate a download)
and then, once it is downloaded, double-click on the file on your system.
When prompted "Are you sure you
want to add the information in shortcut-arrow-removal.reg to the
registry?", select "Yes". That action will result in the key being
removed; the prompt about adding information is just the default
message that appears whenever you click on a
.reg file.
References:
-
Remove shortcut arrow from desktop icons
Free PC Tech Support -
Guides and FAQs
[/os/windows/registry]
permanent link
Sat, Apr 28, 2007 12:33 pm
Problem Uninstalling Starddock Central Applications
A family member uninstalled
StarDock
Central, but then found the files for the software were still under
C:\Program Files and the applications, such as WindowBlinds,
which are part of the software, still seemed to be active on the system.
I suggested reinstalling StardDock Central and then uninstalling the various
modules, such as WindowBlinds from within it. After reinstalling StarDock
Central and then opening StarDock Central, right-clicking on the various
packages and choosing "uninstall" would not uninstall the packages.
Trying to uninstall IconPackager produced the message below.
| Stardock Central |
There has been an error uninstalling IconPackager. Would you like to set the
item as uninstalled?
Yes
No
|
Trying to uninstall WindowBlinds produced a similar message
| Stardock Central |
There has been an error uninstalling WindowBlinds4. Would you like to set the
item as uninstalled?
Yes
No
|
On one of the StarDock Forums, there
was a posting
Uninstall Problem Gives me an error where someone reported a problem
uninstalling WindowBlinds to which a respondent suggested running a "zapper"
program from StarDock to uninstall StarDock applications. The
ODNT Component
Zapper is available from
Downloads at the Stardock site.
Stardock describes it as a "Utility program that can be used to unload or
remove Object Desktop components (like if an install.log file is missing). Warning:
this will delete any installed skins/themes for the component when used to
uninstall that component."
I ran the program and chose "Select All" to remove all Object Desktop
components.
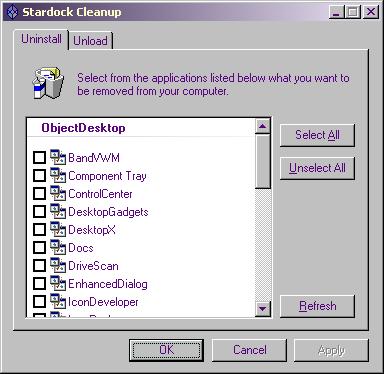
A window popped up showing the applications to be removed, but the list
was so long I couldn't see the buttons at the bottom and there was no
scrollbar. But, since the default response button was "Yes", hitting
the enter key resulted in an attempt to zap the programs, but then
I saw "odnt_zapper.exe has encountered a problem and needs to close.
We are sorry for any inconvenience." However when I restarted the ODNT
Component Zapper, I didn't see any applications listed to remove this
time under the Uninstall tab. But under the Unload tab,
I saw WebBlinds listed. I chose to unload it by selecting
it and then clicking on Apply.
I then clicked on Start, Control Panel, and then
Add or Remove Programs, chose Stardock Central,
and then Change/Remove to remove it from the system.
The C:\Program Files\Stardock folder remained, so I
attempted to manually delete it.
When I tried deleting it, I saw the message "Renaming, moving or
deleting 'Stardock' could make some programs not work. Are you
sure you want to do this?" I chose "No" and rebooted, thinking
perhaps a DLL
file associated with the program might still be loaded in memory.
I got the same message after rebooting when I tried uninstalling
it again, but this time I chose "Yes" to proceed with the
uninstall
-
Uninstall Problem Gives
me an error
By kid4christ
Posted December 10, 2005
Stardock Forums
[/os/windows/software/themes]
permanent link
Fri, Apr 27, 2007 9:16 pm
Paint Shop Pro Hangs at Startup
Whenever I attempted to start PaintShop Pro 9 on a Windows XP system,
the program would hang at startup. When I tried to uninstall it, the
uninstall routine hung as well. I finally resolved the problem by
disabling hardware acceleration for the Nvidia video adapter in the system,
though updating the driver for the video card may resolve the
problem as well [Update: that is probably the better alternative, since
turning off hardware acceleration may create problems for other programs
as noted in
GoPets and Second Life Won't Run After Nvidia Hardware
Acceleration Turned off]
[ More
Info ]
[/os/windows/software/graphics/corel/psp]
permanent link
Thu, Apr 26, 2007 8:58 pm
Add Notification Sounds to SquirrelMail
To add additional notification sounds that a user can select to have played
when she receives new email, place the
wav
file you wish to add in
/usr/share/squirrelmail/plugins/newmail/sounds.
You've Got Mail Wav File
[/network/email/squirrelmail]
permanent link
Mon, Apr 23, 2007 9:00 pm
PayPal Phishing Page at Hong Kong University Removed
When I checked agin, I found the PayPal phishing page that was located
on a webserver at the Hong Kong Polytechnic University this weekend was
now gone.
[/security/scams/phishing/paypal]
permanent link
Mon, Apr 23, 2007 6:42 pm
Adding an Account to the Administrator Group
Sometimes you may need to add an account to the Administrator group
temporarily to install software that otherwise won't run from a
normal users account. Perhaps the software can be made to run if
you can determine all of the files and registry keys it needs to
access and provide the appropriate permissions on those, but
sometimes the most reasonable course is just to reinstall the software
from a user account after adding the user to the administrator group
temporarily and then remove the user account afterwards.
To do so on Windows XP system, e.g a Windows XP Home or Media Center
Edition system, take the following steps:
- Log into the system as the administrator.
- Click on Start.
- Click on Control Panel.
- Double-click on User Accounts.
- Double-click on the account to which you wish to grant administrator
access.
- Click on Change the account type.
- Change the account type from Limited to Computer
Administrator.
- Click on the Change Account Type button.
- Logoff as administrator and logon under the user account.
You can then follow the same procedure after you have installed the
software to change the account type back to Limited.
[/os/windows/xp]
permanent link
Sun, Apr 22, 2007 2:59 pm
PayPal Phishing at Hong Kong Polytechnic University
When I checked to see if the spoofed
PayPal webpages were still present at
http://production.mic.polyu.edu.hk/pp/login.html, I found the pages
were still accessible. Yesterday, someone forwarded a message to me
which stated an email address had been added to his PayPal account. The
message asked him to confirm the addition by going to a PayPal website, but
the link in the message actually led to the server at the Media Innovation
Centre in the School of Design at the Hong Kong Polytechnic University.
The recipient doesn't have a PayPal account. Whoever created the spam
message probably sent it to thousands of people with no way of knowing
how many of those recipients might have PayPal accounts.
I checked the online directory for the university today and sent another
message regarding the spoofed site; this time I sent the message to
the chair of the School of Design at the
university plus email addresses for people who appeared to be IT people at
the university, and some general contact addresses. Hopefully, one of them
can get the spoofed webpages removed and take action that will result in
the perpetrator being apprehended and disciplined.
[/security/scams/phishing/paypal]
permanent link
Sat, Apr 21, 2007 8:15 pm
PayPal Phishing at a Hong Kong University
A user forwarded an email message to me today that attempts to lure
gullible
PayPal users to a website
at a university in Hong Kong. The email message asked the recipient to
verify the addition of an email address to his PayPal account by going
to the PayPal website. But the link actually directed anyone who clicked
on it to
http://production.mic.polyu.edu.hk/pp/login.html. The "hk" at the end
of the domain name indicates the site is in Hong Kong, since "hk" is the
country code for Hong Kong. The "edu" before it indicates it is an
educational institution.
Going to http://mic.polyu.edu.hk/
instead, I found the following information for the site:

I reported the spoofed site to to the contact address listed for the Hong Kong
Polytechnic University.
The webserver being used to host the spoofed PayPal site apparently
belongs to the Multimedia Innovation Centre School of Design at that university.
I also reported this
phishing
attempt to PayPal via the PayPal
Report Fake Site/Spoofwebpage.
And I reported the spoofed site at the
following phishing report wepbages:
[/security/scams/phishing/paypal]
permanent link
Tue, Apr 17, 2007 9:50 pm
Attachment Sizes for Free Email Services
Google offers a free email service
Gmail. Google offers up to 2,500 MB (2 GB)
of storage for Gmail accounts. With that service attachments
can be up to 10 MB in size. I have successfully sent a message with a 10 MB
attachment to a test Gmail account I maintain. It is possible that
a message with an attachment that is somewhat less than 10 MB might not
be delivered, though. Google states the following in regards to attachment
size for messages from/to Gmail accounts:
With Gmail, you can send and receive messages up to 10 megabytes (MB) in size.
However, the precise amount allowable will depend on the attachment.
When you add an attachment, the size of a file may increase because transport
encodings are automatically added. (Transport encodings are the information
that allows your message to be safely sent and read.)
This means that in some cases, attachments that are 6 to 10MB in size may push
the total message size above 10MB. When this happens, Gmail displays a warning
that your message exceeds the 10MB limit.
Microsoft offers a free email service
Hotmail, which provides 1,000 MB (1 GB)
of free storage for email. That service currently has a 10 MB limit on
attachments. I have successfully sent a message with a 10 MB attachment to
a test Hotmail account I maintain.
Hotmail also has the following restrictions currently:
- You can send a maximum of 250 messages per day.
- You can send a message to a maximum of 50 e-mail addresses at the same time.
These addresses can be distributed among the To, Cc, and Bcc lines, or they
can all be on one line.
- You can send messages up to 10 MB each, including attachments.
[/network/email/free]
permanent link
Mon, Apr 16, 2007 7:42 pm
ClamWin No Longer Reporting Opera Infected with Trojan.Bifrose-495
When I scanned
opera.exe, the executable for the
Opera 8.54 web browser on April 8, 2007
with
ClamWin 0.90.1, it reported
the file was infected with Trojan.Bifrose-495 (see
ClamWin Reporting Opera Infected with Trojan.Bifrose-495). The
report appeared to be a false positive and I submitted the file as a false
positive using the form at
ClamAV Virus Database.
When I opened ClamWin today to see if new virus definitions would result in
the file no longer being reported as infected, I saw the message
"You have not yet downloaded Virus Definitions Database. Would you like to
download it now?" I chose "Yes". ClamWin appeared to download new definitions,
but when I selected the file the Scan button was grayed out. I closed
and reopened ClamWin. Again I got the message stating that I had not yet
downloaded virus definitions. I chose to download them again, but the results
were the same. When I exited from the program, right-clicked on the file to
scan and chose "Scan with ClamWin Free Antivirus", I saw the message
"Virus Definitions Database Not Found! Please download it now."
So I checked the ClamWin website. I found there was a new version, 0.90.1.1
The site had the following information on the new version:
Wednesday, 11 April 2007
This quick-fix release addresses the "Missing Virus Database" Error. Also it
includes couple of bug fixes:
- Fixed file creation errors during scanning of OLE and MSI files
- Added description message when a "Can't Open File" error occurs
- Setup now installs virus definitions database
I installed the new version. I was then able to scan opera.exe
and it now reports that the file is uninfected. Previously ClamWin 0.90.1
was reporting that laplink.exe was also infected. It reported that
file was infected with Trojan.Mybot-7604. I felt then that there was a fairly
high probabability that the report was another false positive. When I scanned
the file with the new version of ClamWin with current virus definitions, that
file is now reported as uninfected as well.
[/security/antivirus/clamav]
permanent link
Sun, Apr 15, 2007 4:53 pm
Stopping an Attacker with the Route Reject Command
You can use
KRIPP
to monitor
FTP dictionary
attacks where an attacker tries to guess a userid and password combination to
break into an FTP server. You can block the attacking system with the
route command, e.g.
route add 202.123.213.3 reject
to block all packets from 202.123.213.3. When the attacker has moved on to
other targets, you can remove the routing table entry with
route del 202.123.213.3 reject.
[ More Info ]
[/os/unix/commands]
permanent link
Sat, Apr 14, 2007 9:12 pm
Changing an Uppercase Name in Perl
For a Perl variable,
$name, which contains a name in the form
first name followed by a space and then the last name with all letters in
uppercase, the following code will change the name so that only the first
letter of both parts of the name is capitalized with the rest of the name
in lowercase. E.g. if $name contains
JOHN SMITH, afterwards it
will contain
John Smith.
# The name is in all uppercase letters. Leave the first letter of
# each part of the name in upper case, but put all the others in lowercase
$name =~ tr/A-Z/a-z/;
$name =~ s/([a-z]+)\s([a-z]+)/\u$1 \u$2/;
The first line changes all uppercase letters to lowercase. The next line
looks for the first part of the name, which is stored in $1. There is then
a space followed by the last name, which is stored in $2. Using the substitute
command, the first letter of $1 is changed to uppercase as is the first letter
of $2.
The [a-z] instructs Perl to look for an occurrence of any
letter from "a" to "z". The + afterwards indicates that Perl should
look for 1 or more occurrences of any letter between "a" and "z". Enclosing
the [a-z]+ between ( and ) instructs
Perl to store what if finds, i.e. the first name in this case, in a variable
$1. The \s tells it to look for a whitespace
character, i.e. a space in this
case, and then the next ([a-z]+) will find all of the letters for
the last name and store it in a variable $2 The \u
changes the following letter to uppercase for $1, which is the
first name. The \u$2 then changes the first letter of $2
, which is the last name to uppercase.
[/languages/perl]
permanent link
Mon, Apr 09, 2007 11:01 pm
Anomalous Windows XP Firewall Rules
When checking the firewall settings on a Windows XP Service Pack 2
system tonight, I found several anomalous firewall rules. The system
is running the Windows XP firewall.
When I checked the firewall openings with the netsh firewall show
state command, I didn't see anything unusual.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Enable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
135 TCP IPv4 (null)
137 UDP IPv4 (null)
139 TCP IPv4 (null)
138 UDP IPv4 (null)
9370 UDP IPv4 C:\Program Files\Logitech\Desktop Messenger\8876480\Pr
ogram\LogitechDesktopMessenger.exe
3389 TCP IPv4 (null)
445 TCP IPv4 (null)
22 TCP IPv4 C:\Program Files\Network\OpenSSH\usr\sbin\sshd.exe
Nor did I see anything unusual when I issued the command
netsh firewall show portopening.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
22022 TCP Enable OpenSSH
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
However, when I went to the
GUI for configuring the
firewall to correct an mistake I noticed in the firewall configuration, I
saw DwnMaster listed. I didn't know what that program was
nor why it needed a firewall rule.

Double-clicking on DwnMaster showed that the program
associated with the firewall rule was syst.exe in
C:\WINDOWS\Temp.
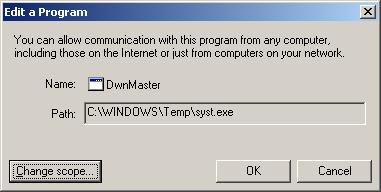
When I checked to see if syst.exe was running, I didn't
see evidence of it running.
C:\>tasklist /fi "imagename eq syst.exe"
INFO: No tasks running with the specified criteria.
And when I checked for the existence of the file, however, though
I found it, it was only zero bytes in length. I am presuming
that it was nullified during an antivirus or antispyware
scan of the system.
C:\>dir c:\windows\temp\syst.exe
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\windows\temp
02/02/2007 03:32 AM 0 syst.exe
1 File(s) 0 bytes
0 Dir(s) 57,556,082,688 bytes free
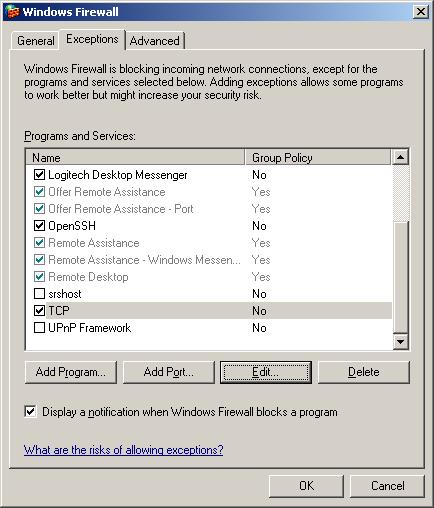
Looking at the "allowed programs" list for the firewall, I noticed another
unusual entry, C:\win.com.
C:\>netsh firewall show allowedprogram
Allowed programs configuration for Domain profile:
Mode Name / Program
-------------------------------------------------------------------
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable DwnMaster / C:\WINDOWS\Temp\syst.exe
Enable TCP / C:\WIN.COM
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
Allowed programs configuration for Standard profile:
Mode Name / Program
-------------------------------------------------------------------
Enable restorea0 / c:\windows\system32\restorea0.exe
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
The name given to it was TCP, apparently in an attempt to
make it less likely to stand out as possible malware.
But I wouldn't expect to find a win.com file in the
root directory of a Windows XP system.
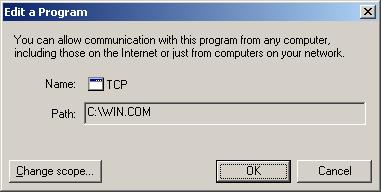
It was also a zero byte file when I checked for its existence, however, so
may also have been nullified by a previous scan of the system with antivirus
or antispyware software.
C:\>dir c:\win.com
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\
02/09/2007 02:47 AM 0 WIN.COM
1 File(s) 0 bytes
0 Dir(s) 57,555,771,392 bytes free
Another allowed program that looked suspicious was
restorea0 in
c:\windows\system32\.
But when I looked for it, I did not see it on the system. So
it may have been removed completely by antivirus or antispyware software
previously. At
FKIYY.EXE
Spyware Remove, I found it listed as one of many alternative names
associated with malware detected by Prevx.
At
SYST.EXE Spyware Remove, Prevx lists syst.exe as being
associated with Trojan Downloader Small yt. At
WIN.COM
Spyware Remove, win.com is linked to
Adware Virtumonde
[/os/windows/xp/firewall]
permanent link
Mon, Apr 09, 2007 9:47 pm
Allow Rtvscan Access Through Windows XP Firewall
Symantec AntiVirus Corporate Edition 8.0 uses rtvscan.exe on client systems
for management of those systems from the antivirus server. Rtvscan listens
on
UDP port 2967 on the
client systems. You can determine if rtvscan.exe is running on a Windows
XP or later system with the
tasklist command.
C:\>tasklist /fi "imagename eq rtvscan.exe"
Image Name PID Session Name Session# Mem Usage
========================= ====== ================ ======== ============
Rtvscan.exe 1784 Console 0 9,736 K
From the above information, I can see that rtvscan.exe is running on the
system and that it has process ID (PID) 1794. I can verify that the process
with PID 1784 is listening on port 2967 on the system using the
netstat command.
C:\>netstat -ano | find "1784"
UDP 0.0.0.0:1061 *:* 1784
UDP 0.0.0.0:2967 *:* 1784
You can create a firewall rule to allow the server to communicate with the
client using the instructions at
Configuring Windows XP Firewall for Symantec
Antivirus Client through either a
GUI or the command line.
An example using the command line is shown below. The example below presumes
the server's IP address is 192.168.0.33.
C:\>netsh firewall set portopening protocol = UDP port = 2967 name = "Symantec A
ntiVirus Client Management" mode = ENABLE scope = CUSTOM 192.168.0.33
Ok.
You can verify the firewall now has the appropriate port opening with the
netsh firewall show portopening command.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
22 TCP Enable OpenSSH
2967 UDP Enable Symantec AntiVirus Client Management
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
3389 TCP Enable Remote Desktop
Port configuration for Local Area Connection:
Port Protocol Mode Name
-------------------------------------------------------------------
3389 TCP Enable Remote Desktop
Or, alternatively, you can use the netsh firewall show state
command.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Enable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
10243 TCP IPv4 (null)
10280 UDP IPv4 (null)
10281 UDP IPv4 (null)
10282 UDP IPv4 (null)
10283 UDP IPv4 (null)
10284 UDP IPv4 (null)
135 TCP IPv4 (null)
137 UDP IPv4 (null)
139 TCP IPv4 (null)
138 UDP IPv4 (null)
3389 TCP IPv4 (null)
445 TCP IPv4 (null)
22 TCP IPv4 C:\Program Files\Network\OpenSSH\usr\sbin\sshd.exe
1562 TCP IPv4 C:\WINDOWS\SYSTEM32\SVCHOST.EXE
2869 TCP IPv4 (null)
1900 UDP IPv4 C:\WINDOWS\SYSTEM32\SVCHOST.EXE
2967 UDP IPv4 C:\Program Files\Symantec_Client_Security\Symantec Ant
iVirus\Rtvscan.exe
Additional ports open on Local Area Connection:
Port Protocol Version
-------------------------------------------------------------------
3389 TCP Any
The netsh firewall show state command will show you what program
is listening on the port. In this case it shows that Rtvscan.exe is listening
on port 2967
References:
-
Configuring Windows XP Firewall for Symantec Antivirus Client
Written: May 30, 2005
MoonPoint Support
[/security/antivirus/symantec/SAV-Firewall]
permanent link
Sun, Apr 08, 2007 11:10 pm
ClamWin Reporting Opera Infected with Trojan.Bifrose-495
When I scanned a system with
ClamWin
0.90.1, it reported that the executable
opera.exe for the
Opera web browser was infected with
Trojan.Bifrose-495. The system has Opera 8.54 on it.
Checking the definitions timestamp in ClamWin, I saw the following:
ClamAV 0.90.1
Protecting from 107238 Viruses
Virus DB Version: (main: 42, daily: 3049)
Updated: 18:49 08 Apr 2007
I found someone else reporting the same problem on a ClamWin support forum at
False Positives. And I found a post,
Opera.exe: Trojan.Bifrose-495 FOUND,
on an Opera community forum site, where someone posted that ClamAV reported
"Trojan.Bifrose-495 FOUND" for opera.exe, though in his case it appeared he
had version 7 of Opera on his system. He submitted opera.exe from his system
to VirusTotal,
which provides a free service allowing you to upload a file for analysis by
many different antivirus programs. Only ClamAV
and Fortinet identified the file as
being suspicious. The other 27 antivirus scanners used by VirusTotal reported
it was uninfected. ClamWin is a Windows implementation of
ClamAV.
There was also another posting,
Trojan.Bifrose-495?
in a ClamWin forum where someone stated that ClamWin 0.88.7 reported
the same infection for his copy of opera.exe. One of the ClamWin
developers, sherpya, responded that it was a false positive. That person
also submitted his copy to VirusTotal. The result was the same for him, with
only ClamAV reporting the file as infected and Fortinet labelling it as
"suspicious".
I found someone else reporting that ClamWin reported Opera was infected
with Trojan.Bifrose-495 at
Cleaning up a trojan, but the poster didn't appear to consider
the possibility that the report may have been a false positive.
I submitted the opera.exe file from my system to
VirusTotal also. One of the ClamWin
developer's referred the person who posted at
False Positives on the ClamWin forum
to How can I report a
virus that ClamWin doesn't recognise? Or a false positive?, which also
suggests submitting the file to VirusTotal
, if you suspect that ClamWin is reporting a false positive.
The file was scanned by 23 antivirus programs. Only ClamAv and Fortinet
reported an issue with the file. ClamAv reported it found "Trojan.Bifrose-495",
while Fortinet reported the file as "suspicious".
I also submitted the file to
Jotti's Malware Scan, which also
provides a free virus scanning service. Of the 17 antivirus programs it
uses, only ClamAv reported the file as infected with ClamAv reporting
"Found Trojan.Bifrose-495". It scanned the
file with Fortinet as well, but reported for Fortinet that "Found nothing"
(see report
).
I did submit the file using the on-line form at
ClamAV Virus Database as a false positive.
So what does Trojan.Bifrose-495 do? I don't know and could not find any
information on it via a
Google
search. Though I really like ClamWin and ClamAV, using them on many
systems, one major advantage I see to a program like Symantec's antivirus
software, aside from real-time scanning, is that Symantec will provide you
with details on how most of the viruses it identifies work. By looking
at the provided details, you can determine, if your system was infected,
what the virus or trojan may have done and what other indicators of the
infection you should expect to find on the system. ClamAV and thus ClamWin,
which is built on ClamAV, provide no virus encyclopedia you can use for
reference. If this wasn't a false positive I would certainly like to
know how the virus or trojan operates, not just a name for it. Does it
allow someone to take remote control of the infected system? Does it send
out spam from the system, delete or corrupt files, etc.?
I normally use ClamWin as an adjunct to other antivirus software on a system
and don't want real-time scanning capability from it, but really would like to
have further details on any infections found. I have found ClamWin
identifies malware other antivirus programs sometimes miss and am very
appreciative of the work done by the developers for both ClamAV
and ClamWin, but, whenever they report an infected file, I often have
to submit the file to VirusTotal
or Jotti's Malware Scan to
attempt to figure out the potential harm that may have been caused
by an infection. I look at the names used for the infection by
other antivirus programs that also report the submitted file is
infected. I then look check virus encyclopedias they may provide or
do further searching of the web using the names they use for the malware.
Details for the file I submitted:
| Filename: | opera.exe |
| Size: | 76.5 KB (78,336 bytes) |
| Created: | Saturday, April 15, 2006, 1:34:26 PM |
| Modified: | Friday, March 24, 2006, 5:40:10 PM |
| File Version: | 7730 |
| Product Name: | Opera Internet Browser |
| Product Version: | 8.54 |
| MD5 Sum: | 40d2e3a6f1c1dbe7825553164a3b86d3 |
| SHA-1 Hash: | c9623b9018fb6faebef38af37ff02dad361f774d |
The modification date listed on the file when I right-clicked on it
and chose Properties was March 24, 2006. I installed Opera 8.54
on the system on April 15, 2006, so the modification date listed is several
weeks prior to the software being installed on the system.
I also scanned the file with BitDefender 8 Free Edition, which had virus
definitions of April 8, 2007, which is today's date, and Symantec AntiVirus
Corporate Edition 8, which had virus definitions from April 4, 2007. Both of
those antivirus programs were on the system where I ran the ClamAV scan. Both
reported the file was uninfected, so I'm fairly confident at this point
that ClamAV's report of the file as infected was a false positive.
References:
-
False Positives
Posted February 11, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Opera.exe: Trojan.Bifrose-495 FOUND
Posted: December 20, 2006
Forums - Opera Community
-
Trojan.Bifrose-495?
January 5, 2007
ClamWin Free Antivirus Support and
Discussion Forums
-
Cleaning up a trojan
December 21, 2006
WebDeveloper.com Forum
[/security/antivirus/clamav]
permanent link
Sun, Apr 08, 2007 7:53 pm
LibClamAV Error When Scanning a System with ClamWin 0.90.1
I upgraded ClamWin on a system from
version 0.88.4 to 0.90.1, set it to scan all of drive C on the
system and then went to bed.
When I checked the results 9 hours later, I was surprised to find ClamWin
still running. I also saw lots of error messages similar to the following:
LibClamAV Error: ERROR: failed to create file: c:\docume~1\admini~\locals~1
\temp/clamav-b3e9e513a21a2f87d6834aa7fb84676.00000530.clamtmp/
_becaa_r_ndoaa_geiaa_cemaa_r_behaa_feiaa_heeaa_kdbaa_idhaa_idpaa_ldg
aa_ldoaa_idjaa_D_ideaa_idjaa_ldmaa_
On the Clamwin support forums, I found several references to the problem.
At ERROR: failed to create file, shepya, one of the
ClamWin developers, responded on November 12 that the
problem was due to the
OLE2
unpacker that is used by ClamWin attempting to
unpack CAB
files, but encountering problems when doing so, since the files
inside the CAB file have seemingly random names and unpacking them with the OLE2
unpacker would lead to new files being created with the same name as existing
files, if ClamWin didn't stop unpacking the files and produce the error message
instead. Sherpya stated in his response that ClamWin first tries
to unpack the CAB files with a CAB unpacker, but for Installshield CAB files,
since Installshield CAB files are not supported, it then passes the file on to
the OLE2 unpacker, which can't properly unpack the CAB files. Shepya states
the problem is due to Microsoft using the same file signature for both CAB and
OLE2 files.
File Extension for .CAB also indicates that InstallShield CAB
files are not compatible with Microsoft CAB files.
Shepya further stated in a December 11, 2006 posting in the same thread that
"since the cab code skips the archive, so it's passed to the ole2 code
that doesn't pick the correct filenames to extract and since there are a lof of
garbage in file names, clamav tries to sanitize it by replacing invalid chars
by a _, this causes a lot of name clashes, but I preferred to warn instead of
silent ignoring." ClamWin is using ClamAV
for virus scanning; it is a Windows implementation for ClamAV.
There is another thread on the topic at
Scan Write Errors. Sherpya states in that one that
"m$ decided to make .msi files like ole2 container just like office
document, but really they are a sort of cab archives."
And in response to the
LIBCLAM AV error posting on April 4, 2007 by cebo, sherpya responds
that "these messages are harmless, they will be removed on next release."
I certainly hope there is an improvement with the next release.
Previously, when
I started ClamWin on this system before going to bed, it would be finished when
I checked it in the morning. When I checked the system at 9:00 A.M.
after starting it around 11:00 P.M. the previous night, I found the
CPU utilization was at about 100%. ClamWin was using over half the CPU time,
but Spy Sweeper was also using a considerable amount of CPU time. I stopped
Spy Sweeper. Then ClamWin was getting almost all of the CPU time, with the
Task Manager showing its CPU utilization fluctuating between 90% and 97%,
yet it still did not complete until 7:00 P.M., almost 20 hours after I started
it.
I also saw the error message LibClamAV Error: Message is not un
uuencoded form during the scan.
References:
-
ClamWin
-
ERROR: failed to create file:
Posted: November 6, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Scan Write Errors
Posted: October 11, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Cabinet
(file format)
Wikipedia, the free encyclopedia
-
File Extension for .CAB
FILExt
-
Object Linking and Embedding
Wikipedia, the free encyclopedia
-
LIBCLAM AV error
Posted: Wednesday, April 4, 2007
ClamWin Free Antivirus Support and Discussion Forums
[/security/antivirus/clamav]
permanent link
Sun, Apr 08, 2007 12:24 pm
Excluding ClamWin Quarantine Directory When Scanning
While searching for information on error messages I was getting while
scanning a system with
ClamWin 0.90.1,
I found a comment by one of the ClamWin developers, alch, at
clamwin is scanning
its own quarantine files that in version 1 the quarantined
files will be encrypted in such a way that they won't be flagged as infected
files on subsequent scans. The response was to a ClamWin user's
complaint about the current version's default behavior of
scanning files in the quarantine folder, flagging them as infected, and then
quarantining them again with a different name. Alch made the statement on
March 23, 2007. He also stated version 1 "is in it's final stages of
development."
You can exclude ClamWin's quarantine directory from being scanned by ClamWin
by following the steps listed in
Excluding the Quarantine Directory from a ClamWin scan.
[/security/antivirus/clamav]
permanent link
Sat, Apr 07, 2007 8:03 am
Happy Birthday Internet!
Reckoning by the publication of the first Request for Comment (RFC) document,
the Internet was born April 7, 1969, when
RFC 1 Title: Host Software was
published by Steve Crocker.
RFC's
document the protcols on the Internet. The precursor to today's Internet was
the ARPANET, which was
developed for the United States Department of Defense. The first RFCs were
published in 1969 for the ARPANET. At first researchers distributed hard
copies of the RFCs among themselves, but in December of 1969 they began
distributing them using the ARPANET itself.
References:
-
April 7, 1969: Birth of That Thing We Call the Internet
By Tony Long
Wired News
-
Request for
Comments
Wikipedia, the free encyclopedia
-
ARPANET
Wikipedia, the free encyclopedia
-
RFC 1 Title: Host Software
By Steve Crocker
IETF Tools
[/network/Internet]
permanent link
Tue, Apr 03, 2007 12:01 pm
Googlebot Alert
If you would like to know when the Google webcrawler, Googlebot, visits
your website you can insert the
PHP code
below in the home page for your site.
<?
$email = "yourname@example.com";
if( eregi("googlebot", $_SERVER['HTTP_USER_AGENT']) )
{
mail($email, "Googlebot Alert",
"Google just indexed your following page: " .
$_SERVER['REQUEST_URI']);
}
?>
You will, of course, need to replace yourname@example.com with
your own email address.
On a Linux or Unix system, you can issue the following commands to see
how many requests for pages on your site today have come from a Googlebot
visit to your site.
grep "$(date +"%d/%b/%Y")" access.log | grep -i "googlebot" | wc -l
You will need to substitute the name and location of the log file that tracks
access to your site for access.log.
The $(date +"%d/%b/%Y") tells grep to look for occurrences of the
current date in the form dd/mmm/YYYY, e.g. 03/Apr/2007
. In my Apache log files, entries appear similar to the one below.
66.249.66.147 - - [03/Apr/2007:09:10:42 -0400] "GET /robots.txt HTTP/1.1" 200 146
If the date is formatted in a different manner in your log file,
you will need to adjust the format accordingly. You can obtain information
on formatting the date with man date.
If you don't have IP addresses translated to a
FQDN, e.g. if your log
file records 66.249.66.147 instead of
crawl-66-249-66-147.googlebot.com, which is the case for my
log file, then you will need to look for the IP address range that is used
by Googlebot.
Googlebot's and Mediapartners-google's IP indicates that
66.249.71.x appears to be assigned to Googlebot, though
reverse name lookups only work up to 66.249.71.208. You
can use the following commands to search for the Googlebot IP address range
66.249.71.1 to 66.249.71.255.
grep "$(date +"%d/%b/%Y")" access.log | grep -i '66.249.66.' | wc -l
The Googlebot's
and Mediapartners-google's IP article mentions that Google uses
a separate bot
that checks pages with Google AdSense ads on them. So, if you have Google
AdSense ads on your site, then both the main Googlebot bot and the
MediaPartners-Google bot will probably visit your site. The author of that
article states he has seen the following IP addresses used for the
Mediapartners-Google bot.
| 66.249.65.40 | crawl-66-249-65-40.googlebot.com |
| 66.249.66.65 | crawl-66-249-66-65.googlebot.com |
References:
-
Googlebot
Alert
By Philipp Lenssen
June 23, 2004
Google Blogoscoped
-
Googlebot's and Mediapartners-google's IP
By Tim Johansson
gurka.se
-
FQDN
Wikipedia, the free encyclopedia
-
Internet bot
Wikipedia, the free encyclopedia
[/network/web/search]
permanent link

Privacy Policy
Contact








