

|
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Image 1 at full scale
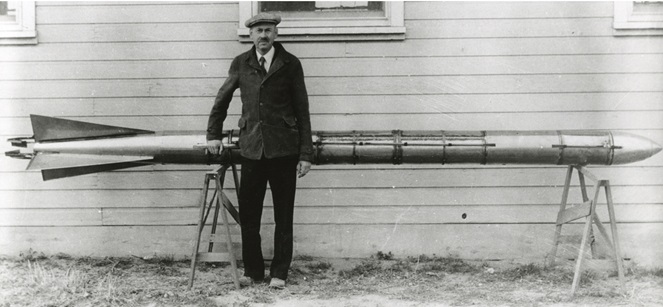
Image 1 at 75% scale

Note: The image above is a photo of Robert H. Goddard with an A-series rocket circa 1935
Related articles:
"%ProgramFiles(x86)%\Windows Media
Player\wmplayer.exe" at a command prompt window (be sure to enclose the
command within double quotes since there are spaces in the
directory path). You might wish to do so if you are logged into
one user account, but wish to open a movie or music file that is
not accesible from the currently logged in user account. If you
wished to run the program from an administrator account, you can open a command prompt window as
an administrator or you can open a unprivileged command prompt window from
the currently logged in account and then use the runas /user
command e.g., runas /user:username
"%ProgramFiles(x86)%\Windows Media Player\wmplayer.exe" where
username is the account name for the account from which you wish
to run the program. E.g., runas /user:jane "%ProgramFiles(x86)%\Windows
Media Player\wmplayer.exe" to run the Windows Media Player with Jane's
account privileges. If you need to run the command from a
Windows domain
account, you can use runas /user:domainname\username
"%ProgramFiles(x86)%\Windows Media Player\wmplayer.exe" where
domainname is the name of the domain and username is the
name of the domain user account. Once the Windows Media Player app
is open, you can then hit the Ctrl-O keys (the Ctrl
and the letter "O" key) simultaneously to open a window where you can then
browse for audiovisual files in directories to which the other user
account has access.
netstat -a -p TCP command at a command prompt.
The -a parameter specifies all connections and listening
ports should be displayed while the -p parameter can be
used to select a protocol from TCP, UDP, TCPv6, or UDPv6. If used with the
-s option to display per-protocol statistics, the protocol
argument may be any of: IP, IPv6,
ICMP, ICMPv6, TCP, TCPv6, UDP, or
UDPv6. If you only wish to view IPv6 TCP ports in use,
you can use netstat -a -p TCPv6. If you only wish to
see currently established connections, you can pipe the output of
the netstat command to the find command. E.g.,
netstat -a -p TCP | find "ESTABLISHED". Or, if you wished to
see all of the TCP ports on which the system was listening for a connection,
you could use netstat -a -p TCP | find "LISTENING". If you
wanted to see connections to a particular port, e.g., 22, for Secure
Shell (SSH) connections, you could use netstat -a | find ":ssh"
, which would show the IP addresses of the remote systems connected
via SSH, or netstat -a | find ":https" for
HTTPS connections to web sites. If you wished to see host names rather than IP addresses, you could
add the -f option, which displays a
Fully Qualified Domain Name
(FQDN) instead of an IP address for a remote system. E.g.,
netstat -a -f | find ":https". Since SSH, HTTP, and HTTPS
use TCP rather than UDP transmissions, you don't need to add the
-p parameter.
jar xf filename.jar command,
where filename.jar is the relevant .jar file, if you have
the Java
Development Kit (JDK) installed on the system — the JDK software
can be downloaded for free from Oracle's
Java Downloads
page.
Minecraft uses
.jar files for mods and if you wish to view the models (.json files), textures
(.png files) within a JAR file used by Minecraft, you can use the
jar xf filename.jar command to see those. If you
copy the .jar file to a directory where you wish to extract its contents
and then run the command from the directory in which the .jar file is located,
you should see a directory named assets appear beneath which you
can find blockstates, lang, models, and
textures subdirectories.
The .json files files, such as those you may see in a models/block
subdirectory are
JavaScript Object Notation (JSON)
files, which you can view or edit in a text editor, such as the
Windows Notepad
application. The .png files, which you may see in a textures
subdirectory are Portable Network Graphics (PNG) files, which you can
view or edit in graphics applications such as
Microsoft Paint
on Microsoft Windows systems. You can also use a tool such as
Blockbench to work with the
JSON model files and PNG images.
To change the name of a Cisco network switch, you can use
the command hostname newHostname where
newHostname is the new name you wish to apply to the switch. To
make the change permanent so the new name is still in place after a reboot,
you can follow the command with the write memory command.
Switch> Switch>enable Password: Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#hostname Styx Styx(config)#end Styx# *Sep 23 01:14:23.917: %SYS-5-CONFIG_I: Configured from console by console Styx#write memory Building configuration... [OK] Styx#
For a Cisco network switch, to change the
default gateway
address, i.e., to specify the IP address of a router that the switch will
use, enter privileged EXEC mode with the enable command, then
enter configuration mode with the command configure terminal
and then set the default gateway address with the command ip
default-gateway gatewayIPAddress where gatewayIPAddress
is the address for the router you wish the switch to use. Then exit
configuration mode with the end command. To make the change
permanent, so that it will persist after a reboot of the switch, enter
the command write memory.
Switch>enable Password: Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z. Switch(config)#ip default-gateway 192.168.1.1 Switch(config)#end Sep 23 01:26:53.415: %SYS-5-CONFIG_I: Configured from console by console Switch#write memory Building configuration... [OK] Switch#
You can view the default gateway address with the command
show ip default-gateway.
Switch>show ip default-gateway 192.168.1.1 Switch>

If you open a
command prompt window and issue
the command netstat -anp udp and
pipe the output
into the find, you should also see the system is listening
on all network interfaces, i.e., 0.0.0.0, on UDP port 69.
C:\Users\Public\Downloads>netstat -anp udp | find "0.0.0.0:69" UDP 0.0.0.0:69 *:* C:\Users\Public\Downloads>
The installation program also installs a TFTP service, which is
set to run automatically when Windows boots; you can see information
on the service if you open Services and scroll through the list of
services on the system — you can open a Services window by
typing services.msc at a command prompt window and hitting
Enter.
[ More Info ]
:v/FALL/d, i.e.,
type the colon key and then v, which works
like the grep command
grep -v to select only lines in a file that don't contain a
specified text
string.
The particular text on which you wish vim to searh is preceded and followed by
the slash
delimiter with a d at the end to specify you wish those lines
not containing the text, e.g., FALL in this case, to be deleted. If I want to
delete only those lines that begin with FALL, I can use
:v/^FALL/d as the
caret specifies that the text should occur at
the beginning of lines (a dollar sign, $, would indicate I wanted to select
only lines where the text was found at the end of the line). Note:
you can also use :g!/^FALL/d to achieve the same end —
without the exclamation mark after the global command, all
lines containing FALL would be deleted, but as the exclamation mark
represents "not", all lines not containing FALL at the beginning of the line
are deleted.
When you open the program, type d to have the program send
a DHCP discover packet, which should result in responses from DHCP servers
on the LAN. You can type Ctrl-C or q to quit
the program.
[ More Info ]
c key, which is shorthand for
ChDir, which will provide the prompt Open mailbox ('?' for
list):. You can type the name of the folder, e.g., sent to
change the currently displayed folder. If you wish to go immediately to the
sent folder when opening mutt you can use the -f option, i.e.,
mutt -f sent.
wfs and then hitting Enter.
There are a few command line parameters you can enter when staring the
program from the command line. E.g., you can enter
wfs /switch fax to start the program with its faxing interface;
wfs /switch scan is the alternative for starting with the
scanning option. Without those, the application will start in the last used
mode. For other possible arguments to the app, see
Windows Fax And Scan Command Line Options?
To install Private Internet Access (PIA) Virtual Private Network (VPN) software on an Ubuntu Linux system, download the .run file from Download the Best VPN for Linux in 2024 — Set Up in Minutes. Change the permissions on the file with the chmod command to make it executable then execute the .run file.
$ chmod +x pia-linux-3.5.7-08120.run $ ./pia-linux-3.5.7-08120.run Verifying archive integrity... 100% MD5 checksums are OK. All good. Uncompressing Private Internet Access 100% ================================= Private Internet Access Installer ================================= Installing PIA for x86_64, system is x86_64 [sudo] password for jim: ✔ Added group piavpn ✔ Added group piahnsd ✔ Copied Private Internet Access files ✔ Allow non-root /opt/piavpn/bin/pia-unbound to bind to privileged ports ✔ Created var folder ✔ Installed icon ✔ Created desktop entry ✔ Set wgpia interface to be unmanaged ✔ Created piavpn service Created symlink /etc/systemd/system/multi-user.target.wants/piavpn.service → /etc/systemd/system/piavpn.service. ✔ Started piavpn service $
You will then see a window where you can establish a VPN connection or take a tour of the software.
Or you can just hit Ctrl-L, i.e., the Ctrl and L keys simultaneously, to bring up the option to select the language for the audio associated with the video.
The menu that appears that allows you to pick a language also allows you to choose a subtitle file, such as a .srt file, if you have one for the video.
7/1/2024 for
July 1, 2024 in cell A1, you could use the formula =A1 + 280 in
cell A2, if that cell is specified with a date format (you can right-click on
the cell and choose Format Cells to verify a date format is selected
for the cell) to calcuate the date that is 280 days from July 1, 2024. You
would then see 4/7/2025 for April 7, 2025 in cell A2, if you use
the month/day/year format for the date in cell A2. Or you could put the formula
=A1 - 280 in the cell to determine the date that was 280 days
before, i.e., 9/25/2023.
If you have a Portable Document
Format (PDF) file and wish to determine the version of the PDF standard
used for the document, that information is stored in the first line of the
file. You can open the file with a
text editor, such
as the Windows
Notepad application on a Microsoft Windows system and view
the first line to determine the PDF version used for the file.
You will see %PDF-x.y where x.y is the
version of the PDF standard used in the creation of the file,
e.g., %PDF-1.7 for version 1.7.
On a Microsoft Windows system, you could also open a
PowerShell window (you can type PowerShell
in the Windows Search field and click on the
application when you see it returned in the list of
results) and use the Get-Content
cmdlet
and the -First parameter followed by the number one.
E.g.:
PS C:\> Get-Content "July 2024 Newsletter.pdf" -First 1 %PDF-1.7 PS C:\>
Related:
I added two Western
Digital 10 TB hard disk drives to a Windows 11 system.
I wanted to have the second hard disk drive (HDD) mirror the first, which
is a
Redundant Array of Independent Disks 1 (RAID 1) configuration. You
can configure Windows to mirror the drives using the Disk Management utility
that comes with the Microsoft Windows operating system. To run the
utility, you can
open a command prompt with
administrator privileges and then type diskmgmt.msc
and hit Enter. You will then see a window showing all the drives
attached to the system. In this case, the new 10 TB drives are shown as
"unallocated", since they have not been partitioned and formatted yet.
[ More Info ]
sudo apt-get install openssh-server.sudo systemctl enable ssh --now.
If you wish to enable the service, but not start it immediately, you
can omit the --now at the end of the command, i.e., you
can use sudo systemctl enable ssh and then later issue
the command sudo systemctl start ssh to start the service.
[ More Info ]
If you wish to view information for a
package installed
on an Ubuntu Linux system,
you can use the command apt show packageName or
dpkg -s packageName where packageName is the
name of the relevant package. If you are only interested in the version number
for a package, you can
pipe the output
of either command into the grep
command.
$ apt show net-tools Package: net-tools Version: 1.60+git20181103.0eebece-1ubuntu5 Priority: optional Section: net Origin: Ubuntu Maintainer: Ubuntu Developers <ubuntu-devel-discuss@lists.ubuntu.com> Original-Maintainer: net-tools Team <team+net-tools@tracker.debian.org> Bugs: https://bugs.launchpad.net/ubuntu/+filebug Installed-Size: 819 kB Depends: libc6 (>= 2.34), libselinux1 (>= 3.1~) Homepage: http://sourceforge.net/projects/net-tools/ Task: ubuntukylin-desktop Download-Size: 204 kB APT-Manual-Installed: yes APT-Sources: http://archive.ubuntu.com/ubuntu jammy/main amd64 Packages Description: NET-3 networking toolkit This package includes the important tools for controlling the network subsystem of the Linux kernel. This includes arp, ifconfig, netstat, rarp, nameif and route. Additionally, this package contains utilities relating to particular network hardware types (plipconfig, slattach, mii-tool) and advanced aspects of IP configuration (iptunnel, ipmaddr). . In the upstream package 'hostname' and friends are included. Those are not installed by this package, since there is a special "hostname*.deb". $ apt show net-tools | grep "Version:" WARNING: apt does not have a stable CLI interface. Use with caution in scripts. Version: 1.60+git20181103.0eebece-1ubuntu5 $ dpkg -s net-tools Package: net-tools Status: install ok installed Priority: important Section: net Installed-Size: 800 Maintainer: Ubuntu Developers <ubuntu-devel-discuss@lists.ubuntu.com> Architecture: amd64 Multi-Arch: foreign Version: 1.60+git20181103.0eebece-1ubuntu5 Depends: libc6 (>= 2.34), libselinux1 (>= 3.1~) Description: NET-3 networking toolkit This package includes the important tools for controlling the network subsystem of the Linux kernel. This includes arp, ifconfig, netstat, rarp, nameif and route. Additionally, this package contains utilities relating to particular network hardware types (plipconfig, slattach, mii-tool) and advanced aspects of IP configuration (iptunnel, ipmaddr). . In the upstream package 'hostname' and friends are included. Those are not installed by this package, since there is a special "hostname*.deb". Homepage: http://sourceforge.net/projects/net-tools/ Original-Maintainer: net-tools Team <team+net-tools@tracker.debian.org> $ dpkg -s net-tools | grep "Version:" Version: 1.60+git20181103.0eebece-1ubuntu5 $
Another command that will show you the installed version of a package
on a Ubuntu systems is apt-cache policy packageName.
$ apt-cache policy net-tools
net-tools:
Installed: 1.60+git20181103.0eebece-1ubuntu5
Candidate: 1.60+git20181103.0eebece-1ubuntu5
Version table:
*** 1.60+git20181103.0eebece-1ubuntu5 500
500 http://archive.ubuntu.com/ubuntu jammy/main amd64 Packages
100 /var/lib/dpkg/status
$
Microsoft provides a capability to create
virtual machines (VMs)
within the Windows
operating system
via Hyper-V. To set up
Microsoft's Hyper-V virtualization software on a Windows 11 system
so that you can create and use virtual machines on the system, you can
type Turn Windows features in the Windows Search field
at the bottom of your screen and thn select the Control Panel option
to "Turn Windows features on or off" when it is displayed.
In the Windows Features window, scroll down until you see Hyper-V. If
you click on the plus sign next to its check box, you will see there are
two subcomponents, Hyper-V Management Tools and Hyper-V Platform.
If you check the Hyper-V check box, the two subcomponents will both be turned on. Click on OK when you are done. You will then see "Searching for required files", which should be followed by "Applying changes" and then the completion window where you will be notified that "Windows needs to reboot your PC to finish installing the requested changes." Click on the Restart now button to immediately apply the changes or you can click on Don't restart to apply them at a later reboot of the system.
[ More Info ]
[ More Info ]
If a Microsoft Windows system is running the
Microsoft Defender
Firewall,
firewall software that comes with Microsoft Windows systems, you can
check on whether connectivity is allowed on a particular
network
port from a
command-line
interface (CLI) using
PowerShell. You can determine whether the Windows Firewall is active on a
system from a command prompt
using the command netsh advfirewall show
currentprofile. If the value of "State" is "ON", then the Windows
Firewall is active on the system.
C:\>netsh advfirewall show currentprofile Domain Profile Settings: ---------------------------------------------------------------------- State ON Firewall Policy BlockInbound,AllowOutbound LocalFirewallRules N/A (GPO-store only) LocalConSecRules N/A (GPO-store only) InboundUserNotification Enable RemoteManagement Disable UnicastResponseToMulticast Enable Logging: LogAllowedConnections Disable LogDroppedConnections Disable FileName %systemroot%\system32\LogFiles\Firewall\pfirewall.log MaxFileSize 4096 Ok. C:\>
You can check on whether the firewall is permitting connectivity on a
particular network port, e.g., TCP port 3389 for the
Remote Desktop
Protocol (RDP), from a PowerShell prompt, which you can obtain by
typing powershell in the Windows "Search" field at the bottom
of the screen and then clicking on Windows PowerShell when you see
it returned by the search function. At the PowerShell prompt, you can issue
the command Get-NetFirewallPortFilter | Where-Object { $_.LocalPort -eq
3389 } | Get-NetFirewallRule. If you wished to check on whether
firewall connectivity is permitted for some other protocol, substitute
the port used by that protocol, e.g., port 22 for
Secure Shell (SSH)
connections.
[ More Info ]
When I sat down at a system running the Microsoft Windows 11 operating system on Saturday, I saw a message stating that Microsoft Paint had updated itself automatically. I had at least a dozen Paint windows open where I had posted screenshots over the past week for things I wanted to check later. I had not saved those Paint windows; I had anticipated going through them on Saturday, extracting information I wanted to keep from some images and then closing the windows and saving others. But I found the update had just closed them all without any prompt asking whether I wanted to save them and without saving the images. So I lost all the information from them irretrievably. Certainly, I should have saved the images in those Paint windows or used some other graphics application that automatically saves the contents of windows for that application or at least won't automatically update itself without saving any unsaved work, but I'm still irritated at the mindset of Microsoft developers regarding not caring about the impact to users if users have unsaved content in Microsoft applications, in addition to being irked with myself for not saving the information. I do use Paint a lot for simple graphics tasks, such as cropping and resizing screenshots, and I don't want it updating itself without warning when that may lead to a loss of information I haven't yet saved. You can determine when a Microsoft Store app was last updated and turn off automatic updates for apps obtained from the Microsoft Store, though you have to turn off the auto update feature for all apps, since there is not a way to do it only for a particular app, such as Paint.
[ More Info ]
The PowerShell cmdlet
Get-FileHash provides a
cryptographic hash function that will allow you to determine a
hash value of a file on a Microsoft Windows system. By default,
the cmdlet
uses the SHA-256 hash
function, but you can specify other functions, such as
MD5, using the
-Algorithm parameter. You can change the output to a list
format by
piping the output
of the cmdlet to Format-List.
PS C:\users\public\downloads> Get-FileHash ".\rel_x64_Xming-7-7-1-1-setup.exe" Algorithm Hash Path --------- ---- ---- SHA256 B7B4C0A191E315686A2481DCC8BBB27D6D7A156FBF689768E48CF08207B86560 C:\users\public\downloads\rel... PS C:\users\public\downloads> Get-FileHash ".\rel_x64_Xming-7-7-1-1-setup.exe" | Format-List Algorithm : SHA256 Hash : B7B4C0A191E315686A2481DCC8BBB27D6D7A156FBF689768E48CF08207B86560 Path : C:\users\public\downloads\rel_x64_Xming-7-7-1-1-setup.exe PS C:\users\public\downloads> Get-FileHash -Algorithm MD5 ".\rel_x64_Xming-7-7-1-1-setup.exe" Algorithm Hash Path --------- ---- ---- MD5 BA200636A596A84E0877901CE89D1C2E C:\users\public\downloads\rel... PS C:\users\public\downloads>
[ More Info ]
The message included the following text:
This email confirms that your subscription has been renewed for another 1 year with Norton Life-Lock for $399.00 on April 11th,2024.
This subscription will Auto-Renew every year unless you turn it OFF. No later than 24 hour before the end of the subscription period.
To cancel this subscription, Call: +1(844)962-1087
An online search of the 844-962-1087 number showed it is not a number associated with Norton LifeLock, a clear indication that the email was a scam where the scammer attempts to get people to call a number to cancel an expensive "subscription" for a well-known product or company. I assume those who call the number will be asked to provide their credit or debit card information, so someone pretending to be a customer service representative for the company can supposedly look up the account information to "cancel" the subscription. If credit card information is provided, the scammer can then use it for fraudulent charges or sell the information to others. Another indicator that a message such as this is fraudulent is poor English. E.g., "...unless you turn if OFF. No later than 24 hour before the end of the subscription period." Proper English would be "...unless you turn it OFF no later than 24 hours before the end of the subscription period." I.e., there should not be a period before "No later" and "hours" should be used rather than "hour." Another indication that the email is a fraud attempt in this case is that the sender hyphenated the product name, i.e., "Life-Lock" whereas if you go to the Norton website and look at their consumer products or visit the NortonLifeLock website, you can see that the name of the product is listed as "LifeLock" not "Life-Lock." The Wikipedia LifeLock page also shows the product name is not hyphenated. Such phishing emails purporting to be notifications of upcoming charges for NortonLifeLock have been prevalent for years — the NortonLifeLock website has a January 11, 2022 article " Keep an eye out for Norton email scams" warning people about such attempts and showing similar scam messages regarding their product.
Unfortunately, such scams can deceive enough people to make sending such messages profitable for scammers. People anxious to avoid a charge of several hundred dollars for a product they may not even be using may call the number and provide credit/debit card or banking information that the scammer may use to fraudulently charge their credit or debit card or steal money from a banking account.
If the LG TV is visible to other devices on the network, such as the PC, you should see it within "Media Devices" under "Network" in the Windows File Explorer.
If you have an MPEG-4 (.mp4) or Audio Video Interleave (.avi) file on the PC, you can right-click on video file, then choose "Show more options," and then choose "Cast to Device" at which point you should see the LG TV as a device to which you can stream the video.
[ More Info ]
For a mail server running
Sendmail email server
software, if you wish to block email from a particular "from" address to
any email address on the server, you can include the address you wish to
block in the /etc/mail/access file. E.g., if you wished to
block email from the address
spammer@example.com, you can include the following
line in that file:
# Block envelope "from" address of spammers spammer@example.com REJECT
Any line beginning with a # is treated as a comment, so the
first line above isn't needed, but adding a comment line may help you
recognize why the reject statement is in the file. After you have
added the line, you need to regenerate the
/etc/mail/access.db file, or create a new one if there isn't
already one present, using the command shown below (you don't need to
restart sendmail):
# makemap hash /etc/mail/access </etc/mail/access #
This will only work if you have a
FEATURE(`access_db')dnl line in /etc/mail/sendmail.mc.
E.g., a line like the one below:
FEATURE(`access_db', `hash -T<TMPF> -o /etc/mail/access.db')dnl
If you don't have such a line, you will need to add it. If the line begins
with dnl, you will need to remove the dnl at the
beginning of the line, since that "comments out" the line.
[ More Info ]
From a command prompt on a
Microsoft Windows system, you can obtain details on the network configuration
by issuing the command ipconfig or ipconfig /all, if
you wish to see more details. If you are only interested in a specific value or
values, though, you can
pipe the output
of the command to the findstr
command. If you wish to see multiple values, e.g., the subnet mask and the
default gateway address, you can put text associated with both values,
separated by a space, within double quotes. Findstr will treat the space
between strings as instructing it to perform a
logical OR
operation, i.e., it will find any lines that contain either of the strings.
Findstr uses a case sensitive search, so you need to either match the case of
the text or use the /i option with findstr, which instructs it to
ignore the case of text and perform a case insensitive search.
C:\>ipconfig | findstr "Mask Gateway" Subnet Mask . . . . . . . . . . . : 255.255.255.224 Default Gateway . . . . . . . . . : 192.168.1.1 C:\>ipconfig | findstr "mask gateway" C:\>ipconfig /all | findstr /i "mask gateway" Subnet Mask . . . . . . . . . . . : 255.255.255.224 Default Gateway . . . . . . . . . : 192.168.1.1 C:\>
You can also use a Windows Management Instrumentation Command-line (WMIC) command to obtain the same information.
C:\>wmic nicconfig get defaultIPGateway, IPSubnet
DefaultIPGateway IPSubnet
{"192.168.1.1"} {"255.255.255.224", "64"}
C:\>[ More Info ]
[ More Info ]
somefile.txt contains the following
ten lines:
line 1 line 2 line 3 line 4 line 5 line 6 line 7 line 8 line 9 line 10
The following Get-Content commands could be used to obtain the first 5 and the last 5 lines in the file.
PS C:\Users\Arnold\Documents> Get-Content somefile.txt -Head 5 line 1 line 2 line 3 line 4 line 5 PS C:\Users\Arnold\Documents> Get-Content somefile.txt -Tail 5 line 6 line 7 line 8 line 9 line 10 PS C:\Users\Arnold\Documents> Get-Content somefile.txt -TotalCount 5 line 1 line 2 line 3 line 4 line 5 C:\Users\Arnold\Documents>
The TotalCount parameter can function like the
Head parameter and will return the first x number of
lines specified with x being 5 in the example above. You can also
use it to obtain a specific line, though. E.g., if you wished to see the
7th line in the file, you could use the command below.
PS C:\Users\Arnold\Documents> (Get-Content Somefile.txt -TotalCount 7)[-1] line 7 PS C:\Users\Arnold\Documents>
By default the delimiter for lines is the
newline, aka end-of-line
character, \n, but you can change that with the -Delimiter
parameter.
References:
You can also find the value by checking the
Windows Registry,
which you can view or edit by using the Registry Editor program that
comes with Microsoft Windows. You can find the value by navigating to
HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Excel\Options
and checking the value for AutoRecoverTime.
[ More Info ]
Some of the documents listed may have been saved by the user without any subsequent changes being made and will have "Version created last time the user saved the file" beneath the file name as shown above.
[ More Info ]
If you want to determine the model number of an optical drive, such as
a CD or DVD drive, in a system running a Microsoft Windows operating system
from a command-line interface (CLI), you can
open a command prompt window
and issue a Windows Management
Instrumentation Command-line (WMIC) command:
wmic cdrom get name (the value for
caption may return the same information). E.g.:
C:\>wmic cdrom get name Name HL-DT-ST DVD-ROM DU90N C:\>wmic cdrom get caption Caption HL-DT-ST DVD-ROM DU90N C:\>
If you wish to determine whether media, such as a CD or DVD, is in the
drive, you can use the command wmic cdrom get medialoaded. If
there is no disc in the drive, the value for MediaLoaded will be
FALSE. If there is a disc in the drive, the value will be true
as in the example below where there is a CD in the drive.
C:\>wmic cdrom get medialoaded MediaLoaded TRUE C:\>
[ More Info ]
Sandboxie is a free and
open-source program that runs on systems using the Microsoft Windows operating system that
allows you to run other programs in a secure
sandbox.
If you wish to run programs in Sandboxie without the programs having
administrative rights, even if you are running Sandboxie from an account
that is in the system's administrator group, you can do so by editing the
Sandboxie configuration file, Sandboxie.ini. The file will usually be in the
C:\Windows folder on most systems running a Microsoft Windows
operating system. Sandboxie will first look for its configuration file
in C:\Windows, but if it doesn't find the file there, it will then
look in the Sandboxie installation folder, which will usually be
C:\Program Files\Sandboxie or
C:\Program Files\Sandboxie-Plus. When it finds an instance of
the file, it will not check other locations. There is a DropAdminRights
setting that can be used in the file. If you set the value to
y for a sandbox, then any programs running in the sandbox
will have administrative rights stripped from them, i.e,. the security
credentials used to start the sandbox won't include membership in the
Administrators and Power Users groups. If you are running Sandboxie
from an account that is not an administrator account, then the setting
won't have any effect.
[ More Info ]
If you need to determine the horizontal and vertical video resolution of the
system you are working on from a command-line interface (CLI) on a Microsoft
Windows systeem, you can open a
PowerShell window
(you can type PowerShell in the Windows "search" field and
click on PowerShell when you see it in the returned results) and
issue the
Windows Management Instrumentation Command-line (WMIC) command
Get-WmiObject win32_videocontroller | select caption, CurrentHorizontalResolution, CurrentVerticalResolution.
PS C:\> Get-WmiObject win32_videocontroller | select caption, CurrentHorizontalResolution, CurrentVerticalResolution caption CurrentHorizontalResolution CurrentVerticalResolution ------- --------------------------- ------------------------- NVIDIA Quadro K2000 2560 1440 PS C:\>
If you need to determine the resolution on another system in the same
Windows domain on
the local area network (LAN), you can add -ComputerName followed
by the name of the computer to the command as shown below.
PS C:\> Get-WmiObject -ComputerName apollo win32_videocontroller | select caption, CurrentHorizontalResolution, CurrentVerticalResolution caption CurrentHorizontalResolution CurrentVerticalResolution ------- --------------------------- ------------------------- Microsoft Basic Display Adapter 1024 768 PS C:\>
[ More Info ]
A user reported the sound from a Linux CentOS server was loud. I thought the noise was likely from a fan in the system. The lm_sensors package provides the capability to check central processing unit (CPU) temperatures and fan speeds for systems running a Linux operating system. I first checked to see if the package was installed and found it was installed.
$ rpm -qi lm_sensors Name : lm_sensors Version : 3.3.4 Release : 11.el7 Architecture: x86_64 Install Date: Sat 15 Oct 2016 12:14:14 PM EDT Group : Applications/System Size : 418761 License : LGPLv2+ and GPLv3+ and GPLv2+ and Verbatim and Public domain Signature : RSA/SHA256, Sat 14 Mar 2015 04:15:54 AM EDT, Key ID 24c6a8a7f4a80eb5 Source RPM : lm_sensors-3.3.4-11.el7.src.rpm Build Date : Thu 05 Mar 2015 10:48:12 PM EST Build Host : worker1.bsys.centos.org Relocations : (not relocatable) Packager : CentOS BuildSystem <http://bugs.centos.org> Vendor : CentOS URL : http://www.lm-sensors.org/ Summary : Hardware monitoring tools Description : The lm_sensors package includes a collection of modules for general SMBus access and hardware monitoring. $
I then ran the sensors command to view the CPU temperature and
fan speeds. The CPU and motherboard (MB) temperatures were high and
the output showed 0 RPM for the chassis fan speed, indicating either there
was no sensor monitoring its speed or it had stopped rotating.
$ sensors atk0110-acpi-0 Adapter: ACPI interface Vcore Voltage: +1.28 V (min = +0.85 V, max = +1.60 V) +3.3 Voltage: +3.36 V (min = +2.97 V, max = +3.63 V) +5 Voltage: +5.17 V (min = +4.50 V, max = +5.50 V) +12 Voltage: +12.41 V (min = +10.20 V, max = +13.80 V) CPU FAN Speed: 2518 RPM (min = 0 RPM, max = 7200 RPM) CHASSIS FAN Speed: 0 RPM (min = 800 RPM, max = 7200 RPM) CPU Temperature: +79.5°C (high = +60.0°C, crit = +95.0°C) MB Temperature: +61.0°C (high = +45.0°C, crit = +95.0°C) $
References:
Scroll down to the bottom of that message where you will find a Sign-in button, then click on it to sign into a Microsoft account.
You will then have an opportunity to describe the image you would like to create using Cocreator.
[ More Info ]
SSLCertificateFile
and SSLCertificateChainFile lines in the Apache configuration file,
/etc/httpd/conf/httpd.conf, I saw they were pointing to the
following .pem files (.pem stands for
"Privacy-Enhanced
Mail" and a .pem file holds a security certificate).
SSLCertificateFile /etc/letsencrypt/live/support.moonpoint.com-0001/cert.pem
SSLCertificateKeyFile /etc/letsencrypt/live/support.moonpoint.com-0001/privkey.pem
Include /etc/letsencrypt/options-ssl-apache.conf
SSLCertificateChainFile /etc/letsencrypt/live/support.moonpoint.com-0001/chain.pem
When I checked the expiration of that security certificate, I saw it was valid until May 17.
# openssl x509 -enddate -noout -in /etc/letsencrypt/live/support.moonpoint.com-0001/cert.pem notAfter=May 17 04:02:51 2024 GMT #
You can determine the location of the .pem file used by Dovecot by
looking for the ssl_cert variable in
/etc/dovecot/conf.d/10-ssl.conf.
[ More Info ]
When you first run the program, you will see a My Devices window displaying the Western Digital drives the software has found, both USB-attached and internal disk drives. Other storage media will be shown under Other Devices.
Click on the Western Digital drive you wish to check on to see details on that drive including disk space used, disk space available, and disk space capacity as well as the interface speed, drive temperature, health, and performance information.
[ More Info ]
The Disk Management utility that comes with Microsoft Windows operating
systems can be used to view details of drives and partitions in the system
and attached to the system via
USB. To start the utility,
you can type diskmgmt.msc in the Windows search field, which you
can access by clicking on the magnifying glass icon at the bottom of the screen
on a Windows 11 system or by typing diskmgmt.msc in the
Type here to search field on a Windows 10 system. To use the utility,
you must run it as an administrator, so if you are not logged into an
administrator account, you need to right-click on the utility when you see it
returned in the search results and choose "Run as administrator".
[ More Info ]
Many—but not all—live-streamed programs are recorded. We understand it's not always possible to watch a program in real time, and as a courtesy to ticket buyers we are glad to make recordings available within 24 hours after the program has taken place. The recordings can be viewed for up to three days (72 hours) after they become available.
SmithSonian Associates has stated that they don't have sufficient storage space to make the recordings permanently available. If you can't watch the recording within the 3 days it will be available or want to have a permanent copy available for future reference, you can take the steps listed below to download an MP4 file of the recorded presentation.
If you click on the Watch button from your Encores page on the Smithsonian Associates website, you will be taken to a Zoom webpage. You can watch the video from that page, but if you right-click on the video, you will not see any option to save it. So you need to install a browser extension that will enable right-clicks to work on pages where they have been disabled.
Note: the instructions below are specifically for the Brave browser on a Microsoft Windows system, but the procedure for other browsers is likely to be similar.
[ More Info ]
<table width="100%">.
In HTML 5, using width in
that way has been deprecated in favor of putting the width within a style
designation. If you use <table width="100%"> in an HTML 5
webpage and check the page with the W3C
HTML validation tool, you will see the message
" Error The width attribute
on the table element is obsolete. Use CSS instead." You can use the following,
instead:
<table style="width: 100%;">
The same is true for specification of the width of <td>
table elements. Under HTML 4, the following was ok:
<td width="33%" align="left">
In the above HTML code, the cell width could be specified as 33% of the
table width and text in a cell could be left-aligned with
align="left". Under HTML 5, though, both specifications are
considered obsolete and the following should be used, instead:
<td style="width:33%; text-align:left;">
If you need to center the text, you can use text-align:center,
instead. If you wish to vertically align an element in a table cell, such
as text or an image, in HTML 4 you could use the following:
<td valign="top">March 12</td>
In HTML 5, you can use the following instead of the above deprecated use of valign:
<td style="vertical-align: top;">March 12</td>
[ More Info ]
You can obtain information on the
Central
Processing Unit (CPU) in a system
running a Microsoft Windows
operating system
(OS) using
Windows Management Instrumentation Command-line (WMIC) commands. To
see the value of all parameters,
open a command prompt window
and issue the command wmic /namespace:\\root\cimv2 path win32_processor
get /format:list (using the /format option, you can see the information
in a more readable fashion).
C:\>wmic /namespace:\\root\cimv2 path win32_processor get /format:list AddressWidth=64 Architecture=9 AssetTag=UNKNOWN Availability=3 Caption=Intel64 Family 6 Model 85 Stepping 4 Characteristics=252 ConfigManagerErrorCode= ConfigManagerUserConfig= CpuStatus=1 CreationClassName=Win32_Processor CurrentClockSpeed=2195 CurrentVoltage=16 DataWidth=64 Description=Intel64 Family 6 Model 85 Stepping 4 DeviceID=CPU0 ErrorCleared= ErrorDescription= ExtClock=100 Family=179 InstallDate= L2CacheSize=14336 L2CacheSpeed= L3CacheSize=19712 L3CacheSpeed=0 LastErrorCode= Level=6 LoadPercentage=3 Manufacturer=GenuineIntel MaxClockSpeed=2195 Name=Intel(R) Xeon(R) Gold 5120 CPU @ 2.20GHz NumberOfCores=14 NumberOfEnabledCore=14 NumberOfLogicalProcessors=28 OtherFamilyDescription= PartNumber= PNPDeviceID= PowerManagementCapabilities= PowerManagementSupported=FALSE ProcessorId=BFEBFBFF00050654 ProcessorType=3 Revision=21764 Role=CPU SecondLevelAddressTranslationExtensions=TRUE SerialNumber= SocketDesignation=CPU0 Status=OK StatusInfo=3 Stepping= SystemCreationClassName=Win32_ComputerSystem SystemName=MUNICH ThreadCount=28 UniqueId= UpgradeMethod=1 Version= VirtualizationFirmwareEnabled=TRUE VMMonitorModeExtensions=TRUE VoltageCaps= C:\>
[ More Info ]
I checked the status of drives attached to the system by opening a command prompt window and issuing a Windows Management Instrumentation Command-line (WMIC) command, but the results indicated all of the drives were OK.
C:\>wmic diskdrive get status, size, model Model Size Status DELL PERC S150 SCSI Disk Device 999642954240 OK WD Elements SE 2622 USB Device 1000169372160 OK PNY USB 2.0 FD USB Device 62018611200 OK C:>
[ More Info ]
You can still access the results of a scan in such cases, though, because when
you exit from viewing the scan results, the program automatically appends the
results to C:\ProgramData\.clamwin\log\ClamScanLog.txt. The
ProgamData directory is a hidden directory that you won't see in the
Windows File Explorer
unless you have configured it to display hidden files and folders. You
can see the directory is present if you
open a command prompt window
and issue the command dir /ah — the "/ah" tells the
dir command to display files and folders with the attribute "hidden."
E.g.:
C:\>dir /ah
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\
08/21/2022 07:38 PM <DIR> $Recycle.Bin
07/08/2017 03:45 PM <DIR> $Windows.~WS
02/14/2024 10:43 AM <DIR> $WinREAgent
10/30/2015 02:18 AM 1 BOOTNXT
08/21/2022 01:01 PM 112 bootTel.dat
02/28/2024 03:54 PM <DIR> Config.Msi
11/04/2011 01:20 AM 30,425 dell.sdr
07/14/2009 12:08 AM <JUNCTION> Documents and Settings [C:\Users]
03/03/2024 11:51 PM 8,192 DumpStack.log.tmp
03/04/2024 03:51 PM 6,373,736,448 hiberfil.sys
01/30/2012 09:36 PM <DIR> MSOCache
03/03/2024 11:51 PM 8,589,934,592 pagefile.sys
03/03/2024 09:48 AM <DIR> ProgramData
10/11/2023 09:00 AM <DIR> Recovery
03/03/2024 11:51 PM 268,435,456 swapfile.sys
01/28/2012 08:26 PM <DIR> System Recovery
03/04/2024 08:00 PM <DIR> System Volume Information
7 File(s) 15,232,145,226 bytes
10 Dir(s) 795,701,448,704 bytes free
C:\>>Though the log file containing scan results is beneath a hidden directory,
you can access it from a text editor such as
Windows Notepad
by typing in the directory path and file name, i.e.,
C:\ProgramData\.clamwin\log\ClamScanLog.txt when you choose
Open to open a file, or you could open it from a command prompt
window as shown below.
C:\&>notepad C:\ProgramData\.clamwin\log\ClamScanLog.txt C:\&>
The ClamScanLog.txt file will contain the results of all scans run on the system, unless it was edited to remove prior results, with the results of the latest scan at the bottom of the file.
HKEY_CURRENT_USER\SOFTWARE\SimonTatham\PuTTY\Sessions.
If you want to view the SSH tunnels configured for a particular host, i.e.,
the port forwarding
settings for that host, you can navigate to
HKEY_CURRENT_USER\SOFTWARE\SimonTatham\PuTTY\Sessions\SessionName\PortForwardings
where SessionName is the name you have given to the session
associated with the host. E.g., suppose you regularly establish an
SSH
connection to www.example.com and have named a session for that site
MySite. You could navigate to
HKEY_CURRENT_USER\SOFTWARE\SimonTatham\PuTTY\Sessions\MySite\PortForwardings
to find the port forwardings settings. If you had named the session
My Site, there would be a %20 in the session name
stored in the registry as %20 is an HTML representation for the
space character. You can doubleclick on the PortForwardings key
in the right pane of the registry window to see the values stored in the key.
You might see something like the following:
L22011=192.168.0.11:22,L33018=192.168.0.18:33018
[ More Info ]