

|
| ||||||||||||||||||||||||||||||||||||||||||||||||||
As one of the commenters on the article by Mr. Perez noted, many people who see Google Street View images as a significant privacy issue may ignore far more serious privacy issues, such as warrantless wiretapping.
You can see where Street View is available in the U.S. at http://maps.google.com/help/maps/streetview/.
I had problems with the dsiplay of an HP tc4400 laptop, which was running Windows XP Professional Service Pack 3, after updating the video driver. When I right-clicked on the desktop and selected Properties, then Settings, I found the screen resolution was 640x480. The color quality was "Lowest (4 bit)", i.e. only 16 colors. I couldn't increase either setting. I clicked on the Advanced button and then the Adapter tab. When I clicked on List All Modes, the only options were those shown below:
List of valid modes
640 by 480, 16 Colors, Default Refresh
800 by 600, 16 Colors, Default Refresh
I changed the setting to 800x600 to make it a little better. I didn't get any error messages, but the resolution remained at 800 x 600.
Under the Display adapters setting of the Device Manager, I found two adapters listed:
Mobile Intel(R) 945 Express Chipset Family
Mobile Intel(R) 945 Express Chipset Family
The names were exactly the same, as were the drivers:
| Entry | Driver Provider | Driver Date | Diver Version |
|---|---|---|---|
| 1 | Intel Corporation | 8/24/2007 | 6.14.10.4864 |
| 2 | Intel Corporation | 8/24/2007 | 6.14.10.4864 |
I right-clicked on the second one and chose Uninstall. Whem prompted to restart the system, I did so.
When the system rebooted, I saw the following error message:
| hkcmd.exe - Unable to Locate Component |
|
This application has failed to start because hccutils.DLL was not found.
Re-installing the application may fix this problem.
|
The system notified me it had found a new video adapter and suggested I reboot again, which I did.
The resolution was still at 640 x 480, but when I checked the video adapters listed in the Device Manager, I saw the following:
Mobile Intel(R) 945GM Express Chipset Family
Mobile Intel(R) 945GM Express Chipset Family
Though the names and drivers differed from what I had seen previously, the names of the two entries were exactly the same, as were the drivers for them:
| Entry | Driver Provider | Driver Date | Diver Version |
|---|---|---|---|
| 1 | Intel Corporation | 3/23/2006 | 6.14.10.4543 |
| 2 | Intel Corporation | 3/23/2006 | 6.14.10.4543 |
I right-clicked on the bottom entry and chose "uninstall". I again had to restart the computer. But, when I logged in again, I found both entries listed in the Device Manager again. I removed both of them by right-clicking on them and choosing "uninstall". I then rebooted again. This time I had a 640 x 480 resultion again, but the color quality was "Highest (32 bit)". I was able to change the resolution to 800 x 600 by right-clicking on the desktop and choosing Settings.
Shortly afterwards I saw the "Found New Hardware" balloon pop up with "Mobile Intel(R) 945GM Express Chipset Family" listed as the new hardware found. I saw the message "Windows has finished installing new devices. The software that supports your device requires that you restart your computer. You must restart your computer before the new settings will take effect. Do you want to restart your compute now?" I chose "yes."
When the system rebooted, it was back to the 640 x 480 resolution. When I checked the Device Manager, I saw the "Mobile Intel(R) 945GM Express Chipset Family" listed twice again with the March 23, 2006 driver listed for both again. I again uninstalled both adapters from within the Device Manager and then rebooted. I had 32-bit color and 800 x 600 resolution when I logged in. When I right-clicked on the desktop, chose Properties, Settings, Advanced, then Adapter, I didn't see an adapter listed under Adapter Type. Clicking on Properties showed VGASave under the General tab. CLicking on the Driver tab showed the following:
Service name: VGASave
Display name: VGA Display Controller
But again I was notified of a "System Settings CHange" with the message that "Windows has finished installing new devices..." I chose not to restart the system immediately. I checked what the Device Manager was showing. It showed the same duplicated "Mobile Intel(R) 945GM Express Chipset Family" entries as before with both having the Intel March 23, 2006 driver associated with them. But the top entry had an exclamation mark in a yellow circle next to it. I right-clicked on that one and chose "disable" rather than "uninstall" this time. I then rebooted.
After rebooting, I had the 800 x 600 resolution and 32-bit color. The Device Manager still showed the duplicated Display Adapters with the same March 23, 2006 Intel driver for both, but there was a red "X" next to the top entry. Right-clicking on the Desktop and choosing Properties, Settings, Advanced, Adapter showed nothing listed under Adapter Type and the following for Adapter Information
| Chip Type: | <unavailable> |
| DAC Type: | <unavailable> |
| Memory Size: | <unavailable> |
| Adapter String: | <unavailable> |
| Bios Information: | <unavailable> |
I changed the resolution to 1024 x 768 and rebooted again, just to make sure the settings would remain and the problem wouldn't recur. The problem did not recur.
References:
42odhr0b.exe, which it found in a
user's Local Settings\Temp folder was infected with the virus
Trojan.Dropper.Small-8.
I submitted the file, which has an MD5 hash of 93d2546e58042ebe7f5ae26ec0ec50b3, to VirusTotal, a free service "that analyzes suspicious files and facilitates the quick detection of viruses, worms, trojans, and all kinds of malware detected by antivirus engines." It reported the file was first received on 10.07.2006 22:08:05 (CET). I had it reanalyze the file. VirusTotal reported that 91.18%, i.e. 31 of 34, of the antimalware programs with which it scanned the file identified the file as being malware (see VirusTotal report)
I also submitted the file to VirSCAN.org, "a FREE on-line scan service, which checks uploaded files for malware", using multiple antivirus engines. On uploading files you want to be checked, you can see the result of scanning and how dangerous and harmful/harmless for your computer those files are. VirSCAN reported that 76%, i.e. 28 of 37, of the antimalware programs it used reported the file as being malware (see VirSCAN report).
I also submitted the file to Jotti's Online Malware Scan, another free malware scanning site, for analysis. On that site, 18 of the 19 antivirus programs it used detected the file as malware (see Jotti report).
ThreatExpert, "an advanced automated threat analysis system designed to analyze and report the behavior of computer viruses, worms, trojans, adware, spyware, and other security-related risks in a fully automated mode" identified the file as being associated with Spyware.FavoriteMan (see ThreatExpert report).
ThreatExpert provided the following information on Spyware.FavoriteMan:
FavoriteMan is a Browser Helper Object, which connects to its controlling servers to download and install other programs and add entries to your Internet Explorer favorites menu or computer desktop. This program has been known to download at least 28 different adware or spyware programs. Some controlling servers are www.f1organizer.com, www.prize4all.com, www.yourspecialoffers.com and www.r-vision.org.
ThreatExpert indicated that the file creates the following files on the system:
%System%\ATPartners.dll
%System%\im64.dll
I had found ATPartners.dll on the system on February 27 of 2005
when I had scanned the system with other antimalware software. I had removed
ATPartners.dll at that time. Apparently
42odhr0b.exe was left in the user's local settings\temp
folder from that time. Checking my notes for information on
FavoriteMan, I found I had encountered it on other systems, e.g.
a Windows 98 system on March 28, 2004 (see
Windows 98 System
Hanging After Login) and a Windows 98 Second Edition system on April 25 of
2005 (see
Calsdr.Dll Remnant).
Download a zipped copy of 42odhr0b.exe for analysis or testing antimalware software (use zoo as userid and malware as password). Note: You do so at your own risk; this file can infect a system, so only run the program on a test system.
23010852235.exe, which
has an MD5 hash of
9ec78aac59b04643bfb43415c6fa2909,
in a user's Local Settings\Temp directory.
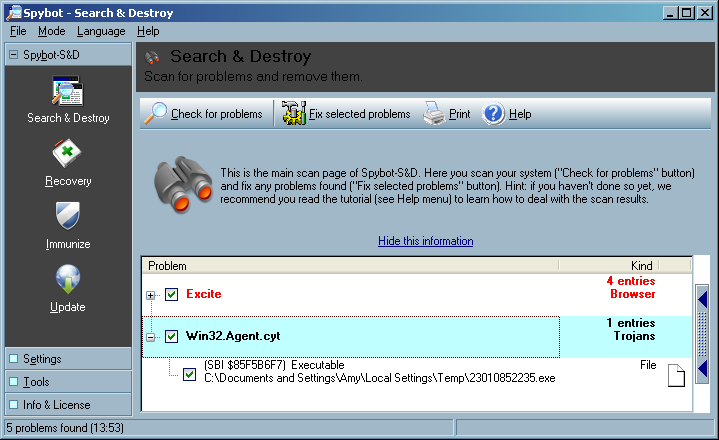
I uploaded the file to VirusTotal, a free online virus and malware scan website for analysis. Twenty-four of the 39 malware scan programs with which it scanned the file reported it contained malware (see VirusTotal report).
I also uploaded the file to VirSCAN.org, another multi-engine virus scanner site. It reported "The file are 23010852235.exe uploaded by other users and scanned successfully at 2008/01/18 20:48:04". I had it rescan the file. It reported that 49%, i.e. 18 of 37, of the malware detection programs that it used, identified the file as containing malware (see VirSCAN report).
File Name: 23010852235.exe File Size: 3072 File Type: PE32 executable for MS Windows (GUI) Intel 80386 32-bit MD5: 9ec78aac59b04643bfb43415c6fa2909 SHA1: 546e2d9c76fad865ac56b89fa54a864d564f1c16 Compressed: NA
Prevx, a security company that makes
software that "identifies malicious code by its 'behavior'" lists
SYSNSAD.EXE as being an alias for a file with this MD5 hash
(see Prevx report).
The Prevx report states the following:
A file with the name SYSNSAD.EXE have been seen to have the following Vendor, Product and Version Information in the file header:
Microsoft Corporation; File Compare Utility; 5.1.2600.0
Microsoft Corporation; File Compare Utility; 5.1.2600.0 (xpclient.010817-1148)
When I examined the file with Filealyzer , I saw the following version information:
| File version | 5.1.2600.0 (xpclient.010817-1148) |
| Company name | Microsoft Corporation |
| Internal name | Comp |
| Comments | |
| Legal copyright | ©Microsoft Corporation. All rights reserved. |
| Legal trademarks | |
| Original filename | Comp.Exe |
| Product name | Microsoft® Windows® Operating System |
| Product version | 5.1.2600.0 |
| File description | File Compare Utility |
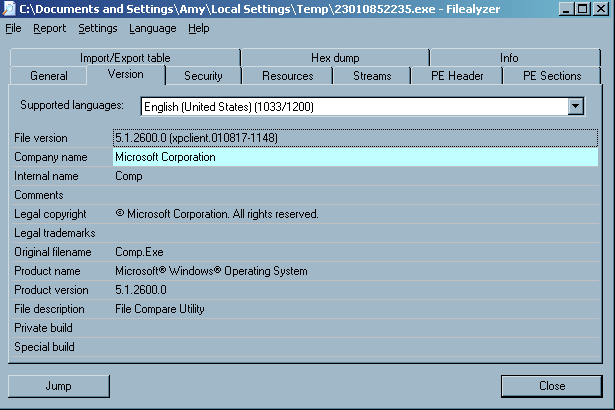
The version information was likely inserted by the malware author to try to disguise the file as an innocuous Microsoft-provided operating system file.
I had Spybot fix the problem, i.e. delete the file.
Download
23010852235.exe for analysis or testing antimalware software
(use zoo as userid and malware as password).
Note: You do so at your own risk; this file can infect a system, so only run
the program on a test system.
$NT*KB* directories showed the following:
C:\TEMP>dir /ah \Windows\$NT*KB*
Volume in drive C is Sys-WinXP
Volume Serial Number is B0E3-65A7
Directory of C:\Windows
01/21/2005 02:34 PM <DIR> $NtUninstallKB828741$
01/21/2005 02:38 PM <DIR> $NtUninstallKB833987$
01/21/2005 07:37 PM <DIR> $NtUninstallKB834707$
01/21/2005 02:36 PM <DIR> $NtUninstallKB835732$
01/21/2005 02:36 PM <DIR> $NtUninstallKB840987$
01/21/2005 02:36 PM <DIR> $NtUninstallKB841356$
01/21/2005 02:37 PM <DIR> $NtUninstallKB841533$
01/21/2005 01:21 PM <DIR> $NtUninstallKB842773$
02/12/2005 07:59 PM <DIR> $NtUninstallKB867282$
01/21/2005 02:38 PM <DIR> $NtUninstallKB871250$
02/12/2005 07:59 PM <DIR> $NtUninstallKB873333$
01/21/2005 05:13 PM <DIR> $NtUninstallKB873339$
01/21/2005 02:37 PM <DIR> $NtUninstallKB873339_0$
01/21/2005 02:37 PM <DIR> $NtUninstallKB873376$
02/12/2005 07:59 PM <DIR> $NtUninstallKB885250$
01/21/2005 05:13 PM <DIR> $NtUninstallKB885835$
01/21/2005 02:37 PM <DIR> $NtUninstallKB885835_0$
01/21/2005 05:13 PM <DIR> $NtUninstallKB885836$
01/21/2005 02:38 PM <DIR> $NtUninstallKB885836_0$
01/21/2005 07:37 PM <DIR> $NtUninstallKB886185$
02/12/2005 07:59 PM <DIR> $NtUninstallKB887472$
02/22/2005 07:22 PM <DIR> $NtUninstallKB887742$
01/21/2005 07:37 PM <DIR> $NtUninstallKB887797$
02/12/2005 07:59 PM <DIR> $NtUninstallKB888113$
02/12/2005 07:58 PM <DIR> $NtUninstallKB888302$
01/21/2005 02:37 PM <DIR> $NtUninstallKB889293-IE6SP1-20041111.2356
19$
01/07/2006 11:46 AM <DIR> $NtUninstallKB890046$
09/02/2005 03:39 PM <DIR> $NtUninstallKB890046_0$
02/12/2005 07:58 PM <DIR> $NtUninstallKB890047$
01/21/2005 05:13 PM <DIR> $NtUninstallKB890175$
01/21/2005 02:38 PM <DIR> $NtUninstallKB890175_0$
05/14/2005 07:07 PM <DIR> $NtUninstallKB890859$
05/14/2005 07:08 PM <DIR> $NtUninstallKB890923$
01/21/2005 02:38 PM <DIR> $NtUninstallKB891711$
02/12/2005 07:59 PM <DIR> $NtUninstallKB891781$
05/14/2005 07:08 PM <DIR> $NtUninstallKB893066$
05/14/2005 07:08 PM <DIR> $NtUninstallKB893086$
09/02/2005 03:40 PM <DIR> $NtUninstallKB893756$
09/02/2005 03:39 PM <DIR> $NtUninstallKB894391$
01/07/2006 11:46 AM <DIR> $NtUninstallKB896344$
09/02/2005 03:39 PM <DIR> $NtUninstallKB896358$
09/02/2005 03:40 PM <DIR> $NtUninstallKB896422$
09/02/2005 03:40 PM <DIR> $NtUninstallKB896423$
01/07/2006 11:48 AM <DIR> $NtUninstallKB896424$
09/02/2005 03:39 PM <DIR> $NtUninstallKB896428$
10/23/2005 10:05 AM <DIR> $NtUninstallKB896688$
09/02/2005 03:39 PM <DIR> $NtUninstallKB896727$
09/02/2005 03:28 PM <DIR> $NtUninstallKB898461$
09/02/2005 03:40 PM <DIR> $NtUninstallKB899587$
09/02/2005 03:39 PM <DIR> $NtUninstallKB899588$
10/23/2005 10:05 AM <DIR> $NtUninstallKB899589$
09/02/2005 03:40 PM <DIR> $NtUninstallKB899591$
08/13/2006 09:32 PM <DIR> $NtUninstallKB900485$
10/23/2005 10:05 AM <DIR> $NtUninstallKB900725$
01/07/2006 11:46 AM <DIR> $NtUninstallKB900930$
10/23/2005 10:06 AM <DIR> $NtUninstallKB901017$
09/02/2005 03:39 PM <DIR> $NtUninstallKB901214$
03/22/2006 07:55 PM <DIR> $NtUninstallKB902344$
10/23/2005 10:05 AM <DIR> $NtUninstallKB902400$
10/23/2005 10:04 AM <DIR> $NtUninstallKB904706$
03/22/2006 07:57 PM <DIR> $NtUninstallKB904942$
10/23/2005 10:05 AM <DIR> $NtUninstallKB905414$
10/23/2005 10:04 AM <DIR> $NtUninstallKB905749$
01/07/2006 11:53 AM <DIR> $NtUninstallKB905915$
01/12/2006 10:58 PM <DIR> $NtUninstallKB908519$
08/13/2006 09:29 PM <DIR> $NtUninstallKB908531$
01/07/2006 11:49 AM <DIR> $NtUninstallKB910437$
08/13/2006 09:35 PM <DIR> $NtUninstallKB911280$
08/13/2006 09:32 PM <DIR> $NtUninstallKB911562$
03/22/2006 07:56 PM <DIR> $NtUninstallKB911564$
03/22/2006 07:55 PM <DIR> $NtUninstallKB911565$
08/13/2006 09:29 PM <DIR> $NtUninstallKB911567$
03/22/2006 07:55 PM <DIR> $NtUninstallKB911927$
03/22/2006 07:57 PM <DIR> $NtUninstallKB912475$
01/07/2006 11:53 AM <DIR> $NtUninstallKB912919$
03/22/2006 07:57 PM <DIR> $NtUninstallKB912945$
03/22/2006 07:56 PM <DIR> $NtUninstallKB913446$
08/13/2006 09:29 PM <DIR> $NtUninstallKB913580$
08/13/2006 09:30 PM <DIR> $NtUninstallKB914388$
08/13/2006 09:29 PM <DIR> $NtUninstallKB914389$
04/20/2007 10:10 AM <DIR> $NtUninstallKB914440$
04/20/2007 10:11 AM <DIR> $NtUninstallKB915865$
08/13/2006 09:29 PM <DIR> $NtUninstallKB916595$
08/13/2006 09:32 PM <DIR> $NtUninstallKB917159$
08/13/2006 09:30 PM <DIR> $NtUninstallKB917344$
08/13/2006 09:30 PM <DIR> $NtUninstallKB917422$
08/13/2006 09:36 PM <DIR> $NtUninstallKB917734_WMP10$
08/13/2006 09:30 PM <DIR> $NtUninstallKB917953$
03/21/2007 10:32 AM <DIR> $NtUninstallKB918118$
08/13/2006 09:30 PM <DIR> $NtUninstallKB918439$
08/13/2006 09:30 PM <DIR> $NtUninstallKB918899$
09/15/2006 07:32 PM <DIR> $NtUninstallKB919007$
01/12/2007 02:35 PM <DIR> $NtUninstallKB920213$
08/13/2006 09:35 PM <DIR> $NtUninstallKB920214$
04/20/2007 09:53 AM <DIR> $NtUninstallKB920342$
08/13/2006 09:30 PM <DIR> $NtUninstallKB920670$
08/13/2006 09:29 PM <DIR> $NtUninstallKB920683$
09/15/2006 07:32 PM <DIR> $NtUninstallKB920685$
09/15/2006 07:32 PM <DIR> $NtUninstallKB920872$
08/13/2006 09:31 PM <DIR> $NtUninstallKB921398$
12/29/2007 08:03 PM <DIR> $NtUninstallKB921503$
08/13/2006 09:35 PM <DIR> $NtUninstallKB921883$
09/15/2006 07:32 PM <DIR> $NtUninstallKB922582$
08/13/2006 09:35 PM <DIR> $NtUninstallKB922616$
10/16/2006 09:54 AM <DIR> $NtUninstallKB922819$
10/16/2006 09:51 AM <DIR> $NtUninstallKB923191$
10/16/2006 09:54 AM <DIR> $NtUninstallKB923414$
01/12/2007 02:36 PM <DIR> $NtUninstallKB923689$
01/12/2007 02:35 PM <DIR> $NtUninstallKB923694$
01/12/2007 02:37 PM <DIR> $NtUninstallKB923980$
10/16/2006 09:54 AM <DIR> $NtUninstallKB924191$
01/12/2007 02:37 PM <DIR> $NtUninstallKB924270$
10/16/2006 09:53 AM <DIR> $NtUninstallKB924496$
03/21/2007 10:34 AM <DIR> $NtUninstallKB924667$
01/12/2007 02:37 PM <DIR> $NtUninstallKB925398_WMP64$
01/12/2007 02:38 PM <DIR> $NtUninstallKB925454$
10/07/2006 01:29 PM <DIR> $NtUninstallKB925486$
04/20/2007 07:47 PM <DIR> $NtUninstallKB925720$
04/20/2007 09:54 AM <DIR> $NtUninstallKB925876$
04/20/2007 09:36 AM <DIR> $NtUninstallKB925902$
04/20/2007 09:59 AM <DIR> $NtUninstallKB926239$
01/12/2007 02:35 PM <DIR> $NtUninstallKB926255$
03/21/2007 10:33 AM <DIR> $NtUninstallKB926436$
03/21/2007 10:34 AM <DIR> $NtUninstallKB927779$
03/21/2007 10:34 AM <DIR> $NtUninstallKB927802$
05/31/2007 11:08 PM <DIR> $NtUninstallKB927891$
03/21/2007 10:32 AM <DIR> $NtUninstallKB928090$
03/21/2007 10:34 AM <DIR> $NtUninstallKB928255$
03/21/2007 10:31 AM <DIR> $NtUninstallKB928843$
12/29/2007 08:00 PM <DIR> $NtUninstallKB929123$
03/21/2007 10:33 AM <DIR> $NtUninstallKB929338$
04/20/2007 07:45 PM <DIR> $NtUninstallKB929399$
01/12/2007 02:37 PM <DIR> $NtUninstallKB929969$
04/20/2007 09:36 AM <DIR> $NtUninstallKB930178$
05/12/2007 03:04 PM <DIR> $NtUninstallKB930916$
04/20/2007 09:36 AM <DIR> $NtUninstallKB931261$
04/20/2007 09:37 AM <DIR> $NtUninstallKB931784$
03/21/2007 10:33 AM <DIR> $NtUninstallKB931836$
04/20/2007 09:35 AM <DIR> $NtUninstallKB932168$
09/17/2008 11:37 AM <DIR> $NtUninstallKB932823-v3$
12/29/2007 08:03 PM <DIR> $NtUninstallKB933729$
12/29/2007 07:54 PM <DIR> $NtUninstallKB935839$
12/29/2007 07:54 PM <DIR> $NtUninstallKB935840$
12/29/2007 08:03 PM <DIR> $NtUninstallKB936021$
12/29/2007 08:03 PM <DIR> $NtUninstallKB936357$
12/29/2007 07:53 PM <DIR> $NtUninstallKB936782_WMP11$
12/29/2007 08:04 PM <DIR> $NtUninstallKB937894$
09/17/2008 11:37 AM <DIR> $NtUninstallKB938464$
12/29/2007 08:03 PM <DIR> $NtUninstallKB938828$
12/29/2007 08:03 PM <DIR> $NtUninstallKB938829$
12/29/2007 07:55 PM <DIR> $NtUninstallKB939683$
12/29/2007 07:55 PM <DIR> $NtUninstallKB941202$
12/29/2007 07:55 PM <DIR> $NtUninstallKB941568$
12/29/2007 07:59 PM <DIR> $NtUninstallKB941569$
01/15/2008 07:12 PM <DIR> $NtUninstallKB941644$
12/29/2007 07:59 PM <DIR> $NtUninstallKB942763$
12/29/2007 08:04 PM <DIR> $NtUninstallKB943460$
01/15/2008 07:12 PM <DIR> $NtUninstallKB943485$
12/29/2007 07:53 PM <DIR> $NtUninstallKB944653$
09/17/2008 11:44 AM <DIR> $NtUninstallKB946648$
09/17/2008 11:37 AM <DIR> $NtUninstallKB950749$
09/17/2008 11:40 AM <DIR> $NtUninstallKB950762$
09/17/2008 11:41 AM <DIR> $NtUninstallKB950974$
09/17/2008 11:39 AM <DIR> $NtUninstallKB951066$
09/17/2008 11:40 AM <DIR> $NtUninstallKB951072-v2$
09/17/2008 11:45 AM <DIR> $NtUninstallKB951376-v2$
09/17/2008 11:41 AM <DIR> $NtUninstallKB951698$
09/17/2008 11:38 AM <DIR> $NtUninstallKB951748$
12/18/2008 10:16 PM <DIR> $NtUninstallKB952069_WM9$
09/17/2008 11:40 AM <DIR> $NtUninstallKB952287$
09/17/2008 11:44 AM <DIR> $NtUninstallKB952954$
09/17/2008 11:44 AM <DIR> $NtUninstallKB953839$
09/17/2008 11:37 AM <DIR> $NtUninstallKB954154_WM11$
09/17/2008 11:41 AM <DIR> $NtUninstallKB954156_WM9L$
11/08/2008 10:42 AM <DIR> $NtUninstallKB954211$
12/18/2008 10:12 PM <DIR> $NtUninstallKB954600$
11/21/2008 11:23 AM <DIR> $NtUninstallKB955069$
12/18/2008 10:15 PM <DIR> $NtUninstallKB955839$
11/08/2008 10:43 AM <DIR> $NtUninstallKB956391$
12/18/2008 10:12 PM <DIR> $NtUninstallKB956802$
11/08/2008 10:43 AM <DIR> $NtUninstallKB956803$
11/08/2008 10:41 AM <DIR> $NtUninstallKB956841$
11/08/2008 10:43 AM <DIR> $NtUninstallKB957095$
11/21/2008 11:24 AM <DIR> $NtUninstallKB957097$
11/08/2008 10:40 AM <DIR> $NtUninstallKB958644$
02/14/2009 10:34 AM <DIR> $NtUninstallKB958687$
02/14/2009 10:34 AM <DIR> $NtUninstallKB960715$
0 File(s) 0 bytes
187 Dir(s) 46,294,913,024 bytes free
After I ran Remove Hotfix Backups, Windows Explorer
reported "Free space: 46,308,824 bytes 43.1 GB" and checking for
$NT*KB* directories showed the following:
C:\TEMP>dir /ah \Windows\$NT*KB*
Volume in drive C is Sys-WinXP
Volume Serial Number is B0E3-65A7
Directory of C:\Windows
01/21/2005 02:34 PM <DIR> $NtUninstallKB828741$
01/21/2005 02:38 PM <DIR> $NtUninstallKB833987$
01/21/2005 02:36 PM <DIR> $NtUninstallKB835732$
01/21/2005 02:36 PM <DIR> $NtUninstallKB840987$
01/21/2005 02:36 PM <DIR> $NtUninstallKB841356$
01/21/2005 02:37 PM <DIR> $NtUninstallKB841533$
01/21/2005 01:21 PM <DIR> $NtUninstallKB842773$
01/21/2005 02:38 PM <DIR> $NtUninstallKB871250$
01/21/2005 02:37 PM <DIR> $NtUninstallKB873339_0$
01/21/2005 02:37 PM <DIR> $NtUninstallKB873376$
01/21/2005 02:37 PM <DIR> $NtUninstallKB885835_0$
01/21/2005 02:38 PM <DIR> $NtUninstallKB885836_0$
01/21/2005 02:37 PM <DIR> $NtUninstallKB889293-IE6SP1-20041111.2356
19$
09/02/2005 03:39 PM <DIR> $NtUninstallKB890046_0$
01/21/2005 02:38 PM <DIR> $NtUninstallKB890175_0$
01/21/2005 02:38 PM <DIR> $NtUninstallKB891711$
08/13/2006 09:36 PM <DIR> $NtUninstallKB917734_WMP10$
01/12/2007 02:37 PM <DIR> $NtUninstallKB925398_WMP64$
09/17/2008 11:37 AM <DIR> $NtUninstallKB932823-v3$
12/29/2007 07:53 PM <DIR> $NtUninstallKB936782_WMP11$
09/17/2008 11:40 AM <DIR> $NtUninstallKB951072-v2$
09/17/2008 11:45 AM <DIR> $NtUninstallKB951376-v2$
12/18/2008 10:16 PM <DIR> $NtUninstallKB952069_WM9$
09/17/2008 11:37 AM <DIR> $NtUninstallKB954154_WM11$
09/17/2008 11:41 AM <DIR> $NtUninstallKB954156_WM9L$
0 File(s) 0 bytes
25 Dir(s) 46,308,941,824 bytes freeI also removed the $NTServicePackUninstal directory under
C:\Windows, which was using 338 MB (355,138,581 bytes) of disk
space and holding 2,457 files, by holding down the Shift key to
ensure the folder wouldn't go into the Recycle Bin, but, instead
would be permanently removed, selected Delete. When asked to confirm
the deletion of an exe file I chose "Yes to All" to avoid further prompts for
the removal of executable files in the directory.
References:
C:\WINDOWS\Downloaded Program Files. You can view
the information through Windows Explorer, or if you want to view
information on what is in that folder from the command line, you can use
show-downloaded-program-files.vbs, which you can run from the command
line with cscript /nologo show-downloaded-program-files.vbs.
[ More Info ]
[ More Info ]
I created a script, bios-info.vbs from the code provided on Microsoft's webpage that will retrieve the information from the BIOS.
I have the Toshiba Power Management Utility configured on the system to sound an alarm and display a message when the battery charges drops to 10%. I have it configured to sound an alarm, display a message, and hibernate when the charge drops to 5%. But it never takes those actions. Instead, the laptop just powers off.
So that I could at least have some forwarning of when the battery charge is getting very low, I installed Laptop Battery Power Monitor, which places a battery widget on the desktop which displays the battery's charge level and which appears above other windows.
When you run the downloaded file, setup.exe, by default, it will
attempt to extract the files stored within itself to
c:\Temp\BatteryMonitor2006. If there is no c:\Temp
directory, you will receive the message below:
| WinZip Self-Extractor |
 Could not
create "c:\Temp\BatteryMonitor2006" - unzip operation cancelled. Could not
create "c:\Temp\BatteryMonitor2006" - unzip operation cancelled.
|
In that case, choose another directory into which the files will be extracted. The software requires 6,992 KB of free space on the disk on which it will be installed.
The installation process creates a program group named Duomart.com. Within it you will find a Laptop Battery Power Monitor group. When you run the progam it will place a battery widget on your desktop showing the battery charge level.
That widget will remain over top of windows that you open. Moving the mouse pointer over it will display information about the state of the battery. If you right-click on it, you can change the size of the battery displayed. You also have the option to adjust its transparency or close the program.
The software can be downloaded from the developer website, which is a source for purchasing computer accessories, bluetooth devices, or laptop batteries. Other sources for the software are listed below.
Download Sites
DuoMart
MoonPoint Support
FileBuzz
Wallpaper
in the registry key
HKCU\Software\Microsoft\Windows\CurrentVersion\Themes\LastTheme.
I can do so using the reg query command.
C:\>reg query HKCU\Software\Microsoft\Windows\CurrentVersion\Themes\LastTheme /v
Wallpaper
! REG.EXE VERSION 3.0
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\LastTheme
Wallpaper REG_EXPAND_SZ %SystemRoot%\Web\Wallpaper\Ripple.jpg
From a batch file, though, I only want the filename, i.e.
%SystemRoot%\Web\Wallpaper\Ripple.jpg.
I can select just that part of the output usng the
FOR /F command in a batch
file. The syntax of the FOR /F command is as follows:
FOR /F ["options"] %%parameter IN ('command_to_process') DO command
Key
options:
delims=xxx The delimiter character(s)
(default = a space)
skip=n A number of lines to skip at the beginning.
(default = 0)
eol=; Character at the start of each line to indicate a comment
The default is a semicolon ; Use "eol=" to process all lines
tokens=n Specifies which numbered items to
read from each line
(default = 1)
usebackq Specify `back quotes`
the command_to_process is placed in `BACK quotes`
instead of 'straight' quotes
command_to_process : The output of the 'command_to_process' is
passed into the FOR parameter.
command : The command to carry out, including any
command-line parameters.
%%parameter : A replaceable parameter:
in a batch file use %%G (on the command line %G)
FOR /F processing of a command consists of reading the output from
the command one line at a time and then breaking the line up into individual
items of data or 'tokens'. The DO command is then executed with the
parameter(s) set to the token(s) found.
By default, /F breaks up the command output at each blank space, and any blank lines are skipped. You can override this default parsing behavior by specifying the "options" parameter. The options must be contained within double quotes.
In this case, the last line of output is the following:
Wallpaper REG_EXPAND_SZ %SystemRoot%\Web\Wallpaper\Ripple.jpgThe delimiter between the fields in the output is the tab character
(I checked for whether the delimiter was spaces or tabs with
hod
by redirecting the output of the reg query command to a file with
reg query
HKCU\Software\Microsoft\Windows\CurrentVersion\Themes\LastTheme /v Wallpaper
> temp.txt).
For the FOR /F command, the default delimiter is the space and
tab characters so I don't have to specify delims=. But, if
I don't, the output will be incorrect in cases where the path name or
file name contain spaces, since the second space will be treated as
a demarcation point, so that the space-separated parts of the path name or file
name are treated as separate tokens.
"Tokens" are the parts of the line separated by the delimiter. In this case,
I'm only interested in the third token, i.e.
%SystemRoot%\Web\Wallpaper\Ripple.jpg,
so I can use the following lines in a batch file:
FOR /F "tokens=3" %%R in ('reg query HKCU\Software\Microsoft\Windows\CurrentVersion\Themes\LastTheme /v Wallpaper') DO SET wallpaper=%%R
echo %wallpaper%I used the tokens=3 option to select just the third
token on the output line. The %%R for the parameter name
is arbitrary. I could have called it %%S, %%T, etc.,
instead, if I wished. The command I wished to process is enclosed
between '( and )'. Note: for the reg
query command, if the registry key contains spaces in the key name,
then you must enclose the registry key name within double quotes as in the
following batch file example:
@echo off
FOR /F "tokens=3" %%R in ('reg query "HKCU\Control Panel\Desktop" /v ConvertedWallpaper') DO SET wallpaper_file=%%R
echo %wallpaper_file%
The output produced by the batch file is shown below:
C:\WINDOWS\Web\Wallpaper\Ripple.jpg
But, if I checked the value for OriginalWallper in the
registry key
HKCU\Control Panel\Desktop with reg query as below,
I would see a path name containing spaces.
C:\>reg query "HKCU\Control Panel\Desktop" /v OriginalWallpaper
! REG.EXE VERSION 3.0
HKEY_CURRENT_USER\Control Panel\Desktop
OriginalWallpaper REG_SZ C:\Documents and Settings\James\Local Settings\A
pplication Data\Microsoft\Wallpaper1.bmpIf I don't specify delims= in the batch file, e.g., if I use
the code below, I would get incorrect output.
@echo off
FOR /F "tokens=3" %%R in ('reg query "HKCU\Control Panel\Desktop" /v OriginalWallpaper') DO SET wallpaper_file=%%R
echo %wallpaper_file%
The output would be as shown below:
C:\Documents
That is because C:\Documents will be treated as one token
and then the space between Documents and and Settings
is treated as the demarcation point between two tokens. But, if I instead
include delims= and immediately hit the tab key, that
problem won't occur, since the the horizontal tab character between the fields
will be used to break up the line into tokens.
@echo off
FOR /F "delims= tokens=3" %%R in ('reg query "HKCU\Control Panel\Desktop" /v OriginalWallpaper') DO SET
wallpaper_file=%%R
echo %wallpaper_file%
You can't see any character after the delims=, but in order
for the FOR /F command to work in this case, I had to
type delims= and then hit the tab key while editing the file
in Windows Notepad. If you then save the file, it will produce the correct
output, e.g.:
C:\Documents and Settings\James\Local Settings\Application Data\Microsoft\Wallpaper1.bmp
Note: if you are using Vim as your editor
on a Windows system, as I usually do, then you need to insert the tab character
after delims= by hitting the Ctrl-I keys simultaneously.
You can then hit the spacebar and type tokens=. If you just
hit the tab key, your output won't be as you expect.
Wallpaper-info.bat is an example batch file to query the values in
the Windows registry pertaining to the file used for the Windows wallpaper
using the FOR /F command.
References:
hod.exe from
the zip file
available on the author's website.
If you just type hod file the contents of file will be displayed
in both hexadecimal and
ASCII.
C:\>"C:\Program Files\Utilities\hod.exe" temp.txt
0 1 2 3 4 5 6 7 8 9 a b c d e f 0123456789abcdef
0: 0d 0a 21 20 52 45 47 2e 45 58 45 20 56 45 52 53 ..! REG.EXE VERS
10: 49 4f 4e 20 33 2e 30 0d 0a 0d 0a 48 4b 45 59 5f ION 3.0....HKEY_
20: 43 55 52 52 45 4e 54 5f 55 53 45 52 5c 53 6f 66 CURRENT_USER\Sof
30: 74 77 61 72 65 5c 4d 69 63 72 6f 73 6f 66 74 5c tware\Microsoft\
40: 57 69 6e 64 6f 77 73 5c 43 75 72 72 65 6e 74 56 Windows\CurrentV
50: 65 72 73 69 6f 6e 5c 54 68 65 6d 65 73 5c 4c 61 ersion\Themes\La
60: 73 74 54 68 65 6d 65 0d 0a 20 20 20 20 57 61 6c stTheme.. Wal
70: 6c 70 61 70 65 72 09 52 45 47 5f 45 58 50 41 4e lpaper.REG_EXPAN
80: 44 5f 53 5a 09 25 53 79 73 74 65 6d 52 6f 6f 74 D_SZ.%SystemRoot
90: 25 5c 57 65 62 5c 57 61 6c 6c 70 61 70 65 72 5c %\Web\Wallpaper\
a0: 52 69 70 70 6c 65 2e 6a 70 67 0d 0a 0d 0a Ripple.jpg....
For help on using the program, use the -h option.
C:\>"C:\Program Files\Utilities\hod.exe" -h usage: C:\Program Files\Utilities\File\Analysis\hod.exe [options] <filename> Where the options are: -v : show version information -h : show this help -o : dump in octal -8 : show as block of 8 bytes -x str : convert a hex input to decimal -d : show offsets in decimal -s : show identical output lines -r : reverse hod hexdump to binary -w : reverse regular hex bytes to binary If no filename specified, it will read from stdin Example: $ hod file $ hod < file $ cat file | hod $ cat file | hod - $ hod < file $ hod -o file $ echo "hello" | hod $ echo -n "hello" | hod $ hod -x 1c0 1c0 : 448 $ echo "0a 01 ff ef 0b" | hod -w > bin.bin $ hod bin.bin | hod -r > bin_again.bin
Note: -r and -w works with hexadecimal only.
If you want to convert an ASCII string, such as the word hello,
to its hexadecimal equivalent, you can use the echo command to
pipe the word to hod, as below.
C:\>echo hello | "C:\Program Files\Utilities\hod.exe"
0 1 2 3 4 5 6 7 8 9 a b c d e f 0123456789abcdef
0: 68 65 6c 6c 6f 20 0a hello .
From the above output, you can see that the letters in hello
have the following hexadecimal equivalent representation.
| ASCII | Hex | Note |
|---|---|---|
| h | 68 | |
| e | 65 | |
| l | 6c | |
| l | 6c | |
| o | 6f | |
| SP | 20 | space |
| LF | 0a | line feed |
A space (hex 20) is listed after hello, since there was a space
between the word and the | pipe operator that feeds the output of
the echo command to hod. If I had placed the
| immediately after hello, i.e.
echo hello|, it wouldn't have been listed. A line feed (hex 0a) is
shown after the space.
Download hod
Author's
website
If you are using Microsoft Windows, such as Windows XP, you can
extract a substring from a variable string using character positional
notation, i.e. %myvar:~char_skip_num%. I.e., where you have
some variable, e.g. %myvar%, you can place the
:~ operator prior to the ending % and then specify
a the number of characters to skip followed by the ending %.
E.g. from a command line if you checked the value of a user profile variable,
i.e. %userprofile%, for a user named James, you might see the
following:
C:\>echo %userprofile% C:\Documents and Settings\James
If I wanted to extract just the user's account name, i.e. James,
I could use the following:
C:\>echo %userprofile:~26% James
The "J" in James is the 27th character,
so I used 26 to have the first 26 characters skipped.
You can also specify that you only want to extract a certain number of characters by putting a comma after the number of characters to be skipped followed by the number of characters to extract. E.g, if I only wanted to extract the first 3 characters starting at position 27, I could use the following:
C:\>echo %userprofile:~26,3% Jam
If you don't want to skip any characters, but specify only a certain number
of characters to extract, you can use the syntax %myvar:~0,x
where you specify that zero characters are to be skipped and x
represents the number of characters to extract from the string.
C:\>echo %userprofile:~0,3% C:\
You can also specify that you want to start the extraction from the end of
the line rather than the beginning by using -x, where
x is some number, for the starting position. E.g. you could
use the following to extract the last 3 characters from the line:
C:\>echo %userprofile:~-3% mes
You can specify the number of characters to extract, just as noted before, with this method as well. E.g. to extract the substring that starts at 3 characters from the end of the string, but only includes 2 characters from that point, the following could be used:
C:\>echo %userprofile:~-3,2% me
If you are using a batch file, e.g. substring-extract-example.bat,
you could display just the desired part of the string as follows:
@echo off
echo %userprofile:~-3,2%
When the batch file is executed, it wold display just "me"
C:\>substr-extract-example me
For further examples, see Variables: extract part of a variable (substring)
References:
I came across the site by accident while doing a search on a company name. The site revealed that the president of the company had made a campaign contribution to George W. Bush in 2004. I tried a search on my zip code and the site returned a list of people in my zip code who had made contributions to either the Democratic or Republican party and the amount donated.
The site states the following:
All calculations are based on public records filed with the FEC of contributions by all individuals totaling more than $200 (and some totaling less than $200) to a single Republican or Democratic presidential campaign or national committee for the 2004 and 2008 election cycles.
FundRace is updated according to the reporting schedule set by the FEC. Public contribution data is geocoded using public U.S. Census Bureau data. Dynamic maps are powered by Google Maps.
powercfg.cpl. Note: if you aren't logged
into an administrator account when you run it, you can
run it with administrator privileges by obtaining a command
prompt and then taking the following steps:
runas /user:administrator cmd to obtain a command
prompt under the administrator account. Note: you may have to use
owner or some other account in the administrator group,
depending on your particular system, instead of the administrator
account.powercfg.cpl in the new command prompt window that
opens for the administrator account.runas /user:administrator powercfg.cpl. If you try that,
you will get the message " powercfg.cpl is not a valid Win32 application."
For a list of of Control Panel tools and how to run them from the command line, see How to run Control Panel tools by typing a command.
Because I also hear the fan making a fair amount of noise at times, I thought I would install a utility to monitor the fan speed and CPU temperature. I used SpeedFan 4.37, but found that the laptop's motherboard doesn't support such monitoring. The temperature of the hard drive in the laptop can be monitored, though. I see it varies between 34 and 37 degrees Celsius.
logbooks
directory beneath the installation directory, e.g.
C:\Program Files\ELOG\logbooks. To
do so, I took the following steps:
elogd.cfg, which is stored in the ELOG
installation directory, e.g. C:\Program Files\ELOG\elogd.cfg,
with Notepad from an administrator account.global section add a Logbook dir =
<directory> line where <directory> is
the directory where you wish to have the logbooks stored. Note:
don't use quotes around directory names, even if there are spaces
in the names of directories in the path to the logbook directory. E.g.:
[global]
port = 8080
logbook dir = C:\Documents and Settings\James\My Documents\ELOG\logbookselogd.cfg for the
logbook. Put the name of the logbook between "[" and "]" and then
add the relevant lines for that particular logbook. E.g.:
[sysadmin]
Theme = default
Comment = System Administration
Attributes = Author, Type, Category, Subject
Options Type = Configuration, Malware Scan, Patches, Problem, Problem Fixed, Routine, Software Installation, Upgrade, Other
Options Category = General, Hardware, Software, Network, Security, Other
Options Author = John Smith
Required Attributes = Authorelogd.cfg.C:\>net stop elogd The elogd service is stopping. The elogd service was stopped successfully. C:\>net start elogd The elogd service is starting. The elogd service was started successfully.
somedoc.txt there
will be a somedoc.txt.swp in the same directory from which
I can recover the document should the system crash. In this case, though,
I didn't think I could recover the document, since I had never saved it
with a file name. So I didn't know where a .swp file would
have been stored and was doubtful there was one.
But after powering the laptop back on and logging into
the same account again, I opened Vim, hit the Esc key and typed
:recover. Lo and behold there was my work exactly as it was
when I went to eat dinner, saving me a lot of time I would otherwise have
been forced to spend recreating the document. I immediately saved it to a file.
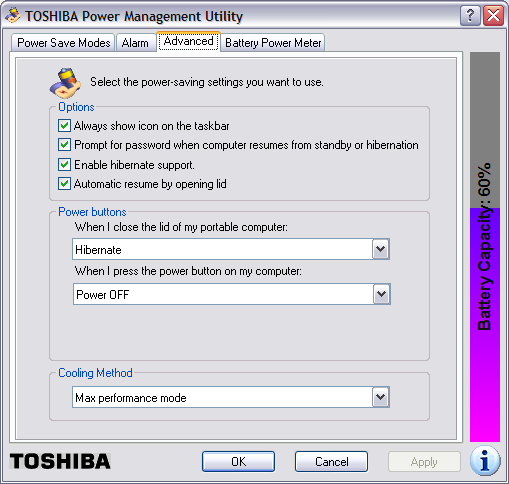
Note: in order to enable hibernate support, you will
need enough free space on the hard drive to hold
the contents of the system's memory. You can determine
the amount of memory in the system by clicking on
Start, selecting Run, typing
winver and hitting Enter.
In the window that then opens, you will see
a value for "Physical memory available to Windows".
You will need that amount of disk space free on the
hard drive, because the contents of memory are written
to the file hiberfil.sys, usually in
c:\hiberfil.sys when the system is put
into hibernation mode. If you don't have at least that amount
of disk space free, you won't be able to enable hibernation
support.
Once hibernation support is enabled, you can put the system into hibernation by clicking on Start, selecting Turn Off Computer, moving the mouse pointer over Stand By, and then hitting the Shift key. The Stand By option should then change to Hibernate, which you can click on to hibernate the computer.