Sat, Jul 30, 2016 10:39 pm
BitDefender Free Antispam for Mail Servers (FRAMS) with Sendmail
I have been using several
email blacklists on a CentOS 7 server where I use
Sendmail
to handle email. The blacklists, aka blocklists, I've been employing are
DNS-based
Blackhole Lists (DNSBLs). A DNSBL is a list of
IP addresses
known to be associated with the transmission of spam. The ones I've
been using are listed below:
I configured Sendmail to use those blacklists by putting the following lines
in /etc/mail/sendmail.mc:
FEATURE(`blacklist_recipients')dnl
FEATURE(`dnsbl', `sbl.spamhaus.org', `550 Spam Block: mail from $&{client_addr} refused - See http://www.spamhaus.org/sbl/')dnl
FEATURE(`dnsbl', `psbl.surriel.com', `550 Spam Block: mail from $&{client_addr} refused - see http://psbl.surriel.com/')dnl
FEATURE(`dnsbl',`dnsbl.sorbs.net',`550 Spam Block: mail from $&{client_addr} refused - see http://dnsbl.sorbs.net/')dnl
FEATURE(`dnsbl',`dnsrbl.swinog.ch',`550 Spam Block: mail from $&{client_addr} refused - see http://antispam.imp.ch/spamikaze/remove.php')dnl
FEATURE(`enhdnsbl', `bl.spamcop.net', `"Spam blocked see: http://spamcop.net/bl.shtml?"$&{client_addr}', `t')dnlIf you add those lines to the Sendmail configuration file, you need to
regenerate /etc/mail/sendmail.cf with the command m4
/etc/mail/sendmail.mc > /etc/mail/sendmail.cf. Then restart sendmail
with service sendmail restart.
Still, despite those multiple anti-spam blacklists, a lot of spam is getting
through to accounts on the mail server. So I decided to install
Free Antispam for Mail Servers (FRAMS)
from Bitdefender,
which describes the software thusly:
Bitdefender Free Antispam for Mail Servers provides essential features
for increased productivity in any organization by blocking spam on
Linux-based mail servers. Bitdefender's award winning antispam engines
provide antiphishing, content and attachment filtering. It's extremely
easy to install and administrators have an easy to use web-based interface
and powerful command line management.
[ More Info ]
[/network/email/sendmail]
permanent link
Fri, Jul 29, 2016 11:56 pm
Windows 7 Image Backup to Network Location
The deadline Microsoft has given for its free upgrade of Windows 7 and 8
to Windows 10 is 5:59 AM EDT Saturday July 30, 2016. When I checked with the
owner of a couple of Windows 7 systems on whether she wished me to upload
the systems prior to the deadline, she said "Yes." I wanted to have
current backups for the systems, so I backed them up using the built-in
backup program Microsoft provides with the Windows 7 operating system - see
Windows 7 Image Backup to Network Location
on the steps to start and configure that software. I found that there
was only a few megabytes of disk space still available on the USB-attached
backup device for one of the systems and I wanted to retain the earlier backups
on that device, so I decided to backup the system over the network, instead.
That backup was much slower than I would have liked it to have been over the
100 Mbs LAN. The steps to perform a Windows 7 backup to a network location
are listed
here.
[/os/windows/win7]
permanent link
Fri, Jul 29, 2016 4:51 pm
Another app is currently holding the yum lock
After resolving a problem with network connectivity on a
CentOS 7 Linux
server, I attempted to install a package using
yum, but received the message "Another app is currently
holding the yum lock; waiting for it to exit..."
# yum install rdesktop
Loaded plugins: fastestmirror, langpacks
Existing lock /var/run/yum.pid: another copy is running as pid 16020.
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:14 ago
State : Running, pid: 16020
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:16 ago
State : Sleeping, pid: 16020
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:18 ago
State : Sleeping, pid: 16020
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:20 ago
State : Sleeping, pid: 16020
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:22 ago
State : Sleeping, pid: 16020
Another app is currently holding the yum lock; waiting for it to exit...
The other application is: PackageKit
Memory : 46 M RSS (1.4 GB VSZ)
Started: Fri Jul 29 12:08:28 2016 - 01:24 ago
State : Sleeping, pid: 16020
^C
Exiting on user cancel.
#I checked the process and saw the following information:
# ps aux | grep yum
root 16020 28.4 2.3 1455028 79512 ? SN 12:08 1:16 /usr/bin/python /usr/share/PackageKit/helpers/yum/yumBackend.py refresh-cache yes
root 16354 0.0 0.0 112652 952 pts/0 S+ 12:12 0:00 grep --color=auto yum
#
[ More Info ]
[/os/unix/linux/utilities/package]
permanent link
Tue, Jul 26, 2016 9:57 pm
Taking a screenshot with GIMP
If you need to take an image of a window or an area on the screen on a
Linux system, one of the options available is to use the
GNU Image
Manipulation Program, which is a
free and
open-source graphics editor that is also available for
FreeBSD,
Mac OS X, Microsoft Windows, and
Solaris systems.
You can determine if the application is already installed using the
which command.
If it isn't installed, on systems that use the
yum package management tool, such as
CentOS, you
can use the command yum install gimp from the root
account to install it. On Linux distributions that use the
Advanced
Packaging Tool (APT) for package management, e.g.,
Ubuntu, you can use sudo apt-get install gimp.
To take a snapshot of a window or an area of the screen, take the following
steps:
- Click on File.
- Click on Create.
- Select Screenshot.
-
You can then select from the following:
- Take a screenshot of a single window
- Take a screenshot of the entire screen
- Select a region to grab
[ More Info ]
[/software/graphics/gimp]
permanent link
Mon, Jul 25, 2016 10:22 pm
Checking sendmail mail delivery from the command line
A user reported problems with email deliveries this morning, but when I
checked the outgoing mail queue with the
mailq command on
the CentOS 7 server running
sendmail, the queue was empty.
# mailq
/var/spool/mqueue is empty
Total requests: 0
#
I tried sending a test message from the mail sever to an
external email account with the mailx command. For the body of the message, I put some text into a file
named test.txt and used the < character to
provide the contents of the
file as input to mailx for the body of the message. I didn't receive
any error message and I didn't see any messages stuck in the mail queue
when I checked it after I sent the message. But the message was not received
at the destination email account.
# mailx -s "Testing" moonpoint@example.com <test.txt
# mailq
/var/spool/mqueue is empty
Total requests: 0
#
So I then used the
sendmail command, instead, to send a test message to see if it would provide
me with any information that I could use for troubleshooting the problem. I
created a file with the following contents to send as a test message.
# cat temp.txt
Subject: Sendmail test
This is a test.
This is only a test.
You can send a test message whose contents are contained in a text file
from a command line interface using a
sendmail command in
the form sendmail recipient_email_address <
input_file. But when I did that, I saw a "Connection
refused by [127.0.0.1]" message.
[ More Info ]
[/network/email/sendmail]
permanent link
Sun, Jul 24, 2016 6:33 pm
HTML attributes obsoleted by HTML5
There are quite a few
HTML attributes made obsolete in
HTML5,
which is the current
HTML standard. I've been trying to make new web pages
on my site compliant with version 5 of the standard and transitioning some
created using HTML 4.1 to HTML5, so I've had to modify the HTML code to use
other tags or eliminate the use of attributes that have been deprecated with
HTML5. Some of the
elements
and attributes that have been deprecated are listed below:
-
cellpadding attribute
-
frameborder attribute on the iframe element
-
scrolling
attribute on the iframe element
-
name attribute
-
valign attribute
-
tt element
[/network/web/html/css]
permanent link
Sat, Jul 23, 2016 6:09 pm
Adding Evernote add-on to Firefox on Linux
Evernote
Corporation, which produces the Evernote note-taking application,
unfortunately, doesn't provide an application for Linux as it does for
Microsoft Windows and OS X, but you can use Evernote from within a browser,
such as Firefox. To install Evernote support from within Firefox, take
the steps listed
here.
[/network/web/browser/firefox]
permanent link
Fri, Jul 22, 2016 5:56 pm
Troubleshooting POP3S connections through a NetScreen firewall
A user reported that she was unable to receive email using her Outlook email
client. When I checked her system, I found that Outlook 2016 was reporting
the following error message:
Task 'nell@example.com - Receiving' reported error (0x80042108): 'Outlook
cannot connect to your incoming (POP3) email server. If you continue to receive
this message, contact your server administrator or Internet service provider
(ISP).'
I verified that I could connect to the email server on the
SMTP port, port 25, and the
POP3
port, port 110, from external systems and she told me that
her husband's system was able to check his email successfully. Since I knew
his system was establishing a POP3 connection to the mail server to check
email, but her system was establishing an encrypted POP3S connection
on port 995, I checked the Linux email server to verify that it was
listening for connections on port 995, since there had been a power
outage at its location recently that I thought might have caused it to
reboot. It was listening on that port.
$ netstat -a | grep -i pop3s
tcp 0 0 0.0.0.0:pop3s 0.0.0.0:* LISTEN
tcp6 0 0 [::]:pop3s [::]:* LISTEN
So I thought the problem was likely at a NetScreen firewall between the
user and the server. I logged into the firewall via
Secure Shell (SSH).
I verified that there were no filters currently set for the firewall and
then set a filter for destination port 995 with the command
set ffilter dst-port 995. I then cleared the debug buffer with
clear db and started debugging on the router/firewall with
debug flow basic - see
NetScreen Debugging
Commands for an explanation of the debugging commands. I could see
that TCP packets were reaching the firewall, but the firewall
was reporting "packet dropped: for self but not interested".
[ More Info ]
[/security/firewalls/netscreen]
permanent link
Thu, Jul 21, 2016 10:54 pm
Restoring a disk drive from an image backup on an OS X system
I needed to restore an external USB-connected Toshiba disk drive from
an image created with Disk Utility
on a MacBook Pro running the OS X operating system. With the external disk
drive attached, a
diskutil command,
diskutil list, showed the following:
$ diskutil list
/dev/disk0
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *500.3 GB disk0
1: EFI EFI 209.7 MB disk0s1
2: Apple_HFS Macintosh HD 499.4 GB disk0s2
3: Apple_Boot Recovery HD 650.0 MB disk0s3
/dev/disk2
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *13.8 MB disk2
1: Apple_HFS C_PGP2FV_B_A0 13.8 MB disk2s1
/dev/disk3
#: TYPE NAME SIZE IDENTIFIER
0: GUID_partition_scheme *500.1 GB disk3
1: EFI EFI 209.7 MB disk3s1
2: Apple_HFS TOSHIBA EXT 499.8 GB disk3s2
3: Apple_Boot Boot OS X 134.2 MB disk3s3
$
[ More Info ]
[/os/os-x]
permanent link
Wed, Jul 20, 2016 10:51 pm
OS X ncal command
If you wish to generate a calendar on an Apple system running the
OS X operating
system at a
command line interface (CLI), e.g., within a
terminal
window, you can use the
ncal command to display a calendar. If you enter the command
with no parameters, it will display a calendar for the current month
$ ncal
July 2016
Mo 4 11 18 25
Tu 5 12 19 26
We 6 13 20 27
Th 7 14 21 28
Fr 1 8 15 22 29
Sa 2 9 16 23 30
Su 3 10 17 24 31If you wish to display the calendar for another month, you can specify
the month on the command line by putting the month and year after the
command. E.g., to display a calendar for February of 20216, the command
below could be used. The command ncal february 2016 would
also work.
$ ncal 2 2016
February 2016
Mo 1 8 15 22 29
Tu 2 9 16 23
We 3 10 17 24
Th 4 11 18 25
Fr 5 12 19 26
Sa 6 13 20 27
Su 7 14 21 28[ More Info ]
[/os/os-x]
permanent link
Tue, Jul 19, 2016 11:57 am
OS X pgrep command
You can use the OS X
pgrep
command to list all of the process IDs for an application, such
as Safari.
$ pgrep Safari
51313
78209
95848
95874
If you wish to see the newest, i.e., the most recently started
one, of those processes, you can use the -n option.
You can use the -l option to viewer longer information on
the processes, i.e, process names as well as PIDs.
$ pgrep -l Safari
51313 Safari
78209 SafariNotificat
95848 com.apple.Safar
95874 com.apple.Safar
If you combine the -l option with the -f option,
you will see even more information for the process that may be helpful when
the process name is truncated.
$ pgrep -lfn Safari
95874 /System/Library/PrivateFrameworks/SafariServices.framework/Versions/A/XPCS
ervices/com.apple.SafariServices.xpc/Contents/MacOS/com.apple.SafariServices
[/os/os-x]
permanent link
Mon, Jul 18, 2016 10:45 pm
Making an image of a disk drive using Disk Utility
To create an image backup of an external disk drive using the OS X
Disk
Utility found in the
Applications/Utilities folder, take the
following steps after attaching the drive to the Apple computer.
-
Open Disk Utility, from the Applications/Utilities
directory.
-
Click on the external disk drive in the left pane of the utility to select it.
-
Click on File, then select New and Disk Image from, e.g.
Disk Image from "TOSHIBA EXT" for an external Toshiba USB drive.
-
You will then be prompted to give the image a name and can select the
directory where you wish it to be stored. You can also select whether the
image will be compressed and whether it will be encrypted.
-
Click on Save to initiate the creation of the disk image. When prompted
that "diskimages-helper wants to make changes. Type your password to allow
this.", provide a password for an account with administrator privileges on the
system. When the image has been created, you will see it listed in the
left pane of the Disk Utility window.
You can then use the OS X
Finder program to view the files stored in the
Apple Disk Image DMG file that was created by double-clicking on
the .dmg file that was created.
[ More Info ]
[/os/os-x]
permanent link
Sat, Jul 16, 2016 10:16 pm
Windows Technical Department Scam
My wife received a call at 1:02 PM Eastern Time today from someone with an
Indian accent claiming he was from the "Windows Technical Department" calling
because they noticed that our "computer is infected with some harmful viruses."
The call was obviously a scam, but I picked up the phone and played along for
several minutes to see what the person would try to do. He had
me open the Windows
Event Viewer and suggested that the entries I saw in
the Application log indicated the system was infected with viruses. There
will normally be a plethora of entries in the log associated with the normal
functioning of a Microsoft Windows system, but I can undestand
how such con artists might be able to scare someone who has never
looked at such log entries before into thinking they were evidence of
something being terribly wrong with his/her system. When I asked him
what percentage of people he called fell for the scam, he insisted it
wasn't a scam. When I asked him if he was calling from outside of the
U.S. and so felt immune from prosecution in the U.S., he hung up. When
I used *69 to get the calling number I found it was 315-825-8947.
When I tried calling the number, I heard a recorded message stating
"The person you are trying to reach is not accepting calls at this time.
Please try your call again later."
When I then searched online for that number, I found others reporting
receiving similar scam calls from that number, e.g., at the 800Notes page at
315-825-8947
I found reports such as "They called me 4 times. I finally picked up
on the last time and it was a woman with an Indian accent claiming to
be from Windows Tech Support and I immediately hung up. This is a scam."
Fifty minutes later, my wife received a similar call again at 1:52 PM
from someone with an Indian accent. She informed the caller that she knew
it was a scam and asked to be removed from the calling list. I used
*69 again and this time I was informed that the caling number was
315-639-8222. I found that number also listed at the 800Notes site at
315-639-8222.
When I tried calling that number I heard a message that "The number you
have reached has been disconnected or is no longer in service."
We received two more "Windows Technical Departement" calls within a
couple of hours. We were watching a series on Netflix during that period
and I didn't try to check those two calling numbers with *69.
I think it was the second call where I again picked up the phone and talked
to the caller who again had an Indian accent - my wife told me all four
seemed to have an Indian accent. I asked where he was calling from and he
told me New York. I asked him what company he worked for; he said "Windows
Technical Department". I asked him if he knew what company produces Windows.
He didn't answer, but attempted to continue with his spiel telling me where
to click with the mouse. I tried to see if he knew anything except the spiel
he had been given, but this caller wanted to stick with the spiel telling me
where to click, though he eventually hung up when I told him to hold on for
a minute while I went to another phone, where I was going to record our
conversation.
My wife gets very annoyed by such calls; she's usually the one picking
up the phone for our home phone number, which is a
VoIP
service from our cable provider. I haven't received such scam calls on
my cell phone number, though I do get a fair number of unwanted telemarketing
calls on that number,
often from
spoofed numbers. My wife said she frequently gets the Windows scam calls
when I'm not home. A few months ago,
I received a call on our
home number from another scammer pretending to be from the IRS.
Our phone numbers are on the U.S. Federal Trade Commission (FTC)
Do Not Call
list, but, of course, scammers, and many telemarketers as well, don't bother
checking that list.
Coincidentally, today I read an article on the Ars Technica site titled
Mobile carriers aren’t doing enough to fight robocalls, senators say. I
wasn't pleased by the following paragraph in that article:
AT&T CEO Randall Stephenson recently
claimed
that AT&T doesn't have the "authority" to implement new robocall blocking
technology in its mobile network, even though the Federal Communications
Commission
clearly stated last year that carriers have the "green light"
to offer robocall-blocking services to consumers.
[/security/scams]
permanent link
Fri, Jul 15, 2016 11:02 pm
Using the eject command on CentOS
To eject a CD/DVD tray on a CentOS 7 system, you can use the
eject
command. With no arguments given to the command on the command line,
i.e., a shell prompt, the tray will be ejected. To retract the tray,
you can use
eject --trayclose or
-t. You can
use
-T or
--traytoggle to open the drive,
if it is closed or close it, if it is open.
If you specify the -n or
--noop option, information on the device will be shown, but no
action is taken.
$ eject -n
eject: device is `/dev/sr0'
You can use eject --default to see the default name for the
device.
$ eject --default
eject: default device: `/dev/cdrom'
[ More Info ]
[/os/unix/linux/centos]
permanent link
Thu, Jul 14, 2016 10:53 pm
Time since last reboot on an OS X system
If you want to know how long a Mac OS X system has been running since the
last reboot, you can use the
uptime command, which can be run from a command line interface available
from a
Terminal window.
$ uptime
22:17 up 20 days, 12:24, 18 users, load averages: 2.95 2.93 2.46
$
The output above shows that the time is 10:17 PM (the time is in
24-hour clock format, often referred to as
military time) and that it has been 20 days, 12 hours, and
24 minutes since the system was last rebooted. The three numbers
at the end of the output, 2.95, 2.93, and 2.46, are the load average
of the system over the last 1, 5, and 15 minutes.
The output above shows 18 users on the system when the uptime command
was run. If you want to see a list of those users, use the
w command. If you are the
only user of the system, don't worry that you may see a number greater than
1 listed; it's likely they are all logins for your account as they were when
I checked for the above instance where "18 users" was listed. The output
is showing every logged in session and in this case I had multiple shell
prompts through open tabs in the Terminal application.
[/os/os-x]
permanent link
Wed, Jul 13, 2016 10:39 pm
Python control flow using comparators and logical operators
In
Python, you can use the followng six comparators to determine
if one value is or isn't equal to another or whether the value
is less than, less than or equal to, greater than, or greater than or
equal to another.
| Symbol | Description |
|---|
| == | Equal to |
| != | Not equal to |
| < | Less than |
| <= | Less than or equal to |
| > | greater than |
| >= | greater than or equal to |
[ More Info ]
[/languages/python]
permanent link
Tue, Jul 12, 2016 10:54 pm
OS X Wireless Diagnostics Conflicting Country Codes
I have been experiencing issues with wireless network connectivity at one
location recently while using my MacBook Pro laptop running OS X Yosemite
(10.10.5). Until fairly recently, wireless network connectivity at the location
was great, but recently I would find that
SSH
connections I made from the laptop to another MacBook Pro laptop were
constantly being dropped requiring me to re-establish the connection. And when
I would ping the other system, which I was accessing via the wireless network,
I would see "request timeout" messages. I would also see "request timeout"
messages when I pinged the router's address. A few minutes later I might be
able to successfully ping both systems. Or I could go to
System Preferences
, then double-click on
Network, and then click on "Turn Wi-Fi Off"
and then, after WiFi connectivity was disabled, I could turn it back on and
the Wi-Fi access would then work.
When I used the airport
utility from a Terminal windowto check the noise level and
signal strength for the WiFi connection, I saw the following:
$ /System/Library/PrivateFrameworks/Apple80211.framework/Versions/Current/Resources/airport -I
agrCtlRSSI: -56
agrExtRSSI: 0
agrCtlNoise: -87
agrExtNoise: 0
state: running
op mode: station
lastTxRate: 73
maxRate: 72
lastAssocStatus: 0
802.11 auth: open
link auth: wpa2-psk
BSSID: 94:44:52:4a:43:40
SSID: Rain
MCS: 7
channel: 11[ More Info ]
[/os/os-x/wireless]
permanent link
Sun, Jul 10, 2016 10:27 pm
Safari extensions not appearing
After reopening the last session when I reopened Safari 9.1.1 (10601.6.17)
on a MacBook Pro laptop running OS X Yosemite (10.10.5), I found that, though
the icon for Evernote was appearing the the left of the address bar, clicking
on it did not bring up the Evernote window that would allow me to save
webpages, though
I had installed Evernote
previously.
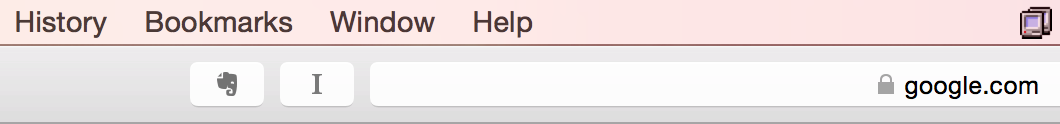
I had closed and reopened Safari after it stopped responding to any
keyboard entries or mouse movement.
When I clicked on Safari from Safari's menu bar and chose
Preferences and then clicked on Extensions, no extensions
were shown. I noticed that the Develop option was not appearing
in the Safari menu bar, though I had
enabled the Develop menu.
So I re-enabled the Develop menu by clicking on Safari from
the Safari menu bar, selecting Preferences, then clicking on
Advanced and then checking the check box next to
"Show Develop menu in menu bar". I then clicked on Develop from
the menu bar when that option reappeared. I then selected
Disable Extensions. I then clicked on Develop again and
again selected Disable Extensions, which this time removed the check
mark next to that option.
[ More Info ]
[/network/web/browser/safari]
permanent link
Fri, Jul 08, 2016 10:55 pm
Ejecting a CD or DVD drive from a command prompt
If you need to eject a CD/DVD disk drive from a command line interface
(CLI) there are a number of ways to do so. Three ways to do so from
a command prompt on a Microsoft Windows system are included below.
Batch File
@echo off
echo Set oWMP = CreateObject("WMPlayer.OCX.7") >> %temp%\temp.vbs
echo Set colCDROMs = oWMP.cdromCollection >> %temp%\temp.vbs
echo For i = 0 to colCDROMs.Count-1 >> %temp%\temp.vbs
echo colCDROMs.Item(i).Eject >> %temp%\temp.vbs
echo next >> %temp%\temp.vbs
echo oWMP.close >> %temp%\temp.vbs
%temp%\temp.vbs
timeout /t 1
del %temp%\temp.vbs[ More Info ]
[/os/windows/utilities]
permanent link
Thu, Jul 07, 2016 9:46 pm
Correcting the time and date on a NetScreen router/firewall via a CLI
If you wish to check or update the date and time on a
Juniper NetScreen router/firewall from a command line interface, you can
establish a
Secure Shell (SSH) connection to the device, provided you have already
configured it to permit SSH access. You can then use the
get clock
command to view the current date and time on the Netscreen device.
ns5gt-> get clock
Date 06/24/1997 07:43:02, Daylight Saving Time enabled
The Network Time Protocol is Disabled
Up 917 hours 27 minutes 27 seconds Since 17 May 1997 02:15:35
867138182.710668 seconds since 1/1/1970 0:0:0 GMT
GMT time zone area -5:00
GMT time zone offset 4:00
ns5gt->
In the above output, I can see that the date and time are not set
correctly. I can see that the time offset from
Greenwich Mean Time (GMT) is four hours, which is currently correct for
this device, though. You can see the current GMT time as well as the times for
many major cities throughout the world at
The World Clock - Worldwide.
The set clock command can be used to set the date.
ns5gt-> set clock ?
mm/dd/yyyy month/day/year
dst-off disable daylight saving time
ntp enable network time protocol
timezone GMT Time zone area
ns5gt->
You can specify the month, date, and year in the form mm/dd/yyyy
. The time should be specified after the date in the form hh:mm
or hh:mm:ss.
[ More Info ]
[/security/firewalls/netscreen]
permanent link
Wed, Jul 06, 2016 11:03 pm
Checking Firefox bookmarks on OS X from a shell prompt
I needed to be able to retrieve a Firefox bookmark for an account on a
MacBook Pro laptop running OS X Yosemite (10.10.5). I wanted to be able
to view the bookmarks from a command line interface (CLI), i.e., a
shell prompt that I would get in a
Terminal window. On an OS X system, the bookmarks and other account-unique
information is stored beneath the profile directory for the
account, which you can find beneath the
~/Library/Application
Support/Firefox/Profiles directory.
$ ls ~/Library/Application\ Support/Firefox/Profiles
bgq13udo.default
$
Within that directory is a places.sqlite
SQLite database.
OS X comes with the sqlite3 program for creating, viewing,
and editing SQLite databases - see
Using SQLite for
information on how to use the program.
[ More Info ]
[/network/web/browser/firefox]
permanent link
Tue, Jul 05, 2016 9:49 pm
Viewing cookies stored by a web page in Safari
I wanted to check on the
cookies stored when I visited a site using
Safari 9.1.1 (10601.6.17) on a MacBook Pro laptop running OS X
Yosemite (10.10.5). When I clicked on
Safari on the Safari
menu
bar and then selected
Preferences, then
Privacy,
I saw a "Cookies and website data" section, but no means to view
the cookies, only a way to delete them by clicking on
Remove All
Website Data.
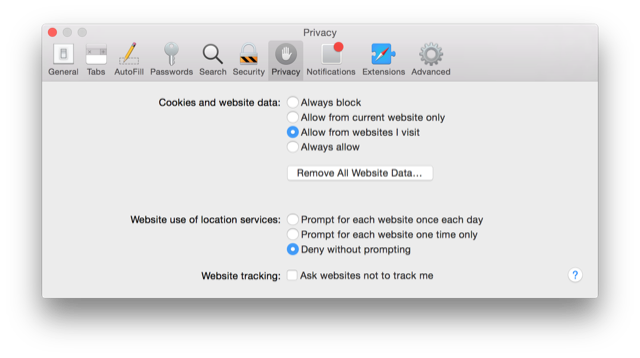
However, you can configure Safari to show details on cookies that are
placed on the system when you visit a webpage by taking the following steps
within the Safari browser.
[ More Info ]
[/network/web/browser/safari]
permanent link
Mon, Jul 04, 2016 2:36 pm
Dovecot - client connections are being dropped
Two users reported that they were not receiving any email this morning.
I logged into the email server, which is a CentOS Linux system using
Dovecot to provide
POP3 email
service, i.e., it is the software on the server to which email clients
connect to download users' email. I then connected to the POP3
port,
TCP port 110, using the
Telnet
program on the system and attempted to check email for a user's account
by issuing the
user command, but after I entered the command
the connection was terminated before I could enter the
pass
command with the password for the account.
# telnet 127.0.0.1 110
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
user nell
Connection closed by foreign host.
#
So I then checked Dovecot's log file. I saw many entries similar to the
following ones in that file:
# grep dovecot /var/log/maillog | tail -5
Jul 4 09:15:44 moonpoint dovecot: master: Warning: service(pop3-login): process
_limit (100) reached, client connections are being dropped
Jul 4 09:18:55 moonpoint dovecot: master: Warning: service(pop3-login): process
_limit (100) reached, client connections are being dropped
Jul 4 09:19:57 moonpoint dovecot: master: Warning: service(pop3-login): process
_limit (100) reached, client connections are being dropped
Jul 4 09:21:01 moonpoint dovecot: master: Warning: service(pop3-login): process
_limit (100) reached, client connections are being dropped
Jul 4 09:26:13 moonpoint dovecot: master: Warning: service(pop3-login): process
_limit (100) reached, client connections are being dropped
#
[ More Info ]
[/network/email/dovecot]
permanent link
Sun, Jul 03, 2016 10:55 pm
Generate random numbers on a Microsoft Windows system
If you need to produce a
random number on a Microsoft Windows system, you can do so at a command
line interface (CLI) or in a batch file using the
%RANDOM%
environment variable - see
Windows
Environment Variables for a list of the environment variables available
on Microsoft Windows systems.
To generate random numbers at the command line, you can
open a command prompt window
and type echo %random%.
c:\Users\Public\Documents>echo %random%
31090
c:\Users\Public\Documents>echo %random%
16802
c:\Users\Public\Documents>echo %random%
20253
c:\Users\Public\Documents>
When you use %random%, you will get numbers between 0 and
32,767, which is 2 to the 15th power. But you can
make the range of numbers smaller by using a command like the following
where 0 is the lower bound for the numbers and n-1 is the upper bound
of the range.
SET /a _rand=(%RANDOM%*n/32768)
[ More Info ]
[/os/windows]
permanent link
Sat, Jul 02, 2016 9:57 pm
SFTP received message too long error
I was able to log into a Microsoft Windows 7 system running
CopSSH via
Secure
Shell (SSH) using
PuTTY, but when I attempted to transfer a file to the
system via the
SSH File Transfer Protocol (SFTP) using
WinSCP, I received the
error message below:
Received too large (1298752370 B) SFTP package. Max supported package size
is 1024000 B.
The error is typically caused by message printed from startup script (like
.profile). The message may start with "Micr".
Cannot initialize SFTP protocol. Is the host running a SFTP server?
[ More Info ]
[/network/ssh]
permanent link
Fri, Jul 01, 2016 10:39 pm
2o7.net
While checking a firewall's logs, I noticed a "TCP FIN SCAN" entry for
66.235.139.18. The log entry showed the local host accessing port 80 on the
remote host at that IP address. Out of curiosity, I performed an nslookup on
the IP address. The
PTR record for the IP address points to the 2o7.net
domain
name.
C:\>nslookup
Default Server:
Address: 192.168.0.1
> 66.235.139.18
Server:
Address: 192.168.0.1
Name: *.112.2o7.net
Address: 66.235.139.18
>
When I put
http://2o7.net in the address bar of a browser,
I was taken to a
Adobe Marketing Cloud privacy web page, which states:
The Adobe Marketing Cloud
solutions enable our business customers to personalize and improve the
performance of their websites, apps, and social networking pages. These
companies use Adobe Marketing Cloud solutions to collect and analyze
information, such as clicks made by visitors on their websites, apps, and
social networking pages. The solutions also allow the companies to provide you
with more relevant messages within their emails, text messages, and other
online and offline marketing campaigns. In general, companies use Adobe
Marketing Cloud solutions when they want to better understand and improve
their online resources and marketing.
[ More Info ]
[/network/Internet/domains]
permanent link

Privacy Policy
Contact




