Sat, Aug 23, 2008 3:42 pm
GSpot
When attempting to playing a movie file, such as an
AVI, you may find that
the audio and/or video doesn't play because of a missing
codec. One solution is
to use a audio/video player, such as
VLC,
which has built-in support for a wide variety of audio/video codecs.
Or, if you prefer to stick with the media player you are accustomed to, such
as
Windows
Media Player, then you can use a program, such as
GSpot to identify
the missing codec.
[ More Info ]
[/os/windows/software/audio-video/GSpot]
permanent link
Sat, Aug 23, 2008 3:17 pm
VLC Media Player
VLC media player is a free
cross-platform media player, which runs on Microsoft Windows,
Mac OS X, BeOS, Syllable, and GNU/Linux systems. It also runs on
BSD and Solaris systems. It is released under a
GPL version 2
license.
VLC media player is a highly portable multimedia player for various
audio and video formats, such as MPEG-1, MPEG-2, MPEG-4, DivX, mp3, ogg, etc, as
well as DVDs, VCDs, and various streaming protocols. It can also be
used as a server
to stream with extended features, such as video on demand, on the
fly transcoding, etc., in unicast or multicast in IPv4 or IPv6 on a
high-bandwidth network. It doesn't need any external codec or program
to work.
VLC supports the following types of files and, when installed,
will make itself the default program for opening these types of files, unless
you specify otherwise.
VLC File Type Associations
Audio Files
.a52
.aac
.ac3
.dts
.flac
.mka
.mp1
.mp2
.mp3
.ogg
.spx
.wav
.wma
Video Files
.asf
.avi
.divx
.dv
.m1v
.m2v
.mkv
.mov
.mp4
.mpeg
.mpeg1
.mpeg2
.mpeg4
.mpg
.ps
.ts
.ogm
.vob
.wmv
Other
.asx
.bin
.cue
.m3u
.pls
.vlc
References:
-
The VideoLAN Web site
-
VLC ReadMe
[/os/windows/software/audio-video/VLC]
permanent link
Mon, Aug 18, 2008 8:21 pm
Transferring BlackBerry Filters to Another System
To transfer BlackBerry email filters from one system to another, take the
following steps. Note: these steps were written for BlackBerry Desktop
Manager Version 4.2.2.12 [Mar 19 2007] running on a Windows XP system.
- Click on Start.
- Select Programs.
- Select BlackBerry.
- Select BlackBerry Desktop Manager.
- Double-click on Email Settings.
- Click on the Filters tab.
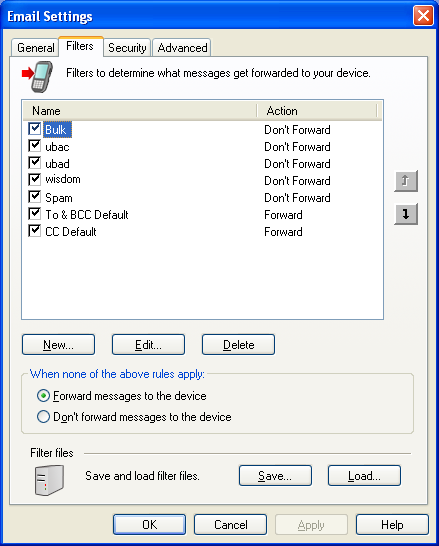
-
- Click on Save.
- Save the filters to an .rfi file.
- Take the saved file to the other computer and
go through the same steps, except click on Load
to load the filters, rather than Save to save
them.
[/network/email/blackberry]
permanent link
Sun, Aug 17, 2008 11:30 pm
Symantec Backup Exec 12 Installation
I installed Symantec Backup Exec 12 on a server tonight. I didn't have time
to try it after I installed it. I had been using Norton Ghost 7.5 for
backups of systems in the domain from that server, but the installation
of Backup Exec caused Ghost 7.5 to stop working when I first rebooted
the system after the Backup Exec installation. However, when I rebooted
again, I received a VXValidate.exe error message, but Norton Ghost 7.5
worked.
[
More Info ]
[/os/windows/utilities/backup/backup_exec]
permanent link
Sun, Aug 17, 2008 5:26 pm
Norton Ghost 7.5 - Realtek RTL8139 NIC
After replacing the motherboard in a Gateway PC, I had to update
the template used by Norton Ghost 7.5 to reflect the network controller
built into the motherboard of the new system. The built-in controller was
a Realtek RTL8139 Family PCI Fast Ethernet NIC. I've included the
necessary NDIS2 driver and instructions for configuring Ghost 7.5 to
use it at
Norton
Ghost 7.5 - Realtek RTL8139 NIC
[/os/windows/utilities/backup/ghost]
permanent link
Sat, Aug 16, 2008 5:14 pm
Ozdok/Mega-D Infected System
I encounted some problems disinfecting a system infected with the
Ozdok/Mega-D trojan.
[ More Info ]
[/security/trojans]
permanent link
Fri, Aug 15, 2008 6:38 pm
Belkin Wireless G Router Model F5D7230-4 Logs
I tested a Belkin Wireless G Router Model F5D7230-4 router that I
had purchased for home use by my mother-in-law, but later replaced
with a Linksys wireless router after she had a network access problem
that I traced to the Belkin router not responding. I thought I might
be able to use it to isolate and test systems that I suspected were
infected with malware.
The version information for the router I tested is shown below:
| Firmware version: | F5D7230-4_US_8.01.07 |
| Boot version: | v1.01 |
| Hardware version: | F5D7230-4 6000 |
The Belkin F5D7230-4 router has a security logging
feature that shows a "system log" and a "firewall log", but the logging
capabilities provided by the router are extremely limited. There's no
way to have a log transmitted by email or for log information to be
transmitted from the router by
syslog. And the information logged is very rudimentary.
The example below shows entries in the system log for attemnpts I made from a
system at 192.168.2.4, which was on the
WAN side of the
router, to login with an incorrect password, from a system that wasn't allowed
to remotely manage the router. The entries in the firewall log section are
from an nmap scan I ran against the router from
a system on the WAN side of the router.
|
Log File
|
System log:
Administrator login fail, Access deny - IP:192.168.2.4
Administrator login fail, Access deny - IP:192.168.2.4
Administrator login fail, Access deny - IP:192.168.2.4
Friday Aug 15 15:22:05 2008 - 192.168.5.4 login
Administrator login fail, Access deny - IP:192.168.2.4
Administrator login fail, Access deny - IP:192.168.2.4
Friday Aug 15 15:22:09 2008 - 192.168.5.4 login
Administrator login fail, Access deny - IP:192.168.2.4
Administrator login fail, Access deny - IP:192.168.2.4
Friday Aug 15 15:22:29 2008 - 192.168.5.4 login
Firewall log:
Friday Aug 15 15:24:00 2008 1 Blocked/RST by DoS protection 192.168.2.5
Friday Aug 15 15:25:13 2008 1 Blocked/RST by DoS protection 192.168.2.5
Friday Aug 15 15:26:20 2008 1 Blocked/RST by DoS protection 192.168.2.5
Friday Aug 15 15:27:32 2008 1 Blocked/RST by DoS protection 192.168.2.5
|
|
The router provides the capability to set "client IP filters" that allow one
to limit outbound access through the router from systems on the
LAN side of the router. You
can specify an IP range and port range to be blocked and whether the block
should apply only during specified days of the week and times or whether
the block should always apply. And you can easily enable and disable a block.
Using that capability you can limit outbound email access to only certain
systems, etc.
There is also a "Parental Control" feature. Belkin states
"Belkin's Parental Control protects you and your children/employees from
objectionable content on the web. Parental Control comes pre-configured to
block many types of web content, but is custom configurable to be more or less
restrictive. Any web site can easily be set to be either, always blocked, or
always allowed." That feature requires a subscription to Belkin's parental
control service.
I had hoped that, if I specified a port block in the client IP filters section,
I would see firewall log entries, if a system on the inside of the router
attempted to access a system on the outside on a blocked port. Alas, no entries
appear in the firewall log in such cases. For me, that makes the firewall
logging capability provided by the router too limited to be of much value.
I'd have to put a real firewall in front of it.
And for rating its security, you can access a lot of information from the
router without even logging into it. If you use your web browser to access
the router you can see the following information without logging into the
router:
| Version Info |
LAN Settings |
| Firmware Version |
LAN/WLAN MAC |
| Boot Version |
IP Address |
| Hardware (model number) |
Subnet Mask |
| Serial No. |
DHCP Server (enabled/disabled) |
| |
| Internet Settings |
Features |
| WAN MAC Address |
NAT (enablded/disabled) |
| Subnet Mask |
SSID |
| WAN IP |
Security (enabled/disabled) |
| DNS Addresses |
|
If the router is going to be used strictly for home use, making that
information so readily available may not be a big concern, since,
hopefully, family members connected by cables to the router can be
reasonably trusted. Hopefully, wireless protection has been activated,
so that no one can easily access the device, since
providing all of that information so readily then could make an attacker's
job much easier.
In addition to the lack of logging functionality,
I have concerns regarding the router's reliability. I replaced it at
my mother-in-law's house after she had some problems printing via the
wireless interface in her laptop. I traced the problem to the Belkin router
not responding. Powering the router off and on resolved the problem, but
this happened a couple of times and I thought it best to replace the router.
I also encountered problems with the router not responding when I tested
it. The problems occurred within just a few minutes of testing. While logged
into the router from a system on the LAN side, I tried accessing it from
the WAN side from a system permitted to manage the router. I wanted to see
what be logged if I entered the wrong password from that system. Well, the
router simply stopped responding completely. I couldn't even ping it
from either the WAN or LAN side. It wouldn't provide IP addresses via DHCP
and it was no longer accessible from either the LAN or WAN side by HTTP.
I had to power the router off and on. I tried again with the same results.
Even for a router designed primarily for home use, having to power the
router off and on frequently could irritate other family members and,
if it was used in a small office, users would likely find any
tendency to stop responding aggravating.
[/hardware/network/router/belkin]
permanent link
Thu, Aug 14, 2008 9:39 pm
Error in Netopia Router Outbound Filter Set
I had configured a Netopia R5300 router to block outgoing connections
to
TCP
port 25, i.e. to block outgoing email traffic, except from two designated
email servers, yet other systems on the
LAN were also able to
connect to the
SMTP port
(port 25) on systems outside the LAN. After checking the outbound filters
(firewall rules), I finally realized I had incorrectly specified
0.0.0.0 for the subnet mask in rules rather than 255.255.255.255.
[More
Info ]
[/hardware/network/router/netopia]
permanent link
Thu, Aug 14, 2008 7:01 am
Opting Out of Credit Card Offers
It seems most weeks I receive several credit card offers in the mail. Since
there are recycle bins in my community for paper, as well as cans and some
types of plastic, I usually shred them and put the pieces in a box to be taken
to the recycle bins with other items. But, since an offer I received
yesterday had the following opt-out notice on the back of it, I decided it
was time to opt out.
PRESCREEN & OPT-OUT NOTICE: This "prescreened" offer of credit is
based on information in your credit report indicating that you meet
certain criteria. This offer is not guaranteed if you do not meet our
criteria. If you do not want to receive prescreened offers of credit
from this or other companies, call toll free 1 (888) 567-8688; or write:
Experian Consumer Opt Out, P.O. Box 919, Allen, TX 75013; Equifax Options,
P.O. Box 740123, Atlanta, GA 30374-0123; TransUnion Opt Out Request,
P.O. Box 505, Woodlyn, PA 19094-0505.
I called the opt-out number, 1-888-567-8688. I was informed it was
the consumer credit reporting industry opt-in and opt-out number, which
allows you to add or remove your name from "receiving firm offers of
credit or insurance based on your credit report" with the following
credit reporting services:
Experian
Equifax
Innovis
TransUnion
You can choose to add your name, i.e. opt-in, to such offers, remove your
name for 5 years, or remove your name permanently. If you try to remove
your name permanently, you will be informed that you have to complete
a form you will be sent, so I chose to remove my name for 5 years.
You will be asked to confirm your phone number, name and address and provide
your Social Security Number (SSN) and date of birth. The whole process is
handled by an automated system and it only took me a couple of minutes
to complete it.
When I completed the process, I was informed that my removal request
would be completed within 5 business days, but that I might continue to
receive offers for several months from companies to which my information
had already been provided and that I might also receive offers from
companies that had obtained my information by other means. Hopefully,
though, I will see a substantial diminution of the daily deluge of junk
mail we receive at my house.
[/financial]
permanent link
Mon, Aug 11, 2008 7:03 pm
Excel Password Protection
For encrypting Excel workbooks with a password, use the following technique.
Note: these steps apply to Office 2003 and 2007; for other versions the
exact steps may vary.
- From the Excel menu select "File" or, if you are using Office 2007,
click on the Office Button at the top left corner of the
Excel window.
- Select "Save As"
- From the "Save As" window, select "Tools"
- Select "General Options"
- Specify a "Password to open"
- Click on "OK" to save the file.
A password is now required to open and view the file.
[/os/windows/office/excel]
permanent link
Mon, Aug 11, 2008 6:33 pm
Password Protecting a PDF File in Adobe Acrobat
Acrobat supports public/private key encryption, but if you don't have
a security certificate for another party to whom you are going to provide
the encrypted document, then you need to use the
"shared secret", i.e. password, approach for encrypting a PDF file where
you specify a password for the document and give that password to the
other party by some means other than email, e.g. by phone.
You can use the method outlined by Adobe in
Set passwords for PDFs to password protect PDF files that you
will then email to others.
The article mentions that PDF documents can have two types of passwords:
- User, aka "document open", password
- Pemissions, aka "master", password, which provides access controls for the
PDF document
To keep unauthorized individuals from viewing a PDF file, employ a "user"
password. The other type of password, which you might also want to use in
some cases, controls what recipients can do with a document.
Note: there are low-cost tools readily available online to remove that
type of password from a PDF file. There are also low-cost programs readily
available to defeat the first type of password unless you pick a strong
password, i.e. one that is not a dictionary word, car name, sports team,
person's name, etc. There are plenty of password dictionaries available to
allow people to crack weak passwords. Any password protection scheme is
virtually worthless, if someone picks a weak password. A strong password
should have at least 8 characters with a combination of characters from
at least 3 character sets. Character sets include those below:
- Upper case letters
- Lower case letters
- Numbers
- Special characters, such as "!", "-", "_", "$", etc.
Open the file you want to protect in Adobe Acrobat and follow the instructions
below for encrypting and password protecting the file.
- Click the secure button
 in the Tasks
toolbar and choose Password Encrypt.
in the Tasks
toolbar and choose Password Encrypt.
- Click on Yes when prompted "Are you sure you want to change
the security on this document?" If necessary, type the Permissions password
that lets you change security settings. If you don't know the password, contact
the author of the PDF file.
- In the Password Security - Settings dialog box set the security options
as desired. For the Compatibility setting, "Acrobat 5.0 or later"
is the default option. That will provde 128-bit
RC4 encryption. Selecting
"Acrobat 3.0 or later", instead, will mean that users of older versions of
Acrobat will be able to open the file, if they know the password, but I
would strongly advise against choosing that option, if you need to guarantee
that only someone who has been given the password can open it.
If that option is selected, a 40-bit encryption scheme is used instead of
128-bit encryption. Even with a strong password, if you use 40-bit encryption,
there are plenty of low-cost programs available online for anyone to easily
break the password protection. With 128-bit protection, you can be confident
that the protection will likely remain unbreakable for years to come (eventually
increases in computing speeds, or the development of
quantum computers,
will likely render even that level of encryption breakable).
- Specify a password, click OK and then OK again.
- Save the file
Note: these instructions were written specifically for Adobe Acrobat
8 Standard edition, but will likely be similar for other versions.
[/os/windows/software/pdf]
permanent link
Mon, Aug 11, 2008 3:01 pm
Windows Defender Detected Activity Monitor File
I performed a full scan of my HP laptop with Windows Defender after updating
its definitions today to definition version: 1.4.172.0 created on 8/7/2008 at
4:00 AM.
Windows Defender Version: 1.1.1593.0
Engine Version: 1.1.3807.0
Definition Version: 1.41.172.0
Windows Defender found two items it gave a "medium" alert level. I
instructed it to ignore both, since they were false positives. The
first was for a download of the Activity
Monitor program, which is in
a "downloads" folder, but isn't installed on the system. The second
occurred because SpySweeper updated the
C:\WINDOWS\system32\drivers\etc\hosts file on 12/18/2006 to block
nefarious sites.
| Name | Alert level |
|---|
| MonitoringTool:Win32/ActivityMonitor | Medium |
| SettingsModifier:Win32/PossibleHostsFileHijack | Medium |
MonitoringTool:Win32/ActivityMonitor
Category:
Monitoring Software
Description:
This program monitors user activity, such as keystrokes typed.
Advice:
Review the alert details to see why the software was detected. If you do not like how the software
operates or if you do not recognize and trust the publisher, consider blocking or removing the software.
Resources:
file:
C:\Documents and Settings\JDoe\My Documents\Downloads\activmon39full.zip->amagent39.exe
containerfile:
C:\Documents and Settings\JDoe\My Documents\Downloads\activmon39full.zip
View more information about this item online
SettingsModifier:Win32/PossibleHostsFileHijack
Category:
Settings Modifier
Description:
This program has potentially unwanted behavior.
Advice:
Review the alert details to see why the software was detected. If you do not like how the software operates or if you do not recognize and trust the publisher, consider blocking or removing the software.
Resources:
file:
C:\WINDOWS\system32\drivers\etc\hosts
View more information about this item online
[/os/windows/software/security/monitoring/activity_monitor]
permanent link
Sun, Aug 10, 2008 5:13 pm
Sun, Aug 10, 2008 1:15 pm
Using Helix for Forensics
I had come across
Helix -
Incident Response & Computer Forensics Live CD by e-fense
™ before, but hadn't done anything with it.
I read an article
An Introduction to Digital Forensics by BJ
Gleason in
Linux+DVD 3/2008
and decided to try it.
[ More Info ]
[/security/forensics]
permanent link
Sun, Aug 10, 2008 9:34 am
Regaining Access to Hidden Windows Account
I have a laptop running Windows XP Home Edition Service Pack 2 with one
"
hidden account", i.e. the account is
not visible on the Windows welcome screen, which shows the accounts one
can log into. I can log into that hidden account, by hitting Ctrl-Alt-Del and
then putting in the username for the hidden account and its password. But
a problem I have when I'm logged into that account and the screen saver
activates, is that when I hit a key or move the mouse to access the system
again, the system displays the welcome screen with the two visible
accounts, but then hitting
Ctrl,
Alt, and
Del won't
bring up the login window where I can type in the username for the hidden
account and its password.
The screen saver for the hidden account is set to the "Windows XP" screen
saver with "On resume, display Welcome screen" checked.
At
Hide user accounts from the Windows XP Welcome screen, one can
download a tool that makes it easy to hide and unhide accounts. The webpage
also mentions that the Ctrl-Alt-Del trick for logging into hidden accounts
has a a pitfall - "it will fail to work if a user is still currently logged in."
If I hit Ctrl-End, the cursor is placed in the passwod field for one of the
visible accounts, but hitting Ctrl-Alt-Del at that point has no effect
and I can't get back into the logged in account.
I've found I can get around this problem by logging into one of the
visible accounts and then immediately logging off that account. If I
then hit Ctrl-Alt-Del a couple of times, I get the "Log On to Windows" user
name and password prompt and can regain access to the hidden account under
which I'm already logged in.
[/os/windows/xp]
permanent link
Sat, Aug 09, 2008 8:01 pm
Flash Saving Plugin
I wanted to be able to view
Flash
movies cached by a browser, such as Internet Explorer or
Firefox on a system.
One free tool that allows you to view cached
SWF files is
Flash
Saving Plugin
[ More Info ]
[/os/windows/software/network/web]
permanent link
Fri, Aug 08, 2008 9:00 pm
RUBotted (Beta)
I installed a free bot detection utility from
Trend Micro called
RUBotted on a system to check for
bot software on the system.
I didn't expect to find such software on the system, but wanted to check it
thorougly.
[ More Info ]
[/os/windows/software/security/antimalware]
permanent link
Fri, Aug 08, 2008 12:10 pm
Adding a Link to a Local File in ELOG
I had some initial difficulties adding a link in an ELOG entry for a
file stored locally on the server on which ELOG was running. I discovered
that I needed to prepend a timestamp to the file name when placing it
in the directory where entries are stored for the relevant logbook and
then use that prepended timestamp as part of the path to the file in
the
URL.
E.g. for a file called samplefile.txt, I had to store it in
the logbook directory as 080808_110230_samplefile.txt where
080808 represented the date for the file, August 8, 2008, and
110230 represented a timestamp for the file, i.e. 11:02:03 A.M.
The date is in yymmdd format. I was then able to use
http://server.example.com/sysadmin/080808_110230/samplefile.txt
as the URL for the link in the logbook entry. I placed the
080808_110230 between slashes and followed it by the orginal
filename.
I was then able to access the file through a link in the logbook entry.
[ More Info ]
[/network/web/blogging/elog]
permanent link
Wed, Aug 06, 2008 11:09 pm
Configuring Apache as a Proxy Server
I needed to configure an
Apache
(version 2.0.59) server to act as a
proxy server. I also needed it to continue to act as a web server.
To do so, I added the 3
LoadModule directives shown below to the
LoadModule section of Apache's
httpd.conf, which is located in
/usr/local/apache2/conf on this particular system, which
is a Solaris 2.7 server (it will likely be in
/etc/httpd/conf/httpd.conf, if you are running Apache on a Linux system).
# Dynamic Shared Object (DSO) Support
#
# To be able to use the functionality of a module which was built as a DSO you
# have to place corresponding `LoadModule' lines at this location so the
# directives contained in it are actually available _before_ they are used.
# Statically compiled modules (those listed by `httpd -l') do not need
# to be loaded here.
#
# Example:
# LoadModule foo_module modules/mod_foo.so
#
LoadModule proxy_module modules/mod_proxy.so
LoadModule proxy_connect_module modules/mod_proxy_connect.so
LoadModule proxy_http_module modules/mod_proxy_http.so
The following lines, except for the comment lines, are also needed in
httpd.conf:
#
# Proxy Server directives. Uncomment the following lines to
# enable the proxy server:
#
ProxyRequests On
#
Order deny,allow
Deny from all
Allow from 192.168.1.3 192.168.1.4 127.0.0.1
In this case I wanted to limit access to the proxy server to access from
the system itself, e.g. from the loopback address, 127.0.0.1, and two
other IP addresses, 192.168.1.3 and 192.168.1.4. I could have also used
192.168.1 to allow access from any 192.168.1.x address.
After modifying the httpd.conf file, I restarted Apache with
/usr/local/apache2/bin/apachectl restart. For a Linux system
apachectl restart should suffice, though it is likely located in
/usr/sbin, if you need to specify the full path.
After restarting Apache I was able to configure a browser on the system at
the 192.168.1.4 address to use the Apache server as a proxy server. I used
the IP address of the Apache server, 192.168.1.1 as the HTTP proxy server
address with 80 as the port. I verified that the browser was using the
Apache server as a proxy server by pointing the browser on the
192.168.1.4 system to www.showmyip.com.
That site showed the address for the system as 192.168.1.1, i.e. it showed
the connection as originating from the proxy server rather than the actual
system on which the browser was being used.
I was also still able to access webpages on the website I host on the
Apache server on the default HTTP port.
If you want to turn the proxy service off, you need only change the
ProxyRequests On line to ProxyRequests Off and
restart Apache.
References:
-
Configuring Apache 2.0 as a Forward Proxy Server
By: Martin Brown
Date: January 4, 2008
ServerWatch
-
Configuring mod_proxy support for Apache
IBM
[/network/web/server/apache]
permanent link
Tue, Aug 05, 2008 10:15 pm
Turnitin Crawler
While troubleshooting a problem with a website using
wireshark, I was capturing
HTTP traffic.
I noticed a connection from 65.98.224.2 with the contents
of the first packet received from that address showing
the software accessing my support website identifying itself
as shown below:
User-Agent: TurnitinBot/2.1 (http://www.turnitin.com/robot/crawlerinfo.html)
Checking the URL listed, I found the following:
Chances are that you are reading this because you found a reference
to this web page from your web server logs. This reference was left
by Turnitin.com's web crawling robot, also known as TurnitinBot. This
robot collects content from the Internet for the sole purpose of helping
educational institutions prevent plagiarism. In particular, we compare
student papers against the content we find on the Internet to see if
we can find similarities. For more information on this service, please
visit www.turnitin.com
The Wikipedia
article on Turnitin states that it is as "an Internet-based
plagiarism-detection service created by iParadigms, LLC. Institutions
(typically universities and high schools) buy licenses to submit essays
to the Turnitin website, which checks the document for plagiarism."
I had read that many schools now use such services to deter students
from submitting plagiarized papers. I've seen services offerring pre-written
papers for students to submit for classes, so I can see the need for teachers
to use such detection services. I didn't realize this service crawled websites
to index materials on the web as part of its detection efforts, but it makes
sense to me that the service would do so. This is the first time I've
noticed this particular web
crawler
[/network/web/crawlers]
permanent link
Tue, Aug 05, 2008 9:58 pm
Installing Wireshark
I wanted to install Ethereal on a CentOS Linux system to sniff network traffic
to try to resolve a problem for a website. I have
tcpdump on the system,
but I wanted to have a
GUI
tool to make analyzing the packets a little easier for me.
I ran yum install ethereal, which installed wireshark
and its dependency, libsmi. Wireshark was installed, because
development of ethereal has stopped and the core development team is now
developing wireshark.
The FAQ for
wireshark offers the following explanation of the name change.
In May of 2006, Gerald Combs (the original author of Ethereal) went
to work for CACE Technologies (best known for WinPcap). Unfortunately,
he had to leave the Ethereal trademarks behind.
This left the project in an awkward position. The only reasonable way to
ensure the continued success of the project was to change the name. This
is how Wireshark was born.
Wireshark is almost (but not quite) a fork. Normally a "fork" of an
open source project results in two names, web sites, development teams,
support infrastructures, etc. This is the case with Wireshark except for
one notable exception -- every member of the core development team is now
working on Wireshark. There has been no active development on Ethereal
since the name change. Several parts of the Ethereal web site (such as the
mailing lists, source code repository, and build farm) have gone offline.
After the installation completed, I tried running wireshark by issuing
the command wireshark.
# wireshark
bash: wireshark: command not found
I then discovered that installing the wireshark
RPM only installs
a command line program, tshark. The program was installed in
/usr/sbin/tshark. You can obtain help on
tshark using man tshark or tshark -h.
There is also documentation installed in /usr/share/wireshark/help.
I had to install wireshark-gnome to get the GUI version, which
I did with yum -y install wireshark-gnome. I could then start
the GUI version from a shell prompt with wireshark or start it
by clicking on Applications, Internet, and then
Wireshark Network Analyzer.
Since I wanted to capture only HTTP
traffic, I typed HTTP in the Filter field and
then clicked on the Apply button. I then clicked on Capture,
Interfaces, and clicked on the Start button next to the
eth0 interface to start capturing all HTTP traffic.
[/network/tools/sniffing/wireshark]
permanent link
Tue, Aug 05, 2008 7:35 am
Web Developer Extension for Firefox
The
Web
Developer extension for Firefox adds a menu and a toolbar to the browser
with various web developer tools. It is designed for
Firefox,
Flock and
Seamonkey, and will
run on any platform that these browsers support including Windows, Mac OS X
and Linux.
You can install the extension by simply clicking on the
link for it. When it
is installed, you will be notified you should restart Firefox to complete
your changes.
The extension provides the capability for one to easily view the
headers or CSS information for
a page, check for
Section 508 compliance, display the dimentions of images on the page,
and many other capabilities useful to web developers.
[ More Info ]
[/network/web/browser/firefox]
permanent link
Mon, Aug 04, 2008 10:21 pm
Setting Up SquirrelMail
I wanted to set up
SquirrelMail
on a CentOS Linux system. After verifying that the SquirrelMail package was
not already installed with
rpm -qi squirrelmail,
I installed the SquirrelMail package with
yum install squirrelmail.
The
php-mbstring package is a dependency for the squirrelmail
package, so it was installed as well.
SquirrelMail is installed in /usr/share/squirrelmail. The
configuration files are installed in /etc/squirrelmail.
# ls /etc/squirrelmail
config_local.php config.php default_pref sqspell_config.php
After the software was installed I ran the configuration script to
configure SquirrelMail.
# /usr/share/squirrelmail/config/conf.pl
When I ran the configuration script, I saw the following menu:
SquirrelMail Configuration : Read: config.php (1.4.0)
---------------------------------------------------------
Main Menu --
1. Organization Preferences
2. Server Settings
3. Folder Defaults
4. General Options
5. Themes
6. Address Books
7. Message of the Day (MOTD)
8. Plugins
9. Database
10. Languages
D. Set pre-defined settings for specific IMAP servers
C Turn color off
S Save data
Q Quit
Command >>
I typed D and hit Enter to configure SquirrelMail for a
specific IMAP server. In this
case, I'm running dovecot on the server, which is one of the IMAP servers for
which the configuration script can optimize SquirrelMail's settings.
SquirrelMail Configuration : Read: config.php
---------------------------------------------------------
While we have been building SquirrelMail, we have discovered some
preferences that work better with some servers that don't work so
well with others. If you select your IMAP server, this option will
set some pre-defined settings for that server.
Please note that you will still need to go through and make sure
everything is correct. This does not change everything. There are
only a few settings that this will change.
Please select your IMAP server:
bincimap = Binc IMAP server
courier = Courier IMAP server
cyrus = Cyrus IMAP server
dovecot = Dovecot Secure IMAP server
exchange = Microsoft Exchange IMAP server
hmailserver = hMailServer
macosx = Mac OS X Mailserver
mercury32 = Mercury/32
uw = University of Washington's IMAP server
quit = Do not change anything
Command >>
I typed dovecot and hit Enter to configure SquirrelMail
for the dovecot IMAP server. I was then shown the configuration options set
for dovecot.
imap_server_type = dovecot
default_folder_prefix =
trash_folder = Trash
sent_folder = Sent
draft_folder = Drafts
show_prefix_option = false
default_sub_of_inbox = false
show_contain_subfolders_option = false
optional_delimiter = detect
delete_folder = false
Press any key to continue...
When I hit a key, I was returned to the main menu. I typed S and
hit Enter to save the settings. I was informed "Data saved in
config.php". I then typed Q and hit Enter to exit from the
configuration script.
The system runs the Apache webserver,
so I then restarted the Apache server with apachectl restart.
During the installation, the file
/etc/httpd/conf.d/squirrelmail.conf is created. The file
contains the following lines:
#
# SquirrelMail is a webmail package written in PHP.
#
Alias /webmail /usr/share/squirrelmail
The web interface for SquirrelMail can be accessed at
http://a.example.com/webmail [substitute the actual name for
your server for a.example.com]. You should see a login page
where you can login to check email.
You can also test the SquirrelMail configuration using
http://a.example.com/webmail/src/configtest.php [again,
substitute your actual domain name for a.example.com].
When that page is displayed, you will see configuration information.
The script will try to check some aspects of your SquirrelMail configuration
and point you to errors whereever it can find them. You need to have run
conf.pl in the config/ directory first, as I mentioned above, before you run
this script. At the bottom of the webpage that is displayed, you should see
"Congratulations, your SquirrelMail setup looks fine to me!"
[/network/email/squirrelmail]
permanent link
Sun, Aug 03, 2008 4:25 pm
Outlook 2003 Mailbox Size Exceeded
An Outlook 2003 user received the message below:
You have exceeded the size limit on your mailbox. You can find types of
items to delete or move, empty the deleted items folder, or you can have
Outlook transfer items to an archive file.
I had to delete copies of messages he forwarded multiple times and archive
some messages to bring the mailbox size below 2 GigaBytes (GB) [See
Outlook 2003 Mailbox Size Exceeded].
I also checked the size of all other users' mailboxes on the Microsoft
Exchange 6.5 server that processes his email. [See
Determining Mailbox Size
for All Exchange Users]
[/network/email/clients/outlook]
permanent link
Sat, Aug 02, 2008 6:23 pm
ELOG Port Configuration
I installed the
Electronic Logbook
(ELOG) package developed by Stefan Ritt on a Windows Small Business
Server (SBS) 2003 system to track work I do on the system. By default,
ELOG uses port 8080, but I already had other webserver software listening
on that port, so I changed the listening port for ELOG. I also configured
ELOG to support SSL, i.e. to accept HTTPS connections. I also set a
read and write password for access to the logbook I created.
Port Configuration
SSL Configuration
Password Configuration
[/network/web/blogging/elog]
permanent link
Sat, Aug 02, 2008 3:10 pm
Determining Version of JRE
If you have
Sun Microsystem's Java Runtime
Environment (JRE) installed on a system, you can check its version by
obtaining a command prompt and entering the command
java -version.
C:\>java -version
java version "1.6.0_07"
Java(TM) SE Runtime Environment (build 1.6.0_07-b06)
Java HotSpot(TM) Client VM (build 10.0-b23, mixed mode, sharing)
If you selected the default install directory, the JRE software will likely
be stored in C:\Program Files\Java.
C:\PROGRA~1\Java>dir
Volume in drive C has no label.
Volume Serial Number is AC89-88C6
Directory of C:\PROGRA~1\Java
08/02/2008 08:55 AM <DIR> .
08/02/2008 08:55 AM <DIR> ..
11/20/2004 04:49 PM <DIR> j2re1.4.2_03
12/13/2004 02:57 AM <DIR> j2re1.4.2_05
08/15/2005 09:20 PM <DIR> jre1.5.0_04
01/12/2006 12:57 AM <DIR> jre1.5.0_06
08/02/2008 08:55 AM <DIR> jre1.6.0_07
0 File(s) 0 bytes
7 Dir(s) 54,967,054,336 bytes free
On a Linux system, you can also issue the java -version command
to see the version.
$ java -version
java version "1.4.2"
gij (GNU libgcj) version 4.1.2 20071124 (Red Hat 4.1.2-42)
Copyright (C) 2006 Free Software Foundation, Inc.
This is free software; see the source for copying conditions. There is NO
warranty; not even for MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
[/software/java]
permanent link

Privacy Policy
Contact




 in the Tasks
toolbar and choose Password Encrypt.
in the Tasks
toolbar and choose Password Encrypt.