←December→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| 1 |
2 |
3 |
4 |
5 |
6 |
7 |
| 8 |
9 |
10 |
11 |
12 |
13 |
14 |
| 15 |
16 |
17 |
18 |
19 |
20 |
21 |
| 22 |
23 |
24 |
25 |
26 |
27 |
28 |
| 29 |
30 |
31 |
|
|
|
|
|
|
Sat, Dec 28, 2013 9:18 pm
Viewing Installed Fonts on a Windows 8 System
To see a list of the fonts installed on a Windows 8 system, you can
take the following steps:
-
Move the mouse pointer to a corner of the screen to bring up the menu with
the magnifying glass representing the Search function. When you
select the search function, you will see field appear where you can type
fonts to search on that term. Hit Enter once you have
typed fonts to initiate the search.
-
You may see "No apps match your search" and
0 next to Apps
on the right of the screen, but beneath Apps you should see
Settings with a number to the right of it, which should be 6 or
greater. Click on Settings.
-
Click on Fonts or View Installed Fonts.
If you wish to see what a particular font looks like, you can double-click
on it or touch the icon for it if you have a touchscreen.
If you have a TrueType .ttf font file
you have downloaded, you can right-click on it and choose Install
to install it on your system or you can double-click it to open a font
preview window and then select install. To install a font, you will
need to provide a userid and password for an account with administrator
privileges on the system.
[/os/windows/win8]
permanent link
Sat, Nov 16, 2013 6:45 pm
Updating an entry in a MySQL Database
The
UPDATE command allows one to update an existing entry in
a MySQL database. The format for the command is as follows:
UPDATE table_name SET column1=value1, column2=value2, columnN=valueN WHERE clause;
E.g., suppose there is a database named "software" with a table
named "system1", which is used to maintain records of all the software
installed on system1, with the fields id, which ia a numeric value, and a
character field named "developer". The following commands could be used to
update just the developer field for the record in the table with id=37.
mysql> use software;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql> update system1 set developer="Acme Corporation" where id=37;
Query OK, 1 row affected (0.00 sec)
Rows matched: 1 Changed: 1 Warnings: 0
You can enter a date for a date field with the value enclosed in single
quotes in the form YYYY-MM-DD. E.g.:
update system1 set Obtained='2013-11-14' where id=37;
You can calculate the value for a field based on the contents of another
field in the database. E.g., suppose there is a field named Obtained
in the database and anotehr column with a field indicating when a virus scan
was conducted named Scan_date. If I knew a particular piece of software
was scanned the day after it was obtained, I could use the command below:
update system1 set Scaned=Obtained+1 where id=37;
What if there was no date previously entered in the Obtained field, i.e,
it has a null entry for that field. Then the Scaned field will still be
null.
Note: it is critically important not to forget the WHERE
clause when using an UPDATE command. If you forget it, then the
update will be applied to every record in the database and you won't be able
to undo the update command unless you've followed the steps listed at
13.3.1. START TRANSACTION, COMMIT, and ROLLBACK Syntax prior to applying
the update command. If you haven't taken such steps, unless you have a
backup you can rely on, you won't be able to revert your data to what
it was before you applied the update command.
[/software/database/mysql]
permanent link
Thu, Nov 07, 2013 8:15 pm
Replacing a character with a newline character using vi
If you wish to replace all occurrences of a character with a newline character, which is used on Linux/Unix systems to indicate the start
of a new line, you can represent the new line with a
\r in a vi command; think of the "r" as representing a carriage return. E.g., if
I had a long line with items on the line separated by commas, I could use the command below to remove each comma and start another line where
the comma occurred, instead.
:s/,/\r/g
[/editors/vi]
permanent link
Thu, Nov 07, 2013 7:54 pm
Sorting lines in a file using the vi editor
If you need to sort all the lines in a file alphabetically with the vi editor, you can use
! sort. E.g., you could sort
lines 10 to 20 with the following command:
:10,20 ! sort
You can sort all lines in the file with 1,$ ! sort.
[/editors/vi]
permanent link
Wed, Nov 06, 2013 9:49 pm
SystemUIServer CPU Usage High
My MacBook Pro laptop running OS X 10.8.3 was performing abysmally. It was taking an inordinate amount of time to switch from application to application and to
perform even simple tasks in programs. I closed VMWare, which helped, but then
when I went to view a video in Safari I found I needed to increase the volume
to hear the audio, but the pinwheel just kept spinning preventing me from
doing so.
I started the Activity Monitor, which can be found in
Applications/Utilities, to see what was happening. After starting
the application, I clicked on the % CPU column header to order the
process list by CPU utilization. The Activity Monitor was showing
that the process SystemUIServer was using from 75% to 85%
of the CPU cycles. I clicked on SystemUIServer to select the
process then clicked on the Quit Process button then the
Quit button to kill the process.
The process got restarted shortly afterwards, but it was then using
about 0% of the CPU cycles.
I found someone else experiencing the problem posting at
High CPU use caused by SystemUIServer?
that he found the problem to be asociated with menubar apps, specifically
Dropbox in his case, but I don't use Dropbox and don't know what app
may have triggered the problem on my laptop.
[/os/os-x]
permanent link
Thu, Oct 31, 2013 11:27 am
Senior Assistance Telemarketer
Our home phone number is on the U.S. federal government
Do Not Call list, but that doesn't
stop some telemarketers from calling, even though people who have added
their phone numbers to the do not call registry are unlikely to do
business with some company that calls them in spite of their numbers
being on that list.
I received a robocall with a spiel about an opportunity to receive
$3,000 in free groceries with no option to have our number removed from the
company's calling list. I could only hit a button to speak to a representative,
which I did. I asked for the name of the company and was told it was
"Senior Assistance" something. When I complained about the company ignoring
the do not call list, I was told that I had opted in to receive such calls.
I've heard that excuse before, which I regard as bogus, since I don't opt in
to be contacted by third parties when I register any personal information
with companies or organizations. Companies that ignore the do not call list
likely often tell employees to use that excuse to placate people who call
and complain about their annoying telemarketing calls.
When I used *69 to get the calling number, I found it was 323-281-1384.
At
323-281-1384 / 3232811384 at the
800notes site which provides a directory of unknown callers where
people can report such calls, I found other people on the Do Not Call
registry complaining they also received such calls.
I filed a complaint at the
National Do Not Call Registry Submit a Complaint page as I usually do
when I get such calls. I can only hope that enough other people file a
complaint there that the Federal Trade Commission may take some action
against the company, though I'm doubtful that action will be taken, or, if
it is that any fine would be stiff enough to make ignoring the list untenable
for the company.
[/phone]
permanent link
Thu, Oct 31, 2013 10:49 am
Scrollbars no longer visible
After an operating system upgrade to OS X 10.8.3, aka "Mountain Lion",
on my MacBook Pro laptop, I no longer saw scrollbars in applications,
including the Safari browser. If I resized a window by changing its
width, the scroll bar would appear in the window. But the next time I
opened the application I would have to go through the same procedure to
get the scrollbar again. I've seen people complaining of the disappearance
of scroll bars when they upgraded to OS X 10.9, aka "Mavericks".
To get the scrollbar to appear on windows by default, take the following
steps:
-
Click on the Apple icon at the top, left-hand corner of the screen.
-
Select System Preferences.
-
Under the Personal section, select General
-
For the Show scroll bars options, you will see the following choices:
- Automatically based on mouse or trackpad
- When scrolling
- Always
Select "Always". You can then close the window.
You should then see a scroll bar in applications.
[/os/os-x]
permanent link
Wed, Oct 30, 2013 11:35 pm
Out of office message for Entourage users
If you are using Microsoft Entourage 2008 for email on a Mac and want to have
an out-of-office message sent in reply to email sent to you while you
are out of the office on vacation or for other reasons, you can configure
Entourage to send a message by using its rules feature, which you can
access by clicking on
Tools and selecting
Rules in
Entourage then taking the following steps:
-
Click on New.
-
Select Mail (Exchange), if your email is coming from a Microsoft
Exchange server. For email coming from a
POP server, you can place
the rule under Mail (POP).
Note: POP rules act on a message only when it first arrives in the Inbox
(On My Computer), not when it arrives in any other folder. Once it's
moved to another folder it won't be seen by rules.
-
In the Rule name field type "Out of Office".
-
Leave "if all criteria are met" selected in the Execute field.
-
In the top, left drop down list beneath Then and beneath
the Add Action button, select Reply,
wnich will then show a Reply Text button. Click on that button which
will allow you to provide the out-of-office message you wish sent to senders.
-
Make sure the Enabled checkbox is checked and click on the
OK button.
You should then see the rule listed under the Mail (Exchange) tab
of the Rules window, which you can close.
If you need to change the rule, e.g., to change the message sent in reply
to incoming email, click on Tools, select Rules and then,
under the Mail (Exchange) tab, provided that you created the rule
in that category, double-click on the Out of Office rule to open it. Then
make any needed changes.
When you no longer need the rule, click on Tools, select
Rules, and then click on the Mail (Exchange) tab. Then
uncheck the checkbox in the Enabled column next to the Out of Office
rule to disable it.
The above method requires that you leave your computer turned on with
network access and with Entourage running. Of course, it might be a laptop
you wish to take with you which might not be on all the time while you
are out of the office. So a better method, if your company/organization
is using a Microsoft Exchange server, is to use your browser to log into
the Outlook Web App, then take the following steps:
-
Click on Options (look in the upper, right-hand corner of the web
page).
-
Select Automatic Replies.
-
Select the radio button for "Send automatic replies".
-
You can then set the start and end times for the replies.
-
You can then fill in a message to be sent to those who send you email while
you are out of the office. There are two sections, one for internal senders
and one for senders outside of your organization. You can send different
messages to internal versus external senders, if you wish, or you
can fill in the same text to be sent to both types of senders.
Fill in the "Send a reply once to each sender inside my organization with
the following message" for the message you wish to go to internal senders.
-
To have the out-of-office messages go to senders
outside of your organization, check the checkbox next to "Send automatic reply
messages to senders outside my organization". Beneath that checkbox, you
can select from the following 2 options:
- Send replies only to senders in my Contacts list
- Send replies to all external senders
-
Fill in the "Send a reply once to each sender outside my organization with the
following message" section, if you have chosen to send automated replies to
external senders.
-
Click on the Save Button.
This method will send out of office messages whether your Mac running
Entourage is turned off and you won't need to configure Entourage to send
such messages. When it is set up, if you select Tools then
Out of Office from within Entourage, you can see the message
that will be sent as an out-of-office reply
[/network/email/clients/entourage]
permanent link
Tue, Oct 29, 2013 11:53 pm
Loss of network access after VPN connection times out
On my MacBook Pro laptop, I've found that whenever a VPN connection, which
I establish through Juniper Networks VPN client software, times out,
or is dropped for some other reason prematurely, I lose network access. From
a shell prompt, I can ping the system's own address, but I can't ping
any other system and all network access via the Safari browser, email access,
etc. doesn't work.
If I try pinging an IP address other than the system's own address, I see
"cannot allocate memory" messages. E.g., an attempt to ping the router
would give me the results below:
$ ping 192.168.0.1
PING 192.168.0.1 (192.168.0.1): 56 data bytes
ping: sendto: Cannot allocate memory
ping: sendto: Cannot allocate memory
Request timeout for icmp_seq 0
ping: sendto: Cannot allocate memory
Request timeout for icmp_seq 1
^C
--- 192.168.0.1 ping statistics ---
3 packets transmitted, 0 packets received, 100.0% packet loss
I tried disabling and re-enabling Wi-Fi by going into the network settings
and selecting "Turn Wi-Fi Off", but turning it off and on didn't help. The
following steps did work, though, from an account with admin privileges:
-
Click on the Apple icon in the upper-left corner of the screen and select
System Preferences.
-
Select Network.
-
Click on the Advanced button near the bottom, right-hand corner
of the window next to the question mark button.
-
Click on the TCP/IP tab.
-
For "Configure IPv4", change the setting from "Using DHCP" to "Off" and then
click on the OK button then click on Apply. Then click
on the Advanced button again and change the setting back to
"Using DHCP" and click on OK and Apply again.
References:
-
"Cannot Allocate Memory" error when trying to ssh or ping or curl due to
unrelated vpn?
Date: January 22, 2013
superuser.com
[/os/os-x]
permanent link
Mon, Oct 28, 2013 10:50 pm
Obtaining the serial number of a Mac OS X system
If you need to locate the serial number for a Mac OS X system, you can
do so by clicking on the Apple icon in the upper, left-hand corner of the
screen then selecting
About This Mac and then clicking on the
More Info... button.
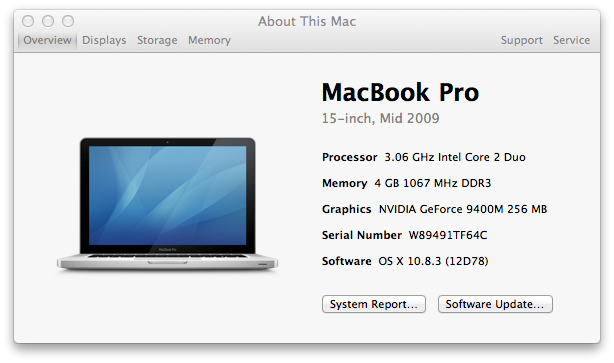
The window also shows the year the system was manufactured, the
processor speed, amount of memory in the system, graphics adapter,
and the version of the operating system as well as the serial number.
If you need to get the serial number from a shell prompt, i.e., a command
line interface, you can use the ioreg command:
$ ioreg -l | awk '/IOPlatformSerialNumber/ {print $4;}'
"W89491TFCCC"If you are on version 10.3 or later of OS X, you can also determine the
serial number by using the system_profiler command.
$ system_profiler SPHardwareDataType | awk '/Serial/ {print $4}'
W89491TFCCC
[/os/os-x]
permanent link
Sun, Oct 27, 2013 5:19 pm
Obtaining the date a web page was last modified
If you wish to know the date a web page was last modified, when you are
visiting the page, you can replace the URL of the page in the address bar
with
javascript:alert(document.lastModified) to see the date
the page was last modified. Note: you can access the address bar by the
keyboard shortcut
Ctrl-L. If you are pasting
javascript:alert(document.lastModified) into Internet Explorer's
address bar, you may find that
javascript: gets stripped off,
so you will need to put it back in front of
alert(document.lastModified)
before hitting
Enter.
One caveat is that this will only work for telling you when the content of
the page was last modified for static web pages. Ones that
include content dynamically, e.g., ads, etc. will show the time that the
page was last modified as when that content for the page was last updated.
I.e., the time may not be the time the author of the page wrote the
information you've found on the page.
On a Microsoft Windows system, you will see a window similar to the following
one open when you enter the javascript command in the address bar.
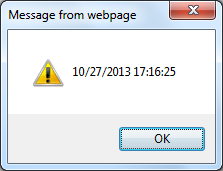
Another technique to attempt to learn when a webpage was created or modified
is to check the Wayback Machine
to see when it archived the site.
[/network/web/browser]
permanent link
Sun, Oct 27, 2013 2:19 pm
IE 9 to 10 Upgrade Failure with Code 9C59 Error
Yesterday, while in the process of bringing all of the software on a laptop
running Windows 7 Professional up-to-date, I tried upgrading Internet Explorer
from version 9 to 10 as
Windows Update listed it as one of the
important updates pending installation on the system. But every time I
tried updating Internet Explorer 9 to version 10 through
Windows
Update, I received a "Code 9C59" error message. I worked on the issue
for all day yesterday before being finally being able to successfully
complete the upgrade from IE 9 to 10 today after uninstalling packages
from the
C:\Widnows\servicing\packages directory via the
pkgmgr /up command.
[ More Info ]
[/network/web/browser/ie]
permanent link
Sun, Oct 27, 2013 2:12 pm
Google +1 button markup validation
At Google's
+1 Button page, Google suggests adding start and end tags similar to
the following at a point in a webpage where you want the plus 1 button to
appear:
<g:plusone></g:plusone>
But if you use those tags on a page and check the page with the
W3C Markup Validation Service, which
checks the validity of HTML code, you will see errors reported such as
the following:
 Line 731, Column 11: element "G:PLUSONE" undefined
Line 731, Column 11: element "G:PLUSONE" undefined
<g:plusone></g:plusone>
An alternative is to use another mechanism provided by Google to have the
button appear. The alternative is to insert the following div
start and end tags where you wish the button to appear.
<div class="g-plusone"></div>
[/network/web/services/google]
permanent link
Sat, Oct 26, 2013 1:20 pm
Determining the version of IE from a command prompt
To determine the version of Internet Explorer from a command prompt without
having to run the program, you can enter the command
reg query "HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer" /v
version | find "version" at the command line:
C:\>reg query "HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer" /v vers
ion | find "version"
version REG_SZ 9.0.8112.16421
[/network/web/browser/ie]
permanent link
Fri, Oct 25, 2013 11:32 pm
Checking uptime and last reboot time on an OS X system
On a Mac system running the OS X operating system, you can determine
how long a system has been up through the Graphical User Interface (GUI)
by clicking on the Apple icon at the top left of the screen then pressing and
holding down the
option button on the keyboard, which will cause
System Information to appear in place of
About This Mac.
Select
System Information, then from within that window select
Software (you can use the downward cursor key to move down through
the list). In the right pane of the window, you will see "Time since boot".
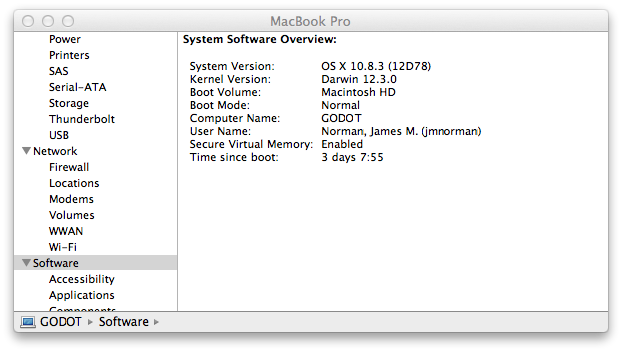
You can also view the system's uptime since the last reboot from
a shell prompt that you have through a terminal window or SSH session by
using the uptime command.
$ uptime
22:10 up 3 days, 7:50, 3 users, load averages: 2.12 2.04 2.00
You can also see when the system was last rebooted and prior boot times
by using the command last reboot.
$ last reboot
reboot ~ Tue Oct 22 14:19
reboot ~ Tue Oct 1 08:16
reboot ~ Fri Sep 27 09:39
reboot ~ Thu Sep 26 14:39
reboot ~ Tue Sep 24 17:03
reboot ~ Sun Sep 22 10:34
reboot ~ Thu Sep 19 20:27
reboot ~ Tue Sep 17 15:19
reboot ~ Tue Sep 17 11:00
reboot ~ Fri Sep 13 10:50
reboot ~ Fri Sep 6 02:44
[/os/os-x]
permanent link
Thu, Oct 24, 2013 11:24 pm
Determining the amount of physical memory on a OS X System
On an Apple OS X system, you can determine the amount of memory in the
system by clicking on the Apple icon at the upper, left-hand corner of
the screen and selecting "About This Mac".

If you need to determine the amount of memory from a shell prompt,
you can use the sysctl command.
$ sysctl -n hw.memsize
4294967296
The sysctl -n hw.memsize command above shows my MacBook Pro
laptop running OS X 10.8.3 has 4 GB of memory (4294967296 bytes = 4 GB).
Another sysctl option you could use is to query
hw.physmem. But, be warned this will result in inaccurate results
on systems with more than 2 GB of memory.
E.g., checking the amount of physical memory with the command
sysctl -n hw.physmem on my MacBook Pro with 4 GB of memory
results in the command telling me the system has 2 GB of memory rather than
4 GB.
$ sysctl -n hw.physmem
2147483648
If you wish to have the number displayed in GB rather than bytes, you can
use memsize.py,
which is a simple python script to convert the output of sysctl -n
hw.physmem from bytes to gigabytes. You can run it from a shell
prompt by typing python memsize.py.
[/os/os-x]
permanent link
Wed, Oct 23, 2013 10:59 pm
Displaying CPU speed from a shell prompt on OS X
If you need to view CPU information, such as processor type or speed from a
shell prompt, you can use the command
sysctl -n machdep.cpu.brand_string.
$ sysctl -n machdep.cpu.brand_string
Intel(R) Core(TM)2 Duo CPU T9900 @ 3.06GHz
Through the graphical user interface (GUI), you could get the information
by clicking on the Apple icon at the upper, left-hand corner of the screen
and selecting "About This Mac".

But the command-line method is sometimes
needed, e.g., when you are remotely logged into a system via SSH or need
to script collection of the information.
You can see other information that is availabe via the sysctl
command by typing sysctl -a.
[/os/os-x]
permanent link
Tue, Oct 22, 2013 10:56 pm
GIMP for OS X
If you are looking for a free, but full-featured, image editing program for OS
X systems,
GNU Image Manipulation Program
(GIMP), which is available for Linux, Solaris, and even Microsoft
Windows operating systems, also, is available
for OS X. Mac OS X versions can be downloaded as .dmg
Apple Disk Image
files.
GIMP's native image format is
eXperimental Computing Facility (XCF), but it also provides
import and export support for image formats such as BMP, GIF, JPEG, PNG,
and TIFF, along with the file formats of several other applications
such as Autodesk flic animations, Corel Paint Shop Pro images, and
Adobe Photoshop documents. Other formats with read/write support include
PostScript documents, X bitmap image and Zsoft PCX. GIMP can also read
and write path information from SVG files and read/write ICO Windows
icon files.
[/os/os-x]
permanent link
Mon, Oct 21, 2013 10:23 pm
Checking CPU Utilization with Activity Monitor or top
If you are using an Apple system running the OS X operating system and
find that it is running slowly, you can check memory and
CPU utilization using
the
Activity Monitor application that comes with the operating
system. You can find the program under
Applications/Utilities.
If you wish to see which application is using the greatest amount of
memory, you can click on the Real Mem column header to display the list
of processes running on the system ordered by memory utilization. To order
the list by the percentage of CPU utilization, you can click on the % CPU
column header to see which application is most heavily using the CPU.
In the example below, Entourage is using 40.4% of CPU cycles and 102.7
megabytes of memory.
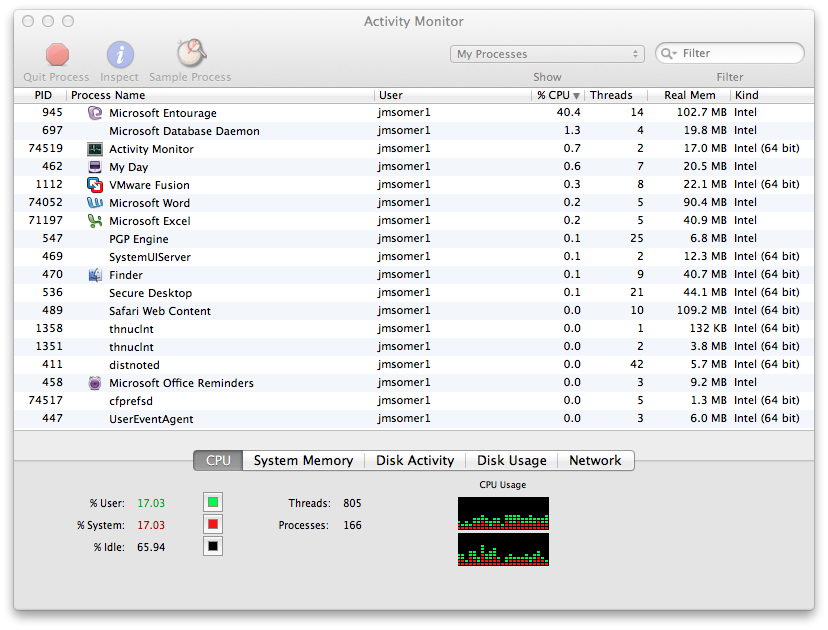
Another utility that comes with the OS X operating system which you can
use to check on the resources used by applications is the top
utility which can be run from a shell prompt, which you can get by running
the Terminal program found in Applications/Utilities. You will
get a text display that provides information on system performance by
running the top command. The command top -o cpu
will order the displayed list of running processes by CPU utilization.
Processes: 165 total, 3 running, 13 stuck, 149 sleeping, 718 threads 22:04:55
Load Avg: 1.50, 2.52, 2.81 CPU usage: 25.11% user, 22.83% sys, 52.5% idle
SharedLibs: 796K resident, 0B data, 0B linkedit.
MemRegions: 30234 total, 1308M resident, 45M private, 1267M shared.
PhysMem: 1691M wired, 1196M active, 1187M inactive, 4074M used, 21M free.
VM: 335G vsize, 1026M framework vsize, 4076678(0) pageins, 3624731(0) pageouts.
Networks: packets: 6273654/3871M in, 5724447/3985M out.
Disks: 7453865/220G read, 6472245/405G written.
PID COMMAND %CPU TIME #TH #WQ #PORTS #MREG RPRVT RSHRD RSIZE
945- Microsoft En 77.5 14:43:34 14/1 4 258 1288+ 69M+ 38M 99M+
90973 top 8.0 00:02.45 1/1 0 24 30 1280K 216K 2028K
697- Microsoft Da 2.0 27:09.14 3 1 105 199 39M 5892K 41M
1329 vmware-vmx 1.6 09:41:27 15 1 260 555 4704K 47M 956M+
0 kernel_task 1.4 01:57:04 88/2 0 2 652 65M 0B 411M
456 Terminal 0.4 00:29.01 5 1 147 229 7556K 7192K 16M
87 WindowServer 0.4 01:43:11 4 1 547 4074 13M 88M 56M+
74- AgentService 0.1 08:47:21 8 1 89 103 1436K 1384K 2928K
489 WebProcess 0.1 03:18:09 10 1 266- 2738- 96M+ 121M 183M+
462- My Day 0.1 09:51.57 7 2 171 340- 11M- 14M 18M-
49 mds 0.1 32:49.92 7 5 284- 397 36M- 3176K 63M-
74052- Microsoft Wo 0.1 00:27.20 4 2 163 630 9892K 22M 17M
71197- Microsoft Ex 0.1 00:49.76 5 3 153 517 7832K 79M 17M
187- SymAutoProte 0.0 15:55.03 8 1 74- 227- 21M- 2060K
The list of processes above has Microsoft Entourage at the top at
77.5 %CPU.
[/os/os-x]
permanent link
Sun, Oct 20, 2013 10:12 pm
Excel end of month function EOMONTH
Excel provides an
EOMONTH function that will allow you to
determine the last day of a particular month that is a certain number of
months away from a specified date. The syntax for the function is as follows:
EOMONTH(start_date, months)
Start_date is a date which can be entered as a text string between
quotation marks, e.g. "10/20/2013" or "2013/10/20". Or it can refer
to a cell that contains a date, e.g. =EOMONTH(A2,1), which,
if cell A2 holds the relevant date will display the date
for the day that is the end of the month one month from the day in cell
A2. Note: if you con't format the cell where you want the result displayed
as a date, Excel will display the result as a serial number because it
stores dates as sequential serial numbers. If your workbook uses the
1900 date system, then January 1, 1900 is day 1, i.e., serial number 1.
E.g., for the formula =EOMONTH("10/20/2013",4), Excel would
display 2/28/2014 in the cell where the formula was entered,
if that cell was formatted to hold a date.
You can use negative numbers for months, e.g.
=EOMONTH("10/20/2013",-2) would produce 8/31/2013.
Error conditions:
- If start_date is not a valid date, EOMONTH returns the #NUM! error value.
- If months is not an integer, it is truncated.
- If start_date plus months yields an invalid date, EOMONTH returns the
#NUM! error value. E.g., =EOMONTH("10/20/2013",-2000)
would return the #NUM! error.
If you are using Excel 2000 and you see the error #Name? when
you use the function, you need to install the Analysis ToolPak to make the
function available. After you install the Analysis TookPak, make sure that
the Analysis TookPak is enabled by clicking on Tools
then selecting Add-Ins and making sure Analysis TookPak
is checked.
[/os/windows/office/excel]
permanent link
Sat, Oct 19, 2013 10:01 pm
Pasting from PuTTY to Linux
If you are using
PuTTY for
SSH or telnet
connections to a Linux system and need to copy and paste text from
the Microsoft Winodws system on which PuTTY is running into a file or
application on a Linux system, you can paste the data you've copied into
the clipboard on the Windows system into the file/application on the
Linux system by hitting both buttons on your mouse simultaneously or by
hitting the
Shift and
Insert keys simultaneously.
[/os/windows/network/ssh/putty]
permanent link
Fri, Oct 18, 2013 11:06 pm
Last Update Registry Entries
If you need to know when a Microsoft Windows system was last updated using
the Windows Update feature, you can find the information in the registry
by running
regedit and navigating to
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\Results. Beneath this location you will find
Detect,
Download, and
Install keys.
Beneath each of those you will find a
LastSuccessTime value with
a timestamp in the form yyyy-mm-dd hh:mm:ss
(year-month-day hours:minutes:sectonds), e.g.,
2013-10-18 20:25:19.
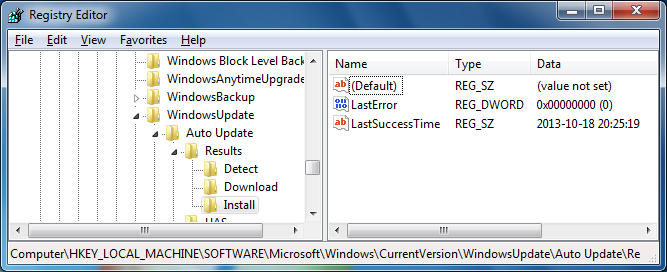
You can display all of the values from a command prompt usin the reg
query command below:
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\Results" /s
E.g.,
C:\>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wind
owsUpdate\Auto Update\Results" /s
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto
Update\Results\Detect
LastSuccessTime REG_SZ 2013-10-18 17:17:17
LastError REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto
Update\Results\Download
LastSuccessTime REG_SZ 2013-10-16 23:05:55
LastError REG_DWORD 0x0
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto
Update\Results\Install
LastSuccessTime REG_SZ 2013-10-18 20:25:19
LastError REG_DWORD 0x0
If you just wish to view a particular one, such as the value for the
LastSuccessTime for installation of an update, you can use a
command such as the following:
C:\>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto Update\Results\Install" /v LastSuccessTime
Put the value to be queried after the /v argument to the
command.
E.g.:
C:\>reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Wind
owsUpdate\Auto Update\Results\Install" /v LastSuccessTime
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowsUpdate\Auto
Update\Results\Install
LastSuccessTime REG_SZ 2013-10-18 20:25:19
[/os/windows]
permanent link
Thu, Oct 17, 2013 11:03 pm
Forgotten No-IP DUC Password
I needed to change the
Dynamic DNS (DDNS) host name used by the
No-IP DUC 2.2.1 client on a system on which I had installed the
client software years ago. The system was on a LAN with a router
that had a dynamically assigned external address provided by the
company's Internet Service Provider (ISP). I used
No-IP's DDNS service to
have the system contact a DDNS server provided by No-IP which would
note the IP address from which it was contacted and associate that
address with a
FQDN,
e.g., acme.example.com, so that I could connect to the site for
troubleshooting without having someone at the site determine what
the site's currently assigned IP address might be by going to
a site like
WhatIsMyIP, which
is a site I usually have people go to when I need them to provide
me with their current IP address. The No-IP DUC client was running
on the system as a system service and the icon for the software
was in the notification area, aka the system tray, but I found
that the password I thought I had set for it didn't work and I
couldn't remember what it might be.
Since it was very late and I was in a hurry to make the change,
I thought I could probably find a registry key where the password
was stored and fix the problem more quickly by blanking out the
contents of that registry key. For DUC 2.2.1, the relevant registry
key, which can be accessed by the Microsoft Windows built-in
utility regedit, is
HKEY_LOCAL_MACHINE\SOFTWARE\VitalWerks\TrayPassword,
which is a REG_SZ key. To remove the tray password, you can
simply double-click on the key and remove the value, which is stored
in encrypted form, associated with it. You can then access the
options for the software without a password. Note: you may only see
this key under HKLM\SOFTWARE if the DUC client has
been configured to run as a system service. If it isn't look under
HKEY_CURRENT_USER.
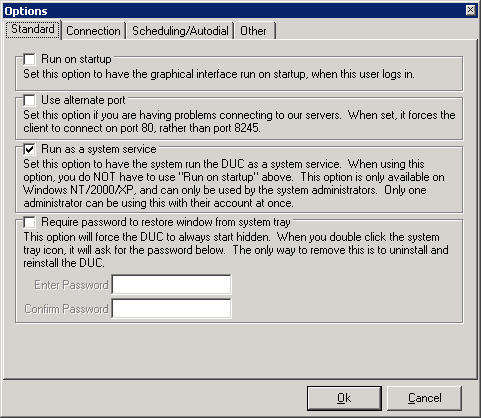
To reset the password, click on the No-IP icon in the system tray
and choose Show or double-click on it. Then, click on
Options and, under the Standard tab, check the box for
"Require password to restore window from system tray". The text
associated with that option states "This option will force the DUC
to always start hidden. When you double click the
system tray icon, it will ask for the password below.
The only way to remove this is to uninstall and
reinstall the DUC." But by removing the value from
HKEY_LOCAL_MACHINE\SOFTWARE\VitalWerks\DUC\TrayPassword, which
you can do if you are logged in under the administrator account, you can skip
the reinstallation.
I don't see being able to remove the password via the registry
as a security issue, since doing so requires administrator
privileges; it's simply a shortcut that saves the time of
reinstalling the software.
Note: the current version of the DUC software, which is 4.0.1
does not store the password at this location. If you configure it
to run as a service, there is a
HKEY_LOCAL_MACHEINE\SOFTWARE\Vitalwerks key will be created
at the time you set the software to run as a service, but there is no
TrayPassword key beneath it.
[/network/dns]
permanent link
Wed, Oct 16, 2013 5:51 pm
Finding large files on a Ubuntu Linux system
I encountered an issue of low available disk space on a Ubuntu Linux system.
The system had an old 30 GB disk drive and I needed to determine what files
were consuming the most space beneath a user's home directory. So I made
the user directory the working directory with
cd /home/doe
and used the
find command.
The synatax that can be used for the find command to find all files
greater than a certain size in megabytes (MB) is
find starting_directory -type f -size
+numM -exec ls -lh {} \;.
| starting_directory | Files in and below this directory
will be checked. You can use a period to specify the current directory or
specify a path name. |
| num | A number specifying the file size. You can put a
"b" at the end to use a number in bytes,
a "k" for a number in kilobytes, or an "M" to use a number in
megabytes, e.g. 100M for files greater than 100 megabytes in
size. |
The -exec parameter tells find to execute the ls -lh
command, the output of which it will check for the specified file
size. The -lh tells ls to use a "long" style
display for each line with file sizes displayed in a more human-readable
format.
E.g., the following command will search the current directory and its
subdirectories recursively for all files larger than 100 MB in size.
# find . -type f -size +100M -exec ls -lh {} \;
-rw-r--r-- 1 doe doe 105M Oct 16 14:26 ./.mozilla/firefox/d0i4yvwz.default/urlclassifier3.sqlite
-rw-r--r-- 1 doe doe 634M Nov 19 2012 ./.thunderbird/p8c6q04i.default/global-messages-db.sqlite
-rw------- 1 doe doe 12G Nov 16 2012 ./.thunderbird/p8c6q04i.default/ImapMail/192.168.2.5/logs.sbd/daily
-rw------- 1 doe doe 160M Apr 8 2012 ./.thunderbird/p8c6q04i.default/ImapMail/192.168.2.5/sent-mail
-rw------- 1 doe doe 6.8G Dec 12 2012 ./.thunderbird/p8c6q04i.default/ImapMail/192.168.2.5/INBOX
find: `./.gvfs': Permission deniedThe above find command displays the permissions on the files,
the file owner and group, and a timestamp for the file in addition to the
file name and size. If you wish to just display the file names and sizes,
you can pipe the output through awk to just display the sizes
and file names. The file size appears in the 5th column and the file name
appears in the 9th column, so you can instruct awk to only
display the data from those two columns.
# find . -type f -size +100M -exec ls -lh {} \; | awk '{print $5 " " $9}'
find: `./.gvfs': Permission denied
105M ./.mozilla/firefox/d0i4yvwz.default/urlclassifier3.sqlite
634M ./.thunderbird/p8c6q04i.default/global-messages-db.sqlite
12G ./.thunderbird/p8c6q04i.default/ImapMail/192.168.0.5/logs.sbd/daily
160M ./.thunderbird/p8c6q04i.default/ImapMail/192.168.0.5/sent-mail
6.8G ./.thunderbird/p8c6q04i.default/ImapMail/192.168.0.5/INBOXIn this case, I can see that the largest files are associated with
Firefox and Thunderbird.
Note: if you wish to find a file that is exactly a certain size in MB, you
would omit the plus sign, "+" before the number. E.g.,:
# find . -type f -size 105M -exec ls -lh {} \; | awk '{print $5 " " $9}'
find: `./.gvfs': Permission denied
105M ./.mozilla/firefox/d0i4yvwz.default/urlclassifier3.sqliteIf you wish to find all files below a certain size, you would prefix the
number with a minus, "-".
[/os/unix/linux/ubuntu]
permanent link
Tue, Oct 15, 2013 10:40 pm
Deleting a command from your bash history
The
bash
shell is a commonly used
shell on
Unix/Linux systems. The history feature which is available with the bash
shell is very useful, allowing you to easily recall and reuse previously
entered commands without retyping them. E.g., if you had entered a long
ssh command with a lot of options, you can simply hit
Ctrl-R
and type
ssh to recall the last ssh command entered. You
can then edit the command or simply hit
Enter to execute the
same command again.
Occasionally, though, you may not want something you've typed at
the shell prompt to remain in your history file. E.g., I've occasionally
inadvertently typed a password at a point where a password prompt hadn't
appeared. You can delete a particular command by using history -d
num where num is the number assigned to the command
in the history file, which you can see by typing history with
no parameters. After deleting the command use history -w to
write the update to your ~/.bash_history file to disk.
E.g., If I saw that command 245 was showing the password I
mistakenly typed, I could use the following commands to ensure that
the password couldn't be viewed by anyone who might gain access to the
history information:
$ history -d 245
$ history -w
If you wished to delete all the commands stored in the history file, you
could use history -c followed by history -w.
[/os/unix/bash]
permanent link
Tue, Oct 15, 2013 10:16 pm
Moving a window
On a Ubuntu Linux system, if you need a window from one area of the screen
to another, you can use the keyboard shortcut
Alt-F7 to move the
current window. Once you've entered the keyboard shortcut, a hand icon will
appear in the window and you can use the mouse, touchpad, or the
cursor keys on the keyboard to move the window about. When you hit
Enter, the window will remain at the position to which you've
moved it.
[/os/unix/linux/ubuntu]
permanent link
Mon, Oct 14, 2013 10:52 pm
Determining the file system type
If you need to determine the
file system type for
a mounted drive on a linux system, one method you can use is to use the
command
df -T.
$ df -T
Filesystem Type 1K-blocks Used Available Use% Mounted on
/dev/sda1 ext4 306643128 4768956 286297596 2% /
udev devtmpfs 497680 4 497676 1% /dev
tmpfs tmpfs 203152 812 202340 1% /run
none tmpfs 5120 0 5120 0% /run/lock
none tmpfs 507880 288 507592 1% /run/shm
/home/joe/.Private ecryptfs 306643128 4768956 286297596 2% /home/joe
df displays the
amount of disk space available on the file system containing each
file name argument. If no file name is given, the space available
on all currently mounted file systems is shown. Disk space is
shown in 1K blocks by default, unless the environment variable
POSIXLY_CORRECT is set, in which case 512-byte blocks are used. The
-T parameter results in the file system type being printed
as will using --print-type.
If you know the device name, e.g., /dev/sda1, you can
specify it on the command line to eliminate extraneous information.
$ df -T /dev/sda1
Filesystem Type 1K-blocks Used Available Use% Mounted on
/dev/sda1 ext4 306643128 4776944 286289608 2% /
You can eliminate additional extraneous information, such as the 1K-blocks,
used, available, and use% fields by piping the output into awk.
E.g., the following command would print only the information for columns
1, 2 and the last column, which is "mounted on".
df -T /dev/sda1 | awk '{print $1,$2,$NF}'
Filesystem Type on
/dev/sda1 ext4 /For awk, NF represents the number of fields on a line
and $NF prints the last one. For just the filesystem type,
you could print only the information from column 2 and eliminate any
results for the first header line by using grep -v "Type":
$ df -T /dev/sda1 | awk '{print $2}' | grep -v "Type"
ext4References:
-
5 Methods to Identify Your Linux File System Type (Ext2 or Ext3 or Ext4)
By Ramesh Natarajan
Date: April 18, 2011
The Geek Stuff
[/os/unix/linux]
permanent link
Sun, Oct 13, 2013 10:10 pm
Verifying an SSL Certificate
If you have an SSL certificate on a Linux or Unix system, you can check it
using the
openssl command with
openssl verify
/path_to_certificate/certificate, e.g., as below:
# openssl verify /etc/ssl/certs/example.crt
/etc/ssl/certs/example.crt: /C=US/CN=example.com
error 18 at 0 depth lookup:self signed certificate
OK
In the case above, the country specified with the domain is the
United States as shown by /C=US and the common name
specified for the domain when the certificate was created and for which the certificate should be valid is example.com
as shown by /CN=example.com.
The certificate is self-signed, which results in the error 18
message.
The dates for which the certificate is valid can be specified with
openssl x509 -in /path_to_certificate/certificate -text | grep Not
as shown below:
# openssl x509 -in /etc/ssl/certs/example.crt -text | grep Not
Not Before: Oct 11 21:06:30 2013 GMT
Not After : Oct 11 21:06:30 2014 GMTIn the case above, the certificate is valid from October 11, 2013
through October 11, 2014. After October 11, 2014, anyone visiting the
website for which the certificate was used for HTTPS connections will
be warned by his/her browser that there is a problem with the certificate
because it will have expired.
X.509 specifies
standard formats for public key certificates, certificate revocation
lists, attribute certificates, and a certification path validation
algorithm.
References:
-
OpenSSL: The Open Source toolkit for
SSL/TLS
-
Troubleshooting with openssl
Date: February 11, 2010
MoonPoint Support
[/security/encryption/openssl]
permanent link
Sat, Oct 12, 2013 8:20 pm
Adding a hyperlink to a spreadsheet in Google Docs
In Microsoft Excel, if you wish to add a hyperlink, i.e., a
URL, to
text in a cell, you can click on
Insert and select
Hyperlink. For a spreadsheet in Google Docs, the process is to
click in the cell where you want the hyperlinked text to appear and
then use a formula similar to the one below:
=hyperlink("example.com/link.html"; "Example page")
You start the formula with =hyperlink then within
parentheses put the URL with or without the "http://", then a
semicolon and then within parentheses the text you wish to have
displayed for the hyperlink.
One thing to note, if you hover your cursor over the hyperlink,
you will see that google prepends a www.google.com/url?q=
at the beginning of the hyperlink you provided and additional parameters
at the end such as &usd=x&usg=xxxxxx.
If you wish to remove the hyperlink, right-click on the cell and
choose Remove hyperlinks. If you wish to restore the hyperlink,
right-click on the cell and choose Show hyperlinks.
[/network/web/services/google]
permanent link
Sat, Oct 12, 2013 7:51 pm
You may be a victim of software counterfeiting
I had to enter a new product key on a Windows 7 Professional system
that was displaying the message "You may be a victim of software
counterfeiting." When I clicked on a link to "go online and resolve now",
I was informed "The product key used to activate Windows on your PC is
already in use on another PC or has been blocked by Microsoft."
[ More Info ]
[/os/windows]
permanent link
Fri, Oct 11, 2013 12:08 pm
Nobr tag deprecated
While checking an old webpage I created in February of 2009 with the
W3C Validator, I received an error
for the following code:
<nobr><code>%SystemRoot%\Web\Wallpaper\Ripple.jpg</code></nobr>
The error reported by the W3C Validator, which checks the validity of
HTML code was as follows:
Line 387, Column 6: element "NOBR" undefined
I thought "why is the validator complaining about the NOBR tag; that's a valid
tag." But at
Replace NOBR Tags with CSS I discovered, though the tag may still work in
major browsers, the NOBR tag has been deprecated. Though most of the commenters
on the page noted they hadn't even heard of the NOBR tag, which tells a browser
not to break a line of text enclosed within the <nobr> and
</nobr> tags, one commenter noted
"Bah humbug, KIDS these days! Never heard of nobr. Bet they’ve never played a
45rpm record or an 8-track either. lol"; I'm old enough to have done both.
The recommendation in the article was to use
CSS, instead, to achieve the
desired effect. E.g., a span tag such as the following:
<span style="white-space:nowrap;">
Though the article suggested creating a nobr CSS class.
.nobr { white-space:nowrap; }
Someone else suggested using { white-space:pre; }.
I decided to replace the tag with a CSS span tag so the validator wouldn't
complain about it, making the line:
<span style="white-space:nowrap;"><code>%SystemRoot%\Web\Wallpaper\Ripple.jpg</code></span>
[/network/web/html/css]
permanent link
Thu, Oct 10, 2013 10:11 pm
Using TeamViewer on Ubuntu Linux to manage other systems
TeamViewer provides
software that will allow you to remotely control a system from another
system. You can use it to remotely troubleshoot a system, share a desktop
remotely, or transfer files between systems. The software runs on Android,
iOS, Linux, OS X, Windows, Windows Phone, and Windows RT systems.
You don't have to install client software on a Linux system to use it as
a remote management system to manage other systems. You can simply use
a browser, such as Firefox, to connect to the remote system through the
TeamViewer website. But installing the TeamViewer client software on a
Linux system and using it will give you additional features not present
in the browser-based method. E.g., you can adjust the screen resolution
for the client's display of the remote desktop, take screen snapshots
on the remote system, transfer files, etc.
[
More Info ]
[/os/windows/software/remote-control/teamviewer/ubuntu]
permanent link
Thu, Oct 10, 2013 12:05 pm
ASCII Art
Before today's
Graphical User
Interfaces (GUIs), computer users were presented with an entirely
text-based interface. Those old enough to remember those days may also remember
ASCII art where
artists constructed images entirely from the characters available to them
via their keyboards, i.e., the 95 printable characters available from the
128 possible characters one could have using just 7
bits. The term "ASCII art" was
used because the characters were defined by the
ASCII Standard from 1963, a
standard that on March 11, 1968 U.S. President
Lyndon Baines
Johnson mandated that all computers purchased by the U.S. government
support.
An example of such art is the "smiling dragon" below.
|\_,
I, \, /|
,__/______\ _____/ |
,___, ,/__ \/ ,/
// \, |/ \. / ,/ _______,
II @@ \, ,/\____| ,/ _____/ __\
II \____/ /' I__ ____/ _/ \
\\ ___ //\_/ _/
\_______ 'I` // \\_____ \
\_________________/ // \____.\ |
\_____ \\. \_\____/\|
, \_ \\. \_/ '
/ \ ______ \ ,/ \\. \|
/.. \_/ \__,_ __/ ,/ // _______|
/.....\ \_\v \_ ,/ // / \
/_______\, \_\_ / || /
_/ \\_\_ |__, // / _______,
_/ \_ \_\_ \// I ___/ \_
_/ \_ \ \_ \|_____I__/ \,
__/ \_/ I \ \_ \_
,_______/ \__I I \_ \ ________ \
_/ __/ \_____\ I \ \_ _/ \ I
/ _/ /_// \ / \ \___/ I
|/ // //\_____ _/ \_ \____ I
` ` |/ I\___ \_____/ \_ \__________________I
` I\___, /\___, \
,__I\____, ,___ I \________, I
_/ \_____, _/ \____\_____ \______/ I
,/ . \____/ ,/ . \______/ |__/
| /| /| \_____/ | /| /| _ \____/
|__/ |__/ |__/ \_____|__/ |__/ |__/ \__________________/
For anyone nostalgic for the days when online art was text-based,
textfiles.com
has a subdomain, Art Scene
where you can peruse some of the old ASCII art.
Some of the oldest examples of ASCII art were creations from the 1960's by
Kenneth Knowlton,
a computer graphics pioneer and artist who worked at
Bell Labs.
[/graphics]
permanent link
Wed, Oct 09, 2013 10:39 pm
Inserting text at the beginning and end of lines with vi's regexp
The
vi and
Vim text editors support
the use of
regular expressions
(abbreviated regex or regexp) for editing files.
In a regular expression ^ signifies the beginning of a line and
$ specifies the end of a line. To have an operation apply
to multiple lines at once, you can specify a range of lines, e.g.
16,25. To have the operation apply starting with the current
line, you can use a period, ., to represent the current line,
so .,25 would mean apply the operation to the current line
and all subsequent lines up to and including line 25. Or you could specify
that the operation should be applied from the current line to the end of
the file by using $ to represent the last line in the file,
e.g., .,$.
Or you can have an operation apply to every line in a file
using
%. E.g., the following line would insert
123
at the beginning of every line in a file.
:% s/^/123/
The s indicates a substitute operation will follow and the
forward slashes, / delineate the pattern to be replaced and
the replacement pattern. In the above case, the ^ indicates the
beginning of the line and the replacement pattern is 123.
When you are using / to delineate the patterns, it has a special
meaning and if you want to use it in a pattern you have to "escape" its
special meaning with an
escape character, which is the backslash, \.
E.g. to insert </td> at the end of every line from the
current line to line 25, the following regular expression could be used:
.,25 s/$/<\/td>/
Supposing that I wanted to put a <td> at the beginning
of each line and a </td> at the end of each line from the
current line through line 25. In that case I need to store the characters
in between the beginning and end of a line. You can specify text to be
stored by using parentheses, ( to mark the beginning of the
area on the line to be stored and ) to mark the end. Since a
period, ., represents any character and an asterisk, *
represents multiple occurrences, ^(.*)$ would store
all the characters on the line between the beginning and end of a line.
You must also "escape" the ( and ) with the
backslash escape character as well. To reuse the characters you have stored
you recall them with \1 ("1" is the number one). If you had
multiple occurrences of characters enclosed in parentheses, the second
instance could be recalled with \2.
The line below would insert a <td> at the beginning of lines 16
through 25 and a </td> at the end of the lines.
:16,25 s/^\(.*\)$/<td>\1<\/td>
If you wished to have the editor prompt you as to whether you wanted
the change made on a line, you could add a /c option at the
end of the command to the editor. The command below would perform the same
action as the one above on every line from line 16 to the end of the file,
but would prompt you at each line as to whether the change should be made.
:.,$ s/^\(.*\)$/<td>\1<\/td>/c
You would see each line highlighted one by one as you progressed through the
file with the following prompt each time.
replace with <td>\1<\/td> (y/n/a/q/l/^E/^Y)?
Answering y would result in the replacement occurring whereas
answering n would result in the line remaining unchanged.
In this case, there is also a simpler means for inserting the table td
tags at the beginning and end of each line as below:
s/.*/<td>&<\/td>
Again the .* represents the search pattern, which is every
character on the line. The ampersand, &, also has a special
meaning; it is the text that matches the search pattern, so putting it between
the two tags results in all the text originally on the line remaining on
the line. The / at the end of the replacement pattern can be
eliminated if there is nothing following it such as a /c.
References:
-
Adding characters at the start and end of each line in a file
May 2, 2012
Stack Overflow
-
Search and replace
Vim Tips Wiki
[/software/editors/vi]
permanent link
Wed, Oct 09, 2013 8:56 pm
Survey and Correlation Data from 2013 Search Engine Ranking Factors
At
2013 Search Engine Ranking
Factors Survey & Correlation Data, I found some interesting information
from a survey of search marketers regarding how search engines may rank
websites. Many of the factors that may lead to an increase in page ranking
didn't surprise me, but some of those that were listed as resulting in
a decrease in a page's ranking did surprise me, e.g., the number of
characters in a page's title and the use of hyphens
in URLs, which I often use. I've factors expected to have negative results
below:
| Page Has Twitter Card Markup |
-0.02 |
| # of Large Images (Greater Than Or Equal to 1024X768px) |
-0.02 |
| Folder Depth of URL (# of Trailing Slashes) |
-0.02 |
| # of Videos On Page |
-0.03 |
| Page Contains Google+ Authorship Markup |
-0.03 |
| # of Google Adsense Slots in The Page |
-0.03 |
| Domain has Numbers (example123.com) |
-0.03 |
| # of Hyphens in Domain Name |
-0.03 |
| Total Area of Adsense Slots on Page |
-0.04 |
| # of Characters in the Title |
-0.04 |
| URL Contains Hyphens |
-0.04 |
| Total Length of the Full Domain (www.subdomain.pld.com) |
-0.09 |
| URL Length in Characters |
-0.10 |
| Response Time of Page in Seconds |
-0.10 |
[/network/web/search/SEO]
permanent link
Tue, Oct 08, 2013 10:39 pm
Keeping an SSH connection alive with ServerAliveInterval
While working on a Ubuntu Linux laptop, I found my SSH sessions to a Linux
server were being dropped after a few minutes when I switched to other tasks
on the laptop. Using the
ServerAliveInterval parameter when
establishing the SSH connection allowed me to alleviate the problem of
idle connections being dropped. E.g., I could use:
$ ssh -o ServerAliveInterval=5 -o ServerAliveCountMax=1 jdoe@a.example.com
Setting the ServerAliveInterval to 5 will send a "heartbeat" signal
to the server every 5 seconds to keep the connection alive. Setting
ServerAliveCountMax to 1 means that when the time comes to send
another keepalive signal, if a response to the last one wasn't received, then
the connection will be terminated.
The TCPKeepAlive setting could also be used, but, if there
is an intervening firewall it might be configured to drop the empty TCP ACK
packets that would be sent. The ServerAliveInterval setting
sends data through the SSH connection, so from the perspective of the firewall
the packets are the same as any other encrypted packet.
References:
-
How does tcp-keepalive work in ssh?
Date: March 12, 2012
Unix & Linux Stack Exchange
-
Keeping Your SSH Sessions Alive Through Pesky NAT Firewalls
Date: June 3, 2005
Steve Kehlet's Pages
[/network/ssh]
permanent link
Mon, Oct 07, 2013 8:46 pm
Main Id element in Blosxom's story.html
I upgraded Blosxom today from version 2.0 to 2.1.2. I normally validate
the HTML code in webpages and blog entries I've created with
the
W3C Markup Validation Service,
which is a free service provided by the
World Wide Web Consortium (W3C)
for verifying that HTML code in a file you upload to the service, or at a
URL you request be checked by the service, is correct. I've always gotten
errors similar to the one below when I've checked blog entries, but have
never taken the time to figure out how to fix the problem, which I thought
was in the Blosxom Perl code.
Line 210, Column 10: ID "MAIN" already defined
<div id="main">
An "id" is a unique identifier. Each time this attribute is used in a
document it must have a different value. If you are using this attribute
as a hook for style sheets it may be more appropriate to use classes
(which group elements) than id (which are used to identify exactly
one element).
I still got those errors when checking blog entries with the new version,
but decided that I should deal with the problem at last. I found that the
problem was within the story.html file I was using for Blosxom.
I hadn't changed that file when I upgraded Blosxom. The file had the following
contents:
<div id="main">
<a name="$fn"><b>$title</b></a>
<br>
<br>
$body
<p>
[<a href="$url$path">$path</a>]
<a href="$url/$yr/$mo_num/$da#$fn">permanent link</a>
</p>
</div>
Since that was specifying that a <div id="main">
be used for each blog entry, whenever I would check a Blosxom blog page
with multiple entries, at least one of the error messages would be reported
by the W3C Markup Validation Service, since "id=main" should appear only
once within a webpage since it should specify a style in
CSS for a
single, unique element on a page. If there were 10 entries on a page, then I
would see 9 such error messages reported.
So I changed "id=main" to "class=main", since
unlike "id", the class selector is used to specify a style for a group of
elements on a page - see
The id and class
Selectors for an explanation of the two elements.
In the style.css file I specified for the blog in the
head.html file for Blosxom, I inserted the following line just
to have something there that I could alter later if I wanted to format entries
differently. There hadn't been an element for "main" there previously.
div.main {text-align:left;}
In the head section of the head.html file, I had
the following line to bring in the stylesheet I use for the blog.
<link rel="stylesheet" href="/css/style.css" type="text/css">
[/network/web/blogging/blosxom]
permanent link
Mon, Oct 07, 2013 7:40 pm
Blosxom upgrade
Today while checking the server's Apache error log file, I noticed error
messages that appeared to be related to
Blosxom, which I've been
using for this blog, which runs on a Linux server, for almost 9 years now. I
found the error messages had been occurring since at least the beginning of the
year and they may have been occurring for a much longer period. When I checked
on the error messages, I found a February 3, 2013 posting at
[Blosxom]
server error where someone reported similar error messages, I
found someone responding
here that
the messages could be due to the absence of the
XML::Parser Perl
module. The responder mentioned that the module is reqiured by the
atomfeed plugin, which I don't use. His message also referenced the categories
plugin, which I don't have, either. But I thought I would check on whether
the
XML::Parser module was present on the system. It wasn't,
so I installed it, but that didn't stop the error messages from occurring
in the Apache server's log file. I then noticed that Blosxom was not up-to-date.
I had version 2.0 on the system while the current version is 2.1.2.
Blosxom is available from SourceForge
at blosxom :: the zen of blogging.
Upgrading from the 2.0 version to the 2.1.2 version was very easy. I made
a backup copy of the existing blosxom script in case anything went wrong. I
then unzipped and untarred the
gunzip blosxom-2.1.2.tar.gz file I downloaded.
gunzip blosxom-2.1.2.tar.gz
tar -xvf blosxom-2.1.2.tar
The only file I needed was the blosxom one, which I edited
to set the configurable variables, which are at the top of the
file, to those I had for the 2.0 version. I also set the plugins directory
variable, plugin_dir, in the Plugins (Optional)
section of the file, which is after the Configurable variables
section, since I'm using a calendar plugin for Blosxom. I then copied the
new blosxom file over top the old one and then verified that the blog was
still working as it had been.
When I checked the latest blog entry with the
W3C Markup Validation Service,
which allows one to verify that a webpage is coded correctly in HTML,
I saw the warning below:
Character Encoding mismatch!
The character encoding specified in the HTTP header (utf-8) is different
from the value in the <meta> element (iso-8859-1). I will use the value
from the HTTP header (utf-8) for this validation.
The issue was reported as a warning rather than an error and shouldn't
effect the display of entries in anyone's browser, but I thought I should
fix it. I found the following line in the head.html file for
Blosxom.
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
I replaced it with the following line:
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
Since I didn't change head.html as part of the upgrade,
that issue has likely always been there; I don't know why I never noticed
it before when checking blog entries with the W3C Markup Validation Service.
The upgrade didn't eliminate the error messages in the Apacehe server
log file, but at least I am now at the current version of Blosxom.
[/network/web/blogging/blosxom]
permanent link
Mon, Oct 07, 2013 5:16 pm
Perl Module XML::Parser
I installed the Perl module
XML::Parser, which is a Perl module for parsing
XML documents.
# perl -MCPAN -e shell
Terminal does not support AddHistory.
cpan shell -- CPAN exploration and modules installation (v1.7602)
ReadLine support available (try 'install Bundle::CPAN')
cpan> install XML::Parser
...
cpan> exit
After exiting from cpan, I checked on the module installation:
# perldoc -l XML::Parser
/usr/lib64/perl5/site_perl/5.8.8/x86_64-linux-thread-multi/XML/Parser.pm
During the installation I was advised that a later version of CPAN was
available for the system, so I updated it as well, which took quite awhile.
I accepted the default answers for all of the yes/no questions posed during
the installation.
cpan> install Bundle::CPAN
...
cpan> reload cpan
.......................................................................................................................................................................................................
199 subroutines redefined
cpan> exit
[/languages/perl]
permanent link
Mon, Oct 07, 2013 4:53 pm
Which Perl modules are installed on a system
There are a number of methods you can use to determine which Perl modules
are installed on a system. I use a script,
list-modules.pl. To use the script change the permissions on it so
that it can be executed with
chmod 755 list-modules.pl. The
script produces an HTML file as output. You can use
perl
list-modules.pl >list-modules.html to produce the file or you
can put the script in your cgi-bin directory on a webserver and access
it via a browser to see the installed modules on the system
(
example output).
Another script that can be run from a shell prompt to show you the installed
Perl modules on a system is
find-modules.pl. To use it, you can change the permissions with
chmod and then simply use ./find-modules.pl.
(example output).
Another means of checking for installed Perl modules is through
Lister.pm,
which was developed by Brian D.
Foy and which can be found at GitHub
at app-module-lister
(example output).
Lister.pm can
be run at a shell prompt with perl Lister.pm, after changing
permissions on the file, e.g. chmod 755 Lister.pm, or you can
also make the results available through a webpage, for instance, if you don't
have access to a shell prompt on a webserver via SSH, by putting the file
in a cgi-bin directory on the server and renaming the file to
something like Lister.cgi, if scripts need the .cgi extension on
the server. It can provide version information for some modules.
Another method is to use the perldoc module_name command,
if perldoc is installed on the system. You should see documentation
information if a module is installed, but the message "No documentation found
for module_name", if the module isn't installed.
$ perldoc XML::Parser
No documentation found for "XML::Parser".
You can also use the -l argument to perldoc, which
will report the location of the file for the module, if one is present or also
report "No documentation found", if the module can't be found.
# perldoc -l LWP::Simple
/usr/lib/perl5/vendor_perl/5.8.8/LWP/Simple.pm
Note: The perldoc method will show modules installed via
CPAN, but
may not show modules that have been installed manually.
References:
-
List Perl Modules
Date: November 28, 2005
MoonPoint Support
-
How do I get a list of installed CPAN modules?
Date: September 22, 2008
Stack Overflow
-
App-Module-Lister
The CPAN Search Site
[/languages/perl]
permanent link
Sun, Oct 06, 2013 6:11 pm
Adding CometChat to an SMF Theme
A family member uses
CometChat
on a
Simple Machines Forum (SMF)
forum to allow members of the forum to chat with one another online when they
are visiting the forum. I installed a couple of Halloween themes for the forum,
but she found that CometChat was not available with the new themes, though it
was available with the default theme.
Checking changes that had been made quite to that theme's files when I installed
CometChat on the forum a few years ago, I found that the installation process
for CometChat had modified
the index.template.php file for the default theme, which was stored
in the Themes/default directory for the forum.
I found the following PHP code in that file:
echo '<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml"', $context['right_to_left'] ? ' dir="rtl"' : '', '>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=', $context['character_set'], '" />
<link type="text/css" href="/cometchat/cometchatcss.php" rel="stylesheet" charset="utf-8"> >script type="text/javascript" src="/cometchat/cometchatjs.php" charset="utf-8"></script>
Since the CometChat additions to the file occurred immediately after the
head tag, to make CometChat available in the new theme, I added the
following immediately after <head> in the
Themes/Halloween/index.template.php
file under the forum's directory on the server for the forum:
<link type="text/css" href="/cometchat/cometchatcss.php" rel="stylesheet" charset="utf-8"> <script type="text/javascript" src="/cometchat/cometchatjs.php" charset="utf-8"></script>
She was then able to log into the forum and change the default theme to the
Halloween theme with CometChat now being available with that theme. I made
a similar change to othere themes she wanted to use for the forum by updating
the index.template.php file in the appropriate theme directory.
Note: If you see ';
immediately after <head>, you need to put the
code for CometChat between the <head> and the
';.
[/network/web/forums/smf]
permanent link
Sun, Oct 06, 2013 1:29 pm
Check a Domain's Reputation
There are a number of companies that provide a means of checking
a domain's reputation. E.g., perhaps you may wish to determine if a particular
domain name is associated with the transmission of spam or want to know whether
it is safe to visit a particular website. Often antispam and antivirus vendors
will allow you to lookup an IP address or
fully qualified domain name (FQDN)
, e.g.
somesite.example.com to make that determination through
a website they provide.
[ More
Info ]
[/network/Internet/domains]
permanent link
Sat, Oct 05, 2013 9:17 pm
Finding the largest files in a directory
To find the largest files in a directory on a Linux system, you can use
ls -lS to order the directory listing by size with the
largest files at the top of the list and the smallest at the bottom. The
command will show the size of files in bytes, so you may wish to add the
h parameter to display file sizes in a more human-readable
format, such as kilobytes, megabtyes, etc. depending on the file size,
i.e.,
ls -lSh. Often, you will wish to have the largest
files displayed at the bottom of the list. To do so, add the
r
parameter, i.e.,
lS -lShr.
$ ls -lShr /usr/lib/xorg/modules
total 1.2M
drwxr-xr-x 2 root root 4.0K 2012-04-23 12:01 multimedia
drwxr-xr-x 2 root root 4.0K 2011-10-12 10:30 input
drwxr-xr-x 2 root root 4.0K 2012-04-23 12:01 extensions
drwxr-xr-x 2 root root 4.0K 2012-04-23 12:16 drivers
-rw-r--r-- 1 root root 18K 2011-10-19 01:19 libfbdevhw.so
-rw-r--r-- 1 root root 22K 2011-10-19 01:19 libvbe.so
-rw-r--r-- 1 root root 26K 2011-10-19 01:19 libshadow.so
-rw-r--r-- 1 root root 27K 2011-10-19 01:19 libvgahw.so
-rw-r--r-- 1 root root 34K 2011-10-19 01:19 libshadowfb.so
-rw-r--r-- 1 root root 98K 2011-10-19 01:19 libexa.so
-rw-r--r-- 1 root root 138K 2011-10-19 01:19 libfb.so
-rw-r--r-- 1 root root 152K 2011-10-19 01:19 libint10.so
-rw-r--r-- 1 root root 178K 2011-10-19 01:19 libwfb.so
-rw-r--r-- 1 root root 414K 2011-10-19 01:19 libxaa.so
[/os/unix/linux]
permanent link
Fri, Oct 04, 2013 5:43 pm
Copying Themes from One Windows 7 System to Another
If you wish to copy themes from one Windows 7 system to another, copy the
contents of
\Users\Username\AppData\Local\Microsoft\Windows\Themes,
where
Username is the account name for the account from which
you wish to copy the themes. If the new system doesn't have a
Themes
under the
\Users\Username\AppData\Local\Microsoft\Windows\ directory, because no themes have been added, just copy the
Themes
directory itself from the source system to the destination system.
Afterwards, on the destination system, you can right-click on an empty area of
the desktop, select
Personalize, then select the theme you wish to use.
[/os/windows/win7]
permanent link
Thu, Oct 03, 2013 10:47 pm
Restoring terminal scrollbar
While using the terminal application on a Ubuntu 11.10 system, I found
that the scrollbar that will appear on the right side of a terminal window
had disappeared and that I couldn't get it to reappear. The problem occurred
after I was disconnected from terminal sessions I had established within
several tabbed windows in the terminal application.
At
Terminal output scrolling is gone (Headless 11.10 Server,
Upgraded from 10.10), I found a solution that worked to restore the
scrollbar. By using the
less command on a file that was long enough to require paging to view
the entire file, I was able to restore the ability to scroll in the terminal
windows. I issued a command less longfile.txt and then paged
through the file and exited normally from less. I was then able
to see the scrollbar again. I had to do that for each terminal window.
On another occasion, I found that using less wouuldn't resolve
the problem but using more, e.g., more longfile.txt,
resolved the problem.
[/os/unix/linux/ubuntu]
permanent link
Wed, Oct 02, 2013 10:02 pm
Vertically aligning text to an image
To vertically align text with the middle of an image in HTML code, you
can add a style parameter with a
vertical-align property to the
img tag,
e.g.
style="vertical-align: middle;" to align the text with the
middle of the image. You can use "top" or "bottom", instead, if you
wished to have the text appear at the side of the image, but aligned
with the top or bottom of the image.
<img src="Schloss-Moyland-2013-02.jpg" alt="Moyland Castle, side view"
width="500" height="691" style="padding:10px; vertical-align: middle;">
<a href="http://en.wikipedia.org/wiki/Moyland_Castle"> Moyland
Castle</a>, side view.
E.g., the above code would produce the following result:
 Moyland Castle, side view.
Moyland Castle, side view.
Note: the above image is available at Wikimedia Commons
here. It was a featured picture for October 2, 2013. The image was provided
by Tuxyso and is
licensed under the Creative Commons
Attribution-Share Alike 3.0 Unported license, so anyone is free to use it
or redistribute it.
[/network/web/html/css]
permanent link
Tue, Oct 01, 2013 10:35 pm
Determining the version of Ubuntu on a system
To determine the version of Ubuntu Linux on a system from a command prompt,
you can use the
lsb-release -a command.
$ lsb_release -a
No LSB modules are available.
Distributor ID: Ubuntu
Description: Ubuntu 11.10
Release: 11.10
Codename: oneiric
[/os/unix/linux/ubuntu]
permanent link
Mon, Sep 30, 2013 11:14 pm
Extreme Volume Pop Halloween
One of the places I searched for music to play from our porch for
trick-or-treaters was the
Internet Archive
site at
archive.org. The site provides
permanent storage for collections of digitized materials, including websites,
music, moving images, and nearly three million public-domain books, all of which
are freely available to the public. If you ever attempt to follow a link on
a webpage only to find it is no longer working, you may be able to find an
archived version of the page through the Internet Archive's
Wayback Machine;
simply put the URL into the search field for the Wayback Machine, which will
show you all of the times the page was archived in the past.
You can search the Internet Archive site for "Halloween" and get lots of
results, if you are looking for free public domain music that you could use
for Halloween. I found
Extreme Volume Pop Halloween, which is 46 minutes and 7 seconds of
instrumental music described by its creator
Tom Baker as:
An album of eclectic , haunting music, inspired by the greatest holiday in the
history of the world. Dark ambient passages, beautiful keyboard compositions,
and occult music to give you many nights of uneasy dreams are what this free
recording are all about! For fans of dark music, gothic orchestrations, horror
movie soundtracks.
The titles for the songs it includes are as follows:
- The Inner Sanctum
- Lurking Fear
- Halloween Overture 2008
- Mind of a Killer
- Gypsy Caravan
- The Stalker
- Witchcraft Through the Ages
- Midnight Shadows
- Vlad the Impaler
- Galactic Carnivore
- Here There Be Ghosts
- Sabbat
You can download a zip file,
Halloween_928, which contains one MP3 file of all the songs or you can
listen to the music online.
At his website,
Tom Baker describes himself thusly:
an experimental musician dabbling in forms as diverse as metal, punk, noise,
ambient, drone, industrial, and aleatoric. He has been featured on a number of
different internet radio programs, including The Black Cat Lounge, Stirring the
Cauldron with Marla Brooks, and Seps Paranormal Radio. He has written a number
of novels, and covered nonfiction topics as diverse as true crime, UFOs, urban
legends, ghosts and hauntings, and other paranormal events.
A list of books he has written is available
here.
Scary Urban Legends (illustrated by John C. Eng),
Haunted Indianapolis and Other Indiana Ghost Stories
(with Jonathan Titchenal), and
Indiana Ghost Folklore might also be interesting Halloween reading.
[/music]
permanent link
Sun, Sep 29, 2013 8:58 pm
Halloween Music Stations at Live365
Like Pandora,
Live365 also provides
Halloween radio stations.
Live365 is an Internet radio broadcasting and listening network where
people can create their own online radio stations or listen
to thousands of stations created by other people from around the world.
You
can listen to over 7,000 stations across 265 genres of music.

For a list of the Halloween stations provided by Live365, you can go to Listen to Free Halloween
Music Online - Live365 Internet Radio.

One of the stations is
Musique Macabre,
which is "Horror & Halloween Radio." The station plays oldies,
novelty, horror movie soundtracks, horror punk, surf, psychobilly,
deathrock, gothic, space, library, symphonic, progressive rock,
electronic, soundscapes, rare and weird" music. The website for the station
is at Musique Macabre Horror &
Halloween Radio.
Other stations include the following:
- Holidaze Halloween
- The Haunted Mansion!
- Halloween Radio: KDOA!!
- Horror Old Time Radio
- The Grimly Show
- Bindlegrim Halloween
- Drive In of the Damned
- Boogeyman Radio
- WGTR Hallotober
- Halloween Party Music
- Monster Kid Radio
- Welcome To Weirdsville
- All the World's a Stage
- Kiddfellas Radio
[/music]
permanent link
Sun, Sep 29, 2013 5:28 pm
Halloween Music from Pandora
My wife and I decorate the house for Halloween, both inside and out,
so I thought I'd also put up some Halloween decorations here, also. For others
who may also like to listen to music that fits with Halloween,
Pandora Internet
Radio, aka "Pandora Radio" or just "Pandora",
offers several Halloween-themed stations at this time of the year.
Pandora is the "custodian" for the
Music Genome Project, which associates a list of attributes with songs as one might associate
genes with
phenotypical
traits of an organism.
Halloween
Party Radio plays songs such as
Monster Mash by John Zacherle,
while the
Spooky Symphonies station plays music from films, such as
The Nightmare Before Christmas, and
Family
Halloween Radio provides Halloween music for children of all ages,
which one could use for a children's Halloween party or can play from
the porch as we do for trick-or-treaters. The station plays songs such as
The Purple People Eater by Shep Wooley.
There's also
Ghostly
Grooves, which plays songs such as
When I'm Small by Phantogram.
You can point your browser to any of the stations and listen
for free to songs appropriate for the holiday.
Note: Pandora's Terms of Use
states "Pandora can only be used in the United States, New Zealand,
Australia and those countries' respective territories."
[/music]
permanent link
Sat, Sep 28, 2013 9:59 pm
Viewing Cached Google Pages from DuckDuckGo
I've often found Google's cached copies of webpages useful when a website
isn't currently accessible or when I would like to see a previous version
of a page that has recently changed. Unfortunately, Google doesn't make it
as easy as it once did to view such pages. Though
DuckDuckGo doesn't provide cached
copies of pages, it does provide a very easy method to access Google
cached pages from the DuckDuckGo search field as explained at
Cache. You simply
put
!cache in front of a URL in the
DuckDuckGo search field. E.g.,
!cache http://example.com.
DuckDuckGo states that "We would like to provide cached results
ourselves, but unfortunately it is non-trivial to do so as it requires
a lot of storage."
[/network/web/search]
permanent link
Fri, Sep 27, 2013 11:04 pm
Google's 15th Birthday
Google celebrated its 15th birthday today. Though the company was
incorporated a few weeks earlier, the company celebrates its birthday
on September 27. It announced on its birthday that it is updating its
search algorithm as part of an update it has named "Hummingbird". Three
years ago it had an update it called Caffeine. Amit Singhal, a senior
vice-president for Google estimates that the redesign will affect how
Google analyzes about 90% of the search requests it receives. Singhal
said that Hummingbird is primarily aimed at giving Google's search engine
a better grasp at understanding concepts instead of mere words. The
increasing use of Google's voice-recognition technology for spoken
search requests through smartphones was a factor in the development of
changes for Hummingbird.
Google's ad revenue related to web content is expected to
approach $60 billion U.S. dollars this year.
References:
-
A Google Google doodle? Search giant celebrates 15 years and a new algorithm
[/network/web/services/google]
permanent link
Sat, Sep 21, 2013 12:03 pm
Testing a value to prevent a divide by zero error in Excel
Excel's
IF function can be used to prevent divide by zero errors,
which show up as
#DIV/0! values in cells, in calculations. The
format for the
IF function is:
IF(logical_test, [value_if_true], [value_if_false])
E.g., suppose column B holds values for items ordered on
particular days and column C holds values for items shipped on
those days, as shown below:
| | A | B | C | D |
| 1 |
Date | Items Ordered | Items Shipped |
% Shipped |
| 2 |
9/1/13 | 0 | 0 |
|
| 3 |
9/2/13 | 2 | 1 |
|
| 4 |
9/3/13 | 0 | 1 |
|
| 5 |
9/4/13 | 3 | 0 |
|
If column C is simply divided by column B, e.g.
=C2/B2, to get the percentage of orders shipped, the results would be
as follows:
| | A | B | C | D |
| 1 |
Date | Items Ordered | Items Shipped |
% Shipped |
| 2 |
9/1/13 | 0 | 0 |
#DIV/0! |
| 3 |
9/2/13 | 2 | 1 |
50.00% |
| 4 |
9/3/13 | 0 | 1 |
0.00% |
| 5 |
9/4/13 | 3 | 0 |
#DIV/0! |
A simple IF test can be used so that if a cell in column B is
zero, then a zero value is put in the "% shipped column".
=IF(B2>0, C2/B2, 0)
| | A | B | C | D |
| 1 |
Date | Items Ordered | Items Shipped |
% Shipped |
| 2 |
9/1/13 | 0 | 0 |
0.00% |
| 3 |
9/2/13 | 2 | 1 |
50.00% |
| 4 |
9/3/13 | 0 | 1 |
0.00% |
| 5 |
9/4/13 | 3 | 0 |
0.00% |
Or if no items were ordered on a particular day, "N/A", for "Not Applicable" could be used instead of zero, if preferred.
=IF(B2>0, C2/B2, "N/A")
[/os/windows/office/excel]
permanent link
Tue, Sep 10, 2013 9:37 pm
Changing the background color for a cell in Excel for Unequal Values
To compare whether two cells contain equal values, whether numbers or text,
in Excel you can use
<>. E.g., to take some action,
such as changing the background color of a cell,
C3, if it
does contain the same data as another cell,
B3, I could
use a formula of
=B3<>C3. E.g., Suppose I have two
columns,
B and
C, containing values I wish
to compare and wish to change the background color of a cell in column
C to pink whenever it does not match the value in the adjacent B cell,
so that I can easily scan the spreadsheet to find all instances where
the values differ. The first row is a heading row and the second row is
blank with the data starting in the third row as shown below:
| A |
B |
C |
D |
E |
| 1 |
Sensor | 1st Reading | 2nd Reading | Checked |
| 2 |
| | | |
| 3 |
Alpha | 32 | 32 | 9/3/13 |
| 4 |
Beta | 35 |
37 | 9/3/13 |
| 5 |
Delta |
36 |
33 | 9/3/13 |
| 6 |
Epsilon |
38 |
34 | 9/3/13 |
| 7 |
Gamma | 38 | 38 | 9/3/13 |
In Microsoft Excel 2008 for Mac,
to have the background color of cells in column C change to pink whenever
the value does not match the adjacent value in column B, I can click on
cell C3, the first cell in column C to contain data, then
click on Format then select Conditional Formatting.
I can then for Condition 1, change "Cell Value Is" to "Forumula Is"
and use =B3<>C3 for the formula. I can then click on the
Format button, select Patterns, and pick the color I want
for the cell background and click on OK.
If I click on OK again, the conditional formatting is set for
cell C3. To copy it to all the cells below in the column, I can hit
Command-C on a Mac (the equivalent to Control-C on a
Microsoft Windows system) to copy the cell. I can then click on the
cell immediately below and drag downwards until all of the cell from
C4 to the bottom of the column are highlighted. I can then click on
Edit and select Paste Special. If I then select
Formats from the Paste section and click on OK,
the conditional formatting will be applied to all cells with data in column
C so that any that don't match their adjacent neighbor in column B will have
a pink background.
[/os/windows/office/excel]
permanent link
Fri, Sep 06, 2013 7:57 pm
Creating a Service for a Windows System
You can create a new service on a Windows system, including Windows 8, using
the
sc command. To create a new service named "ExampleService",
the command below could be issued from a
Command Prompt:
Microsoft Windows [Version 6.2.9200]
(c) 2012 Microsoft Corporation. All rights reserved.
C:\Windows\system32&sc create ExampleService binpath="C:\Program Files (x86)\ExampleApp\Example.exe"
[SC] CreateService SUCCESS
C:\Windows\system32&
To delete the service you created, e.g., ExampleService,
you can use the command sc delete servicename, e.g.:
C:\Windows\system32>sc delete ExampleService
[SC] DeleteService SUCCESS
Once you have created a service, you can modify it, e.g., to have it start
automatically by using services.msc to bring up the
Windows
Services list.
Or you can get to the services list through the Control Panel,
which you can do on a Windows 8 system by selecting System and Security
from the Control Panel, then select Administrative
Tools, then Services. Double-click on the service you wish to
modify and make any changes you wish, for instance changing the startup type to
Automatic so that the service starts whenever the system boots.
References:
-
Create Windows service from executable
Date: August 27, 2010
stackoverflow
-
How To Create a
User-Defined Service
Microsoft Support
[/os/windows/commands]
permanent link
Tue, Sep 03, 2013 8:51 pm
Starting RunUO automatically with FireDaemon Pro
If you would like to have
RunUO start automatically when you boot the system on which it is
installed, you can do so by creating a Windows service for it using
FireDaemon Pro.
[ More Info ]
[/gaming/runuo/firedaemon]
permanent link
Mon, Sep 02, 2013 2:16 pm
freeSSHd on Windows 8
If you want to set up a Windows 8 system as a
Secure Shell (SSH)
server, you can use
freeSSHd, which
as the name implies is free, to do so. I had problems getting it to run
as a service on a Windows 8 system, though.
[ More Info ]
[/os/windows/network/ssh]
permanent link
Mon, Sep 02, 2013 1:17 pm
Counting the number of specific characters in a file
On a Linux/Unix system, you can count the occurences of a specific character
in a file by using the
fgrep and
wc commands. E.g.,
suppose you wish to count the number of times the letter "A" occurs in a file
named temp.txt.
fgrep -o A temp.txt | wc -l
The "-o PATTERN" option for fgrep tells it to show only the part of a
matching line that matches PATTERN where PATTERN is what you are searching
for, in this case the letter "A". Piping the output to wc -l
will count the number of times the PATTERN appears in the file.
[/os/unix/commands]
permanent link
Mon, Jul 08, 2013 10:11 pm
Configuring a Windows Vista system for WOL
To configure Microsoft Windows Vista for
Wake-on-LAN support,
i.e., to allow it to be "awakened" by sending a specific Ethernet packet
to it, take the following steps:
- Click on Start.
- Select Control Panel.
-
Select Network and Internet.
-
Click on Network and Sharing Center.
-
Click on Manage network connections.
-
Right-click on Local Area Connection and choose Properties.
-
Click on the Configure button to configure your Network Interface Card (
NIC).
-
Click on the Power Management tab.
-
Click on Allow the computer to turn off this device to save power, which
will then allow you to put a checkmark in the box for Allow this device to
wake the computer.
-
Click on OK
[/network/wol]
permanent link
Sat, Jun 29, 2013 5:01 pm
Copying and Pasting in SSH Session on Chrome OS
To copy and paste information into an SSH session on Chrome OS, you can use
ctrl-c to copy the information and
ctrl-shift-v to paste
the information.
[/os/chrome]
permanent link
Sat, Jun 29, 2013 4:53 pm
VNC Access Blocked by Firewall on OS X System
I turned on Apple Remote Desktop access on an eMac system
running Mac OS X 10.4.11 by the following steps:
-
Click on the Apple symbol at the upper, left-hand corner of the screen.
-
Select System Preferences.
-
Select Sharing under Internet & Network.
-
Start Apple Remote Desktop and set the appropriate
privileges for it as detailed at
Configuring a Mac OS X 10.6
System to Provide VNC Access.
But when I tried establishing a VNC connection to the system from another
system on the same LAN,
I could not establish the connection. Yet I could establish a VNC connection
when I attempted to do so through an
SSH tunnel, which led me to believe that the firewall software running on
the eMac was blocking the connection.
I went to Sharing again on the system and selected Apple
Remote Desktop and then clicked on the Firewall tab. I clicked
on the padlock icon so I could edit the firewall settings. I then saw a message
telling me that I couldn't change the settings when I clicked on Edit.
You cannot change the firewall settings for this service.
When you turn on Apple Remote Desktop in the
Services pane, you also allow the service access
through the firewall on TCP port(s) 3238 and UDP
port(s) 3238. To stop access through the firewall
you must turn off this service through the Services
pane.
I didn't see a reference to the default VNC port of 5900, so
I opened a terminal window to check the firewall rules (Applications -
Utilities - Terminal) using the ipfw command. The
command has to be issued while logged into an account that
has administrator access on the system.
Maroon-Apple:~ JDoe$ sudo ipfw list
Password:
02000 allow ip from any to any via lo*
02010 deny ip from 127.0.0.0/8 to any in
02020 deny ip from any to 127.0.0.0/8 in
02030 deny ip from 224.0.0.0/3 to any in
02040 deny tcp from any to 224.0.0.0/3 in
02050 allow tcp from any to any out
02060 allow tcp from any to any established
02065 allow tcp from any to any frag
02070 allow tcp from any to any dst-port 3238 in
02080 allow tcp from any to any dst-port 22 in
02090 allow tcp from any to any dst-port 548 in
02100 allow tcp from any to any dst-port 427 in
02110 allow tcp from any to any dst-port 139 in
02120 allow tcp from any to any dst-port 631 in
02130 allow tcp from any to any dst-port 515 in
12190 deny tcp from any to any
65535 allow ip from any to any
I could see that connections to port 3238 were
allowed, but there was no entry for port 5900, though
the system was listening on port 5900 as a
netstat -an command verified.
Haroon-Apple:~ Jim$ netstat -an | grep 5900
tcp4 0 0 *.5900 *.* LISTEN
To resolve the problem, with the Firewall tab selected under
Sharing, I clicked on the New button. I then selected
VNC for Port Name, which automatically selected
TCP ports 5900-5902 and UDP port 5900.
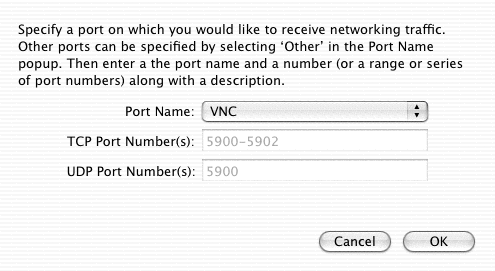
VNC then appeared in the list of services in the firewall
window with a checkmark next to it. When I checked the
firewall rules with the ipfw list command, I also
saw ports 5900 to 5902 listed.
$ sudo ipfw list
Password:
02000 allow ip from any to any via lo*
02010 deny ip from 127.0.0.0/8 to any in
02020 deny ip from any to 127.0.0.0/8 in
02030 deny ip from 224.0.0.0/3 to any in
02040 deny tcp from any to 224.0.0.0/3 in
02050 allow tcp from any to any out
02060 allow tcp from any to any established
02065 allow tcp from any to any frag
02070 allow tcp from any to any dst-port 3238 in
02080 allow tcp from any to any dst-port 22 in
02090 allow tcp from any to any dst-port 548 in
02100 allow tcp from any to any dst-port 427 in
02110 allow tcp from any to any dst-port 139 in
02120 allow tcp from any to any dst-port 5900-5902 in
02130 allow tcp from any to any dst-port 631 in
02140 allow tcp from any to any dst-port 515 in
12190 deny tcp from any to any
65535 allow ip from any to any
I was then able to successfully connect to
the system from another Mac by putting
vnc://192.168.0.103 in the
address bar of Safari (192.168.0.103 was the
address of the system functioning as a VNC
server). When prompted for login credentials,
I could put in the userid and password
of an account on the system functioning
as the VNC server and log into it.
[/os/os-x]
permanent link
Fri, Jun 28, 2013 9:29 pm
SSH Port Forwarding for VNC under Chrome OS
If you need a
Virtual
Network Computing client for a
Chromebook, such as the
one manufactured by Acer,
RealVNC
provides a free one that is available through the Google
Chrome Web Store. For details on the app, see
VNC® Viewer for
Google Chrome™.
When I used it to connect to a Mac OS X system, I was warned that
the connection would not be encrypted.
Unencrypted Connection
This connection will not be encrypted. Your authentication credentials
will be transmitted securely, but all subsequent data exchanged while
the connection is in progress may be susceptible to interception by
third parties.
That's not a significant concern for me when both systems are on a
Local Area Network (LAN) I control, but I normally tunnel VNC connections
through an SSH connection when connecting over the Internet to ensure
transmissions are encrypted.
Chrome OS on a Chromebook contains
A Secure Shell
(SSH) client application. To access it, hit the Ctrl-Alt-T
keys simultaneously, which will open a terminal window as a tab in the
Chrome browser. Type ssh at the "crosh>" prompt to access
the ssh client.
Welcome to crosh, type 'help' for a list of commands.
crosh> ssh
Within the ssh application, typing help will show you a
list of the available commands.
ssh> help
connect - connect
dynamic-forward port - dynamic socks proxy (-D)
forward port:host:port - static port forward (-L)
help - this
host <hostname> - remote hostname
key <file> - sets private key to use (-i)
nocmd - don't execute command (-N)
port <num> - port on remote host (-p)
server-alive-interval <num> - set ServerAliveInterval option
exit - exit ssh subsystem
user <username< - username on remote host
Note that this program can only bind local ports in the range
8000-8999, inclusive.
ssh>
If you wish to encrypt a
Virtual Nework Computing (VNC) connection by tunneling it through
an SSH connection, you will need to specify a port from 8000 to 8999
as the port to be used for forwarding the VNC traffic when using SSH
under Chrome OS. You can do so using a forward command such as the following:
crosh> ssh
ssh> user JDoe
ssh> host my.example.com
ssh> forward 8000:127.0.0.1:5900
ssh> connect
Then using the RealVNC
client for Chrome OS, you can specify 127.0.0.1:8000
or localhost::8000 as the address through
which to establish the VNC connection. You could also have
used forward 8000:localhost:5900 for the SSH
forwarding command. The address 127.0.0.1 is the
localhost
address and with the port number of 8000 tells VNC to try
establishing the VNC connection by connecting to port number 8000 on
the system on which VNC is running, i.e., the Chromebook. Because there
is an SSH tunnel through that port, SSH will route any traffic to TCP
port 8000 through its connection to port 5900 on the remote system.
You will still get the warning from the VNC Viewer about transmissions
not being encrypted when you tunnel the traffic through the SSH tunnel,
but you no longer have to worry about the warning, since the traffic is
going through an encrypted SSH tunnel. The VNC Viewer does not know
that its transmissions are going through an encrypted tunnel; it only
knows that it isn't performing any encryption.
[/os/chrome]
permanent link
Fri, Jun 28, 2013 1:06 pm
Remote Screen Sharing using VNC on a Mac OS X System
A Mac OS X system that is functioning as a Virtual Network Computing
(VNC) server can be remotely accessed using VNC client software that comes
with the OS X operating sytem, which will allow you to see what appears
on the screen of the system remotely and control that remote system just
as if you were sitting at the system using its keyboard and mouse.
[ More Info ]
[/os/os-x]
permanent link
Sun, Jun 23, 2013 8:13 pm
Scratchpad not Synching
I've been having problems with my Chromebook after an update from Google
this week. Periodically, I will lose the capability to view videos
I've downloaded. A window will open for the video, but it won't play;
clicking on the button to play the video will have no effect. Also,
when I open the files application, it won't show the files in a directory.
Shutting the system off and then restarting it can resolve the problem,
though I then find that each time I do so, when I reopen the browser
about half the previously opened tabs no longer appear. And, also,
annoyingly, the last time I shut the system down and restarted it,
about 1/2 hour's worth of notes I had taken in the Scratchpad
app about 1/2 hour prior to shutting down the system had disappeared.
I checked Google Drive, but the particular Scratchpad note I had been
editing wasn't there. Though Scratchpad had at one time been
synchronizing between my Chromebook and Google Drive, it appeared
it hadn't done so for quite some time.
I opened the Scratchpad app (version 3.1.0), which opened a new
browser tab. On the left-hand side where a list of the notes I had
created appeared there was also a "Scratchpad tips and tricks" note. I
clicked on it; one of the options that appeared in the note was "Connect your Scratchpad to Google Docs." When I
clicked on Connect, I saw that, under Options,
"Sync with Google Docs" was set to "Off". I clicked on the option to
change it and gave the application access to the Google Docs for my Gmail
account. I then saw the option was set to "On". Hopefully, now I will
have a copy of my notes on Google Docs should the problem reoccur. I
recall once previously being asked what version of a note I wanted,
the one stored locally or the one on Google Docs.
Note: you can also get to the setting to change the
synchronization option by taking the following steps in
the browser:
-
Click on the the "Customize and control Google Chrome"
button at the top, right-hand side of the browser window,
the one with the 3 short horizontal bars one below the
other on it.
-
Click on Settings.
-
Click on Extensions.
-
Click on the Options link under
Scratchpad and set the synchronization
option.
[/os/chrome]
permanent link
Mon, May 27, 2013 8:33 pm
SNMP Tester
If you need an SNMP test tool for a Windows system,
Paessler, a company that produces
network monitoring software, offers
SNMP Tester for
free. There is no installation process for the software other than
extracting the files in the downloaded zip file to a directory of your
choice and running
snmptest.exe.
After extracting the files to a directory under
Program Files using an administrator account, I tried running the
program from a normal user account. The program didn't appear to open, though
I could see it running when I used the Task Manager to check on
running processes, although the CPU utilization for it stayed at 0. So I
right-clicked on snmptest.exe and chose "Run as administrator".
The program then opened. I found that I could extract the files to a folder
in the My Documents directory of the regular user account and
run it from there. The issue I first encountered when attempting to run the
program from the Program Files directory was that the program
wants to update an snmp.ini file in the directory from which it
runs and that account didn't have write access to the Program Files
subdirectory within which it was located.
When you run the program, place the IP address of the system you wish to
scan in the
Device/IP field; if the SNMP port has been changed from the default
value of port 161, change that also. Specify the community string in the
Community field. If you want to see the uptime of the device to
just verify the device is responding to SNMP queries, leave
"Read Device Uptime" selected under Select Request Type. Then click
on the Start button to initiate the scan.
You can also put an
OID, such as 1.3.6.1.2.1 in the
Walk field, select the Walk radio button and click on
Start to "walk" through a sequence of OIDs or specify a particular
OID, e.g.,1.3.6.1.2.1.1.5.0 in the Custom OID field.
[/os/windows/software/network/snmp]
permanent link
Wed, May 22, 2013 11:05 pm
Using the SSH Client on a Chromebook to Establish a Socks Proxy Connection
The
Chrome OS on a
Chromebook contains
a
Secure Shell
(SSH) client application. To access it, hit the
Ctrl-Alt-T
keys simultaneously, which will open a terminal window as a tab in the
Chrome browser. Type
ssh at the "crosh>" prompt to access
the ssh client.
Welcome to crosh, type 'help' for a list of commands.
crosh> ssh
Within the ssh application, typing help will show you a list of the available commands.
ssh> help
connect - connect
dynamic-forward port - dynamic socks proxy (-D)
forward port:host:port - static port forward (-L)
help - this
host <hostname> - remote hostname
key <file> - sets private key to use (-i)
nocmd - don't execute command (-N)
port <num> - port on remote host (-p)
server-alive-interval <num> - set ServerAliveInterval option
exit - exit ssh subsystem
user <username< - username on remote host
Note that this program can only bind local ports in the range
8000-8999, inclusive.
ssh>
To establish the SOCKS
proxy connection via SSH, type dynamic-forward port
where port is the port number you wish to use
for the SOCKS proxy. E.g., dynamic-forward 8000. Note:
the help information for the SSH client states "that this program
can only bind local ports in the range 8000-8999, inclusive." Then
type host fqdn where fqdn is the fully qualified domain name
or IP address of the system to which you wish to connect followed by
user username where username
is the account under which you wish to log into the SSH server. They
type connect to establish the connection.
ssh> dynamic-forward 8000
ssh> host example.com
ssh> user jdoe
ssh> connect
You will be prompted for the password for the login once the Chromebook
connects to the remote SSH server.
To now change the proxy settings of the Chrome browser, take the
following steps:
- Click the network icon
 in the lower-right
corner of your screen.
in the lower-right
corner of your screen.
- Select Settings and find the "Internet
connection" section on the Settings page that appears.
- You will need to check the "Allow proxies for
shared networks" check box if the network is shared with all users of
the Chromebook. If checked, all profiles on your Chrome device will use the proxy
settings set for a network. If this box isn't checked and the network is
shared for all users of the Chromebook, you won't be able to configure the
proxy settings, as they will be grayed out, until you check this box.
- Click the network for which you're using the proxy settings.
- Select the Proxy tab in the window that displays
the network options.
- Configure your proxy settings by selecting
the "Manual proxy configuration" option and then entering the proxy
settings. For the case above, where I'm using a socks proxy created
through the SSH client, I would put
127.0.0.1, which is the
localhost
address, in the SOCKS host field and 8000 in the
port field, since that was the port I chose to use. Putting
127.0.0.1 in the host field tells the browser to establish
the connection via port 8000 on the local system from which you
established the SSH connection.
Then click on the Close button to initiate the use of the socks proxy.
- You can verify that you are
using the socks proxy, by going to a website, such as whatismyip.com that will show you the
IP address from which it sees your connection originating.
[/os/chrome]
permanent link
Sun, May 19, 2013 6:12 pm
TeamViewer and Chromebook
The antivirus software on a family member's Microsoft Windows desktop system
was close to expiring and another member of the household had a license for
Norton 360 that would cover 3 systems, so I uninstalled the free
Avast antivirus
software I had placed on the system previously and started the installation
for Norton 360. Because it was going to take more than a half hour for the
download of Norton 360 to complete once I had started the installation, I left
and tried connecting to the system remotely with
TeamViewer, a program that allows you
to remotely control a system from a variety of other systems, which I had
installed on the system previously.
I had used the TeamViewer application on a Microsoft Windows system before
to manage the family member's PC, but since I didn't have access to the
Microsoft Windows desktop system which I had used previously at the moment,
I thought I would try using my Android phone, instead, since TeamViewer provides
an app for it.
I installed the TeamViewer app on my Android phone and remotely connected
to the Microsoft Windows 7 PC. The following gestures can be made on the
Android phone to remotely manage another system.
Mouse interactions:
- Tap to click.
- Tap and hold to click right.
- Drag a finger on the screen for mouse movement.
- Double tap and drag for drag & drop.
- Two-finger drag to scroll.
- Pinch to zoom.
From my phone, I connected to the PC, but I found it difficult to
manage the PC from the phone's small screen. So I tried from a
Chromebook system
running the Google
Chrome OS, instead.
Using the
Chrome browser on
it, I logged into the TeamViewer website. I then could see the system
I wanted to control with TeamViewer. I then was presented the option
to download and install a client program or to use the alternative
Web client. When I clicked on "Download and install", I was taken to a
download page for a Microsoft Windows application, so I went back and
selected the Web client, instead. However, I then received an error
message:
Translate(FlashConnectionError)
TypeError: Object#<HTMLObjectElement> has no
method 'ExternalConnect'
But I was able to proceed past it to a login page to establish the
connection where I was able to put in the email address I had given
for the TeamViewer account and the accompanying password. But I kept getting
"Timeout while connection" messages when I clicked on the Connect to
partner button. I went back to the point where I opted for the Web
client connection and tried again. This time I was able to successfully
establish a connection. The text on the remote Windows system was very tiny,
but I was able to read it well enough to complete the installation of the
antivirus software.
I clicked on View at the top of the webpage displayed for the
connection, then clicked on Quality and changed the setting
from Optimize speed to Optimize quality, which made the
remote display somewhat easier to read. Quicking on View and
changing the scaling to "original" made the display even easier to read,
but I had to scroll the display then to see various parts of the remote
display.
At this point, I would consider managing a Microsoft Windows system
remotely from a Chromebook with TeamViewer acceptable, but I'll have to
experiment with managing a system from the Android phone more before I
can consider it an acceptable means of remotely managing another system
with TeamViewer on it in a situation where I might not have access to
another device to use for remote troubleshooting.
[/os/windows/software/remote-control/teamviewer]
permanent link
Sun, Mar 31, 2013 6:08 pm
Turning Off Outlook's New Mail Alerts
To turn off Outlook's popup alerts telling you that new mail has arrived,
take the following steps in Outlook:
- Click on File.
- Click on Options.
- Click on Mail.
- Under Message arrival, clear the
checkbox for Display a Desktop Alert.
Applies to Outlook 2010 to 2013
References:
-
Turn on or off new message alert pop-up window
Office.com
[/os/windows/office/outlook]
permanent link
Fri, Mar 22, 2013 10:15 pm
Missing IMAP Folders in Thunderbird
Thunderbird was
not showing some folders listed for an email account on
an an
IMAP server.
In order to get them to display on the PC on which I was running
Thunderbird 17.0.4, within Thunderbird I clicked on
File, then
selected
Subscribe. I then saw a folder list with "Select the
folders to subscribe to" displayed above the folders on the IMAMP server
for the account. I checked the boxes to the right of the ones that weren't
displaying. For some folders that had subfolders, I had to click on the
rightward pointing arrowhead to the left of the folder to display the
subfolders and their checkboxes.
[/network/email/clients/thunderbird]
permanent link
Wed, Mar 06, 2013 6:42 pm
Adding Live365 to Online Services in Winamp 5.63
I installed
WinAmp 5.63 on a family
member's Windows 8 system She wanted to add
Live365 as a service to it. I had written
instructions for doing that for Winamp 5.552 previously at
Adding Live365 to WinAmp's
Online Services List. I found that I had to modify the procedure
slightly for Winamp 5.63. I found
ml_online.ini was now
in
C:\Users\Username\AppData\Roaming\Winamp\Plugins\ml where
Username was the user's account name.
The
ml_online.ini file contained the following lines:
[Setup]
[ml_online_config]
maxbandwidth=350
minbandwidth=1
[Navigation]
order=10100;221836;222078;222150;222427;222509;222542;22259
Beneath the
C:\Users\Username\AppData\Roaming\Winamp\Plugins\ml
directory was an omServices subdirectory with files named
omService_{0000xxxxxx}.ini where xxxxxx was a sequence of
digits, e.g., omService_{0000221836}.ini, which had the
following lines in it.
[OnlineService]
id=221836
name=Song of the Day
url=http://www.spinner.com/winamp-mp3-of-the-day
icon=http://download.nullsoft.com/customize/component/2009/1/22/W/icon_image/Mp3_of_the_Day.png
flags=0x00000001
version=3
generation=2
I put a
365.png file to serve as an icon in
C:\Users\Username\AppData\Roaming\Winamp\Plugins\ml\omServices and created a
file omService_{0000000365}.ini and put the following lines
in it.
[OnlineService]
id=000365
name=Live365
url=http://www.live365.com
icon=live365.png
flags=0x00000001
version=1
generation=1
When I did so and reopened Winamp, I found that the
ml_online.ini had 365 added to the
order line as shown below:
[Setup]
[ml_online_config]
maxbandwidth=350
minbandwidth=1
[Navigation]
order=10100;221836;222078;222150;222427;222509;222542;222598;222598;365
Live365 was then at the bottom of the list of online services in WinAmp.
[/os/windows/software/audio/winamp/live365]
permanent link
Wed, Mar 06, 2013 4:44 pm
Closing Windows 8 Metro Applications
When you open a Windows 8
Metro
app, there is no immediately apparent way to close the application
when you are done with it. You won't see an "x" at the upper, right-hand corner
of Metro applications windows and Moving the mouse pointer to the corners of
the window doesn't show a way to close it. You can close the application
by hitting Alt-F4, i.e., by hitting the
Alt and
F4 keys
simultaneously.
An alternative method of closing one of the applications is to hit
Ctrl-Alt-Del to bring up the Windows Task Manager and then
select the application to close by clicking on it and then choosing End
Task.
References:
-
How to close Windows 8 apps, and how to disable SmartScreen
By Sebatian Anthony
Date: November 15, 2012
ExtremeTech
[/os/windows/win8]
permanent link
Wed, Mar 06, 2013 4:11 pm
Personalizing Windows 8
To change the background that appears on a Windows 8 system when the
system is locked, i.e., when it is waiting for you to enter the userid
and password, you can follow the steps below. By default, the system
shows a stylized image of the Seattle Tower in Seattle, Washington in the
U.S.
-
Hit the Windows key and
the I key simultaneously. The Windows key is the one with a Windows
logo on it normally at the lower, left-hand corner of the keyboard as shown
below:

-
Then select "Change PC Settings" which will be at the bottom of the panel
that opens on the right of your screen.
-
With Personalize selected and Lock screen highlighted at
the top of the window, you can then
pick one of the other 5 images shown below the one for the Seattle Tower,
or click on Browse to select another image of your choosing. Click
on Choose Picture when you find the one you wish to use.
If you wish to change the picture that appears for your account, you can
follow the same procedure as above, but choose Account picture,
instead of Lock screen. An image can be displayed as a small
96 x 96 pixel image, a large 448 x 448 pixel image, or a video
(dynamic image) - see
Guidelines for user names and account pictures (Windows).
You can also change the Start Screen colors by choosing
Start screen.
[/os/windows/win8]
permanent link
Wed, Mar 06, 2013 2:59 pm
Copying Windows 7 Themes to a Windows 8 System
To copy the
themes that someone downloaded to her Windows 7 system to
her new Windows 8 system, I located the
.themepack files on
the Windows 7 system, which I found in
C:\Users\Username\AppData\Local\Temp, where
Username was the name for her account on the Windows 7 system.
Then on her Windows 8 system, I just double-clicked on each Windows Theme
Pack file to install it on the new system.
[/os/windows/win8]
permanent link
Wed, Mar 06, 2013 12:43 pm
Adding a Link to a Website to the Windows 8 Start Screen
If you wish to add a shortcut to the Windows 8
Start Screen
so that you can click on an icon on the Start Screen to go to the
URL for a website, you can
do so by taking the following steps using Internet Explorer 10.
-
Go to the website in Internet Explorer.
-
Click on Tools. If you don't see the Tools menu, hit the
Ctrl and T keys simultaneously to bring up the Tools
menu.
-
Select Add site to Start Screen.
-
A Windows Internet Explorer window will open showing the
name that will be used for the item to be added to the Start Screen with
the URL in the From field. Click on Add to add the
site to the Start Screen.
References:
-
How to Pin a Website (Windows)
Microsoft Developer Network
[/os/windows/win8]
permanent link
Sun, Mar 03, 2013 9:59 pm
MUSHclient 4.84 Help Function for Windows 8
I installed
MUSHclient 4.84,
which is a free program for accessing a
MUSH server from a Microsoft Windows system on a Windows 8 system.
Afterwards, when I tried the "help" function, I saw the following:
The Help for this program was created in Windows Help format, which depends on
a feature that isn't included in Windows 8 or Windows RT. For more info, go to
the
Microsoft Support website.
At
I cannot open Help that was created in the Windows Help format
(WinHlp32.exe), there are download links for Windows Help program
(WinHlp32.exe) for various versions of Windows. The one for Windows 8
is at
Windows Help program (WinHlp32.exe) for Windows 8.
After installing
Windows
Help program (WinHlp32.exe) for Windows 8, I was able to use the
Help function in MUSHclient without even needing to restart the
program.
The same issue exists when MUSHclient is installed on Windows 7 - see
Windows Help Under Windows 7.
[/gaming/mushclient]
permanent link
Sun, Mar 03, 2013 8:48 pm
Sending a Test Message When Setting Up Outlook 2013
While setting up a
POP3 account
for a user using Microsoft Outlook 2013, I received the message below when
I clicked on
Test Account Settings:
Send test e-mail message: An unknown error occurred, error code: 0x800c8101
I found a June 18, 2012 posting by
CharlieBrady at
Email configuration who stated the problem can occur because there
is a bug in Outlook 2013's "test email" function.
Unfortunately, this is what you should expect to see. Outlook has a bug
in its "test email" function. It sends a test message with an illegal
format - it has no "Date" header. This is documented in the wiki:
http://wiki.contribs.org/Email#Outlook_test_message_doesn.27t_come_through
SME server does not accept those illegal messages, as such messages are usually spam. Legitimate mail clients do not generate such messages.
So I unchecked "Automatically test account settngs when Next is clicked"
and proceeded to complete the setup of the email account for the user.
After it was set up, I sent an email using Outlook 2013 from the account to
two other addresses, one outside the user's email server, which uses
Sendmail to send email,
and verified that both were received.
[/os/windows/office/outlook]
permanent link
Sun, Mar 03, 2013 8:45 pm
Outlook 2013 Incompatible with Exchange 2003
When trying to set up Microsoft Outlook 2013 for a user to use a Microsoft
Exchange 2003 server, I received the following message:
The resource that you are trying to use is located on an unsupported
version of Microsoft Exchange. Contact your e-mail administrator for
assistance.
That was followed by the message below:
Cannot start Microsoft Outlook. Cannot open the Outlook window. The
set of folders cannot be opened. The file
C:\Users\JDoe\AppData\Local\Microsoft\Outlook\JDoe@example.com.ost
is not an Outlook data file (.ost).
At
Office 2013 known issues, I found the following:
Workaround Outlook 2013 isn't supported on Exchange 2003 and connectivity is blocked. Please connect Outlook 2013 to Exchange 2007, 2010, or 2013.
[/os/windows/office/outlook]
permanent link
Sun, Mar 03, 2013 7:01 pm
Adding a Tile to the Windows 8 Start Screen
If you wish to add a tile to the Microsoft Windows 8 Start Screen, you can
do so by clicking on the
Start button which will appear at the lower,
left-hand corner of the screen when you move the mouse there, and then
typing the name of the application you wish to add or by right-clicking on
an empty area of the desktop and then clicking on
All Apps when
it appears at the lower, right-hand corner of the screen, which will show
all applications. Once you see the application you wish to add to the Start
Screen, right-click on it and select
Pin to Start. The item
will then appear on the Start Screen at the end of the entries when you
scroll to the right. If you wish to add it to a particular group of tiles you
can drag it to an existing group or create a new group by following
the instructions at
Creating Application Groups in Windows 8.
References:
-
Quick Tip: Create a tile on the Windows 8 Start Screen
Date: November 21, 2012
By Mark Kaelin
TechRepublic - A Resource for
IT Professionals
[/os/windows/win8]
permanent link
Sun, Feb 17, 2013 10:35 pm
Book Collector Missing Images
After upgrading
Book Collector
from
Collectorz.com to version
9.0.6, I found that images on detail pages for some templates were missing
when I used an existing book database on a shared network drive..
E.g., images for "hardback", "paperback", and "English".
Inside Book Collector, I clicked on Tools, Maintenance,
Update File Links, which showed me that the program was expecting
to find missing files in the
C:\Users\Administrator\Documents\Book Collector\Images\Listitemimages
directory.
There was no Listitemimages directory beneath the
Book Collector\Images directory on the network shared folder where
I had the book database, so I copied the Listitemimages directory
from the user folder, i.e., the C:\Users\Administrator\Documents Book
Coletor\Images\Listitemimages\ folder underneath that location.
I had already updated the location for image and template files by selecting
Tools, Optins, and changing the location for
User Templates Folder and then clicking on the Images
tab and modifying the values for Default Folder for Image Files and
Default Folder for Thumbnail Files to point to the
Templates and Images subdirectories on the shared network
location, so I closed Book Collector and reoopened it to see if that
would cause the missing images to now appear. They didn't, so I clicked
on Tools, Maintenance, and Update File Links
again. When the Update File Links window opened, I clicked on
the Update button. I saw a window stating "This will update 76 file
paths. Are you sure?" I clicked on Yes, but 0 files were updated,
so I highlighted all of the misssing files in the Update File Links
window by clicking on the top one, then scrolling to the bottom and clicking
on the bottom file while holding down the shift key. Then with all of the
files highlighted, I clicked on the Automatic button. A window opened
allowing me to browse to the Listitemimages subdirectory
I created at the shared network folder location. I then clicked on
OK. I then saw the new location appear in the New Folder
column in the Update File Links window for most, but not all of
the files. E.g., there was nothing listed in the New Folder column
for files associated with languages. I then clicked on
the Update button. I was notified that "42 of the 76 files have
been updated." I clicked on OK then Close.
After closing and reopening Book Collector 9.0.6, I saw there was
now a small image representing "hardback" and "paperback", depending
on the book, but there was still a missing image for "English".
So I went through the same process as before for updating the file links.
Again, I browsed to the Listitemimages directory. This time
Book Collector showed an entry under New Folder for most, but not all,
of the remaining missing files when I selected all of the files, browsed to
the Listitemimages subdirectory and clicked on Automatic.
I clicked on Update and saw "This will update 34 file paths. Are
you sure?" I clicked on Yes and saw "26 files have been updated."
I clicked on OK and then Close. The image for English
then appeared.
I then went through the same Update File Links process as before.
This time all but 2 of the missing files were found, though I was browsing
to the exact location as before when Book Collector had not found them. When
I clicked on Update this time, I was informed that 6 of the 8 missing
files had been updated.
I then repeated the Update File Links process once more. This
time the remaining two missing files were found. It's weird how Book Collector
couldn't find them all in one pass, but required me to repeat the process
multiple times, though each time I was browsing to the same location.
[/software/database/collectorz]
permanent link
Sun, Feb 17, 2013 6:13 pm
Collectorz Movie Database Locked
I installed the 9.0.6 version of
Movie Collector from
Collectorz.com
. When I attempted to open an existing movie database with it,
I saw the following message:
| Collectorz.com Movie Collector 9.0 |
|---|
| Opening the database in Read-Only mode, because another user (Jane) on
computer "Tarzan" is currently using this database in Writable mode.
[ OK ] |
Because Movie Collector thought the database was already in use it opened
it in read-only mode.
The database was located on a shared network drive, but when I checked
the mentioned computer and all other computers on the
LAN, I did not find any running
Movie Collector. I found a jane_movies.mvclck database file in the
same directory as the database jane_movies. I opened that file
with Notepad and saw the following:
<lockinfo><writable><client pcname="TARZAN" name="Jane Doe" key="196876543211" username="Jane"/></writable><readonly/></lockinfo>
I closed Movie Collector and deleted the .mvclck file. I was then able
to open the database with Movie Collector in write mode.
[/software/database/collectorz]
permanent link
Mon, Jan 21, 2013 9:16 pm
Performing a System Image Backup on a Windows 8 System
Microsoft Windows 8 comes with a utility that will you to perform a system image
backup of a system running Windows 8, but the process for performing an image
backup under Windows 8 isn't readily apparent. To do so, you can follow the
steps
here.
[/os/windows/win8]
permanent link
Mon, Jan 14, 2013 11:03 pm
Adding a Printer by IP Address to an OS X System
To add access to a printer over the network using the
Line
Printer Daemon (LPD) protocol, take the following steps:
-
Cllick on the Apple icon at the top left-hand corner of the screen.
-
Select System Preferences.
-
Select Print & Fax.
-
Click on the "+" underneath the list of printers to add a new printer.
-
Click on the IP icon in the toolbar at the top of the Add
Printer window.
-
Leave the Protocol value set to
Line Printer Daemon - LPD and
put the IP address of the printer in the Address field, e.g.
192.168.0.100. You can leave the Queue value
blank to use the default printer queue. The Name field will
be given the IP address by default. You can change it to something else,
if you like, to make it more recognizable to you. You can also identify
the location, if you like, e.g. "Xerox area". You can specify the print
driver to use, if you wish or use a generic print driver. E.g., if the
printer supports
postscript printing, you could opt for Generic PostScript Printer
in the Print Using field. Or you could choose the
Select Printer Software option for Print Using and
then pick the appropriate printer from the list presented, e.g.
"Xerox 700 Digital Color Press, 2.35.0".
-
Click on the Add button. If you are presented with an
Installable Options window, choose any options you know
are installed then click on Continue when finished.
[/os/os-x]
permanent link
Mon, Jan 14, 2013 9:31 pm
SSH Access to an OS X System
To allow
SSH access to
an Apple OS X system take the following steps:
- Click on the Apple icon on the top left hand corner of
the screen, which will display a menu of options.
- Select System Preferences
- Under the Internet & Network grouping, click on
Sharing
- Click on Remote Login, which is under the
Services
section.
- You will have the choice of permitting SSH access for
"All users" or "Only these users". If you select the latter, specify the
accounts for which you wish to grant SSH access by clicking on the "+"
beneath the two options and then selecting the accounts that will have
SSH access.
- Close the window by clicking on the "X" in the upper
left-hand corner of the window.
When logging in by SSH, use
the "short name" for the account, which can be found by going to
System Preferences, Accounts, then clicking on the
lock icon, and then selecting the account.
Note: written for Mac OS X 10.5.8, but will apply to other versions
as well.
[/os/os-x]
permanent link
Mon, Jan 07, 2013 10:05 pm
Printing to a Shared Windows Printer from OS X
If you need to print from a Mac system running OS X 10.5 or later to a
printer that is shared over a network from a Microsoft Windows system,
you can take these
steps.
[/os/os-x]
permanent link
Sun, Jan 06, 2013 2:48 pm
Using Firefox Cookies with Wget
If you need to use
wget to
access a site that relies on
HTTP cookies
to control access to the site, you can log into the site with Firefox and
use the Firefox add-on
Export Cookies to export all of the cookies stored by Firefox to a
file, e.g.
cookies.txt. After installing the add-on,
restart Firefox. You can then click on
Tools and choose
Export Cookies. Note: you may not get the cookie you need, if
you put Firefox in private browsing mode.
You can then use the cookies file you just exported with wget. E.g. presuming
the cookies file was named cookies.txt and was in the same
directory as wget, you could use the following:
wget --load-cookies=cookies.txt http://example.com/somepage.html
[/network/web/tools/wget]
permanent link
Sat, Jan 05, 2013 9:10 pm
Creating a Filter to Display HTTP Cookies
To create a filter to display
HTTP cookies in
Wireshark, take the
following steps:
-
Open Wireshark and click on Analyze.
-
Select Display Filters.
-
Click on New.
-
For filter name, type
HTTP cookie or whatever name you would
like and for filter string type http.cookie.
-
Click on OK. You should then see only the packets containing
HTTP cookies displayed.
Note: written for Wireshark 1.8.4, but should apply to other versions
as well.
References:
-
cookie and query strings
Wireshark Q&A
[/network/tools/sniffing/wireshark]
permanent link
Sat, Jan 05, 2013 8:59 pm
Installing Wireshark 1.8.4 and WinPcap 4.1.2 on a Windows 8 System
I installed Wireshark 1.8.4. When I started it, I was
informed that I hadn't specified an interface on which to perform a
capture. When I tried specifying an interface, I was informed there were
no interfaces on which a capture could be done. I saw "(Unable to load
WinPcap (wpcap.dll); you will not be able to capture packets."
I needed to install WinPcap in order
to utilize Wireshark, so I downloaded
WinPcap 4.1.2. When I ran
the installation program, a Program Compatibility Assistant
window opened stating "This program has compatibility issues." There
were two options: (1) Get help online and (2) Run the program without
getting help. I chose the latter. That resulted in a WinPcap 4.1.2
Setup window opening with the message "This version of Windows is
not supported by WinPcap 4.1.2. The installation will be aborted."
To resolve the problem, the following steps can be taken.
- Right-click on the installation file,
WinPcap_4_1_2.exe and select Properties.
- Click on the Compatibility tab.
-
Check the box next to "Run this program in compatibility mode for" and select
"Windows 7".
- Check the box for "Run this program as an administrator"
under Privilege level.
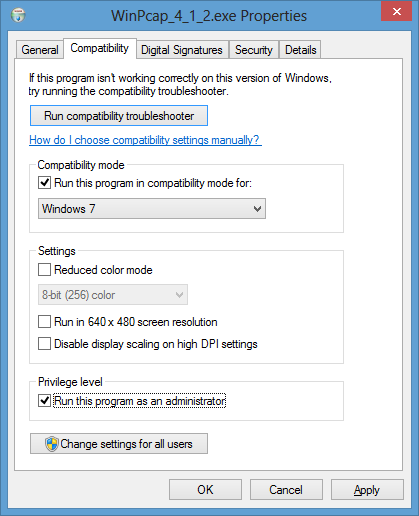
- Click on the OK button.
-
Run the installation program again and allow it to make changes to the system.
-
When the Program Compatibility Assistant window opens informing
you that "This program has compatibility issues", select "Run the program
without getting help". The WinPcap 4.1.2 Setup window should
then open allowing you to proceed with the installation.
References:
-
[Winpcap-users] Windows 8
By Andrew Stewart
Date: July 6, 2012
WinPcap
-
Installing WIRESHARK/WinPCap on Windows 8 RTM
By Kaushal Kumar
Panday
Date: August 7, 2012
Unleashed
[/network/tools/sniffing/wireshark]
permanent link
Tue, Jan 01, 2013 5:57 pm
Creating Application Groups in Windows 8
Windows 8 has a new "metro" user interface which puts applications
on the desktop in tiled groups instead of using groups under
Programs or
All Programs as in prior versions of
Windows. When you have a lot of programs installed on a system, finding
what you want within one large group may be difficult. You can group
tiles in categoris of your own making with Windows 8, however.
[ More Info ]
[/os/windows/win8]
permanent link

Privacy Policy
Contact

















 in the lower-right
corner of your screen.
in the lower-right
corner of your screen.











