←December→
| Sun |
Mon |
Tue |
Wed |
Thu |
Fri |
Sat |
| |
|
|
|
|
|
1 |
| 2 |
3 |
4 |
5 |
6 |
7 |
8 |
| 9 |
10 |
11 |
12 |
13 |
14 |
15 |
| 16 |
17 |
18 |
19 |
20 |
21 |
22 |
| 23 |
24 |
25 |
26 |
27 |
28 |
29 |
| 30 |
31 |
|
|
|
|
|
|
|
Sun, Dec 30, 2007 11:12 pm
LimeWire
After I had cleaned a lot of malware from someone's home system, I found
LimeWire on the system.
McAfee security software was on
the system and prompted me as to whether I wanted to allow LimeWire
to run or block it. My last experience with LimeWire was several years
ago. At that time I had found the free version came bundled with
adware/spyware, so I had the McAfee software block LimeWire. After
checking on the current version, though, I found it no longer comes
bundled with adware/spyware according to the developer, Lime Wire LLC
(see
LimeWire's response: Spyware) and the
Wikipedia article
on LimeWire.
Granted, one should never rely on the developer's or
distributors' word on such matters, since they will often simply define
the terms "adware" and "spyware" so that they don't include techniques
used by their software, instead of using the commonly accepted definitions.
But, as far as I can determine, LimeWire has indeed been distributed,
even in the free version, without adware or spyware for several years now.
[ More Info ]
[/network/p2p]
permanent link
Sun, Dec 30, 2007 8:38 pm
AdSpy.TTC Detected by Spybot
I ran a scan of a family member's system with
Spybot Search & Destroy
version 1.5, which reported
AdSpy.TTC based on
the presence of a registry entry, but when I checked the system for
C:\Program Files\MSN Apps\MSN Toolbar\MSN
Toolbar\01.02.5000.1021\en-us\msntb.dll, which was the file
referenced by the registry entry Spybot detected, I did not see it on
the system and
CastleCops
identified the
CLSID key referenced as being associated with legitmate software.
[ More
Info ]
[/security/trojans]
permanent link
Sat, Dec 15, 2007 10:58 pm
RPC Won't Start Because of Missing Svchost File
On a Windows XP SP2 system where I saw the following error message when I tried
to start the Remote Procedure Call (RPC) service, the problem was due to a
missing
svchost.exe file in
C:\Windows\System32\
| Services |
Could not start the Remote Procedure Call
(RPC) service on Local Computer.
Error 2: The system cannot find the file specified.
OK
|
The location where svchost.exe should be located can be found in
the registry at HKLM\SYSTEM\CurrentControlSet\Services\RpcSs\ImagePath.
I copied the file from another Windows XP SP2 system. The file was 14KB and
was dated 8/4/2004 with an MD5 hash of 8f078ae4ed187aaabc0a305146de6716
.
I discovered the svchost.exe file was missing while trying to
determine why the taskbar wasn't displaying properly - it was 1/2 height
and couldn't be stretched, even though unlocked, there were no programs shown
on the taskbar, and the Start button was missing.
References:
-
Infected Gateway Laptop -
December 2007
[/os/windows/xp]
permanent link
Tue, Dec 11, 2007 8:33 pm
Infected Dell Inspiron 6000 Laptop
When checking a Dell Inspiron 6000 laptop fo malware, I found a very
large burden of malware on the system. The system also had no network
connectivity, since the
tcpip.sys file was missing from
c:\windows\system32\drivers. Because of the missing
tcpip.sys file, whenever I issued the
ipconfig
command, I would see the following:
C:\WINDOWS\system32>ipconfig
Windows IP Configuration
An internal error occurred: The request5 is not supported.
Please contact Microsoft Product Support Services for further help.
Additional information: Unable to query host name.
It took several days for me to remove all of the malware and restore network
connectivity.
[ More Info ]
[/security/removal-logs]
permanent link
Tue, Dec 04, 2007 11:09 pm
Reconfiguring IP Interface for DHCP from the Command Line
The IP address on a Windows XP system can be changed from a static
value to a
DHCP assigned
IP address from the command line using the command below (presuming you wish
to change the IP address for the interface "Local Area Connection", since you
may have multiple or differently named network connections).
netsh interface ip set address "Local Area Connection" dhcp
You can also set the
DNS servers from the command line using the command below.
netsh interface ip set dns "Local Area Connection" dhcp
References:
-
Configure TCP/IP from the Command Prompt
By Daniel Petri
Petri IT Knowledgebase
[/os/windows/commands]
permanent link
Tue, Dec 04, 2007 10:48 pm
Resetting Password with Offline NT Password & Registry Editor
The date on a repaired laptop I had returned to me, after a motherboard
problem was fixed, was January 28, 2150. The laptop is running Windows
XP Professional. I knew the password for my normal user account on the
laptop, but couldn't remember the password for my administrator account
on the system.
I downloaded
Offline
NT Password & Registry Editor in
ISO format. After
extracting the .iso file from the .zip file I downloaded, I created a bootable
CD from the ISO file. I booted from the boot CD and saw the following.
Disks:
Disk /dev/sda: 80.0 GB, 80026361856 bytes
Candidate Windows partitions found:
1 : /dev/sda1 76316MB BOOT
Please select partition by number or
q = quit
d = automatically start disk drivers
m = manually select disk drivers to load
f = fetch additional drivers from floppy / usb
a = show all partitions found
l = show propbable Windows (NTFS) partitions only
Select: [1]
I hit
Enter to take the default option of one for
/dev/sda1. I then saw the following.
Selected 1
Mounting from /dev/sda1, with filesystem type NTFS
NTFS volume version 3.1.
=========================================================
Step TWO: Select PATH and registry files
=========================================================
What is the path to the registry directory? (relative to windows disk)
[WINDOWS/system32/config] :
Since
WINDOWS/system32/config was the correct location, I hit
Enter and had the opportunity to select the password reset option
by hitting
Enter again.
Select which part of registry to load, use predefined choices
1 - Password reset [sam system security]
2 - RecoveryConsile parameters [software]
q - quit - return to previous
[1] :
For step 3, "Password or registry edit", I had the option to "edit user
data and passwords", which I chose by hitting
Enter.
<>========<> chntpw Main Interactive Menu <>========<>
Loaded hives: <sam> <system> <security>
1 - Edit user data and passwords
2 - Syskey status & change
3 - RecoveryConsole settings
9 - Registry editor, now with full write support!
q - Quit (you will be asked if there is something to save)
What to do? [1] ->
I was then presented with a list of the local accounts on the system. Those
that were disabled or locked were marked as "dis/lock". I
chose the administrator account for which I wished to reset the password
and was presented with information on the account and the opportunity to
blank the password, which is the option I chose.
Failed login count: 1, while max tries is: 5
Total login count: 68
- - - - User Edit Menu:
1 - Clear (blank) user password
2 - Edit (set new) user password (careful with this on XP or Vista)
3 - Promote user (Make user an administrator)
(4 - Unlock and enable user account) [seems unlocked already]
q - Quit editing user, back to user select
Select: [q] >
I then saw "Password cleared!". I then hit "!" to quit modifying accounts
and then "q" to quit. At the next step, step 4, you will be asked to confirm
whether to actually write the changes to disk. The default response is "n",
so you need to hit "y" to actually apply the changes you've requested.
You will then see "***** EDIT COMPLETE *****". Hitting
Enter will
give you a Linux shell prompt of "$". You can then reboot the system;
remove the CD so the system won't attempt to boot from it again.
When the system booted into Windows XP, I tried logging into the
administrator account. I saw the message "Your password has expired and must be
changed." I entered a new password and was able to login to the administrator's
account.
[/os/windows/utilities/sysmgmt]
permanent link
Fri, Nov 30, 2007 11:00 pm
Mounting a Dirty NTFS Volume
If you try to mount an NTFS volume on Linux that was used on a Windows
system and get the message below, then Windows was not shut down properly.
E.g. the system may have crashed or there was a power failure.
$LogFile indicates unclean shutdown (0, 0)
Failed to mount '/dev/sda1': Operation not supported
Mount is denied because NTFS is marked to be in use. Choose one action:
Choice 1: If you have Windows then disconnect the external devices by
clicking on the 'Safely Remove Hardware' icon in the Windows
taskbar then shutdown Windows cleanly.
Choice 2: If you don't have Windows then you can use the 'force' option for
your own responsibility. For example type on the command line:
mount -t ntfs-3g /dev/sda1 /mnt/hdd -o force
Or add the option to the relevant row in the /etc/fstab file:
/dev/sda1 /mnt/hdd ntfs-3g defaults,force 0 0
Presuming the volume is
/dev/sda1 and you want to mount it
at
/mnt/hdd, you can mount the volume read-only with
mount -r /dev/sda1 /mnt/hdd. Or you can force a mount in
read-write mode with
mount /dev/sda1 /mnt/hdd -o force.
But it might be best to run Windows
chkdsk or a utility
with similar functionality first, since the fact that the dirty bit
is set could indicate corruption to the volume's file structure.
[/os/unix/commands/mount]
permanent link
Fri, Nov 30, 2007 7:23 am
Comcast NTP Servers
I wanted to configure a user's home router to synchronize its time with
a
Network
Time Protocol (NTP) server, so that its log entries would have
accurate time stamps. Since the user had a Comcast-provided connection
to the Internet, I decided to use a Comcast NTP server. The one that I
used is ntp01.inflow.pa.bo.comcast.net [68.87.96.5].
If you want to verify that a NTP server is available and responding to
NTP queries, you can go to
Query NTP server and enter the Fully Qualified Domain Name (FQDN) or
IP address of the system to be queried to submit an NTP query to the system
from that site. If the queried system is responding to NTP requests, you will
see something similar to the following:
Output of NTP server at 68.87.96.5
ntpdate
30 Nov 16:12:42 ntpdate[23942]: ntpdate 4.1.1@1.786 Tue Sep 23 17:37:40 UTC 2003 (1)
server 68.87.96.5, stratum 2, offset 0.001361, delay 0.10997
30 Nov 16:12:42 ntpdate[23942]: adjust time server 68.87.96.5 offset 0.001361 sec
If you see "stratum 0" displayed on the results page, the system is not
responding to NTP queries. The offset and delay values will be zero as
well in that case.
You can find a list of publicly accessible NTP servers at
NTP.Servers Web
.
[/network/ntp]
permanent link
Wed, Nov 28, 2007 5:24 pm
Multiple IP Address on a Solaris System
I needed to assign a second
IP
address to a network interface on a Solaris 2.7 system. The system
has 2 network cards, designated hme0 and hme1, each with its own IP
address, but I needed to assign a second IP address to the hme0 interface.
A webserver, which would normally be at the second IP address, was down
and I wanted the webserver on this particular system to assume the functions
of the offline system temporarily by responding at the IP address of the server
that was down.
In order to have a Solaris 2.x system listen on a second IP address on
an interface, the following steps can be taken.
- Create an entry in /etc/hosts for the second hostname. In
this particular case I added a
myhost2 entry, so that I had
the following entries in the file.
127.0.0.1 localhost
10.0.74.214 myhost1.example.com myhost1 loghost
10.0.74.193 myhost2.example.com myhost2
192.168.1.1 janus
Myhost1 and myhost2 will apply to the same network interface, whereas
janus is for the second network interface card in the system. The
myhost2 entry is the only new entry.
- Create /etc/hostname.hme:n files, or /etc/hostname.le0:n
files depending on your system configuration, that contain the hostname
for the virtual host n. You don't need to create hostname.hme0:0
as it is the same as hostname.hme0.
The above changes will cause the virtual hosts to be configured at boot
time. If you don't want to reboot the system, you can use the
ifconfig command to have the system start responding on
the second IP address without rebooting.
# ifconfig hme0:1 up
# ifconfig hme0:1 128.183.72.193 netmask 255.255.255.0
References:
-
FAQs document :How to setup multiple ip for Solaris
Date: March 30, 1998
Freelab
-
Configuring Networking
By: Keith Parkansky
Date: May 1, 2002
Solaris x86
[/os/unix/solaris]
permanent link
Tue, Nov 27, 2007 10:44 pm
Mounting a Hibernated Drive
I went back to working on a problem where I couldn't get
a Windows XP system to resume from hibernation
1 by trying
to examine the
hiberfil.sys file, but wasn't able
to get much further today.
References:
-
System Won't Resume from Hibernation
MoonPoint Support
[ More Info ]
[/os/unix/linux/ubuntu]
permanent link
Wed, Nov 21, 2007 12:39 pm
BlackBerry Email Filters
For BlackBerry Desktop Manager 4.2.2 (Apr 26 2007), take the steps below.
For BlackBerry Desktop Manager Version 4.0.1.10 (Apr 27 2005), see
Creating an Email Filter for a Blackberry.
- Open the BlackBerry Desktop Manager.
- Double-click on Email Settings.

- Click on the Filters tab.
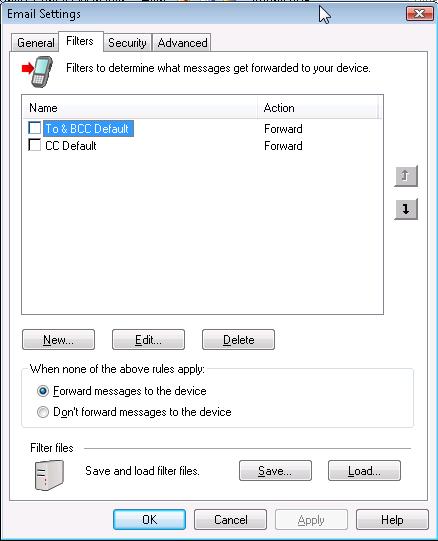
- Click on the New button.
- At the Add Filter window type whatever name you wish to
use for the filter in the Filter Name field.

- You can filter on the "from", "sent to", "subject", and "body" fields.
If you did not want to forward messages from a particular email address, you
would check the From checkbox. If you didn't want to forward messages
from multiple senders, you could put all of their email addresses in the
From field, separating the addresses by semicolons. You can also use
an asterisk as a wildcard to block multiple sending addresses. For instance if
you wanted to block all email from xyzcorp.com senders, you could put
*@xyzcorp.com in the From field.
- Check the "Don't forward message to the device" checkbox.
- Click on OK.
- Click on OK again at the Email Settings window.
[/network/email/blackberry]
permanent link
Tue, Nov 20, 2007 8:47 pm
MXToolBox
If you need to check the
Mail
Exchanger (MX) record for a domain, you can do so online using an MX
Lookup Tool at
MXToolBox. Once
you have looked up MX information for a domain, you are given the option
of running Simple Mail Transfer Protocol (SMTP) diagnostics, which will
connect to a mail server via SMTP, perform a simple Open Relay Test and verify
the server has a reverse DNS (PTR) record. It will also measure the response
times for the mail server, giving you an indication of whether they are
good or bad.
You also have the option, after you've looked up the MX
information for a domain, to perform a blacklist check.
That test will check a mail server IP address against 147 DNS based email
blacklists. (Commonly called Realtime blacklist,
DNSBL or
RBL
). If your mail server has been blacklisted, some email you send may not
be delivered. Email blacklists are a common method employed by email server
administrators to reduce spam.
[/network/email/info]
permanent link
Sun, Nov 18, 2007 6:57 pm
Iomega Clik! Drive
While tyring to make space in my garage for other stuff, I came across
an unopened box with an Iomega Clik! PC Card Drive plus a 4-pack of the 40 MB
Clik! disks. I've posted
information
on the drive here to use for an
eBay
listing.
[/hardware/storage/iomega]
permanent link
Fri, Nov 16, 2007 7:34 pm
Linux LiveCD SATA Support
I booted a system which has a Serial ATA (SATA) drive in it from a
Knoppix 5.0.1
LiveCD, but could not
get the operating system to recognize the presence of the hard drive. So I
then booted from a
Slax LiveCD, but it
did not recognize the drive either.
The version of Slax I tried was the SLAX KillBill Edition 5.1.8.1. I then
booted the system with a
Sabayon
3.4e DVD. I was able to access the SATA drive then.
The problem is apparently due to the other distributions of Linux
not recognizing the Serial ATA chipset on the motherboard of the
system, at least for the versions that I was using. The system
has a PCChips
A31G V:1.0 motherboard According to Serial ATA (SATA)
chipsets ? Linux support status, "Some SATA chipsets have been
supported since practically forever, as their programming interfaces
are unchanged from PATA predecessors. Others are brand-new and require
new drivers from scratch.
Refererences:
-
LiveCD
Wikipedia - the free encyclopedia
-
Serial ATA (SATA) chipsets ? Linux support status
Revised: February 27, 2007
Linuxmafia
[/os/unix/linux/knoppix]
permanent link
Wed, Nov 14, 2007 10:30 pm
System Won't Resume From Hibernation
When I tried to reboot a laptop after putting it into hibernation mode,
I kept getting the message "The last attempt to restart the system from its
previous location failed. Attempt to restart again?" I had the option
to "Delete restoration data and proceed to sytem boot menu" or
"Continue with system restart". I tried to continue, but the system
would just reboot and then I got the same menu again.
[ More
Info ]
[/os/windows/xp]
permanent link
Wed, Nov 14, 2007 9:49 pm
Netscape 7.2 Unread Mail Number Appears to be Wrong
A user of Netscape 7.2 informed me that the number displayed for the number of
unread email messages in his inbox was not matching the number he saw
highlighted as unread. He had a problem earlier that day with Netscape
when his system ran very low on the amount of free space on his hard disk.
I deleted a lot of files from a temp folder and deleted other no longer needed
files. I then deleted his inbox.msf file, because I believed that index file
had become corrupted (see
Netscape
7.2 Inbox Corrupted for information on Netscape mailbox corruption)
due to the disk space issue.
The .msf file is a
Mail Summary File. It does not contain the messages for a mailbox, only an
index of those messages to make sorting and locating messages quicker. If you
delete an msf file, which you should only do without Netscape being open, the
mailbox messages themselves remain and the index will be rebuilt the next
time you open Netscape and access the mailbox.
However, even after deleting the inbox.msf file twice and having Netscape
rebuild it, the user reported the problem recurring. I sent a few test
messages to his address. When I checked his inbox they were highlighted as
unread. I marked the entire folder as read to reset the counter. He said that
sometime later he was having the same problem. For instance he might see
145 listed as the number of unread messages, but only a couple would be
bolded indicating they were unread. And when I sorted messages by their
read status, I would only see a couple.
I finally traced the issue to Netscape's "view" options.
Netscape offers different "views" for your mailboxes. You can chose
to view all mail or restrict the display of messages in various ways,
e.g. perhaps you only want to see unread mail, or messages marked as
important, or messages with attachments, or just email from the last
5 days. Another option is to display only mail from "People I Know",
which I believe is email from addresses in your address book, though
I'm not sure if in Netscape 7.2 it inclues email addresses from the
Collected
Address Book as well.
When I clicked on "View" then "Messages", I saw that Netscape was set to
display messages from "People I Know" rather than "All". I changed the
setting to "All".
[/network/email/clients/netscape]
permanent link
Mon, Nov 12, 2007 9:02 pm
Silent Runners
Silent Runners is a Visual
Basic script, which can be used to scan a system for software that
starts automatically when Windows starts, which may aid you in determining
if a system is infected with malware.
[ More Info ]
[/languages/vbs]
permanent link
Mon, Nov 12, 2007 3:35 pm
Rejecting Email To a Specific Address in Sendmail
In checking the previous night's mail server log, I noticed a large
number of messages addressed to
someuser@frostdragon.com. There is
an account,
someuser on the system and email addressed to
someuser@moonpoint.com should go through, but, though email for
both domain names is processed by the server, email to
someuser@frostdragon.com should not be delivered. Presumably,
since
someuser is acually a common male name, email addressed to
someuser@frostdragon.com is from some spammer trying common
names to deliver his spam.
I edited /etc/mail/access and added the line below:
someuser@frostdragon.com 550 Mailbox disabled for this recipient
The 550 is a standard error code for an email server to return
to an email client when email is rejected. You can specify whatever message
you wish after it. In this case I chose "Mailbox disabled for this recipient".
I could have just used the following line instead, if I didn't want to specify
my own specific error message.
someuser@frostdragon.com REJECT
After executing the command makemap hash /etc/mail/access
</etc/mail/access to rebuild the access database file, you can test
the block by establishing a telnet connection to port 25 on the server,
issuing an helo or ehlo command, then a mail
from command with any address as the "from" address, and then a
rcpt to command with the relevant recipient address.
mail from: someone@example.com
250 2.1.0 someone@example.com... Sender ok
rcpt to: someuser@frostdragon.com
550 5.0.0 someuser@frostdragon.com... Mailbox disabled for this recipient
rcpt to: someuser@moonpoint.com
250 2.1.5 someuser@moonpoint.com... Recipient ok
quit
221 2.0.0 frostdragon.com closing connection
From the above, I can see that email to the address I wanted marked as invalid
is rejected immediately, but email to the same username at a different domain
name gets through. Mail with a "from" address of
someuser@frostdragon.com would still be accepted,
even though it is now rejected as a "to" address.
Since I don't want the server to accept email if that address appears as
a "from" address either, I added the line below to /etc/mail/access
as well and rebuilt the access database with makemap hash /etc/mail/access
</etc/mail/access.
From:someuser@frostdragon.com 550 We don't accept mail from spammers
If you try sending using a "from" address of someuser@frostdragon.com
now, the message will be rejected. However, if you test the block by
the telnet e.g. telnet frostdragon.com 25 and then issuing
an ehlo or helo command followed by mail
from and rcpt to commands, you won't see the rejection
message until you've entered the rcpt to command, i.e. it
doesn't occur when the mail from command is issued.
mail from:<someuser@frostdragon.com>
250 2.1.0 <someuser@frostdragon.com>... Sender ok
rcpt to:<myself@moonpoint.com>
550 5.0.0 <myself@moonpoint.com>... We don't accept mail from spammers
References:
-
FEATUREs for check_* in sendmail 8.9
Sendmail.Org
-
Configuring sendmail to Reject Unsolicited Mail
HP Technical Documentation
-
Anti-Spam Configuration Control
Sendmail.Org
-
SMTP Service Extension for Returning Enhanced Error Codes
The Internet Engineering Task Force (IETF)
-
22.6. The /etc/mail/access and access.db files
Securing and Optimizing Linux
RedHat Edition - A Hands on Guide
[/network/email/sendmail]
permanent link
Sat, Nov 10, 2007 8:43 pm
Red Hat 9 RPMs
The RPMs on the Red Hat 9 (Shrike) CDs:
By Disc
Alphabetical listing
Additional packages in RPM format can be found at
Dag Wieër's
Apt/Yum RPM package overview.
[/os/unix/linux/redhat]
permanent link
Thu, Nov 08, 2007 6:24 pm
Root Hints
I was notified by someone that the L root name server had changed. To
see what root name servers one of my DNS servers, running Redhat
Linux 9, was using, I ran
dig and saw the following output:
# dig
; <<>> DiG 9.2.1 <<>>
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 60704
;; flags: qr rd ra; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 2
;; QUESTION SECTION:
;. IN NS
;; ANSWER SECTION:
. 517448 IN NS G.ROOT-SERVERS.NET.
. 517448 IN NS H.ROOT-SERVERS.NET.
. 517448 IN NS I.ROOT-SERVERS.NET.
. 517448 IN NS J.ROOT-SERVERS.NET.
. 517448 IN NS K.ROOT-SERVERS.NET.
. 517448 IN NS L.ROOT-SERVERS.NET.
. 517448 IN NS M.ROOT-SERVERS.NET.
. 517448 IN NS A.ROOT-SERVERS.NET.
. 517448 IN NS B.ROOT-SERVERS.NET.
. 517448 IN NS C.ROOT-SERVERS.NET.
. 517448 IN NS D.ROOT-SERVERS.NET.
. 517448 IN NS E.ROOT-SERVERS.NET.
. 517448 IN NS F.ROOT-SERVERS.NET.
;; ADDITIONAL SECTION:
F.ROOT-SERVERS.NET. 172107 IN A 192.5.5.241
J.ROOT-SERVERS.NET. 172107 IN A 192.58.128.30
;; Query time: 169 msec
;; SERVER: 207.233.128.10#53(207.233.128.10)
;; WHEN: Thu Nov 8 16:15:46 2007
;; MSG SIZE rcvd: 260
I only saw the addresses for two of the thirteen root servers listed. The
servers are named A.ROOT-SERVERS.NET. through
M.ROOT-SERVERS.NET. as shown
by the output of a dig command below.
# dig . NS @f.root-servers.net
; <<>> DiG 9.2.1 <<>> . NS @f.root-servers.net
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 19934
;; flags: qr aa rd; QUERY: 1, ANSWER: 13, AUTHORITY: 0, ADDITIONAL: 13
;; QUESTION SECTION:
;. IN NS
;; ANSWER SECTION:
. 518400 IN NS H.ROOT-SERVERS.NET.
. 518400 IN NS I.ROOT-SERVERS.NET.
. 518400 IN NS J.ROOT-SERVERS.NET.
. 518400 IN NS K.ROOT-SERVERS.NET.
. 518400 IN NS L.ROOT-SERVERS.NET.
. 518400 IN NS M.ROOT-SERVERS.NET.
. 518400 IN NS A.ROOT-SERVERS.NET.
. 518400 IN NS B.ROOT-SERVERS.NET.
. 518400 IN NS C.ROOT-SERVERS.NET.
. 518400 IN NS D.ROOT-SERVERS.NET.
. 518400 IN NS E.ROOT-SERVERS.NET.
. 518400 IN NS F.ROOT-SERVERS.NET.
. 518400 IN NS G.ROOT-SERVERS.NET.
;; ADDITIONAL SECTION:
A.ROOT-SERVERS.NET. 3600000 IN A 198.41.0.4
B.ROOT-SERVERS.NET. 3600000 IN A 192.228.79.201
C.ROOT-SERVERS.NET. 3600000 IN A 192.33.4.12
D.ROOT-SERVERS.NET. 3600000 IN A 128.8.10.90
E.ROOT-SERVERS.NET. 3600000 IN A 192.203.230.10
F.ROOT-SERVERS.NET. 3600000 IN A 192.5.5.241
G.ROOT-SERVERS.NET. 3600000 IN A 192.112.36.4
H.ROOT-SERVERS.NET. 3600000 IN A 128.63.2.53
I.ROOT-SERVERS.NET. 3600000 IN A 192.36.148.17
J.ROOT-SERVERS.NET. 3600000 IN A 192.58.128.30
K.ROOT-SERVERS.NET. 3600000 IN A 193.0.14.129
L.ROOT-SERVERS.NET. 3600000 IN A 199.7.83.42
M.ROOT-SERVERS.NET. 3600000 IN A 202.12.27.33
;; Query time: 235 msec
;; SERVER: 192.5.5.241#53(f.root-servers.net)
;; WHEN: Thu Nov 8 16:22:59 2007
;; MSG SIZE rcvd: 436
I also checked the status of the DNS service on the system with the
rndc status command and saw the following:
# rndc status
number of zones: 6
debug level: 0
xfers running: 0
xfers deferred: 0
soa queries in progress: 0
query logging is OFF
server is up and running
When I checked the /var/named/named.ca file on the system, I
found it was dated January 24, 2003, so was almost 5 years old, since
the current date is November 8, 2007. I backed up the current
named.ca file and then overwrote the file with the latest
information.
# dig . NS @f.root-servers.net >/var/named/named.ca
I then restarted the DNS server with
/etc/init.d/named restart.
Note: if you see the following when you check the DNS server status,
try issuing the /etc/init.d/restart command again.
# rndc status
rndc: connect failed: connection refused
The root hints file, /var/named/named.ca should be updated
periodically, which I hadn't been doing on the server. A script to
do so can be found at
Keeping it
working. The script will have to be customized for your particular
system though, e.g. I would need to use named.ca instead of
root.hints for the filename. And you also need to substitute
the name of a system or an IP address of a system that should normally be
reachable over your Internet connection for some.machine.net
References:
-
Configuring DNS > Configuring named
O'Reilly - Safari Books Online
-
LOCAL AREA NETWORK DOMAIN NAME SYSTEM (DNS)
Small Enterprise Networking and
Computing Primer
-
Keeping it working
Linux.com
[/network/dns]
permanent link
Wed, Nov 07, 2007 10:34 pm
Restart.Exe
When I scanned a system for malware,
BitDefender Free Edition v10 reported the presence of
Spyware.Destart.A in
Restart.exe, which was in
the directory
C:\Windows\System32\Tools. I submitted the file to
VirusTotal for analysis and also
to
Jotti's Online Malware Scan.
Other antimalware software used by those sites also reported the file
as malware. However, after further checking, I believe that the file
is actually innocuous.
[ More Info ]
[/security/spyware]
permanent link
Sun, Nov 04, 2007 7:20 pm
Numbered NIC in Device Manager
A Network Interface Controller (NIC) built into a
PCChips A31G V:1.0 motherboard was
appearing as a "Sis190 100/10 Ethernet Device #3" in the Windows Device
Manager. I wanted to remove the "#3" from the end of the description.
I tried fixnetwork.vbs, but that didn't work. I tried manually removing
registry entries, but was unsuccessful in resolving the issue that way either.
[ More Info ]
[/hardware/network/nic/sis]
permanent link
Sun, Nov 04, 2007 1:08 pm
No MAC Address on SiS190 NIC
I had a problem with a
PCChips
motherboard with a
Silicon Integrated Systems
(SiS) chipset not working because it had all zeros listed for the
MAC address. Fortunately, the MAC, aka Ethernet, address can be changed
through the Windows Device Manager.
[ More Info ]
[/hardware/network/nic/sis]
permanent link
Mon, Oct 29, 2007 11:12 pm
Root Access Using Ubuntu Live CD
I thought I would try
Ubuntu, so I booted
a system from a Ubuntu 7.10 Desktop CD I created from the .iso file
I downloaded. The system didn't have access to a
DHCP
server, so I needed to manually set the network information for the system.
But I didn't know the default password assigned to the root account by
Ubuntu. I discovered at
Ubuntu Default Root Password or the sudo way that the
root account is created without a predefined password and that you can't
log into it. The suggested action for gaining root access was to use
sudo sh, which did give me root access. I was then able to
assign an IP address, network mask, and default gateway address.
# ifconfig eth0 192.168.1.5 netmask 255.255.255.0
# route add default gw 192.168.1.1 eth0
[/os/unix/linux/ubuntu]
permanent link
Sat, Oct 27, 2007 3:37 pm
ibmonitor
ibmonitor is a Perl script that can be used to
monitor bandwidth usage.
Interface Received Sent Total
Kbps Kbps Kbps
eth0 189.04 4.00 193.12
lo 0.00 0.00 0.00
All 189.04 4.00 193.12
Press 'q' to quit... Elapsed time: 0 hrs, 0 mins, 4 s
If you hit the m key while the program is running, it will show the maximum
bandwidth used while it has been running. You can also start the program with
ibmonitor --max to display the maximum bandwidth utilization.
Interface Received Sent Total
Kbps Kbps Kbps
eth0 294.40 5.92 300.32
|---- Max 443.12 64.40 448.40
lo 0.00 0.00 0.00
|---- Max 20.24 20.24 40.56
All 294.40 5.92 300.32
|---- Max 453.28 74.56 468.64
Press 'q' to quit... Elapsed time: 0 hrs, 0 mins, 43 s
ibmonitor is a command
line program which will run
on a linux console or xterm (rxvt, konsole, gnome-terminal, etc)
usage: ibmonitor [ --bits ] [ --bytes ] [ --max ] [ --avg ] [
--interval n ] [--data]
[ --colors | --nocolors ] [--dev regex] [--file procfile]
[ --help ] [--version]
The following command line options (and their explanation) are
available:
| --bits |
Show output values in KBits/sec.
This is the default |
| --bytes |
Show output values in KBytes/sec |
| --max |
Show maximum values per interface |
| --avg |
Show average values per interface |
--interval n
|
Set time interval as n seconds. The
default is 2 seconds |
| --data |
Show data transferred in KB/MB/GB |
| --colors |
Show some fancy coloring! (This is
the default) |
| --nocolors |
No fancy coloring please!
|
--dev regex
|
Show output from device matching
regex
|
--file proc
|
Specify which file to use in the
proc filesystem
for the interface byte counter
|
| --help |
Show help and exit
|
| --version |
Show version number and exit
|
While running,
ibmonitor can read
the input key from the user
and dynamically change its output display format depending on the key
pressed.
The following keys are supported. Note that
ibmonitor responds
immediately
to the single keystroke. ie. The 'Enter' key need not be pressed
q
|
[q]uit |
1 - 9
|
Set sleep time interval (in seconds)
to the digit entered |
| m |
Toggle display of [m]ax bandwidth |
a
|
Toggle display of [a]verage bandwidth |
i
|
Toggle display of values in
KB[i]ts/sec (Kbps) |
y
|
Toggle display of values in
KB[y]tes/sec (KBps) |
d
|
Toggle display of [d]ata
transferred |
s
|
Shift interface up/down.
This should be followed by the interface number,
and then the direction (u or d)
|
r
|
[R]eset all values |
? / h
|
Help screen for interactive commands |
References:
-
ibmonitor Interactive Bandwidth Monitor
SourceForge.net
-
Perl ReadKey Module for ibmonitor
Date: October 26, 2007
MoonPoint Support
[/languages/perl]
permanent link
Fri, Oct 26, 2007 5:32 pm
Perl ReadKey Module for ibmonitor
I tried installing
ibmonitor
using the
ibmonitor-1.4-1.noarch.rpm RPM file I obtained from
ftp://download.fedora.redhat.com/pub/fedora/linux/extras/6/i386.
However, when I tried to install it, I got a message indicating the
Term::Readkey module was missing.
# rpm --install ibmonitor-1.4-1.noarch.rpm
warning: ibmonitor-1.4-1.noarch.rpm: V3 DSA signature: NOKEY, key ID 1ac70ce6
error: Failed dependencies:
perl(Term::ReadKey) is needed by ibmonitor-1.4-1
# perldoc -l Term::ReadKey
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
But when I used the perldoc -l command to check on whether all
of the required modules for ibmonitor were present, I saw it listed.
$ perldoc -l Term::ANSIColor
/usr/lib/perl5/5.8.0/Term/ANSIColor.pm
$ perldoc -l Term::ReadKey
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
$ perldoc -l Time::HiRes
/usr/lib/perl5/vendor_perl/5.8.0/i386-linux-thread-multi/Time/HiRes.pm
I also saw it listed when I used the
find-modules.pl
script I have on the system.
# ./find-modules.pl | grep -i ReadKey
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
When I used the one-line Perl command perl -MTerm::ReadKey -el
Perl did not complain. Nor did it complain when I tried perl -e
'use Term::ReadKey;'. If the module wasn't found by Perl it should
complain it couldn't locate the module anywhere when I used either command.
And when I used the
List Perl Modules CGI
script, I have on the system, I also saw it listed there. So I didn't know why
I got the message indicating the module is missing when I tried to install
ibmonitor.
I used the locate command to look for any other occurrences
of the file ReadKey.pm on the system, which showed the following.
# locate ReadKey.pm
/root/.cpan/build/TermReadKey-2.21/ReadKey.pm
/root/.cpan/build/TermReadKey-2.21/blib/lib/Term/ReadKey.pm
/usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
I decided to try downloading and installing the module again through
CPAN.
# perl -MCPAN -e shell
Undefined value assigned to typeglob at (eval 14) line 15, line 11.
Warning [/etc/inputrc line 11]:
Invalid variable `mark-symlinked-directories'
cpan shell -- CPAN exploration and modules installation (v1.76)
ReadLine support enabled
cpan> install Term::ReadKey
PAN: Storable loaded ok
Going to read /root/.cpan/Metadata
Database was generated on Thu, 24 Nov 2005 14:54:20 GMT
CPAN: LWP::UserAgent loaded ok
Fetching with LWP:
ftp://archive.progeny.com/CPAN/authors/01mailrc.txt.gz
LWP failed with code[500] message[LWP::Protocol::MyFTP: connect: timeout]
Fetching with Net::FTP:
ftp://archive.progeny.com/CPAN/authors/01mailrc.txt.gz
Fetching with LWP:
ftp://carroll.cac.psu.edu/pub/CPAN/authors/01mailrc.txt.gz
Going to read /root/.cpan/sources/authors/01mailrc.txt.gz
CPAN: Compress::Zlib loaded ok
Fetching with LWP:
ftp://archive.progeny.com/CPAN/modules/02packages.details.txt.gz
LWP failed with code[500] message[LWP::Protocol::MyFTP: connect: timeout]
Fetching with Net::FTP:
ftp://archive.progeny.com/CPAN/modules/02packages.details.txt.gz
<text snipped>
/usr/bin/make test -- OK
Running make install
Installing /usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/auto/Term/ReadKey/ReadKey.so
Files found in blib/arch: installing files in blib/lib into architecture dependent library tree
Installing /usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/Term/ReadKey.pm
Installing /usr/share/man/man3/Term::ReadKey.3pm
Writing /usr/lib/perl5/site_perl/5.8.0/i386-linux-thread-multi/auto/Term/ReadKey/.packlist
Appending installation info to /usr/lib/perl5/5.8.0/i386-linux-thread-multi/perllocal.pod
/usr/bin/make install -- OK
cpan> exit
No history written (no histfile specified).
Lockfile removed.
Installing the later version of ReadKey.pm didn't help, though. I
still got the same error message when I tried to install ibmonitor.
# rpm --install ibmonitor-1.4-1.noarch.rpm
warning: ibmonitor-1.4-1.noarch.rpm: V3 DSA signature: NOKEY, key ID 1ac70ce6
error: Failed dependencies:
perl(Term::ReadKey) is needed by ibmonitor-1.4-1
I downloaded the src.rpm file,
ibmonitor-1.4-1.src.rpm
. Installed it with rpm --install ibmonitor-1.4-1.src.rpm, which created two
files: usr/src/redhat/SOURCES/ibmonitor-1.4.tar.gz and
/usr/src/redhat/SPECS/ibmonitor.spec. When I checked the ibmonitor.spec file,
I found the following line in the spec file:
Requires: perl(Term::ReadKey)
The Term::ReadKey module is only needed for ibmonitor fo changing the display on the fly
by hitting certain keys, e.g. "m" to show the maximum bandwidth used while the program has been
running. The program, which is a Perl script, will run without ReadKey support being present on the
system. There is code within the script that checks for the presence of the module, but doesn't
require it to be present. That code is shown below.
# Check for installation of Term-ReadKey module
eval q/use Term::ReadKey;/;
if (!$@) {
$useReadKey = 1;
}
Since the module is actually present on the system and I can change the ibmonitor display by hitting
the keys that trigger options in the program, such as the display of maximum bandwidth, I used
rpm --nodeps --install ibmonitor-1.4-1.noarch.rpm to ignore the dependency check
for Term::ReadKey and proceed with the installation of the ibmonitor
RPM file. The program worked fine after
the installation.
The RPM installation installs the following files:
$ ls -l /usr/share/doc/ibmonitor-1.4/
total 44
-rw-r--r-- 1 root root 33 Oct 13 2006 AUTHORS
-rw-r--r-- 1 root root 4260 Oct 13 2006 ChangeLog
-rw-r--r-- 1 root root 18009 May 3 2003 COPYING
-rw-r--r-- 1 root root 5477 Oct 13 2006 README
-rw-r--r-- 1 root root 67 Oct 13 2006 TODO
$ ls -l /usr/bin/ibmonitor
-rwxr-xr-x 1 root root 31971 Oct 13 2006 /usr/bin/ibmonitor
References:
-
How do I find which modules are installed on my system?
perlfaq3 - perldoc.perl.org
-
Chapter 10. Advanced RPM Packaging
Fedora Documentation on docs.fedoraproject.org
-
Chapter 22. Spec File Syntax
Fedora Documentation on docs.fedoraproject.org
-
[COMMIT LOGREPORT] package/rpm/SPECS lire.spec,1.26,1.27
By: Wytze van der Raay wraay at users.sourceforge.net
Date: August 4, 2006
lists.logreport.org Mailing Lists
-
Spec file tags
Date: July 2, 2005
Wraptastic
[/languages/perl]
permanent link
Wed, Oct 24, 2007 6:25 pm
Power Adapters List
Since I have a lot of devices with various power adapters, I've started
a
list of model numbers for power
adapters and the model numbers for the devices for which they are used.
[/hardware/power]
permanent link
Sun, Oct 21, 2007 11:40 pm
Problems with Windows Update
I was able to connect to a system, G, using Remote Desktop Assistance
on Saturday, October 20, 2007, but then the system stopped responding.
I couldn't even ping it
from the server. When I checked the system on October 21, I found a
BSOD with the following
displayed:
A problem has been detected and Windows has been shut down to prevent damage
to your computer.
If this is the first time yo've seen this Stop error screen,
restart your computer. If this screen appears again, follow
these steps:
Check to besure you have adequate disk space. If a driver is
identified in the Stop message, disable the driver or check
with the manufacturer for driver updates. Try changing video
adapters.
Check with your hardware vendor for any BIOS updates. Disable
BIOS memory options such as caching or shadowing. If you need
to use Safe Mode to remove or disable compoinets, restart your
computer, pres F8 to select Advanced Startup Options, and then
select Safe Mode.
Technical information:
*** STOP: 0x0000008E (0xC0000005,0xBFA14A9B,0xEBF7D7Dc,0x00000000)
*** ialmdev5.DLL - Address FBA14A9B base at BFA02000, DateStamp 40292c7e
Beginning dump of physical memory
Physical memory dump complete.
Contact your system administrator or technical support group for further
assistance.
When I rebooted the system, which is running Windows XP Professional Service
Pack 2, and logged in, I received a notification that
the system had recovered from a serious error. I chose to send the log
to Microsoft and saw a webpage appear stating "Problem caused by Intel
Graphics Driver".
Problem caused by Intel Graphics Driver
This problem was caused by Intel Graphics Driver. Intel Graphics
Driver was created by Dell Inc..
There is no solution for this probem at this time.
However, your computer is missing updates that can help improve its
stability and security.
In Internet Explorer (6.0.2900), I clicked on Tools then selected
Windows Update. I was notified that "To use Microsoft
Update, you must first install the latest version of some Windows
components. This will allow your computer to work with these new
features on the site:". But the installation of Windows Genuine
Advantage Validation Tool (KB892130) failed. I tried several more
times, including after rebooting, but the results were always the same.
I then tried the method outlined at
Easy Way to Bypass Windows Genuine Advantage. I took the following
steps in Internet Explorer.
- Click on Tools.
- Select Internet Options.
- Click on the Programs tab.
- Click on the Manage Add-ons tab.
- Scroll down to you see "Windows Genuine Advantage Validation Tool" in
the Name field.
- Click on Disable to disable that add-on.
- You will see an Add-on Status window appear stating
"You have chosen to disable this add-on. For the change to take effect,
you may need to restart Internet Explorer." Click on OK.
- Click on OK to close the Manage Add-ons window.
- Click on OK to close the Internet Options window.
- Close Internet Explorer.
I then reopened Internet Explorer and clicked on Tools then
Windows Update. Again, I clicked on the Express button
to get high-priority updates. Again the Microsoft website wanted to
install Windows Genuine Advantage Tool (KB892130), but again it
failed.
I then went back to the Manage Add-ons window in Internet Explorer.
I left Windows Geinuine Advantage Tool disabled, but clicked on
the Update ActiveX button. I was prompted as to whether I wanted
to install Windows Genuine Advantae and clicked on the
Install button. I received a message that "The add-on was updated
successfully.
I closed and reopened Internet Explorer. I then clicked on Tools and
selected Windows Update again. I again clicked on the Express
button to get high-priority updates. Again the installation of
Windows Genuine Advantage Validation Tool failed. I re-enabled the
add-on and restarted Internet Explorer.
Looking over the comments to the Digg
posting at
HOW TO: Bypass Windows Genuine Advantage!, I found that
Microsoft patched that Windows Genuine Advantage bypass some time ago.
The system was purchased from Dell and has the pre-installed
version of Microsoft Windows XP on it. It is a valid copy, but because
of Microsoft's Windows Genunine Advantage process, I don't
appear to be able to download
updates through Windows Update in Internet Explorer.
The system
is configurd to download and install automatic updates every
day at 3:00 A.M.. Looking at the "Review your update history" information, I
see Windows Defender updates are occurring regularly with the last one
occurring on Friday, October 19, 2007. The last WIndows XP update occurred
on Thursday, October 11 with the Security Update for Windows XP
(KB933729) listed.
At Microsoft
Windows Update Troubleshooter, under the Manual installation
instructions for Windows Update controls, I found a statement that
"Several problems on the Windows Update site can be caused by outdated or
mismatched site software." I downloaded the iuctl.cab file mentioned
from
http://v4.windowsupdate.microsoft.com/cab/x86/unicode/iuctl.cab. I followed
the instructions for extracting its contents and then right-clicked on
the iuctl "Setup Information" file, i.e. iuctl.inf, and chose Install.
I still had the same problem afterwards, though. Nor did closing Internet
Explorer, reinstalling from the iuctl.inf, and reopening Internet Explorer and
trying again, produce any different results.
Looking in C:\WINDOWS\WindowsUpdate.log, I see the following lines
at the bottom of the file.
WARNING: WU client failed insalling updates with error 0x80240020
>>-- RESUMED -- COMAPI: Install [ClientId = MicrosoftUpdate]
- Install call failed
- Reboot required = No
- WARNING: Exit code = 0x80240FFF; Call error code = 0x80240020
---------
-- END -- COMAPI: Install [ClientID = MicrosoftUpdate]
-------------
WARNING: Operation failed due to earlier error, hr=80240020
At Window's
Update error??, I found a suggestion to check whether
*.microsoft.com and *.windowsupdate.com are in Internet Explorer's Trusted
sites list. They were not, so I put them there by taking the following
steps in Internet Explorer.
- Click on Tools.
- Select Internet Options.
- Click on the Security tab.
- Click on Trusted Sites.
- Click on the Sites button.
- Uncheck "Require server verification (https:) for all sites in this zone.
- Put
*.microsoft.com in the "Add this Web site to
this zone" field and click on Add.
- Put
*.windowsupdate.com in the "Add this Web site to
this zone" field and click on Add.
- Click on OK.
I again tried Windows Update. Again the installation of the
Windows Genuine Advantage Tool failed after I clicked on the
Download and install now button to install it. I still got the
message that "The following updates were not installed: Windows Genuine
Advantage Tool (KB892130)". It still doesn't show up as a failure under
the "Review your update history" link, though. But I can't search for
updates either.
I found the same problem as evidenced by WindowsUpdate.log described
at
Re: Update still failing with 80240020 and 8024000c
I've tried Windows Update by logging into the domain administrator's
account, the local administrator's account for the system, and another account
in the local administrator's group. The results are always the same.
I next tried the suggestion at
Windows Update Installation Error by clicking on Start,
selecting Run, typing Secpol.msc, and hitting
Enter. Then, under Local Policies, I checked that the
Administrators group was included in the Security Setting for the following
policies. It was listed for all of them.
Back up files and directories
Debug programs
Manage auditing and security log
Restore files and directories
Take ownership of files or other objects
So to this point, I've been unable to resolve the problem. Since I need
to resolve a problem with Microsoft Excel on the system, I can't spend any
more time on this issue tonight. I thought perhaps an update to Microsoft
Office that I might find through Windows Update could resolve that problem,
but I'll have to address that problem outside of the Windows Update process.
And I'll have to look for an update to the graphics adapter later as well.
References:
-
Easy Way to Bypass Windows Genuine Advantage
YouAreAdopted.Com
-
HOW TO: Bypass Windows Genuine Advantage!
Digg
-
Windows Update Troubleshooter
Microsoft Corporation
-
Re: Update still failing with 80240020 and 8024000c
By: Robert Aldwinckle (robald_at_techemail.com)
Date: October 17, 2004
Tech-Archive.net: The source
for usenet news
-
Windows Update Installation Error
By Torgeir Bakken (MVP)
Discussion - microsoft.public.windowsupdate | Google Groups
[/os/windows/xp]
permanent link
Thu, Oct 18, 2007 9:06 pm
SSH Connection Closed By Remote Host
After upgrading SSH on a system to version 4.7p1, I found I could no longer
SSH into the system, except if I used ssh 127.0.0.1 from the
system itself.
At first, I thought it was a firewall issue, but I was told that the firewall
was configured to allow outside access to the system via port 22, yet I still
couldn't get in. When I tried to connect to the system via ssh from the
console of the system itself, I couldn't get in if I used the Fully Qualified
Domain Name (FQDN) nor the IP address of the system. I got an
"ssh_exchange_identification" error when I tried.
# ssh server1.example.com
ssh_exchange_identification: Connection closed by remote host
I rebooted the system, but the results were the same.
When I checked to see whether the system was listening on all interfaces
on port 22, I saw the following:
# netstat -a | grep 22
*.22 *.* 0 0 0 0 LISTEN
When I used tail /var/log/authlog, I saw the following:
Oct 18 18:49:44 server1 reboot: rebooted by jsmith
Oct 18 18:51:23 server1 sshd[258]: error: Bind to port 22 on 0.0.0.0 failed: Address already in use.
Oct 18 18:51:23 server1 sshd[258]: fatal: Cannot bind any address.
Oct 18 18:53:21 server1 sshd[2310]: refused connect from 89.sub-75-196-157.myvzw.com
Oct 18 18:54:51 server1 sshd[2415]: refused connect from server1.example.com
Oct 18 18:55:25 server1 sshd[2420]: refused connect from server1.example.com
Oct 18 18:57:13 server1 sshd[2426]: refused connect from frostdragon.com
When I checked to see what application had port 22 open with lsof,
I found sshd listed.
# lsof -i TCP:22
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
sshd 249 root 4u inet 0x30000115068 0t0 TCP *:22 (LISTEN)
I didn't see any setting in /usr/local/etc/sshd_config that I
thought would cause the problem. I then looked in /etc/hosts.allow
and realized I needed to add SSH access there. I added the line below.
sshd : allow ALL
I was then able immediately to SSH into the system. But, when I did so,
I realized that no login banner was appearing. I needed to have a warning
banner clearly stating, before any userid or password prompt appeared, that
access is allowed only for authorized users. So I created a file
/etc/banner with text for that warning message (the file has
744 protection, i.e. world read access). I then modified the "banner" section
of /usr/local/etc/sshd_config to point to the banner text file
/etc/banner.
# no default banner path
#Banner /some/path
Banner /etc/banner
I then restarted sshd.
# /etc/init.d/sshd stop
Stopping sshd
# /etc/init.d/sshd start
Starting sshd
Then when I attempted to ssh into the system, I saw the banner prior to the
password prompt appearing.
[/network/ssh]
permanent link
Tue, Oct 16, 2007 7:51 pm
OpenSSH upgrade to 4.7.1
When I checked the version of the
OpenSSH
software on a Sun SPARC system running Solaris 7 for which I am the
administrator, I found it was outdated.
# ssh -V
OpenSSH_3.7.1p1, SSH protocols 1.5/2.0, OpenSSL 0.9.7b 10 Apr 2003
Note: if you need to check the version of the SSH daemon software on a remote
system, you can ssh to the system using the -v option to obtain
verbose debugging messages, which will reveal the version number on the remote
system in the "remote protocol version" line. Note: the version you see on the
first line is the version of the ssh client you are using, not the version on
the remote SSH server.
# ssh -v jsmith@192.168.0.11
OpenSSH_3.5p1, SSH protocols 1.5/2.0, OpenSSL 0x0090701f
debug1: Reading configuration data /etc/ssh/ssh_config
debug1: Applying options for *
debug1: Rhosts Authentication disabled, originating port will not be trusted.
debug1: ssh_connect: needpriv 0
debug1: Connecting to example.com [192.168.0.11] port 22.
debug1: Connection established.
debug1: identity file /home/jim/.ssh/identity type -1
debug1: identity file /home/jim/.ssh/id_rsa type -1
debug1: identity file /home/jim/.ssh/id_dsa type -1
debug1: Remote protocol version 2.0, remote software version OpenSSH_3.7.1p1
debug1: match: OpenSSH_3.7.1p1 pat OpenSSH*
An updated package, 4.7.1, is available from
Sunfreeware.com.
openssh-4.7p1
Installation of that version also requires the installation of the packages
openssl-0.9.8e (do not use the older openssl packages),
zlib,
libgcc-3.3
or
gcc-3.3.2,
prngd and
optionally, but highly recommended, the
perl,
egd and
tcp_wrappers packages.
When I checked the OpenSSL version on the system, I found it also needed to
be updated.
# /usr/local/ssl/bin/openssl version
OpenSSL 0.9.7b 10 Apr 2003
The information for the OpenSSL 0.9.8e package stated that you
"may also need to install either gcc-3.4.6 or libgcc-3.4.6 to obtain the
libgcc_s.so.1 library.
I found that gcc was also outdated.
# gcc -v
Reading specs from /usr/local/lib/gcc-lib/sparc-sun-solaris2.7/3.0.4/specs
Configured with: ../gcc-3.0.4/configure
Thread model: posix
gcc version 3.0.4
The gcc package requires the installation of libiconv, but that
was already on the system in /usr/local/lib. The gcc package is
fairly large; since I already had an earlier version of gcc on the system,
I decided to proceed with the installation of OpenSSL 0.9.8e instead of waiting
over a 1/2 hour to download the latest version of the gcc package.
# gunzip openssl-0.9.8e-sol7-sparc-local.gz
# pkgadd -d ./openssl-0.9.8e-sol7-sparc-local
The following packages are available:
1 SMCossl openssl
(sparc) 0.9.8e
Select package(s) you wish to process (or 'all' to process
all packages). (default: all) [?,??,q]: 1
Processing package instance <SMCossl> from
</tmp/openssl-0.9.8e-sol7-sparc-local>
openssl
(sparc) 0.9.8e
The OpenSSL Group
Using as the package base directory.
## Processing package information.
## Processing system information.
711 package pathnames are already properly installed.
## Verifying disk space requirements.
## Checking for conflicts with packages already installed.
The following files are already installed on the system and are being
used by another package:
* /usr/local/ssl
* /usr/local/ssl/bin
* /usr/local/ssl/bin/c_rehash
* /usr/local/ssl/bin/openssl
* /usr/local/ssl/certs
* /usr/local/ssl/include
* /usr/local/ssl/include/openssl
* /usr/local/ssl/include/openssl/aes.h
* /usr/local/ssl/include/openssl/asn1.h
* /usr/local/ssl/include/openssl/asn1_mac.h
* /usr/local/ssl/include/openssl/asn1t.h
* /usr/local/ssl/include/openssl/bio.h
* /usr/local/ssl/include/openssl/blowfish.h
* /usr/local/ssl/include/openssl/bn.h
* /usr/local/ssl/include/openssl/buffer.h
* /usr/local/ssl/include/openssl/cast.h
* /usr/local/ssl/include/openssl/comp.h
* /usr/local/ssl/include/openssl/conf.h
* /usr/local/ssl/include/openssl/conf_api.h
[Hit to continue display]
* /usr/local/ssl/include/openssl/crypto.h
* /usr/local/ssl/include/openssl/des.h
* /usr/local/ssl/include/openssl/des_old.h
* /usr/local/ssl/include/openssl/dh.h
* /usr/local/ssl/include/openssl/dsa.h
* /usr/local/ssl/include/openssl/dso.h
* /usr/local/ssl/include/openssl/e_os2.h
* /usr/local/ssl/include/openssl/ebcdic.h
* /usr/local/ssl/include/openssl/ec.h
* /usr/local/ssl/include/openssl/engine.h
* /usr/local/ssl/include/openssl/err.h
* /usr/local/ssl/include/openssl/evp.h
* /usr/local/ssl/include/openssl/hmac.h
* /usr/local/ssl/include/openssl/idea.h
* /usr/local/ssl/include/openssl/krb5_asn.h
* /usr/local/ssl/include/openssl/kssl.h
* /usr/local/ssl/include/openssl/lhash.h
* /usr/local/ssl/include/openssl/md2.h
* /usr/local/ssl/include/openssl/md4.h
* /usr/local/ssl/include/openssl/md5.h
[Hit to continue display]
* /usr/local/ssl/include/openssl/obj_mac.h
* /usr/local/ssl/include/openssl/objects.h
* /usr/local/ssl/include/openssl/ocsp.h
* /usr/local/ssl/include/openssl/opensslconf.h
* /usr/local/ssl/include/openssl/opensslv.h
* /usr/local/ssl/include/openssl/ossl_typ.h
* /usr/local/ssl/include/openssl/pem.h
* /usr/local/ssl/include/openssl/pem2.h
* /usr/local/ssl/include/openssl/pkcs12.h
* /usr/local/ssl/include/openssl/pkcs7.h
* /usr/local/ssl/include/openssl/rand.h
* /usr/local/ssl/include/openssl/rc2.h
* /usr/local/ssl/include/openssl/rc4.h
* /usr/local/ssl/include/openssl/ripemd.h
* /usr/local/ssl/include/openssl/rsa.h
* /usr/local/ssl/include/openssl/safestack.h
* /usr/local/ssl/include/openssl/sha.h
* /usr/local/ssl/include/openssl/ssl.h
* /usr/local/ssl/include/openssl/ssl2.h
* /usr/local/ssl/include/openssl/ssl23.h
[Hit to continue display]
* /usr/local/ssl/include/openssl/ssl3.h
* /usr/local/ssl/include/openssl/stack.h
* /usr/local/ssl/include/openssl/symhacks.h
* /usr/local/ssl/include/openssl/tls1.h
* /usr/local/ssl/include/openssl/tmdiff.h
* /usr/local/ssl/include/openssl/txt_db.h
* /usr/local/ssl/include/openssl/ui.h
* /usr/local/ssl/include/openssl/ui_compat.h
* /usr/local/ssl/include/openssl/x509.h
* /usr/local/ssl/include/openssl/x509_vfy.h
* /usr/local/ssl/include/openssl/x509v3.h
* /usr/local/ssl/lib
* /usr/local/ssl/lib/libcrypto.a
* /usr/local/ssl/lib/libssl.a
* /usr/local/ssl/lib/pkgconfig
* /usr/local/ssl/lib/pkgconfig/openssl.pc
* /usr/local/ssl/man
* /usr/local/ssl/man/man1
* /usr/local/ssl/man/man1/CA.pl.1
* /usr/local/ssl/man/man1/asn1parse.1
[Hit to continue display]
* /usr/local/ssl/man/man1/ca.1
* /usr/local/ssl/man/man1/ciphers.1
* /usr/local/ssl/man/man1/crl.1
* /usr/local/ssl/man/man1/crl2pkcs7.1
* /usr/local/ssl/man/man1/dgst.1
* /usr/local/ssl/man/man1/dhparam.1
* /usr/local/ssl/man/man1/dsa.1
* /usr/local/ssl/man/man1/dsaparam.1
* /usr/local/ssl/man/man1/enc.1
* /usr/local/ssl/man/man1/gendsa.1
* /usr/local/ssl/man/man1/genrsa.1
* /usr/local/ssl/man/man1/nseq.1
* /usr/local/ssl/man/man1/ocsp.1
* /usr/local/ssl/man/man1/openssl.1
* /usr/local/ssl/man/man1/passwd.1
* /usr/local/ssl/man/man1/pkcs12.1
* /usr/local/ssl/man/man1/pkcs7.1
* /usr/local/ssl/man/man1/pkcs8.1
* /usr/local/ssl/man/man1/rand.1
* /usr/local/ssl/man/man1/req.1
[Hit to continue display]
* /usr/local/ssl/man/man1/rsa.1
* /usr/local/ssl/man/man1/rsautl.1
* /usr/local/ssl/man/man1/s_client.1
* /usr/local/ssl/man/man1/s_server.1
* /usr/local/ssl/man/man1/sess_id.1
* /usr/local/ssl/man/man1/smime.1
* /usr/local/ssl/man/man1/speed.1
* /usr/local/ssl/man/man1/spkac.1
* /usr/local/ssl/man/man1/verify.1
* /usr/local/ssl/man/man1/version.1
* /usr/local/ssl/man/man1/x509.1
* /usr/local/ssl/man/man3
* /usr/local/ssl/man/man3/ASN1_OBJECT_new.3
* /usr/local/ssl/man/man3/ASN1_STRING_length.3
* /usr/local/ssl/man/man3/ASN1_STRING_new.3
* /usr/local/ssl/man/man3/ASN1_STRING_print_ex.3
* /usr/local/ssl/man/man3/BIO_ctrl.3
* /usr/local/ssl/man/man3/BIO_f_base64.3
* /usr/local/ssl/man/man3/BIO_f_buffer.3
* /usr/local/ssl/man/man3/BIO_f_cipher.3
[Hit to continue display]
* /usr/local/ssl/man/man3/BIO_f_md.3
* /usr/local/ssl/man/man3/BIO_f_null.3
* /usr/local/ssl/man/man3/BIO_f_ssl.3
* /usr/local/ssl/man/man3/BIO_find_type.3
* /usr/local/ssl/man/man3/BIO_new.3
* /usr/local/ssl/man/man3/BIO_push.3
* /usr/local/ssl/man/man3/BIO_read.3
* /usr/local/ssl/man/man3/BIO_s_accept.3
* /usr/local/ssl/man/man3/BIO_s_bio.3
* /usr/local/ssl/man/man3/BIO_s_connect.3
* /usr/local/ssl/man/man3/BIO_s_fd.3
* /usr/local/ssl/man/man3/BIO_s_file.3
* /usr/local/ssl/man/man3/BIO_s_mem.3
* /usr/local/ssl/man/man3/BIO_s_null.3
* /usr/local/ssl/man/man3/BIO_s_socket.3
* /usr/local/ssl/man/man3/BIO_set_callback.3
* /usr/local/ssl/man/man3/BIO_should_retry.3
* /usr/local/ssl/man/man3/BN_CTX_new.3
* /usr/local/ssl/man/man3/BN_CTX_start.3
* /usr/local/ssl/man/man3/BN_add.3
[Hit to continue display]
* /usr/local/ssl/man/man3/BN_add_word.3
* /usr/local/ssl/man/man3/BN_bn2bin.3
* /usr/local/ssl/man/man3/BN_cmp.3
* /usr/local/ssl/man/man3/BN_copy.3
* /usr/local/ssl/man/man3/BN_generate_prime.3
* /usr/local/ssl/man/man3/BN_mod_inverse.3
* /usr/local/ssl/man/man3/BN_mod_mul_montgomery.3
* /usr/local/ssl/man/man3/BN_mod_mul_reciprocal.3
* /usr/local/ssl/man/man3/BN_new.3
* /usr/local/ssl/man/man3/BN_num_bytes.3
* /usr/local/ssl/man/man3/BN_rand.3
* /usr/local/ssl/man/man3/BN_set_bit.3
* /usr/local/ssl/man/man3/BN_swap.3
* /usr/local/ssl/man/man3/BN_zero.3
* /usr/local/ssl/man/man3/CRYPTO_set_ex_data.3
* /usr/local/ssl/man/man3/DH_generate_key.3
* /usr/local/ssl/man/man3/DH_generate_parameters.3
* /usr/local/ssl/man/man3/DH_get_ex_new_index.3
* /usr/local/ssl/man/man3/DH_new.3
* /usr/local/ssl/man/man3/DH_set_method.3
[Hit to continue display]
* /usr/local/ssl/man/man3/DH_size.3
* /usr/local/ssl/man/man3/DSA_SIG_new.3
* /usr/local/ssl/man/man3/DSA_do_sign.3
* /usr/local/ssl/man/man3/DSA_dup_DH.3
* /usr/local/ssl/man/man3/DSA_generate_key.3
* /usr/local/ssl/man/man3/DSA_generate_parameters.3
* /usr/local/ssl/man/man3/DSA_get_ex_new_index.3
* /usr/local/ssl/man/man3/DSA_new.3
* /usr/local/ssl/man/man3/DSA_set_method.3
* /usr/local/ssl/man/man3/DSA_sign.3
* /usr/local/ssl/man/man3/DSA_size.3
* /usr/local/ssl/man/man3/ERR_GET_LIB.3
* /usr/local/ssl/man/man3/ERR_clear_error.3
* /usr/local/ssl/man/man3/ERR_error_string.3
* /usr/local/ssl/man/man3/ERR_get_error.3
* /usr/local/ssl/man/man3/ERR_load_crypto_strings.3
* /usr/local/ssl/man/man3/ERR_load_strings.3
* /usr/local/ssl/man/man3/ERR_print_errors.3
* /usr/local/ssl/man/man3/ERR_put_error.3
* /usr/local/ssl/man/man3/ERR_remove_state.3
[Hit to continue display]
* /usr/local/ssl/man/man3/EVP_BytesToKey.3
* /usr/local/ssl/man/man3/EVP_DigestInit.3
* /usr/local/ssl/man/man3/EVP_EncryptInit.3
* /usr/local/ssl/man/man3/EVP_OpenInit.3
* /usr/local/ssl/man/man3/EVP_PKEY_new.3
* /usr/local/ssl/man/man3/EVP_PKEY_set1_RSA.3
* /usr/local/ssl/man/man3/EVP_SealInit.3
* /usr/local/ssl/man/man3/EVP_SignInit.3
* /usr/local/ssl/man/man3/EVP_VerifyInit.3
* /usr/local/ssl/man/man3/OBJ_nid2obj.3
* /usr/local/ssl/man/man3/OPENSSL_VERSION_NUMBER.3
* /usr/local/ssl/man/man3/OpenSSL_add_all_algorithms.3
* /usr/local/ssl/man/man3/PKCS12_create.3
* /usr/local/ssl/man/man3/PKCS12_parse.3
* /usr/local/ssl/man/man3/PKCS7_decrypt.3
* /usr/local/ssl/man/man3/PKCS7_encrypt.3
* /usr/local/ssl/man/man3/PKCS7_sign.3
* /usr/local/ssl/man/man3/PKCS7_verify.3
* /usr/local/ssl/man/man3/RAND_add.3
* /usr/local/ssl/man/man3/RAND_bytes.3
[Hit to continue display]
* /usr/local/ssl/man/man3/RAND_cleanup.3
* /usr/local/ssl/man/man3/RAND_egd.3
* /usr/local/ssl/man/man3/RAND_load_file.3
* /usr/local/ssl/man/man3/RAND_set_rand_method.3
* /usr/local/ssl/man/man3/RSA_blinding_on.3
* /usr/local/ssl/man/man3/RSA_check_key.3
* /usr/local/ssl/man/man3/RSA_generate_key.3
* /usr/local/ssl/man/man3/RSA_get_ex_new_index.3
* /usr/local/ssl/man/man3/RSA_new.3
* /usr/local/ssl/man/man3/RSA_padding_add_PKCS1_type_1.3
* /usr/local/ssl/man/man3/RSA_print.3
* /usr/local/ssl/man/man3/RSA_private_encrypt.3
* /usr/local/ssl/man/man3/RSA_public_encrypt.3
* /usr/local/ssl/man/man3/RSA_set_method.3
* /usr/local/ssl/man/man3/RSA_sign.3
* /usr/local/ssl/man/man3/RSA_sign_ASN1_OCTET_STRING.3
* /usr/local/ssl/man/man3/RSA_size.3
* /usr/local/ssl/man/man3/SMIME_read_PKCS7.3
* /usr/local/ssl/man/man3/SMIME_write_PKCS7.3
* /usr/local/ssl/man/man3/SSL_CIPHER_get_name.3
[Hit to continue display]
* /usr/local/ssl/man/man3/SSL_COMP_add_compression_method.3
* /usr/local/ssl/man/man3/SSL_CTX_add_extra_chain_cert.3
* /usr/local/ssl/man/man3/SSL_CTX_add_session.3
* /usr/local/ssl/man/man3/SSL_CTX_ctrl.3
* /usr/local/ssl/man/man3/SSL_CTX_flush_sessions.3
* /usr/local/ssl/man/man3/SSL_CTX_free.3
* /usr/local/ssl/man/man3/SSL_CTX_get_ex_new_index.3
* /usr/local/ssl/man/man3/SSL_CTX_get_verify_mode.3
* /usr/local/ssl/man/man3/SSL_CTX_load_verify_locations.3
* /usr/local/ssl/man/man3/SSL_CTX_new.3
* /usr/local/ssl/man/man3/SSL_CTX_sess_number.3
* /usr/local/ssl/man/man3/SSL_CTX_sess_set_cache_size.3
* /usr/local/ssl/man/man3/SSL_CTX_sess_set_get_cb.3
* /usr/local/ssl/man/man3/SSL_CTX_sessions.3
* /usr/local/ssl/man/man3/SSL_CTX_set_cert_store.3
* /usr/local/ssl/man/man3/SSL_CTX_set_cert_verify_callback.3
* /usr/local/ssl/man/man3/SSL_CTX_set_cipher_list.3
* /usr/local/ssl/man/man3/SSL_CTX_set_client_CA_list.3
* /usr/local/ssl/man/man3/SSL_CTX_set_client_cert_cb.3
* /usr/local/ssl/man/man3/SSL_CTX_set_default_passwd_cb.3
[Hit to continue display]
* /usr/local/ssl/man/man3/SSL_CTX_set_generate_session_id.3
* /usr/local/ssl/man/man3/SSL_CTX_set_info_callback.3
* /usr/local/ssl/man/man3/SSL_CTX_set_max_cert_list.3
* /usr/local/ssl/man/man3/SSL_CTX_set_mode.3
* /usr/local/ssl/man/man3/SSL_CTX_set_msg_callback.3
* /usr/local/ssl/man/man3/SSL_CTX_set_options.3
* /usr/local/ssl/man/man3/SSL_CTX_set_quiet_shutdown.3
* /usr/local/ssl/man/man3/SSL_CTX_set_session_cache_mode.3
* /usr/local/ssl/man/man3/SSL_CTX_set_session_id_context.3
* /usr/local/ssl/man/man3/SSL_CTX_set_ssl_version.3
* /usr/local/ssl/man/man3/SSL_CTX_set_timeout.3
* /usr/local/ssl/man/man3/SSL_CTX_set_tmp_dh_callback.3
* /usr/local/ssl/man/man3/SSL_CTX_set_tmp_rsa_callback.3
* /usr/local/ssl/man/man3/SSL_CTX_set_verify.3
* /usr/local/ssl/man/man3/SSL_CTX_use_certificate.3
* /usr/local/ssl/man/man3/SSL_SESSION_free.3
* /usr/local/ssl/man/man3/SSL_SESSION_get_ex_new_index.3
* /usr/local/ssl/man/man3/SSL_SESSION_get_time.3
* /usr/local/ssl/man/man3/SSL_accept.3
* /usr/local/ssl/man/man3/SSL_alert_type_string.3
[Hit to continue display]
* /usr/local/ssl/man/man3/SSL_clear.3
* /usr/local/ssl/man/man3/SSL_connect.3
* /usr/local/ssl/man/man3/SSL_do_handshake.3
* /usr/local/ssl/man/man3/SSL_free.3
* /usr/local/ssl/man/man3/SSL_get_SSL_CTX.3
* /usr/local/ssl/man/man3/SSL_get_ciphers.3
* /usr/local/ssl/man/man3/SSL_get_client_CA_list.3
* /usr/local/ssl/man/man3/SSL_get_current_cipher.3
* /usr/local/ssl/man/man3/SSL_get_default_timeout.3
* /usr/local/ssl/man/man3/SSL_get_error.3
* /usr/local/ssl/man/man3/SSL_get_ex_data_X509_STORE_CTX_idx.3
* /usr/local/ssl/man/man3/SSL_get_ex_new_index.3
* /usr/local/ssl/man/man3/SSL_get_fd.3
* /usr/local/ssl/man/man3/SSL_get_peer_cert_chain.3
* /usr/local/ssl/man/man3/SSL_get_peer_certificate.3
* /usr/local/ssl/man/man3/SSL_get_rbio.3
* /usr/local/ssl/man/man3/SSL_get_session.3
* /usr/local/ssl/man/man3/SSL_get_verify_result.3
* /usr/local/ssl/man/man3/SSL_get_version.3
* /usr/local/ssl/man/man3/SSL_library_init.3
[Hit to continue display]
* /usr/local/ssl/man/man3/SSL_load_client_CA_file.3
* /usr/local/ssl/man/man3/SSL_new.3
* /usr/local/ssl/man/man3/SSL_pending.3
* /usr/local/ssl/man/man3/SSL_read.3
* /usr/local/ssl/man/man3/SSL_rstate_string.3
* /usr/local/ssl/man/man3/SSL_session_reused.3
* /usr/local/ssl/man/man3/SSL_set_bio.3
* /usr/local/ssl/man/man3/SSL_set_connect_state.3
* /usr/local/ssl/man/man3/SSL_set_fd.3
* /usr/local/ssl/man/man3/SSL_set_session.3
* /usr/local/ssl/man/man3/SSL_set_shutdown.3
* /usr/local/ssl/man/man3/SSL_set_verify_result.3
* /usr/local/ssl/man/man3/SSL_shutdown.3
* /usr/local/ssl/man/man3/SSL_state_string.3
* /usr/local/ssl/man/man3/SSL_want.3
* /usr/local/ssl/man/man3/SSL_write.3
* /usr/local/ssl/man/man3/X509_NAME_ENTRY_get_object.3
* /usr/local/ssl/man/man3/X509_NAME_add_entry_by_txt.3
* /usr/local/ssl/man/man3/X509_NAME_get_index_by_NID.3
* /usr/local/ssl/man/man3/X509_NAME_print_ex.3
[Hit to continue display]
* /usr/local/ssl/man/man3/X509_new.3
* /usr/local/ssl/man/man3/bio.3
* /usr/local/ssl/man/man3/blowfish.3
* /usr/local/ssl/man/man3/bn.3
* /usr/local/ssl/man/man3/bn_internal.3
* /usr/local/ssl/man/man3/buffer.3
* /usr/local/ssl/man/man3/crypto.3
* /usr/local/ssl/man/man3/d2i_ASN1_OBJECT.3
* /usr/local/ssl/man/man3/d2i_DHparams.3
* /usr/local/ssl/man/man3/d2i_DSAPublicKey.3
* /usr/local/ssl/man/man3/d2i_PKCS8PrivateKey.3
* /usr/local/ssl/man/man3/d2i_RSAPublicKey.3
* /usr/local/ssl/man/man3/d2i_SSL_SESSION.3
* /usr/local/ssl/man/man3/d2i_X509.3
* /usr/local/ssl/man/man3/d2i_X509_ALGOR.3
* /usr/local/ssl/man/man3/d2i_X509_CRL.3
* /usr/local/ssl/man/man3/d2i_X509_NAME.3
* /usr/local/ssl/man/man3/d2i_X509_REQ.3
* /usr/local/ssl/man/man3/d2i_X509_SIG.3
* /usr/local/ssl/man/man3/des.3
[Hit to continue display]
* /usr/local/ssl/man/man3/dh.3
* /usr/local/ssl/man/man3/dsa.3
* /usr/local/ssl/man/man3/engine.3
* /usr/local/ssl/man/man3/err.3
* /usr/local/ssl/man/man3/evp.3
* /usr/local/ssl/man/man3/hmac.3
* /usr/local/ssl/man/man3/lh_stats.3
* /usr/local/ssl/man/man3/lhash.3
* /usr/local/ssl/man/man3/md5.3
* /usr/local/ssl/man/man3/mdc2.3
* /usr/local/ssl/man/man3/pem.3
* /usr/local/ssl/man/man3/rand.3
* /usr/local/ssl/man/man3/rc4.3
* /usr/local/ssl/man/man3/ripemd.3
* /usr/local/ssl/man/man3/rsa.3
* /usr/local/ssl/man/man3/sha.3
* /usr/local/ssl/man/man3/ssl.3
* /usr/local/ssl/man/man3/threads.3
* /usr/local/ssl/man/man3/ui.3
* /usr/local/ssl/man/man3/ui_compat.3
[Hit to continue display]
* /usr/local/ssl/man/man5
* /usr/local/ssl/man/man5/config.5
* /usr/local/ssl/man/man7
* /usr/local/ssl/man/man7/des_modes.7
* /usr/local/ssl/misc
* /usr/local/ssl/misc/CA.pl
* /usr/local/ssl/misc/CA.sh
* /usr/local/ssl/misc/c_hash
* /usr/local/ssl/misc/c_info
* /usr/local/ssl/misc/c_issuer
* /usr/local/ssl/misc/c_name
* /usr/local/ssl/openssl.cnf
* /usr/local/ssl/private
* - conflict with a file which does not belong to any package.
Do you want to install these conflicting files [y,n,?,q] y
...
/usr/local/ssl/misc/c_hash
/usr/local/ssl/misc/c_info
/usr/local/ssl/misc/c_issuer
/usr/local/ssl/misc/c_name
/usr/local/ssl/openssl.cnf
[ verifying class ]
Installation of <SMCossl> was successful.
#
I chose to replace the outdated versions of files when prompted as to
whether I wanted to "install these conflicting files". I checked the
version of OpenSSL afterwards and saw the new version listed.
# /usr/local/ssl/bin/openssl version
OpenSSL 0.9.8e 23 Feb 2007
I then installed OpenSSH 4.7.1
# gunzip openssh-4.7p1-sol7-sparc-local.gz
# pkgadd -d openssh-4.7p1-sol7-sparc-local
The following packages are available:
1 SMCosh471 openssh
(sparc) 4.7p1
Select package(s) you wish to process (or 'all' to process
all packages). (default: all) [?,??,q]: 1
Processing package instance <SMCosh471> from </tmp/openssh-4.7p1-sol7-sparc-local>
openssh
(sparc) 4.7p1
The OpenSSH Group
Using as the package base directory.
## Processing package information.
## Processing system information.
9 package pathnames are already properly installed.
## Verifying disk space requirements.
## Checking for conflicts with packages already installed.
The following files are already installed on the system and are being
used by another package:
* /usr/local/bin/scp
* /usr/local/bin/sftp
* /usr/local/bin/ssh
* /usr/local/bin/ssh-add
* /usr/local/bin/ssh-agent
* /usr/local/bin/ssh-keygen
* /usr/local/bin/ssh-keyscan
* /usr/local/etc/moduli
* /usr/local/etc/ssh_config
* /usr/local/etc/sshd_config
* /usr/local/libexec
* /usr/local/libexec/sftp-server
* /usr/local/libexec/ssh-keysign
* /usr/local/libexec/ssh-rand-helper
* /usr/local/man/man1/scp.1
* /usr/local/man/man1/sftp.1
* /usr/local/man/man1/ssh-add.1
* /usr/local/man/man1/ssh-agent.1
* /usr/local/man/man1/ssh-keygen.1
[Hit to continue display]
* /usr/local/man/man1/ssh-keyscan.1
* /usr/local/man/man1/ssh.1
* /usr/local/man/man5/ssh_config.5
* /usr/local/man/man5/sshd_config.5
* /usr/local/man/man8
* /usr/local/man/man8/sftp-server.8
* /usr/local/man/man8/ssh-keysign.8
* /usr/local/man/man8/ssh-rand-helper.8
* /usr/local/man/man8/sshd.8
* /usr/local/sbin
* /usr/local/sbin/sshd
* /usr/local/share/Ssh.bin
* - conflict with a file which does not belong to any package.
Do you want to install these conflicting files [y,n,?,q] y
## Checking for setuid/setgid programs.
Installing openssh as
## Installing part 1 of 1.
/usr/local/bin/scp
/usr/local/bin/sftp
/usr/local/bin/ssh
/usr/local/bin/ssh-add
/usr/local/bin/ssh-agent
/usr/local/bin/ssh-keygen
/usr/local/bin/ssh-keyscan
/usr/local/doc/openssh/CREDITS
/usr/local/doc/openssh/ChangeLog
/usr/local/doc/openssh/INSTALL
/usr/local/doc/openssh/LICENCE
/usr/local/doc/openssh/OVERVIEW
/usr/local/doc/openssh/README
/usr/local/doc/openssh/README.dns
/usr/local/doc/openssh/README.platform
/usr/local/doc/openssh/README.privsep
/usr/local/doc/openssh/README.smartcard
/usr/local/doc/openssh/README.tun
/usr/local/doc/openssh/TODO
/usr/local/doc/openssh/WARNING.RNG
/usr/local/doc/openssh/contrib/Makefile
/usr/local/doc/openssh/contrib/README
/usr/local/doc/openssh/contrib/aix/README
/usr/local/doc/openssh/contrib/aix/buildbff.sh
/usr/local/doc/openssh/contrib/aix/inventory.sh
/usr/local/doc/openssh/contrib/aix/pam.conf
/usr/local/doc/openssh/contrib/caldera/openssh.spec
/usr/local/doc/openssh/contrib/caldera/ssh-host-keygen
/usr/local/doc/openssh/contrib/caldera/sshd.init
/usr/local/doc/openssh/contrib/caldera/sshd.pam
/usr/local/doc/openssh/contrib/cygwin/Makefile
/usr/local/doc/openssh/contrib/cygwin/README
/usr/local/doc/openssh/contrib/cygwin/ssh-host-config
/usr/local/doc/openssh/contrib/cygwin/ssh-user-config
/usr/local/doc/openssh/contrib/findssl.sh
/usr/local/doc/openssh/contrib/gnome-ssh-askpass1.c
/usr/local/doc/openssh/contrib/gnome-ssh-askpass2.c
/usr/local/doc/openssh/contrib/hpux/README
/usr/local/doc/openssh/contrib/hpux/egd
/usr/local/doc/openssh/contrib/hpux/egd.rc
/usr/local/doc/openssh/contrib/hpux/sshd
/usr/local/doc/openssh/contrib/hpux/sshd.rc
/usr/local/doc/openssh/contrib/redhat/gnome-ssh-askpass.csh
/usr/local/doc/openssh/contrib/redhat/gnome-ssh-askpass.sh
/usr/local/doc/openssh/contrib/redhat/openssh.spec
/usr/local/doc/openssh/contrib/redhat/sshd.init
/usr/local/doc/openssh/contrib/redhat/sshd.init.old
/usr/local/doc/openssh/contrib/redhat/sshd.pam
/usr/local/doc/openssh/contrib/redhat/sshd.pam.old
/usr/local/doc/openssh/contrib/solaris/README
/usr/local/doc/openssh/contrib/ssh-copy-id
/usr/local/doc/openssh/contrib/ssh-copy-id.1
/usr/local/doc/openssh/contrib/sshd.pam.freebsd
/usr/local/doc/openssh/contrib/sshd.pam.generic
/usr/local/doc/openssh/contrib/suse/openssh.spec
/usr/local/doc/openssh/contrib/suse/rc.config.sshd
/usr/local/doc/openssh/contrib/suse/rc.sshd
/usr/local/doc/openssh/contrib/suse/sysconfig.ssh
/usr/local/etc/moduli
/usr/local/etc/ssh_config
/usr/local/etc/sshd_config
/usr/local/libexec/sftp-server
/usr/local/libexec/ssh-keysign
/usr/local/libexec/ssh-rand-helper
/usr/local/man/man1/scp.1
/usr/local/man/man1/sftp.1
/usr/local/man/man1/ssh-add.1
/usr/local/man/man1/ssh-agent.1
/usr/local/man/man1/ssh-keygen.1
/usr/local/man/man1/ssh-keyscan.1
/usr/local/man/man1/ssh.1
/usr/local/man/man5/ssh_config.5
/usr/local/man/man5/sshd_config.5
/usr/local/man/man8/sftp-server.8
/usr/local/man/man8/ssh-keysign.8
/usr/local/man/man8/ssh-rand-helper.8
/usr/local/man/man8/sshd.8
/usr/local/sbin/sshd
/usr/local/share/Ssh.bin
[ verifying class ]
Installation of <SMCosh471> was successful.
When I tried to run ssh afterwards, though, I got an error message.
# ssh -v
ld.so.1: ssh: fatal: libz.so: open failed: No such file or directory
Killed
According to information I found at
Re: OpenSSH 3.7.1p1, that occurs when OpenSSH has been compiled
with a shared libz and the ssh binary can't find libz on the target system.
The suggested solution was to put libz on the target system or rebuild
the source code with a static library. At
Minimizing the Solaris Operating Environment for Security: Updated for
Solaris 9 Operating Environment, I found libz.so.1 associated with
the SUNWzlib package, which has a description of "The Zip compression
library".
At
Very nice OpenSSH 4.3p2 packages for 8,9,10, I found a reference
to someone building packages for Solaris 8, 9, and 10 which are built against
the static version of zlib (1.2.3), so SUNWzlib is no longer required. Those
packages are available from
http://firewallworks.com/downloads/unsupported/Solaris-sparc/
I decided to download
zlib-1.2.3
from the Sunfreeware site instead.
The package contains zlib compression libraries - installs in /usr/local. This
package has both libz.a and libz.so libraries. The package requires that
libgcc_s.so.1 be in /usr/local/lib. This can be done by installing
libgcc-3.3
or gcc
or higher. This package contains the patch for the
security vulnerability described, for example, in
USN-148-1 zlib vulnerability.
I installed that package.
# pkgadd -d ./zlib-1.2.3-sol7-sparc-local
The following packages are available:
1 SMCzlib zlib
(sparc) 1.2.3
Select package(s) you wish to process (or 'all' to process
all packages). (default: all) [?,??,q]: 1
Processing package instance <SMCzlib> from </tmp/zlib-1.2.3-sol7-sparc-local>
zlib
(sparc) 1.2.3
Jean-loup Gailly
Using as the package base directory.
## Processing package information.
## Processing system information.
6 package pathnames are already properly installed.
## Verifying disk space requirements.
## Checking for conflicts with packages already installed.
The following files are already installed on the system and are being
used by another package:
* /usr/local/include/zconf.h
* /usr/local/include/zlib.h
* /usr/local/lib/libz.a
* - conflict with a file which does not belong to any package.
Do you want to install these conflicting files [y,n,?,q] y
## Checking for setuid/setgid programs.
Installing zlib as
## Installing part 1 of 1.
/usr/local/bin/minigzip
/usr/local/doc/zlib/ChangeLog
/usr/local/doc/zlib/FAQ
/usr/local/doc/zlib/INDEX
/usr/local/doc/zlib/README
/usr/local/doc/zlib/algorithm.txt
/usr/local/doc/zlib/contrib/README.contrib
/usr/local/doc/zlib/contrib/ada/buffer_demo.adb
/usr/local/doc/zlib/contrib/ada/mtest.adb
/usr/local/doc/zlib/contrib/ada/read.adb
/usr/local/doc/zlib/contrib/ada/readme.txt
/usr/local/doc/zlib/contrib/ada/test.adb
/usr/local/doc/zlib/contrib/ada/zlib-streams.adb
/usr/local/doc/zlib/contrib/ada/zlib-streams.ads
/usr/local/doc/zlib/contrib/ada/zlib-thin.adb
/usr/local/doc/zlib/contrib/ada/zlib-thin.ads
/usr/local/doc/zlib/contrib/ada/zlib.adb
/usr/local/doc/zlib/contrib/ada/zlib.ads
/usr/local/doc/zlib/contrib/ada/zlib.gpr
/usr/local/doc/zlib/contrib/asm586/README.586
/usr/local/doc/zlib/contrib/asm586/match.S
/usr/local/doc/zlib/contrib/asm686/README.686
/usr/local/doc/zlib/contrib/asm686/match.S
/usr/local/doc/zlib/contrib/blast/Makefile
/usr/local/doc/zlib/contrib/blast/README
/usr/local/doc/zlib/contrib/blast/blast.c
/usr/local/doc/zlib/contrib/blast/blast.h
/usr/local/doc/zlib/contrib/blast/test.pk
/usr/local/doc/zlib/contrib/blast/test.txt
/usr/local/doc/zlib/contrib/delphi/ZLib.pas
/usr/local/doc/zlib/contrib/delphi/ZLibConst.pas
/usr/local/doc/zlib/contrib/delphi/readme.txt
/usr/local/doc/zlib/contrib/delphi/zlibd32.mak
/usr/local/doc/zlib/contrib/dotzlib/DotZLib.build
/usr/local/doc/zlib/contrib/dotzlib/DotZLib.chm
/usr/local/doc/zlib/contrib/dotzlib/DotZLib.sln
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/AssemblyInfo.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/ChecksumImpl.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/CircularBuffer.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/CodecBase.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/Deflater.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/DotZLib.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/DotZLib.csproj
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/GZipStream.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/Inflater.cs
/usr/local/doc/zlib/contrib/dotzlib/DotZLib/UnitTests.cs
/usr/local/doc/zlib/contrib/dotzlib/LICENSE_1_0.txt
/usr/local/doc/zlib/contrib/dotzlib/readme.txt
/usr/local/doc/zlib/contrib/infback9/README
/usr/local/doc/zlib/contrib/infback9/infback9.c
/usr/local/doc/zlib/contrib/infback9/infback9.h
/usr/local/doc/zlib/contrib/infback9/inffix9.h
/usr/local/doc/zlib/contrib/infback9/inflate9.h
/usr/local/doc/zlib/contrib/infback9/inftree9.c
/usr/local/doc/zlib/contrib/infback9/inftree9.h
/usr/local/doc/zlib/contrib/inflate86/inffas86.c
/usr/local/doc/zlib/contrib/inflate86/inffast.S
/usr/local/doc/zlib/contrib/iostream/test.cpp
/usr/local/doc/zlib/contrib/iostream/zfstream.cpp
/usr/local/doc/zlib/contrib/iostream/zfstream.h
/usr/local/doc/zlib/contrib/iostream2/zstream.h
/usr/local/doc/zlib/contrib/iostream2/zstream_test.cpp
/usr/local/doc/zlib/contrib/iostream3/README
/usr/local/doc/zlib/contrib/iostream3/TODO
/usr/local/doc/zlib/contrib/iostream3/test.cc
/usr/local/doc/zlib/contrib/iostream3/zfstream.cc
/usr/local/doc/zlib/contrib/iostream3/zfstream.h
/usr/local/doc/zlib/contrib/masm686/match.asm
/usr/local/doc/zlib/contrib/masmx64/bld_ml64.bat
/usr/local/doc/zlib/contrib/masmx64/gvmat64.asm
/usr/local/doc/zlib/contrib/masmx64/gvmat64.obj
/usr/local/doc/zlib/contrib/masmx64/inffas8664.c
/usr/local/doc/zlib/contrib/masmx64/inffasx64.asm
/usr/local/doc/zlib/contrib/masmx64/inffasx64.obj
/usr/local/doc/zlib/contrib/masmx64/readme.txt
/usr/local/doc/zlib/contrib/masmx86/bld_ml32.bat
/usr/local/doc/zlib/contrib/masmx86/gvmat32.asm
/usr/local/doc/zlib/contrib/masmx86/gvmat32.obj
/usr/local/doc/zlib/contrib/masmx86/gvmat32c.c
/usr/local/doc/zlib/contrib/masmx86/inffas32.asm
/usr/local/doc/zlib/contrib/masmx86/inffas32.obj
/usr/local/doc/zlib/contrib/masmx86/mkasm.bat
/usr/local/doc/zlib/contrib/masmx86/readme.txt
/usr/local/doc/zlib/contrib/minizip/ChangeLogUnzip
/usr/local/doc/zlib/contrib/minizip/Makefile
/usr/local/doc/zlib/contrib/minizip/crypt.h
/usr/local/doc/zlib/contrib/minizip/ioapi.c
/usr/local/doc/zlib/contrib/minizip/ioapi.h
/usr/local/doc/zlib/contrib/minizip/iowin32.c
/usr/local/doc/zlib/contrib/minizip/iowin32.h
/usr/local/doc/zlib/contrib/minizip/miniunz.c
/usr/local/doc/zlib/contrib/minizip/minizip.c
/usr/local/doc/zlib/contrib/minizip/mztools.c
/usr/local/doc/zlib/contrib/minizip/mztools.h
/usr/local/doc/zlib/contrib/minizip/unzip.c
/usr/local/doc/zlib/contrib/minizip/unzip.h
/usr/local/doc/zlib/contrib/minizip/zip.c
/usr/local/doc/zlib/contrib/minizip/zip.h
/usr/local/doc/zlib/contrib/pascal/example.pas
/usr/local/doc/zlib/contrib/pascal/readme.txt
/usr/local/doc/zlib/contrib/pascal/zlibd32.mak
/usr/local/doc/zlib/contrib/pascal/zlibpas.pas
/usr/local/doc/zlib/contrib/puff/Makefile
/usr/local/doc/zlib/contrib/puff/README
/usr/local/doc/zlib/contrib/puff/puff.c
/usr/local/doc/zlib/contrib/puff/puff.h
/usr/local/doc/zlib/contrib/puff/zeros.raw
/usr/local/doc/zlib/contrib/testzlib/testzlib.c
/usr/local/doc/zlib/contrib/testzlib/testzlib.txt
/usr/local/doc/zlib/contrib/untgz/Makefile
/usr/local/doc/zlib/contrib/untgz/Makefile.msc
/usr/local/doc/zlib/contrib/untgz/untgz.c
/usr/local/doc/zlib/contrib/vstudio/readme.txt
/usr/local/doc/zlib/contrib/vstudio/vc7/miniunz.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc7/minizip.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc7/testzlib.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc7/zlib.rc
/usr/local/doc/zlib/contrib/vstudio/vc7/zlibstat.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc7/zlibvc.def
/usr/local/doc/zlib/contrib/vstudio/vc7/zlibvc.sln
/usr/local/doc/zlib/contrib/vstudio/vc7/zlibvc.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/miniunz.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/minizip.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/testzlib.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/testzlibdll.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/zlib.rc
/usr/local/doc/zlib/contrib/vstudio/vc8/zlibstat.vcproj
/usr/local/doc/zlib/contrib/vstudio/vc8/zlibvc.def
/usr/local/doc/zlib/contrib/vstudio/vc8/zlibvc.sln
/usr/local/doc/zlib/contrib/vstudio/vc8/zlibvc.vcproj
/usr/local/doc/zlib/example.c
/usr/local/include/zconf.h
/usr/local/include/zlib.h
/usr/local/lib/libz.a
/usr/local/lib/libz.so
/usr/local/lib/libz.so.1
/usr/local/lib/libz.so.1.2.3
/usr/local/man/man3/zlib.3
[ verifying class ]
Installation of <SMCzlib> was successful.
I was then able to run ssh and could see that the new version was in use.
# ssh -v
OpenSSH_4.7p1, OpenSSL 0.9.8e 23 Feb 2007
Zlib was listed as a requirement for OpenSSH 4.7.1; I thought it was already
present and hadn't bothered to check before installing that version of OpenSSH.
I then tried to restart the sshd daemon. I created a file
/tmp.ssh_restart, which I made executable with chmod 700
ssh_restart, with the following commands:
/etc/init.d/sshd stop
sleep 10
/etc/init.d/sshd start
I then set it to run in the background, hoping I wouldn't lose SSH
access to the system, since I was trying to restart the SSH daemon from a
remote location.
# /tmp/ssh_restart &
16314
# Stopping sshd
Starting sshd
Privilege separation user sshd does not exist
It did not restart. Though I remained connected, I could not establish
new ssh connections.
# ssh -v 127.0.0.1
OpenSSH_4.7p1, OpenSSL 0.9.8e 23 Feb 2007
debug1: Reading configuration data /usr/local/etc/ssh_config
debug1: Connecting to 127.0.0.1 [127.0.0.1] port 22.
debug1: connect to address 127.0.0.1 port 22: Connection refused
ssh: connect to host 127.0.0.1 port 22: Connection refused
I resolved the "privilege separation" problem by creating an sshd
group and account on the system.
# groupadd -g 74 sshd
UX: groupadd: WARNING: gid 74 is reserved.
# useradd -u 74 -g 74 -c "Privilege-separated SSH" -d /var/empty/sshd -s /bin/false sshd
UX: useradd: WARNING: uid 74 is reserved.
I then reran the /tmp/ssh_restart script.
# /tmp/ssh &
22647
#
# Starting sshd
When I then tried connecting to the system via SSH, I could see that
the new 4.7.1 version was running.
# ssh -v 127.0.0.1
OpenSSH_4.7p1, OpenSSL 0.9.8e 23 Feb 2007
debug1: Reading configuration data /usr/local/etc/ssh_config
debug1: Connecting to 127.0.0.1 [127.0.0.1] port 22.
debug1: Connection established.
debug1: permanently_set_uid: 0/1
debug1: identity file /.ssh/identity type -1
debug1: identity file /.ssh/id_rsa type -1
debug1: identity file /.ssh/id_dsa type -1
debug1: Remote protocol version 1.99, remote software version OpenSSH_4.7
References:
-
Re: OpenSSH 3.7.1p1
By: Scott Burch
Date: September 26, 2003
MARC: Mailing list ARChives
-
Minimizing the Solaris Operating Environment for Security: Updated for Solaris
9 Operating Environment
By: Sun Microsystems
Date: February 7, 2003
informIT
-
Installation - Very nice OpenSSH 4.3p2 packages for 8,9,10
By DTF
Date: November 11, 2004
Sun Developer Network (SDN)
Forums
-
Privilege separation user sshd does not exist
By: perh
Date: March 16, 2004
UNIXguide.net
-
FC4-Starting sshd: Privilege separation user sshd does not exist FAILED
By:
kiranherekar
Date: December 23, 2005
LinuxQuestions.org
[/os/unix/solaris/network]
permanent link
Sun, Oct 07, 2007 4:52 pm
Copying a MUSH
A family member wanted to create a new
TinyMUSH using an existing one
as a starting point. She felt it would be easier to modify the existing one
than to start a new one from scratch. I took the steps detailed below to
copy the existing MoonDreaming MUSH to a new one that she wanted to set up
for SailorMoon roleplaying.
I shut down the original MUSH
using the @shutdown command
while logged into the MUSH as god. I then ran ./Backup from
the command line.
$ ./Backup
Creating flatfile ./backups/moondreaming.1007-1558
Loaded module: comsys
Loaded module: mail
Using gdbm file: ./data/moondreaming.gdbm
Reading ........
Input: TinyMUSH-3 version 1: Zone Link GDBM AtrName AtrKey Parent AtrMoney ExtFlags MoreFlags Powers QuotedStr TypedQuotas Timestamps VisualAttrs
Output: TinyMUSH-3 version 1: Zone Link Parent ExtFlags MoreFlags Powers QuotedStr TypedQuotas Timestamps VisualAttrs
Writing ........
Cleaned 1600 attributes (now 1376): 222 deleted, 186 renumbered (96 objects and 463 individual attrs touched).
Creating database archive ./backups/moondreaming.1007-1558.tar.gz
./backups/moondreaming.1007-1558
./data/mod_comsys.db
./data/mod_mail.db
I changed the working directory to the one containing the existing
MUSH directory and then copied that directory and its subdirectories
recursively.
$ cp -p -r moondreaming sailormoon
I then made the current working directory the one for the new MUSH.
$ cd sailormoon
I then edited mush.config in that directory. I changed the
GAMENAME line to match the name of the new MUSH. I left the
OWNER line the same, since the owner was the same person in this case.
GAMENAME=sailormoon
I then renamed the old conf file to match the new MUSH name and deleted
the log and pid files from the other MUSH. The pid file contains the process
id for the other MUSH process. A new one will be assigned the first time
the new MUSH is run. If the pid file is not deleted, when you run
Startmush it will state that the MUSH is already running.
$ mv moondreaming.conf sailormoon.conf
$ rm moondreaming.log*
$ rm moondreaming.pid
I also deleted the db directories that came from the other MUSH's directory.
$ rm -f -r db-*
I edited the new sailormoon.conf file I renamed to set the port for the new
MUSH and its new name, changing the lines below within it.
crash_database moondreaming.db.CRASH
gdbm_database moondreaming.gdbm
port 7676
mud_name MoonDreamingMUSH
The new MUSH must listen on a different port than the existing MUSH and
one that is not in use by any other application. You can use
netstat -a | grep 9999 substituting the port number you've
picked instead of 9999 to see whether an application is
listening on that port. If no other process is listening on that port, at
least at the time you run the command, you see the command prompt returned, but
nothing else. Only the root account can use a port less than 1024; ports below
that number are considered to be "reserved".
I changed the working directory to the data directory and renamed the
old gdbm file to use the name associated with the new MUSH. I deleted
the FLAT and KILLED files associated with the other MUSH.
$ cd data
$ ls
mod_comsys.db mod_mail.db moondreaming.FLAT moondreaming.KILLED
mod_comsys.db.old mod_mail.db.old moondreaming.gdbm
$ mv moondreaming.gdbm sailormoon.gdbm
$ rm moondreaming.FLAT
$ rm moondreaming.KILLED
I then moved up to the main diectory for the MUSH and removed all of the
backup files from the other MUSH, which are in the backups directory.
$ cd ..
$ ls
moondreaming.0310-2131.tar.gz moondreaming.0316-1729.tar.gz
moondreaming.0315-1900.tar.gz moondreaming.1007-1416.tar.gz
$ rm backups/*
I then ran ./Startmush
$ ./Startmush
./Startmush: line 83: [: : integer expression expected
Indexing help.txt
1004 topics indexed
Indexing mushman.txt
395 topics indexed
Indexing news.txt
...
62 topics indexed
Indexing plushelp.txt
line 4: line too long
line 9: line too long
line 142: line too long
line 229: line too long
line 254: line too long
line 282: line too long
line 655: line too long
line 680: line too long
line 880: line too long
42 topics indexed
Indexing qhelp.txt
18 topics indexed
Indexing wizhelp.txt
379 topics indexed
Indexing wiznews.txt
1 topics indexed
Checking for database files and creating backups of old files.
tail: sailormoon.log: No such file or directory
Saving old comsys module db.
Saving old mail module db.
ls: sailormoon.log.*: No such file or directory
No previous game log.
Log cleanup done.
Process 19086
071007.164045 TinyMUSH INI/START: Starting: TinyMUSH version 3.1 patchlevel 4 #1 [10/11/2006]
071007.164045 TinyMUSH INI/START: Build date: Sat Mar 10 21:25:06 EST 2007
071007.164045 TinyMUSH INI/START: Build info: ./configure
gcc -g -I./gdbm-1.8.0
071007.164045 TinyMUSH CNF/MOD : Loaded module: comsys
071007.164045 TinyMUSH CNF/MOD : Loaded module: mail
071007.164045 SailorMoonMUSH INI/LOAD : Using gdbm file: sailormoon.gdbm
071007.164045 SailorMoonMUSH INI/LOAD : Loading object structures.
071007.164045 SailorMoonMUSH INI/LOAD : Loading db: data/mod_mail.db
071007.164045 SailorMoonMUSH INI/LOAD : Loading db: data/mod_comsys.db
071007.164045 SailorMoonMUSH INI/LOAD : Load complete.
071007.164045 SailorMoonMUSH CFG/UPDAT: God(#1) entered config directive: money_name_singular with args 'Moon Coin'. Status: Success.
071007.164045 SailorMoonMUSH CFG/UPDAT: God(#1) entered config directive: money_name_plural with args 'Moon Coins'. Status: Success.
071007.164045 SailorMoonMUSH INI/LOAD : Startup processing complete.
071007.164045 SailorMoonMUSH NET/SLAVE: DNS lookup slave started on fd 1
071007.164045 SailorMoonMUSH INI/LOAD : Cleanup completed.
Don't worry about the "integer expression expected", the first time
the Startmush is run for the MUSH; it won't appear the
next time you use Startmush.
After the MUSH loaded, I logged in as god and changed the password.
@password oldpassword=newpassword
Password changed.
[/gaming/tinymush]
permanent link
Sun, Sep 30, 2007 8:41 pm
Using a Disk Drive from a Dimension 2350 in a 4600
I had to move a disk drive from a Dell Dimension 2350 to a Dell Dimension 4600,
because of a problem with the processor on the 2350 motherboard overheating.
Unfortunately, Windows XP doesn't react well to a change of motherboard
and the process or repairing Windows XP, so that the system was usable again,
took me many hours.
[ More Info ]
[/os/windows/xp]
permanent link
Mon, Sep 24, 2007 10:40 pm
Ghost 2003 Internal Error 36000
After running
chkdsk /f on all drives in the system,
I started an image backup of a Windows Small Business Server (SBS) 2003 system
from a Norton Ghost 2003 boot CD. I was attempting to backup an internal
IDE drive to a double-layer DVD in the system's internal DVD writer.
When I attempted to backup drive C (the second partition to a double-layer DVD,
I got a "File Name ? (546)" error message. The backup aborted shortly after
it started with the current file being backed up listed as "0 $MFT".
When I hit enter for "OK", I then received the following error message:
Internal Error 36000
An internal inconsistency has been detected
If this problem persists, contact Symantec Technical Support
at http://service.symantec.com
[ OK ]
When I hit enter, I saw the following:
ABORT: 12020, Write to CD/DVD disc failed
ABORT: 36000, A generalException occurred
I rebooted and hit F8 prior to the system booting from the Ghost boot
disc to choose what entries in config.sys and autoexec.bat should be
processed. I chose not to execute "Ghost.exe" from autoexec.bat. When
I got a command prompt, I entered
ghost -fni instead, as suggested
by
How to troubleshoot the error: "Internal error 36000 . . . ".
I then proceeded with the backup of the second partition, excactly as before.
This time the backup completed succcessfully.
[/os/windows/utilities/backup/ghost]
permanent link
Sat, Sep 22, 2007 11:59 am
Visual Basic Script to Check CPU Utilization
A user of a Windows 2000 Professional system was complaining that his system
has been running very slow. He has stated that when he is typing in a Word
document or an email message that the time between when he types characters
and when they appear on his screen can be quite lengthy. I've seen problems
on his system before with high CPU utilization and wanted to use a script
that would monitor and record CPU utilization on his system.
I found a script posted on TechRepublic at
CPU Utilization Script1.
I modified the script so that I could
specify the time interval between CPU utilization checks through an argument
to the script when it is run. The modified script is available at
CPU_Use.vbs
2.
The script can be run with csript /nologo CPU_Use.vbs or
alternatively cscript /nologo CPU_Use num where "num" is the
number of seconds to wait between CPU checks, e.g. csript /nologo CPU_Use
300 to check every 5 minutes.
The output is placed in C:\Processor.log; the output location can
be changed by modifying the value of the strLogFile
variable in the script. Output will look similar to the following:
9/22/2007 09:43
9/22/2007 09:48 19
9/22/2007 09:53 17
9/22/2007 09:58 17
9/22/2007 10:03 35
9/22/2007 10:08 14
9/22/2007 10:13 15
The first two columns list the date and time the script was run while
the third lists the CPU utilization at the time the script was executed.
There is no value for CPU utilization for the first entry in the log.
The script requires Windows XP or later. It will not run on Windows 2000.
If it is run on Windows 2000, you will see
CPU_Use.vbs(48, 1) Microsoft VBScript runtime error: ActiveX component
can't create object: 'WbemScripting.Swbemrefresher'
3, 4
Most of the systems I support are Windows XP systems, so the script will
still be useful to me, but I can't check the system I wanted to check
in this case, since that system is a Windows 2000 system.
References:
-
CPU Utilization Script
By: neilb
Posted: January 4, 2006
TechRepublic
-
CPU_Use.vbs
By: Jim Cameron (modifications to script written by neilb)
MoonPoint Support
-
ActiveX component can't create object: 'WbemScripting.Swbemrefresh
Posted By: Daniel
Date: April 19, 2005
Ureader.com - Microsoft community
-
SWbemRefresher Object
Microsoft Developer Network
[/languages/vbs]
permanent link
Fri, Aug 31, 2007 11:33 am
Setting Savin C3535 Printer for Folding and Stapling
A client was having problems printing a brochure from Microsoft Publisher to a
Savin C3535 copier/printer. She wanted to have the document folded and stapled.
Folding and stapling worked for tabloid pages, but not letter-size pages.
The company providing support for the Savin 3535 printer suggested the
following steps be taken at the server from which the printer was being
shared.
- Click on Start.
- Select Printers and Faxes.
- Right-click on the printer, in this case SAVIN C3535 PCL 6, and
select Properties
- Click on the Accessories tab.
- Check Tray 3 (LCT) and Finisher SR3020
- Click on the Paper Size Settings tab.
- Select Tray 1 under Input Tray.
- For Paper Size, select Letter (8.5" x 11") then
click on Update
- For Tray 2, select 11" x 17" as the paper size
and click on Update.
- For Tray 3 (LCT), select 8.5" x 11" as the paper size
then click on Update.
- Click on OK.
When that didn't resolve the problem, the tech support person I spoke to
suggested deleting the shared printer from the system on which the print
job was being generated and then adding the share for the printer again.
[/os/windows/printers]
permanent link
Thu, Aug 30, 2007 10:11 pm
Print Last Page First in Adobe Acrobat
To reverse page printing order, i.e. to print the last page of a document
first, in Adobe Acrobat 6.0, take the following steps:
- Click on File.
- Select Print.
- Check Reverse pages.
- Click on OK.
References:
-
Options in the Print dialog box
Adobe Systems Incorporated
[/os/windows/software/pdf]
permanent link
Tue, Aug 28, 2007 11:04 pm
Forwarding Email to Another Exchange User
For an Exchange 2003 server, If you need to forward email to another Exchange
user when an employee leaves, take the following steps.
- Go to Active Directory Users and Computers.
- Select the account for the user who left and right click on it.
- Select Properites.
- Under the Exchange General tab, click on the Delivery
Options button.
- Click on the Modify button at the Delivery Options
window that opens.
- In the "Enter object name to select" field, type the account name of the
user to whom email should be forwarded, e.g. jsmith.
- Click on the Check names button to verify the account name and
then click on OK when it has been verified.
- Click on OK again to close the Delivery Options window.
- Click on OK to close the Properties window.
If you need to forward email to an external address instead of an internal
Exchange address,
see
Forwarding an Exchange User's Email to an External Address.
References:
-
Forwarding an Exchange User's Email to an External Address
November 5, 2006
MoonPoint Support
-
Redirect mail from old staff and reply to senders with new instructions
November 11, 2005
TechRepublic
[/network/email/exchange]
permanent link
Mon, Aug 20, 2007 11:35 pm
Premature EOM in Sendmail Log File
A user reported that she had been unable to receive email from two email
addresses. The server processing her incoming email is running
sendmail. When I looked in the
/var/log/maillog files, where entries related to successful
and unssuccessful email delivery attempts for sendmail are stored, for
any entries related to one of the email addresses she mentioned, I did
not see any, but I saw many entries similar to the following for
the domain name used in that email
address, which mentioned
collect: unexpected close on connection.
Aug 16 23:37:57 frostdragon sendmail[3738]: l7H3ak69003738: collect:
premature EOM: unexpected close
Aug 16 23:37:57 frostdragon sendmail[3738]: l7H3ak69003738: collect: unexpected close on connection from mail6.tcusa.com,
sender=<orders@example.com>
I had also been receiving reports from others that sending even small messages
sometimes takes a long time. A couple of times when I checked the number of
SMTP connections to
the server with netstat -a | grep smtp | wc -l, I found over
60 connections from other email servers. Previously, I would find that there
would usually be no more than a dozen such connections at any give time. And,
if I connected to the SMTP port with telnet mail.example.com 25,
I would sometimes see fairly slow responses.
In searching for information on the problem, I found
Sendmail ‘collect: premature EOM: unexpected close’ solution
. The author was encountering the same problem, which he traced to the use
of a defunct DNSBL,
relays.ordb.org. Like the author, I have been using relays.ordb for a long
time to block incoming spam to the server. In the /etc/mail/sendmail.mc
file on the server, I have the following line.
FEATURE(`dnsbl', `relays.ordb.org', `"550 Mail from " $`'&{client_addr} " refused due to sending server misconfiguration - see http://www.ordb.org/faq/\#why_rejected"')dnl
I removed the above line from /etc/mail/sendmail.mc, but added
another DNSBL in its place, the Abusive
Hosts Blocking List (AHBL), which I found listed at
HOWTO: Sendmail tips for Ensim, by adding the following line to
/etc/mail/sendmail.mc.
FEATURE(dnsbl,`dnsbl.ahbl.org', `"550 Host is on the AHBL - Please see [url]http://www.ahbl.org/tools/lookup.php?ip=[/url]"$&{client_addr}')dnl
I then took the following steps to update sendmail's configuration information
so that it no longer checks the relays.ordb.org blocklist, but uses the AHBL
list instead.
- I issued the command below
m4 /etc/mail/sendmail.mc > /etc/mail/sendmail.cf
-
I then stopped and restarted sendmail with the command below
/etc/init.d/sendmail restart
According to
DNS Blacklist ORDB.org is shutting down the relays.ordb.org DNSBL
has been shut down since December 18, 2006. When I tried pinging it, I don't
get a response and an nslookup on the name returns an error message as well.
# nslookup relays.ordb.org
Note: nslookup is deprecated and may be removed from future releases.
Consider using the `dig' or `host' programs instead. Run nslookup with
the `-sil[ent]' option to prevent this message from appearing.
;; connection timed out; no servers could be reached
I'm using 5 other blocklists as well, so I checked all of them by pinging
them to ensure that no other blocklists that I am using have disappeared.
I got responses for all of them, but that just verifies that a system is
functioning at the address pinged. To check whether a system is actually
functiong as a DNSBL at that address, you should issue use the nslookup,
host, or dig commands to query the system using a query in the form
2.0.0.127.blacklist.example.com.
All of the commands should result in the address 127.0.0.2 being
displayed as the IP address for
the query. This is because DNSBL's normally work by storing the IP address
of systems to be blocked as reversed mappings so that queries are submitted
akin to how you would do a reverse lookup for an in-addr.arpa
query (see
Chapter 9: Howto Create a DNSBL (DNS Black List), if
you wish further details on how DNSBL's work). Since the convention is
for DNSBL's to always have the address 127.0.0.2 in the list, querying
for that address allows for easy testing. E.g. for AHBL, I could use
2.0.0.127.dnsbl.ahbl.org with nslookup, host, or dig.
# nslookup 2.0.0.127.dnsbl.ahbl.org
Note: nslookup is deprecated and may be removed from future releases.
Consider using the `dig' or `host' programs instead. Run nslookup with
the `-sil[ent]' option to prevent this message from appearing.
Server: 207.233.128.10
Address: 207.233.128.10#53
Non-authoritative answer:
Name: 2.0.0.127.dnsbl.ahbl.org
Address: 127.0.0.2
# host 2.0.0.127.dnsbl.ahbl.org
2.0.0.127.dnsbl.ahbl.org has address 127.0.0.2
# dig +short 2.0.0.127.dnsbl.ahbl.org
127.0.0.2
Note: this won't work for all DNSBL's, e.g. performing an nslookup for
2.0.0.127.dnsrbl.swinog.ch returns
** server can't find 2.0.0.127.dnsrbl.swinog.ch: NXDOMAIN, even
though the DNSBL is working.
For checking whether a particular IP address is in one of the blacklists,
you would reverse the address and then put a period and the name of
the blacklist after it when issuing an nslookup, host, or dig query.
E.g., if I wanted to find out whether the addresses
62.30.35.75 and 62.30.35.76 are in the
Composite Blocking List (CBL), I could use
the commands below.
# host 75.35.30.62.cbl.abuseat.org
75.35.30.62.cbl.abuseat.org has address 127.0.0.2
# host 76.35.30.62.cbl.abuseat.org
Host 76.35.30.62.cbl.abuseat.org not found: 3(NXDOMAIN)
From the results, I see that the first address is in the CBL DNSBL, but
the second address is not in the blacklist.
Checking other blacklists, aka blocklists, I'm using by querying for
the presence of 127.0.0.2 in the lists, I found that opm.blitzed.org
is no longer functioning either.
# host 2.0.0.127.opm.blitzed.org
;; connection timed out; no servers could be reached
At OPM status, I learned
that opm.blitzed.org has also been shut down. It was shut down in May 2006.
Details on the shutdown have been posted at
[opm-announce] opm.blitzed.org has shut down.
So I removed the line below from /etc/mail/sendmail.mc.
FEATURE(`dnsbl', `opm.blitzed.org', `"550 Mail from " $`'&{client_addr} " refused - see http://opm.blitzed.org"')dnl
After verifying all of the other blacklists I was using in sendmail.mc still
worked, I then rebuilt the sendmail.cf file with the m4 command as above and
then restarted sendmail again.
References:
-
Sendmail ‘collect: premature EOM: unexpected close’ solution
Posted by plattapuss
on February 28th, 2007
Out of Control Image
-
DNSBL
Wikipedia, the free encyclopedia
-
Abusive Hosts Blocking List
-
HOWTO: Sendmail tips for Ensim
Posted By: pblinux
Posted: December 1, 2003
The Planet Forums
-
DNS Blacklist ORDB.org is shutting down
Article ID: KBID002925
GFI Knowledge Base
-
Chapter 9: Howto Create a DNSBL (DNS Black List)
ZyTrax, Inc.
-
Composite Blocking List
-
OPM Status
Blitzed Wiki
-
[opm-announce] opm.blitzed.org has shut down
Posted By: Andy Smith grifferz at blitzed.org
Posted: May 7, 2006
lists.blitzed.org Mailing Lists
[/network/email/sendmail]
permanent link
Fri, Aug 17, 2007 9:43 pm
DNS Server Listening on All Addresses
I removed the line
listen-on { 127.0.0.1; };
from
/etc/named.conf
to enable a Solaris server to listen on all IP addresses for the server, not
just the loopback address, making it usable as a
DNS server by other systems
on the LAN.
[/os/unix/solaris]
permanent link
Fri, Aug 17, 2007 9:23 pm
Start Named Service under Solaris
I had configured a Solaris 10 system to function as a name server
(see
Configuring a
Solaris System as a DNS Server), but when I rebooted the system
it was no longer functioning as a DNS server and since the only name server
I had listed in
/etc/resolv.conf was the system itself, i.e.
its loopback address, I could not resolve system names to IP addresses.
# svcs | grep 'named'
# nslookup cisco.com
;; connection timed out; no servers could be reached
# cat /etc/resolv.conf
domain example.com
nameserver 127.0.0.1
I could run named to start the named daemon again, so that
I could resolve names, but I wanted it to start automatically when the
system boots. To do so, I created the file /etc/init.d/named
with the following lines in the file:
#!/sbin/sh
#
# named
#
case "$1" in
start)
# Start daemon.
echo "Starting named"
/usr/sbin/named
;;
stop)
# Stop daemon.
echo "Shutting down named"
pkill named
;;
*)
echo "Usage: $0 { start | stop }"
exit 1
;;
esac
exit 0
I then changed the group ownership for the file to sys to make
it consistent with the other files in that directory and made it executable.
# chgrp sys /etc/init.d/named
# chmod 744 /etc/init.d/named
# ls -l /etc/init.d/named
-rwxr--r-- 1 root sys 284 Aug 17 20:07 /etc/init.d/named
To have it start automatically, I also needed to add it to
/etc/init.d/rc3.d. You need to prefix the name with
"S" and then a number to have it start automatically. You will see other
files with names beginning with Sxx where "xx" is some number. You must
pick a number that is different from any already used. I picked the next
higher number, 91, in this case.
# cp -p /etc/init.d/named /etc/rc3.d/S91named
When you reboot, you can check that the service is running with
the ps or svcs commands or do an nslookup
.
# ps -ef | grep named
root 537 1 0 20:42:16 ? 0:00 /usr/sbin/named
# svcs | grep named
legacy_run 20:42:18 lrc:/etc/rc3_d/S91named
# nslookup cisco.com
Server: 127.0.0.1
Address: 127.0.0.1#53
Non-authoritative answer:
Name: cisco.com
Address: 198.133.219.25
References:
-
Configuring a Solaris
System as a DNS Server
MoonPoint Support
-
Building
and configuring BIND 9 in a chroot jail
By Steve Friedl
Unixwiz.net - Software Consulting Central
[/os/unix/solaris]
permanent link
Mon, Aug 13, 2007 6:10 pm
Deleting a User Under Solaris 2.7
To delete a user on a system running Solaris 2.7, run
admintool,
select the user's account by clicking on it, then click on
Edit
then
Delete. You will be prompted as to whether you really want
to delete the user's account and can choose to delete the home directory
when the account is deleted. You may have to manually delete a mail file for the
user from /var/mail, e.g.
rm /var/mail/jsmith.
[/os/unix/solaris]
permanent link
Sun, Aug 12, 2007 6:22 pm
Too Many Partitions for Norton Ghost
I tried to backup a system with four primary partitions across the network
with Norton Ghost 7.5 using the Symantec Ghost Console, but was unable to do so,
since Ghost was unable to set up the virtual partition it needed on the client
system. When I deleted one of the partitions on the client system, I was able
to successfully backup the system.
[ More
Info ]
[/os/windows/utilities/backup/ghost]
permanent link
Fri, Aug 10, 2007 9:01 pm
mii-tool
If you want to know the speed at which a system has connected to the
LAN, e.g. the system can
autonegotiate its speed and you need to know which speed it is using, you can
use the
mii-tool
command to check the status of Ethernet devices in the system.
# mii-tool
eth0: no autonegotiation, 10baseT-HD, link ok
From the above output from the command on a Linux system, I can see that
the Ethernet device, eth0, is not using autonegotiation to determine its
speed and is set to 10 Mbs half duplex.
If you want more details for Ethernet devices in the system, you can
use -v or --verbose as a parameter to the command.
# mii-tool -v
eth0: no autonegotiation, 10baseT-HD, link ok
product info: vendor 00:10:18, model 23 rev 7
basic mode: autonegotiation enabled
basic status: autonegotiation complete, link ok
capabilities: 100baseTx-FD 100baseTx-HD 10baseT-FD 10baseT-HD
advertising: 100baseTx-FD 100baseTx-HD 10baseT-FD 10baseT-HD flow-control
From the above, I can see that eth0, though it is set for a 10baseT connection,
i.e. 10 Mbs, can support a 100baseTx, i.e. 100 Mbs, connection.
The device is capable of the following port speeds:
| Port Speed | Description |
|---|
| 10baseT-HD |
10 megabits/s half duplex |
| 10baseT-FD |
10 megabits/s full duplex |
| 100baseTx-HD |
100 megabits/s half duplex |
| 100baseTx-FD |
100 megabits/s full duplex |
mii-tool manpage
References:
-
B.5. mii-tool
Guide to IP Layer Network Administration
with Linux
[/os/unix/commands]
permanent link
Thu, Aug 09, 2007 9:56 pm
Configuring Outlook Express 6 For TLS
Outlook Express can be configured to use
TLS to authenticate
with an email server and to transmit messages securely, i.e. in
encrypted form between Outlook Express and the server set to be its
SMTP server.
Note: TLS doesn't gurantee end-to-end encryption of the message, just
the encrypted transmission of the message from the client email program, such
as Outlook Express, to the SMTP server to which it hands off the message.
That server may in turn transmit the message to other servers in unencrypted
form.
[
More Info ]
[/network/email/clients/outlook-express]
permanent link
Tue, Aug 07, 2007 11:19 pm
Expired sendmail.pem Security Certificate
I had been getting reports from users of one domain handled by my
Linux email server
that email from/to a particular client they deal with had been getting
delayed. When I checked the maillog files, I found references to
"TLS errors" for that domain. When I discussed the problem with a tech
support person for the other company, he said his company is using Exchange
with a
TLS connector and
would prefer my server communicate using
TLS
with their server. He told me that the security certificate for my server
had expired.
I didn't know how to check the expiration date until I found instructions
for checking the expiration at
Renew SSL certificate in RedHat 9.
Sugree, the author of
that webpage, suggested running the command openssl x509 -in
sendmail.pem -text | grep Not. The instructions were written for
a RedHat 9 system. When I ran the command, I saw the following
results.
# cd /usr/share/ssl/certs
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Not
Not Before: Nov 9 21:26:57 2003 GMT
Not After : Nov 8 21:26:57 2004 GMT
The author then recommended using the command openssl x509 -in
sendmail.pem -text | grep Subject. It produced the following
results on my server.
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Subject
Subject: C=US, ST=Maryland, L=Annapolis, O=MoonPoint, CN=frostdragon.com/emailAddress=support_999@frostdragon.com
Subject Public Key Info:
X509v3 Subject Key Identifier:
The information above will be needed when you generate a new certificate.
I deleted the /usr/share/ssl/certs/sendmail.pem file and generated
a new one with make sendmail.pem, which I ran from
/usr/share/ssl/certs. The bold text items are the responses I entered
to queries and repeat the information I saw when I ran openssl x509 -in
sendmail.pem -text | grep Subject.
[root@frostdragon certs]# make sendmail.pem
umask 77 ; \
PEM1=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
PEM2=`/bin/mktemp /tmp/openssl.XXXXXX` ; \
/usr/bin/openssl req -newkey rsa:1024 -keyout $PEM1 -nodes -x509 -days 365 -out $PEM2 ; \
cat $PEM1 > sendmail.pem ; \
echo "" >> sendmail.pem ; \
cat $PEM2 >> sendmail.pem ; \
rm -f $PEM1 $PEM2
Generating a 1024 bit RSA private key
...........++++++
..............................................++++++
writing new private key to '/tmp/openssl.Ipeqjd'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [GB]:US
State or Province Name (full name) [Berkshire]:Maryland
Locality Name (eg, city) [Newbury]:Annapolis
Organization Name (eg, company) [My Company Ltd]:MoonPoint
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:frostdragon.com
Email Address []:support_999@frostdragon.com
When I then checked the expiration of the sendmail.pem certificate,
I saw the following.
[root@frostdragon certs]# openssl x509 -in sendmail.pem -text | grep Not
Not Before: Aug 8 02:41:22 2007 GMT
Not After : Aug 7 02:41:22 2008 GMT
So now I've got a certificate that is good for another year.
References:
-
Transport
Layer Security
Wikipedia, the free encyclopedia
-
Renew SSL certificate in RedHat 9
By Sugree
howforge.com | Share Know-How
[/network/email/sendmail/tls]
permanent link
Sun, Aug 05, 2007 10:19 pm
Norton Ghost 7.5 - Broadcom 57xx Integrated Controller
If you want to backup a Dell system with a Broadcom NetXtreme 57xx
integrated network controller using Norton Ghost 7.5, then you will
need to create a template for that network interface card (NIC) using
an NDIS2 driver.
[ More Info ]
[/os/windows/utilities/backup/ghost]
permanent link
Tue, Jul 31, 2007 10:28 am
Rosetta Stone
Someone on the
solaris-l mailing list mentioned the
Rosetta Stone for Unix webpage
today as an informative source for determining which commands are available
on the various flavors of Unix systems to perform common administrative
tasks. When I checked the webpage, I found it had information for
the operating systems listed below.
- AIX
- A/UX
- DG/UX
- FreeBSD
- HP-UX
- IRIX
- Linux
- Mac OS X
- NCR Unix
- NetBSD
- OpenBSD
- Reliant
- SCO OpenServer
- Solaris
- SunOS 4
- Tru64
- Ultrix
- UNICOS
[/os/unix]
permanent link
Mon, Jul 23, 2007 10:26 pm
Invalid MAC Address for SiS 900-Based NIC
When I installed a new firewall at a site, the domain controller
could not ping the firewall nor access the Internet through the firewall,
yet it could ping and access all other systems on the LAN. The problem
was due to the domain controller using a SiS 900-based PCI Fast Ethernet
network adapter, which had a physical, aka
MAC, address of all zeroes.
When I assigned a non-zero address to the adapter, the problem disappeared.
[ More Info ]
[/network/arp]
permanent link
Mon, Jul 23, 2007 6:01 pm
No Display on Monitor
One of my wife's aunts was not getting any display on her monitor.
I replaced the
AGP
video adapter in her system with another AGP adapter, but still nothing
would appear on the monitor when the system was booted. I tried
a
PCI video adapter instead, but the results were the same. The
original AGP adapter from her system worked in another system, so it
appears the problem is a fried motherboard; she said the problem happened
after a storm, though the system was plugged into an
UPS.
The motherboard in the system is an
EliteGroup Computer Systems (ECS)
K7S5A motherboard.
For anyone having video display problems, there is a flowchart,
Troubleshooting a Video
Adapter and Computer Monitor by Morris Rosenthal that lists steps
you can take to isolate the problem.
[/hardware/pc/video]
permanent link
Tue, Jul 17, 2007 10:13 pm
Adding a Column to a MySQL Database
To add a column to a MySQL database, you can use the following steps:
- Start the text-based MySQL client
$ mysql -u testacct -p
The -u testacct parameter specifies that the client should
be started using the account named testacct, while the
-p parameter indicates that the system should prompt you
for the password.
- At the mysql> prompt, enter the command use dbname;, where dbname is the database name. If you don't know
the name of the database, you can see a list of available databases with
the show databases; command.
-
Use the alter table command to modify the appropriate table. If
you need to see a list of tables in the database, you can use the show
tables; command. E.g. to add a column,
delivered, which
will hold a delivery date for a shipment, to the table requests,
you could use the command below:
ALTER TABLE requests ADD delivered DATE;
That would put the new column at the end of the existing columns.
If you want to add the column after a specific column, you can specify that
column with AFTER colname. E.g., suppose I wish to add the
column delivered after the column orderdate.
I could use the command below:
ALTER TABLE requests ADD delivered DATE AFTER orderdate;
If you don't know the names of the existing columns, you can use the
command SHOW COLUMNS FROM dbname;. E.g., if the table is
named requests, I could use the command below:
mysql> show columns from requests;
References:
-
Add a column to an existing MySQL table
Created: February 8, 2004
Updated: July 17, 2004
tech-recipes
[/software/database/mysql]
permanent link
Sun, Jul 15, 2007 10:33 pm
QuarkXPress 7.0 on Windows Vista
I needed to install QuarkXPress 7.0 on a new system running Microsoft
Windows Vista. When I attempted to install it, I received the message
below.
| QuarkXPress 7.0 - Setup |
 QuarkXpress 7.0 requires that your computer is running Windows XP or
Windows 2003
QuarkXpress 7.0 requires that your computer is running Windows XP or
Windows 2003
OK
|
I found numerous people complaining about the same problem at
Cannot install Quark installer 7.2 on VISTA. The solution
listed on that page was to download the 30-day evaluation version of
QuarkXPress 7.2 installer. Unfortunately, Quark forces you to register to
download the installer. It doesn't matter that you may haver registered with
them previously. You will have to register again. Then you have to wait for
an email message with a link in it to download the software. Although
the evaulation version is labeled as an "evaluation version", it is fully
functional and will accpet the 7.0 validation code. The link
to download the software is
http://www.quark.com/products/xpress/evaluate/demos.cfm.
Quark states at
Updating to QuarkXPress 7.2 on a computer running Windows Vista which
DOES NOT HAVE a version of QuarkXPress installed that
"Before trying to use QuarkXPress 7.2 after installing it, please be sure
to run the QuarkXPress license transfer function (Help> Transfer
QuarkXPress License) on your old computer and follow the steps provided."
To transfer the license, take the following steps in QuarkXPress:
- Click on Help
- Click on Transfer QuarkXPress license
References:
-
Cannot install Quark installer 7.2 on VISTA
First Posting: April 5, 2007
Quark Forums
-
Microsoft Windows Vista Support
Date: 2007
Quark, Inc.
-
Updating to QuarkXPress 7.2 on a computer running Windows Vista which
DOES NOT HAVE a version of QuarkXPress installed.
Date: 2007
Quark, Inc.
[/os/windows/software/quarkxpress]
permanent link
Sun, Jul 08, 2007 9:01 pm
Creating a Watermark on an Excel Spreadsheet
I wanted to put a watermark of "Paid" on a one-page Excel 2000 spreadsheet
I had created as an invoice form. I found instructions on how to do
so at
Print a Watermark on Excel Worksheet. To do so, take the
following steps in Excel with the spreadsheet open.
- Click on View.
- Select Page Break Preview.
- When you see the "You can adjust where the page breaks are by
clicking and dragging them with your mouse" window, click on the
OK button.
- Click on the WordArt button, which is represented by a blue "A"
tilted slightly to the right, in the Drawing toolbar at the
bottom of the Excel window. If you don't
see this toolbar, click on View, select Toolbars and check
Drawing by selecting it.
- When prompted to pick a WordArt style, pick the one at the top left
corner of the rows of different styles, which will give you a simple outline
style.
- Click on OK.
- Pick the font and the size you want for it or accept the default values,
then type the text you want in the "Text" field, e.g. "Paid" to have
that word as the "watermark".
- Click on OK.
- You will then see the word appear as an outline off to the right
of the spreadsheet with small sqaures along the edge of the text that
serve as handles where you can grab the text. You can click in the middle
of the text to grab it and then hold down the left mouse button and
drag it where you want to place it on the spreadsheet. You can also grab the
text at one of the squares along one of the sides with the cursor and stretch it
to make it larger, if you wish. On the WordArt toolbar there is also a
"Free Rotate" button, which is represented by a curved arrow. You can use
it to rotate the text by clicking on that button and then grabbing one
of the corners of the text.
- The watermark may obscure some of the text on the spreadsheet when
you've placed it where you want it. To fix that problem, right click on the
watermark text and choose "Format WordArt". You can change the color
of the fill and the line color. I left the fill color as white, but
checked "semitransparent" and changed the line color to gray.
- You can go to View and select Normal View now, if you
want to better see how the page looks with the watermark on it.
- If you only have a one-page spreadsheet, you are finished. If you
have multiple pages, right-click on the watermark, choose Copy.
Then go to other pages and choose Edit and Paste.
[/os/windows/office/excel]
permanent link
Sun, Jul 08, 2007 1:47 pm
Windows Not Genuine
I moved disk drives from a system with hardware problems to another system.
I had to repair Windows afterwards, since the hardware was different. But
then I got messages that my copy of Windows was not genuine and that I
might have a counterfeit version of Windows, which I did not believe was
true. I spent several hours trying to resolve the problem including
speaking to several customer service personnel working for Microsoft
without getting anywhere.
[ More Info ]
[/os/windows/xp]
permanent link
Tue, Jun 26, 2007 8:28 pm
Using ngrep to Monitor Email Transmissions
A user informed me that an email message she was trying to send was not
going out; Outlook showed it remaining in her outbox and would show an
error message regarding its attempted connection to the
SMTP server eventually,
because it couldn't send the message.
When I looked at bandwidth utilization at the SMTP server end with
bwmon, I saw
that almost all the available bandwidth was being consumed. When I checked
to see what type of traffic was involved using
IPTraf and
pkstat, I saw that email traffic, i.e. connections to port 25 on the
server, was consuming the bandwidth. A netstat -a | grep smtp
command showed a lot of connections to the
SMTP port, which is port 25.
When I counted them with netstat -a | grep smtp | wc -l, I
found there were 51 connections, which is far more than I would normally
see to the server.
To try to get more information on that traffic, I installed
ngrep. The author's
description of the tool is listed below:
ngrep strives to provide most of GNU grep's common features, applying
them to the network layer. ngrep is a pcap-aware tool that will allow
you to specify extended regular or hexadecimal expressions to match
against data payloads of packets. It currently recognizes IPv4/6, TCP,
UDP, ICMPv4/6, IGMP and Raw across Ethernet, PPP, SLIP, FDDI, Token
Ring and null interfaces, and understands BPF filter logic in the same
fashion as more common packet sniffing tools, such as tcpdump and snoop.
To see the "from" and "to" addresses being used in the transmissions,
I used the command ngrep -i 'rcpt to|mail from' tcp port smtp,
The -i option tells ngrep to ignore the case of characters
when looking for pattern matches. The 'rcpt to|mail from'
tells it to look for either rcpt to or mail from,
which are the commands sent to an email server to specify the recipient
and the sender of an email message. SMTP transmissions use
the TCP, so
the tcp parameter specifies that protocol and the smtp
specifies that the SMTP port, port 25 is the one to monitor.
Note: you will need to run the command as root or you will get the
message "no suitable device found: Operation not permitted".
The command showed the followng output:
# ngrep -i 'rcpt to|mail from' tcp port smtp
interface: eth0 (66.22.186.48/255.255.255.240)
filter: (ip) and ( tcp port smtp )
match: rcpt to|mail from
###############
T 59.172.123.117:1625 -> 66.22.186.53:25 [AP]
MAIL FROM: <kvocqcbrxzqxqs@fdvwiqrprdewt.logicbest.com>..
####
T 59.172.123.117:1625 -> 66.22.186.53:25 [AP]
RCPT TO:<janesmith@moonpoint.com>..
###########################
T 216.188.126.165:57486 -> 66.22.186.53:25 [AP]
MAIL FROM:<175419_VMTA12778-angel=MOONPOINT.COM@DPCTECHNOLOGIES.NET> BODY=8
BITMIME..RCPT TO:<angelica1@MOONPOINT.COM>..DATA..
#############################
T 66.115.129.69:4852 -> 66.22.186.53:25 [AP]
MAIL FROM:<>..
##
T 66.115.129.69:4852 -> 66.22.186.53:25 [AP]
RCPT TO:<moonpointm@moonpoint.com>..
Most of the traffic had invalid "rcpt to" addresses, i.e. there was no such
email address on the server. Many of the messages had no "mail from"
address. The "mail from" and "rcpt to" addresses are for the
"envelope"
of the message, i.e., they aren't necessarily the same as the "from" and
"to" addresses a recipient would see when viewing the message in an email
client. Instead, they are part of the SMTP transmission protocol.
An email server will use the "rcpt to" value to route a message to the
appropriate mailbox.
While I was checking on the issue, the bandwidth utilization dropped back
down to normal and I didn't take any further action.
References:
-
Bandwidth Monitoring on a Linux System
Date: September 15, 2004
MoonPoint Support
-
Using pktstat to Monitor Network Traffic
Date: December 13, 2006
MoonPoint Support
-
ngrep - network grep
By: Jordan Ritter
Date: November 18, 2006
SourceForge.net
-
The MAIL, RCPT, and DATA verbs
By D. J. Bernstein
D.J. Bernstein - Mathematics and
compuer science
-
ngrep RPM for
Red Hat, CentOS, and Fedora
By: Dag Wiiers
DAG: Field Commander Wieers
[/network/tools/ngrep]
permanent link
Mon, Jun 25, 2007 7:10 am
Pentagon Takes 1,500 Systems Offline
A
Time article dated Thursday, June 21,
2007, titled
Cyber Attack Hits Pentagon states that the Pentagon
took as many as 1,500 computers offline because of a cyber attack, which
occurred on Wednesday. The article stated that Defense Secretary
Robert Gates
said the Pentagon sees hundreds of attacks a day and this one had no adverse
impact on department operations. Employees whose computers were affected could
still use their handheld BlackBerrys.
I'm not surprised that the Pentagon sees hundreds of attacks a day, but
It is hard for me to believe that taking 1,500 systems offline had no
impact on department operations. Sure employees could still deal with email via
their BlackBerry's, but, even if the systems were used solely for
administrative purposes, I would expect the employees would be hampered by
a lack of access to spreadsheets, presenations, and other documents normally
used in an office environment. Hopefully, the attackers didn't glean
sensitive data from any of those systems.
I was surprised by Mr. Gates response when he was asked if his own e-mail
account was affected. He responded "I don't do e-mail. I'm a very low-tech
person." I understand that for his generation (he's 63 years old) email
may not be as much a part of the fabric of business life as for younger
Americans, but I was surprised to hear him state he doesn't use it at all,
especially since his prior position was president of Texas A&M University.
[/security/attacks]
permanent link
Tue, Jun 19, 2007 8:12 pm
MPack Used to Compromise Thousands of Websites
I received a message from
eWeek today
titled
MPack Trojan Attack Claims 10,000 Web Sites, which stated that
as many as ten thousand websites may have been infected with malware that
directs visitors to those websites to other sites where JavaScript code awaits
that attempts to use a buffer overflow attack against vulnerable browser to
cause malware to be downloaded to the systems of those visitors.
I would have liked to have more detail in the eWeek article about what
web server software was vulnerable to the MPack attack and what browsers
might be vulnerable, but it appears many
reports on the problem are just being posted today.
The eWeek article was the first I
had heard about the problem, so I appreciate the heads-up, though.
I also found information from Symantec at "Italy
Under Attack: Mpack Gang Strikes Again!,
after reading the eWeek article. There is another Symantec article
titled MPack, Packed Full of Badness. I also located
an ars technica article posted
earlier today at "
Security researchers uncover massive attack on Italian web sites,
which had much more detail than the eWeek article.
According to that article the MPack software being used on compromised web
servers "provides would-be malware installers with a complete package
that can be installed on any web server that runs PHP with an SQL
database." So that sounds like it can be used against both Apache web
server software running on a variety of platforms, including Linux and
Windows, as well as Microsoft's IIS web server software, since PHP along
with MySQL or Microsoft's own SQL server software may be running on such
systems. The article further states "The compromised web sites attempt
to use exploits in unpatched versions of Internet Explorer, QuickTime,
Windows 2000, Firefox, WinZip, and Opera, in order to install malware
packages on end users' computers."
[/security/attacks]
permanent link
Sun, Jun 17, 2007 8:21 pm
Troubleshooting With the Microsoft Exchange Troubleshooting Assistant
Microsoft provides the
Microsoft Exchange Troubleshooting Assistant v1.1 to aid in
troubleshooting problems with Microsoft Exchange Servers. I installed and
ran the tool today to try to figure out why messages sometimes get
stuck in
SMTP
queues on an Exchange 2003 server running on a Windows Small Business
Server (SBS) 2003 system.
[ More
Info ]
[/network/email/exchange]
permanent link
Sun, Jun 17, 2007 2:43 pm
Links Without Underlining
Occasionally, I want a specific link to appear in a webpage without
underlining. You can add
style="text-decoration:none"
with the link to prevent the text associated with the link from being
underlined.
For instance, sometimes I use superscripts in a document to link to
a reference. Normally a link will be underlined, which will look
slightly odd. E.g., if I link back to the reference
1, I
used for this blog entry, the number "1" has an underline below it.
If I don't want it to appear I can use the HTML code below.
<a href="http://www.pageresource.com/html/link3.htm"
style="text-decoration:none"><sup>1</sup></a>
Using that code the reference
1 superscrpt is not
underlined.
If you don't want any URLs in the webpage underlined, you can add the
following code to the head section of the HTML for the webpage.
<STYLE type="text/css">
<!--
A { text-decoration:none }
-->
</STYLE>
With the above code placed between your <HEAD> and
</HEAD> tags, you can
code your links as you normally would, but none of them will be underlined.
The style sheet in the head section will make them all non-underlined.
[/network/web/html]
permanent link
Sun, Jun 17, 2007 12:29 pm
Email Stuck in Exchange SMTP Queues
When a user complained that her email was not reaching a mailing list,
I checked the Exchange server that handles her email and found messages
stuck in
SMTP
queues on the server. I was able to force Exchange to send the queued messages,
but several messages had been stuck in a queue for days with one in a queue
for six days.
[ More Info ]
[/network/email/exchange]
permanent link
Sat, Jun 16, 2007 10:59 pm
Enabling Microsoft Exchange Message Logging
A Microsoft Exchange user reported to me that email she sent from Outlook
was not reaching recipients, but Outlook was putting it in the
Sent
folder indicating it had been successfully sent from Outlook.
I found that message tracking was not enabled on the Exchange server,
so I needed to turn it on to try to figure out what was happening.
[ More Info ]
[/network/email/exchange]
permanent link
Sat, Jun 16, 2007 4:16 pm
Prevent Mailing List Email from Going Into Junk E-mail or Spam Folders
I posted
instructions for Hotmail, Gmail, and Outlook users for steps
that can be taken to prevent email sent from mailing lists from being
automatically placed in junk email or spam folders.
[/network/email/mailing_list]
permanent link
Tue, Jun 12, 2007 8:01 pm
Tcpdump Permission Denied on OS-X
I needed to use tcpdump to perform network troubleshooting on an Apple OS-X
system (Darwin Kernel Version 7.9.0), but when I tried running it from
my account, I received a "permission denied" message.
$ tcpdump
tcpdump: (no devices found) /dev/bpf0: Permission denied
I don't know the root password for the system, but my account has
administrator privileges on the system. Without knowing the root
password, though, I could not su to the root account.
Fortunately, I found a solution at
Ethereal "Turbo Charged", where Olivier Biot posted a solution,
which I qoute below:
Do a "sudo chown Gurue /dev/bpf*" (or whatever your login name is on your
Mac). Once you've done that, you can (at least until the machine is
rebooted) run Ethereal or Tethereal or tcpdump or... as yourself, rather
than as root. (Mac OS X's "/dev" is implemented with devfs, so the special
files aren't persistent across reboots, and it's an older devfs so it can't
be configured to set up particular devices with particular owners and
permissions, so any ownership or permission changes you make don't survive
across reboots.)
I checked the existing permissions on /dev/bpf* files first.
$ ls -l /dev/bpf*
crw------- 1 root wheel 23, 0 12 Jun 18:32 /dev/bpf0
crw------- 1 root wheel 23, 1 12 Jun 15:30 /dev/bpf1
crw------- 1 root wheel 23, 2 12 Jun 15:30 /dev/bpf2
crw------- 1 root wheel 23, 3 12 Jun 15:30 /dev/bpf3
I then used changed the permissions on just /dev/bpf0. I was
prompted for a password when I used sudo chown myacct /dev/bpf0
and was able to change the permissions when I entered my password.
$ sudo chown jdoe /dev/bpf0
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these two things:
#1) Respect the privacy of others.
#2) Think before you type.
Password:
I was then able to run tcpdump. When I disconnected and reconnected,
I received the message tcpdump: (no devices found) /dev/bpf1: Permission
denied when I tried running tcpdump again, so I changed
the permission on /dev/bpf1 as well. I could have used
sudo chown jdoe /dev/bpf* initially to change the permissions
on all the /dev/bpf* files. Since I very infrequently need to
run tcpdump on this system, it doesn't matter to me that I will have
to reset the permissions on the files again whenever the system is rebooted.
[/os/os-x]
permanent link
Sun, Jun 10, 2007 9:27 pm
Email From 166.102.165.166 and 65.54.246.172 Rejected
A family member reported that someone who had tried to send email to
her received a bounced message indicating the email was blocked because
of antispam provisions. I checked all email from the sender's email
address using the
find-recipients Perl script I created for such purposes. I saw that one
message she sent was rejected and one accepted.
# ./find-recipients.pl wendyvi21@alltel.net /var/log/maillog
Found 2 messages from wendyvi21@alltel.net in /var/log/maillog
Message recipients
Time Message ID Status Recipient
----------------------------------------------------------------
Jun 10 07:58:02 l5ABupmb001042 Rejected kittycat321@moonpoint.com
Jun 10 08:05:03 l5AC3omb001081 Sent kittycat321@moonpoint.com
When I checked the /var/log/maillog file for those two message
IDs, I found that the first message had been blocked by the
Spam and Open-Relay Blocking
System (SORBS) blocklist. SORBS is a
DNS Blacklist (DNSBL).
The message that was rejected was from ispmxmta05-srv.windstream.net
[166.102.165.166], while the one that was accepted was from
ispmxmta09-srv.windstream.net [166.102.165.170].
When I checked the SORBS list, it appeared that the 166.102.165.166
had been there for at least a week due to SORBS detecting spam
orginating from the email server at that address.
Database of servers sending to spamtrap addresses
| Address: | 166.102.165.166 |
| Record Created: | Tue Apr 17 01:00:04 2007 GMT |
| Record Updated: | Mon Jun 4 01:00:03 2007 GMT |
| Additional Information: |
[ Updated via: Spam 'o Matic ] Received: from
ispmxmta05-srv.windstream.net (ispmxmta05-srv.windstream.net [166.102.165.166]) by desperado.sorbs.net (Postfix) with ESMTP id EE4311144D for <[email]>;
Mon[email] 04 Jun 2007 10:40:27 +1000 (EST) |
| Currently active and flagged to be published in DNS |
But when I looked up the other IP address, 166.102.165.170, it appeared it
was also in the SORBS blocklist.
Database of servers sending to spamtrap addresses
| Address: | 166.102.165.170 |
| Record Created: | Tue Oct 4 13:04:20 2005 GMT |
| Record Updated: | Thu Apr 26 04:41:17 2007 GMT |
| Additional Information: |
Received: from ispmxmta09-srv.windstream.net (ispmxmta09-srv.windstream.net
[166.102.165.170]) by desperado.sorbs.net (Postfix) with ESMTP id 69DC21143A
for <[email]>; Sat[email] 10 Feb 2007 13:52:40 +1000 (EST) |
| Currently active and flagged to be published in DNS |
When I queried the SORBS database through the SORBS
Database Lookup
webpage, it appeared both addresses were present in the SORBS blocklist,
yet when I used
blq to query the SORBS blocklist, I found only the first .166 address listed
and not the .170 address, which was consistent with Sendmail's rejection of
the first message, but not the second one.
# ./blq sorbs 166.102.165.166
166.102.165.166 ispmxmta05-srv.windstream.net : dnsbl.sorbs.net : BLOCKED
# ./blq sorbs 166.102.165.170
166.102.165.170 ispmxmta09-srv.windstream.net : dnsbl.sorbs.net : ok
I received another report from a Hotmail sender
that she was finding email rejected as well. I went through the same process
as above. Again the SORBS website database query seemed to indicate that both
addresses would be blocked, but using blq showed only one was blocked, which
matched the entries I found in today's maillog file with the first message
from the sender being rejected and the second accepted. The first was from
bay0-omc2-s36.bay0.hotmail.com [65.54.246.172] and the second from
bay0-omc2-s37.bay0.hotmail.com [65.54.246.173].
When performing a database check via the website, I saw the following
for the IP address from which a message was rejected:
Database of servers sending to spamtrap addresses
| Address: | 65.54.246.172 |
| Record Created: | Thu Aug 3 02:30:03 2006 GMT |
| Record Updated: | Sat Jun 9 09:00:04 2007 GMT |
| Additional Information: |
[ Updated via: Spam 'o Matic ] Received: from
bay0-omc2-s36.bay0.hotmail.com (bay0-omc2-s36.bay0.hotmail.com [65.54.246.172])
by desperado.sorbs.net (Postfix) with ESMTP id 7EE241147D for <[email]>;
Sat, 09 Jun 2007 18:33:28 +1000 (EST) |
| Currently active and flagged to be published in DNS |
But I also saw the following for the IP address of the server from which
a message was accepted:
Database of servers sending to spamtrap addresses
| Address: | 65.54.246.173 |
| Record Created: | Fri Aug 4 13:53:11 2006 GMT |
| Record Updated: | Sat Mar 3 08:00:34 2007 GMT |
| Additional Information: |
[ Updated via: Spam 'o Matic ] Received: from bay0-omc2-s37.bay0.hotmail.com
(bay0-omc2-s37.bay0.hotmail.com [65.54.246.173]) by desperado.sorbs.net
(Postfix) with ESMTP id 8E17F114AE for <[email]>; Wed, 28 Feb 2007
21:44:25 +1000 (EST)
|
| Currently active and flagged to be published in
DNS |
Again, the information returned didn't seem to be consisttent with
what a blq query returned:
# ./blq sorbs 65.54.246.172
65.54.246.172 bay0-omc2-s36.bay0.hotmail.com : dnsbl.sorbs.net : BLOCKED
# ./blq sorbs 65.54.246.173
65.54.246.173 bay0-omc2-s37.bay0.hotmail.com : dnsbl.sorbs.net : ok
So the results I obtained through the website query don't seem to accurately
reflect what will be blocked, if I interpret seeing
"Currently active and flagged to be published in DNS" appearing in a red
block as an indication the address is in the blocklist as one to be blocked.
[/network/email/spam/blocklists]
permanent link
Sun, Jun 10, 2007 4:20 pm
Content Management System (CMS) Comparison
I need to set up a Content Management System (CMS) for a new website.
I've considered
Drupal and
Mambo, but wanted to find
information comparing the two. I found a site today,
The CMS Matrix that allows you to
compare the features of dozens of content management systems. You can select
up to 10 at a time to see a comparison chart of features.
A comparison of Drupal and Mambo can also be found at
Leading Open Source CMS: Mambo versus Drupal - A Comprehensive
Comparison. That article references a more comprehensive
comparison of Drupal and Mambo,
Drupal VS. Mambo written for Xaneon
Development, a company which developed Mambo extensions.
References:
- The CMS Matrix
-
Leading Open Source CMS: Mambo versus Drupal - A Comprehensive Comparison
By Angsuman Chakraborty
September 13, 2005
Simple Thoughts - Simple solutions
for complex problems
-
Drupal VS. Mambo
Originally written for Xaneon Development by Arto Bendiken
Submitted: January 12, 2006
Xaneon Development
[/network/web/cms]
permanent link
Sun, Jun 10, 2007 1:25 pm
OS-X Running on a PC
Enterprising OS-X hackers have found a way to run Apple's OS-X operating
system on standard PC hardware as related in
Wired's article
Mac Hacks Allow OS X on PCs. Despite Apple's use of a chip to
specifically prevent users from putting the operating system (OS) on a standard
PC, it is now possible to run the OS on standard
PC hardware.
[/os/os-x]
permanent link
Sun, Jun 10, 2007 1:17 pm
Apple's Core Animation
Wired has an article,
Kiss Boring Interfaces Goodbye With Apple's New Animated OS
about a new animation feature that will become available in the Leopard
version of OS-X. The feature will allow developers to provide an animated
interface to their applications.
[/os/os-x]
permanent link
Sun, Jun 10, 2007 12:28 am
Mailman Mailing List Messages Arriving with Unwanted Attachment
I set up a
Mailman
mailing list for a family member. After I set up the list, she sent
a message to the list. The message arrived with a .txt attachment,
ATT00088.txt, that was 251 bytes in size. The attachment
had only 3 lines. The first was the mailing list name, the next was
the mailing list email address, and the last was the listinfo URL for
the mailing list. She uses Outlook 2003
and this is apparently a problem that occurs with Mailman maling list messages
received by Outlook users
when a footer is added to messages, which is Mailman's default behavior.
Apparently Mailman adds the footer as an attachment if the
original message posted contains a message formatted in HTML MIME,
or a text/plain MIME bodypart using a different character set than
what Mailman would use for the footers.
To prevent the addition of a footer to messages,
from the main mailman administration page for the list, I clicked on
[Non-digest options] The text below appeared in the
"Footer added to mail sent to regular list members" field.
_______________________________________________
%(real_name)s mailing list
%(real_name)s@%(host_name)s
%(web_page_url)slistinfo%(cgiext)s/%(_internal_name)s
The information listed has the following meaning.
msg_footer (nondigest): Footer added to mail sent to regular list membersText appended to the bottom of every immediately-delivery
message. This text can include
Python
format strings which are resolved against list attributes. The
list of substitutions allowed are:
real_name - The `pretty' name of the list; usually
the list name with capitalization.
list_name - The name by which the list is
identified in URLs, where case is significant. (For backwards
compability, _internal_name is equivalent.)
host_name - The fully qualified domain name
that the list server runs on.
web_page_url - The base URL for Mailman. This
can be appended with,
e.g. listinfo/%(internal_name)s to yield the
listinfo page for the mailing list.
description - The brief description of the
mailing list.
info - The full description of the mailing
list.
cgiext - The extension added to CGI scripts.
Since the list owner did not want any footer being sent with messages,
I removed all of the text from that field.
I also went to the digest options page and for the "Header added to
every digest" field, I removed all of the text in that field.
References:
-
[Mailman-Users] Why are footers sent as attachments?
Posted: January 29, 2006
The Mailman-Users
Archives
-
4.39. HELP! Mailman is munging HTML & MIME-formatted messages before they are
sent out? (problems with Mailman 2.1.x footers)
Mailman FAQ Wizard
[/network/email/mailing_list/mailman]
permanent link
Sun, Jun 10, 2007 12:15 am
Messages from Mailman Mailing List Appear From Listname-bounces
I set up a
Mailman
mailing list for a family member. When she receives messages from the
list they are arriving with a "from" address of
listname-bounces@listdomain.net On Behalf Of", with "listname" being the name
of the mailing list, followed by the sender's address. She uses Outlook
2003 and sees this as the "from" address, but when the same messages arrive
in a
Hotmail account, the "from" address
is the sender's email address. This behavior is apparently due to the fact
that Mailman creates, among other message headers, a "Sender" header of the form
"Sender: listname-bounces@listdomain". Some email clients, such as Outlook will
place the contents of that "sender" header in the "from" field when they
display the message.
By default, most email clients don't display the message headers, but if you
view the message headers for a message, you will see the "sender" header that
Mailman adds.
Viewing Message Headers in Outlook 2002
explains how to view those headers in Outlook
References:
-
Why do posts appear to be from listname-bounces@mailman.u.washington.edu?
Author: R. Skiver Thompson
August 2004
Frequently Asked Questions About Mailman
-
Viewing Message Headers in Outlook 2002
December 16, 2004
MoonPoint Support
[/network/email/mailing_list/mailman]
permanent link
Sat, Jun 09, 2007 10:04 pm
Email to Mailing List from 65.54.246.86 Rejected
I added a
Hotmail email address
to a mailing list for testing that mailing list. I found that messages
from the Hotmail address were being bounced though, because the
IP address of the sending Hotmail email server, 65.54.246.86, is
in the
Spam and Open-Relay Blocking
System (SORBS) blocklist. SORBS is a
DNS Blacklist (DNSBL).
When I checked the SORBS list, it appeared that the 65.54.246.86
had been there for at least a week due to SORBS detecting spam
orginating from the Hotmail email server at that address.
Database of servers sending to spamtrap addresses
| Address: | 65.54.246.87 |
| Record Created: | Sat Aug 12 12:30:09 2006 GMT |
| Record Updated: | Fri Jun 1 19:30:05 2007 GMT |
| Additional Information: |
[ Updated via: Spam 'o Matic ] Received: from
bay0-omc1-s15.bay0.hotmail.com (bay0-omc1-s15.bay0.hotmail.com [65.54.246.87])
by desperado.sorbs.net (Postfix) with ESMTP id F0C6311466 for <[email]>;
Sat, 02 Jun 2007 05:14:49 +1000 (EST) |
| Currently active and flagged to be published in DNS |
I've been using SORBS as a blocklist for quite awhile, but I have
encountered problems many times due to the fact that AOL, Hotmail, EarthLink,
and email servers from some other large Internet Service Providers (ISPs)
tend to get on the SORBS list frequently and stay there for a long time.
I've contacted AOL and EarthLink support previously when I found one or more
of their email servers were on the SORBS blocklist. I've found that, though
the support personnel with which I communicated understand that their company
employs blocklists or other means of blocking spam, they never seem to
understand that other email providers may employ similar means. I've never been successful in getting the support personnel I've communicated with at AOL or
EarthLink to take any action and usually it doesn't appear that they even
understand the problem; I usually just get canned responses about how to stop
their service from blocking email rather than any response indicating that they
understand the problem is with email going from their systems to other
systems (See
SORBS Blocking AOL and EarthLink Servers and
Report of SORBS listing to EarthLink).
I've found reports by others using SORBS of similar problems with email
from Hotmail addresses (see
Hotmail on sorbs?!?).
I understand that SORBS policy charging server owners to remove systems does
drastically lessen the chances that systems will be removed quickly. I've
considered removing the SORBS list from the blocklists I employ to reduce
the deluge of spam in users' mailboxes, but it does block thousands of spam
messages daily on my server, so I haven't taken that step yet. Usually, I
add the sender's email address to the /etc/mail/access list used
by Sendmail to keep email from particular senders being checked against the
blocklists I employ.
In this case, though, I don't want any email addressed to the mailing list
to be checked against a blocklist to preclude this problem. The Mailman
mailing list software won't allow any email to the mailing list unless the
"from" address is for a member of the mailing list, so I don't need the
additional blocklist check.
Fortunately Sendmail, which is the
software that handles email on the server, does allow you to specify that
email to particular "to" addresses will always be accepted and won't be
checked against DNSBL's. You can allow email to a particular address to
bypass the blocklist checks by editing /etc/mail/access. Place
a line similar to the following in that file:
To:jsmith@example.com OK
The line above would ensure that email addressed to jsmith@example.com
would not be checked against any blocklists employed on the email server.
After editing /etc/mail/access, you need to recreate the access
database with a command similar to the following:
makemap hash /etc/mail/access </etc/mail/access
Once I added the mailing list address, I was able to send email to that
address from the Hotmail account without worrying that the Hotmail email
server used to transmit the messages might be on the SORBS blocklist or
another blocklist I'm employing to limit spam.
References:
-
Spam and Open-Relay Blocking System
-
DNSBL
Wikipedia, the free encyclopedia
-
SORBS Blocking AOL and EarthLink Servers
April 23, 2006
MoonPoint Support
-
Report of SORBS listing to EarthLink
April 23, 2006
MoonPoint Support
-
Hotmail on sorbs?!?
Posted: September 21, 2005
ReadList.com - Threaded Mailing List
Reader
-
Sendmail cf/README - Anti-Spam Configuration Control
sendmail.org
[/network/email/mailing_list]
permanent link
Sat, Jun 09, 2007 5:50 pm
Installing Yum on a RedHat 9 System
For a RedHat Linux 9 system,
I wanted to install
Yum,
which is an automatic updater and package installer/remover for Linux systems
that use
RPMs to manage
installed software.
I checked to see if
Yum was already installed, but it was not installed.
# rpm -qa | grep -i yum
The Yum Download
webpage listed the requirements for the latest version of Yum, version 3.2.0,
as python 2.4+ and rpm 4.3 and above. I checked the version of the python and
rpm packages on the system, but found they were not at the required versions.
# rpm -q --last rpm python
rpm-4.2-0.69 Sat 08 Nov 2003 02:37:24 PM EST
python-2.2.2-26 Sat 08 Nov 2003 02:37:22 PM EST
Instead I needed to get a much earlier version,
2.0.8,
which only required python 2.1+ and rpm 4.1.1-4.3.1. After downloading the rpm
file, I installed it with rpm --install yum-2.0.8-1.noarch.rpm.
I then checked for updates for the system with yum check-update.
An update was available for tcpdump among other utilities. An
rpm -q --last tcpdump command showed the following information for
the version already installed on the system:
tcpdump-3.7.2-1.9.1 Sat 08 Nov 2003 08:39:55 PM EST
I tried updating tcpdump with
yum install tcpdump, but received
the error message below:
# yum install tcpdump
Gathering header information file(s) from server(s)
Server: Red Hat Linux 9 - i386 - Base
Server: Red Hat Linux 9 - Updates
Finding updated packages
Downloading needed headers
Resolving dependencies
Dependencies resolved
I will do the following:
[update: tcpdump 14:3.7.2-7.9.1.i386]
Is this ok [y/N]: y
Downloading Packages
Getting tcpdump-3.7.2-7.9.1.i386.rpm
retrygrab() failed for:
http://mirror.dulug.duke.edu/pub/yum-repository/redhat/updates/9//x86/i386/tcpdump-3.7.2-7.9.1.i386.rpm
Executing failover method
failover: out of servers to try
Error getting file http://mirror.dulug.duke.edu/pub/yum-repository/redhat/updates/9//x86/i386/tcpdump-3.7.2-7.9.1.i386.rpm
[Errno 4] IOError: HTTP Error 404: Not Found
When I checked the Duke University wepage at
http://mirror.dulug.duke.edu/pub/yum-repository/redhat/updates/9/x86/,
I found it had only one file in that directory. So I needed to add another
repository for updates to software for RedHat 9 systems. I found a list of
such sites at
http://fedoralegacy.org/download/fedoralegacy-mirrors.php. Many of those
I checked in the US also no longer had the files available for download. But
the DataPipe one at
http://mirror.datapipe.net/fedoralegacy/ did still have files available.
I added the following line to the updates section of /etc/yum.conf
baseurl=http://mirror.datapipe.net/fedoralegacy/redhat/9/updates/i386/
The yum.conf file now has the following information in it:
[main]
cachedir=/var/cache/yum
debuglevel=2
logfile=/var/log/yum.log
pkgpolicy=newest
distroverpkg=redhat-release
tolerant=1
exactarch=1
[base]
name=Red Hat Linux $releasever - $basearch - Base
baseurl=http://mirror.dulug.duke.edu/pub/yum-repository/redhat/$releasever/$basearch/
[updates]
name=Red Hat Linux $releasever - Updates
baseurl=http://mirror.dulug.duke.edu/pub/yum-repository/redhat/updates/$releasever/
baseurl=http://mirror.datapipe.net/fedoralegacy/redhat/9/updates/i386/
I then ran yum install tcpdump again and this time was able
to update tcpdump. Checking the version of the rpm installed afterwards,
I saw the following:
# rpm -q --last tcpdump
tcpdump-3.7.2-7.9.4.legacy Sat 09 Jun 2007 05:08:22 PM EDT
References:
-
Yellow Dog Updater (YUM)
Linux@DUKE
-
RPM Package
Manager
Wikipedia, the free encyclopedia
-
RedHat 9 Updates - Using Fedora Legacy
-
Mirror sites by country
The Fedora Legacy Project
[/os/unix/linux/sysmgmt]
permanent link
Thu, Jun 07, 2007 9:01 pm
Skipping Download of Large Email Messages
An Apple eMAC user told me he had been waiting for over an hour to download
his email with no new messages yet appearing in his inbox of the 21 new messages
on the server. When I checked the email server, I did not see any problems
there, but did notice a lot of bandwidth to the server was being used by
a
POP3 connection
from the user's site.
POP3 is a
protocol used to download email. When I checked his mailbox, I found that the
first new message was over 90 MB, which was the source of the problem.
On an Apple system running the OS-X operating system, you can configure
the Mail program to prompt before downloading messages that are above
a specified size. To do so, take the following steps:
- Open the Mail program.
- Click on Mail on the program's menubar.
- Select Preferences.
- Click on the Advanced tab.
- Place a value in the "Prompt me to skip messages over [ ] KB" field.
E.g. to skip messages over 50 MB in size you could put 51200 in the
field (50 megabytes x 1024 kilobytes/megabyte = 51,200 KB).
- You can then close the Preferences window choosing Save
when prompted as to whether you wish to save the changes you have made.
[/os/os-x]
permanent link
Wed, Jun 06, 2007 9:03 pm
Backing Up a Specific Filetype with Tar
To backup a specific filetype, e.g. all
PHP
files in the current directory and all subdirectories beneath it,
you can use the following command:
tar -cvf example.tar $(find . -name "*.php")
The find command will find all of the PHP files and pass them to
the tar command. You can see that all of the PHP files are in the
tar backup file, example.tar with the command below:
tar -tvf example.tar
You can add HTML
files to the backup using the -u option for tar to update the
archive file as below:
tar -uvf example.tar $(find . -name "*.html")
References:
-
tar find ssh
May 2004
Computing.Net
[/os/unix/commands]
permanent link
Wed, May 30, 2007 5:39 pm
Checking on Whether a Remote System is an Oracle Server
Nmap can be used to determine if
a system is functioning as an Oracle server using the command
nmap -p 1521 -P0 -sT <ip_address>.
Port 1521 is a port used by
Oracle server software, but the port may also be used by other software,
so, if nmap reports the system is listening on that port, it does not
guarantee that the system is an Oracle server.
The options specified above are as follows:
-p <port ranges>
This option specifies what ports you want to query.
-P0 Do not try and ping hosts at all before scanning them. This
allows the scanning of networks that don't allow ICMP echo
requests (or responses) through their firewall.
-sT TCP connect() scan: This is the most basic form of TCP scanning.
The connect() system call provided by your operating system is
used to open a connection to every interesting port on the
machine. If the port is listening, connect() will succeed,
otherwise the port isn't reachable. One strong advantage to this
technique is that you don/t need any special privileges. Any
user on most UNIX boxes is free to use this call.
For a list of other ports used by Oracle, you can check
Which TCP/UDP port or ports does 'oracle' use?
References:
-
Which TCP/UDP port or ports does 'oracle' use?
SecureTrust TCP/UDP Port Search Lookup Tool
[/network/Internet/IP/ports]
permanent link
Wed, May 30, 2007 3:28 pm
List-Update Script
Every month I receive a spreadsheet with a list of members in a retirees'
organization. I extract the column in the spreadsheet containing the
email addresses to a text file on a PC and then transfer it to a Solaris
server that handles email addressed to the mailing list. I've been manually
processing the text file each month to remove blank email addresses, duplicates,
and invalid email addresses. At lunch today, I wrote a small
BASH script,
list-update
to automate the process.
Since I don't use sed often,
but sometimes need to use it to delete blank lines, such as the many that
occur in the membership list, I thought I would put a note to myself here
on the syntax for the sed command to remove blank lines from a file:
cat filename | sed -e '/^$/d' > newfilename
[/os/unix/programs/utilities]
permanent link
Tue, May 29, 2007 10:32 am
Commerce Bank Phishing Email
When I checked my email today, I found a
phishing email that ostensibly pointed recipients to
http://commerceconnections-session843435953.commercebank.com/ibank/cmserver/verify.cfm, but which actually pointed to a phishing webpage at
http://commerceconnections-session843435953.commercebank.com.plosure.at/ibank/cmserver/verify.cfm/
I reported the spoofed site at the
following phishing report wepbages:
[/security/scams/phishing/commercebank]
permanent link
Sat, May 26, 2007 12:44 pm
Netscape 7.2 Inbox Corrupted
A user who uses Netscape 7.2 for email reported to me that whenever he clicked on
any message in his inbox, the same old message would be displayed instead of
the contents of the message matching the one he clicked on. He also told
me he could not move messages from his inbox to another mailbox.
I corrected the problem by deleting the inbox.msf file for his account.
The inbox.msf file indexes the messages in the inbox.
The inbox.msf file can be found at the following location:
C:\Documents and Settings\<userid>\Application Data\Mozilla\Profiles\<account_name>\7q0bwoem.slt\Mail\<email_server>
userid |
the userid under which the user logged into the system |
account_name |
the name associated with the user's account |
email_server |
the email server for the mailbox, usually an
ISP provided email server
|
In this case, that directory was similar to the following:
C:\Documents and Settings\jsmith\Application Data\Mozilla\Profiles\Joseph M. Smith\7q0bwoem.slt\Mail\jmsmith.com
Netscape should be closed when you delete the inbox.msf file. After I deleted
the file and reopened Netscape, it took quite a while before the contents of
the inbox were visible in Netscape again. The user had a large 2 GB inbox with
1,462 messages in it (I have about 38,000 in my own inbox) and it apparently
took quite some time to rebuild the index file for all of those messages. I had
to wait over 15 minutes before Netscape displayed the list of messages in the
inbox. The inbox.msf file was appearing as 0 bytes in size during that process.
After the inbox.msf file was rebuilt, I right-clicked on "inbox" in Netscape
and chose "compact this folder", which also took a long time to complete,
because of the size of the inbox.
References:
-
Netscape 7.0 mail corrupt
inbox, need to delete?
Posted: August 21, 2006
SillyDog701 Message Centre
[/network/email/clients/netscape]
permanent link
Sun, May 20, 2007 11:30 pm
Mailman Not Sending Welcome Message
I'm using
Mailman, the
GNU Mailing List Manager for a new mailing list. After creating a new mailing
list through the web interface for mailman, I created aliases in
/etc/aliases, which are shown below, for the list and ran the
command
newaliases.
## book_nook mailing list
book_nook: "|/var/mailman/mail/mailman post book_nook"
book_nook-admin: "|/var/mailman/mail/mailman admin book_nook"
book_nook-bounces: "|/var/mailman/mail/mailman bounces book_nook"
book_nook-confirm: "|/var/mailman/mail/mailman confirm book_nook"
book_nook-join: "|/var/mailman/mail/mailman join book_nook"
book_nook-leave: "|/var/mailman/mail/mailman leave book_nook"
book_nook-owner: "|/var/mailman/mail/mailman owner book_nook"
book_nook-request: "|/var/mailman/mail/mailman request book_nook"
book_nook-subscribe: "|/var/mailman/mail/mailman subscribe book_nook"
book_nook-unsubscribe: "|/var/mailman/mail/mailman unsubscribe book_nook"
I then added an email address to the list with the option to send a welcome
message checked. But the welcome message was never sent. After doing a little
checking, I discovered I needed to create a crontab entry for mailman
1
.
On my RedHat Linux system, the file to be submitted for the cronjob is
/var/mailman/cron/crontab.in, but may be in
/usr/local/mailman/cron on other systems
2
At the end of the crontab.in file, I saw the following lines:
# At 3:27am every night, regenerate the gzip'd archive file. Only
# turn this on if the internal archiver is used and
# GZIP_ARCHIVE_TXT_FILES is false in mm_cfg.py
27 3 * * * /usr/bin/python -S /var/mailman/cron/nightly_gzip
There was no GZIP_ARCHIVE_TXT_FILES entry in
/var/mailman/Mailman/mm_cfg.py, so I commented out the entry in
crontab.in. Since I don't need to gate news from a news server to mail,
I also commented out the entry for that function by putting a "#" in front of
it.
# Every 5 mins, try to gate news to mail. You can comment this one out
# if you don't want to allow gating, or don't have any going on right now,
# or want to exclusively use a callback strategy instead of polling.
0,5,10,15,20,25,30,35,40,45,50,55 * * * * /usr/bin/python -S /var/mailman/cron/gate_news
I then submitted the cronjob for mailman with
crontab -u mailman /var/mailman/cron/crontab.in.
References:
-
[Mailman-Users] Not sending password reminders, subscription confirmations
By Helmut Schneider
July 13, 2006
mail.python.org Mailing Lists
-
Mailman - a mailing list manager
The FreeBSD Diary
[/network/email/mailing_list/mailman]
permanent link
Wed, May 16, 2007 9:57 pm
htDig Invalid Comptype
I ran
ht://Dig to index the site
today using the command
/usr/bin/rundig -c /etc/htdig_support.conf
>>/var/log/htdig 2>&1, but when I performed htdig searches
of the site after the indexing process completed, which took a considerable
amount of time, none of the searches returned any results. When I checked
the output file for the rundig command,
/var/log/htdig, I saw
the errors below:
# cat /var/log/htdig
FATAL ERROR:Compressor::get_vals invalid comptype
FATAL ERROR at file:WordBitCompress.cc line:827 !!!
/usr/bin/rundig: line 36: 23767 Segmentation fault $BINDIR/htdig -i $opts $
stats $alt
/usr/bin/rundig: line 81: 24766 Segmentation fault /usr/bin/htfuzzy $opts m
etaphone
/usr/bin/rundig: line 82: 24767 Segmentation fault /usr/bin/htfuzzy $opts s
oundex
I found some references to others encountering the same error message when
I performed a
Google search, but didn't
see anything that I felt would give me an appropriate fix for my system.
Some of the references seemed to indicate the problem occurred when htdig
was indexing an enormous number of files. But there are only a few hundred
files for it to index on my site, so I didn't think the number of files
should be the cause of the problem. However, htdig had been indexing pages
in my
Blosxom blog several times,
because of my use of the
Find plugin for
Blosxom.
I included a search feature on each page of the blog that uses
Fletcher Penney's find plugin to allow a search of the blog for information.
Underneath the search box there is an "Advanced Search" link that provides
more advanced search capabilities. Clicking on it will display the same blog
page as was visible before, but with advanced search options visible. This
was resulting in ht://Dig returning the same page multiple times whenever
I used it to search the entire site (the Find plugin only searches the blog
while I have htdig search the entire site).
I thought I might reduce the extraneous results for htdig queries, reduce
the time to index the site when running rundig, and possibly elimininate the
"FATAL ERROR:Compressor::get_vals invalid comptype" error message by having
htdig exclude the "Advanced Search" links when indexing the site. Since
that link on pages always includes "advanced_search=1" in the link URL, I
edited the htdig configuration file for the website, which is
/etc/htdig_support.conf in this case, and added "advanced_search=1"
to the exclude_urls list. So I now have the following line in
that conf file (the "/cgi-bin/ .cgi" was there by default):
exclude_urls: /cgi-bin/ .cgi advanced_search=1
I also added some file extensions to the list of filetypes htdig should
exclude from its indexing process. I added ".mp3 .img .iso .dat .dll .scr"
to the bad_extensions section, so I now have the following in that
list:
bad_extensions: .wav .gz .z .sit .au .zip .tar .hqx .exe .com .gif \
.jpg .jpeg .aiff .class .map .ram .tgz .bin .rpm .mpg .mov .avi .css \
.cab .png .rar .mp3 .img .iso .dat .dll .scr
There is no need for htdig to index binary files. It will only take more
time for htdig to index the site if they aren't excluded and greatly increase
the changes htdig will fail while indexing the site. If you store other types
of music or movie files on a site, you should add them to the
bad_extensions list, if you use htdig.
When I reran rundig with the command
/usr/bin/rundig -c /etc/htdig_support.conf >/var/log/htdig 2>&1,
it did not fail this time and when I performed htdig searches of the site, I
didn't get results returned that were duplicates due to the Blosxom Find
plugin's "Advanced Search" links.
References:
-
RE: [htdig] Segfault indexing a site with 3.2.0b2
May 23 2000
ht://Dig 3.x list archive
-
Error in zlib Compressor for WordDB
July 30, 2002
web.htdig.devel
-
FindPlugin
Author: Fletcher T. Penney
[/network/web/tools/search]
permanent link
Sat, May 12, 2007 9:46 pm
Configuring Exchange to Check a POP3 Account
If you need to configure Microsoft Exchange on a Microsoft Small Business
Server (SBS) 2003 system to pull email from a user's
POP3 account to her
Exchange account, you can take the following steps:
- Click on Start.
- Select All Programs.
- Select Microsoft Exchange.
- Select System Manager.
- Click on the "+" to the left of Connectors to expand
the list of connectors.
- Right-click on POP3 Connector Manager and select
Properties.
- Click on the Add button.
- Complete the fields in the POP3 Mailbox window.
| E-mail server | The address of the POP3 email server, e.g.
example.com |
| Port | Most POP3 servers listen on
TCP port 110,
so in most cases you would have no need to change the default value of 110 |
| User name | The user name on the POP3 server. | .
| Password | The password of the user account on the POP3 server. |
| Confirm Password | The password of the user account on the POP3
server. |
| Log on using Secure Password Authentication |
Specifies whether to log on using encrypted authentication credentials each
time the Microsoft Connector for POP3 Mailboxes downloads POP3 e-mail.
Some ISPs require that you use Secure Password Authentication (SPA). It is
recommended that you select this option if your ISP supports it but does not
require you use it.
|
| Mailbox type | For a mailbox that holds an individual's email,
the mailbox type should be "User Mailbox" |
| Exchange mailbox | The user's exhange mailbox |
- Click on OK.
- Click on the Schduling tab.

- The default check interval is once per hour. You can make that more
frequent, e.g. 0 hours and 15 minutes to check every 15 minutes,
which is the most frequent interval allowed.
- Click on OK again to close the POP3 Connector Manager
Properties window.
- Click on File then Exit to exit the System
Manager window.
References:
-
Connecting Microsoft
Exchange Server to a POP3 Account
Updated: September 6, 2006
Slipstick Systems
-
Microsoft Exchange Connector for POP3 Mailboxes
For Small Business Server 4.5
Updated: May 1, 2001
Microsoft Corporation
[/network/email/exchange]
permanent link
Thu, May 10, 2007 8:57 pm
Dell Precision 380 WOL
I needed to set up a Dell Precision 380 for
Wake on LAN (WOL)
support. To check the network adapter's support for the feature within
Windows, you can take the following steps.
- Click on Start.
- Click on Settings (This step doesn't apply under Windows Vista).
- Select Control Panel.
- Double-click on System.
- Click on the Hardware tab (This step doesn't apply under
Windows Vista).
- Click on Device Manager.
- Click on the "+" to the left of Network Adapters
- Select the relevant network adapter by right-clicking on it
and choosing Properties.
- Click on the Advanced tab.
In this case the system has a Broadcom NetXtreme 57xx Gigabit Controller.
I clicked on
Wake Up Capabilities and saw the value was "Both"
meaning it supports a wakeup call using a
"
Magic Packet
" or a "Wake Up Frame". I then clicked on the
Power Management
tab. "Allow the computer to turn off this device to save power" was not
checked, so I didn't need to worry about "Allow this device to bring the
computer out of standby" being unchecked.
You also need to set the system's BIOS to support WOL. To do so, take
the following steps, which are specific to the Dell Precision 380's BIOS.
- Reboot the system and, as soon as the system begings to reboot, hit
the F2 key to go into the BIOS Setup.
- Use the cursor key to go down to Power Management and hit the
Enter key to view the options within it.
- Go down to "Remote Wake Up" and hit the Enter key.
- Use the right cursor key to move to the On button, which
should turn green. The factory default setting is Off.
- Hit the Enter key.
- Hit the Esc key to exit Setup.
- Use the tab or right cursor key to choose Save/Exit and hit
the Enter key to reboot.
Before the system boots, you can power it off and, from another system, use
a program that can send a magic packet to the system, such as
mc-wol to wake it up.
[/network/wol]
permanent link
Mon, May 07, 2007 5:21 pm
Mboxgrep Installation on Solaris 7
I installed mboxgrep on a system running SunOS 5.7 today. I encountered
some minor problems last year when I installed the software on a
Solaris 10 system (see
Mboxgrep Installation on Solaris 10), but no problems at all
with the installation this time. After unzipping and untarring the file I
downloaded from freshmeat.net at
http://freshmeat.net/projects/mboxgrep/, I changed my working directory
to the one holding the mboxgrep files and issued the following commands:
./configure
make
make install
I needed to find all email messages in my inbox with the phrase "subnet by
subnet", so I issued the following command:
mboxgrep -o subnetinfo "subnet by subnet" /var/mail/jimc
The -o mailboxname creates an output file with the name
mailboxname.
[/os/unix/solaris]
permanent link
Sun, May 06, 2007 4:57 pm
Activity Monitor Detection
When I scanned a system that had the monitoring portion of Activity
Monitor installed, i.e. the system was the one doing the monitoring,
with various antivirus and antispyware programs,
Spybot Search & Destroy and
Windows Defender reported its presence.
[
More Info ]
[/os/windows/software/security/monitoring/activity_monitor]
permanent link
Sat, May 05, 2007 10:30 pm
Opening One Form in Access from a Field in Another Form
I had two tables in a database, one called "HDD", which holds information
on hard disk drives, such as serial number, model number, capapcity, etc.
I had another table I called "External", which I use to keep track of
information regarding external disk drive enclosures I use for backing up
systems. That External database also has a "Drive SN" field that has the
serial number for the hard disk drive within the enclosure. I created forms
with matching names for each table, i.e. an "HDD" and "External" form.
I wanted to be able to double-click on the drive serial number in the "External"
form and have the "HDD" form open with the record displayed with the
corresponding serial number, so that I could view all of the information on
the particular hard disk drive within the drive enclosure that I had selected
in the "External" form. I used the following procedure to be able to do so.
- In the drive serial number field of the "external" form, I right-clicked
and chose Properties.
- Scrolled down to the "On Dbl Click" field.
- I clicked on the button with "..." on it.
- I chose Macro Builder and clicked on OK.
- I gave it a name of OpenHDD and clicked on OK.
- For Action, I chose OpenForm.
- In the Form Name field, I put in HDD, the name of
the form that displays information on the hard disk drives.
- For View, I selected Form.
- For Where Condition, I clicked on the "..." button and chose
Tables then the HDD table beneath it.
- I then selected Serial Number in the next column and
double-clicked on <Value> in the last column, which gave me
[HDD]![Serial Number] in the Expression Builder
field.
- I then clicked on the equal button to add
= at the end of the
expression and then added Forms![External]![Serial Number] giving me
[HDD]![Serial Number] = Forms![External]![Drive SN] .
- I then clicked on OK
- For the Comment field, which is to the right of the Action
field, I put "Open HDD form to drive corresponding to External drive SN"
- I then closed the Expression Builder window, saving the macro.
- I then closed the Properties window that was open for the Drive
SN field.
I was then able to click on the drive serial number field in the External
form and have the HDD form open displaying the information
on the hard disk drive within the enclosure.
[/software/database/access]
permanent link
Thu, May 03, 2007 8:12 pm
Sharing Files Between a Microsoft Windows and Apple OS-X System
To allow selected Windows users access to shared folders on an Apple OS-X
system using
SMB/CIFS, which is the mechanism Windows systems use to share
resources such as folders and printrs, take the following steps:
- Click on the Apple icon on the top left hand corner of the screen, which
will display a menu of options.
- Select System Preferences
- Under the Internet & Network grouping, click on Sharing
- Click on the lock icon at the bottom left-hand side of the sreen to
make changes, if the lock is in the locked position.
- Click on Windows Sharing, which is under the Services
section, so that it has a checkmark next to it.
- Click on the Enable Accounts button.
- Select the accounts for which you wish to provide access by clicking on
them, so that there is a checkmark in the "on" column for those accounts
that should be able to access the system through "Windows Sharing".
You will be prompted to enter the password for each account for which you have
enabled this access.
- Click on the Done button.
- Close the window by clicking on the "X" in the upper left-hand corner
of the window.
[/os/os-x]
permanent link
Thu, May 03, 2007 7:31 pm
Opening a Terminal Window on OS-X
To open a terminal window, i.e. to obtain a shell prompt, take the
following steps from the desktop:
- Double-click on Macintosh HD
- Double-click on the Applications folder.
- Double-click on the Utilities folder.
- Double-click on Terminal.
[/os/os-x]
permanent link
Thu, May 03, 2007 7:21 pm
SSH Access to an OS X System
To allow SSH access to an Apple OS X system take the following steps:
- Click on the Apple icon on the top left hand corner of the screen, which
will display a menu of options.
- Select System Preferences
- Under the Internet & Network grouping, click on Sharing
- Click on Remote Login, which is under the Services
section.
- Close the window by clicking on the "X" in the upper left-hand corner
of the window.
When logging in by
SSH, use
the "short name" for the account, which can be found by going to
System Preferences,
Accounts, then clicking on the
lock icon, and then selecting the account.
[/os/os-x]
permanent link
Thu, May 03, 2007 7:20 pm
Adding a New Account to an OS-X System
To add a new account to an Apple OS-X system take the following steps:
- Click on the Apple icon on the top left hand corner of the screen, which
will display a menu of options.
- Select System Preferences
- Under the System grouping, click on Accounts
- Click on the lock icon at the lower left-hand corner of the window.
- When prompted for an administrator's name and password type those in
the relevant fields.
- Click on the plus sign, i.e. the "+" above the now open lock icon.
- Provide a name in the name field, e.g. John Smith and then a
short name, e.g. john (you will use the short name if logging in
by SSH). Then put in the password and retype the same password in the Verify
field. Click on the "Allow user to administer this computer", if the
person should have administrative privileges on the system.
- Click on the Create Account button.
- Close the window by clicking on the "X" in the upper left-hand corner
of the window.
[/os/os-x]
permanent link
Thu, May 03, 2007 7:01 pm
Changing the System Name of an OS X System
To change the system name of an Apple OS X system take the following steps:
- Click on the Apple icon on the top left hand corner of the screen, which
will display a menu of options.
- Select System Preferences
- Under the Internet & Network grouping, click on Sharing
- Type the computer name you wish to use in the Computer Name field.
- Close the window by clicking on the "X" in the upper left-hand corner
of the window.
[/os/os-x]
permanent link
Mon, Apr 30, 2007 11:13 pm
Charlene Infection
After a user complained of popup windows advising her to download
antivirus software, I checked the system with
Spybot Search & Destroy.
Spybot found the following malware on the system:
FunWeb
FunWebProducts
MyWay.MyWebSearch
MyWebSearch
TagASaurus
Zlob.VideoAccessActiveXObject
I also found that the popup ad was appearing whenever Internet Explorer was
opened. When Interenet Explorer was opened it would go immediately to
http://aprotectservice.com/, which
would result in a dubious W32.Myzor.FK@yf virus warning appearing.
[ More Info ]
[/security/spyware/funwebproducts]
permanent link
Mon, Apr 30, 2007 12:38 am
Remotely Enabling Remote Desktop Protocol
If you need to enable Remote Desktop support on a system in a
domain from the domain controller, you can do it by editing
the
HKLM\SYSTEM\CurrentControlSet\Control\Terminal Server
key in the registry of the remote system. By changing the
value of
fDenyTSConnection from 1 to 0 and
then rebooting the system, you can enable Remote Desktop
support.
[
More Info ]
[/os/windows/software/remote-control/rdp]
permanent link
Sun, Apr 29, 2007 9:30 pm
Updating NVIDIA Driver Fixed GoPets and Second Life Problem
When I updated the driver for the NVIDIA GeForce 6150 LE video adapter
in a Windows XP PC earlier today from version 8.2.08 (driver date:
5/9/2006) to version 6.14.10.9371 (driver date: 10/22/2006),
the update corrected a problem with
GoPets and a problem with
Second
Life.
A family member has many fruit trees on GoPets from which she harvests
fruit regularly. However, whenever she put the fruit in her inventory,
GoPets would randomly crash. Sometimes it would crash after she put only
1 piece of fruit in her inventory. At other times, she could put 3 or 4
pieces of fruit in her inventory before it crashed. And sometimes even 10 or
more pieces of fruit in her inventory. Upgrading the driver for the NVIDIA
video card stopped those crashes altogether.
When she was in Second Life, her avatar would continually turn to the right,
as if she was clicking the arrow to turn to the right. The only way she
could stop the behavior was to switch to full-screen mode, which she
preferred not to do. Updating the video driver resolved that problem, also.
For anyone experiencing either problem, you can check the version of the
driver for the video adapter in your system by the following steps on a
Windows XP system:
- Click on Start.
- Click on Settings. If you don't see Settings,
look for Control Panel instead.
- Click on Control Panel.
- Within the Control Panel, double-click on System.
- Click on the Hardware tab.
- Click on the Device Manager button.
- Double-click on Display Adapters to expand the list of
display adapters.
- Right-click on a display adapter (for most systems there will be only 1)
and choose Properties.
- Click on the Driver tab. You should then see the driver
provider, driver date, and driver version listed.
- You can then click on Cancel and close the window.
If you are experiencing any of the above problems a driver update may help.
If your system has an NVIDIA adapter, you can get the latest drvier from
the NVIDIA
software download webpage.
[/os/windows/software/games]
permanent link
Sun, Apr 29, 2007 3:31 pm
GoPets and Second Life Won't Run After Nvidia Hardware Acceleration Turned Off
I turned off hardware acceleration for an Nvidia GeForce 6150 LE
video adapter in a Windows XP Media Center PC, but then the family member using
the system found that neither GoPets nor Second Life would start.
For
GoPets, the following
window appeared.
| Initialize Error |
Your video card could not support the requested 3D function.
This error may occur if your video card is not supported by GoPets.
Please view the Download page at the GoPets website for a list of
unsupported video cards.
OK
|
When she clicked on OK, another error window appeared.
| Error |
 Failed to
initialize the rendering engine.: 0 Failed to
initialize the rendering engine.: 0
OK
|
Clicking OK on that window closed the
application.
When she started Second Life
the message "detecting hardware" appeared followed by the error
window below.
| Error |
Second Life is unable to run because your video card drivers
are out of date or unsupported. Please make sure you have
the latest video card drivers installed.
If you continue to receive this message, contact customer service.
OK
|
I had turned video acceleration off for the Nvidia graphics adapter
when Paint Shop Pro 9 would not start with it turned on. To turn
it back on I tried the following steps.
- Right-click on desktop.
- Select Properties.
- Click on Settings.
- Click on the Advanced button.
But then the following message appeared.
| NVIDIA Display |
The NVIDIA Display Panel extension cannot be created.
Possible reasons include:
Disabled graphics hardware acceleration. To enable Hardware
Acceleration:
- Right click on your desktop, select Properties, the Settings
tab, and click Advanced.
- Click the Troubleshoot tab and move the 'Hardware
acceleration' slider all the way to Full.
- Click OK.
- If prompted, restart your computer.
OK
|
I clicked on the Troubleshoot tab instead, clicked
on the hardware acceleration slider and dragged it down
to the "Full" end. GoPets and Second Life then started
when I tried to open them. Paint Shop Pro 9 wouldn't
start again, though. It hung while starting up (see
Paint Shop Pro Hangs at Startup).
I checked the version of the driver installed for the
NVIDIA GeForce 6150 LE through the device manager.
I saw the following.
| Driver Provider: | NVIDIA |
| Driver Date: | 5/9/2006 |
| Driver Version: | 8.2.0.8 |
| Digital Signer: | Microsoft Windows Hardware Compatibility
Publisher |
I went to the NVIDIA
software download page. I didn't find a driver listed specifically for
the NVIDIA GeForce 6150 LE adapter, but I found that the GeForce 6 Series
driver supports the GeForce 6150 LE adapter.
The "Driver Installation Hints" for the new driver stated the following.
Before installing new drivers make sure you uninstall all NVIDIA display drivers
from the Windows Control Panel. Browse to the Start Menu > Windows Control Panel >
Add/Remove Programs and search for "NVIDIA Windows Display Drivers" or "NVIDIA
Display Drivers" and select remove.
I removed the existing NVIDIA drivers through "Add or Remove Programs".
I chose to "Remove all NVIDIA drivers, including Display". I also opted
to remove the nView profiles. After rebooting, GoPets, Second Life, and
Paint Shop Pro 9 all started without problems.
[/os/windows/software/games]
permanent link
Sat, Apr 28, 2007 1:30 pm
Removing the Arrow from Windows Shortcuts
If you want to remove the arrow that appears on Windows shortcuts,
you can do so by using the following procedure.
- Click on Start.
- Select Run.
- Type regedit
- Click on Ok.
- Navigate to HKEY_CLASSES_ROOT\lnkfile.
- On the right side of the window, right-click on IsShortcut and
choose Delete.
Remember, you must be careful when editing the registry. Mistakes in
editing registry entries can cause significant problems.
As an alternative to the above method, you can use this
shortcut-arrow-removal.reg registry file,
which will delete the IsShortcut key from the registry. Download the
file (you can right-click on the link and choose "download", "save
link target as", or whatever your browser ues to initiate a download)
and then, once it is downloaded, double-click on the file on your system.
When prompted "Are you sure you
want to add the information in shortcut-arrow-removal.reg to the
registry?", select "Yes". That action will result in the key being
removed; the prompt about adding information is just the default
message that appears whenever you click on a
.reg file.
References:
-
Remove shortcut arrow from desktop icons
Free PC Tech Support -
Guides and FAQs
[/os/windows/registry]
permanent link
Sat, Apr 28, 2007 12:33 pm
Problem Uninstalling Starddock Central Applications
A family member uninstalled
StarDock
Central, but then found the files for the software were still under
C:\Program Files and the applications, such as WindowBlinds,
which are part of the software, still seemed to be active on the system.
I suggested reinstalling StardDock Central and then uninstalling the various
modules, such as WindowBlinds from within it. After reinstalling StarDock
Central and then opening StarDock Central, right-clicking on the various
packages and choosing "uninstall" would not uninstall the packages.
Trying to uninstall IconPackager produced the message below.
| Stardock Central |
There has been an error uninstalling IconPackager. Would you like to set the
item as uninstalled?
Yes
No
|
Trying to uninstall WindowBlinds produced a similar message
| Stardock Central |
There has been an error uninstalling WindowBlinds4. Would you like to set the
item as uninstalled?
Yes
No
|
On one of the StarDock Forums, there
was a posting
Uninstall Problem Gives me an error where someone reported a problem
uninstalling WindowBlinds to which a respondent suggested running a "zapper"
program from StarDock to uninstall StarDock applications. The
ODNT Component
Zapper is available from
Downloads at the Stardock site.
Stardock describes it as a "Utility program that can be used to unload or
remove Object Desktop components (like if an install.log file is missing). Warning:
this will delete any installed skins/themes for the component when used to
uninstall that component."
I ran the program and chose "Select All" to remove all Object Desktop
components.
A window popped up showing the applications to be removed, but the list
was so long I couldn't see the buttons at the bottom and there was no
scrollbar. But, since the default response button was "Yes", hitting
the enter key resulted in an attempt to zap the programs, but then
I saw "odnt_zapper.exe has encountered a problem and needs to close.
We are sorry for any inconvenience." However when I restarted the ODNT
Component Zapper, I didn't see any applications listed to remove this
time under the Uninstall tab. But under the Unload tab,
I saw WebBlinds listed. I chose to unload it by selecting
it and then clicking on Apply.
I then clicked on Start, Control Panel, and then
Add or Remove Programs, chose Stardock Central,
and then Change/Remove to remove it from the system.
The C:\Program Files\Stardock folder remained, so I
attempted to manually delete it.
When I tried deleting it, I saw the message "Renaming, moving or
deleting 'Stardock' could make some programs not work. Are you
sure you want to do this?" I chose "No" and rebooted, thinking
perhaps a DLL
file associated with the program might still be loaded in memory.
I got the same message after rebooting when I tried uninstalling
it again, but this time I chose "Yes" to proceed with the
uninstall
-
Uninstall Problem Gives
me an error
By kid4christ
Posted December 10, 2005
Stardock Forums
[/os/windows/software/themes]
permanent link
Fri, Apr 27, 2007 9:16 pm
Paint Shop Pro Hangs at Startup
Whenever I attempted to start PaintShop Pro 9 on a Windows XP system,
the program would hang at startup. When I tried to uninstall it, the
uninstall routine hung as well. I finally resolved the problem by
disabling hardware acceleration for the Nvidia video adapter in the system,
though updating the driver for the video card may resolve the
problem as well [Update: that is probably the better alternative, since
turning off hardware acceleration may create problems for other programs
as noted in
GoPets and Second Life Won't Run After Nvidia Hardware
Acceleration Turned off]
[ More
Info ]
[/os/windows/software/graphics/corel/psp]
permanent link
Thu, Apr 26, 2007 8:58 pm
Add Notification Sounds to SquirrelMail
To add additional notification sounds that a user can select to have played
when she receives new email, place the
wav
file you wish to add in
/usr/share/squirrelmail/plugins/newmail/sounds.
You've Got Mail Wav File
[/network/email/squirrelmail]
permanent link
Mon, Apr 23, 2007 9:00 pm
PayPal Phishing Page at Hong Kong University Removed
When I checked agin, I found the PayPal phishing page that was located
on a webserver at the Hong Kong Polytechnic University this weekend was
now gone.
[/security/scams/phishing/paypal]
permanent link
Mon, Apr 23, 2007 6:42 pm
Adding an Account to the Administrator Group
Sometimes you may need to add an account to the Administrator group
temporarily to install software that otherwise won't run from a
normal users account. Perhaps the software can be made to run if
you can determine all of the files and registry keys it needs to
access and provide the appropriate permissions on those, but
sometimes the most reasonable course is just to reinstall the software
from a user account after adding the user to the administrator group
temporarily and then remove the user account afterwards.
To do so on Windows XP system, e.g a Windows XP Home or Media Center
Edition system, take the following steps:
- Log into the system as the administrator.
- Click on Start.
- Click on Control Panel.
- Double-click on User Accounts.
- Double-click on the account to which you wish to grant administrator
access.
- Click on Change the account type.
- Change the account type from Limited to Computer
Administrator.
- Click on the Change Account Type button.
- Logoff as administrator and logon under the user account.
You can then follow the same procedure after you have installed the
software to change the account type back to Limited.
[/os/windows/xp]
permanent link
Sun, Apr 22, 2007 2:59 pm
PayPal Phishing at Hong Kong Polytechnic University
When I checked to see if the spoofed
PayPal webpages were still present at
http://production.mic.polyu.edu.hk/pp/login.html, I found the pages
were still accessible. Yesterday, someone forwarded a message to me
which stated an email address had been added to his PayPal account. The
message asked him to confirm the addition by going to a PayPal website, but
the link in the message actually led to the server at the Media Innovation
Centre in the School of Design at the Hong Kong Polytechnic University.
The recipient doesn't have a PayPal account. Whoever created the spam
message probably sent it to thousands of people with no way of knowing
how many of those recipients might have PayPal accounts.
I checked the online directory for the university today and sent another
message regarding the spoofed site; this time I sent the message to
the chair of the School of Design at the
university plus email addresses for people who appeared to be IT people at
the university, and some general contact addresses. Hopefully, one of them
can get the spoofed webpages removed and take action that will result in
the perpetrator being apprehended and disciplined.
[/security/scams/phishing/paypal]
permanent link
Sat, Apr 21, 2007 8:15 pm
PayPal Phishing at a Hong Kong University
A user forwarded an email message to me today that attempts to lure
gullible
PayPal users to a website
at a university in Hong Kong. The email message asked the recipient to
verify the addition of an email address to his PayPal account by going
to the PayPal website. But the link actually directed anyone who clicked
on it to
http://production.mic.polyu.edu.hk/pp/login.html. The "hk" at the end
of the domain name indicates the site is in Hong Kong, since "hk" is the
country code for Hong Kong. The "edu" before it indicates it is an
educational institution.
Going to http://mic.polyu.edu.hk/
instead, I found the following information for the site:

I reported the spoofed site to to the contact address listed for the Hong Kong
Polytechnic University.
The webserver being used to host the spoofed PayPal site apparently
belongs to the Multimedia Innovation Centre School of Design at that university.
I also reported this
phishing
attempt to PayPal via the PayPal
Report Fake Site/Spoofwebpage.
And I reported the spoofed site at the
following phishing report wepbages:
[/security/scams/phishing/paypal]
permanent link
Tue, Apr 17, 2007 9:50 pm
Attachment Sizes for Free Email Services
Google offers a free email service
Gmail. Google offers up to 2,500 MB (2 GB)
of storage for Gmail accounts. With that service attachments
can be up to 10 MB in size. I have successfully sent a message with a 10 MB
attachment to a test Gmail account I maintain. It is possible that
a message with an attachment that is somewhat less than 10 MB might not
be delivered, though. Google states the following in regards to attachment
size for messages from/to Gmail accounts:
With Gmail, you can send and receive messages up to 10 megabytes (MB) in size.
However, the precise amount allowable will depend on the attachment.
When you add an attachment, the size of a file may increase because transport
encodings are automatically added. (Transport encodings are the information
that allows your message to be safely sent and read.)
This means that in some cases, attachments that are 6 to 10MB in size may push
the total message size above 10MB. When this happens, Gmail displays a warning
that your message exceeds the 10MB limit.
Microsoft offers a free email service
Hotmail, which provides 1,000 MB (1 GB)
of free storage for email. That service currently has a 10 MB limit on
attachments. I have successfully sent a message with a 10 MB attachment to
a test Hotmail account I maintain.
Hotmail also has the following restrictions currently:
- You can send a maximum of 250 messages per day.
- You can send a message to a maximum of 50 e-mail addresses at the same time.
These addresses can be distributed among the To, Cc, and Bcc lines, or they
can all be on one line.
- You can send messages up to 10 MB each, including attachments.
[/network/email/free]
permanent link
Mon, Apr 16, 2007 7:42 pm
ClamWin No Longer Reporting Opera Infected with Trojan.Bifrose-495
When I scanned
opera.exe, the executable for the
Opera 8.54 web browser on April 8, 2007
with
ClamWin 0.90.1, it reported
the file was infected with Trojan.Bifrose-495 (see
ClamWin Reporting Opera Infected with Trojan.Bifrose-495). The
report appeared to be a false positive and I submitted the file as a false
positive using the form at
ClamAV Virus Database.
When I opened ClamWin today to see if new virus definitions would result in
the file no longer being reported as infected, I saw the message
"You have not yet downloaded Virus Definitions Database. Would you like to
download it now?" I chose "Yes". ClamWin appeared to download new definitions,
but when I selected the file the Scan button was grayed out. I closed
and reopened ClamWin. Again I got the message stating that I had not yet
downloaded virus definitions. I chose to download them again, but the results
were the same. When I exited from the program, right-clicked on the file to
scan and chose "Scan with ClamWin Free Antivirus", I saw the message
"Virus Definitions Database Not Found! Please download it now."
So I checked the ClamWin website. I found there was a new version, 0.90.1.1
The site had the following information on the new version:
Wednesday, 11 April 2007
This quick-fix release addresses the "Missing Virus Database" Error. Also it
includes couple of bug fixes:
- Fixed file creation errors during scanning of OLE and MSI files
- Added description message when a "Can't Open File" error occurs
- Setup now installs virus definitions database
I installed the new version. I was then able to scan opera.exe
and it now reports that the file is uninfected. Previously ClamWin 0.90.1
was reporting that laplink.exe was also infected. It reported that
file was infected with Trojan.Mybot-7604. I felt then that there was a fairly
high probabability that the report was another false positive. When I scanned
the file with the new version of ClamWin with current virus definitions, that
file is now reported as uninfected as well.
[/security/antivirus/clamav]
permanent link
Sun, Apr 15, 2007 4:53 pm
Stopping an Attacker with the Route Reject Command
You can use
KRIPP
to monitor
FTP dictionary
attacks where an attacker tries to guess a userid and password combination to
break into an FTP server. You can block the attacking system with the
route command, e.g.
route add 202.123.213.3 reject
to block all packets from 202.123.213.3. When the attacker has moved on to
other targets, you can remove the routing table entry with
route del 202.123.213.3 reject.
[ More Info ]
[/os/unix/commands]
permanent link
Sat, Apr 14, 2007 9:12 pm
Changing an Uppercase Name in Perl
For a Perl variable,
$name, which contains a name in the form
first name followed by a space and then the last name with all letters in
uppercase, the following code will change the name so that only the first
letter of both parts of the name is capitalized with the rest of the name
in lowercase. E.g. if $name contains
JOHN SMITH, afterwards it
will contain
John Smith.
# The name is in all uppercase letters. Leave the first letter of
# each part of the name in upper case, but put all the others in lowercase
$name =~ tr/A-Z/a-z/;
$name =~ s/([a-z]+)\s([a-z]+)/\u$1 \u$2/;
The first line changes all uppercase letters to lowercase. The next line
looks for the first part of the name, which is stored in $1. There is then
a space followed by the last name, which is stored in $2. Using the substitute
command, the first letter of $1 is changed to uppercase as is the first letter
of $2.
The [a-z] instructs Perl to look for an occurrence of any
letter from "a" to "z". The + afterwards indicates that Perl should
look for 1 or more occurrences of any letter between "a" and "z". Enclosing
the [a-z]+ between ( and ) instructs
Perl to store what if finds, i.e. the first name in this case, in a variable
$1. The \s tells it to look for a whitespace
character, i.e. a space in this
case, and then the next ([a-z]+) will find all of the letters for
the last name and store it in a variable $2 The \u
changes the following letter to uppercase for $1, which is the
first name. The \u$2 then changes the first letter of $2
, which is the last name to uppercase.
[/languages/perl]
permanent link
Mon, Apr 09, 2007 11:01 pm
Anomalous Windows XP Firewall Rules
When checking the firewall settings on a Windows XP Service Pack 2
system tonight, I found several anomalous firewall rules. The system
is running the Windows XP firewall.
When I checked the firewall openings with the netsh firewall show
state command, I didn't see anything unusual.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Enable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
135 TCP IPv4 (null)
137 UDP IPv4 (null)
139 TCP IPv4 (null)
138 UDP IPv4 (null)
9370 UDP IPv4 C:\Program Files\Logitech\Desktop Messenger\8876480\Pr
ogram\LogitechDesktopMessenger.exe
3389 TCP IPv4 (null)
445 TCP IPv4 (null)
22 TCP IPv4 C:\Program Files\Network\OpenSSH\usr\sbin\sshd.exe
Nor did I see anything unusual when I issued the command
netsh firewall show portopening.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
22022 TCP Enable OpenSSH
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
3389 TCP Enable Remote Desktop
However, when I went to the
GUI for configuring the
firewall to correct an mistake I noticed in the firewall configuration, I
saw DwnMaster listed. I didn't know what that program was
nor why it needed a firewall rule.

Double-clicking on DwnMaster showed that the program
associated with the firewall rule was syst.exe in
C:\WINDOWS\Temp.
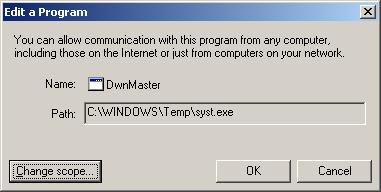
When I checked to see if syst.exe was running, I didn't
see evidence of it running.
C:\>tasklist /fi "imagename eq syst.exe"
INFO: No tasks running with the specified criteria.
And when I checked for the existence of the file, however, though
I found it, it was only zero bytes in length. I am presuming
that it was nullified during an antivirus or antispyware
scan of the system.
C:\>dir c:\windows\temp\syst.exe
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\windows\temp
02/02/2007 03:32 AM 0 syst.exe
1 File(s) 0 bytes
0 Dir(s) 57,556,082,688 bytes free
Looking at the "allowed programs" list for the firewall, I noticed another
unusual entry, C:\win.com.
C:\>netsh firewall show allowedprogram
Allowed programs configuration for Domain profile:
Mode Name / Program
-------------------------------------------------------------------
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable DwnMaster / C:\WINDOWS\Temp\syst.exe
Enable TCP / C:\WIN.COM
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
Allowed programs configuration for Standard profile:
Mode Name / Program
-------------------------------------------------------------------
Enable restorea0 / c:\windows\system32\restorea0.exe
Enable Remote Assistance / C:\WINDOWS\system32\sessmgr.exe
Enable Logitech Desktop Messenger / C:\Program Files\Logitech\Desktop Messenge
r\8876480\Program\LogitechDesktopMessenger.exe
The name given to it was TCP, apparently in an attempt to
make it less likely to stand out as possible malware.
But I wouldn't expect to find a win.com file in the
root directory of a Windows XP system.
It was also a zero byte file when I checked for its existence, however, so
may also have been nullified by a previous scan of the system with antivirus
or antispyware software.
C:\>dir c:\win.com
Volume in drive C has no label.
Volume Serial Number is 909B-3E78
Directory of c:\
02/09/2007 02:47 AM 0 WIN.COM
1 File(s) 0 bytes
0 Dir(s) 57,555,771,392 bytes free
Another allowed program that looked suspicious was
restorea0 in
c:\windows\system32\.
But when I looked for it, I did not see it on the system. So
it may have been removed completely by antivirus or antispyware software
previously. At
FKIYY.EXE
Spyware Remove, I found it listed as one of many alternative names
associated with malware detected by Prevx.
At
SYST.EXE Spyware Remove, Prevx lists syst.exe as being
associated with Trojan Downloader Small yt. At
WIN.COM
Spyware Remove, win.com is linked to
Adware Virtumonde
[/os/windows/xp/firewall]
permanent link
Mon, Apr 09, 2007 9:47 pm
Allow Rtvscan Access Through Windows XP Firewall
Symantec AntiVirus Corporate Edition 8.0 uses rtvscan.exe on client systems
for management of those systems from the antivirus server. Rtvscan listens
on
UDP port 2967 on the
client systems. You can determine if rtvscan.exe is running on a Windows
XP or later system with the
tasklist command.
C:\>tasklist /fi "imagename eq rtvscan.exe"
Image Name PID Session Name Session# Mem Usage
========================= ====== ================ ======== ============
Rtvscan.exe 1784 Console 0 9,736 K
From the above information, I can see that rtvscan.exe is running on the
system and that it has process ID (PID) 1794. I can verify that the process
with PID 1784 is listening on port 2967 on the system using the
netstat command.
C:\>netstat -ano | find "1784"
UDP 0.0.0.0:1061 *:* 1784
UDP 0.0.0.0:2967 *:* 1784
You can create a firewall rule to allow the server to communicate with the
client using the instructions at
Configuring Windows XP Firewall for Symantec
Antivirus Client through either a
GUI or the command line.
An example using the command line is shown below. The example below presumes
the server's IP address is 192.168.0.33.
C:\>netsh firewall set portopening protocol = UDP port = 2967 name = "Symantec A
ntiVirus Client Management" mode = ENABLE scope = CUSTOM 192.168.0.33
Ok.
You can verify the firewall now has the appropriate port opening with the
netsh firewall show portopening command.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Name
-------------------------------------------------------------------
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
22 TCP Enable OpenSSH
2967 UDP Enable Symantec AntiVirus Client Management
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
Port configuration for Standard profile:
Port Protocol Mode Name
-------------------------------------------------------------------
10280 UDP Enable Windows Media Connect
10281 UDP Enable Windows Media Connect
10282 UDP Enable Windows Media Connect
10283 UDP Enable Windows Media Connect
10284 UDP Enable Windows Media Connect
10243 TCP Enable Windows Media Connect
139 TCP Enable NetBIOS Session Service
445 TCP Enable SMB over TCP
137 UDP Enable NetBIOS Name Service
138 UDP Enable NetBIOS Datagram Service
1900 UDP Enable SSDP Component of UPnP Framework
2869 TCP Enable UPnP Framework over TCP
3389 TCP Enable Remote Desktop
Port configuration for Local Area Connection:
Port Protocol Mode Name
-------------------------------------------------------------------
3389 TCP Enable Remote Desktop
Or, alternatively, you can use the netsh firewall show state
command.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Enable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
10243 TCP IPv4 (null)
10280 UDP IPv4 (null)
10281 UDP IPv4 (null)
10282 UDP IPv4 (null)
10283 UDP IPv4 (null)
10284 UDP IPv4 (null)
135 TCP IPv4 (null)
137 UDP IPv4 (null)
139 TCP IPv4 (null)
138 UDP IPv4 (null)
3389 TCP IPv4 (null)
445 TCP IPv4 (null)
22 TCP IPv4 C:\Program Files\Network\OpenSSH\usr\sbin\sshd.exe
1562 TCP IPv4 C:\WINDOWS\SYSTEM32\SVCHOST.EXE
2869 TCP IPv4 (null)
1900 UDP IPv4 C:\WINDOWS\SYSTEM32\SVCHOST.EXE
2967 UDP IPv4 C:\Program Files\Symantec_Client_Security\Symantec Ant
iVirus\Rtvscan.exe
Additional ports open on Local Area Connection:
Port Protocol Version
-------------------------------------------------------------------
3389 TCP Any
The netsh firewall show state command will show you what program
is listening on the port. In this case it shows that Rtvscan.exe is listening
on port 2967
References:
-
Configuring Windows XP Firewall for Symantec Antivirus Client
Written: May 30, 2005
MoonPoint Support
[/security/antivirus/symantec/SAV-Firewall]
permanent link
Sun, Apr 08, 2007 11:10 pm
ClamWin Reporting Opera Infected with Trojan.Bifrose-495
When I scanned a system with
ClamWin
0.90.1, it reported that the executable
opera.exe for the
Opera web browser was infected with
Trojan.Bifrose-495. The system has Opera 8.54 on it.
Checking the definitions timestamp in ClamWin, I saw the following:
ClamAV 0.90.1
Protecting from 107238 Viruses
Virus DB Version: (main: 42, daily: 3049)
Updated: 18:49 08 Apr 2007
I found someone else reporting the same problem on a ClamWin support forum at
False Positives. And I found a post,
Opera.exe: Trojan.Bifrose-495 FOUND,
on an Opera community forum site, where someone posted that ClamAV reported
"Trojan.Bifrose-495 FOUND" for opera.exe, though in his case it appeared he
had version 7 of Opera on his system. He submitted opera.exe from his system
to VirusTotal,
which provides a free service allowing you to upload a file for analysis by
many different antivirus programs. Only ClamAV
and Fortinet identified the file as
being suspicious. The other 27 antivirus scanners used by VirusTotal reported
it was uninfected. ClamWin is a Windows implementation of
ClamAV.
There was also another posting,
Trojan.Bifrose-495?
in a ClamWin forum where someone stated that ClamWin 0.88.7 reported
the same infection for his copy of opera.exe. One of the ClamWin
developers, sherpya, responded that it was a false positive. That person
also submitted his copy to VirusTotal. The result was the same for him, with
only ClamAV reporting the file as infected and Fortinet labelling it as
"suspicious".
I found someone else reporting that ClamWin reported Opera was infected
with Trojan.Bifrose-495 at
Cleaning up a trojan, but the poster didn't appear to consider
the possibility that the report may have been a false positive.
I submitted the opera.exe file from my system to
VirusTotal also. One of the ClamWin
developer's referred the person who posted at
False Positives on the ClamWin forum
to How can I report a
virus that ClamWin doesn't recognise? Or a false positive?, which also
suggests submitting the file to VirusTotal
, if you suspect that ClamWin is reporting a false positive.
The file was scanned by 23 antivirus programs. Only ClamAv and Fortinet
reported an issue with the file. ClamAv reported it found "Trojan.Bifrose-495",
while Fortinet reported the file as "suspicious".
I also submitted the file to
Jotti's Malware Scan, which also
provides a free virus scanning service. Of the 17 antivirus programs it
uses, only ClamAv reported the file as infected with ClamAv reporting
"Found Trojan.Bifrose-495". It scanned the
file with Fortinet as well, but reported for Fortinet that "Found nothing"
(see report
).
I did submit the file using the on-line form at
ClamAV Virus Database as a false positive.
So what does Trojan.Bifrose-495 do? I don't know and could not find any
information on it via a
Google
search. Though I really like ClamWin and ClamAV, using them on many
systems, one major advantage I see to a program like Symantec's antivirus
software, aside from real-time scanning, is that Symantec will provide you
with details on how most of the viruses it identifies work. By looking
at the provided details, you can determine, if your system was infected,
what the virus or trojan may have done and what other indicators of the
infection you should expect to find on the system. ClamAV and thus ClamWin,
which is built on ClamAV, provide no virus encyclopedia you can use for
reference. If this wasn't a false positive I would certainly like to
know how the virus or trojan operates, not just a name for it. Does it
allow someone to take remote control of the infected system? Does it send
out spam from the system, delete or corrupt files, etc.?
I normally use ClamWin as an adjunct to other antivirus software on a system
and don't want real-time scanning capability from it, but really would like to
have further details on any infections found. I have found ClamWin
identifies malware other antivirus programs sometimes miss and am very
appreciative of the work done by the developers for both ClamAV
and ClamWin, but, whenever they report an infected file, I often have
to submit the file to VirusTotal
or Jotti's Malware Scan to
attempt to figure out the potential harm that may have been caused
by an infection. I look at the names used for the infection by
other antivirus programs that also report the submitted file is
infected. I then look check virus encyclopedias they may provide or
do further searching of the web using the names they use for the malware.
Details for the file I submitted:
| Filename: | opera.exe |
| Size: | 76.5 KB (78,336 bytes) |
| Created: | Saturday, April 15, 2006, 1:34:26 PM |
| Modified: | Friday, March 24, 2006, 5:40:10 PM |
| File Version: | 7730 |
| Product Name: | Opera Internet Browser |
| Product Version: | 8.54 |
| MD5 Sum: | 40d2e3a6f1c1dbe7825553164a3b86d3 |
| SHA-1 Hash: | c9623b9018fb6faebef38af37ff02dad361f774d |
The modification date listed on the file when I right-clicked on it
and chose Properties was March 24, 2006. I installed Opera 8.54
on the system on April 15, 2006, so the modification date listed is several
weeks prior to the software being installed on the system.
I also scanned the file with BitDefender 8 Free Edition, which had virus
definitions of April 8, 2007, which is today's date, and Symantec AntiVirus
Corporate Edition 8, which had virus definitions from April 4, 2007. Both of
those antivirus programs were on the system where I ran the ClamAV scan. Both
reported the file was uninfected, so I'm fairly confident at this point
that ClamAV's report of the file as infected was a false positive.
References:
-
False Positives
Posted February 11, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Opera.exe: Trojan.Bifrose-495 FOUND
Posted: December 20, 2006
Forums - Opera Community
-
Trojan.Bifrose-495?
January 5, 2007
ClamWin Free Antivirus Support and
Discussion Forums
-
Cleaning up a trojan
December 21, 2006
WebDeveloper.com Forum
[/security/antivirus/clamav]
permanent link
Sun, Apr 08, 2007 7:53 pm
LibClamAV Error When Scanning a System with ClamWin 0.90.1
I upgraded ClamWin on a system from
version 0.88.4 to 0.90.1, set it to scan all of drive C on the
system and then went to bed.
When I checked the results 9 hours later, I was surprised to find ClamWin
still running. I also saw lots of error messages similar to the following:
LibClamAV Error: ERROR: failed to create file: c:\docume~1\admini~\locals~1
\temp/clamav-b3e9e513a21a2f87d6834aa7fb84676.00000530.clamtmp/
_becaa_r_ndoaa_geiaa_cemaa_r_behaa_feiaa_heeaa_kdbaa_idhaa_idpaa_ldg
aa_ldoaa_idjaa_D_ideaa_idjaa_ldmaa_
On the Clamwin support forums, I found several references to the problem.
At ERROR: failed to create file, shepya, one of the
ClamWin developers, responded on November 12 that the
problem was due to the
OLE2
unpacker that is used by ClamWin attempting to
unpack CAB
files, but encountering problems when doing so, since the files
inside the CAB file have seemingly random names and unpacking them with the OLE2
unpacker would lead to new files being created with the same name as existing
files, if ClamWin didn't stop unpacking the files and produce the error message
instead. Sherpya stated in his response that ClamWin first tries
to unpack the CAB files with a CAB unpacker, but for Installshield CAB files,
since Installshield CAB files are not supported, it then passes the file on to
the OLE2 unpacker, which can't properly unpack the CAB files. Shepya states
the problem is due to Microsoft using the same file signature for both CAB and
OLE2 files.
File Extension for .CAB also indicates that InstallShield CAB
files are not compatible with Microsoft CAB files.
Shepya further stated in a December 11, 2006 posting in the same thread that
"since the cab code skips the archive, so it's passed to the ole2 code
that doesn't pick the correct filenames to extract and since there are a lof of
garbage in file names, clamav tries to sanitize it by replacing invalid chars
by a _, this causes a lot of name clashes, but I preferred to warn instead of
silent ignoring." ClamWin is using ClamAV
for virus scanning; it is a Windows implementation for ClamAV.
There is another thread on the topic at
Scan Write Errors. Sherpya states in that one that
"m$ decided to make .msi files like ole2 container just like office
document, but really they are a sort of cab archives."
And in response to the
LIBCLAM AV error posting on April 4, 2007 by cebo, sherpya responds
that "these messages are harmless, they will be removed on next release."
I certainly hope there is an improvement with the next release.
Previously, when
I started ClamWin on this system before going to bed, it would be finished when
I checked it in the morning. When I checked the system at 9:00 A.M.
after starting it around 11:00 P.M. the previous night, I found the
CPU utilization was at about 100%. ClamWin was using over half the CPU time,
but Spy Sweeper was also using a considerable amount of CPU time. I stopped
Spy Sweeper. Then ClamWin was getting almost all of the CPU time, with the
Task Manager showing its CPU utilization fluctuating between 90% and 97%,
yet it still did not complete until 7:00 P.M., almost 20 hours after I started
it.
I also saw the error message LibClamAV Error: Message is not un
uuencoded form during the scan.
References:
-
ClamWin
-
ERROR: failed to create file:
Posted: November 6, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Scan Write Errors
Posted: October 11, 2006
ClamWin Free Antivirus Support and
Discussion Forums
-
Cabinet
(file format)
Wikipedia, the free encyclopedia
-
File Extension for .CAB
FILExt
-
Object Linking and Embedding
Wikipedia, the free encyclopedia
-
LIBCLAM AV error
Posted: Wednesday, April 4, 2007
ClamWin Free Antivirus Support and Discussion Forums
[/security/antivirus/clamav]
permanent link
Sun, Apr 08, 2007 12:24 pm
Excluding ClamWin Quarantine Directory When Scanning
While searching for information on error messages I was getting while
scanning a system with
ClamWin 0.90.1,
I found a comment by one of the ClamWin developers, alch, at
clamwin is scanning
its own quarantine files that in version 1 the quarantined
files will be encrypted in such a way that they won't be flagged as infected
files on subsequent scans. The response was to a ClamWin user's
complaint about the current version's default behavior of
scanning files in the quarantine folder, flagging them as infected, and then
quarantining them again with a different name. Alch made the statement on
March 23, 2007. He also stated version 1 "is in it's final stages of
development."
You can exclude ClamWin's quarantine directory from being scanned by ClamWin
by following the steps listed in
Excluding the Quarantine Directory from a ClamWin scan.
[/security/antivirus/clamav]
permanent link
Sat, Apr 07, 2007 8:03 am
Happy Birthday Internet!
Reckoning by the publication of the first Request for Comment (RFC) document,
the Internet was born April 7, 1969, when
RFC 1 Title: Host Software was
published by Steve Crocker.
RFC's
document the protcols on the Internet. The precursor to today's Internet was
the ARPANET, which was
developed for the United States Department of Defense. The first RFCs were
published in 1969 for the ARPANET. At first researchers distributed hard
copies of the RFCs among themselves, but in December of 1969 they began
distributing them using the ARPANET itself.
References:
-
April 7, 1969: Birth of That Thing We Call the Internet
By Tony Long
Wired News
-
Request for
Comments
Wikipedia, the free encyclopedia
-
ARPANET
Wikipedia, the free encyclopedia
-
RFC 1 Title: Host Software
By Steve Crocker
IETF Tools
[/network/Internet]
permanent link
Tue, Apr 03, 2007 12:01 pm
Googlebot Alert
If you would like to know when the Google webcrawler, Googlebot, visits
your website you can insert the
PHP code
below in the home page for your site.
<?
$email = "yourname@example.com";
if( eregi("googlebot", $_SERVER['HTTP_USER_AGENT']) )
{
mail($email, "Googlebot Alert",
"Google just indexed your following page: " .
$_SERVER['REQUEST_URI']);
}
?>
You will, of course, need to replace yourname@example.com with
your own email address.
On a Linux or Unix system, you can issue the following commands to see
how many requests for pages on your site today have come from a Googlebot
visit to your site.
grep "$(date +"%d/%b/%Y")" access.log | grep -i "googlebot" | wc -l
You will need to substitute the name and location of the log file that tracks
access to your site for access.log.
The $(date +"%d/%b/%Y") tells grep to look for occurrences of the
current date in the form dd/mmm/YYYY, e.g. 03/Apr/2007
. In my Apache log files, entries appear similar to the one below.
66.249.66.147 - - [03/Apr/2007:09:10:42 -0400] "GET /robots.txt HTTP/1.1" 200 146
If the date is formatted in a different manner in your log file,
you will need to adjust the format accordingly. You can obtain information
on formatting the date with man date.
If you don't have IP addresses translated to a
FQDN, e.g. if your log
file records 66.249.66.147 instead of
crawl-66-249-66-147.googlebot.com, which is the case for my
log file, then you will need to look for the IP address range that is used
by Googlebot.
Googlebot's and Mediapartners-google's IP indicates that
66.249.71.x appears to be assigned to Googlebot, though
reverse name lookups only work up to 66.249.71.208. You
can use the following commands to search for the Googlebot IP address range
66.249.71.1 to 66.249.71.255.
grep "$(date +"%d/%b/%Y")" access.log | grep -i '66.249.66.' | wc -l
The Googlebot's
and Mediapartners-google's IP article mentions that Google uses
a separate bot
that checks pages with Google AdSense ads on them. So, if you have Google
AdSense ads on your site, then both the main Googlebot bot and the
MediaPartners-Google bot will probably visit your site. The author of that
article states he has seen the following IP addresses used for the
Mediapartners-Google bot.
| 66.249.65.40 | crawl-66-249-65-40.googlebot.com |
| 66.249.66.65 | crawl-66-249-66-65.googlebot.com |
References:
-
Googlebot
Alert
By Philipp Lenssen
June 23, 2004
Google Blogoscoped
-
Googlebot's and Mediapartners-google's IP
By Tim Johansson
gurka.se
-
FQDN
Wikipedia, the free encyclopedia
-
Internet bot
Wikipedia, the free encyclopedia
[/network/web/search]
permanent link
Sat, Mar 31, 2007 3:15 pm
Saving YouTube Videos
YouTube doesn't offer a way for you
to easily download videos from the site, but there are other webssites where
you can paste the URL of the video you wish to download and then download
it from those sites.
[ More Info ]
[/video/youtube]
permanent link
Sun, Mar 25, 2007 11:13 pm
Setting Up Samba on A DocuSP Solaris 10 System
I needed to set up file sharing access to a Xerox DocuSP system running the
Solaris 10 operating system, which was controlling a
Xerox DocuColor 250 device. Xerox recommends using Samba, which is already
on the Solaris system to share a directory to Windows systems. Since I
encountered some problems setting up the system using the instructions
Xerox provided, I've written my own instructions in case I have to repeat
the process again or should anyone else also need to implement the same
file sharing.
[ More Info ]
[/os/unix/solaris]
permanent link
Fri, Mar 23, 2007 7:30 pm
Using Google's Cache
If you encounter a "file not found", "internal server error", "cannot find
server or DNS Error" when trying to access a webpage, you may still be
able to access the webpage by viewing a saved copy of it in
Google's Cache or
at the
Internet Archive,
aka Wayback Machine.
[ More Info ]
[/network/web/search]
permanent link
Thu, Mar 22, 2007 5:55 pm
Adding Printer from Command Line
I was logged into a system using an ordinary user account under Windows XP
and needed to create a new printer port so that I could print to an HP
printer, which was on the network to which I was connected. The user account
doesn't have access to add network printers, but I had a lot of applications
open with ongoing work and didn't want to have to save and close everything I
was working on, log off, login as the administrator, log off, log back
in under the user account and reopen all the applications and files,
especially since I only had a few minutes to get a document printed prior
to a meeting.
Fortunately, I was able to find information on how to easily resolve my
problem at
Command Line Printer Control in Windows 2000 / XP. All I had to do to
add a printer from the administrator account while still remaining logged into
my user account was the following:
- Open Windows Explorer and navigate to
C:\WINDOWS\system32.
-
Right-click on cmd.exe while holding down a shift key, then
select Run as.
-
Select "The following user", put in the userid for the administrator
account for the system, e.g. SystemName\administrator, for user
name and its password, then click on OK.
-
At the command prompt window that opens, enter the following command:
RUNDLL32 PRINTUI.DLL,PrintUIEntry /il
That will run the Add Printer Wizard from the administrator account,
allowing you to add a printer port.
Note: The capitalization of PrintUIEntry is important.
If you don't use PrintUIEntry, but, instead used
printUIEntry, you would get the error message below:
Error in printui.dll
Missing entry:printUIEntry
The /il parameter is also case sensitive.
References:
-
Command Line Printer Control in Windows 2000 / XP
Rob van der Woude's Scripting Pages
[/os/windows/printers]
permanent link
Wed, Mar 21, 2007 9:13 pm
Updating Plushelp Information in TinyMUSH
If you have updated the plushelp.txt file in
TinyMUSH, you can make
the information available within the
MUSH by taking the following
steps:
-
After editing the plushelp.txt file, within the directory where the
plushelp file is located, issue the following command to rebuild the
plushelp index file:
./mkindx plushelp.txt plushelp.indx
Alternatively, you could run ../Index to rebuild all index files.
-
Within the MUSH, issue the command
@readcache
References:
-
TinyMUSH 3: The Home Page
sourceforge.net
- MUSH
Wikipedia, the free encyclopedia
-
root/releases/1.50/11/README
PennMUSH
[/gaming/tinymush]
permanent link
Thu, Mar 15, 2007 1:05 am
Checking User VPN Connections on SBS 2003
If you need to check on who is logged into a Windows
Small Business (SBS) 2003 server via a VPN connection
you can do so by using
Routing and Remote Access
under
Start then
Administrative Tools.
For analyzing the log files for information on VPN logins
through the SBS 2003 server, Microsoft offers the iasparse
tool, which can be found on Disc # 2 of the installation CDs.
But the shareware tool,
IAS Log Viewer, is better at displaying the data in a more
manageable fashion.
[ More Info ]
[/os/windows/server2003]
permanent link
Mon, Mar 12, 2007 10:03 pm
Why Do I See a Lot of Strange Symbols When I Compose an Email Message
If you are seeing a lot of unexpected symbols when you are composing
an email message in Outlook 2003, such as the ones shown below, then you may
have accidentally turned on the display of nonprinting characters.
You may be seeing ¶ symbols at the end of each paragraph. Those
are called "para symbols" or "pilcrow signs". You may also see
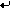 symbols.
Those downwards arrows that turn a 90-degree corner leftwards indicate
line breaks or carriage returns in your text. These
symbols.
Those downwards arrows that turn a 90-degree corner leftwards indicate
line breaks or carriage returns in your text. These
 carriage return arrows should appear wherever you've hit the return key when
composing a message. You will also see small raised dots between words,
i.e. "He
carriage return arrows should appear wherever you've hit the return key when
composing a message. You will also see small raised dots between words,
i.e. "He  took
took
 his
his  vorpal
vorpal  sword". The
sword". The  character simply means that
there is a space there.
character simply means that
there is a space there.
If Outlook is configured to use Microsoft Word to edit your email
messages, those characters are embedded in your documents, but are
normally invisible to you. Displaying them can help some users when
formatting their documents.
You can toggle their display on or off by clicking on the ¶
symbol that you should see in the toolbar menu at the top of your
message composition window. You can also toggle the display of
these characters on or off by hitting the Ctrl, Shift, and "8" keys,
i.e. Ctrl then asterisk, simultaneously. And, if those characters
have suddenly appeared in your documents when you don't want them there,
it is likely because you inadvertently hit the Ctrl key while hitting
Shift+8 to get an asterisk symbol.
References:
-
What do all those funny marks, like the dots between the words in
my document, and the square bullets in the left margin, mean?
Frequently Asked Questions - Microsoft Word MVP FAQ Site
Article contributed by Suzanne
Barnhill and
Dave Rado
-
Turning Display of Paragraph Markers On and Off in Microsoft Word
MoonPoint Support
-
List of XML and HTML character entity references
Wikipedia, the free encyclopedia
[/os/windows/office/outlook]
permanent link
Sat, Mar 10, 2007 9:52 pm
Upgrading TinyMUSH 3.0 to 3.1
I upgraded TinyMUSH roleplaying software from version 3.0 to version 3.1.
[ More Info ]
[/gaming/tinymush]
permanent link
Fri, Mar 09, 2007 10:09 pm
Finding a String with a Recursive Grep
If you need to find a specific string in all files of a particular
type in the current directory and all directories beneath it, you
can use a command similar to the following:
find . -name "*.php" -exec grep "noindex" {} /dev/null \;
In this case I want to find all of the PHP files where I have included
the string "noindex" in a META tag.
References:
-
Greg Hinkel's UNIX Tip of the Week for March 3, 1996
[/os/unix/commands]
permanent link
Mon, Mar 05, 2007 10:56 pm
Correcting Poor Print Quality on an HP Business Inkjet 2800 Printer
A user of an HP Business Inkjet 2800 printer was having problems with
poor print quality for printouts. Characters were smudged or there
were gaps in printing. I've posted tips from the
HP Business
Inkjet 2800 series Toolbox for alleviating the problem.
[ More Info ]
[/hardware/printer/hp]
permanent link
Fri, Mar 02, 2007 1:37 pm
Excluding the Quarantine Directory from a ClamWin scan
Unless you tell it to exclude it's own quarantine directory,
ClamWin will scan that
directory when you perform a scan of the entire hard disk
or any directory that contains the quarantine directory beneath
it. When it encounters already quarantined items, ClamWin will
put a numerical value at the end as an extension, e.g. "000".
A subsequent scan will repeat the process, so a file may then
get the extension "000.000".
I don't want ClamWin to scan its own quarantine directory and
report infections for items it quarantined during previous
scans. To avoid that result, you can take the following steps
(instructions written for ClamWin 0.90, but should apply
to other versions as well):
- Open ClamWin.
- Click on Tools and select Preferences.
- Click on the Advanced tab.
- Put
--exclude-dir=".clamwin\\quarantine" in the
Additional Clamscan Command Line Parameters field. Note:
you must use two backslashes after "clamwin", because ClamWin
treats the entry as a regular expression. In a regular expression,
a backslash, "\", has special significance, so you need to "escape"
that special significance by putting another backslash in front
of any backslash you need to use.
If you wish to exclude multiple directories, you can use multiple
--exclude-dir commands separated by spaces, e.g.
--exclude-dir=".clamwin\\quarantine"
--exclude-dir="BitDefender8\\Quarantine".
To exclude individual files, you can use the exclude command,
e.g. exclude="test.exe".
[/security/antivirus/clamav]
permanent link
Sun, Feb 25, 2007 6:14 pm
Enabling a TFTP Server on Solaris 10
I needed to configure a Solaris 10 system as a
TFTP server.
When I checked to see if the system was already functioning as a TFTP server,
I found it was not.
# svcs | grep tftp
#
I removed the "#" from the following line in /etc/inetd.conf:
tftp dgram udp6 wait root /usr/sbin/in.tftpd in.tftpd -s /tftpboot
I then ran inetdconv.
# inetconv
inetconv: Notice: Service manifest for 100235/1 already generated as /var/svc/manifest/network/rpc/100235_1-rpc_ticotsord.xml, skipped
inetconv: Notice: Service manifest for 100083/1 already generated as /var/svc/manifest/network/rpc/100083_1-rpc_tcp.xml, skipped
inetconv: Notice: Service manifest for 100068/2-5 already generated as /var/svc/manifest/network/rpc/100068_2-5-rpc_udp.xml, skipped
tftp -> /var/svc/manifest/network/tftp-udp6.xml
Importing tftp-udp6.xml ...Done
When I then checked to ensure the system was functioning as a TFTP server,
I found it was functioning as one.
# netstat -a | grep tftp
*.tftp Idle
*.tftp Idle
# svcs | grep tftp
online 16:21:53 svc:/network/tftp/udp6:default
# netstat -a | grep tftp
*.tftp Idle
*.tftp Idle
You can disable the TFTP service with inetadm -d svc:/network/tftp/udp6
and re-enable it with inetadm -e svc:/network/tftp/udp6.
Create a /tftpboot directory where files can be placed to be
downloaded by tftp clients.
# mkdir /tftpboot
For further information on the TFTP service, you can use the man command
man tftpd.
References:
-
Enabling tftpd in Solaris 10
By Lasse Østerild
October 11, 2005
unixzone.dk
[/os/unix/solaris]
permanent link
Thu, Feb 08, 2007 11:19 am
PayPal Phising Site at bourke.pcpro.net.au
Someone forwarded a
phishing
email message to me this morning that was an attempt to garner PayPal userids
and passwords as well as personal information, including a credit card number
from unsuspecting PayPal users.
The
message attempted to trick PayPal users to going to a spoofed PayPal
website to confirm the addition of an email address to a user's PayPal
account. In reality, the link in the message would take the victim to
http://sv1.melbhosting.com.au/%7Eforcast/index.html, which would
redirect him to
http://bourke.pcpro.net.au/icons/.pay/pal/index.html. There he
would see a website mimicking the PayPal site where he would be prompted for
his PayPal userid and password. If he entered a userid and password, he
would see a form asking for personal information, including a credit card
number.
I reported the spoofed site at 10:33 A.M. using PayPal's
Contact Us -
Protections/Privacy/Security - Report Fake Site/Spoof form. I also reported
the site to the Phishing Incident
Reporting and Termination (PIRT) Squad at 10:48 A.M. At 11:15 A.M. the
webpage to which the link pointed,
http://sv1.melbhosting.com.au/%7Eforcast/index.html was removed from
the webserver on which it resided, resulting in a "HTTP 404 - File not found"
message, but the spoofed PayPal site at bourke.pcpro.net.au was still
accessible.
[/security/scams/phishing/paypal]
permanent link
Tue, Feb 06, 2007 11:57 pm
Wake On LAN using mc-wol
I needed to share an Outlook user's calendar with someone else in her
office. I had expected to be able to remotely log into her system to
configure Outlook to share her calendar. But when I attempted to log
into her system at 9:30 P.M., I found it was inaccessible. I then remembered
that she always turns her system off when she leaves. I didn't want to spend
1/2 driving to her office to make a change I could complete in less than 10
minutes and then have to spend another 1/2 hour driving back home.
Fortunately, I had selected the option to have Dell preconfigure the system
for Wake On Lan (WOL)
support in the BIOS
when her company purchased the system. Wake On Lan support allows one to
restart a computer that has been shut down by sending a "Magic Packet" to
the Media Access Control
(MAC) address of the network card in a computer to "wakeup" the computer,
i.e. power on and boot up the computer.
This can occur when the system is
still providing power to the Ethernet controller in the system. Most
modern computers with a network connection provided through the motherboard
support this functionality. The functionality is also present in motherboards
that support the
PCI 2.2 standard when a PCI 2.2 network adapter is used. In other cases,
when WOL support is provided through the motherboard, the motherboard must have
a WAKEUP-LINK header onboard and connected to the network card via a special
3-pin cable. Wake on LAN must also be enabled in the Power Management section
of the systems's BIOS. It may also be necessary to configure the computer to
reserve power for the network card when the system is shut down.
To wake a shut down system, you need a program that can send the Magic Packet
to the MAC address of the target system. You also need to know the MAC address
of the target system. In this case I use Norton Ghost to backup the systems on
the LAN and Norton Ghost provided me with the MAC address.
There are quite a few free programs that provide WOL capabilities. You can find
many listed in the Wikipedia
Wake-on-Lan article on the topic. I used the free utility provided by
MATCODE at
http://www.matcode.com/wol.htm.
To use the MATCODe WOL utility, mc-wol.exe, you simply download the utility
and then run it with mc-wol <MAC Address>, e.g.
as shown below.
C:\Program Files\Network\WOL>mc-wol 00:13:72:3B:4A:B6
WakeOnLAN v1.0 Copyright (c)2001, MATCODE Software.
Web: http://www.matcode.com
Author: Vitaly Evseenko, ve@matcode.com
Sending "Magic Packet" to 00:13:72:3b:4a:b6 - Success!
Once I ran the program, I was able to ping the IP address of the target
system shortly afterwards to verify the system was back up.
If you need to obtain the MAC address of a system you can ping it and then
look in the ARP table
on the system from which you ran the ping, with arp -a to find the
relevant entry. Or you can use the MATCODE, MCGETMAC.EXE
utility available from the same URL as the MC-WOL.EXE utility
or from the links listed below.
C:\Program Files\Network\WOL>mcgetmac 192.168.0.15
Get MAC v1.0 Copyright (c)2001, MATCODE Software.
Web: http://www.matcode.com
Author: Vitaly Evseenko, ve@matcode.com
Name: js.example.com
IP address: 192.168.0.15
Ethernet MAC address: 00:13:72:3B:4A:B6
Press any key ...
References:
-
Wake-On-Lan
MATCODE
-
Wake-on-LAN
Wikipedia
-
MAC address
Wikipedia
-
Conventional PCI 2.2
PCI-SIG
[/network/wol]
permanent link
Sun, Feb 04, 2007 8:04 pm
Vi Reference
I found a useful vi reference page at
http://www.ungerhu.com/jxh/vi.html, which I have copied
here. The page was created
by
Maarten Litmaath and is maintained by
James Hu. I found it a useful reference
for substitution patterns, though it also has a lot of other vi information.
If you want to replace "Life's but a walking" with "Life's but a walking
shadow" you can use
:s/Life's but a walking/& shadow/. The ampersand, in the
pattern to be substituted in place of the prior one,
references the previously found match.
[/software/editors/vi]
permanent link
Fri, Jan 12, 2007 9:48 pm
Who is Logged On to a Computer - VBS Script
If you need to know whether anyone is logged into a remote computer
in your domain or who that might be, you can use
LoggedOn.vbs,
a script I found at
List User Logged On To A Remote Computer, which was written by
Cheyenne Harden and is available at the
LazyNetworkAdmin.Com website
or from this site (see links below).
To use the utility, you can enter LoggedOn.vbs
at the command line while in the directory where the file
is located. A small window will open prompting you for the name
of the computer to query.
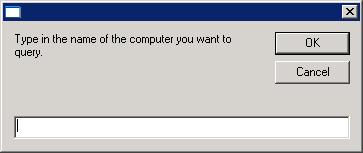
You will see the logged on user displayed in a small Windows
Script Host window as shown below:
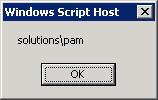
If no one is logged on to the system, you will see "null" displayed
in the small Windows Script Host window that opens.
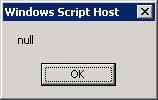
If you want the logged on user information displayed in a form
that you can copy and paste into a document, you can use
cscript /nologo LoggedOn instead. The results will
then be displayed on the command line as below:
C:\Program Files\Utilities\Miscellaneous>cscript /nologo LoggedOn.vbs
solutions\pam
If no one is logged into the system, you will see "null" displayed
on the command line.
C:\Program Files\Utilities\Miscellaneous>cscript /nologo LoggedOn.vbs
null
If the system can't be queried, you won't see an error message.
Instead, you won't see anything displayed.
Information on other utilities to display the logged on user can
be found at Who Is
Logged On?.
LoggedOn.vbs
LoggedOn.zip
References:
-
List User Logged On To A Remote Computer
By Cheyenne Harden
LazyNetworkAdmin.com
-
Who Is Logged On?
MoonPoint Support
[/languages/vbs/sysadmin]
permanent link
Fri, Jan 12, 2007 8:10 pm
Creating an Alias Email Address on Exchange 2003 Server
You can create an alias on a Microsoft Exchange server so that an
account can receive email for multiple email addresses. E.g., suppose
John Smith in the sales department has an account in the domain with
a userid of John. He would like to receive email whether it is addressed
to john@example.com, jsmith@example.com, or sales@example.com. Perhaps
there are several people who need to receive any email addressed to
sales@example.com. You can attach an alias to an individual user account
or you can set up a new group on the server and include all of the
relevant user accounts in the group, so that they all get email
addressed to the group name.
[ More Info ]
[/network/email/exchange]
permanent link
Mon, Jan 01, 2007 2:22 pm
Bazooka Update Failure
When attempting to update the malware database for
Bazooka ™ Adware and Spyware Scanner,
a free tool for detecting adware, spyware, trojans, keyloggers, etc. on a
system, which is compatible with Windows 95/98/ME/NT/2000/XP, I received the
message below:
Error updating database. Could not save the new database on the hard drive.
An error occurred when trying to open the file for writing.
Filename: 'system\bazooka_db.bdb'
Current Working Directory: C:\Program Files\Security\Spyware\Bazooka Scanner\
System error message: Access is denied.
C++ exception: ios::failbit set
Could not update the database. Please check the following:
1. Are you connected to the Internet?
2. Maybe it was a temporary error. Please try again later.
You can also update the database manually. Would you like to have instructions
how to update it manually?
When I checked the properties of the Bazooka database,
bazooka_db.bdb, which is under the system directory
of the Bazooka installation folder, by right-clicking on the file and
selecting Properties, I found it was marked as "read-only".
I unchecked the read-only option and then was able to update the database.
[/security/spyware/bazooka]
permanent link

Privacy Policy
Contact
























