Wed, Dec 31, 2014 4:45 pm
Determining the version of Microsoft Word used to edit a .docx Document
I sent someone a Microsoft Word document that contained a network diagram I had
created in PowerPoint and then copied and pasted into the Word document.
I created the file on an Apple MacBook Pro laptop using
Microsoft® Word 2008 for Mac and saved it in "Word Document (.docx)" format.
The diagram I pasted into the Word document was created with
Microsoft® PowerPoint® 2008 for Mac. The recipient informed me that
some of the text in boxes in the diagram was cropped, so he edited the
diagram and sent me a copy of the document with his edited diagram. When
I viewed his version, I saw text missing that had been present in my version
and some of the double-headed arrows I had on the diagram now looked
odd to me when viewed in Word on the Mac. I presumed the issue was due
to the different versions of Microsoft Word we are using, since I had
encountered issues before where diagrams created in a Microsoft Office
application on a Windows-based PC looked different when viewed in the
same application on a Mac.
I thought he was likely using Office 2013, but I wanted to verify that
was the version he was using. The .docx files we were exchanging became
a standard Word format starting with Office 2007. They are in an
Office Open XML
format, which is a
zipped, XML-based file
format developed by Microsoft; information about the
formats can be found in the Microsoft Office 2007 article
Introducing the Office (2007) Open XML File Formats. Prior to
Office 2007, Microsoft used proprietary file formats based on the OLE
Compound File Binary Format.1
You can check the version of Word that was last used to edit a
document by unzipping the docx file; you can use the unzip
command from a shell prompt on a Mac OS X system. If your unzip program
isn't opening it, you may have to rename it changing the .docx
extension to .zip, but that's not needed for the OS X unzip utility.
When you unzip the docx file, there will be a docProps
directory with an app.xml file within it. In that file
you will see a number between AppVersion tags, e.g., as
shown below:
<AppVersion>15.0000</AppVersion>
To translate that number into the commonly used version number, the
table below can be used:
| Number | Office Version |
|---|
| 12.0000 | 2007 or Office 2008 for Mac |
| 14.0000 | 2010 |
| 15.0000 | 2013 |
If you are interested in the usage for the other documents within the
.docx container file, see the ForensicsWiki article
Word Document (DOCX). The contents of the Word document can be
found in word/document.xml when you examine the files
within the .docx file.
Since I saw 15.0000 as the AppVersion in the file he sent,
I could tell that he was, indeed, using Office 2013. In .docx files
I saved from Word 2008, I saw 12.0000 as the AppVersion
number within app.xml.
To resolve the problem, instead of copying and pasting the
diagram from PowerPoint into the Word document, I saved it as a JPEG image
from within PowerPoint. Then chose "Insert", then "Picture", then "From File"
within Word to insert the diagram as a picture instead. When I viewed the
document with embedded diagram afterwards in Word for Office 2007 and 2010 it
looked the same as it did in Word 2008 on the Mac, though it had also looked
ok in those Microsoft Windows applications when I used the pasted PowerPoint
version. The embedded JPG file also looked the same in Apache OpenOffice
Writer 4; it had not appeared when I viewed the document there
previously and when I had viewed the PowerPoint file in OpenOffice
Impress, the diagram looked quite different with most of the text
missing and small circles beneath the network clouds in the diagram.
References:
-
Microsoft Office: File formats and metadata
Date accessed: December 31, 2014
Wikipedia, the free encyclopedia
-
Which Version of Microsoft Word created a given document?
Date: August 25, 2013
By: Gergely
Herendi
Super User
-
Word Document (DOCX)
ForensicsWiki
[/os/windows/office/word]
permanent link
Tue, Dec 30, 2014 1:24 am
PHP script displaying wrong time
I include the following PHP code in web pages on this system to display the
last time that a file was updated.
<?php
$thisfile = pathinfo($_SERVER['PHP_SELF']);
echo "Last modified: ".date("l F j, Y g:i A",
filemtime($thisfile["basename"]));
?>
After I replaced the hard drive recently and installed
CentOS 7 as a fresh install, the times displayed have been ahead 5 hours, i.e.,
the PHP code was displaying a time stamp matching
Universal
Coordinated Time (UTC), also commonly referred to as
Greenwich Mean
Time, rather than
Eastern Standard Time (EST)
I verified the time zone was set correctly at the operating system level
with the timedatectl
command, so I realized the issue must be with PHP itself. I checked the
location of the PHP configuration file, php.ini and found it was
located at /etc/php.ini.
$ locate php.ini
/etc/php.ini
/usr/share/doc/php-common-5.4.16/php.ini-development
/usr/share/doc/php-common-5.4.16/php.ini-production
I logged into the root account and checked the contents of the
/etc/php.ini file. I found that the timezone was not
set in the file:
[Date]
; Defines the default timezone used by the date functions
; http://php.net/date.timezone
;date.timezone =
So I removed the semicolon which was making the date.timezone
line into a comment and set the time zone to be the appropriate one for
Eastern Time (ET).
[Date]
; Defines the default timezone used by the date functions
; http://php.net/date.timezone
date.timezone =America/New_York
I then restarted the Apache web server software with the
apachectl restart command, which fixed the problem.
[/languages/php]
permanent link
Tue, Dec 30, 2014 12:51 am
Setting the time zone on a CentOS 7 system
You can see the time zones a CentOS 7 system recognizes by entering the
command
timedatectl list-timezones while logged into the root
account.
[root@localhost ~]# timedatectl list-timezones
Africa/Abidjan
Africa/Accra
Africa/Addis_Ababa
Africa/Algiers
Africa/Asmara
Africa/Bamako
Africa/Bangui
Africa/Banjul
Africa/Bissau
Africa/Blantyre
Africa/Brazzaville
Africa/Bujumbura
Africa/Cairo
Africa/Casablanca
<text snipped>
Pacific/Pitcairn
Pacific/Pohnpei
Pacific/Port_Moresby
Pacific/Rarotonga
Pacific/Saipan
Pacific/Tahiti
Pacific/Tarawa
Pacific/Tongatapu
Pacific/Wake
Pacific/Wallis
For a system in the Americas, the following time zones are recognized:
[root@localhost ~]# timedatectl list-timezones | grep America
America/Adak
America/Anchorage
America/Anguilla
America/Antigua
America/Araguaina
America/Argentina/Buenos_Aires
America/Argentina/Catamarca
America/Argentina/Cordoba
America/Argentina/Jujuy
America/Argentina/La_Rioja
America/Argentina/Mendoza
America/Argentina/Rio_Gallegos
America/Argentina/Salta
America/Argentina/San_Juan
America/Argentina/San_Luis
America/Argentina/Tucuman
America/Argentina/Ushuaia
America/Aruba
America/Asuncion
America/Atikokan
America/Bahia
America/Bahia_Banderas
America/Barbados
America/Belem
America/Belize
America/Blanc-Sablon
America/Boa_Vista
America/Bogota
America/Boise
America/Cambridge_Bay
America/Campo_Grande
America/Cancun
America/Caracas
America/Cayenne
America/Cayman
America/Chicago
America/Chihuahua
America/Costa_Rica
America/Creston
America/Cuiaba
America/Curacao
America/Danmarkshavn
America/Dawson
America/Dawson_Creek
America/Denver
America/Detroit
America/Dominica
America/Edmonton
America/Eirunepe
America/El_Salvador
America/Fortaleza
America/Glace_Bay
America/Godthab
America/Goose_Bay
America/Grand_Turk
America/Grenada
America/Guadeloupe
America/Guatemala
America/Guayaquil
America/Guyana
America/Halifax
America/Havana
America/Hermosillo
America/Indiana/Indianapolis
America/Indiana/Knox
America/Indiana/Marengo
America/Indiana/Petersburg
America/Indiana/Tell_City
America/Indiana/Vevay
America/Indiana/Vincennes
America/Indiana/Winamac
America/Inuvik
America/Iqaluit
America/Jamaica
America/Juneau
America/Kentucky/Louisville
America/Kentucky/Monticello
America/Kralendijk
America/La_Paz
America/Lima
America/Los_Angeles
America/Lower_Princes
America/Maceio
America/Managua
America/Manaus
America/Marigot
America/Martinique
America/Matamoros
America/Mazatlan
America/Menominee
America/Merida
America/Metlakatla
America/Mexico_City
America/Miquelon
America/Moncton
America/Monterrey
America/Montevideo
America/Montserrat
America/Nassau
America/New_York
America/Nipigon
America/Nome
America/Noronha
America/North_Dakota/Beulah
America/North_Dakota/Center
America/North_Dakota/New_Salem
America/Ojinaga
America/Panama
America/Pangnirtung
America/Paramaribo
America/Phoenix
America/Port-au-Prince
America/Port_of_Spain
America/Porto_Velho
America/Puerto_Rico
America/Rainy_River
America/Rankin_Inlet
America/Recife
America/Regina
America/Resolute
America/Rio_Branco
America/Santa_Isabel
America/Santarem
America/Santiago
America/Santo_Domingo
America/Sao_Paulo
America/Scoresbysund
America/Sitka
America/St_Barthelemy
America/St_Johns
America/St_Kitts
America/St_Lucia
America/St_Thomas
America/St_Vincent
America/Swift_Current
America/Tegucigalpa
America/Thule
America/Thunder_Bay
America/Tijuana
America/Toronto
America/Tortola
America/Vancouver
America/Whitehorse
America/Winnipeg
America/Yakutat
America/Yellowknife
For a system on the east coast of the U.S., the appropriate time zone
would be "America/New_York". You can see the current timezone setting with the
command timedatectl with no parameters.
[root@localhost ~]# timedatectl
Local time: Tue 2014-12-30 00:15:02 EST
Universal time: Tue 2014-12-30 05:15:02 UTC
RTC time: Tue 2014-12-30 05:15:02
Timezone: America/New_York (EST, -0500)
NTP enabled: yes
NTP synchronized: yes
RTC in local TZ: no
DST active: no
Last DST change: DST ended at
Sun 2014-11-02 01:59:59 EDT
Sun 2014-11-02 01:00:00 EST
Next DST change: DST begins (the clock jumps one hour forward) at
Sun 2015-03-08 01:59:59 EST
Sun 2015-03-08 03:00:00 EDTIf you need to change the time zone, you can enter the command with
a set-timezone parameter, e.g.,
timedatectl set-timezone America/New_York.
You can use the ntpdate package to synchronize your
system with a
Network Time Protocol (NTP) server. You can check if the package is
installed with the command rpm -qi ntpdate. You will see
details on the package, if it is installed. If it is not installed, you
will see "package ntpdate is not installed".
References:
-
How To Configure Server Timezone In CentOS 7
By: Richard W
Date: September 14, 2014
Liberian Geek
[/os/unix/linux/centos]
permanent link
Mon, Dec 29, 2014 9:38 pm
Colasoft Ping Tool 1.2
If you want a graphical version of the ping tool that comes with most
operating systems, the
Colasoft Ping Tool provides a
GUI tool that, in addition to providing the standard
information provided by ping tests, such as minimum, maximum, and average
response times, also puts the information into a chart, which can be
viewed in several formats, e.g., bar chart, line chart, and area chart.
As ping packets are sent, the program updates a graph showing how ping
response times are varying over time with response times in milliseconds
on the y axis and the x axis showing time. The program also allows you to
save an image of the chart it produces as a BMP file, which can be viewed
by a variety of image viewing programs on a Microsoft Windows system.
[ More Info ]
[/reviews/software/windows/network/icmp]
permanent link
Mon, Dec 29, 2014 12:09 am
PowerShell Server 6.0
I installed PowerShell Server software on a Windows 8.1 Professional system to
enable the system to function as an SSH server. I've used Bitvise's SSH
server software and
Copssh with recent operating
systems, but hadn't used the PowerShell Server software before. The
software allows a system to function as an SSH and SFTP server. I had
hoped to be able to allow domain accounts to log into the system as well
as local accounts, but so far I've only been able to log into the system
via SSH after installing the software with local accounts on the system.
[ More Info ]
[/reviews/software/windows/network/ssh]
permanent link
Sat, Dec 27, 2014 11:01 pm
EFI System Partition
PCs now have UEFI firmware rather than the BIOS they once had. Hard disk
drives in systems with UEFI firmware may have an "EFI System Partition",
which will be fairly small, e.g. about 100 MB, which may be a third partition
on drives that may have an operating system, such as Microsoft Windows on
one partition and system recovey software on another partition. The
EFI partition must be formatted with the FAT12, FAT16, or FAT32 file
system. The partiton will store boot loader code for operating systems, such as
Windows, installed on other partitions and may also store device drivers
needed by the firmware.
[ More Info ]
[/hardware/pc/UEFI]
permanent link
Sat, Dec 27, 2014 3:20 pm
Windows Server 2012 - Folders located on the system hard drive
After I set up a Windows Server 2012 Essentials server, I noticed the dashboard
indicated two alerts were pending. One of them was just to reboot the server
since updates had been recently installed that required a reboot, but the
other alert was "One or more server folders are located on the system hard
drive". The folders referenced were as follows:
- Client Computer Backups
- Folder Redirection
- File History Backups
- Users
- Company
If you have a second internal drive or another partition on the primary
drive you can move the
folders with these steps.
[/os/windows/server2012]
permanent link
Thu, Dec 25, 2014 9:29 pm
Windows Server 2012 Essentials Product Key
I needed to install Microsoft
Windows Server 2012
Essentials on a system. Windows Server 2012 is the server version of
Windows 8 and the successor to Windows Server 2008 R2. I had the product key for
Windows Server 2012, but not the media. I downloaded an ISO file for Windows
Server 2012 R2 Essentials from Microsoft at
Windows Server Evaluations. The evaluation version allows you to try the
software for 180 days before purchase. I burned the .iso file to a DVD
and started the installation of the software. When I got to the "Enter
the product key to activate Windows" step, I put in the product key I had,
but received the message "We couldn't verify the product key. Please check
your installation media." After triple-checking the product key, I had to
conclude it wasn't going to work with the latest version of the software I
downloaded from Microsoft's site. Someone provided me with a link where I
could download an ISO file to use with the legitimate product key, but I was
concerned about the possibility of tampering with the contents of that ISO
file. So I checked the
MD5 and
SHA-1 hashes for the ISO file
with
digestIT 2004, which
gave me the following hashes for
en_server_install_disc_windows_server_2012_essentials_x64_dvd_1022281.iso:
MD5: 5ee4c7ad57248b5e791dcfd39d9e54e3
SHA-1: 1f3fbf9cd23f864a2acc6b7a6a8e6a9eb94b5c52
I was then able to verify those hashes with postings from
Server 2012 Essentials RTM (SHA-1 from October 11, 2012) and
Server 2012 Essentials RTM Page 2 (MD5 and SHA-1 from December 8, 2012)
postings at My Digital Life Forums
, which gave me the confidence to use that .iso file for the installation
of the server software, since the hashes matched ones posted for the 2012
version of the software distributed by Microsoft. Such hashes are
commonly used to verify that a file is exactly the same as it was when
provided by the original software developer and has not been modified.
When I installed Windows Server 2012 from the DVD I burned from that
ISO file, I was able to use the product key I had.
[/os/windows/server2012]
permanent link
Thu, Dec 25, 2014 6:20 pm
Cloning a drive with Clonezilla
Clonezilla,
which is a
live
CD based on Debian Linux, provides the capability to clone one disk
drive to another. You can boot a system from the live CD and copy an
entire drive, including Microsoft Windows partitions, to a new drive.
[ More Info ]
[/os/unix/linux/Clonezilla]
permanent link
Mon, Dec 22, 2014 11:59 pm
Allow file downloads in Internet Explorer 11
A user reported she received the following message when attempting to download
an attachment to email she was viewing while logged into her GoDaddy email
account through Internet Explorer 11.
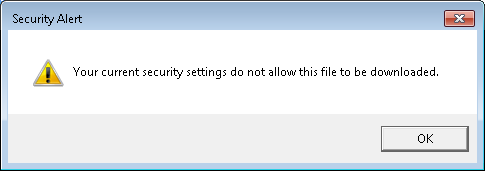
I tried downloading a Microsoft Word .docx attachment to an email and
saw the same Security Alert window, which stated "Your current security
settings do not allow this file to be downloaded."
The setting, which applies to all files rather than a particular type of
file such as a Microsoft Word document, can be changed through the
following steps in Internet Explorer (IE) 11:
- Click on Tools.
- Select Internet Options.
- Click on the Security tab.
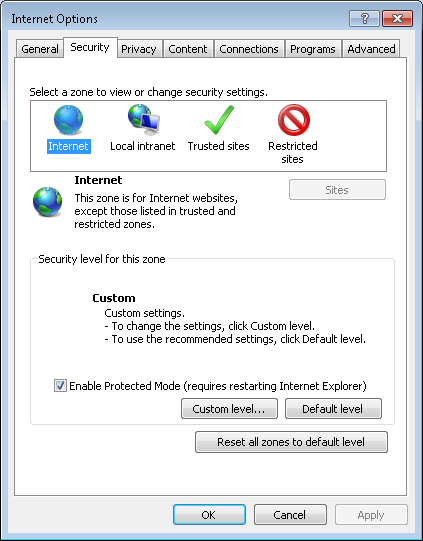
-
Select the Internet zone, which is the left-most zone in the row of icons
representing the four zones: Internet, Local intranet, Trusted sites, and
Restricted sites.
-
Click on the Custom level button.
-
In the Security Settings - Internet Zone window that opens, scroll
down through the settings list until you see Downloads. For
the File download option, change it from "Disable" to "Enable"
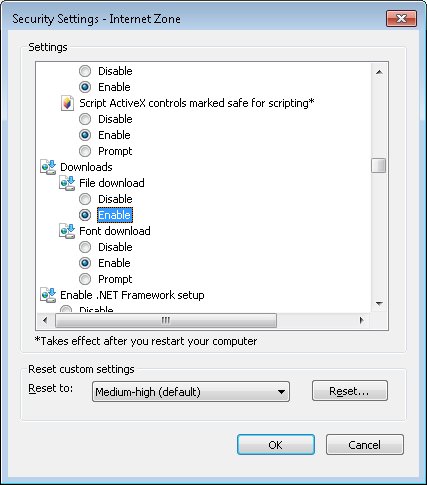
-
Click on the radio button next to "Enable".
- Click on OK.
- When asked "Are you sure you want to change the
settings for this zone?", click on Yes.
- Click on the OK button to close the
Internet Options window.
[/network/web/browser/ie]
permanent link
Sun, Dec 21, 2014 5:38 pm
CoolYou
A friend was complaining that his laptop, which runs Microsoft Windows 7 Home
Premium, was very slow, so he was considering purchasing another laptop.
I suggested he download and install
Malwarebytes Anti-Malware

and scan the system with that software. One of the
items it detected was CoolYou
(
image),
which it classified as
Trojan.Dropper.
[ More Info ]
[/security/malware]
permanent link
Sat, Dec 20, 2014 10:46 pm
Malwarebytes Anti-Malware detection for csrss.exe
A user reported that she saw a message on her system, which runs Windows 7
Professional, Friday morning December 19, 2014 indicating that malware had
been detected on her system by
Malwarebytes Anti-Malware

.
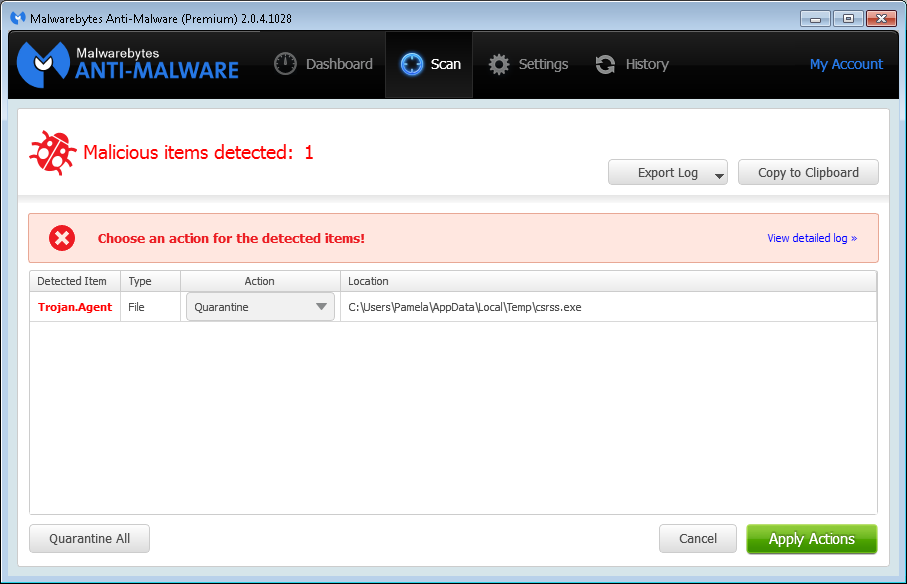
The file, which Malwarebytes identified as
Trojan.Agent, was csrss.exe was located in her
%TEMP% directory, i.e.,
C:\Users\Pamela\AppData\Local\Temp. There is a legitimate
Microsoft Windows file named csrss.exe, but that file is located in
C:\Windows\System32. The legitimate file on her system is
7,680 bytes in size and has a time stamp of 0/7/13/2009 08:39 PM. When
I checked the one Malwarebytes Anti-Malware was identifying as malware,
I saw it had the same size and time stamp.
C:\Windows>dir %TEMP%\csrss.exe
Volume in drive C is OS
Volume Serial Number is 4445-F6ED
Directory of C:\Users\Pamela\AppData\Local\Temp
07/13/2009 08:39 PM 7,680 csrss.exe
1 File(s) 7,680 bytes
0 Dir(s) 864,839,192,576 bytes freeI uploded the one Malwarebytes Anti-Malware flagged as malicious to
Google's VirusTotal site, which
analyzes uploaded files with many antivirus programs to determine if they
are safe or potentially dangerous. I had the site reanalyze the file, which
had been scanned previously. Zero of the fifty-four antivirus programs used
by the site to scan the file identified it as malware. The
SHA256 hash
listed for the file is
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a -
see the
report.
I ran a binary file comparison between the two files using the Microsoft
Windows fc utility. It found no differences between the two
copies of csrss.exe.
C:\Windows>fc /b %TEMP%\csrss.exe c:\windows\system32\csrss.exe
Comparing files C:\USERS\PAMELA\APPDATA\LOCAL\TEMP\csrss.exe and C:\WINDOWS\SYSTEM32\CSRSS.EXE
FC: no differences encountered
I had previously placed
md5deep, which can be downloaded from
md5deep and hashdeep, and its
associated utilities on the system. I used the 64-bit version, since
the system was running the 64-bit version of Microsoft Windows 7, of
sha256deep to check the SHA-256 hash for the version of the
csrss.exe file in C:\Windows\System32. It reported the same
SHA-256 hash as VirusTotal listed for the copy of the file I uploaded from
the users %TEMP% directory. I also checked the
MD5,
Tiger, and
Whirlpool
hashes for both files. For both files the MD5 hash was
60c2862b4bf0fd9f582ef344c2b1ec72 The Tiger hash function yieled a
hash of 42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b for both.
The Whirlpool hash was
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 for both files.
C:\Program Files\Utilities\File\md5deep>sha256deep64 c:\windows\system32\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>sha256deep64 %TEMP%\csrss.exe
cb1c6018fc5c15483ac5bb96e5c2e2e115bb0c0e1314837d77201bab37e8c03a C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 c:\windows\system32\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>md5deep64 %TEMP%\csrss.exe
60c2862b4bf0fd9f582ef344c2b1ec72 C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 c:\windows\system32\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>tigerdeep64 %TEMP%\csrss.exe
42e263a5861a1e3b8e411fec97994a32d2cdfc04cf54ab4b C:\Users\Pamela\AppData\Local\Temp\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 c:\windows\system32\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 c:\windows\system32\csrss.exe
C:\Program Files\Utilities\File\md5deep>whirlpooldeep64 %TEMP%\csrss.exe
def1e95668f22e06b605093df41d3bb635e7096860bb0adb6c405be49e723fb2497a8a2b64ca5d25519c4ba00c75facb0421bebc4df24f7c9918e0bb85f4c8f4 C:\Users\Pamela\AppData\Local\
Temp\csrss.exe
So I've no reason to suspect that the file in the %TEMP%
directory is any different than the one in the C:\Windows\Temp
directory. I thought that perhaps the only reason Malwarebytes
Anti-Malware flagged it to be quarantined is that it was an exe file in
the user's AppData\Local\Temp directory. It is possible that
I copied the file there previously when I was checking on various files
on the system when trying to eliminate a source of malware infection
on the system and that an update to Malwarebytes Anti-Malware now
has it mark any file in that directory as malware. I had Malwarebytes
Anti-Malware quarantine the file and then copied another legitimate
Microsoft Windows exe file, write.exe and also the
csrss.exe file from \C:\Windows\System32
into that directory just to see if Malwarebytes Anti-Malware would
flag them as malicious. It again detected csrss.exe as
malicious, but did not report the write.exe file I copied
into that directory from C:\Windows\system32 as malicious,
so it doesn't seem to be judging all .exe files in that folder as
potential threats, just certain ones.
[/security/antivirus/Malwarebytes]
permanent link
Sat, Dec 20, 2014 9:13 pm
Seagate external USB drive part number 9SF2A4-500
I have a
Power Adapters page where
I list the power adapters that are needed for various devices. I started
the page years ago after repeated instances where I had to figure out what
power adapter went with what device when an adapter got disassociated from
a device and either lost or jumbled with other adapters. To make it easier
for me to immediately associate an adapter with a device, I listed the
model/part number for a device and the model/part number for its power
adapter. I also list, when I can find a source, a site where a suitable
replacement adapter can be purchased. Now, whenever I encounter a device,
I try to immediately enter the power adapter information for it on my
web page. But today, I found a couple of power adapters next to a couple of
devices that I had jumbled together. And when I checked my web page I found
that I hadn't entered the power adapter information for either device.
I was fairly certain that I could
associate the right adapter with each advice, assuming that since the adapters
were near the devices that they were indeed the ones that went with those
devices, but while double-checking
on the adapter for a Seagate USB external drive with part number
9SF2A4-500, I came across
Felix's Blog, a blog from another
person providing tech support, by Marcel "Felix" Giannelia of Terrace, BC,
Canada who provides
Disassembly instructions for Seagate 1 TB Expansion
External Drive (9SE2A4-571 or 9SF2A4-500).
I've copied his instructions to my own site
here,
so that I have a copy should the author's site, or even
just these instructions, disappear, since he states at
Welcome to Felix's little Knowledge Base
thing that "I've been even sloppier about copyright in the files
I've written myself. I intend the ones I wrote myself to be in the public
domain." According to his disassembly instructions, the drive inside the
Seagate External Expansion case is a Seagate Barracuda 7200.12 model
ST31000528AS

.
Checking other postings's to the author's site, I found
"Do NOT paraphrase when calling tech support", which links to
an email
he sent to a user regarding the user's paraphrasing an error message for
the Eudora email
client, a program I once used many years ago and which users
I supported once used.
I can certainly emphasize with his posting; many years ago when I was a sysadmin for
a Digital Equipment Corporation (DEC)
VMS system, a user
contacted me about a problem with one of her databases on the system. She
gave me the error message and, since DEC very nicely provided documentation
for the database software listing possible error messages and steps to take
to rectify the problem associated with a particular error message, I referred
to that documenation and found it listed an error message that was a very
close match to the one the user gave me. After spending a couple of hours
checking all of the possibilities listed for that error message, I contacted
the user and had her recreate the problem. When she then read me the exact
error message, I realized it was quite different than what she had paraphrased
from memory previously. Once I had the exact error message, it only took me
a few minutes to fix the problem, but I had wasted hours on the problem before
that because she hadn't written down the exact message, but gave me a
paraphrased version. One user takes snapshots of error messages on her
computer screen with her phone now and sends them to me; that's very helpful,
since I can see the window containing the error message and its exact
contents.
I also found his "Why cats save humans from house fires" amusing, though
the smoke alarm has almost never gone off in our house due to food
preparation. It did go off one time when I put the tea kettle on the stove
to heat water for tea and then went into another room to work on a
computer. I didn't hear the tea kettle whistling; when the smoke alarm
went off I went into the kitchen and found that all of the water in the
tea kettle had boiled off and there was a burning puddle of plastic next
to the tea kettle due to the plastic on the handle melting. Our cats
didn't like the blaring smoke alarms throughout the house.
In another posting by Felix, I found an adapter that will also be useful
to me, since it supports both IDE, aka PATA, drives as well as
SATA hard disk drives listed in his a "Product Plug!" posting
for a "Ultra USB 2.0 to IDE/SATA Cable for 2.5-Inch/ 3.5-Inch /
5.25-Inch Drive with Power Adapter", which he notes is a "a USB
to any-kind-of-hard-drive adapter. That is, it's got a USB plug on
one end, and all the kinds of hard drive connector mashed together
on the other end. I just ordered one, because this is going to
save me so much time disassembling USB enclosures". His link was to the ULT40112
on the TigerDirect.ca site, i.e., the Canadian site
for TigerDirect; it is available in the U.S. from
TigerDirect.com. I have devices that provide
USB connectivity for hard drives that aren't in an enclosure, but none that
support both IDE, aka PATA, and SATA drives.
Unfortunately, the plug on the Asian Power Devices WA-24E12 (output 12V 2A)
power adapter I found near the drive that I thought went with the drive
would not plug into the drive, even though according to information
I found elsewhere online it should have worked for that drive. Another
12V 2A adapter, model ADS-24F-12 1224GPCU, I tried from another Seagate
external USB disk drive enclosure did connect easily, though.
Seagate® Expansion™ External Data Sheet

[/hardware/storage/Seagate]
permanent link
Sat, Dec 20, 2014 5:38 pm
Checking the warranty on a Segate drive
If you want to check whether a Seagate disk drive is still under warranty,
you can do so at either the
Warranty Validation or the
Customer Returns page. You can check the warranty for an internal
hard disk drive or an external USB drive.
You will need to complete fields on the form for the following information:
- Serial Number
- Product Number / Model Number
- Country
If the warranty is expired, you will see "Warranty is expired for the
entered Product/Serial". You won't see the date that the warranty expired on.
[/hardware/storage/Seagate]
permanent link
Sat, Dec 20, 2014 1:58 pm
Viewing history of DNS server and IP Changes for a Domain
If you wish to view a history of
Domain Name System
(DNS) server changes for a domain name, you can do so through
the
WhoISrequest Domain History
Checker, which tracks nameserver changes since 2002 for all COM, NET, ORG,
INFO, BIZ and US domains.
E.g., if I put
sailormoonworld.com, which was registered in 1998, in the search field, I
can see a list of all of the DNS servers that translated the
fully
qualified domain name (FQDN) to an IP address since WhoISrequest began
tracking name server changes in 2002. The history information for that
particular domain shows that registration for the domain name lapsed in
2013 and the domain name was picked up by a
domain name squatter
then. The domain name squatter let the domain registration lapse in the
summer of 2014. I re-registered the domain name for the original owner, a
family member, in October.
You can also view such information through the
DNS History site, which notes
"Here at DNS History we have been crawling DNS records since 2009, our index
currently contains over 200 million domains and discovering over a billion DNS
records."
If I put sailormoonworld.com in the Doman Search field on that site,
though, it does not have any information on it, though it does have information
on moonpoint.com, though that information was last updated on 2010-08-11, so
that site's information does not appear to be as comprehensive nor as
up-to-date as the information provided through the WhoISRequest site.
You can also find past name server and registration information through
the who.is Search Domain DNS and Name Server
Information page. When you put a domain name in the search field,
and click on "Search DNS and Name Servers", you will see information
on the domain, such as name servers, SOA record, DNS records, including
the mail exchanger (MX) servers for the domain. If you click on the
History tab above that information, you will see past domain
name registrars and name servers associated with the domain.
If you wish to see prior IP addresses associated with a domain name,
you can use ViewDNSInfo IP
History. I noticed when I checked sailormoonworld.com with
its tool, though, that it is not showing a change made near the end of October
for that domain. The last change it shows was for 2014-07-05. The site also
has a lot of other tools, e.g.
Google Pagerank Checker, etc.
[/network/dns]
permanent link
Thu, Dec 18, 2014 10:53 pm
Finding files by modification date in Windows
If you need to search a Microsoft Windows for files modified on a
particular date or within a specific time span, you can use the
datemodified qualifier within the Windows Explorer.
[ More Info ]
[/os/windows/explorer]
permanent link
Sun, Dec 14, 2014 6:05 pm
Determining the accounts in the administrators group form a command prompt
To determine the accounts in the administrators group for a Microsoft
Windows system, you can use the command
net localgroup administrators
C:\Users\Administrator>net localgroup administrators
Alias name administrators
Comment Administrators have complete and unrestricted access to the computer/domain
Members
-------------------------------------------------------------------------------
Administrator
JDoe
mayberry\Administrator
mayberry\Domain Admins
SvcCOPSSH
The command completed successfully.
[/os/windows/commands]
permanent link
Sun, Dec 14, 2014 5:45 pm
Copssh Connection Issues
When I tried connecting to a Windows 7 Professional system running Copssh 5.0.1 from
PuTTY
0.58 on a Windows Small Business Server (SBS) 2003 system, a "PuTTY Fatal Error"
window appeared with the message "Couldn't agree a client-to-server cipher
(available: aes128ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com)".
I tried connecting from the same system with an OpenSSH_3.8.1p1 SSH client
that is part of
OpenSSH for
Windows and received the message "no kex alg", which may mean "no
key-exchange algorithm". When I tried specifying the encryption cipher using
the OpenSSH client, I received an error message similar to the one I saw
with PuTTY.
C:\Program Files\SSH\OpenSSH\bin>ssh -c 3des jdoe@192.168.0.15
no matching cipher found: client 3des-cbc server aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
C:\Program Files\SSH\OpenSSH\bin>ssh -c blowfish jdoe@192.168.0.15
no matching cipher found: client blowfish-cbc server aes128-ctr,aes192-ctr,aes256-ctr,aes128-gcm@openssh.com,aes256-gcm@openssh.com,chacha20-poly1305@openssh.com
When I tried connecting from the SBS 2003 system to another system, to
which I could successfully connect with the OpenSSH SSH client, when I
specified the -v option for debugging output with ssh -v
jdoe@example.com, I saw the following:
debug1: Remote protocol version 2.0, remote software version OpenSSH_6.4
debug1: match: OpenSSH_6.4 pat OpenSSH*
debug1: Enabling compatibility mode for protocol 2.0
debug1: Local version string SSH-2.0-OpenSSH_3.8.1p1
debug1: SSH2_MSG_KEXINIT sent
debug1: SSH2_MSG_KEXINIT received
debug1: kex: server->client aes128-cbc hmac-md5 none
debug1: kex: client->server aes128-cbc hmac-md5 none
I upgraded PuTTY on the client system from version 0.58 to 0.63. I then no
longer received the message about no matching cipher being found, but, instead
saw another "PuTTY Fatal Error" window open, this time with the message
"Network error: Software caused connection abort". I saw the same error
message when I used PuTTY's plink utility from the command line.
C:\Program Files\Network\SSH\PuTTY>plink -ssh jdoe@192.168.0.15
Using username "jdoe".
jdoe@192.168.0.15's password:
FATAL ERROR: Network error: Software caused connection abort
I installed Bitvise
SSH Client (Tunnelier) 6.08 and tried connecting with
that client. Like with PuTTY, after I authenticated with the SSH server, I
was immediately disconnected. I saw the following from Tunnelier:
First key exchange completed using ecdh-sha2/nistp521. Session encryption:
aes256-ctr, MAC: hmac-sha2-256, compression: none.
Attempting password authentication.
Authentication completed.
The SSH2 session has terminated with error. Reason: FlowSocketReader: Error
receiving bytes. Windows error 10054: An existing connection was forcibly closed
by the remote host.
When I was able later to connect to the system running Copssh via
RDP for
troubleshooting after the user had left for the day, I
checked its status log, which you can do on a Windows 7 system by the following
steps:
- Click on Start.
- Select All Programs.
- Select Copssh.
- Select Copssh Control Panel.
- Under the Status tab, you will see
an icon that looks like a piece of paper with one edge folded down. You
may also see something like "6 events last 15 minutes" next to it.
Double-click on that icon.
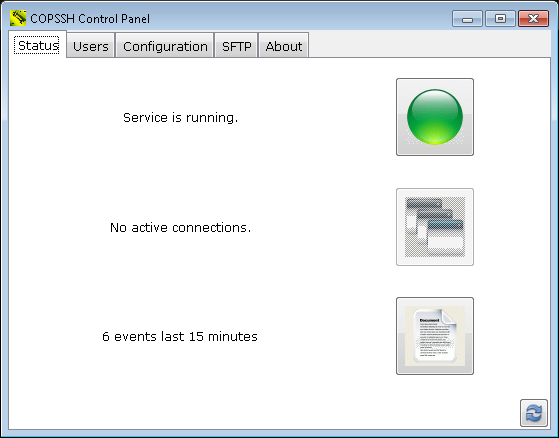
When I checked the log, I saw many "fatal: mm_request_receive: read: Connection reset by peer" messages. There was a "Received SIGHUP; restarting" entry
hours later.
2014.12.12 23:26:23 - Received SIGHUP; restarting.
2014.12.12 18:30:02 - fatal: mm_request_receive: read: Connection reset by peer
Seeing that, I tried establishing a connection with PuTTY again
and was then able to log in by SSH successfully.
But then when I tried logging in remotely by SSH two days later the problem
was back. I restarted the service within the Copssh Control Panel by clicking
on the green button next to "Service is running" to stop the service. When
the button turned red, I clicked on it again to restart the service, but that
didn't resolve the problem; I still got the "Network error: Software
caused connection abort" message when I tried connecting via PuTTY 0.63 and
I saw the "fatal: mm_request_receive: read: Connection reset by peer" message
in the Copssh log for evey connection attempt. Though I didn't expect it
to resolve the problem, I tried the "net stop" and "net start" commands from
a command prompt.
C:\Users\Administrator>net stop "OpenSSH SSHD"
The Openssh SSHD service is stopping.
The Openssh SSHD service was stopped successfully.
C:\Users\Administrator>net start "OpenSSH SSHD"
The Openssh SSHD service is starting.
The Openssh SSHD service was started successfully.
But that did work. I was then able to successfully log into the system
via SSH.
[/os/windows/network/ssh/copssh]
permanent link
Sun, Dec 14, 2014 5:10 pm
Ripping a CD with Microsoft Windows Media Player 12
To rip a CD to the music libary stored on your system, i.e., to copy the music
from the CD to the hard drive on a Windows sytem, using Windows Media Player
12, take the following steps:
-
Insert the CD in the CD/DVD drive in the system.
-
Start the Windows Media Player application.
-
On the left pane of the Windows Media Player window, navigate
to the location of the CD/DVD drive, which should be displaying the
album as shown below where the album is identified as "unknown album"
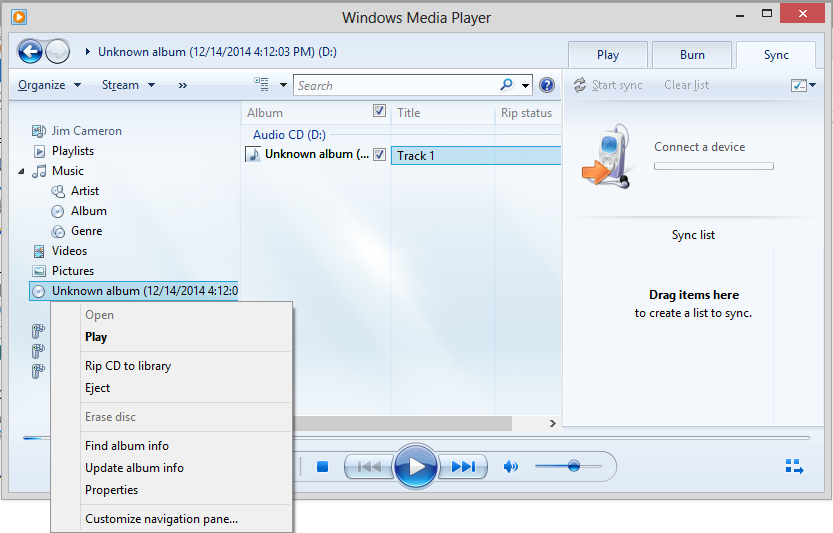
-
Right-click on the CD in the left pane of the window and choose "Rip CD to
library. As the CD is "ripped", you should see the status displayed
under "Rip status" near the top of the window; status information is
also displayed in the lower, right-hand side of the window.
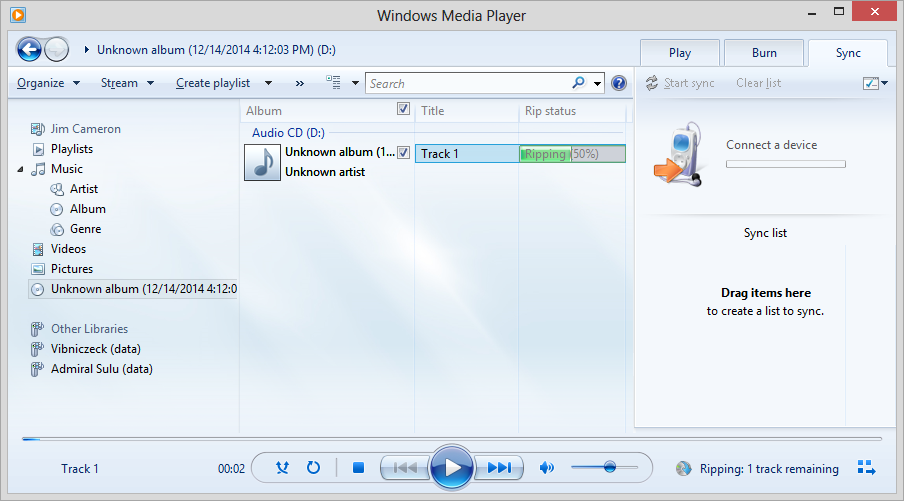
The status under "Rip status" should change to "Ripped to library" at
the completion of the rip process.
On a Microsoft Windows 7 system, you should then see the name of the
album in your music folder under Libraries\Music or
C:\Users\Username\Music\, where Username is
the name for the account under which you logged into the system, if you
look for it using the Windows Explorer. If the
album/artist could not be identified by Windows Media Player, you may
see an "Unknown artist" folder with an "Unknown album" folder within it.
From the Windows Explorer, you can right-click on the folder names and
change them, if you wish.
[/os/windows/software/audio-video/WMP]
permanent link
Fri, Dec 12, 2014 11:54 pm
DNSQuerySniffer v1.35
I installed DNSQuerySniffer v1.35 on a Microsoft Windows Professional
system which has been generating a lot of unusual DNS and HTTP traffic
even when the owner of the system is not using the system. E.g., I've seen
a lot of such traffic overnight, far more than can be accounted for by
normal processes running and checking on available updates, etc. And the
websites being contacted are not ones I would expect to be contacted.
DNSQuerySniffer allows the DNS queries and responses from DNS servers to
the system on which the software is installed to be monitored and captured for
later analysis.
[
More Info ]
[/os/windows/software/network/dns]
permanent link
Wed, Dec 10, 2014 11:53 pm
SysRescueCd
If you need to boot a system outside of the operating system residing on its
hard disk drive, a
live CD or
DVD provides a means to boot the system from an optical drive with an
operating system that is on the CD or DVD. There are many Linux-based live CDs,
which can be used to boot and troubleshoot systems running Microsoft Windows as
well as those running Linux. Many Linux-based live CDs have antivirus, backup
utilities, etc. that facilitate troubleshooting and maintenance of Windows
systems. One such live CD is
SystemRescueCd.
[ More Info ]
[/os/unix/linux]
permanent link
Tue, Dec 09, 2014 11:32 pm
Microsoft Visual C++ Runtime Error from Dell Stage
On a Dell desktop system running Microsoft Windows 7 Professional,
for awhile now whenever the user logged into her account, a Microsoft Visual
C++ Runtime Library window opened with the following information displayed:
Runtime Error!
Program: C:\...
This application has requested the Runtime to terminate it in an
unusual way.
Please contact the application's support team for more information.
[ OK ]
Checking on the application that was creating the window, I found it
to be "Dell Stage", which was software preinstalled on the system, which
I uninstalled.
[ More Info ]
[/os/windows/software]
permanent link
Sun, Dec 07, 2014 10:45 pm
Scan of Windows system with Malwarebytes Anti-Malware on 2014-12-07
When I scanned a Windows 7 Professional system with Malwarebytes Anti-Malware
it reported a file associated with
PUP.Optional.TorchMedia, which I had it
remove.
[ More Info ]
[/security/malware]
permanent link
Sun, Dec 07, 2014 7:30 pm
Rotate the DNS server log file on a Windows server
For a site where a
Windows Small Business Server (SBS) 2003 system serves as a
DNS server, I
wanted to rotate the DNS log file every night at midnight. The log file is
named
DNS.log and I'd like to close the current log at
midnight renaming it to
DNS_YYYYMMDD.log where YYYY is the 4-digit
year, MM, the month (1-12) and DD the day (1-31). The system date can be put in
the format
YYYYMMDD using substring extraction as explained at
Appending a date to a filename in
batch files.
Renaming the log file requires stopping the DNS server service, which
can be done with the command net stop "DNS Server". If
you try to move the file without stopping the service, you will receive
the message below:
D:\Logs\DNS>move dns.log dns_old.log
The process cannot access the file because it is being used by another process.
0 file(s) moved.After the file is moved/renamed, the DNS server service can be restarted
with net start "DNS Server".
The location of the DNS log file is stored in the Windows Registry. A
REG QUERY command can be used to obtain the current location for
the file as explained at
Determing the location of a Microsoft Windows DNS log file from a command prompt. After the location and name of the file is determined, the DNS server
service can be stopped, then the current log file can be renamed, and the
DNS server service can be restarted, creating a new log file with the name
and at the location indicated by the registry entry.
The batch file is shown below and is available
here.
@echo off
REM Name: rotatednslog.bat
REM Version: 1.0
REM Created: December 6, 2014
REM Last Modified: December 6, 2014
REM
REM: Location of latest version:
REM: http://support.moonpoint.com/downloads/computer_languages/mswin_batch/rotatednslog.bat
REM
REM Description: When scheduled to run at the end of each day, this batch
REM file will roate the DNS server log. The DNS server service will be
REM stopped temporarily, so the current DNS log can be renamed to a log file
REM with the name DNS_YYYYMMDD.log, where YYYY is the year, MM the month, and
REM DD the day. The DNS server service will then be restarted creating a
REM new DNS log file. The current location of the DNS log file is obtained
REM from the Windows Registry.
REM Required for substituting the contents of a variable in string subsitution
REM employed to insert the contents of the date variable YYYYMMDD in the log
REM file name.
SETLOCAL ENABLEDELAYEDEXPANSION
REM Windows Registry key holding the location of the DNS log file
SET regkey="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters"
REM Registry value needed from the above key
SET regvalue="LogFilePath"
REM Extract only the file location from the output of the reg query command
FOR /F "tokens=3" %%G IN ('reg query %regkey% /v LogFilePath ^| find %regvalue%') DO set logfile=%%G
REM Set the variable YYYYMMDD to today's date in YYYYMMDD format where
REM YYYY = 4-digit year, MM is month (1-12), and DD is day (1-31)
SET YYYYMMDD=%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%
REM Set the name for the rotated log file to have "_YYYYMMDD.log" at the
REM end of the file name. Need to use delayed expansion.
SET renamedlog=!logfile:.log=_%YYYYMMDD%.log!
REM Stop the DNS server service
NET STOP "DNS Server"
REM Move the log file to its new location with its new name.
REM Since you cannot specify a new drive or path for your destination file with
REM the RENAME command, I'm using the MOVE command, instead, in case I may
REM wish to update this batch script to move the file to another drive and/or
REM directory.
MOVE %logfile% %renamedlog%
REM Restart the DNS server service
NET START "DNS Server"
If it is run from a command prompt, you will see the following output:
C:\Program Files\Utility\Scripts>rotatednslog
The DNS Server service is stopping.
The DNS Server service was stopped successfully.
1 file(s) moved.
The DNS Server service is starting.
The DNS Server service was started successfully.Since I would like the batch file to execute at the end of each day, I
scheduled it to run at 23:59 (11:59 PM) Monday through Sunday with the command
at 23:59 /every:m,t,w,th,f,s,su
"C:\program files\utility\scripts\rotatednslog.bat (specify the location
for the batch file).
C:\Program Files\Utility\Scripts>at 23:59 /every:m,t,w,th,f,s,su "C:\program files\utility\scripts\rotatednslog.bat"
Added a new job with job ID = 5
I could have used 00:00 to run the batch job at midnight, but
I set it to run 1 minute before midnight to be sure that the date inserted
in the name of the file is the one for the day that has just ended rather than
the date of the new day.
If you want to see the details of scheduled batch jobs, you can just
enter at without any parameters at the command line and hit
return. You will then see all the scheduled batch jobs. There may be gaps
in the ID numbers if some batch jobs have been deleted.
C:\Documents and Settings\Administrator>at
Status ID Day Time Command Line
-------------------------------------------------------------------------------
1 Each M T W Th F S 7:30 PM d:\backups\daily.bat
2 Each Su 7:30 PM d:\backups\weekly.bat
5 Each M T W Th F S Su 11:59 PM "C:\program files\utility\scripts\rotatednslog.bat"If you wish to delete a scheduled batch job you can use
at id /delete, where id is the numeric
ID assigned to a batch job. E.g., the rotatednslog batch job above could
be deleted with at 5 /delete.
[/network/dns/windows]
permanent link
Fri, Dec 05, 2014 11:27 pm
Determine the file name and extension from a string containing path and filename
For Microsoft Windows systems, if you have a string or variable holding the
complete path to a file and the file name and extension, but you wish to have
just the file name and the extension of the file you can use
%~nx1
which will expand the batch parameter expansion variable
%1 to a
file name and extension.
Other modifiers you can use in expansion are as follows:
| Modifier | Description |
|---|
| %~1 |
Expands %1 and removes any surrounding quotation marks (""). |
| %~f1
| Expands %1 to a fully qualified path name. |
| %~d1 |
Expands %1 to a drive letter. |
| %~p1 |
Expands %1 to a path. |
| %~n1 |
Expands %1 to a file name. |
| %~x1 |
Expands %1 to a file extension. |
| %~s1 |
Expanded path contains short names only. |
| %~a1 |
Expands %1 to file attributes. |
| %~t1 |
Expands %1 to date and time of file. |
| %~z1 |
Expands %1 to size of file. |
| %~$PATH:1 |
Searches the directories listed in the PATH environment variable and
expands %1 to the fully qualified name of the first one found. If the
environment variable name is not defined or the file is not found, this
modifier expands to the empty string. |
Combinations of modifiers and qualifiers that you can use to get compound
results are shown in the table below:
| Modifier | Description |
|---|
| %~dp1 |
Expands %1 to a drive letter and path. |
| %~nx1 |
Expands %1 to a file name and extension. |
| %~dp$PATH:1 |
Searches the directories listed in the PATH environment variable for %1
and expands to the drive letter and path of the first one found.
|
| %~ftza1 |
Expands %1 to a dir-like output line. |
In the examples above, you can use other batch paramters besides
%1 and PATH. Cmd.exe provides the batch parameter
expansion variables %0 through %9.
Batch parameters can't be manipulated in the same manner that you can
manipulate environment variables. You can't search and replace values or
examine substrings within them. You can, however, assign the parameter to an
environment
variable and then manipulate the environment variable.
So, if I wanted just the file name dns.log from
d:\logs\dns.log, I could use the following in a batch file:
@echo off
call :getfilename "d:\logs\dns.log"
exit /b
REM Determine just the file name
:getfilename
echo %~nx1
If I have the above batch commands in a file called test.bat,
I would see the following when I ran it.
C:\Users\JDoe>test.bat
dns.log
If there is a
Windows Registry key containing the file location and I want to query
that key and extract just the file name, I could use commands such as
the following if the file location was stored in LogFilePath
for the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters:
@echo off
REM Regkey is set to the registry key containing the location of the DNS log
REM file
set regkey="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters"
REM Regvalue is set to the value that is desired from the above registry key
set regvalue="LogFilePath"
REM log_file_location is set to contain the complete path to the log file nad
REM its name, e.g., d:\logs\dns\dns.log
FOR /F "tokens=3" %%G IN ('reg query %regkey% /v LogFilePath ^| find %regvalue%') DO set log_file_location=%%G
call :getfilename %log_file_location%
exit /b
REM Determine just the file name
:getfilename
echo %~nx1
References:
-
Using batch parameters
Microsoft Corporation
-
Determing the location of a Microsoft Windows DNS log file from a command prompt
Date: November 22, 2014
MoonPoint Support
[/os/windows/commands]
permanent link
Fri, Dec 05, 2014 12:45 pm
Using tcpdump on OS X
When I tried running
tcpdump
on a MacBook Pro laptop running Mac OS X 10.8.5 from an account that
was configured to "Allow user to administer this computer" in System
Preference/Users & Groups, I received a "no suitable device found" message.
$ tcpdump
tcpdump: no suitable device found
The problem can be addressed by changing the ownership or permissions
of the Berkeley Packet Filter (BPF) file in /dev. The default
permissions and ownership are shown below:
$ ls -l /dev/bpf*
crw------- 1 root wheel 23, 0 Nov 30 22:42 /dev/bpf0
crw------- 1 root wheel 23, 1 Dec 4 21:45 /dev/bpf1
crw------- 1 root wheel 23, 2 Dec 4 15:39 /dev/bpf2
crw------- 1 root wheel 23, 3 Nov 30 22:41 /dev/bpf3
To resolve the problem, I changed the ownership of the bpf0
file to the account I was using:
$ sudo chown jdoe /dev/bpf0
Password:
I also checked to see what the designation was for the wireless adapter
in the system. It was en1.
$ networksetup -listallhardwareports
Hardware Port: Bluetooth DUN
Device: Bluetooth-Modem
Ethernet Address: N/A
Hardware Port: Ethernet
Device: en0
Ethernet Address: d4:9a:20:0d:e6:cc
Hardware Port: FireWire
Device: fw0
Ethernet Address: d4:9a:20:ff:fe:0d:e6:cc
Hardware Port: Wi-Fi
Device: en1
Ethernet Address: f8:1e:df:d9:2b:66
VLAN Configurations
===================
I then tried again to run tcpdump specifying the wireless interface; this
time I received a "You don't have permission to capture on that
device message with a reference to bfp1, so I changed
the ownership on that file as well. I was then able to observe
traffic with tcpdump.
$ sudo chown jdoe /dev/bpf0
$ tcpdump -i en1
tcpdump: en1: You don't have permission to capture on that device
((no devices found) /dev/bpf1: Permission denied)
$ sudo chown jdoe /dev/bpf1
$ tcpdump -i en1
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on en1, link-type EN10MB (Ethernet), capture size 65535 bytes
I changed the ownership back to root on /dev/bpf0 to see if I could still run
tcdump, but when I did so I was no longer able to observe network traffic with
tcpdump.
$ sudo chown root /dev/bpf0
$ tcpdump -i en1
tcpdump: en1: You don't have permission to capture on that device
((no devices found) /dev/bpf0: Permission denied)
I could have just changed ownership of all of the bpfx files
in /dev initially with sudo chown jdoe /dev/bbf*, but
I wanted to determine if I only needed to change a specific one for the wireless
interface, en1. Alternatively one can expand the
permissions on those files, e.g., one can use sudo chmod 644
/dev/bpf*. When the system is rebooted the permissions/ownership
will be reset, so you will have to take the same steps to run tcpdump
subsequent to a reboot of the system.
I specifically wanted to check on
DNS
queries, so, after changing the ownership for the bpf file back to the account
I was using, I specified port 53, but saw no data.
$ tcpdump -i en1 'port 53'
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
I wasn't able to observe the DNS traffic until I ended the
VPN connection I was using
when I ran the command. Once I disconnected from the VPN, I was able
to check on the DNS queries from the system and the responses from a DNS
server.
References:
-
Tcpdump Permission Denied on OS-X
Date: June 12, 2007
MoonPoint Support
-
Managing Wi-Fi from the terminal command line under OS X
Date: February 28, 2014
MoonPoint Support
-
No Interfaces Available In Wireshark Mac OS X
Date: January 31, 2010
langui.sh Languishing since 2008.
[/os/os-x]
permanent link
Tue, Dec 02, 2014 9:45 pm
Shellshock Vulnerability on OS X Systems
You can test a system to determine if it may be vulnerable to being
exploited through the
shellshock, aka bashdoor, vulnerability using the command
env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'.
If it is vulnerable, you will see the commands executed that appear after
the semicolon. On vulnerable systems,
Bash is
executing commands that are concatenated at the end of function
definitions stored in the contents of environment variables.
When I checked a MacBook Pro running, OS X 10.8.4, I saw output indicating
it was vulnerable, i.e., I saw "vulnerable" displayed when the command was run.
The check can be performed by opening a Terminal window and entering the code.
The terminal application is in Applications/Utilities.
$ env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'
vulnerable
this is a testA bash shell prompt could be otained by a malicious remote user
if Remote Login was enabled and Guest Access was also enabled,
though, hopefully, if Remote Login was enabled, Guest Access would
not be enabled. Of course, a malicious person could also gain access to the
system remotely if Remote Login is enabled and a weak password is present
for an account on the system that is allowed remote access.
A OS X system could also be vulnerable if it is functioning as a web
server and there are scripts present on the server that would allow an
attacker to provide any input he wishes that could be executed as code by the
script.
Apple released a fix for the vulnerability for OS X systems on September
29, 2014.
After the laptop was upgraded to OS X 10.8.5 and security updates were
applied, I didn't see "vulnerable" displayed when the code was executed.
$ env x='() { :;}; echo vulnerable' bash -c 'echo this is a test'
this is a testAnd when I tested the related vulnerability
CVE-2014-7169, the date was no longer displayed.
$ env X='() { (a)=>\' sh -c "echo date"; cat echo
date
cat: echo: No such file or directory
A system that has been patched for both
CVE-2014-6271 and CVE-2014-7169 will simply echo
the word "date" and the file "echo" will not be created, as shown above.
References:
-
Shellshock Vulnerability: What Mac OS X users Need to Know | The Mac
Security Blog
By
Derek Erwin
Date: September 26, 2014
Intego - Mac Antivirus & Security
-
Shellshock (software bug)
Wikipedia
[/security/vulnerabilities/multios]
permanent link
Mon, Dec 01, 2014 10:32 pm
Searching for messages in Outlook 2010
Microsoft Outlook 2010 provides a means to quickly search through email
for particular messages by specifying multiple criteria in its search
field. It also provides the means to use
logical operators,
such as
NOT to exclude some messages that you deem not pertinent.
[ More Info ]
[/network/email/clients/outlook]
permanent link
Sat, Nov 29, 2014 2:02 pm
Creating a Windows 8 System Repair Disc
For any Microsoft Windows system, you should ensure that you have a
Microsoft Windows Repair Disc to aid in recovering from problems before
you experience some problem on the system that makes the system unbootable.
A Windows Repair Disc is a bootable disc that can be created inside
Microsoft Windows which will contain a number of repair tools that will
allow you to recover from some types of problems that can make a system
unbootable from the hard drive. Steps to create a repair disc in Windows 8
are posted
here.
[/os/windows/win8]
permanent link
Wed, Nov 26, 2014 11:28 pm
Logging on a Verizon MI424WR-GEN2 Router
The Actiontec MI424WR-GEN2 router/firewall provided by Verizon to business
clients has a system log that is viewable by logging into the router and
also supports sending logging information to a syslog server. The steps
to view the log and/or set the device to send information regarding
connections through the firewall can be found
here.
[/network/routers/actiontec/MI424WR]
permanent link
Wed, Nov 26, 2014 8:49 pm
Opening a file in Chrome
If you need to open a file on your hard drive in Google's Chrome browser,
you can use the keyboard shortcut
Ctrl-O, i.e., by hitting the
Ctrl and
O keys simultaneously. Or, if you want to open
a file on drive C: on a Microsoft Windows system, you can put
C:\
in the browser's address bar. The address will change to
file:///C:/, i.e., the word "file" followed by a colon and
3 forward slashes and then the drive letter specified, colon, and forward
slash, which conforms to the standard
file URI scheme
for accessing file-based URLs. You can then navigate to the file you wish to
open in the browser. Or, if you know the full path, you can put it in the
address bar, e.g.,
c:\users\jdoe\documents\index.html.
[/network/web/browser/chrome]
permanent link
Wed, Nov 26, 2014 6:58 pm
Turning McAfee Total Protection Real-time protection off
Sometimes you may wish to temporarily disable the antivirus software
on a system in order to scan the system with other antivirus/antispyware
software. If you are using McAfee Total Protection as the antivirus
software on a system, instructions for turning off its real-time scanning
feature are listed
here.
[/security/antivirus/mcafee]
permanent link
Tue, Nov 25, 2014 10:35 pm
Checking on process memory consumption on a Windows system
Sometimes when checking on excessive memory usage on a Microsoft Windows
system with the
Task Manager I see that many instances of a
particular process may be listed. I wanted a way from a command
prompt to total the amount of memory consumed by processes
with a particular name, e.g. chrome.exe, so I created a
showmemusage.bat batch file to allow me to specify a particular
process name and then have the script add the memory usage for all
processes with that name.
[ More Info ]
[/os/windows/commands/batch]
permanent link
Sun, Nov 23, 2014 11:20 pm
Copssh 5.0.1
If I will need to remotely troubleshoot a system, I like to have the
system functioning as an
SSH server, so that I have a means to log into the system over an
encrypted connection to a command line interface. Microsoft Windows
sysems don't come with SSH server software from Microsoft, but there are
third-party applications that allow you to set up a Microsoft Windows
system as an SSH server. By using an SSH connection to obtain a Windows
command prompt, I can log into the system for troubleshooting while the
user continues to work on the system without interfering with the user's
work. One software package that I've found that works well for that purpose is
Copssh (Gygwin + OPenSSH).
[ More Info ]
[/reviews/software/windows/network/ssh]
permanent link
Sat, Nov 22, 2014 11:46 pm
Appending a date to a filename in batch files
I wanted to append today's date to a file name for a file processed by a batch
job on Microsoft Windows systems, specifically a Small Business Server
(SBS) 2003 system and Windows 7 and 8 systems. You can obtain the current
date using the
date /t command (the
/t
option prevents the command from prompting for a change to the date)
or by using
echo %date% to display the contents of the
date environment variable. However, both of those display the date in
the form
DDD mm/dd/yyyy, where
DDD is the
day of the week represented by a 3-character abbrviation, e.g., "Sat",
mm is a two-digit representation of the month, e.g., "11"
for November,
dd is the day and
yyyy is the
year, on the Windows systems I support.
C:\>date /t
Sat 11/22/2014
C:\>echo %date%
Sat 11/22/2014
You can reformat the representation of the date that is stored in the
%date% environment variable, however. I wanted the date in the
form yyyymmdd, so that I could stick that at the end of filenames
to represent the rotation date for a log file. You can use a command like the
one below where a variable, YYYYMMDD is set to hold the reformatted
date (the variable name can be anything you like, e.g., mydate, etc., but that
name reminds me of the format I'm using for the date.
C:\>set YYYYMMDD=%DATE:~10,4%%DATE:~4,2%%DATE:~7,2%
C:\>echo %YYYYMMDD%
20141122
The substring arguments to extract the elements of the date string are
in the format %variable:~startposition,numberofchars%, so if the
"S" in Saturday in the string "Sat 11/22/2014" is at position 0, the
10th character is the "2" of 2014 and I want 4 characters, i.e., "2014", so
%DATE:10,4% will give me those characters. Or you can also
think of the first number as the numer of characters to be skipped, i.e.,
%variable:~num_chars_to_skip,numberofchars%. I can then append
%DATE:~4,2% to get "11" for the month followed by
%DATE:~7,2% to extract the day, i.e., "22" if the date is
November 22, 2014 represented in the %DATE% variable as "Sat 11/22/2014".
References:
-
How to append a date in batch files
Posted: May 14, 2009
stackoverflow
-
Extracting a Substring from a String under Microsoft Windows
MoonPoint Support
[/os/windows/commands]
permanent link
Sat, Nov 22, 2014 10:00 pm
Items detected by a ClamWin Scan on 2014-11-22
In continuance of an effort to ensure that all malware has been removed
from a Windows 7 Professional system, I scanned the system with
ClamWin Free Antivirus today.
It identified 12 suspect items, but I'm not sure any of those contributed
to excessive memory usage I saw at times on the system yesterday from
explorer.exe consuming more than 1/2 the 6 GB of memory on the system
for prolonged periods.
[ More Info ]
[/security/malware]
permanent link
Sat, Nov 22, 2014 12:25 pm
Determing the location of a Microsoft Windows DNS log file from a command prompt
If you need to determine the location of the log file for a Microsoft Windows
server functioning as a DNS server from the command line, you can do so through
a
reg query command.
C:\>reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters /v LogFilePath
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters
LogFilePath REG_SZ d:\logs\dns\dns.logYou can reduce the output displayed to just the line containing the
log file location by piping the output of the reg query command
into the find command.
C:\>reg query HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters /v LogFilePath | find "LogFilePath"
LogFilePath REG_SZ d:\logs\dns\dns.logIf you wish to see just the log file location and not the other information
returned by the reg query command, you can use
a FOR /F loop command such
as the following:
C:\>for /f "tokens=3" %g in ('reg query "HKLM\SYSTEM\CurrentControlSet\Services\DNS\Parameters" /v LogFilePath ^| find "LogFilePath"') do @echo %g
d:\logs\dns\dns.log
C:\>The FOR /F loop breaks up a line of output from the command
that is being processed into items, called "tokens" that are separated by
space on the lines of output from the command. In this case, I'm only
interested in the third token on the line of output, which is the location
of the DNS log file. The output that is being processed is the result of
piping the output of the reg query command into the find
command. Since the pipe symbol, i.e., the vertical bar character
|, has a special meaning for the Windows operating system,
you need to place an
"escape character",
which for Windows is the caret symbol, ^, immediately before
it. You also need to put the at symbol, @, before the echo
command to avoid seeing the echo command itself as output.
If you wish to use a batch file to execute the commands to find the log
file location, you need to replace the %g with %%g
as shown below.
@echo off
FOR /F "tokens=3" %%G IN ('reg query "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters" /v LogFilePath ^| find "LogFilePath"') DO echo %%G
The registry key and the value to be queried can also be placed in
environment
variables that can be modified, if you wish to query other
registry keys, instead of the one for the DNS log file location, so that it
is easier to see what needs to be changed for such other queries.
@echo off
REM Name: queryreg.bat
REM Version: 1.0
REM Created: November 22, 2014
REM Last Modified: November 22, 2014
REM
REM Description: Displays just the value of a registry key from a
REM "reg query regkey /v regvalue" command omitting the additional
REM information that is output by the command
set regkey="HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DNS\Parameters"
set regvalue="LogFilePath"
FOR /F "tokens=3" %%G IN ('reg query %regkey% /v LogFilePath ^| find %regvalue%') DO echo %%G
Download:
queryreg.bat
[/network/dns/windows/logging]
permanent link
Fri, Nov 21, 2014 11:09 pm
Windows DNS Log Analyser
If you've turned on logging for the DNS service provided on Microsoft
Windows servers, a useful tool for analyzing the contents of the log file
is
Windows DNS Log Analyser, which is a small (about 1.44 MB), free
program that understands the Microsoft Windows DNS server log file format which
will present the information to you in a more easily analyzed format.
[ More Info ]
[/network/dns/windows]
permanent link
Thu, Nov 20, 2014 11:17 pm
Enabling DNS Logging on a Microsoft Windows SBS 2003 Sever
DNS logging can be useful when trying to monitor what systems an infected
system is trying to contact. The DNS log will show you what DNS queries
were sent by the system to the DNS server to look up IP addresses for
host names.
[ More Info ]
[/network/dns/windows]
permanent link
Tue, Nov 18, 2014 10:51 pm
Checking and changing the Windows Firewall settings on a Windows system
The
advfirewall command can be used from a command prompt
to check and modify the settings for the Microsoft Windows Firewall
software on a Windows Vista, 7, 8, or Server 2008 system.
[ More Info
]
[/os/windows/software/security/firewall]
permanent link
Mon, Nov 17, 2014 9:57 pm
COPSSH permission denied message
When I tried connecting from PuTTY on a Windows 8 system to a Windows 7
system running
Copssh, a free
OpenSSH-based SSH server package for Microsoft Windows systems, I received the
message "Disconnected: No supported authentication methods available (server
sent: keyboard-interactive)", which appeared in a "PuTTY Fatal Error" window.
When I tried connecting using OpenSSH on a SBS 2003 system, I received
the message "Permission denied (keyboard-interactive)." I received the same
message using the ssh client on a Mac OS X system.
I opened the Copssh control panel on the system and clicked on the Users
tab. I had been trying to login with a domain account, but found that the
activated users list showed only two local accounts on the system, but
no domain accounts. When I clicked on the Add button to add a
new user, I found that for the "Domain" setting, the only option I could
choose was the local system, since its name appeared, but there was no other
value to select in the drop-down list. When I tried using one of the listed
accounts for the user name and password, I was able to successfully log in
by SSH.
[/os/windows/network/ssh/copssh]
permanent link
Sun, Nov 16, 2014 11:28 pm
Malware Detected by Malwarebytes Anti-Malware 2014-11-16
A user who has been experiencing performance problems with her system
recently reported it was running particularly slowly on Friday, November
14. I checked the system this weekend. Malwarebytes Anti-Malware detected
some files associated with malware, but I'm not certain all problems
associated with the system are resolved yet. One of the files, jm78.dll,
it reported as associated with malware may have come from a no longer
existing website in Russia, but I'm not certain of that, either and don't
have time for futher investigation of the system tonight.
[ More Info ]
[/security/malware]
permanent link
Sat, Nov 15, 2014 10:43 pm
Finding the proxy setting for Firefox from a command line
If Firefox on a Microsoft Windows system is configured to use a proxy
server, you can find the proxy server settings in
prefs.js
in the account's Firefox profile directory. Searching the file for
"network.proxy" will provide the settings.
[ More Info
]
[/network/web/browser/firefox]
permanent link
Fri, Nov 14, 2014 10:51 pm
Checking Installed Updates with WinUpdatesList (WUL)
WinUpdatesList (WUL) from
NirSoft is a free program that can show
you the list of intalled updates on a Microsoft Windows system. It was written
by
Nir Sofer.
You don't need to go through an install process to use the program, though
an installer is available for download from the developer's website. If
you don't want to go through an installation process, simply download the
zip file containing the executable program from the developer's website and
unzip the contents of the zip file. Within the zip file are 3 files:
| wul.exe | 43 KB |
| wul.chm | 15 KB |
| readme.txt | 9 KB |
Note: File sizes are for version 1.32, which is the current version.
The wul.chm file is a Compiled HTML Help file.
When you run wul.exe by double-clicking on it, you will see
a list of installed Windows updates, aka
"patches".
On Microsoft Window 98, ME, 2000, and Windows XP you will see a list of
files associated with the patch in the lower pane of the WUL window. On
Microsoft Windows 8, 7, Vista, and 2008 systems there is no information on
files installed by the update in the lower pane.
By default, the list of installed updates is ordered by name, but you can
click on the column headers to sort by other criteria. E.g., you can click
on the column header Installation Date to sort by date the patch
was installed.
You can right-click on an entry in the upper pane of the window and
choose "Properties" to see more details as shown in the example below,
for the installed patch.
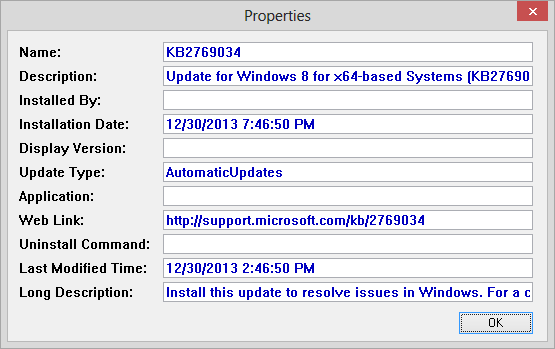
The utility can also be run from the command line with the following
options:
Command-Line Options
|
/stext <Filename>
| Save windows updates list into a regular text file.
|
|
/stab <Filename>
| Save windows updates list into a tab-delimited text file.
|
|
/scomma <Filename>
| Save windows updates list into a comma-delimited text file.
|
|
/stabular <Filename>
| Save windows updates list into a tabular text file.
|
|
/shtml <Filename>
| Save windows updates list into HTML file.
|
|
/sverhtml <Filename>
| Save windows updates list into HTML file. (vertical)
|
|
/sxml <Filename>
| Save windows updates list into XML file.
|
|
/another <Windows Folder>
|
connect to another instance of operating system on the same computer (Windows 2000/XP only).
You can combine this option with one of the save options in order to save the
Windows updates list of another operating system.
Examples:
wul.exe /shtml c:\temp\1.html /another d:\winnt
wul.exe /another f:\winnt
|
|
/remote <Computer Name>
|
Connect to remote Windows 2000/XP operating system.
You can combine this option with one of the save options in order to save the
Windows updates list of a remote computer.
Examples:
wul.exe /shtml c:\temp\1.html /remote \\comp01
wul.exe /another /remote \\192.168.0.101
|
[/os/windows/software/utilities/nirsoft]
permanent link
Thu, Nov 13, 2014 10:41 pm
Determining the version of Flash installed on a system
You can determine the version of Flash installed on a system by visiting
BrowserSPY.dk, which can provide a
variety of information for your system, and running its
Flash test. You can determine
what version is the most current by visiting
the
Adobe Flash Player
web page. As of November 13, 2014, the current version is 15.0.0.223.
Note: browserspy.dk will display commas in place of the periods when it
reports the version, i.e., 15,0,0,223
[/network/web/browser]
permanent link
Thu, Nov 13, 2014 10:38 pm
Determining Java version on a Windows 7 system
To determine the version of
Java installed
on a Windows 7 system, take the following steps, which should also work on
other versions of Windows, though you may need to look for "Programs" rather
than "All Programs" for the first method, depending on your version of Windows.
Method 1
-
Click on the
Windows Start button, normally at the lower left-hand corner of the screen.
- Select All Programs.
Scroll down until you see the Java group, then select it and "Configure
Java" within it. You will then see a Java Control Panel window
appear.
-
Click on the About button in the Java Control Panel window.
An About Java window will appear telling you the version of Java
that is installed on the system.
Method 2
Obtain a command prompt by clicking on the Windows Start button then
typing cmd and hitting return. At the command prompt type
java -version and hit return.
C:\>java -version
java version "1.8.0_25"
Java(TM) SE Runtime Environment (build 1.8.0_25-b18)
Java HotSpot(TM) Client VM (build 25.25-b02, mixed mode, sharing)
The version information displayed above is "1.8.0_25". The first method
displayed "Version 8 Update 25" for the same version. The number after
the underscore in the output from the command line, i.e. "25", is the build
number for that version. A version can have many build numbers before the
developer increments the version number.
You can determine what version of Java is the latest or download the
latest version from www.java.com.
[/software/java]
permanent link
Wed, Nov 12, 2014 9:58 pm
Call to undefined function mysql_connect()
I finally resolved problems with access to MySQL databases on a CentOS 7
server from the command line yesterday - see
MySQL service not running on CentOS 7 system - but when I visited
web pages on the server that rely upon PHP code to access MySQL databases
on the server, I was seeing blank pages, though other PHP web pages that
didn't have any database access were displaying properly. When I checked the
Apache error log for a website where the PHP code should have displayed data
from a database, I saw "PHP Fatal error: Call to undefined function
mysql_connect()" associated with attempts to load the web page containing the
PHP code that connected to the MySQL database.
I verified that the php-mysql package was installed with
rpm -qi php-mysql.
# rpm -qi php-mysql
Name : php-mysql
Version : 5.4.16
Release : 23.el7_0.3
Architecture: x86_64
Install Date: Tue 11 Nov 2014 08:26:15 PM EST
Group : Development/Languages
Size : 237259
License : PHP
Signature : RSA/SHA256, Fri 31 Oct 2014 10:24:56 AM EDT, Key ID 24c6a8a7f4a80eb5
Source RPM : php-5.4.16-23.el7_0.3.src.rpm
Build Date : Fri 31 Oct 2014 09:07:27 AM EDT
Build Host : worker1.bsys.centos.org
Relocations : (not relocatable)
Packager : CentOS BuildSystem <http://bugs.centos.org>
Vendor : CentOS
URL : http://www.php.net/
Summary : A module for PHP applications that use MySQL databases
Description :
The php-mysql package contains a dynamic shared object that will add
MySQL database support to PHP. MySQL is an object-relational database
management system. PHP is an HTML-embeddable scripting language. If
you need MySQL support for PHP applications, you will need to install
this package and the php package.
I created a PHP test page with the following code:
<html>
<head>
<title>PHP Test</title>
</head>
<body>
<h2>A test page</h2>
<?php echo "<p>Hello world</p>"; ?>
<?php phpinfo(); ?>
</body>
</html>
"Hello world" was displayed by the PHP echo command and the information
from the phpinfo function was also displayed. I searched through the
results displayed for references to "MySQL" and found mysql and mysqli
sections, including the following:
| MySQL Support | enabled |
|
Active Persistent Links |
0
|
|
Active Links |
0
|
|
Client API version |
5.5.37-MariaDB |
|
MYSQL_MODULE_TYPE |
external |
|
MYSQL_SOCKET |
/var/lib/mysql/mysql.sock |
|
MYSQL_INCLUDE |
-I/usr/include/mysql |
|
MYSQL_LIBS |
-L/usr/lib64/mysql -lmysqlclient |
Since it appeared that PHP support for MySQL was present,
I restarted Apache with apachectl restart, though I
didn't expect that to resolve the problem. But when I refreshed
the web page afterwards, the information from the MySQL database
was displayed. Apparently, I should have restarted Apache
after I ran the systemctl start mariadb.service
to start the MariaDB database service yesterday. MariaDB is a
fork
of MySQL.
References:
-
Fatal error: Call to undefined function mysql_connect()
Date: May 16, 2012
stackoverflow
-
Resolving a Fatal error: Call to undefined function mysql_connect() in RedHat
By: Shailesh N. Humbad
Created: October 18, 2004
Last Modified: July 24, 2011
Somacon
Articles on web development, software, and hardware
[/software/database/mysql]
permanent link
Tue, Nov 11, 2014 11:06 pm
MySQL service not running on CentOS 7 system
When I issued the
mysql command on a CentOS 7 system,
I received the error message below:
ERROR 2002 (HY000): Can't connect to local MySQL server through socket '/var/lib/mysql/mysql.sock' (111)
It took me awhile to figure out that since I was using
MariaDB, a fork of MySQL, that I needed to enter the following 3 commands
to enable, run, and secure the MariaDB service.
systemctl start mariadb.service
systemctl enable mariadb.service
mysql_secure_installation
[ More Info ]
[/software/database/mysql]
permanent link
Tue, Nov 11, 2014 5:26 pm
Checking the creation and modified times for files with python
If I want to display each line in a file with a python script and at
the end of the output print the number of lines in the file, I can use
the python code below:
filename = raw_input("Enter file name: ")
with open(filename) as input_file:
for i, line in enumerate(input_file):
print line,
print "{0} line(s) printed".format(i+1)
The script will prompt me for the name of the file to be checked and
will loop through that file displaying each line from it, printing the
total number of lines at the end of the file.
The comma after the print line statement prevents a
newline from being printed,
so each file name will be printed immediately below the preceding one without
a blank line between them. If the comma was not there, a blank line would be
printed between each line containing a file name.
The {0} references the first positional argument in the
format statement, which in the case above refers to "i+1". The
.format(value) at the end of the line tells python how to format
the output. So the count of the number of lines in the file, which will be i
plus 1, will be printed after the for loop completes.
If each line in the file is a directory path and file name, e.g.,:
./security/vulnerabilities/windows/wmf-vulnerability-exploited.php
./security/vulnerabilities/windows/kb908519_embedded-web-font.php
./security/antivirus/avast/avast-ie9/index.php
./network/Internet/domains/domain-reputation-check.php
then I can use import os.path, time to import modules that
that will will allow me to obtain the time stamps for the files.
import os.path, time
filename = raw_input("Enter file name: ")
with open(filename) as input_file:
for i, line in enumerate(input_file):
print line,
line = line.rstrip('\r\n')
print "last modified: %s" % time.ctime(os.path.getmtime(line)),
print "created: %s" % time.ctime(os.path.getctime(line))
print "{0} line(s) printed".format(i+1)
Since the input file was created on a Linux system each line ends with a
newline character, which is represented by "\n". So I have to strip off the
trailing newline at the end of each file name in the input file with the
rstrip function. If the input file was created on a
Windows system, I would have to strip off a carriage return, which is
represented by "\r". By using rstrip('\r\n'), any carriage
return or newline characters will be stripped from the end of each line in
the input file, so the script will work on Mac OS, Mac OS X, Microsoft Windows,
or Unix/Linux systems.
I see output such as the following when I run the python script:
$ python checkfile.py
Enter file name: checkfiles2_php.txt
./security/vulnerabilities/windows/wmf-vulnerability-exploited.php
last modified: Mon Jan 9 15:45:00 2006 created: Tue Oct 14 10:21:03 2014
./security/vulnerabilities/windows/kb908519_embedded-web-font.php
last modified: Wed Jan 11 23:42:00 2006 created: Tue Oct 14 10:21:03 2014
./security/antivirus/avast/avast-ie9/index.php
last modified: Sat Aug 11 17:22:14 2012 created: Tue Oct 14 10:21:05 2014
./network/Internet/domains/domain-reputation-check.php
last modified: Sun Oct 6 13:30:27 2013 created: Tue Oct 14 10:21:12 2014
The creation times displayed above are the time I copied files from an old
drive to a new drive.
References:
-
python looping through input file
Date: July 30, 2013
stackoverflow
-
Python trailing comma after print executes next instruction
Date: October 24, 2010
stackoverflow
-
6.1. string — Common string operations
Python 3.4.2 documentation
-
Python string formatting: % vs. .format
Date: February 22, 2011
stackoverflow
-
How can I remove (chomp) a newline in Python?
Date: November 8, 2008
stackoverflow
-
How to get file creation & modification date/times in Python?
Date: October 25, 2008
stackoverflow
[/languages/python]
permanent link
Tue, Nov 11, 2014 5:15 pm
Finding a particular string in files
On a Linux/Unix or Mac OS X system, you can use the
find and
grep commands to search for a specific text string in files.
E.g., if you wished to search all files with a ".php" file extension for
the occurrence of the word "noindex", you could use the following command:
find . -name "*.php" -exec grep "noindex" {} /dev/null \;
Since "*" has a special meaning for the shell, you will need to include it
within quotes or precede it with the backslash
escape character
as shown below:
$ find . -type f -name \*.php -exec grep -l "noindex" {} \;If I wished to search all files, not just those ending with ".php", I
can use a command similar to the following one.
find . -type f -exec grep "noindex" {} \;
The -type f instructs find to only check regular files and
not other objects such as directory names.
If I want to send the results to an output file, I could just append a
>outputfile_name to the end of the line, but that will
also produce output indicating that the output file itself is being checked.
$ find . -type f -exec grep "noindex" {} \; >checkfiles.txt
grep: input file ‘./checkfiles.txt’ is also the outputTo avoid that issue, you can use the --exclude argument.
$ find . -type f -exec grep -l --exclude checkfiles.txt "noindex" {} \; >checkfiles.txtI can also use just the grep command, as shown belown:
$ grep -rwl . -e "noindex" --include=\*.php
The -r option tells grep to search recursively; the "." is
indicating that the search should be started in the current directory.
The -w indicates that I want exact word matches, e.g., " noindex ",
not "nonindex" or "noindexes". The -l option indicates that I
don't want to see the lines on which the word occurs, just the file names for
those files in which it is found. The -e option provides the
pattern that grep should search on and the --include option
tells grep which files it should search within.
-r, --recursive
Read all files under each directory, recursively, following
symbolic links only if they are on the command line. This is
equivalent to the -d recurse option.
-w, --word-regexp
Select only those lines containing matches that form whole
words. The test is that the matching substring must either be
at the beginning of the line, or preceded by a non-word
constituent character. Similarly, it must be either at the end
of the line or followed by a non-word constituent character.
Word-constituent characters are letters, digits, and the
underscore.
-l, --files-with-matches
Suppress normal output; instead print the name of each input
file from which output would normally have been printed. The
scanning will stop on the first match. (-l is specified by
POSIX.)
-e PATTERN, --regexp=PATTERN
Use PATTERN as the pattern. This can be used to specify
multiple search patterns, or to protect a pattern beginning with
a hyphen (-). (-e is specified by POSIX.)
--include=GLOB
Search only files whose base name matches GLOB (using wildcard
matching as described under --exclude).
References:
-
Finding a String with a Recursive Grep
Date: March 10, 2007
MoonPoint Support
-
How can I use grep to show just filenames (no in-line matches) on linux?
Date: July 9, 2011
stackoverflow
[/os/unix/commands]
permanent link
Mon, Nov 10, 2014 10:51 pm
Checking Microsoft Windows 7 firewall status from a command prompt
I enabled the Microsoft Windows Firewall on a Windows 7 system from
the
Control Panel by selecting
System and Security
and then
Firewall After enabling the Windows firewall, I checked on
the firewall status from a command line with
netsh firewall show state
. Though the
netsh firewall command, which I've used
since Microsoft Windows XP was released, is deprecated in Windows 7,
it can still be used to obtain information on the status and configuration
of the Microsoft Windows Firewall from the command line.
C:\>netsh firewall show state
Firewall status:
-------------------------------------------------------------------
Profile = Domain
Operational mode = Enable
Exception mode = Enable
Multicast/broadcast response mode = Enable
Notification mode = Enable
Group policy version = Windows Firewall
Remote admin mode = Disable
Ports currently open on all network interfaces:
Port Protocol Version Program
-------------------------------------------------------------------
22 TCP Any (null)
1900 UDP Any (null)
2869 TCP Any (null)
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
I checked on what applications had the three listed ports open with
netsh firewall show portopening.
C:\>netsh firewall show portopening
Port configuration for Domain profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
22 TCP Enable Inbound Copssh
1900 UDP Enable Inbound Windows Live Communications Platf
orm (SSDP)
2869 TCP Enable Inbound Windows Live Communications Platf
orm (UPnP)
Port configuration for Standard profile:
Port Protocol Mode Traffic direction Name
-------------------------------------------------------------------
22 TCP Enable Inbound Copssh
1900 UDP Enable Inbound Windows Live Communications Platf
orm (SSDP)
2869 TCP Enable Inbound Windows Live Communications Platf
orm (UPnP)
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
I also checked to see what programs were allowed by firewall rules.
C:\>netsh firewall show allowedprogram
Allowed programs configuration for Domain profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
Enable Inbound McAfee Shared Service Host / C:\Program Files\Comm
on Files\McAfee\Platform\McSvcHost\McSvHost.exe
Enable Inbound LifeTray.exe / C:\Program Files (x86)\Microsoft Li
feCam\LifeTray.exe
Enable Inbound LifeExp.exe / C:\Program Files (x86)\Microsoft Lif
eCam\LifeExp.exe
Enable Inbound LifeEnC2.exe / C:\Program Files (x86)\Microsoft Li
feCam\LifeEnC2.exe
Enable Inbound LifeCam.exe / C:\Program Files (x86)\Microsoft Lif
eCam\LifeCam.exe
Disable Inbound Internet Explorer / C:\program files (x86)\interne
t explorer\iexplore.exe
Enable Inbound Dropbox / C:\Users\JSmith.mayfield\AppData\Roaming
\Dropbox\bin\Dropbox.exe
Allowed programs configuration for Standard profile:
Mode Traffic direction Name / Program
-------------------------------------------------------------------
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
Since I need to be able to ping the system from other systems on the
LAN for troubleshooting, I
verified that
ICMP
echo requests and replies were not going to be blocked by the firewall.
C:\>netsh firewall show icmpsetting
ICMP configuration for Domain profile:
Mode Type Description
-------------------------------------------------------------------
Enable 2 Allow outbound packet too big
Enable 8 Allow inbound echo request
ICMP configuration for Standard profile:
Mode Type Description
-------------------------------------------------------------------
Enable 2 Allow outbound packet too big
IMPORTANT: Command executed successfully.
However, "netsh firewall" is deprecated;
use "netsh advfirewall firewall" instead.
For more information on using "netsh advfirewall firewall" commands
instead of "netsh firewall", see KB article 947709
at http://go.microsoft.com/fwlink/?linkid=121488 .
I saw that "allow inbound echo request" was enabled and I was able to
ping the system from the domain controller.
References:
-
Obtaining Information About the Windows XP Firewall from the Command Line
Date: March 1, 2006
MoonPoint Support
[/security/firewalls/windows]
permanent link
Sun, Nov 09, 2014 5:21 pm
Monitoring Failed SSH Logins to a CentOS System
If you have ssh enabled on a system that is accessible to the Internet, it is
probable that malicious individuals will try to gain access to the system
by brute force login attempts. I.e., since a Linux, Unix, or OS X system is
likely to have a root account, an attacker may use "root" as the userid and
then attempt to login with commonly used passwords. There are sites on the
Internet that provide lists of passwords commonly used and an attacker can
easily use a
dictionary attack where he tries every word in a dictionary as a possible
password. Attackers can use dictionaries for multiple languages, lists of
sports teams, name dictionaries, e.g., dictionaries of names parents might
check to aid in selecting a name for a baby, etc. So a root or another
administrator account should have a
strong password.
If it doesn't, the system will likely be cracked by an attacker eventually.
Attackers also routinely use name dictionaries to break into systems with
any accounts that have weak passwords. E.g., an attacker may use a name
dictionary to pick names to use as the userid. Let's say the first name in
the name dictionary is Aaron. The attacker might then use a word dictionary
to try every word in the English language, or some other language, as a
possible password for an
account with the userid of aaron. If an aaron account doesn't exist on the
system or has a strong password, once the attacker has gone through every
word in the word dictionary or whatever other password list he is using, he
will then go onto the next name in his name dictionary, e.g., perhaps Abe.
The attacker will proceed in this manner until he finds an account with a
weak password he can compromise or exhausts all possible combinations of
names for accounts and words to use for possible passwords. Of course it would
take a human an inordinate amount of time to type all such possible userid
and password combinations, but an attacker will let a program make such guesses
for him. He merely needs to start the program and let it run. His program
may be able to check many thousands of userid and password combinations
in minutes.
If the system isn't monitored for such brute-force password attempts, an
attacker can run unchecked for days. Even if he can't get in, he will be
using bandwidth to/from the system under attack as well as CPU cycles, etc.,
so may slow down access to the system for legitimate users. I've seen periods
where a system has been under attack from 5 such attackers in different
countries at once.
On CentOS Linux,
you can check the /var/log/secure log to find instances of
such attacks.
# grep 'Failed password' /var/log/secure | tail -5
Oct 28 09:47:43 frostdragon sshd[32246]: Failed password for root from 123.125.219.130 port 11859 ssh2
Oct 28 09:47:47 frostdragon sshd[32249]: Failed password for root from 123.125.219.130 port 13894 ssh2
Oct 28 09:47:52 frostdragon sshd[32253]: Failed password for root from 123.125.219.130 port 15886 ssh2
Oct 28 09:47:56 frostdragon sshd[32256]: Failed password for root from 123.125.219.130 port 17740 ssh2
Oct 28 09:48:01 frostdragon sshd[32259]: Failed password for root from 123.125.219.130 port 19477 ssh2
You can see the number of failed ssh login attempts from various login
addresses with the command grep 'Failed password' /var/log/secure | grep
sshd | awk '{print $11}' | sort | uniq -c - the IP address from which
the failed login attempt was made is the 11th item on the line.
If you pipe the output of the awk command into sort, you can sort the
output by IP address; uniq -c will then provide you the count
of failed SSH login attempts from particular IP addresses.
# grep 'Failed password' /var/log/secure | grep sshd | awk '{print $11}' | sort | uniq -c
1 101.227.71.40
409 117.27.158.71
2 117.27.158.91
84 122.225.109.104
315 122.225.109.108
232 122.225.109.118
321 122.225.109.197
247 122.225.109.212
115 122.225.109.217
458 122.225.97.103
309 122.225.97.108
96 122.225.97.110
377 122.225.97.117
478 122.225.97.120
121 122.225.97.83
63 122.225.97.84
81 122.225.97.88
36 122.225.97.98
382 123.125.219.130I can see from the above output from that command that there were
382 failed ssh login attempts from the 123.125.219.130 address
at the time I ran the command.
From a search on that IP address at the
American Registry for Internet Numbers (ARIN), I found the address was
part of a block of addresses managed by the
Asia Pacific Network Information Centre (APNIC)
. A whois search on the APNIC site showed the IP address is part of
a large block of addresses, 123.112.0.0 - 123.127.255.255, allocated
to an organization in Beijing, China. I often see attacks from IP addresses
allocated to entities in China.
You can manually block further attempts to compromise a system in this
manner using a route
reject command or through the firewall software
on the system. The default firewall software for CentOS 7 is
FirewallD.
You can configure it through a
Graphical User
Interface (GUI), which can be opened using the command
firewall-config or through a command line interface at a shell
prompt by using the command firewall-cmd. I blocked the IP
address from any access to the system using the command below, though by
the time I blocked it, the login attempts had ceased:
# firewall-cmd --add-rich-rule="rule family='ipv4' source address='123.125.219.130' reject"
success
The block can be viewed through the graphical interface for FirewallD
by running firewall-config. E.g., in this case under "Rich
Rules" for the public zone, I can see the blocked IP when starting the
application after issuing the firewall-cmd command.
The command above will put in place a firewall rule that will apply
to the default firewall zone, but will only remain
until the firewall service is restarted, e.g., with a system reboot.
To put in place a permanent block, I could have used the commands below.
Instituting a permanent change requires a restart of the firewall service,
though.
firewall-cmd --permanent --add-rich-rule="rule family='ipv4' source address='123.125.219.130' reject"
systemctl restart firewalld.service
To have a block apply to a specific firewall zone, e.g., the public zone,
I could use the commands below.
firewall-cmd --permanent --zone='public' --add-rich-rule="rule family='ipv4' source address='123.125.219.130' reject"
systemctl restart firewalld.service
The output of the grep command run against /var/log/secure
displayed above was sorted by IP address; if you, instead, would like
to sort the output by count of failed login attempts you can pipe the
output of the commands above into sort again adding the
-n argument to sort by the number that appears first on
each line.
# grep 'Failed password' /var/log/secure | grep sshd | awk '{print $11}' | sort | uniq -c | sort -n
1 176.222.201.154
1 85.132.71.83
1 91.220.131.33
1 a
1 pi
1 ubnt
2 client
4 ubuntu
4 usuario
27 git
48 122.225.97.117
64 221.228.205.196
71 61.174.51.223
78 admin
129 122.225.97.79
191 122.225.109.198
237 122.225.97.116
268 117.27.158.88
306 113.200.188.55
336 117.27.158.89I can see from the above output that the greatest number of failed
SSH login attempts made on the day I ran the command, which was November 9,
2014, were made from 117.27.158.89. Checking the APNIC site again,
I see that IP address is also assigned to an entity in China.
If you want to reverse the sorting order, so that the largest number
appears first, simply add the -r argument to the last sort command.
# grep 'Failed password' /var/log/secure | grep sshd | awk '{print $11}' | sort | uniq -c | sort -nr
336 117.27.158.89
306 113.200.188.55
268 117.27.158.88
237 122.225.97.116
191 122.225.109.198
129 122.225.97.79
78 admin
71 61.174.51.223
64 221.228.205.196
48 122.225.97.117
27 git
4 usuario
4 ubuntu
2 client
1 ubnt
1 pi
1 a
1 91.220.131.33
1 85.132.71.83
1 176.222.201.154In the above output, some of the failed entries are associated with
userids the attacker attempted to use to login. E.g., for the case of
the usuario one, I can see that the illegitimate login attempts
where that name was used for the userid orginated from the 221.228.205.196
IP address. There is no account on the system with that userid. The IP address
is also assigned to an entity in China.
# grep usuario /var/log/secure
Nov 9 10:53:01 localhost sshd[23516]: Invalid user usuario from 221.228.205.196
Nov 9 10:53:01 localhost sshd[23516]: input_userauth_request: invalid user usuario [preauth]
Nov 9 10:53:03 localhost sshd[23516]: Failed password for invalid user usuario from 221.228.205.196 port 52710 ssh2
Nov 9 10:53:04 localhost sshd[23568]: Invalid user usuario from 221.228.205.196
Nov 9 10:53:04 localhost sshd[23568]: input_userauth_request: invalid user usuario [preauth]
Nov 9 10:53:06 localhost sshd[23568]: Failed password for invalid user usuario from 221.228.205.196 port 53534 ssh2
Nov 9 10:53:07 localhost sshd[23654]: Invalid user usuario from 221.228.205.196
Nov 9 10:53:07 localhost sshd[23654]: input_userauth_request: invalid user usuario [preauth]
Nov 9 10:53:10 localhost sshd[23654]: Failed password for invalid user usuario from 221.228.205.196 port 55193 ssh2
Nov 9 10:53:12 localhost sshd[23657]: Invalid user usuario from 221.228.205.196
Nov 9 10:53:12 localhost sshd[23657]: input_userauth_request: invalid user usuario [preauth]
Nov 9 10:53:14 localhost sshd[23657]: Failed password for invalid user usuario from 221.228.205.196 port 56072 ssh2
To count just by IP address so that the login failurers for particular
usernames don't appear in the output, I can put another grep
command, one that will filter the output of the prior grep command so any lines of output from it are eliminated if they contain "invalid user", before the
awk command.
# grep 'Failed password' /var/log/secure | grep sshd | grep -v "invalid user" | awk '{print $11}' | sort | uniq -c | sort -n
1 176.222.201.154
1 85.132.71.83
1 91.220.131.33
48 122.225.97.117
64 221.228.205.196
71 61.174.51.223
129 122.225.97.79
191 122.225.109.198
237 122.225.97.116
268 117.27.158.88
306 113.200.188.55
336 117.27.158.89If you wish to see what userids are being used most frequently for the
failed login attempts, the string of commands entered above need to be
modified to search for the userids used in failed login attempts. The above
commands don't show the most commonly used userid, which is
root, since almost all Unix/Linux systems will have a root
account.
For failed login attempts the lines that appear in the output are slightly
different depending upon whether the userid used exists on the system. E.g.,
if the account doesn't exist on the system, as in the case for client
and git below, the lines appear as follows:
Nov 9 10:34:14 localhost sshd[21745]: Failed password for invalid user client f
rom 91.220.131.33 port 60223 ssh2
Nov 9 10:52:00 localhost sshd[23204]: Failed password for invalid user git from
221.228.205.196 port 60513 ssh2
If the account does exist, e.g., the root account, then
the lines have the following format:
Nov 9 04:58:50 localhost sshd[21319]: Failed password for root from 122.225.97.
79 port 7951 ssh2
The sed command can be used to strip out the "invalid user"
from lines to make the format of those lines containing "invalid user" the
same as for those for valid userids on the system. You can then use
the awk command to display the contents of the 9th entry on
the line, which is the userid used.
# grep "sshd.*: Failed password for" /var/log/secure | sed 's/invalid user //' | awk '{print $9}' | sort | uniq -c | sort -n
1 a
1 operator
1 pi
1 ubnt
2 client
4 ubuntu
4 usuario
27 git
78 admin
1844 rootThe output from a check of the /var/log/secure file shows
that the most common user name used in attempts to log into the system
by attackers is root.
References:
-
Firewalld - Block an IP Address
By: up2long
Date: February 26, 2014
Fedoraforum.org
[/network/ssh]
permanent link
Sun, Nov 09, 2014 5:04 pm
No JavaScript Support in Firefox
When visiting a web page with the Firefox 33.0 browser, I received a message
indicating that JavaScript was disabled. When I attempted to view
a spreadsheet I had in
Google Docs I
couldn't see any of my sheets. When I went to the
JavaScript test page at
BrowserSPY.dk, it indicated that there was no JavaScript support in the
browser. I don't know how I inadvertently disabled JavaScript support in
Firefox, but to re-enable it, you can put
about:config in
the Firefox address bar where you would normally put the address of a page
you wanted to visit. When you hit
Enter you will see a warning
message "This might void your warranty! Changing these advanced settings
can be harmful to the stability, security, and performance of this application.
You should only continue if you are sure of what you are doing." You will
need to click on the "I'll be careful, I promise!" button to continue so that
you can enable JavaScript again.
In the list of preference options that appear, scroll down until you see
javascript.enabled.
| Preference Name | Status | Type | Value |
|---|
| javascript.enabled | user set | boolean | false |
You will need to double-click on the javascript.enabled line
to change the value from "false" to "true" to enable javascript support. You
can disable javascript support by double-clicking on the line to toggle the
status to false, if it is set to true and you wish to disable it.
Once you have reenabled JavaScript, you should be able to successfully
display webpages that rely upon it.
[/network/web/browser/firefox]
permanent link
Sun, Nov 09, 2014 10:54 am
Determining when Apache was last restarted
If you need to determine the time that an Apache web server was last restarted,
you can look for the word "resuming" in the Apache error log file. On a CentOS
Linux system, you can use the command
grep resuming
/var/log/httpd/error_log.
# grep resuming /var/log/httpd/error_log
[Sun Nov 09 03:29:02.631763 2014] [mpm_prefork:notice] [pid 20663] AH00163: Apac
he/2.4.6 (CentOS) configured -- resuming normal operations
[/network/web/server/apache]
permanent link
Fri, Nov 07, 2014 10:40 pm
Installing YAML Perl module
YAML, which is a
recursive acronym for ""YAML Ain't
Markup Language",
is a human-readable data
serialization format that incorporates concepts from programming languages
such as C, Perl, and Python. To install the YAML Perl module type
perl -e shell -MCPAN at a shell prompt and then at the
cpan prompt, type
install YAML.
# perl -e shell -MCPAN
Terminal does not support AddHistory.
cpan shell -- CPAN exploration and modules installation (v1.9800)
Enter 'h' for help.
cpan[1]> install YAML
Once it is installed you can view documentation on it by issuing the
command perldoc YAML. If you just want to see if it is
installed, you can issue that command. If it is, you will see the documentation.
If it isn't installed, you will see a message "No documentation found" followed
by the module name.
You can also use the -l argument to perldoc, which
will report the location of the
Plain Old
documentation, abbreviated pod, file for the module, if one is present or
also report "No documentation found", if the module can't be found. Be
sure to capitalize "YAML" or you will see the "No documentation found"
message.
# perldoc -l yaml
No documentation found for "yaml".
# perldoc -l YAML
/usr/local/share/perl5/YAML.pod
[/languages/perl]
permanent link
Thu, Nov 06, 2014 10:26 pm
Copying the crontab file from a backup
On a CentOS Linux system, I needed to copy the crontab file for the root
account from a backup disk. The crontab files are stored in
/var/spool/cron, so I needed the
/var/spool/cron/root for the root account. Since I didn't
want to include every line from the old crontab file, I edited the
old one and copied its contents. I then used
crontab -e while
logged into the root account to create a new crontab file. I pasted the
contents of the old file into the new one. When I tried
saving the file, I got the message below:
# crontab -e
no crontab for root - using an empty one
crontab: installing new crontab
"/tmp/crontab.wpnAYC":3: bad minute
errors in crontab file, can't install.
Do you want to retry the same edit?
I had also seen "bad day-of-week", instead of "bad minute" when editing the
file previously. I typed "y" to retry and then realized the source of
the problem, which I thought at first from the error message was some error
in the first five entries on the line that specify when a cron job should run.
Instead, the problem was because when I copied and pasted the contents of
the old file into the new file, entries that had wrapped around to a new
line on the screen were now on two lines whereas before they were only on
one line. E.g., for the output above, line 3, which was the one referenced
for "bad minute" was really the continuation of line 2, but it was now,
because of my copy and paste operation, on line 3 with no time specified, but
instead the end part of the command line.
I edited those lines where that had occurred, so though they wrapped
around on the screen each entry was one continuous line. I was then able
to save the file successfully and then view the crontab file with
crontab -l Since I had SELinux enabled on the system, I
checked the security context for the cron file and saw the following.
# ls -Z /var/spool/cron/root
-rw-------. root root unconfined_u:object_r:user_cron_spool_t:s0 /var/spool/cron/root
References:
-
Cron
Wikipedia, The Free Encyclopedia
-
Cron and Crontab usage and examples
Date: May 4, 2014
Pantz.org Technical Reference Site
-
How to Backup Crontabs of All Users on CentOS, RHEL, Ubuntu & Dabian
By: Rahul Kumar
Date: April 2, 2014
TecAdmin.net
[/os/unix/linux/centos]
permanent link
Wed, Nov 05, 2014 10:38 pm
You don't have permission to access / on this server error
After adding a virtual host section for a website to Apache's
httpd.conf file on a Linux system, I restarted Apache and tried
viewing the website with a browser. Instead of seeing the home page for the
site, I saw:
Forbidden
You don't have permission to access / on this server.
When I looked in the error log for the site, I saw the following:
[Wed Nov 05 21:27:30.519520 2014] [core:error] [pid 4471] (13)Permission denied: [client 207.255.181.210:1604] AH00035: access to / denied (filesystem path '/home/jdoe/public_html') because search permissions are missing on a component of the path
[Wed Nov 05 21:27:31.179045 2014] [core:error] [pid 4471] (13)Permission denied: [client 207.255.181.210:1604] AH00035: access to /favicon.ico denied (filesystem path '/home/jdoe/public_html') because search permissions are missing on a component of the path
Checking the public_html directory and the directories
beneath it, I saw that owner, group, and world all had "execute" access,
i.e., the capability to search through the directories.
$ ls -ld public_html
drwxrwxr-x. 14 jdoe jdoe 4096 Nov 5 21:04 public_html
But, checking the user's home directory I found there was no access to it
except for the owner. When I changed that access to grant search access
to other accounts in the same group and all accounts, then the website became
visible.
$ chmod ga+x /home/jdoe
$ ls -ld /home/jdoe
drwx--x--x. 13 jdoe jdoe 4096 Nov 5 21:17 /home/jdoe
You can check the permissions on a directory and the directories
above it up to the root directory with just one command using
the namei -m command in the form namei -m
/path_to_directory/dirname. E.g.:
$ namei -m /home/jdoe/public_html
f: /home/jdoe/public_html
drwxr-xr-x /
drwxr-xr-x home
drwx--x--x jdoe
drwxrwxr-x public_html
[/network/web/server/apache]
permanent link
Wed, Nov 05, 2014 8:15 am
Denying interactive logins for an account
On a Linux system, you can change the designated shell for an account
to "nologin" to prevent user's from interactive logons. For instance,
if an account is only used for email, then you might wish to block the
user from logging in and obtaining a shell prompt, so that should anyone
else obtain the password for the account the person whould not be able
to do anything other than send and receive email for the account. If the
user's account was jasmith, you could use the command below:
# usermod --shell /sbin/nologin jasmith
[/os/unix/linux/sysmgmt]
permanent link
Tue, Nov 04, 2014 11:57 pm
Dovecot logon_trusted_networks
A user reported that she was no longer able to download her email
after receiving a new system. She uses Outlook, which was reporting the
following error:
Task 'jasmith@example.com - Receiving' reported error (0x800CCC92) :
'Your e-mail server rejected your login. Verify your user name and
password for this account in Account Settings. The server responded:
-ERR [AUTH] Plaintext authentication disallowed on non-secure (SSL/TLS)
connections.'
At first I thought the tech who upgraded the system had made some
change to Outlook on the system, but I eventually realized that the email
server using
dovecot for
POP3 email
access was denying access, because the system had a new IP address. The
user was using POP3, port 110, for downloading email and I had previously
added the old IP address to the login_trusted_networks
line in /etc/dovecot/dovecot.conf file on the email
server. By adding an IP address or IP address range to that line, you can
configure dovecot to allow users to login using an unencrypted userid
and password, i.e., plaintext authentication, from
the specified IP address or range of addresses. The relevant section in
dovecot.conf is shown below:
# Space separated list of trusted network ranges. Connections from these
# IPs are allowed to override their IP addresses and ports (for logging and
# for authentication checks). disable_plaintext_auth is also ignored for
# these networks. Typically you'd specify your IMAP proxy servers here.
login_trusted_networks = 192.168.0.0/24 192.168.1.0/24 172.45.55.82
In the case above, the server will accept plaintext passwords from any
system in the 192.168.0.0/24 address range, i.e., 192.168.0.0 to
192.168.0.255, the 192.168.1.0/24 address range, and from the specific
IP address 172.45.55.82, which was the user's IP address. After updating
her IP address in the file, I restarted dovecot with
service dovecot restart.
The system uses sendmail
for sending email and I also had to update /etc/mail/access
to include her IP address, since the change to the dovecot configuration file
allowed her to download her email, but sendmail would still not except any
email sent from her computer, since relaying was permitted from her old
email address, but not her new one. I added her IP address and a comment
line to the /etc/mail/access file.
# J. A. Smith
172.45.55.82 RELAY
I then used makemap hash
to generate an updated /etc/mail/access.db file.
# makemap hash /etc/mail/access </etc/mail/access
She was then able to send as well as receive email; I didn't need to
restart sendmail.
[/network/email/dovecot]
permanent link
Mon, Nov 03, 2014 9:12 pm
Adding another SMTP Server to Thunderbird
To add another SMTP server for outgoing email in Thunderbird 24.6.0 on a
Microsoft Windows systems, take the following steps:
-
Hit Alt-T to bring up the Tools menu.
-
Select Account Settings.
-
An Account Settings window will open showing you all of the
email accounts you have set up. Scroll down to the bottom of the list of
accounts where you will see Outgoing Server (SMTP), which you
should select by clicking on it.
-
You will then see an Add button that you can click on to add
an additional SMTP server for outgoing email.
-
Complete the fields for the SMTP server, including "Description", "Server
Name" and "Port", which will likely be 25 or 587. If you need to authenticate
with the server when sending email, select the appropriate authentication
method and provide a user name, if needed.
-
Click on the OK button.
-
If you wish any of the email accounts you have set up in Thunderbird to use
that SMTP server, select an account you wish to have use that outgoing email
server by right-clicking on it, e.g. jdoe@example.com, and picking
Settings. For the "Outoging Server (SMTP)" value, which you will see
with the email address selected, i.e., don't click on "Server Settings" or
any other option below the address, select the new server and click on
OK.
References:
-
Multiple SMTP servers - Thunderbird
mozilaZine
[/network/email/clients/thunderbird]
permanent link
Sun, Nov 02, 2014 1:09 pm
CGI.pm missing from CentOS system
When I tried accessing a website on a CentOS 7 server that I had recently
set up as a web server using Apache, when I attempted to view the site,
which I transferred from a CentOS 5 system, I saw the following error message
in my browser.
Internal Server Error
The server encountered an internal error or misconfiguration and was unable
to complete your request.
Please contact the server administrator at webmaster@example.com to inform
them of the time this error occurred, and the actions you performed just before
this error.
More information about this error may be available in the server error log.
Checking the httpd error log, I saw the following entries for the problem:
[Sun Nov 02 11:31:21.399775 2014] [cgi:error] [pid 18794] [client 94.228.34.209:55416] AH01215: Can't locate CGI.pm in @INC (@INC contains: /usr/local/lib64/perl5 /usr/local/share/perl5 /usr/lib64/perl5/vendor_perl /usr/share/perl5/vendor_perl /usr/lib64/perl5 /usr/share/perl5 .) at /home/jdoe/public_html/blog/blosxom line 92.
[Sun Nov 02 11:31:21.399911 2014] [cgi:error] [pid 18794] [client 94.228.34.209:55416] AH01215: BEGIN failed--compilation aborted at /home/jdoe/public_html/blog/blosxom line 92.
[Sun Nov 02 11:31:21.401265 2014] [cgi:error] [pid 18794] [client 94.228.34.209:55416] End of script output before headers: blosxom
When I searched the system for CGI.pm, I found it was not
present.
# find / -name CGI.pm -print 2>/dev/null
#
The file was present on a backup from the CentOS 5 system at
/usr/lib/perl5/5.8.8/CGI.pm.
Since it wasn't installed, I tried installing it.
# perl -e shell -MCPAN
Can't locate CPAN.pm in @INC (@INC contains: /usr/local/lib64/perl5 /usr/local/share/perl5 /usr/lib64/perl5/vendor_perl /usr/share/perl5/vendor_perl /usr/lib64/perl5 /usr/share/perl5 .).
BEGIN failed--compilation aborted.
But that failed because CPAN.pm wasn't installed, either.
# find /usr/lib/perl5 -name CPAN.pm -print 2>/dev/null
# whereis CPAN.pm
CPAN:[root@frostdragon conf]# locate CPAN.pm
#
So I installed the perl-CPAN package with yum.
After the installation, I checked on the package and the location of
CPAN.pm.
# rpm -qi perl-CPAN
Name : perl-CPAN
Epoch : 0
Version : 1.9800
Release : 283.el7
Architecture: noarch
Install Date: Sun 02 Nov 2014 12:02:15 PM EST
Group : Development/Languages
Size : 762403
License : GPL+ or Artistic
Signature : RSA/SHA256, Fri 04 Jul 2014 12:15:45 AM EDT, Key ID 24c6a8a7f4a80eb5
Source RPM : perl-5.16.3-283.el7.src.rpm
Build Date : Tue 17 Jun 2014 01:42:20 PM EDT
Build Host : worker1.bsys.centos.org
Relocations : (not relocatable)
Packager : CentOS BuildSystem <http://bugs.centos.org>
Vendor : CentOS
URL : http://www.perl.org/
Summary : Query, download and build perl modules from CPAN sites
Description :
Query, download and build perl modules from CPAN sites.
# whereis CPAN.pm
CPAN: /usr/share/man/man3/CPAN.3pm.gz
#
I was then able to install CGI.pm.
# perl -e shell -MCPAN
CPAN.pm requires configuration, but most of it can be done automatically.
If you answer 'no' below, you will enter an interactive dialog for each
configuration option instead.
Would you like to configure as much as possible automatically? [yes] yes
<install_help>
Warning: You do not have write permission for Perl library directories.
To install modules, you need to configure a local Perl library directory or
escalate your privileges. CPAN can help you by bootstrapping the local::lib
module or by configuring itself to use 'sudo' (if available). You may also
resolve this problem manually if you need to customize your setup.
What approach do you want? (Choose 'local::lib', 'sudo' or 'manual')
[local::lib] sudo
Autoconfigured everything but 'urllist'.
Now you need to choose your CPAN mirror sites. You can let me
pick mirrors for you, you can select them from a list or you
can enter them by hand.
Would you like me to automatically choose some CPAN mirror
sites for you? (This means connecting to the Internet) [yes] yes
Trying to fetch a mirror list from the Internet
Fetching with LWP:
http://www.perl.org/CPAN/MIRRORED.BY
Looking for CPAN mirrors near you (please be patient)
........................... done!
New urllist
http://cpan-du.viaverio.com/
http://mirror.cogentco.com/pub/CPAN/
http://httpupdate25.cpanel.net/CPAN/
Autoconfiguration complete.
commit: wrote '/root/.cpan/CPAN/MyConfig.pm'
You can re-run configuration any time with 'o conf init' in the CPAN shell
Terminal does not support AddHistory.
cpan shell -- CPAN exploration and modules installation (v1.9800)
Enter 'h' for help.
cpan[1]>
At the cpan[1] prompt, I entered install CGI.
Note: You need to use uppercase letters, not "cgi"
After the installation completed, I typed "exit" at the CPAN prompt. I was
then able to reload the page in the browser without getting the
"Internal Server" error; I did not have to restart Apache.
References:
-
Perl CGI:Can't locate CGI.pm
Date: June 5, 2005
LinuxQuestions.org
-
perl CPAN not installed by default
Date: February 4, 2012
DirectAdmin
[/languages/perl]
permanent link
Tue, Sep 16, 2014 1:02 pm
Recovering the prior Safari session on a Microsoft Windows system
If you are using Apple's Safari web browser on a Microsoft Windows system
and need to recover a prior browsing session, if Safari crashes or you
have to kill the application through the
Task Manager, because it
is no longer responding, you can recover all the open windows and tabs
from the prior browsing session for Safari 5.1.7 once you restart Safari by
using the
Alt-i key combination to have the History menu appear, then
selecting "Reo
pen all Windows from Last Session".
If you would like to have Safari automatically reopen all the prior tabs
and windows when you restart Safari, click on the gear icon at the top
right-hand corner of the browser window, then select Preferences,
then select "All windows from last session" instead of "A new window" for the
value for "Safari opens with".
[/network/web/browser/safari]
permanent link
Tue, Sep 09, 2014 12:40 pm
Evernote Web Clipper for Safari on Windows
The
Evernote Web Clipper is available
for Safari on a Microsoft Windows system from
here. Once you've installed it, you will see the Evernote elephant head
icon at the top left of the Safari browser window, slightly to the right
of the buttons that allow you to move forward and backward in the tab history.
To login to Evernote, click on that icon and hold the button down until the
login window appears.
Once you've logged in, you can click on the button again to save
web pages as an article, simplified article, full page, bookmark, or
screenshot.
[/network/web/browser/safari]
permanent link
Mon, Aug 11, 2014 10:37 pm
Creating a WinPE Boot Disc with MustangPEBuilder 2 ADK
I needed to do some troubleshooting on an HP desktop system
running Microsoft Windows 8 that would no longer boot
into Windows. The system has three 2 TB drives configured as a
RAID 5 array
providing 4 TB of storage, but one of the drives had failed. I could
boot the system from Linux rescue CDs, but, since I didn't have an
appropriate driver to access the drives as a 4 TB RAID array, I couldn't
access user files on the system by that method. I could boot into the
Windows recovery environment and choose the advanced options, which
would allow me to get to a command prompt.
I could then copy files from the drives to an external USB drive using
xcopy, but the user had over 900,000 files in her
My Documents directory and xcopy only copied about 800,000 of
those. I wanted to try another method of copying the files to see if
that would be more successful, but there were no other utilities available
to me from the command prompt that I thought would be more successful.
I created a boot disc on another Windows 8 system using
MustangPEBuilder 2 ADK, which
allowed me to boot into a Windows
GUI,
but without the appropriate driver added I haven't yet been able to
access the data in the user's My Documents directory with it.
I have been able to add Windows applications, such as
IrfanView, but I haven't figured
out yet how to get some other applications I want to use added nor a driver
that will allow me to access the RAID drives.
[/os/windows/mustang]
permanent link
Sat, Aug 09, 2014 3:55 pm
Editing ISO files with Magic ISO Maker
I had an issue with a bootable
Windows PE DVD no longer working as I expected. I thought the problem
was due to the
boot.wim no longer being created correctly.
The .wim file is a
Windows
Imaging Format file and
boot.wim contains a bootable
version of Windows PE. On a Windows 8 system, I was able to use the Windows
Explorer to copy the
boot.wim file from within an
ISO image, but I needed a
way to replace the
boot.wim file in another ISO image file with the
one I copied. To do so, I used the
Magic ISO Maker program, which
provides the capability to create and edit ISO files and extract files
from within ISO files. It also can deal with the BIN disc image format
and
Apple
Disk Image DMG files. MagicISO can open and manipulate just about
any disc image format. Magic ISO Maker can deal with ISO, BIN, IMG,
CIF, FCD, NRG, GCD, PO1, C2D, CUE, CIF, and CD formats.
The unregistered version has a limitation preventing you from saving an
image greater than 300 MB, but in my case that was not an issue since the
image size was 175 MB.
I did purchase the software though, since it worked well and I often deal
with much larger ISO files. When you purchase the software, you will receive
a zip file by email containing a .reg file, which will provide you a
temporary license. Extract the .reg file from the .zip file, and double-click
on it to create the registry entries to register the software. You should
later receive a permanent serial number.
The steps to take to insert or replace a file within an existing ISO file
using MagicISO are listed below:
- Select File.
- Select Open.
- Browse to the location of the ISO file you wish to
modify and open it.
-
If you have a Windows Explorer window open side-by-side with the
Magic ISO Maker window, you can drag the file you want to insert into the
ISO file over into the Magic ISO Maker window and into the directory there
where you wish to insert the copy of the file into the ISO file. If a file
by that name already exists, a "Query for overwriting" window will appear
notifying you that the file already exists and asking if you want to overwrite
it. You can click on the Yes button to overwrite the file.
-
Click on File then Save as to save the update to the ISO file
in a new ISO file, since you can't save to the ISO file you have open within
Magic ISO Maker.
VirusTotal analysis of Setup_MagicISO.exe on 2014-08-09
[/os/windows/utilities/MagicISO]
permanent link
Thu, Aug 07, 2014 10:47 pm
Adding a printer from the command line on an OS X system
While in someone else's office, I needed to add an HP Color LaserJet
CP4025 printer in that office to the list of available printers
on my MacBook Pro laptop. I was able to generate a printout of the
printer's configuration from its front panel to get its IP address. I then
looked for a suitable
Postcript
Printer Description (PPD) file on the laptop. The PPD files can be found in
/Library/Printers/PPDs/Contents/Resources.
$ ls /Library/Printers/PPDs/Contents/Resources | grep -i LaserJet | grep 40
HP Color LaserJet CM4540 MFP.gz
HP Color LaserJet CM6040 MFP.gz
HP Color LaserJet CP4005.gz
HP Color LaserJet CP4020 CP4520 Series.gz
HP LaserJet 400 M401.gz
HP LaserJet 400 M401dne.gz
HP LaserJet 400 MFP M425 Fax.ppd.gz
HP LaserJet 400 MFP M425.gz
HP LaserJet 4000 Series.gz
HP LaserJet 4050 Series.gz
HP LaserJet 4240.gz
HP LaserJet 9040 9050 MFP.gz
HP LaserJet 9040.gz
HP LaserJet M9040 M9050 MFP.gz
HP LaserJet P4010_P4510 Series.gz
The HP LaserJet 4000 Series.gz file seemed appropriate. I
then used the command below to add the printer:
$ lpadmin -p "192.168.234.59" -v "lpd://192.168.234.59/" -D "Matt - HP CP4025" -L "Building 18 Room S188" -P "/Library/Printers/PPDs/Contents/Resources/HP LaserJet 4000 Series.gz" -E
The printer then appeared in the list of available printers under
System Preferences/Print & Scan and I was able to print to it.
The lpadmin command can be used to configure
CUPS printers. CUPS is a
modular printing system often found on Unix and Linux operating systems. Apple's
OS X opertaing system is a Unix-based graphical interface.
The options for the lpadmin command, which can be used to
configure CUPS printers, are
listed below:
-p = Printer name (queue name if sharing the printer)
-v = IP address or DNS name of the printer
-D = Description of the printer (appears in the Printers list)
-L = Location of the printer
-P = Path to the printer PPD file to use for the printer
-E = Enable this printer to accept print jobs
The text specified with the -D option is the description
that I see for the printer when I check Print & Scan under
System Preferences.
[/os/os-x]
permanent link
Wed, Aug 06, 2014 9:00 pm
Command line unrar utility for Microsoft Windows
If you need to extract files from a
.rar file on a Microsoft
Windows system,
RARLAB, which
procues the WinRAR program that provides a
GUI for dealing with RAR files on Microsoft
Windows systems, also provides a free utility,
unrar,
which can be run from a command line on a Windows system. The utility
is available at
WinRAR and
RAR archiver addons.
To use the program, you need to extract the unRAR.exe
file from the file you download. You can do so by simply double-clicking
on the unrarw32.exe file you downloaded. You will then be
prompted for a directory into which the unRAR.exe file
should be extracted.
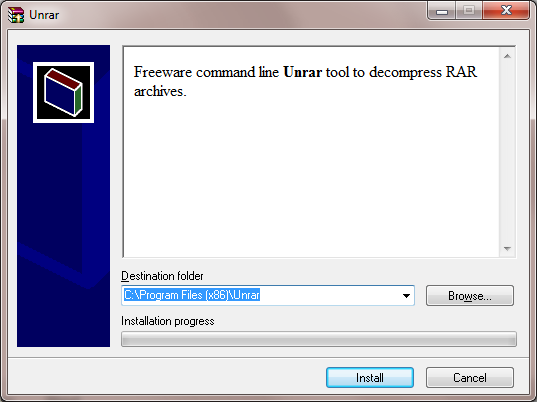
The default installation directory is C:\Program
Files(x86)\Unrar. If you don't have access to install files
in that directory on a system, you can place it anywhere, e.g. in
"My Documents". So you don't need administrator level access to a
system to put the utility on a system or run it on a system.
There is only the one file, Unrar.exe file that you need. to
use the software.
If you see a Program Compatibility Assistant window
appear stating "This program might not have installed correctly, you
can simply click on "This program installed correctly" to have the
Unrar.exe file placed in the directory you chose, if
you have the appropriate access to place files in that directory..
You can see the options availble for the program by typing
unrar at a command prompt in the directory in which you
extracted unrar.exe.
C:\Users\joe\Documents\bin>unrar
UNRAR 5.00 freeware Copyright (c) 1993-2013 Alexander Roshal
Usage: unrar <command> -<switch 1> -<switch N> <archive> <files...>
<@listfiles...> <path_to_extract\>
<Commands>
e Extract files without archived paths
l[t[a],b] List archive contents [technical[all], bare]
p Print file to stdout
t Test archive files
v[t[a],b] Verbosely list archive contents [technical[all],bare]
x Extract files with full path
<Switches>
- Stop switches scanning
@[+] Disable [enable] file lists
ac Clear Archive attribute after compression or extraction
ad Append archive name to destination path
ag[format] Generate archive name using the current date
ai Ignore file attributes
ap<path> Set path inside archive
c- Disable comments show
cfg- Disable read configuration
cl Convert names to lower case
cu Convert names to upper case
dh Open shared files
ep Exclude paths from names
ep3 Expand paths to full including the drive letter
f Freshen files
id[c,d,p,q] Disable messages
ierr Send all messages to stderr
inul Disable all messages
ioff Turn PC off after completing an operation
kb Keep broken extracted files
n<file> Additionally filter included files
n@ Read additional filter masks from stdin
n@<list> Read additional filter masks from list file
o[+|-] Set the overwrite mode
oc Set NTFS Compressed attribute
or Rename files automatically
ow Save or restore file owner and group
p[password] Set password
p- Do not query password
r Recurse subdirectories
ri<P>[:<S>] Set priority (0-default,1-min..15-max) and sleep time in ms
sl<size> Process files with size less than specified
sm<size> Process files with size more than specified
ta<date> Process files modified after <date> in YYYYMMDDHHMMSS format
tb<date> Process files modified before <date> in YYYYMMDDHHMMSS format
tn<time> Process files newer than <time>
to<time> Process files older than <time>
ts<m,c,a>[N] Save or restore file time (modification, creation, access)
u Update files
v List all volumes
ver[n] File version control
vp Pause before each volume
x<file> Exclude specified file
x@ Read file names to exclude from stdin
x@<list> Exclude files listed in specified list file
y Assume Yes on all queries
C:\Users\joe\Documents\bin>To extract the contents of a .rar file, use the e
argument to unrar followed by the name of the rar file.
C:\Users\joe\Documents\bin>unrar e %USERPROFILE%\Downloads\ST0044_9e8d3db5
2aa4e60904a3676eb33f763.rar
UNRAR 5.00 freeware Copyright (c) 1993-2013 Alexander Roshal
Extracting from C:\Users\joe\Downloads\ST0044_9e8d3db592aa4e60904a3676eb33763.rar
Extracting ST0044_BlacX Duet 5G Snow Editon_manual_12071201.pdf OK
All OK
[/software/utilities/file/rar]
permanent link
Tue, Aug 05, 2014 9:12 pm
Session Manager Firefox Add-on
The Firefox add-on
Session Manager created by
Michael Kraft allows you to save a Firefox session at any time. You can
save and restore the state of all or only some Firefox windows and
tabs. The session data saved includes history, text data, and cookies.
All sessions are stored in the sessions folder inside your profile
directory and can be moved around as with any other file.
On a Microsoft Windows 8 system, the sessions folder is in
%APPDATA%\Mozilla\Firefox\Profiles\profiledir\sessions.
You can find the value of %APPDATA% at a command prompt by
issuing the command echo %APPDATA%.
C:\>echo %APPDATA%
C:\Users\JDoe\AppData\Roaming
The value of the
profile beneath the
Profiles
directory will vary. E.g.:
C:\Users\JDoe\AppData\Roaming\Mozilla\Firefox\Profiles\nqp8058i.default\sessions
To get to that folder,
simply select "Open Session Folder" in Session Manager's menu (might not work on
all OSes), which you can get to in Firefox on Microsoft Windows by using the
Alt-T key combination to show the Tools menu, then selecting
Session Manager. Session Manager also allows you to reopen the 10 last
closed windows and tabs. You do not need to restart Firefox after installing
the Session Manager add-on to begin using it.
To save the Firefox session at any time, take the following steps on a
Microsoft Windows system (applies to Firefox 31.0 and Session Manager 0.8.1.5):
-
Use Alt-T key combination to bring up the Tools menu.
Alternatively, you can click on the blue floppy disk icon that is placed on
the Firefox address bar when you install Session Manager. That icon appears
to the left of another icon that is a red cross in a white box which will allow
you to reopen recently closed tabs or windows.

-
Select Session Manager.
-
Select Session Manager again.
-
Select Save Session.
-
A window will open where you can name the session you are about to save.
Provide a name for the session you wish to save in the "Name" field, which
could be the date or anything you like. You can uncheck any tabs you don't
want saved for the session.
-
Click on Save Session. Note: when you click on it, it may appear
that nothing is happening, but don't click again, give it a few seconds to
complete the save.
To load a saved session, go through the same steps to bring up Session
Manager, but instead of selecting Save Session select
Load Session. You will then see a list of any saved sessions.
If Firefox crashes or you reboot the system without closing Firefox, you
will see a window like the one below when you open Firefox, which will
give you the option of restoring Firefox to the state it was in when it
crashed or from a prior saved session.
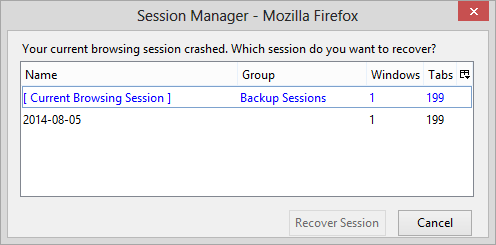
References:
-
Session Manager
Add-Ons
-
Session Manager
mozdev.org
[/network/web/browser/firefox/addons/sessionmgr]
permanent link
Mon, Aug 04, 2014 10:02 pm
Finding a MySQL table entry containing a text string
If you wish to search for an entry in a table in a MySQL database that contains
a text string, such as "Groot", you can use the
LIKE operator.
E.g., for a table named
chatroommessages with a a field named
message, you could search for any occurrences of "Groot" in
a message with the following:
SELECT `message` FROM `chatroommessages` WHERE `message` LIKE '%Groot%';
The percent signs at the beginning and end of the text indicate that any
other text can occur before and after that text, so if a message contained
"I am Groot!", it would be selected. The "%" will match any number of
characters, including zero characters.
You can search for words or phrases with any other text occurring before
or after the text you are seeking:
SELECT `message` FROM `chatroommessages` WHERE `message` LIKE '%only a test%';
If you want to use a wildcard that represents only one character
rather than zero or more characters, you can use the underscore character.
SELECT `message` FROM `chatroommessages` WHERE `message` LIKE '%test_r%';
The above SQL query would look for all messages that contained any
text before "test", followed by any one character, an "r", and then any
number of other characters. So the above query would find any of the following:
Hopefully I don't run out of Testor's Dull coat.
my test results were inconclusive.
I am currently a beta tester.
The case of the text doesn't matter. E.g., it doesn't matter that
I used all lowercase letters in "test" when I issued the SQL query. The
query would find "TEST" with all uppercase letters as well. So the message
contained "Testor" with a capital "T" was also found.
If you need to search for an occurrence of a wildcard character, e.g.,
you need to find "30%", then you would need to use a backslash, \,
as an "escape
character" to take away the special meaning of the percent sign in a query.
SELECT `message` FROM `chatroommessages` WHERE `message` LIKE '30\%';
That will restrict the search to finding only messages containing "30%",
whereas if you used LIKE 30% rather than LIKE 30\%,
the search would also return any messages containing "300", "3000", "30132",
etc.
| String | Description |
|---|
| \% | Matches one “%” character |
| \_ | Matches one “_” character |
References:
-
12.5.1 String Comparison Functions
MySQL Documentation: MySQL Reference Manuals
[/software/database/mysql]
permanent link
Sun, Aug 03, 2014 12:02 pm
Creating shortcuts with XXMkLink
If you need to create shortcuts from the command line or within a batch
file on a Microsoft Windows system, you can use the free
XXMkLink program from
Pixelab, Inc.. The company also produces
free and commercial versions of
XXCLONE,
for cloning disk drives, and
XXCOPY,
a file management utility for copying files.
To use XXMkLink, download the zip file and extract XXMKLINK.EXE from
within it to an appropriate directory on a hard drive. You can then run
that program without any parameters to see options available for it.
C:\>"\Program Files\Utilities\XXMKLINK"
XXMkLink ver 1.00 (c)2005 Copyright Pixelab, Inc.
=========== Syntax =======================
xxmklink spath opath [ arg [ wdir [ desc [ mode [ icon[:n] ]]]]] [switches...]
where spath path of the shortcut (.lnk added as needed)
opath path of the object represented by the shortcut
arg argument string (use quotes with space, see below)
wdir path of the working directory (for "Start in")
desc description string (shown in Shosrtcut's Properties)
mode display mode (1:Normal [default], 3:Maximized, 7:Minimized)
icon[:n] icon file [with optional icon index value n]
Currently, the following switches are supported
/p prompts before action
/q no output when successful (quiet)
Note: Switches (whose first character is always slash) can be placed in
any position of the command argument. A string that starts with
a slash as a non-switch argument must be surrounded by a pair of
double-quotes ("). It is recommended that the XXMKLINK's switches
be placed before or after the non-switch arguments for clarity.
Make sure that each element is surrounded by a pair of
double-quotes (") if embeded space is present.
The third field (arg) is for the argument string for the object
(typically a program that requires command arguments) that must
be entered as one string here, even if it has many parts that are
separated by spaces and possibly with double-quote characters.
When double-quoted string has an embedded double-quote,
add a backslash in front of each embedded double-qoute.
Use an empty string (two consecutive double-quotes) as a
place holder since this command syntax is sensitive to the
order of the field, optional switches cannot alter the
pre-determined order as defined by the program.
When an invalid display mode is specified (not 1, 3 nor 7),
the default (Normal Window) value will be used.
When the icon specifier does not point to an existing file,
the icon field will be ignored.
E.g. mklink "c:\Program Files\mydir\My Shortcut.lnk" c:\boot.ini
(At least two arguments are always needed.)
mklink c:\myauto c:\autoexec.bat "/q" . "I say \"Hello.\"" "desc..."
(In this example, the third argument string, "/q" was entered
as a quoted string. If it were without the quotation marks,
it would be treated as the xxmklink switch, /q, not the argment
string for the object program.)
At a minimum, the following two arguments are needed to the program to
create a shortcut:
spath - path and filename for the shortcut; if you don't add a
.lnk at the end of spath, one will be added automatically, since all
shortcuts must have a .lnk extension.
opath - path and filename of the object represented by the shortcut, i.e.
the location and name for the file or program for which you are creating
the shortcut.
E.g., suppose I wanted to create a shortcut on the desktop for the account
under which I'm currently logged into the system that points to the WinSCP
program, winscp.exe. I could use the following command, if
the xxmklink.exe file is in
C:\Program Files\Utilities and the winscp.exe
program is in c:\program files (x86)\network\SSH\WinSCP\. If I
was logged into the JDoe account, the
environment variable %USERPROFILE% would equate to
C:\Users\JDoe.
C:\>"\Program Files\Utilities\xxmklink" %USERPROFILE%\Desktop\WinScp.lnk "c:\program files (x86)\network\SSH\WinSCP\winscp.exe"
XXMkLink ver 1.00 (c)2005 Copyright Pixelab, Inc.
The shortut created as follows
Shortcut path: C:\Users\JDoe\Desktop\WinScp.lnk
Target object: c:\program files (x86)\network\SSH\WinSCP\winscp.exe
Arguments;
Working Directory:
Description:
Display Mode: Normal Window (1)
Icon file:
If I then hit the Windows
key and the "D" key simultaneously, I would then see the WinSCP shortcut on
the desktop.
Security information for current version of XXMkLink, which is 1.00
| File name: | xxmklink.zip |
| SHA256: |
2fe7b3b9c73e6467ba8d4e5157491a4409b44eab359d0320a3cba1e2bbec08ca |
| MD5: |
8f67bd67f4bd752837276caff870e474 |
| VirusTotal dection ratio: |
0/54
|
| Analysis date: | 2014-06-28 |
[/os/windows/utilities]
permanent link
Sat, Aug 02, 2014 10:38 pm
phpMyAdmin SQL History
If you need to see a recent history of SQL commands you've run inside
phpMyAdmin, you can see recently entered commands by clicking on the
SQL icon, which is a box with "SQL" in red letters within it, that
occurs just below "phpMyAdmin" at the upper, left-hand side of the
phpMyAdmin window.

Once you click on that icon, another small window will pop up which
contains a tab labeled SQL history.

Click on that tab to see the recently entered SQL commands
[/network/web/tools/phpmyadmin]
permanent link
Sat, Aug 02, 2014 10:13 pm
Mustang PEBuilder 2 winpe_x86 exists
On a Windows 8 system, I had to kill
Mustang PEBuilder 2 through the
Task Manager due to it
hanging while creating an ISO file. When I restarted it and clicked on
Create WinPE ISO, I saw the error message below:
Folder C:\winpe_x86 exists. Move, rename or delete and try again. Program
will terminate.
When I clicked on OK, the Mustang PEBuilder window
closed. The C:\winpe_x86 directory gets created during the
process by which Mustang PEBuilder 2 creates the .iso file. The directory
and its contents are normally deleted after the ISO file is created. When it
has not been deleted and I had previously seen the error message,
I was able to delete the C:\winpe_x86 folder and all
its contents and restart the process of building an ISO file without a
problem. But this time I received "access denied" messages when attempting
to delete some of the directories and files within it.
The problem was due to the directories and files being owned by
TrustedInstaller. To remedy the problem, I took the following steps:
- Right-click on a directory that can't be deleted and choose
Properties.
- Click on the Security tab.
- Click on the Advanced button.
- The owner will be listed as TrustedInstaller; click on
Change then in the "Enter the object name to select" field, type
Administrators.
- Click on OK.
- Click on the checkbox next to "Replace owner on subcontainers and objects"
to check the box.
- Click on the Apply button.
- In the "Permission entries" list, make sure Administrators have
"Full control".
- Check the checkbox for "Replace all child object permission entries
with inheritable permission entries from this object. When notified that this
will replace explicity defined permissions on all descendants of this
object with inheritable permissions, click on Yes.
- Click on the Apply button.
- You can now close the "Advanced Security Settings" window by clicking on
OK.
- You can click on OK again to close the Properties window
for the directory.
You should now be able to delete the directory and all subdirectories
and files within it.
References:
-
Windows 7 - How to Delete Files Protected by TrustedInstaller
Help Desk Geek
[/os/windows/utilities/diagnostic/mustang]
permanent link
Thu, Jul 31, 2014 10:48 pm
Uninstalling Shoutbox on an SMF 2.0.x forum
Since I had replaced Shoutbox on a
Simple Machines Forum (SMF) site running
SMF 2.0.8 with
CometChat,
I was asked to uninstall the Shoutbox mod and delete the files associated
with it from the site.
SMFPacks Shoutbox 1.0.3 was shown in the packages list, but there was
no option to install or uninstall it, only options to "List Files" or
"Delete". But there was a configuration page for it within the forum
software. That page showed that Shoutbox was disabled.
I found in the Packages directory for the forum there was a
SMFPacks_Shoutbox.zip file. When I unzipped the file and
checked the package-info.xml for it, I saw the following
in the installation section for 1.x versions of SMF:
<!-- 1.1.x -->
<install for="1.1-1.1.99">
There was an installation section for 2.0.x versions of SMF as well:
<!-- 2.0.x -->
<install for="2.0">
Since it did not list a range of version numbers, I went to Admin, then
Package Manager and then clicked on the Advanced link at
the bottom of the list of mods. I then changed the Emulate Version value
from 2.0.8 to 2.0 and clicked on the Apply button. I was then able to
uninstall SMFPacks Shoutbox 1.0.3 and delete the files associated with
it. I then clicked on the Advanced link again at the bottom of the list
of mods, clicked on Revert beneath Emulate Version, and then
clicked on the Apply button to put Emulate Version back to
its original value.
[/network/web/forums/smf]
permanent link
Sun, Jul 27, 2014 5:30 pm
Copying a MySQL table from one database to another
To copy a MySQL table, both the structure and data, from one database to
another, the following two commands can be used inside MySQL where
db1 is the original database and
db2 is the
new database and
table is the name of the particular table
you wish to copy.
CREATE TABLE db2.table LIKE db1.table;
INSERT INTO db2.table SELECT * FROM db1.table;
[/software/database/mysql]
permanent link
Sun, Jul 27, 2014 4:30 pm
Showing all MySQL databases or all tables in a database
For MySQL on a Linux system, if you need a list of all MySQL databases
you can display a list of the databases by logging into MySQL and
then issuing the command
show tables; or from a shell
prompt you can issue the command
mysqlshow -u username -p
where
username is a MySQL username. The
-p option will
result in a prompt for the password associated with the username.
$ mysqlshow -u jdoe -p
Enter password:
+--------------------+
| Databases |
+--------------------+
| information_schema |
| jdoedbf |
| test |
| tokyo |
+--------------------+
If you need a list of all tables in a MySQL database, you can display a
list of tables by logging into MySQL with an account that has access
to the database and then issuing the command
show tables;
or from a shell prompt you can issue the command
mysqlshow -u
username -p dbname where
username
is the account with access to the database and
dbname is
the name of the database. The
-p option will prompt for
the password for the account.
$ mysqlshow -u jdoe -p products
If you need to find a table with particular text in the name, you can
pipe the output of the mysqlshow command into grep. E.g., if you were looking
for a table in a database named "products" with many tables that contained
"cat" as part of the name of the table, you could use something like
the following:
$ mysqlshow -u jdoe -p products | grep cat
[/software/database/mysql]
permanent link
Sat, Jul 19, 2014 5:17 pm
Taking a screenshot with scrot
Scrot is a command line
screen capturing application for Linux systems developed by Tom Gilbert.
If the package is installed, you can type
scrot
imagefile to take a snapshot of the screen and store it in
the file named
imagefile, e.g.,
scrot test.png. If you
don't want the terminal window from which you ran the command captured in
the screenshot, you can issue the
sleep command followed by
some delay in seconds followed by a semicolon and then the scrot command
to give you time to minimize the terminal window from which you ran the
command. E.g.:
$ sleep 10; scrot test.png
The above command would give you 10 seconds to minimize the terminal
window and any other open windows you didn't want to see in the screenshot.
The results of the screenshot would be stored in the directory from which
the command was run in the file test.png. Or you can use
the scrot command's own delay parameter, -d or --delay
followed by the number of seconds of delay you wish to give yourself
before scrot captures the screen, e.g., scrot -d 10.
For help on the utility issue the command scrot --help.
scrot --help
Usage : scrot [OPTIONS]... [FILE]
Where FILE is the target file for the screenshot.
If FILE is not specified, a date-stamped file will be dropped in the
current directory.
See man scrot for more details
-h, --help display this help and exit
-v, --version output version information and exit
-b, --border When selecting a window, grab wm border too
-c, --count show a countdown before taking the shot
-d, --delay NUM wait NUM seconds before taking a shot
-e, --exec APP run APP on the resulting screenshot
-q, --quality NUM Image quality (1-100) high value means
high size, low compression. Default: 75.
For lossless compression formats, like png,
low quality means high compression.
-m, --multidisp For multiple heads, grab shot from each
and join them together.
-s, --select interactively choose a window or rectangle
with the mouse
-u, --focused use the currently focused window
-t, --thumb NUM generate thumbnail too. NUM is the percentage
of the original size for the thumbnail to be,
or the geometry in percent, e.g. 50x60 or 80x20.
-z, --silent Prevent beeping
SPECIAL STRINGS
Both the --exec and filename parameters can take format specifiers
that are expanded by scrot when encountered.
There are two types of format specifier. Characters preceded by a '%'
are interpreted by strftime(2). See man strftime for examples.
These options may be used to refer to the current date and time.
The second kind are internal to scrot and are prefixed by '$'
The following specifiers are recognised:
$f image path/filename (ignored when used in the filename)
$m thumbnail path/filename
$n image name (ignored when used in the filename)
$s image size (bytes) (ignored when used in the filename)
$p image pixel size
$w image width
$h image height
$t image format
$$ prints a literal '$'
\n prints a newline (ignored when used in the filename)
Example:
scrot '%Y-%m-%d_$wx$h_scrot.png' -e 'mv $f ~/images/shots/'
Creates a file called something like 2000-10-30_2560x1024_scrot.png
and moves it to your images directory.
This program is free software see the file COPYING for licensing info.
Copyright Tom Gilbert 2000
Email bugs to <scrot_sucks@linuxbrit.co.uk>You can also type man scrot to see information on use
of the utility.
References:
-
Scrot
Wikipedia, the free encyclopedia
-
The Tom Gilbert Blog
[/os/unix/linux/utilities/graphics]
permanent link
Sat, Jul 19, 2014 1:11 pm
Steps for taking a screenshot in GIMP
Steps for taking a screenshot in
GNU Image Manipulation Program (GIMP), which
is a free graphics program available for Linux, Mac OS X, Solaris, and
Microsoft Windows systems.
- Click on File.
- Select Create.
- Select Screenshot.
- When the GIMP screenshot window opens, you will have the option of
selecting the area for the screenshot.
Area
- Take a screenshot of a single window
[ ] Include window decoration
- Take a screenshot of the entire screen
[ ] Include mouse pointer
- Select a region to grab
Delay
[ 0 ] seconds
At the end of the delay, click in a window to snap it.
- When you have selected the option you want, click on the
Snap button.
If you choose to take a screenshot of a single window, the cursor will
change to something similar to a "+". Move the cursor over the appropriate
window and that window will be pasted into a GIMP window when you click on the
window. Note: make sure you don't have any windows overlapping the one
you wish to capture, otherwise you may see a portion of an overlapping
window in the screenshot.
If you don't want to capture the border around a window, scrollbars for
the window, and any application menu at the top of the window, uncheck
"Include window decoration.
If you choose "Take a screenshot of the entire screen", a snapshot
will be taken of the entire screen including the GIMP window.
If you select a region to grab, the cursor will change as above. You can
then click in one corner of the area of the screen you wish to include in
the snapshot then drag the mouse to a diagonal corner while holding the
mouse button down. When you release the button, the area selected will
be captured.
Once you have the screen shot, you can create a GIF, JPG, PNG, etc. image
file from the screenshot by clicking on File and selecting
Export.
[/software/graphics/gimp]
permanent link
Fri, Jul 18, 2014 8:53 pm
Determining the default browser from the command line
If you need to determine the default browser on a system running
Microsoft Windows, you can look in the registry at
HKEY_CLASSES_ROOT\http\shell\open\command
To determine the default browser from the command line, you can use
the command reg query HKEY_CLASSES_ROOT\http\shell\open\command
/ve.
C:\>reg query HKEY_CLASSES_ROOT\http\shell\open\command /ve
HKEY_CLASSES_ROOT\http\shell\open\command
(Default) REG_SZ "C:\Program Files\Network\Web\Mozilla Firefox\firefox.exe" -osint -url "%1"If you just wanted a true or false result for determining whether Firefox
is the default browser, you could pipe the output of the reg query
command to the find command as below. A result of 0 means "false", i.e.,
Firefox is not the default browser and a result of 1 means it is the default
browser.
C:\>reg query HKEY_CLASSES_ROOT\http\shell\open\command /ve | find /c /i "firefox"
1
Reference:
-
How Does Your Browser Know that It’s Not The Default?
Date: March 23, 2007
The New Old Thing | Absurdity in Its Fullest
[/network/web/browser]
permanent link
Tue, Jul 08, 2014 10:57 pm
Junos Pulse VPN Client Issue on Mac OS X
The Junos Pulse 5.0.3 VPN client had been working fine on my Mac OS X laptop
for quite some time, but recently whenever I opened it, it would show
"Disconnecting". I could click on the
Connect button, which
resulted in the application displaying "connect requested", but the
application would never connect nor disconnect. I could select
"Close Junos Pulse" in the application, but when I restarted the
application I was in the same situation. I could probably have resolved the
problem by rebooting, but since I had a lot of applications and files open
and didn't want to have to close all the files and applications, I looked for
another alternative. Issuing the following commands at a command prompt
from a terminal window allowed me to eliminate the problem without rebooting.
$ launchctl unload -w /Library/LaunchAgents/net.juniper.pulsetray.plist
$ sudo launchctl unload -w /Library/LaunchDaemons/net.juniper.AccessService.plist
Password:
$ osascript -e 'tell application "Junos Pulse" to quit'
The account I was logged in under had adminisrator level access, so I
simply provided its password at the password prompt above.
When I reopened Junos Pulse afterwards, it wasn't showing any available
connections, so I closed it and then issued the commands below.
$ sudo launchctl load -w /Library/LaunchDaemons/net.juniper.AccessService.plist
$ launchctl load -w /Library/LaunchAgents/net.juniper.pulsetray.plist
When I then reopened the Junos Pulse application through the Finder,
I saw the VPN connection I normally use and was able to successfully
establish a VPN connection. And I was able to disconnect without a
problem afterwards.
[/os/os-x]
permanent link
Sun, Jun 29, 2014 8:58 pm
Showing permissions for MySQL databases
Any of the following commands can be used to view privileges on MySQL databases for the currently logged in user:
SHOW GRANTS;
SHOW GRANTS FOR CURRENT_USER;
SHOW GRANTS FOR CURRENT_USER();
E.g., if logged into MySQL as the user joe:
mysql> show grants;
+----------------------------------------------------------------------------------------------------+
| Grants for joe@localhost |
+----------------------------------------------------------------------------------------------------+
| GRANT USAGE ON *.* TO 'joe'@'localhost' IDENTIFIED BY PASSWORD '75ac044c66d44642' |
| GRANT ALL PRIVILEGES ON `family`.* TO 'joe'@'localhost' |
| GRANT ALL PRIVILEGES ON `partslist`.* TO 'joe'@'localhost' |
| GRANT SELECT, INSERT, UPDATE, DELETE, CREATE ON `tokyo`.`tokyo` TO 'joe'@'localhost' |
+----------------------------------------------------------------------------------------------------+
4 rows in set (0.00 sec)
To show databases for which the user has access, the show databases
command can be used:
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| family |
| partslist |
| tokyo |
+--------------------+
4 rows in set (0.00 sec)
To see which users have access to a particular database, you use the
command select user from mysql.db where db='dbname';, where
dbname is the name of the relevant database, if
you are logged into an account with administrator privileges, e.g., as root.
E.g. for a database named partslist:
mysql> select user from mysql.db where db='partslist';
+------+
| user |
+------+
| joe |
+------+
1 row in set (0.01 sec)
[/software/database/mysql]
permanent link
Sun, Jun 29, 2014 7:40 pm
Dropping tables with a similar prefix from a MySQL database
I wanted to remove all of the tables from a MySQL database where the tables
all had names starting with a similar prefix. Rather than deleting the tables
one by one, I wanted to reduce the time and typing on my part to drop all
of the tables. One way to do so is to use the
mysqldump command
to create a file that contains all of the needed
DROP commands.
You can issue a mysqldump command similar to the following where
user
is a user name with permissions to access the database and
database
is the name of the database:
mysqldump -u user -p database > dump.sql
The -p option will prompt you for the password for the user.
E.g., supposing the user name is jdoe and the database is named jdoe_db:
$ mysqldump -u jdoe -p jdoe_db > dump.sql
Enter password:
Then, on a Unix/Linux/ system, you can use the grep command
to search for lines in the dump.sql file produced by the
mysqldump command for "DROP TABLE IF EXISTS" and then pipe
that output into another grep command that searches only for lines containing
the particular string in the table name that you want to key on for dropping
tables. E.g., suppose you want to drop all tables that have example
as part of the table name:
$ grep "DROP TABLE IF EXISTS" dump.sql | grep example > drop.sql
You can check the drop.sql file output by the above commands to
verify that only the particular tables you wish to drop will be removed from
the database.
$ more drop.sql
DROP TABLE IF EXISTS `example_settings`;
DROP TABLE IF EXISTS `example_smileys`;
DROP TABLE IF EXISTS `example_spiders`;
If you are satisfied that only the tables you want removed from the database
will be deleted from the database, you can then issue the command:
mysql -u user -p database < drop.sql
E.g., for the example above, you could use:
$ mysql -u jdoe -p joe_db < drop.sql
Enter password:
The dump.sql and drop.sql files can then
be deleted.
[/software/database/mysql]
permanent link
Sat, Jun 21, 2014 12:23 pm
Prepending a character to all values in a column
I needed to prepend a "/" value to a directory field in a MySQL table named
files for every entry in the table. With a column named
Directory in the table, that can be done using the
UPDATE command. E.g.:
UPDATE fles SET Directory = Concat('/', Directory);
[/software/database/mysql]
permanent link
Tue, Jun 17, 2014 11:24 am
Creating a business category in Quicken 2014
I wanted to create a new business expense category in Quicken 2014 named
Hardware. But when I created a new expense category, the category
always defaulted to be a personal expense. I could not locate a means to
specify that I wanted the new category to be in the business rather than
personal group and I didn't see any way to change the classification to
business after the category was created. I could put the new business expense
category as a subcategory beneath an existing business category, but that is
not what I wanted to do. There is a way to put the new category as a top-level
category in the business group rather than have it be a subcategory, though,
by first creating it as a subcategory and then changing it.
- Click on Tools.
- Select Category List.
- Click on the Add Category button.
- Type a name for the new category in the Category Name field.
- Select the Subcategory of radio button and pick a business
category, such as "Supplies (Business)". Add a description if you like.
- Click on the Tax Reporting tab and make any changes, if any
are needed, there.
- Click on OK.
- Right-click on the new category in the category list, then select the
Expense radio button, rather than the Subcategory of one.
- Click on OK.
- Click on Done to close the Category List window.
The category will remain as a business category after the change.
[/financial]
permanent link
Sat, May 17, 2014 2:20 pm
Turning airplane mode on and off under Windows 8
To enable or disable "airplane mode" on a Windows 8 system, you can take
the following
steps.
[/os/windows/win8]
permanent link
Sat, Apr 19, 2014 4:47 pm
Making Firefox the default browser
If you wish to make Firefox the default browser on a Microsoft Windows
system, take the following steps:
- Open Firefox.
- Use Alt-T, i.e., the Alt and
T keys simultaneously, to bring up the tools menu.
- Select Options.
- Click on the Advanced tab.
- Click on the Make Firefox the default
browser button.
- At the Set Default Programs window
which then opens, click on Firefox.
- Click on Set this program as default.
- Click on the OK button. You can then
close the Default Programs window.
-
You should now see "Firefox is currently your default browser" in the
Options window where the Make Firefox the default browser button
appeared previously.
Click on the OK button in the Options
window.
Note: applies to Firefox 28 as well as earlier versions.
[/network/web/browser/firefox]
permanent link
Mon, Apr 14, 2014 9:47 pm
QuickBooks company files list from registry
If you wish to see the list of previously opened company files that would be
displayed inside QuickBooks when QuickBooks is open, but no company file is
open, without opening QuickBooks, you can query the registry key
HKEY_CURRENT_USER\Software\Intuit\QuickBooksCommon\QBFinder
using the
reg query command. E.g.:
C:\Users\JDoe>reg query HKEY_CURRENT_USER\Software\Intuit\QuickBooksCommon\QBFinder
HKEY_CURRENT_USER\Software\Intuit\QuickBooksCommon\QBFinder
0 REG_SZ c:\users\jdoe\documents\quickbooks\csi\c.s.i.qbw|23|professional
1 REG_SZ c:\users\jdoe\documents\quickbooks\moonpoint\moonpoint.qbw|23|professionalThe .qbw files displayed would be ones you could select by clicking
on them from the "No Company Open" window inside QuickBooks. The
"|23|professional" at the end can be ignored, if you only want to know
the file names and locations. The directory path and file names displayed
can then be used to backup any relevant QuickBooks files to another location
for archiving, for instance, without needing to open QuickBooks.
[/financial]
permanent link
Mon, Apr 14, 2014 9:19 pm
QuickBooks company file needs to be updated
If you see the following message when you attempt to open a company file
from a prior version of QuickBooks in QuickBooks 2013, which
prevents you from opening the file, you will need to provide a
user name and password for a QuickBooks account that has administrator
level access to the file instead of the account credentials you are
using.
Warning
This company file needs to be updated. Please ask your QuickBooks
Administrator to update the file.
OK
[/financial]
permanent link
Sun, Apr 06, 2014 9:40 pm
Printing to a PDF File with CutePDF Writer
Microsoft Windows operating systems don't provide by default an application
to print files in PDF format, but the CutePDF™ Writer program from
Acro Software Inc. is free and will give you the capability to produce a
PDF file as output from almost any application that supports printing.
[
More Info ]
[/reviews/software/windows/utilities/pdf]
permanent link
Wed, Apr 02, 2014 11:00 pm
Determining the day of the week for a date
I needed to determine the day of the week for a particular date several years
in the past. Rather than page back through the years using a
GUI calendar, I thought
I'd do it from the command line on a Linux system to which I had logged in
by
SSH, but couldn't remember the
format for the command to display the day of the week, so had to look it
up. The
date command on a Linux system can be used to display
information for dates other than the current one.
NAME
date - print or set the system date and time
SYNOPSIS
date [OPTION]... [+FORMAT]
date [-u|--utc|--universal] [MMDDhhmm[[CC]YY][.ss]]
DESCRIPTION
Display the current time in the given FORMAT, or set the system date.
-d, --date=STRING
display time described by STRING, not ‘now’There were several format options available to me.
| %a |
locale’s abbreviated weekday name (e.g., Sun) |
| %A |
locale’s full weekday name (e.g., Sunday) |
| %u |
day of week (1..7); 1 is Monday |
| %w | day of week (0..6); 0 is Sunday |
I wanted to determine the day of the week for May 30, 2005, so I could
use YYYYMMDD, i.e., 20050530 for the date with
any of those format parameters.
$ date --date="20050530" +%a
Mon
$ date --date="20050530" +%A
Monday
$ date --date="20050530" +%u
1
$ date --date="20050530" +%w
1
A calendar can be displayed at a shell prompt using the cal
command as well that will show you the day of the week for a date using
ASCII
characters, e.g.:
$ cal 05 2005
May 2005
Su Mo Tu We Th Fr Sa
1 2 3 4 5 6 7
8 9 10 11 12 13 14
15 16 17 18 19 20 21
22 23 24 25 26 27 28
29 30 31From that calendar, I can see that May 30 in 2005 was a Monday.
[/os/unix/commands]
permanent link
Mon, Mar 31, 2014 11:03 pm
Determining the boot disk for an OS X system
The
bless command, which can be run from a Terminal window,
can be used to determine the boot disk on an OS X system:
$ bless --info --getBoot
/dev/disk0s2
If you are interested in more details for that drive, you can use the
diskutil info command followed by the drive's designation.
E.g.:
$ diskutil info /dev/disk0s2
Device Identifier: disk0s2
Device Node: /dev/disk0s2
Part of Whole: disk0
Device / Media Name: Customer
Volume Name: Macintosh HD
Escaped with Unicode: Macintosh%FF%FE%20%00HD
Mounted: Yes
Mount Point: /
Escaped with Unicode: /
File System Personality: Journaled HFS+
Type (Bundle): hfs
Name (User Visible): Mac OS Extended (Journaled)
Journal: Journal size 24576 KB at offset 0x1119b000
Owners: Enabled
Partition Type: Apple_HFS
OS Can Be Installed: Yes
Media Type: Generic
Protocol: SATA
SMART Status: Verified
Volume UUID: A140B2C6-4C4F-3B14-B179-C1A7FE0325D4
Total Size: 249.2 GB (249199599616 Bytes) (exactly 486717968 512-Byte-Blocks)
Volume Free Space: 56.4 GB (56438132736 Bytes) (exactly 110230728 512-Byte-Blocks)
Device Block Size: 512 Bytes
Read-Only Media: No
Read-Only Volume: No
Ejectable: No
Whole: No
Internal: Yes
Solid State: No
[/os/os-x]
permanent link
Sun, Mar 30, 2014 10:38 pm
OnlineWebCheck HTML Validator
I've been using the
Markup Validation Service provided by the World Wide Web
Consortium (W3C) to check for errors in the HTML code for webpages on
this site, but recently came across another such free service, the
Free HTML & CSS Validation Service at OnlineWebCheck.com.
Like the W3C service, you can provide a URL for your website to be analyzed
for HTML errors. The service will display any errors found on a submitted
page and warnings for page elements that aren't errors, but which may
deserve closer scrutiny. The online service is free and allows you to
check URLs one-by-one. The service uses
CSE HTML Validator Pro,
which is software that runs on Microsoft Windows systems, or Linux and Mac
OSX with Wine. There is a free version of that software available for
download as well as paid versions with more features - see
Compare CSE HTML Validator Editions. I haven't yet tried that software
on a Microsoft Windows system yet, though, but have only used the online
validation service.
I found the service yesterday when the W3C service wasn't responding.
One warning I received for a submitted page was for the lack of a
language specification within the <HTML> start tag. The warning was:
The natural primary language is not specified. It is highly recommended
that the "lang" and/or "xml:lang" (for XHTML) attributes be used with
the "html" element to specify the primary language. For example, add
the attribute lang="en" for English or lang="fr" for French. Specifying
the language assists braille translation software, speech synthesizers,
translation software, and has other benefits.
<html>
I had been including the following within the <head> section:
<meta name="language" content="english">
The OnlneWebCheck.com validator noted in regards to it, though:
Though the W3C validation service had never issued any warnings nor
errors related to the lack of inclusion of the language attribute within
the <HTML> tag or use of the meta tag, at the W3C site
at
Specifying the language of content: the lang attribute
webpage, I found:
Language information specified via the
lang
attribute may be used by a user agent to control rendering in a
variety of ways. Some situations where author-supplied language information may
be helpful include:
- Assisting search engines
- Assisting speech synthesizers
- Helping a user agent select glyph variants for high quality typography
- Helping a user agent choose a set of quotation marks
- Helping a user agent make decisions about hyphenation,
ligatures, and spacing
- Assisting spell checkers and grammar checkers
The recommendation made for assisting search engines and browsers to
determine the language for webpages is to include the language attribute
within the <html> tag as shown below:
<html lang="en">
...
</html>
Or for XHTML:
<html xmlns="http://www.w3.org/1999/xhtml" lang="en" xml:lang="en">
...
</html>
So, I decided to modify the template that I use for pages to include the
language attribute within the <html> tag, i.e., to use
<html lang="en">, and to include the attribute within
the <html> tag for Blosxom's head.html file.
If a page is in another language than English, the appropriate code
can be chosen from the
ISO 639-1 two-letter language codes.
ISO 639-1 defines abbreviations for languages. In HTML and XHTML they can be
used in the lang and xml:lang attributes.
[/network/web/design]
permanent link
Sat, Mar 29, 2014 4:24 pm
Google Analytics Add-on for Google Sheets
If you use
Google
Analytics, for monitoring your website, Google now provides an
add-on for Google Sheets, which is Google's equivalent to Microsoft Excel,
available through Google Docs, that allows you to incorporate Google Analytics
data within a Google Sheets worksheet.
[ More Info ]
[/network/web/services/google]
permanent link
Sat, Mar 29, 2014 10:19 am
Cell Padding in a Table
There are multiple ways to add padding around text
within cells in a table. Specifying
<table
cellpadding="ypx"> with
y
representing the number of pixels of padding will add padding to the left,
right, top, and bottom of the text. If you only wish to have additional
padding at the left and right of the text, you can do so by
CSS, e.g.:
<style type="text/css">
.padded {padding-left: 10px; padding-right: 10px;}
</style>
You can then apply the class "padded" to each td in the
table.
[ More Info ]
[/network/web/design]
permanent link
Fri, Mar 28, 2014 10:12 pm
Problem with Blosxom calendar cache
I use the
Calendar Plugin for Blosxom on this site. When I checked the site
with the
Xenu Link Sleuth tool, which reveals broken links, today I found it
reporting errors for urls with "//" in the directory path in the URL.
It took me a few minutes to realize that the errors were due to the
calendar displayed for the blog that points to prior entries.
When I looked at the URLs for various days on this month's calendar,
I saw that the links were all appearing similar to the following one:
http://support.moonpoint.com/blog/blosxom/2014/03//RS=%5EADAZpNNfKrcEOr1DFixlJAHJ_euLow-/2014/03/04/2014/03/2014/03/01/
They had "RS=" and "euLow-" followed by repetitions of the year
and month in the URL. I knew that the links had been appearng normally, so
I suspected the problem was caused when I posted an entry this morning.
Sometimes when I've worked on something previously, but not yet posted it,
I will change the time on the file associated with the entry to point to the
date and time I worked on it or when I edit an entry I may set its time
stamp to the original date and time after I've finished editing it. I had
done that this morning, so I suspected there was a problem with the
calendar's cache file, .calendar.cache, which is located
in the Blosxom plugins state directory, plugins/state. The
file can be deleted; it will be recreated automatically when the Blosxom
blog is viewed again. I deleted the file and refreshed the page in the browser
with which I was viewing the site and all of the links for the calendar
then appeared normally.
[/network/web/blogging/blosxom]
permanent link
Fri, Mar 28, 2014 9:22 pm
Xenu Link Sleuth
When I checked the error log for this site this morning, I noticed an
entry pointing to a nonexistent file on the site, which led me to check
the Apache CustomLog file to look for information on why someone might
have followed a link to a file that never existed on the site. I didn't
discover the source of the incorrect link, but in the process of checking
for that incorrect link I found a very useful tool, Xenu Link Sleuth, that
revealed a signficant problem with the site due to a change I made this
morning and pointed out broken internal links on the site.
[ More Info ]
[/network/web/tools]
permanent link
Fri, Mar 28, 2014 10:46 am
Determing the NTP servers in use on a Mac OS X system
If you need to know the Network Time Protocl (NTP) server in use on a Mac
OS X system you can use the command
systemsetup -getnetworktimeserver
or you can look at the contents of the
/etc/ntp/conf
file.
$ systemsetup -getnetworktimeserver
Network Time Server: ntp.example.com
$ cat /etc/ntp.conf
server ntp.example.com minpoll 12 maxpoll 17
server time.apple.com
The minpoll and maxpoll values specify the minimum and maximum poll
intervals for querying the time server as a power of 2 in seconds.
So, for the example above, where the time server is ntp.example.com,
the minimum interval is 2 to the power of 12 or 4,096 seconds, which is
a little over an hour (1.14 hours). The minimum interval defaults to 6,
which equates to 2 to the power of 6, which is 64 seconds. The maximum
interval defaults to 10, i.e. 2 raised to the power 10, which is 1,024
seconds. The upper limit for the value is 17, which is 36.4 hours. A
secondary time server is also shown in the example above. The secondary
time server could be used when the primary one is unavailable.
[/os/os-x]
permanent link
Wed, Mar 26, 2014 9:21 pm
Green border around Google Sheets cell
If a green border appears unexpectedly around a cell in a Google Sheets
spreadsheet, then the worksheet is likely open elsewhere. If you've shared
the spreadsheet, someone with whom you have shared it may have it open or
you may have it open on another system or even in another tab within your
browser. In that case the cell that is currently selected in the other
open instance of the worksheet will be highlighted by a green border.
At the top of the worksheet you will also see the number of other instances
of the open worksheet. If it is open in just one other place you will see "1
other viewer" at the top right of the worksheet next to a green square.
If you move the cursor over the cell with the green border, you will
see the name of the other user displayed, or your own logged in name, if you
have the worksheet open multiple times. You can also put the cursor over
the green squares at the top right area above the spreadsheet to see those
names. If the worksheet was open more than twice, e.g., if it was open
3 times, you would see additional green boxes corresponding to the number
of other open instances of it.
[/network/web/services/google]
permanent link
Tue, Mar 25, 2014 9:13 pm
Not enough free disk space for Entourage
If Entourage display the message "Your hard disk is full. The Entrourage
database requires additional free space. Entourage will now quit so you
can make more space available on your hard disk by moving or deleting
files.", if you store a lot of email one area where you may be able to
free disk space is in old identities or backups for an identity beneath
~/Documents/Microsoft User Data
[More Info ]
[/os/os-x/software/office]
permanent link
Mon, Mar 24, 2014 8:17 am
Attempted SQL injection attack
When I checked the webserver's error log file this morning, I noticed
the following two entries related to the IP address 221.11.108.10:
[Mon Mar 24 08:15:07 2014] [error] [client 221.11.108.10] File does not exist: /
home/jdoe/public_html/ctscms
[Mon Mar 24 08:15:12 2014] [error] [client 221.11.108.10] File does not exist: /home/jdoe/public_html/plus, referer: http://support.moonpoint.com/plus/search.php?keyword=as&typeArr[111%3D@`\\'`)+and+(SELECT+1+FROM+(select+count(*),concat(floor(rand(0)*2),(substring((select+CONCAT(0x7c,userid,0x7c,pwd)+from+`%23@__admin`+limit+0,1),1,62)))a+from+information_schema.tables+group+by+a)b)%23@`\\'`+]=a
There is no ctscms file nor directory, nor do I use a search.php file, nor
even have a directory named plus on this web site, so the queries seemed
suspicious.
Performing a Google search on the attempted query to search.php, which
appears to be an SQL query, I
found links to a number of sites in the Chinese language. E.g.,
dedecms plus / search.php latest injection vulnerability (translated
to English).
The query I saw in the Apache error log appeared to be an
SQL injection
attack. In
Arrays in requests, PHP and DedeCMS, an InfoSec Handlers Diary Blog entry,
I found the following in relation to an SQL injection attack used against
/plus/download.php, which is a PHP script associated
with the DedeCMS
Content
Management System (CMS):
And this definitely looks malicious. After a bit of research, it turned
out that this is an attack against a known vulnerability in the DedeCMS,
a CMS written in PHP that appears to be popular in Asia. This CMS has
a pretty nasty SQL injection vulnerability that can be exploited with
the request shown above.
So I blocked any further access to the server hosting this
site from that IP address using a route reject command.
# route add 221.11.108.10 reject
[root@frostdragon ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
221.11.108.10 - 255.255.255.255 !H 0 - 0 -
171.216.29.9 - 255.255.255.255 !H 0 - 0 -
The 221.11.108.10 IP address
is allocated to an entity in China. I blocked another Chinese IP address,
171.216.29.9 two days ago.
The
Arrays in requests, PHP and DedeCMS blog entry indicated the
attacker discussed in that article was using a script that identified itself
with a
user agent string
of
WinHttp.WinHttpRequest:
Additionally, as you can see in the log at the top, the User Agent string
has been set to WinHttp.WinHttpRequest, which indicates that this request
was created by a script or an attack tool executed on a Windows machine.
When I checked the Apache CustomLog to see what user agent string was
submitted with the queries to this site, I saw it was "Googlebot/2.1", so
the attacker appears to be using an updated script.
that misidentifies itself as
Googlebot. The Internet Storm Center blog entry was posted 6 months
ago and discusses a log entry from September 5, 2013. The log entry posted
in that article shows a source IP address of 10.10.10.10, which is a
private IP address
substituted in the article for the actual IP address from
which the attack originated.
I saw the following in my log:
221.11.108.10 - - [24/Mar/2014:08:15:07 -0400] "GET /ctscms/ HTTP/1.1" 404 291 "
-" "Googlebot/2.1 (+http://www.google.com/bot.html)"
221.11.108.10 - - [24/Mar/2014:08:15:12 -0400] "GET /plus/search.php?keyword=as&
typeArr[111%3D@`\\'`)+and+(SELECT+1+FROM+(select+count(*),concat(floor(rand(0)*2
),(substring((select+CONCAT(0x7c,userid,0x7c,pwd)+from+`%23@__admin`+limit+0,1),
1,62)))a+from+information_schema.tables+group+by+a)b)%23@`\\'`+]=a HTTP/1.1" 404
299 "http://support.moonpoint.com/plus/search.php?keyword=as&typeArr[111%3D@`\\
'`)+and+(SELECT+1+FROM+(select+count(*),concat(floor(rand(0)*2),(substring((sele
ct+CONCAT(0x7c,userid,0x7c,pwd)+from+`%23@__admin`+limit+0,1),1,62)))a+from+info
rmation_schema.tables+group+by+a)b)%23@`\\'`+]=a" "Googlebot/2.1 (+http://www.go
ogle.com/bot.html)Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, a
pplication/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-power
point, application/msword, */*"
References:
-
Stopping an Attacker with the Route Reject Command
MoonPoint Support
Date: April 15, 2007
-
Arrays in requests, PHP and DedeCMS
Internet Storm Center
By: Bojan, ISC Handler
[/security/attacks]
permanent link
Sun, Mar 23, 2014 2:08 pm
Julian date in spreadsheets
The
ordinal date, i.e., the day of the year, is a number that ranges from 1 for January 1 through 365
or 366 for December 31, depending if the year is a
leap year.
The ordinal date is also referred to as the
"
Julian date", though
in astronomy "Julian date" is not the ordinal date, but
a serial date system starting on January 1, 4713 B.C.E.
If you wish to display the current ordinal date in a spreadsheet, such as a Microsoft Excel or a
Google Sheets worksheet you can use the formula below:
=TEXT(TODAY() ,"yyyy")&TEXT((TODAY() -DATEVALUE("1/1/"&TEXT(TODAY(),"yy"))+1),"000")
That formula will insert the current day in Julian format with a four-digit
year. E.g. for March 23, 2014, it would result in 2014082
appearing in the cell where the forumla is used, since March 23, 2014 is
the 82nd day of 2014. If you just wish to display
the day of the year and not the year, you can use the formula below:
=TEXT((TODAY() -DATEVALUE("1/1/"&TEXT(TODAY(),"yy"))+1),"000")
That forumula will display 082 in the cell in which the
formula is used.
References:
-
Insert Julian dates
Support - Office.com
[/os/windows/office/excel]
permanent link
Sun, Mar 23, 2014 1:31 pm
W3C Validation
The
World Wide Web Consortium
(W3C) is an international standards organization for the
World Wide Web (WWW).
Among the services offered by the W3C are a
Markup Validation Service a
Link Checker,
a
CSS Validation Service,
and
RSS Feed Validation Service.
The services are free.
The markup
validation service allows you to submit a
URL for a webpage to be
checked by the service or to upload an HTML file to be checked for
incorrect HTML code. If the code in a webpage is incorrect, you may not
see the results you expect for the webpage when it is displayed in a browser
or it may display incorrectly in some browsers used by visitors to the page.
The W3C tool will notify you of the types of errors on the page and the
line numbers on which they are found. You can match those lines numbers with
the appropriate lines in the code in browsers that allow you to view the
source code of a page.
You can provide a URL to the link checker tool and it will determine if any
of the links on the webpage are invalid.
The CSS validation service allows you to check the validity of
Cascading Style Sheets (CSS)
used on webpages to control the appearance and formatting of the pages.
You can provide a URL for a CSS or upload a CSS file to be verified.
The W3C Feed Validation Service
will check the syntax of Atom
or RSS feeds. E.g., if
you use RSS to publish updated information on blog entries, you can provide
the URL for the index.rss file on your site.
The W3C provides other tools as well at
Quality Assurance Tools.
All of the software developed at the W3C is Open Source / Free software, which
means that you can use the software for free and download the code, if you wish.
You can also modify the code to suit your own purposes, if you wish.
There is also a paid W3C Validator
Suite™, if you wish to have the W3C validate an entire site
automatically rather than you validating pages individually.
Note: the W3C validation services can't check pages that require authentication,
but can only check pages that are accessible from the Internet without
passwords or files that you upload to be checked.
[/network/web/design]
permanent link
Sat, Mar 22, 2014 10:49 pm
Blocking Internet access except for virus scanning sites
After a system became infected with malware, I disconnected its network
cable then added rules to the firewall separating it from the Internet
to block all Internet access except for
DNS access to its designated
DNS server provided by the user's
ISP. I then granted
access to the
VirusTotal
IP addresses on all ports. VirusTotal is a website belonging to Google
that will allow you to scan files you upload to it with multiple antivirus
programs to determine if they may be malware.
| Name | IP Addresses |
|---|
| virustotal.com |
216.239.32.21
216.239.34.21
216.239.36.21
216.239.38.21
|
| www.virustotal.com |
74.125.34.46 |
After implementing the firewall rules, I reconnected the network cable
to the system.
Since accessing http://virustotal.com
redirects one to
http://www.virustotal.com, I wasn't able to access the VirusTotal website
until I added the IP address 74.125.34.4 to the list of destination
IP addresses the infected system was allowed to access through the
firewall. Even though I could then access the site's webapge and select
a file to upload, I was unable to actually upload a file that I wanted
to check for malware.
So I then added the IP address for the
Jotti's malware scan website to the
permitted outbound access list for the infected system. I was able to
access it with a web browser on the system and upload a suspect file to
have it scanned by the 22 antivirus programs the site currently uses
to scan uploaded files.
| Name | IP Addresses |
|---|
| virusscan.jotti.org |
209.160.72.83 |
[/security/scans]
permanent link
Sat, Mar 22, 2014 5:42 pm
Blocking access from 171.216.29.98
I noticed entries in Apache's error log today associated with IP address
171.216.29.98:
[Sat Mar 22 15:23:58 2014] [error] [client 171.216.29.98] PHP Notice: Undefined index: HTTP_USER_AGENT in /home/jdoe/public_html/index.php on line 39
[Sat Mar 22 15:23:58 2014] [error] [client 171.216.29.98] PHP Notice: Undefined index: HTTP_USER_AGENT in /home/jdoe/public_html/index.php on line 46
[Sat Mar 22 15:23:58 2014] [error] [client 171.216.29.98] attempt to invoke directory as script: /home/jdoe/public_html/blog/
The error was occurring because of PHP code in the file that checks the
value for
HTTP_USER_AGENT.
I found that the IP address, which is allocated to a system in China, is
listed at the Stop Forum Spam site
as being associated with someone trying to post spam into forums today - see
171.216.29.98.
And when I checked Apache's CustomLog to check the
user agent for the
browser the user or software program running at the site might be using to
identify itself, I found that the log entries indicated that it wasn't
providing user agent information, which browsers and web crawlers normally
provide. The log also showed that other than that one file at the
site's document root, the user or program accessing the site only
queried a directory that has "forums" as part of the path. I have
blog entries posted on forum software, so that may have prompted the
visit to the site from that IP address, if the person or program is
looking for sites where he or it can post forum spam.
I checked the "reputation" of the IP address at other sites that provide
information on whether an IP address has been noted to be associated with
malicous activity and found the following:
-
Site: WatchGuard
Reputation Authority
Rating: Bad
Reputation Score: 95/100
Comment: The score indicates the overall ReputationAuthority reputation
score, including the name and location of the ISP (Internet Service
Provier), for the specified address. A score of 0-50 indicates a good
to neutral reputation. 51-100 indicates that threats have been detected
recently from the address and the reputation has been degraded.
-
Site:
Barracuda Reputation
Reputation: Poor
Comment:
-
Site: McAfee Trusted Source
Reputation: Unrated
Comment:
-
Site:
Check Your IP Reputation - Miracare of Mirapoint
Reputation: High Risk
Comment: This IP address is used for sending Spam on a regular basis
-
Site:
BrightCloud Security Services URL/IP Lookup
Reputation: High Risk
Comment: Location - Chengdu, China. Spam Sources found. Webroot IP Reputation
is listed as "High Risk", but lower down on the page the status assigned
to the address is "Moderate Risk".
To stop any futher access to the server from that IP address, from the
root account, I used the route command to reject access by the IP address.
# route add 171.216.29.9 reject
Note: the command is valid on a Linux system, but though the route
command is available on a Microsoft Windows system, that operating system
doesn't support the "reject" parameter.
The blocked route can be seen by issuing the route command with no
parameters.
# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
171.216.29.9 - 255.255.255.255 !H 0 - 0 -
If I ever want to permit access to the server from that IP address again,
I could use route del 171.216.29.9 to permit access from that
address.
References:
-
Stopping an Attacker with the Route Reject Command
MoonPoint Support
Date: April 15, 2007
[/security/scans]
permanent link
Sat, Mar 22, 2014 2:10 pm
Renamed Website Files Still Being Crawled
I've noticed in the site's error logs that files that haven't existed on
the site for years are producing error entries when
web crawers still
attempt to access them. Apparently, elsewhere on the web that are still
links pointing to the nonexistent files, which has led me to conclude that
I need to create redirects for those files on the site that I move or rename,
if the files have been on the site for any significant lengthh of time.
[ More Info ]
[/network/web/crawlers]
permanent link
Fri, Mar 21, 2014 9:55 pm
Favicon.ico
While trying to reduce entries in the site's Apache error log, I've
decided I should eliminate the many "File does not exist" error messages
for
favicon.ico. I often see attempts to access that file
from the site's root directory, but, since there is no such file, a lot
of extraneous entries appear in the error log file for it when browsers
attempt to access it.
Favicon is short for
"favorite icon" and is also known as a "shortcut icon". Favicons were first
supported in March 1999 when Microsoft released
Internet Explorer
5. In December of 1999, the
World Wide
Web Consortium (W3C) made it a standard element in HTML 4.01
recommendation to be used with a
link relation in
the
<head> section of an HTML document. It is now widely supported
among browsers.
The original purpose of a favicon was to provide a small icon, commonly
16 x 16 pixels, that a browser would associate with a website when a user
bookmarked the site. Today, browsers typically display a page's favicon
in their address bar and
sometimes also in the browser's history display as well as using it in
association with a bookmark. Those browsers that provide a
tabbed
document interface (TDI) also typically display the favicon next to
a page's title on a tab for the site with which the favicon is associated.
I had an icon I had used years ago, but decided I liked
the crescent
moon icon, I found at favicon.cc
better. That site provides a tool that will allow you to create your
own favicon. It also provides many free icons that you can download.
To use the icon file, you can simply place the favicon.ico
in the root directory of the website where browsers can automatically locate
it. Or you can place it elsewhere on the site and specify its location
by inserting the following code within the head section of the HTML code
for a page, substituing the relative path from the website's document
root for YOUR_PATH.
<link href="/YOUR_PATH/favicon.ico" rel="icon" type="image/x-icon" />
Something like the following is also acceptable. I.e., in addition to
specifying the file's location you can can also give the file a name
other than favicon.ico.
<link rel="icon" href="http://example.com/myicon.ico" />
The file also does not have to be a .ico file. See the
file format
support section of the Wikipedia
Favicon article
for other image file formats that are supported by various browsers.
[/network/web/browser]
permanent link
Thu, Mar 20, 2014 9:21 pm
Check marks, x marks, and checkboxes
If you need to represent a
check mark,
aka tick mark, or an
x
mark, aka cross, x, ex, exmark, and into mark, or a
checkbox, aka check box,
tick box, and ballot box, which someone can checkmark, on a webpage, there
are a number of HTML codes that can be used to do so. The codes can be
represented in
decimal
or
hexadecimal
format depending on your personal preference.
| | | Code |
|---|
| Symbol | Description | Decimal | Hexadecimal |
|---|
| ☐ | ballot box | ☐ | ☐ |
| ☑ | ballot box with check | ☑ | ☑ |
| ☒ | ballot box with x | ☒ | ☒ |
| ✅ | white heavy check mark | ✅ | ✅ |
| ✓ | check mark | ✓ | ✓ |
| ✔ | heavy check mark | ✔ | ✔ |
| × | mulitplication sign | × | × |
| ✕ | large multiplication sign | ✕ | ✕ |
| ✖ | heavy multiplication sign | ✖ | ✖ |
| ⨯ | cross product, also known as Gibb's vector
product | ⨯ | ⨯ |
| ✗ | ballot x | ✗ | ✗ |
| ✘ | heavy ballot x | ✘ | ✘ |
If you see squares or question marks instead of the symbols, you may need an appropriate language pack installed to display the symbols.
[/network/web/html]
permanent link
Wed, Mar 19, 2014 11:17 pm
AuthUserFile not allowed here
After setting up a redirect similar to the following in an .htaccess file in
a directory, I found that I would get a
500 Internal Server Error
with the message "The server encountered an internal error or
misconfiguration and was unable to complete your request." whenever I tried
to access a file in a password-protected subdirectory beneath the one
in which I had created the .htaccess file to have the Apache server
redirect visitors accessing an old .html file that I had replaced with a
.php one.
Redirect 301 /dir1/dir2/example.html /dir1/dir2/example.php
In the Apache error log for the website, I saw the following:
[Wed Mar 19 21:05:17 2014] [alert] [client 192.168.0.10] /home/jdoe/public_html/dir1/dir2/dir3/.htaccess: AuthUserFile not allowed here, referer: http://support.moonpoint.com/dir1/dir2/example.php
That error log entry was created when I clicked on a link I had
in example.php to access a file in the directory dir3, which was below the
one in which example.php was located.
To allow the redirect to work, I had inserted the following code in
the VirtualHost section for the website within Apache's
/etc/httpd/conf/httpd.conf file.
<Directory /home/jdoe/public_html/dir1/dir2>
AllowOverride FileInfo
</Directory>
The .htaccess file for controlling access to the subdirectory
dir1/dir2/dir3 had worked fine until I created another
.htaccess file above it in dir2 for the redirect. The one for controlling access
to dir3 with a username and password was similar to the following:
AuthUserFile /home/jdoe/public_html/.htpasswd-test
AuthGroupFile /dev/null
AuthName Testing
AuthType Basic
Require user test1
Because it contained AuthUserFile and
AuthGroupFile, but I didn't specify AuthConfig
within the <Directory> section for the virtual host
in the httpd.conf file, but only FileInfo
for AllowOverride, the authorization control no longer
worked. When I changed the AllowOverride line to that
shown below and restarted Apache with apachectl restart
then both the redirect for the file in dir2 and the HTTP
basic access
authentication method for files in the subdirectory dir3
beneath dir2 both worked.
<Directory /home/jdoe/public_html/dir1/dir2>
AllowOverride AuthConfig FileInfo
</Directory>
I had forgotten that by limiting AllowOverride to just
FileInfo for dir2, I was effectively nullifying any other
type of overrides in any subdirectores beneath it.
References:
-
Apache Core Feartures
Apache HTTP Server Project
[/network/web/server/apache]
permanent link
Tue, Mar 18, 2014 10:34 pm
Use netsh to determine WLAN driver version
To obtain information about the driver for the wirless interface in a
Microsoft Windows system, the
netsh command may be used.
After issuing the command from a command prompt, you can type
wlan,
then
show drivers to show the properites of the wireless
LAN drivers on the system.
C:\Users\JDoe>netsh
netsh>wlan
netsh wlan>show drivers
Interface name: Wi-Fi
Driver : Realtek RTL8188E Wireless LAN 802.11n PCI-E NIC
Vendor : Realtek Semiconductor Corp.
Provider : Realtek Semiconductor Corp.
Date : 2/27/2013
Version : 2007.10.227.2013
INF file : C:\windows\INF\oem13.inf
Files : 2 total
C:\windows\system32\DRIVERS\rtwlane.sys
C:\windows\system32\drivers\vwifibus.sys
Type : Native Wi-Fi Driver
Radio types supported : 802.11n 802.11b 802.11g
FIPS 140-2 mode supported : No
802.11w Management Frame Protection supported : Yes
Hosted network supported : Yes
Authentication and cipher supported in infrastructure mode:
Open None
WPA2-Personal CCMP
Open WEP-40bit
Open WEP-104bit
Open WEP
WPA-Enterprise TKIP
WPA-Personal TKIP
WPA2-Enterprise TKIP
WPA2-Personal TKIP
WPA-Enterprise CCMP
WPA-Personal CCMP
WPA2-Enterprise CCMP
Vendor defined TKIP
Vendor defined CCMP
Vendor defined Vendor defined
Vendor defined Vendor defined
WPA2-Enterprise Vendor defined
WPA2-Enterprise Vendor defined
Vendor defined Vendor defined
Vendor defined Vendor defined
Authentication and cipher supported in ad-hoc mode:
Open None
Open WEP-40bit
Open WEP-104bit
Open WEP
WPA2-Personal CCMP
IHV service present : Yes
IHV adapter OUI : [00 e0 4c], type: [00]
IHV extensibility DLL path: C:\windows\system32\Rtlihvs.dll
IHV UI extensibility ClSID: {6c2a8cca-b2a2-4d81-a3b2-4e15f445c312}
IHV diagnostics CLSID : {00000000-0000-0000-0000-000000000000}
netsh wlan>Or you can issue the netsh wlan show drivers command
at the command prompt to have the information shown and be immediately
returned to the command prompt.
[/os/windows/commands]
permanent link
Mon, Mar 17, 2014 5:48 pm
Recursively locating HTML files
To recursively locate files of a particular file type, e.g., HTML files, on
a Unix, Linux, or OS X system from a command line interface, aka shell prompt,
the following command can be used:
find . -name "*.html"
The subdirectory path will be included in the output along with the file names.
If you wish to have a count of the number of such files, you can use
either of the two commands below:
find . -name "*.html" | grep -c .
find . -name "*.html" | wc -l
Note: if you use the grep command, be sure to include the dot after the
-c.
[/os/unix/commands]
permanent link
Mon, Mar 17, 2014 5:30 pm
How to have Firefox forget basic access authentication credentials
If you've accessed a webpage that uses HTTP
basic access authentication to prompt for a user name and password
to control access to a web page within Firefox, you can have Firefox
"forget" those credentials so you can enter different ones by the
following two methods.
Method 1
Note: this method applies for Firefox 27 and may not apply
to all other versions.
-
Click on Firefox at the upper, left-hand corner of the Firefox window
to access its menu.

-
Select History.
-
Select Clear Recent History.
-
If the site was accessed within the last hour, you can leave "time range to
clear" set at "Last Hour"; if not, you may need to change the value to a
longer period. With Details visible, you can clear the checkmarks for
all the items, except Active Logins, if you wish.
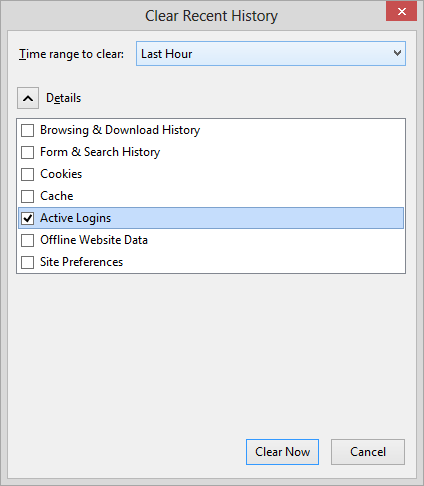
-
Click on the Clear Now button.
Method 2
Note: This method may work for some other browsers as well as Firefox, but
won't work for Internet Explorer. An advantage to this method is it
is applied to just the particular website. It doesn't cause Firefox
to forget the credentials for any other websites.
With some browsers, you can specify the credentials to use to access
a webpage protected by basic authenticaion by putting the userid and
password in the URL for the page with
http://user:pass@www.example.com, substituting
a username for the site for "user" and a password that goes
with that username for "pass" in the address line, e.g.
http://bob:mypassword@www.example.com.
If you put http://abc@www.example.com/some-page.html in the
address bar for the webpage some-page.html that is protected
by the basic authentication method, then the browser can be caused to
forget a valid set of credentials previously used to access that page that
Firefox remembers and will normally reuse until you exit from Firefox. You
will be prompted by the website for a new set of valid credentials,
allowing you to enter a new user name and passwrod to access the page
or cause your browser to forget the previously valid ones.
[/network/web/browser/firefox]
permanent link
Sun, Mar 16, 2014 11:59 am
List of accounts on a Linux or Unix system
To see a list of accounts on a Linux or Unix system, the following command
can be used:
cut -d: -f1 /etc/passwd
[/os/unix/commands]
permanent link
Sun, Mar 16, 2014 9:41 am
Determining low, high, average, and median values with Google Sheets
To determine the smallest, largest, average, and median value for a column
of numbers in a
Google Sheets spreadsheet, the
MIN,
MAX,
AVERAGE, and
MEDIAN functions can be used.
For a column of numbers from A2 to A66, the following forumlas could
be used:
| Minimum: | MIN(A2:A66) |
| Maximum: | MAX(A2:A66) |
| Average: | AVERAGE(A2:A66) |
| Median: | MEDIAN(A2:A66) |
[/network/web/services/google]
permanent link
Sat, Mar 15, 2014 11:17 am
Changing the Channel Number on a NetGear CVG824G Router
Sometimes wireless network disconnections and slow data transfers can
be caused by interference between multiple
wireless access
points, such as neighboring wireless routers using the same radio
frequency channel for communications. Simply changing the channel number
used for wireless communications by one of the routers may resolve the problem.
For a NETGEAR® Wireless Cable Voice Gateway Model CVG824G device,
the channel number can be changed using
these steps.
[/hardware/network/router/netgear]
permanent link
Fri, Mar 14, 2014 10:30 pm
Excel countifs function
Microsoft Excel, starting with Excel 2007, provides a function,
countifs, to count the number of occurrences of some item while
stipulating multiple criteria be met. The function also is available in
Microsoft® Excel® 2008 for Mac. The function works like the
countif function, but whereas
countif only permits one
criteria to be stipulated,
countifs supports one or
more criteria. The syntax for
countifs is:
COUNTIFS( criteria_range1, criteria1, [criteria_range2, criteria2, ...
criteria_range_n, criteria_n] )
As an example, suppose I have the following worksheet in a spreadsheet:
| <> |
A |
B |
C |
D |
| 1 |
Number | Project | Approved | Funded |
| 2 | 38397 | Alpha | 2/12/14 | N |
| 3 | 38400 | Alpha | 2/7/14 | Y |
| 4 | 38407 | Beta | 3/4/14 | N |
| 5 | 38408 | Alpha | 2/25/14 | N |
| 6 | 38409 | Epsilon | 3/14/14 | Y |
| 7 | 38412 | Gamma | 3/14/14 | Y |
| 8 | 38413 | Zeta | 3/14/14 | Y |
| 9 | 38415 | Alpha | 3/14/14 | N |
| 10 | | | | |
| 11 |
Approved today |
4 |
| |
| 12 |
Approved and funded today |
3 |
| |
Number represents work request numbers associated with various projects.
Column C has dates for when the work requests were approved with today's
date being March 14, 2014. Column D indicates whether the requests have
been funded with a "Y" for "yes" and a "N" for "no".
If I wished to count the number of work requests funded today, I
could use the formula =COUNTIF(C2:C10,TODAY()) in cell B11.
COUNTIF works because I have only one criteria. But, if I wanted
to count the number that were approved and funded today, then I
would need to use COUNTIFS rather than COUNTIF. I could use the
formula =COUNTIFS(C2:C10,TODAY(),D2:D10,"Y") in
cell B12.
[/os/windows/office/excel]
permanent link
Fri, Mar 14, 2014 9:55 am
Netsh command to show available Wi-Fi networks
On a system running Microsoft Windows, you can see the available Wi-Fi
networks near the system,the signal strengths, channel numbers, etc.
for each from a
command prompt using the command
netsh show
networks mode=Bssid
C:\Users\JDoe>netsh
netsh>wlan
netsh wlan>show networks mode=Bssid
Interface name : Wi-Fi
There are 5 networks currently visible.
SSID 1 : 558935
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : 0c:54:a5:48:19:e5
Signal : 81%
Radio type : 802.11n
Channel : 1
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 2 : Haze
Network type : Infrastructure
Authentication : WPA2-Personal
Encryption : CCMP
BSSID 1 : 94:44:52:5a:54:54
Signal : 83%
Radio type : 802.11n
Channel : 11
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 3 : 08FX02038916
Network type : Infrastructure
Authentication : Open
Encryption : WEP
BSSID 1 : 00:18:3a:8a:01:c5
Signal : 49%
Radio type : 802.11g
Channel : 6
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 4 : linksys
Network type : Infrastructure
Authentication : Open
Encryption : None
BSSID 1 : 00:13:10:fa:ef:a3
Signal : 45%
Radio type : 802.11g
Channel : 6
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
SSID 5 : Hickox
Network type : Infrastructure
Authentication : Open
Encryption : WEP
BSSID 1 : 0c:d5:02:c5:e8:8c
Signal : 48%
Radio type : 802.11g
Channel : 11
Basic rates (Mbps) : 1 2 5.5 11
Other rates (Mbps) : 6 9 12 18 24 36 48 54
netsh wlan>
[/os/windows/commands]
permanent link
Thu, Mar 13, 2014 11:15 pm
Netsh show interfaces
The signal strength for wireless network connectivity can be checked
on a Windows system from the command line using the
netsh
command. From a command prompt issue the command
netsh
and when the netsh prompt appears issue the command
wlan
and then
show interfaces.
C:\Users\JDoe>netsh
netsh>wlan
netsh wlan>show interfaces
There is 1 interface on the system:
Name : Wi-Fi
Description : Realtek RTL8188E Wireless LAN 802.11n PCI-E NIC
GUID : d79cd37a-fe78-482b-b23e-af4953ba9f6b
Physical address : 48:d2:24:68:e1:aa
State : connected
SSID : Haze
BSSID : 94:44:52:5a:54:54
Network type : Infrastructure
Radio type : 802.11n
Authentication : WPA2-Personal
Cipher : CCMP
Connection mode : Auto Connect
Channel : 11
Receive rate (Mbps) : 72
Transmit rate (Mbps) : 72
Signal : 100%
Profile : Haze
Hosted network status : Not available
netsh wlan>The signal strength for the wireless connection is shown on the
Signal line, e.g., 100% in the case above. The wireless
connection is using the 802.11n
wireless network standard, which is one of the
802.11 standards.
[/os/windows/commands]
permanent link
Wed, Mar 12, 2014 11:40 pm
Adding "rel=nofollow" to Blosxom advanced search option for find plugin
I've noticed in the logs for the blog that search engines are trying to
access pages with "?advanced_search=1" in the URL. E.g., I've seen a lot
of entries similar to the following:
5.10.83.52 - - [12/Mar/2014:00:32:23 -0400] "GET /blog/blosxom/<a%20href=/<a%20h
ref=/<a%20href=/2008/05/01/2008/03/2008/05/05/network/email/clients/outlook/2008
/10/network/email/sendmail/2008/07/network/email/clients/outlook/2008/05/25/2008
/12/2008/05/18/2008/05/03/index.html?advanced_search=1 HTTP/1.1" 200 12080 "-" "
Mozilla/5.0 (compatible; AhrefsBot/5.0; +http://ahrefs.com/robot/)"
They seem to be getting erroneous URLs reflecting a directory structure
related to dates that doesn't exist on the system. The URLs appear to be
related to the find plugin, since its search option includes code for
"advanced_search=1", so I've edited the Perl code for that plugin to
include rel="nofollow" at the end of the URL generated for
the advanced search capability.
The orignal code was:
<a href="$blosxom::url/$path_withflavour?advanced_search=1">Advanced Search</a>
The line is now:
<a href="$blosxom::url/$path_withflavour?advanced_search=1" rel="nofollow">Advanced Search</a>
Adding rel="nofollow" to a URL tells search engines, such as
Google's search engine not to follow any link that includes the nofollow
parameter.
The following meta tag can be included in the head section of the HTML code
for a page to tell search engines not to follow any links on a page.
<meta name="robots" content="nofollow">
But there may be instances, such as this case for me, where a webpage
designer wants only some links on a page not to be followed to their
destination by search engines.
The attribute can also be added to individual links if you don't want
to vouch for the content of the page to which the link points. E.g., adding
it to links placed in comments by those commenting on a page will allow
visitors to go to the linked page, but search engines that adhere to the
nofollow parameter won't use the link to increase their ranking of the page
to which the link points, which may discourage some comment spammers.
The rel="nofollow" option for links was developed as a
way to combat link
spam. In January 2005, Google, Yahoo! and MSN announced that they would
support use of the "nofollow" tag as a way to deter link spam. Microsoft's
MSN Spaces and
Google's Blogger
blogging services joined the effort to utilize the tag to discourage
link spamming At that time a number of blog software providers, including
Six Apart,
WordPress,
Blosxom, and blojsom, also
joined the effort by supporting use of the tag.
References:
-
Use rel="nofollow" for specific links
Google Webmaster Tools
-
Wipedia ponders joining search engines in fight against spam
By: Michael Snow
Date: January 24, 2005
[/network/web/blogging/blosxom]
permanent link
Tue, Mar 11, 2014 10:31 pm
Determining resolution from the command line on OS X
To determine the video resolution from a command line, such as a
Terminal shell prompt, on an OS X system, you can use the command
system_profiler SPDisplaysDataType.
$ system_profiler SPDisplaysDataType
Graphics/Displays:
NVIDIA GeForce 9400M:
Chipset Model: NVIDIA GeForce 9400M
Type: GPU
Bus: PCI
VRAM (Total): 256 MB
Vendor: NVIDIA (0x10de)
Device ID: 0x0863
Revision ID: 0x00b1
ROM Revision: 3448
gMux Version: 1.8.8
Displays:
Color LCD:
Display Type: LCD
Resolution: 1440 x 900
Pixel Depth: 32-Bit Color (ARGB8888)
Main Display: Yes
Mirror: Off
Online: Yes
Built-In: Yes
NVIDIA GeForce 9600M GT:
Chipset Model: NVIDIA GeForce 9600M GT
Type: GPU
Bus: PCIe
PCIe Lane Width: x16
VRAM (Total): 512 MB
Vendor: NVIDIA (0x10de)
Device ID: 0x0647
Revision ID: 0x00a1
ROM Revision: 3448
gMux Version: 1.8.8In the example above, the video resolution for the MacBook Pro
on which I ran the command is 1440 x 900. The
Screen Information page
at BrowserSpy.dk will also report
a system's screen resolution, if you visit that page using a browser on
the system. In this case it reports a width of 1440 and a height of 900 pixels
for the MacBook Pro.
[/os/os-x]
permanent link
Mon, Mar 10, 2014 10:29 pm
Debug output for calendar plugin for Blosxom
I've been using
Blosxom for
this blog and version 0+6i of the
calendar
plugin for Blosxom written by Todd Larason whose website seems
to no longer be extant, though it is available through the
Internet Archive's
WayBack Machine
here.
The last time the Internet Archive archived the site was on March
25, 2010. The plugin can be downloaded from this site at
Calendar Plugin for Blosxom.
The plugin has been contributing a lot of entries in the
site's error log that appear to be related to normal behavior for the
plugin. I've been ignoring them, since the plugin has been working fine
and the entries seem to be more informatonal in nature than reflective
of a problem with the plugin. E.g., I see a lot of entries similar to
the following:
[Sun Mar 09 23:59:19 2014] [error] [client 10.0.90.23] calendar debug 1: start() called, enabled
[Sun Mar 09 23:59:20 2014] [error] [client 10.0.90.23] calendar debug 1: filter() called
[Sun Mar 09 23:59:20 2014] [error] [client 10.0.90.23] calendar debug 1: Using cached state
[Sun Mar 09 23:59:20 2014] [error] [client 10.0.90.23] calendar debug 1: head() called
[Sun Mar 09 23:59:20 2014] [error] [client 10.0.90.23] calendar debug 1: head() done, length($month_calendar, $year_calendar, $calendar) = 3947 1212 5229
I finally decided I should stop the production of those entries, though,
so I could more readily see log entries that are significant. So I looked
at the Perl code for the plugin. On line 30, I see the following:
$debug_level = 1 unless defined $debug_level;
The debug surboutine is on lines 49 through 56 and is as follows:
sub debug {
my ($level, @msg) = @_;
if ($debug_level >= $level) {
print STDERR "$package debug $level: @msg\n";
}
1;
}
On line 517, I see the following comment.
C<$debug_level> can be set to a value between 0 and 5; 0 will output
no debug information, while 5 will be very verbose. The default is 1,
and should be changed after you've verified the plugin is working
correctly.
Since the plugin has been working for a long time and I don't need to
see the debugging information, I set the value for debug_level
on line 30 to zero instead of one.
$debug_level = 0 unless defined $debug_level;
That has stopped the insertion of the calendar plugin entries in the
Apache error log file with no effect on the calendar's functionality.
[/network/web/blogging/blosxom]
permanent link
Sun, Mar 09, 2014 4:04 pm
Redirecting a URL on an Apache Web Server
If you are using an Apache webserver and you need to redirect visitors to
a webpage to another webpage, instead, one method of doing so is to use a
server-side redirect, which can be accomplished by inserting a redirect in
an .htaccess file, to the new page.
[ More Info ]
[/network/web/server/apache]
permanent link
Sat, Mar 08, 2014 10:14 pm
Turning off command echo in MUSHclient but retaining command history
For
MUSHclient, if you don't
want commands echoed back to you when you type them, but
want them stored in the command history, leave command echo turned on.
You can check that it is turned on after you connect to the
MUSH by
clicking on
Display. You should not see a check mark next to
No Command Echo. If one is there click on
No Command Echo
to uncheck it.
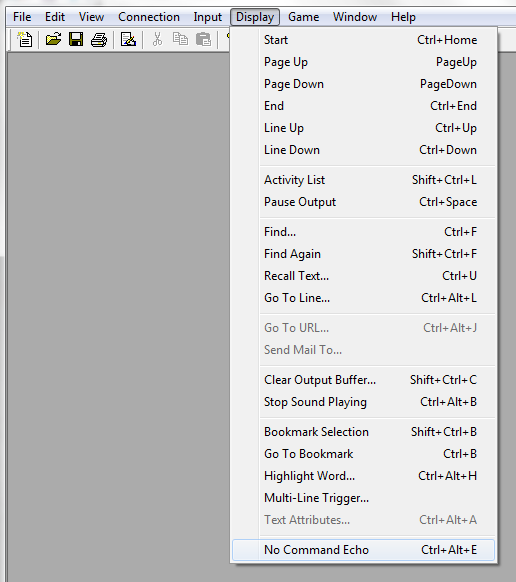
You then need to take the following steps:
- Click on Game.
- Select Configuration.
- Select All Configuration.
- Uncheck the checkbox next to "Echo My Input
In" under Output Window.
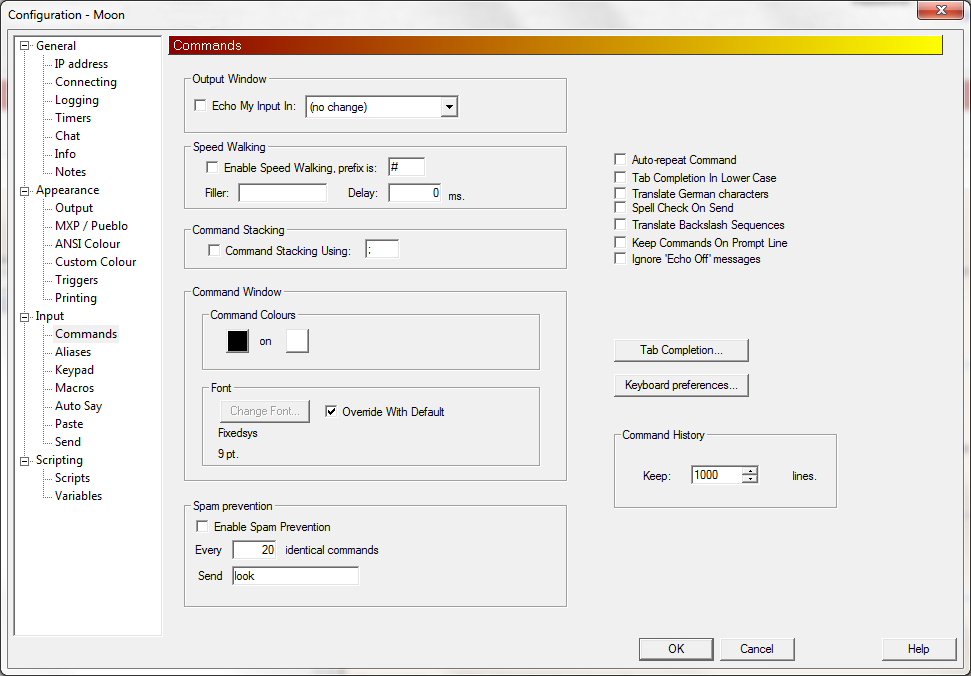
- Make sure the value for the number of lines to keep
under Command History is not set to 0, but is set to the number
of commands you want to keep in the history; the default value is
1,000 lines..
- Click on OK.
You should then be able to see commands you type in the command
history window that you can open with Ctrl-H. If you want
to save the setting so that you don't have to change it the next
time you connect to the MUSH, click on File and select
Save World Details.
Instructions appy to version 4.84.
[/gaming/mushclient]
permanent link
Fri, Mar 07, 2014 10:20 pm
Using mdfind to locate files
On a Mac OS X system, you can use the
mdfind command to locate
files on the system from a command line interface, e.g., from a shell prompt
that you may obtain by running the
Terminal program, which is located
in
Applications/Utilities. You can specify the name of the
file using the
-name option.
$ mdfind -name Waterfalls.mp3
/Users/jdoe/Music/iTunes/iTunes Media/Music/Bob Weir/Relax With Soothing Waterfalls/01 Soothing Waterfalls.mp3
/Users/jdoe/Downloads/Waterfalls.mp3
You can specify just part of the file name and the search is not case
specific, i.e., "waterfall" and "Waterfall" are deemed identical.
$ mdfind -name waterfall
/Users/jdoe/Downloads/Waterfalls.mp3
/Users/jdoe/Music/iTunes/iTunes Media/Music/Bob Weir/Relax With Soothing Waterfalls/01 Soothing Waterfalls.mp3
/Users/jdoe/Music/iTunes/iTunes Media/Music/Bob Weir/Relax With Soothing Waterfalls
/Library/Desktop Pictures/Eagle & Waterfall.jpg
As shown in the above example, directories whose names contain the
string
on which you are performing the search, i.e., "waterfall" in the above case,
will also be returned.
If you just want a count of files and directories containing a
particular string, such as "waterfall" in the name, you can add the
-count parameter.
$ mdfind -count -name waterfall
4
If you want to limit the search to a particular directory you can use
the -onlyin parameter.
$ mdfind -name waterfall -onlyin "/Library/Desktop Pictures/"
/Library/Desktop Pictures/Eagle & Waterfall.jpg
[/os/os-x]
permanent link
Thu, Mar 06, 2014 10:43 pm
Using sw_vers to obtain OS X version
On a MAC OS X system, you can obtain information on the operating system
version from a command line interface, e.g. from a terminal session, which
you can get by running the
Terminal program in
Applications/Utilities, by using the
sw_vers command.
$ sw_vers
ProductName: Mac OS X
ProductVersion: 10.8.3
BuildVersion: 12D78
If you are only interested in the ProductName, ProductVersion
, or BuildVersion, you can specify arguments that will
restrict the output to just that informaton.
$ sw_vers -productName
Mac OS X
$ sw_vers -productVersion
10.8.3
$ sw_vers -buildVersion
12D78
You can also get the OS X version number using the
system_profiler command.
$ system_profiler SPSoftwareDataType | grep "System Version"
System Version: OS X 10.8.3 (12D78)
[/os/os-x]
permanent link
Wed, Mar 05, 2014 10:38 pm
Audio File Play - afplay
On Mac OS X systems you can play an audio file, such as an MP3 file, from a
command-line
interface, i.e., a shell prompt, which you can get by running the
Terminal program found in
/Applications/Utilities,
by using the audio file play command,
afplay. E.g.:
afplay Waterfalls.mp3
You can terminate the playing of the audio file using Ctrl-C.
You can specify that the audio file only be played for a specific number of
seconds using the -t or --time argument. E.g., the
following command would play the specified MP3 file for 10 seconds and then
terminate afplay:
afplay --time 10 Waterfalls.mp3
For help on the command use afplay -h.
$ afplay -h
Usage:
afplay [option...] audio_file
Options: (may appear before or after arguments)
{-v | --volume} VOLUME
set the volume for playback of the file
{-h | --help}
print help
{ --leaks}
run leaks analysis
{-t | --time} TIME
play for TIME seconds
{-r | --rate} RATE
play at playback rate
{-q | --rQuality} QUALITY
set the quality used for rate-scaled playback (default is 0 - low quality, 1 - high quality)
{-d | --debug}
debug print output
[/os/os-x]
permanent link
Tue, Mar 04, 2014 11:35 pm
Obtaining info on an audio file with afinfo
You can obtain information on an audio file, such as an
MP3 file
on a Mac OS X system from the command line using the
afinfo
command.
$ afinfo Waterfalls.mp3
File: Waterfalls.mp3
File type ID: MPG3
Num Tracks: 1
----
Data format: 2 ch, 44100 Hz, '.mp3' (0x00000000) 0 bits/channel, 0 bytes/packet, 1152 frames/packet, 0 bytes/frame
no channel layout.
estimated duration: 3642.644850 sec
audio bytes: 72852897
audio packets: 139445
bit rate: 160000 bits per second
packet size upper bound: 1052
maximum packet size: 523
audio data file offset: 2228
optimized
audio 160637484 valid frames + 528 priming + 2628 remainder = 160640640
----The command will tell you the
bit
rate and the estimated duration if you choose to play the file. In the
example above, the MP3
bitrate is 160 kbit/s, which is a mid-range bitrate quality for an MP3 file.
Common bitrates for MP3 files are as follows:
- 32 kbit/s – generally acceptable only for speech
- 96 kbit/s – generally used for speech or low-quality streaming
- 128 or 160 kbit/s – mid-range bitrate quality
- 192 kbit/s – a commonly used high-quality bitrate
- 320 kbit/s – highest level supported by MP3 standard
The estimated playing time of the MP3 file in the example above is
3642.644850 sec. You can convert that to minutes from the command line by
passing a command to python to convert seconds to minutes.
$ python -c "print 3642.644850 / 60"
60.7107475
If you wanted to convert that to hours, you could just divide by 60
minutes per hour by adding another "/ 60" at the end of the command.
$ python -c "print 3642.644850 / 60 / 60"
1.01184579167
If you just want to know the bit rate, you can pipe the output of
afinfo through grep and awk:
$ afinfo Waterfalls.mp3 | grep "bit rate" | awk '{print $3}'
160000If you just want to know the duration in seconds, you can use the
following commands:
$ afinfo Waterfalls.mp3 | grep "estimated duration" | awk '{print $3}'
3642.644850If you want the value in minutes you can also use awk to print that value
instead.
$ afinfo Waterfalls.mp3 | grep "estimated duration" | awk '{print $3 / 60 , "minutes"}'
60.7107 minutes
[/os/os-x]
permanent link
Mon, Mar 03, 2014 7:31 pm
YandexBot Web Crawler
When checking my website logs to see if there were any entries indicating it
had been "crawled", i.e., indexed, by
DuckDuckGo, I found that there were no log entries for any of the
IP addresses used by the
DuckDuckGoBot for
indexing webpages
for 2013 nor for 2014. I found at DuckDuckGo's
Sources webpage that
though the search engine has its own
web crawler, it relies
heavily on indexes produced by the web crawlers for other search engines
stating:
DuckDuckGo gets its results from
over one hundred sources, including DuckDuckBot (our own
crawler), crowd-sourced
sites (like Wikipedia, which are stored in our own index),
Yahoo! (through
BOSS), Yandex,
WolframAlpha, and Bing.
DuckDuckGo's page states they apply their own algorithm to rank
results obtained from other search engines upon which they rely for
data.
One of the search engines mentioned was
Yandex.
The Yandex search engine,
Yandex Search, can be accessed at
www.yandex.com. According to the Wikipedia articles for
Yandex
and Yandex Search
the company operates the largest search engine in Russia with about 60%
market share in Russia with its search engine generating 64% of all Russian web
search traffic in 2010. The article on the company also states:
Yandex ranked as the 4th largest search engine worldwide, based on
information from
Comscore.com, with more than 150 million searches per day as of April 2012,
and more than 50.5 million visitors (all company's services) daily as
of February 2013.
The article also indicates Yandex is heavily utilized in Ukraine and Kazakhstan,
providing nearly a 1/3 of all search results in those countries and 43% of all
search results in Belarus.
When I searched the logs for this year for this website, I found quite a
few entries indicating the site had been indexed by the Yandex web crawler.
I.e., there were many entries containing the following:
"Mozilla/5.0 (compatible; YandexBot/3.0; +http://yandex.com/bots)"
In the homepage for this site, I include
PHP code to notify me whenever Google's Googlebot indexes the site,
so I updated that code to include a check that will lead to an email alert
being sent to me whenever the YandexBot indicates the site, also.
<?php
$email = "me@example.com";
if( eregi("googlebot", $_SERVER['HTTP_USER_AGENT']) )
{
mail($email, "Googlebot Alert",
"Google just indexed your following page: " .
$_SERVER['REQUEST_URI']);
}
if( eregi("YandexBot", $_SERVER['HTTP_USER_AGENT']) )
{
mail($email, "Yandex Alert",
"Yandex just indexed your following page: " .
$_SERVER['REQUEST_URI']);
}
?>
[/network/web/search]
permanent link
Mon, Mar 03, 2014 5:17 pm
Removing a site from search results
If you don't wish to have any results returned for a particular site when
you are performing a search using
Google,
Bing,
Yahoo, or
DuckDuckGo, you can include the option
-site
on the search line. E.g., if I wished to search for "accessing
deleted wikipedia pages", but didn't want any results returned from
Wikipedia.org, I could use the following
search terms:
accessing deleted wikipedia pages -site:wikipedia.org
If you wish to include only results for a particular site, then you
would put the site's name after the word site, e.g., if
I wished to search just moonpoint.com, I could use the following:
accessing deleted wikipedia pages site:moonpoint.com
If you restrict searches using the site
option, if you use a domain name such as moonpoint.com,
results will also be returned for any domain names that include
the specified domain name at the end of the domain name, e.g.,
in this case anything on www.moonpoint.com or
support.moonpoint.com would also be returned.
The same is true when using the -site option, i.e.,
no results would be returned for en.wikipedia.org
or www.wikipedia.org in the first example.
[/network/web/search]
permanent link
Sun, Mar 02, 2014 10:40 pm
F-Secure Rescue CD 3.16
F-Secure provides a free Rescue CD which allows you to boot a PC from a CD and
scan it for malware using F-Secure's antivirus software. The F-Secure Rescue
CD will attempt to disinfect any infected files and will rename any it can't
disinfect by putting a .virus extension at the end of the file name. By doing
that, when you reboot the system into Microsoft Windows, the infected file will
not be loaded into memory.
[ More Info ]
[/security/antivirus/f-secure]
permanent link
Sun, Mar 02, 2014 10:36 pm
Installing the SSH Server Service on Knoppix
You can determine if a
Knoppix
Linux system is listening for
SSH connections on the
standard SSH
TCP
port of 22 by issuing the command
netstat -a | grep ssh. If you
are returned to the shell prompt with no results displayed, then the
system isn't listening for SSH connections on port 22.
root@Microknoppix:/# netstat -a | grep ssh
root@Microknoppix:/#
You can also check to see if it is running by using the command
service --status-all. If there is a plus sign next to
ssh, it is running. If, instead, there is a minus sign, it is not
running.
root@Microknoppix:/# service --status-all
[ - ] acpid
[ - ] bootlogd
[ - ] bootlogs
[ ? ] bootmisc.sh
[ ? ] checkfs.sh
[ - ] checkroot.sh
[ ? ] console-screen.sh
[ ? ] console-setup
[ ? ] cpufrequtils
[ ? ] cron
[ ? ] cryptdisks
[ ? ] cryptdisks-early
[ + ] dbus
[ + ] ebtables
[ ? ] etc-setserial
[ - ] fsaua
[ ? ] fsrcdtest
[ - ] fsupdate
[ ? ] fsusbstorage
[ ? ] gpm
[ ? ] hdparm
[ - ] hostname.sh
[ ? ] hwclock.sh
[ ? ] hwclockfirst.sh
[ ? ] ifupdown
[ ? ] ifupdown-clean
[ ? ] kexec
[ ? ] kexec-load
[ ? ] keyboard-setup
[ ? ] keymap.sh
[ ? ] killprocs
[ ? ] klogd
[ ? ] knoppix-autoconfig
[ ? ] knoppix-halt
[ ? ] knoppix-reboot
[ ? ] knoppix-startx
[ ? ] loadcpufreq
[ ? ] lvm2
[ ? ] mdadm
[ ? ] mdadm-raid
[ ? ] module-init-tools
[ ? ] mountall-bootclean.sh
[ ? ] mountall.sh
[ ? ] mountdevsubfs.sh
[ ? ] mountkernfs.sh
[ ? ] mountnfs-bootclean.sh
[ ? ] mountnfs.sh
[ ? ] mountoverflowtmp
[ ? ] mtab.sh
[ + ] network-manager
[ ? ] networking
[ - ] nfs-common
[ - ] nfs-kernel-server
[ + ] open-iscsi
[ - ] portmap
[ ? ] pppstatus
[ ? ] procps
[ ? ] rc.local
[ - ] rmnologin
[ - ] rsync
[ ? ] screen-cleanup
[ ? ] sendsigs
[ ? ] setserial
[ - ] smartmontools
[ - ] ssh
[ - ] stop-bootlogd
[ - ] stop-bootlogd-single
[ ? ] sudo
[ ? ] sysklogd
[ ? ] udev
[ ? ] udev-mtab
[ ? ] umountfs
[ ? ] umountiscsi.sh
[ ? ] umountnfs.sh
[ ? ] umountroot
[ - ] urandom
On a Microknoppix system, such as may be present on a Rescue CD or
other live CD or
DVD, the SSH server software may not even be present on the CD or DVD. You
can use the apt-cache search command followed by a
regular
expression, in this case ssh, to determine if
the package is present on the system.
root@Microknoppix:/# apt-cache search ssh
libssl0.9.8 - SSL shared libraries
sshstart-knoppix - Starts SSH and sets a password for the knoppix user
openssh-client - secure shell (SSH) client, for secure access to remote machines
In the case above, I can see that only an SSH client is present. If I run the
sshstart-knoppix command, I will be prompted to set a password for the
knoppix account on the system, but, since the SSH server package is not present,
the command won't actually start an sshd service.
If the SSH server service is not running and the SSH server package
is not installed, first you need to install
the SSH server software. To do so you may need to add an appropriate
package repository, such as http://us.debian.org/debian to
the file /etc/apt/sources.list. E.g., you will need to do
so when using the
F-Secure 3.16
Rescue CD.
If you attempt to install the openssh-server package and
see the results below, then you need to add an appropriate repository
to /etc/apt/sources.list so the system can find the package
and download it.
root@Microknoppix:/# apt-get install openssh-server
Reading package lists... Done
Building dependency tree...
Reading state information... Done
Package openssh-server is not available, but is referred to by another package.
This may mean that the package is missiong, has been obsoleted, or
is only available from another source
E: Package 'openssh-server' has no installation candiate
root@Microknoppix:/#
You can add the http://us.debian.org/debian repository
to the end of the file by using the cat command. Type
cat >> /etc/apt/sources.list (make sure you use two
greater than signs so as to append to the file rather than overwrite it)
then type deb http://http.us.debian.org/debian stable main contrib
non-free and then hit Enter. Then hit the Ctrl
and D keys simultaneously, i.e., Ctrl-D. Next issue the
command apt-get update. When that command has completed,
issue the command apt-get install openssh-server. When
informed of the amount of additional disk space that will be needed and
them prompted as to whether you wish to continue, type "Y". When
prompted "Install these packages without verification [y/N]?",
enter "y".
When the command completes you can then issue the command
netstat -a | grep ssh to verify that the system
is listening on the SSH port, which is normally TCP port 22.
root@Microknoppix:/# netstat -a | grep ssh
tcp 0 0 *:ssh *:* LISTEN
tcp6 0 0 [::]:ssh [::]:* LISTEN
If you issued the command apt-cache search openssh-server
at this point, you would see the following:
root@Microknoppix:/# apt-cache search openssh-server
openssh-server - secure shell (SSH) server, for secure access from remote machines
Use the passwd command to set the password for
the knoppix account, which you can use for remote logins.
root@Microknoppix:/tmp# passwd knoppix
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Hit Return to continue.
Once the SSH server service is running, you should be able to
connect to the system remotely with an SSH client on another system.
To determine what IP address you should use for the connection, you
can issue the command ifconfig. You should see
an inet addr line that will provide the system's
current IP address. It will typically be in the information
provided for the eth0 network interface. The
l0 interface is the
local loopback interface, which will have an IP address
of 127.0.0.1. You can use that address to verify
that the SSH connectivity is working from the local system,
but not for a remote login.
root@Microknoppix:/# ifconfig
eth0 Link encap:Ethernet HWaddr 00:18:f3:a6:01:8a
inet addr:192.168.0.40 Bcast:192.168.0.255 Mask:255.255.255.0
inet6 addr: fe80::218:f3ff:fea6:18a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:334286 errors:0 dropped:0 overruns:0 frame:0
TX packets:262393 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:289663552 (276.2 MiB) TX bytes:183570787 (175.0 MiB)
Interrupt:23 Base address:0xc000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:24 errors:0 dropped:0 overruns:0 frame:0
TX packets:24 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2331 (2.2 KiB) TX bytes:2331 (2.2 KiB)To login remotely via SSH, use knoppix for the login
account and provide the password you entered above for that account
when prompted for the password. Once you have logged in under the
knoppix account, you can obtain a Bash shell prompt
for the root account using the command sudo bash.
knoppix@Microknoppix:~$ sudo bash
root@Microknoppix:/home/knoppix#
If you then need to stop, start, or restart the service, you can do
so using /etc/init.d/ssh followed by the appropriate parameter.
root@Microknoppix:/# /etc/init.d/ssh
[info] Usage: /etc/init.d/ssh {start|stop|reload|force-reload|restart|try-restar
t|status}.The configuration file for the SSHD service is
/etc/ssh/ssh_config. You can change values by removing the
comment character, #, from the beginning of a line and chaning the
default value on the line, then stopping and restaring the service. Note:
stopping the sshd service won't disconnect an existing SSH connection, so
you can remotely restart the service with
/etc/init.d/ssh restart without being disconnected.
[/os/unix/linux/knoppix]
permanent link
Sat, Mar 01, 2014 11:28 am
Using multiple conditions with find
The
find command on Unix/Linux and Apple OS X systems allows
you to specify multiple criteria to be used for a search. For instance,
suppose I have a directory named
man and a file named
manual.txt. If I wanted to find any files or directories
containing "man" within their names, I could issue the command below. If
the directory in which the find command was executed contained a subdirectory
named
man and a text file named
manual.txt, I
would see the results shown below:
$ find . -name \*man\*
./man
./manual.txt
Note: the backslashes before the asterisks are
"escape characters",
i.e., they tell the shell not to interpret the asterisk before the find
command sees it - see
What is the difference between \*.xml and *.xml in find command in Linux/mac.
Another alternative is to enclose the *man* within double quotes.
$ find . -name "*man*"
./man
./manual.txt
But, if I only want to find items that have "man" in the name which are
directories, I could use the following to specify I only want to see items
where the file is of type directory ("d" represents directory and "f" represents
a regular file):
$ find . -name \*man\* -type d
./man
By default, the find command will use a
logical and for the two
conditions, i.e., both conditions must be met. I could explicitly state
I want to "and" the two conditions with a -a, but it isn't
necessary to do so in this case.
$ find . -name \*man\* -a -type d
./man
But what if I want to to specify a
logical "or", i.e.
that I want results returned where either of two conditions are met? E.g.,
suppose I want to find all files where the filename contains man
or guide. Then I need to use a -o parameter.
$ find . -name "*man*" -o -name "*guide*"
./man
./manual.txt
./guide.txt
Suppose I only wanted to see only files with man or guide
in the filename that are "regular" files and not any
directories. I could use -type f to specify that I only want
to see regular files.
$ find . -name "*man*" -o -name "*guide*" -type f
./man
./manual.txt
./guide.txt
As you can see, the directory man is still returned. To get
the results I want, i.e., to not have the directory man appear
in the results, I need to enclose the "or" condtions within parentheses.
$ find . \( -name "*man*" -o -name "*guide*" \) -type f
./manual.txt
./guide.txt
Note: you also need to
"escape" the meaning
of ( and ) by preceding them with the backslash
escape character.
Otherwise, you will get an "unexpected token" error message.
$ find . (-name "*man*" -o -name "*guide*") -type f
-bash: syntax error near unexpected token `('And you need to put a space after the left parenthesis and before the
right parenthesis or you will receive an "invalid predicate" error message.
$ find . \(-name "*man*" -o -name "*guide*"\) -type f
find: invalid predicate `(-name'
As another example, suppose I want to find all HTML or PHP files that
contain the word "Geek" within them when the HTML files have a .html
extension and the PHP files have a .php extension on the file names. Then
I need to use a -o between the conditions to specify that
I want to see results if the file has an extension of .html or .php.
$ find . \( -name "*.php" -o -name "*.html" \) -exec grep -i "Geeks" {} /dev/null \;
./temp.php:1Geeks
./temp.html:2GeeksWhenever a file has a name that ends in .html or .php, the file
contents are sent to the grep command for examination. To specify
that I want to use a logical or, the -o is placed between
-name "*.php" and -name "*.html". Again, I also
have to include the two conditions within parentheses to ensure that
the "or" condition is checked before sending the results to grep for
examination of the contents of the files. If the parentheses aren't used,
I would only see one of the files returned.
$ find . -name "*.php" -o -name "*.html" -exec grep -i "Geeks" {} /dev/null \;
./temp.html:2Geeks
[/os/unix/commands]
permanent link
Fri, Feb 28, 2014 10:41 pm
Using awk to sum numbers in a file
The awk command found on Linux/Unix and Mac OS X systems can be used to
sum numbers in a file. E.g., suppose the file
numbers.txt
contains the following numbers:
10
20
30
40
50
1
2
3
4
5
The contents of the file can be piped into the awk command with
the cat command and then summed by awk.
$ cat numbers.txt | awk '{sum+=$1} END {print sum}'
165If the numbers are not in the first column in the file, but were in the
second column instead, you can adjust $1 to be the relevant
column instead. E.g, if the file contents looked like the following with
the numbers in the second column, then you would use $2 instead.
Dave 10
Bill 20
Joe 30
Mary 40
Maria 50
Howard 1
Sam 2
Lisa 3
Karen 4
Nina 5
$ cat numbers.txt | awk '{sum+=$2} END {print sum}'
165If you know the numbers always occur in specific colum positions in the file,
e.g., in positions 10 to 15, you could also use the cut
command instead of the cat command. E.g., if you file contained:
Dave 10
Bill 20
Joe 30
Mary 40
Maria 50
Howard 1
Sam 2
Lisa 3
Karen 4
Nina 5
$ cut -c10-11 numbers.txt | awk '{sum+=$1} END {print sum}'
165
[/os/unix/commands]
permanent link
Fri, Feb 28, 2014 10:09 pm
Managing Wi-Fi from the terminal command line under OS X
To manage
Wi-Fi connections from a shell prompt on a Mac OS X system you can
obtain a command line interface by running the
Terminal program located
in Applications/Utilities. From that command line interface, you can determine
whether a WiFi interface is present on the system using the command
networksetup -listallnetworkservices. You should see "Wi-Fi"
in the list of services that appears when you issue the command.
$ networksetup -listallnetworkservices
An asterisk (*) denotes that a network service is disabled.
Bluetooth DUN
Ethernet
FireWire
Wi-Fi
To determine the hardware interface supporting Wi-Fi connections you
can use the command networksetup -listallhardwareports.
$ networksetup -listallhardwareports
Hardware Port: Bluetooth DUN
Device: Bluetooth-Modem
Ethernet Address: N/A
Hardware Port: Ethernet
Device: en0
Ethernet Address: d4:9a:20:0d:e6:ec
Hardware Port: FireWire
Device: fw0
Ethernet Address: d4:9a:20:ff:fe:0d:e6:ec
Hardware Port: Wi-Fi
Device: en1
Ethernet Address: f8:1e:df:d9:2b:66
VLAN Configurations
===================
In the case above, the Wi-Fi interface is en1.
To get information on the status of the system's Wi-Fi connection, you
can use the command networksetup -getinfo Wi-Fi.
$ networksetup -getinfo Wi-Fi
DHCP Configuration
IP address: 192.168.0.5
Subnet mask: 255.255.255.0
Router: 192.168.0.1
Client ID:
IPv6: Automatic
IPv6 IP address: none
IPv6 Router: none
Wi-Fi ID: f8:1e:df:d9:2b:66
To find if the system is currently connected to a wireless network and the
network name for the current wireless connection, you can use
networksetup -getairportnetwork <device name> where
device name is the network interface on the system that supports
WiFi connections. E.g.:
$ networksetup -getairportnetwork en1
Current Wi-Fi Network: Copernicus
If you stipulate a network interface that is not a WiFi interface, you
will get an error message indicating the interface is not a Wi-Fi interface
as shown below:
$ networksetup -getairportnetwork en0
en0 is not a Wi-Fi interface.
** Error: Error obtaining wireless information.
If you wish to to turn the Wi-Fi connection on or off from a shell
prompt, you can use the networksetup -setairportnetwork
command.
networksetup -setairportnetwork <device name> <network> [password]
$ networksetup -setairportpower en1 off
$ networksetup -getairportnetwork en1
You are not associated with an AirPort network.
Wi-Fi power is currently off.
$ networksetup -setairportpower en1 on
$ networksetup -getairportnetwork en1
Current Wi-Fi Network: Copernicus
[/os/os-x]
permanent link
Thu, Feb 27, 2014 10:13 pm
Determining available WiFi networks from OS X shell prompt
On a Mac OS X system, such as a MacBook Pro laptop, you can detemine the
available WiFi networks from a shell prompt, which you can get by running
the
Terminal program located in
Applications/Utilities,
by using the command below:
/System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport scan
For example:
$ /System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport scan
SSID BSSID RSSI CHANNEL HT CC SECURITY (auth/unicast/group)
SC8QR f8:e4:fb:ea:29:5d -86 11 Y -- WPA2(PSK/AES,TKIP/TKIP)
08FX02038916 00:18:3a:8a:01:c5 -80 6 N -- WEP
Norman Netgear 84:1b:5e:2d:c9:16 -79 6 Y -- WPA2(PSK/AES/AES)
558935 0c:54:a5:48:19:e5 -16 1 Y -- WPA(PSK/AES,TKIP/TKIP) WPA2(PSK/AES,TKIP/TKIP)
Hickox 0c:d5:02:c5:e8:8e -80 11 N -- WEP
Haze 94:44:52:5a:54:54 -33 11 Y -- WPA(PSK/AES/AES) WPA2(PSK/AES/AES)
David's Net ec:1a:59:8d:dd:61 -80 11 Y -- WPA2(PSK/AES/AES)
The
SSID is the "Service Set Identification", which is a 1 to 32 byte string
that represents the "network name". The SSID allows you to identify a network
to which you may wish to connect. Sometimes a person setting up a wireless
router may choose to not have the SSID broadcast. In that case you wouldn't
see the SSID in the list even though the network is available for connections
if you know the SSID.
The
BSSID is the "Basic Service Set Identification". Each Basic Service Set is
identified by a BSSID. For a BSS operating in infrastructure mode, the BSSID
is the media access control
(MAC) address of the
wireless access
point (WAP), which is generated by combining the 24-bit
Organizationally Unique Identifier, which identifies the manufacturer,
and the manufacturer's assigned 24-bit identifier for the radio
chipset in the WAP. The BSSID is the formal name of the BSS and is
always associated with only one BSS. The SSID is the informal human
name of the BSS which is more easily remembered by humans.
You can determine the manufacturer from the BSSID by searching the
IEE-SA - Registration Authority MA-L Public Listing. Take the first six
digits of the BSSID and replace the colons with dashes and then put the
result, which will be in the form of xx-xx-xx in the "Search for" field. E.g.,
in the case of the wireless network above identified as "David's Net", the
BSSID is ec:1a:59:8d:dd:61, so you would search using
ec-1a-59, which would show the wireless device was
manufacturered by Belkin International Inc., a company that make wireless
routers for the home market. For the network identified as "Norman Netgear",
searching on 84-1b-5e shows the manufacturer is, indeed, Netgear.
If you just want the names of the available networks, i.e., the SSIDs, you
can use the same command and then pipe its output to the cut command. Since
the SSID will be the first 32 characters on each line, you will need to cut
out the first 32 characters from each line.
$ /System/Library/PrivateFrameworks/Apple80211.framework/Versions/A/Resources/airport scan | cut -c1-32
SSID
SC8QR
08FX02038916
Norman Netgear
558935
Hickox
Haze
David's Net
[/os/os-x]
permanent link
Wed, Feb 26, 2014 5:50 pm
MSYS
If you would like to be able to use Unix/Linux utilities such as
awk, cut, grep, less, sed, sort, tail, wc, etc. on a Microsoft Windows
system,
MSYS provides these and
many other
GNU utilities
for Microsoft Windows systems.
[ More Info ]
[/os/windows/software/utilities]
permanent link
Sun, Feb 23, 2014 1:37 pm
Accessing Deleted Wikipedia Pages
Wikipedia pages can be edited by anyone; they can also be deleted
entirely by Wikipedia administrators for a variety of reasons. Within
the Wikipedia community there are differing views regarding the
retention and deletion of articles, e.g., see the Wikipedia article
Deletionism and inclusionism in Wikipedia. If you read an article
and want to ensure you have access to the information in the future, the
best course is probably to use Wikipedia's own "print/export" feature or
to save the content of the article elsewhere by using a service such as
Evernote, which provides notetaking
and webpage archiving services,
Diigo,
which provides a social bookmarking service with the capability to store
a copy of webpages you have visited, i.e., to "cache" them so that you
can view the webpage again as it was when it was cached whether it has
been changed or deleted in the interim, or similar services. But, if
you haven't archived an article and find a Wikipedia page was deleted and
so is inaccessible to you, there are still some options available to you.
If the article was deleted some time between February and September 2008, you may be able to find it on
Deletionpedia at
deletionpedia.dbatley.com
Deletionpedia is an archive that contains 62,224 pages which were deleted from
the English-language Wikipedia between February and September 2008.
If you know the title of the article that was deleted, you can browse
"Pages
deleted after more than 1000 days on Wikipedia" or
"
Pages edited more than 200 times" by their alphabetical listings. If you
know the date the article was deleted which, if you have the Wikipedia URL for the article, can be found
by visiting the URL for the article on Wikipedia, you can find it by
searching Deletionpedia by
Pages by deletion date.
Deletionpdedia's own search feature is disabled and the
site suggests you use Google to search Deletionpedia. However,
I've found that approach is likely to miss articles stored
on Deletionpedia. E.g., Deletionpedia contains the article
Elvis sightings (deleted 03 Jul 2008 at 10:12),
yet if you search the site using Google with Elvis
sightings site:deletionpedia.dbatley.com, no results
are returned. Incidentally, Wikipedia does now contain an Elvis sightings
article.
Interestingly, though Wikipedia now contains a
Deletionpedia article, that article was itself
once deleted from Wikipedia.
Another site Fixed Reference: Snapshots
of Wikipedia provides access to articles archived in April and July of 2004.
Because Fixed Reference and Deletionpedia only provide access to articles from
two years, 2004 for Fixed Reference and 2008 for Deletionpedia, their usefulness
for accessing deleted articles is very limited.
Another alternative is to search the
Internet
Archive at archive.org. The Internet
Archive is a non-profit digital library with the stated mission of
"universal access to all knowledge." It also archives pages found on
the World Wide Web
(WWW). The archived pages, which are created for a website when the Internet
Arhive periodically scans the site, are accessible through its
Wayback Machine.
The name is a reference to the time machine used by Mr. Peabody, a talking dog,
and his human companion, Sherman, in the cartoon series
The Rocky and Bullwinkle Show to visit famous
events in history. You can choose to "Browse History" to search for an
archived copy of the page deleted from Wikipedia, if you know its URL.
If the page was archived by the Internet Archive multiple times over a period
of time, which could span years, you can view the page as it was on the
particular days it was archived.
Another place you can check for deleted Wikipedia pages or pages that
have disappeared from any website is
Archive.is, which aims to be "your personal Wayback Machine!" The site
can be freely used by anyone to take a "snapshot" of a webpage that will
always be online even if the original page disappears. So, if someone else
has archived a particular webpage for which you are searching, you may find
it at Archive.is. You can also use the
site to archive pages you may want to access later that could disappear from
the original site or to make the pages available should the original site
disappear from the web.
[/reference]
permanent link
Sat, Feb 08, 2014 10:31 pm
ToDoList
I needed software that I could run on a system running Microsoft Windows
8 to help me manage projects and tasks. I had been using an online service
for awhile, but was looking for software I could run on the system that
would give me some additional capabilities, but I didn't want to spend
several hundred dollars on Microsoft Project, which, though it offers all
the features I might need, is overkill for my current needs. I found
ToDoList, which
is free to be an easy program to quickly start managing my projects and tasks.
[
More Info ]
[/software/projmgmt]
permanent link
Sat, Feb 08, 2014 5:27 pm
KPT Plugins and Corel Paintshop Pro X6
The Corel
PaintShop
Pro program supports a number of plugins that provide special effects
for images. For the X6 version of PaintShop Pro, Corel provides both 32-bit
and 64-bit versions of the software. However, the
Kai's Power Tools
(KPT) plugins will only work with the 32-bit version as the plugins are
incompatible with the 64-bit version.
Kai's Power Tools (KPT) was developed by
Kai Krause, but sold
to Corel Corporation
. Kai also developed Live Picture, Bryce, Kai's Power Show, Kai's
Power Goo, Convolver, Kai's Photo Soap and
Poser. He pioneered user
interface elements in his software such as soft shadows, rounded corners, and
translucency.
References:
-
Is the Paintshop Pro X6 KPT Collection Compatible with the 64 Bit version of
Paintshop Pro X6?
Corel Discovery Center
[/os/windows/software/graphics/corel/psp]
permanent link
Fri, Feb 07, 2014 8:55 pm
Determine the date of manufacture of a Mac system
On my MacBook Pro laptop, running OS X 10.8.3, I can see the date it was
manufactured by clicking on the Apple icon in the upper-left corner of
the screen then selecting
About This Mac and then clicking on
the
More Info... button.
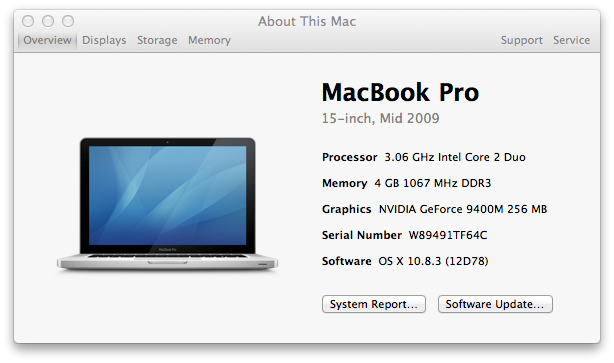
If you need to get the information from a command line interface, e.g., from
a terminal or SSH session, you can't get it directly using the
system_profiler command, but you can use information provided
by that command to look up the information online.
$ system_profiler SPHardwareDataType
Hardware:
Hardware Overview:
Model Name: MacBook Pro
Model Identifier: MacBookPro5,3
Processor Name: Intel Core 2 Duo
Processor Speed: 3.06 GHz
Number of Processors: 1
Total Number of Cores: 2
L2 Cache: 6 MB
Memory: 4 GB
Bus Speed: 1.07 GHz
Boot ROM Version: MBP53.00AC.B03
SMC Version (system): 1.48f2
Serial Number (system): W89491TF64C
Hardware UUID: FDE9B14D-E531-569F-A1EF-D0D0D0D0D0D0
Sudden Motion Sensor:
State: EnabledYou can use the model identifier information to look up information on
when the model was manufactured using
Lookup Mac Specs by
Serial Number, Order, Model, & EMC Number, Model ID @ EveryMac.com.
If you just want the model identifier, you can use awk
to isolate that information.
$ system_profiler SPHardwareDataType | awk '/Model Identifier/ {print $3}'
MacBookPro5,3When I looked up MacBookPro5,3, I saw 3 entries with
a "subfamily" of Mid-2009 15" listed for each. All 3 were
introduced on June 8, 2009 and discontinued on April 13, 2010. Using the
processor speed information provided by system_profiler, I
could narrow the selection down to a specific MacBook Pro "Core 2 Duo" and
see the standard RAM and hard disk size for that model.
You can also enter the last 3 characters of a 11 character serial
number to obtain that information from the site. Though, in my case
I saw an iPhone and several desktop systems listed as well as one
laptop model, though, since I knew it was a laptop, I knew which one
was the appropriate one.
[/os/os-x]
permanent link
Wed, Feb 05, 2014 12:01 pm
Using the control key to select multiple items with IE under VMWare
If you need to select multiple items on a form on a webpage in Internet
Explorer on a Microsoft Windows system, you can usually do so by holding
down the Ctrl key while selecting the items. On an Apple keyboard, though,
there is no Ctrl key though there is a Control key. But if you are using
VMWare Fusion to
run a version of Microsoft Windows in a
virtual machine (VM)
on a Mac OS X system, you can't use that Control key to select multiple items
on a form when you are using Internet Explorer in the VM unless you change
the default keyboard configuration, which can easily be done by taking the
following steps:
-
Click on VMWare Fusion at the top left of the VMWare window.
-
Select "Preferences".
-
Select "Keyboard & Mouse".
-
Click on the "Mouse Shortcuts" tab.
-
Uncheck "Secondary Button"; you can then close the "Keyboard & Mouse"
window.
You can then select multiple items on a form by holding down the Control key
while left clicking on items. If you want to go back to the default
configuration afterwards, you can go back to the "Mouse Shortcuts"
tab and click on the "Restore Defaults" button or just recheck the
"Secondary Button" checkbox, which is associated with the mouse shortcut
"Control - Primary Button".
[/os/os-x]
permanent link
Sun, Feb 02, 2014 10:02 pm
32 or 64-bit Application
If you need to determine whether a Microsoft Windows application is a
32-bit or 64-bit program, there are a number of ways to do so, including
simply right-clicking on the file and examining its properties.
[
More Info ]
[/os/windows]
permanent link
Sun, Jan 26, 2014 11:40 am
Downloading Video Clips with Offliberty
If you wish to download a video clip from a website, such as a news site
or
YouTube, to archive it should it
ever disappear from the Web,
Offliberty,
which provides "evidence of offline life", offers a means to download
the video to your hard drive by simply putting in the URL for the webpage
where it is found and then clicking on the
Off button below the
field where you enter the URL.
[ More Info ]
[/video/offliberty]
permanent link
Sat, Jan 25, 2014 10:22 pm
Turning Off Automatic Updates in Windows 8
By default, a Windows 8 system will automatically install updates and
reboot the system, if it deems it is necessary. You will be warned a
few days beforehand that a reboot will be necessary within a few days,
but when the time arrives, you will get only 15 minutes to save your work
before the system automatically updates. If you are someone like me who
tends to have a lot of windows open at once and who may be working on
many tasks concurrently, 15 minutes may not be enough to save all work
in progress, even if you are sitting at the computer at the 15-minute
warning so have the full amount of time to save work in progress. And,
if the 15-minute warning comes late at night, you may not even be awake
at the time and may find when you first check the system after you have
awakened that it rebooted over night and you have lost a lot of work in
progress in applications that don't autosave. To download the updates, but
control the timing of their installation yourself, take
these steps.
[/os/windows/win8]
permanent link
Sun, Jan 19, 2014 12:00 pm
Conditional Formatting in a Google Docs Spreadsheet
You can use conditional formatting in Google Docs spreadsheets to change
the color of text in a cell or the background color of a cell just as you
can in Microsoft Excel. E.g., if I had a cell that contained an expiration
date and wanted the background color of the cell to be red if the date
had been reached or had passed, I could click in the cell and take the
following steps:
- Click on Format.
- Select Conditional formatting....
- I could then select "Date is before" in the first
field and "today" in the next field. I could then check "Background" and
select the color red for the background color for the cell once the date
in the cell has been passed.
- Once you've set up the rule or rules for the cell or range of cells,
clik on Save rules.
The cell will then have the normal color as long as the date stored in the
cell is before today's date. Once the date in the cell matches today's date
or is before the date of viewing, the cell background color will turn red.
Note: You can ensure that Google knows the cell contains a date by clicking
on Format, selecting Number, and then More formats,
which will allow you to pick a particular format you wish to use for dates,
such as 2008-09-26, 9/26/08, etc.
[/network/web/services/google]
permanent link
Sun, Jan 19, 2014 10:34 am
Kindle Fire Won't Power On
Yesterday, I found my Kindle Fire would not power on. I had used it a few
hours earlier without seeing any message about the battery charge being
low. But repeated attempts to turn it on by hitting the power button did
no good. So I plugged it into a charger. Hours later when I attempted to
power it on, I still was unable to do so. Following advice posted at
My kindle won't turn on, I found that holding in the power button for
30 seconds then releasing the button and then tapping the power button again
resulted in it powering on again. When it powered on, I saw the battery had
a full charge.
[/ebook]
permanent link
Sat, Jan 18, 2014 11:13 pm
Kindle App Invalid Item
I've been getting an "Invalid Item" message stating "Please remove the item
from your device and go to All Items to download it again", when I try
to read some books I've purchased through Amazon on my Android phone.
I've tried suggestions I've found elsewhere for resolving the problem,
but there are still a few books that I've been unable to download and
read with the Kindle app on my phone.
[ More Info ]
[/ebook]
permanent link
Tue, Jan 14, 2014 10:30 pm
Setting up a Cisco DPC3827 Router
I needed to configure a Cisco DPC3827 DOCSIS 3.0 Gateway provided by
an Internet Service Provider (ISP) for a home local area network (LAN)
today, so I've placed some notes
here on steps for
configuring that router.
[/hardware/network/router/cisco]
permanent link
Sun, Jan 12, 2014 12:31 pm
Using an Email Alias in Thunderbird
When I register an email address for a website, I normally create a new
email alias unique to that website or the company associated with the
website. Unfortuately, many companies and websites sell their email lists
to other companies, ususally labelled as their "partners" in their privacy
policies, seeing that as a way to make additional revenue from their
customers or website visitors. Even if a company states they won't do so, most
reserve the right to change their privacy policy at any time and there is also
the possibility that the company will go out of business at some point and
all assets, including its mailing lists, will be sold to others.
I receive an inordinate amount of spam every day and waste a lot of time
purging it from my inbox, so by creating an email alias, which I can
easily do, since I manage the email server that processes my email, I can
simply invalidate any alias when I notice I'm receiving a lot of spam with
a particular alias I created in the "to" field. E.g., if I created an
alias Acme_2014@example.com that points to Me@example.com and start receiving
spam to Acme_2014@example.com, I know that the Acme Corporation sold my
email address to a spammer or had a compromise of their server holding my
account information.
Since Acme_2014 is not an email address that a spammer who employs name
dictionaries to distribute spam might use, I can be sure that
the source of the email is using the email address I gave to the Acme
Corporation. If I used an address such as abe, bill, or zachary@example.com,
I couldn't be certain, since some spammers try sending email to a
domain using every name from a name dictionary. I also wouldn't use
acme@example.com, since that is a word in an English language dictionary,
so spammers using a dictionary for building email addresses might use it.
I can easily create aliases on my email server, but there are a number
of online services that will allow you to create such aliases to thwart
spammers. E.g., with such a service you might be able to create an
alias acme_2014@spamblock1.com that points to me@example.com, if
me@example.com is the email address you normally use.
If you wanted to communicate with Acme Corporation by email, you
might need to use the alias you used in the "from" field of email you
send to them. To do so in Thunderbird 24.2.0, right-click on your
account, which should be located at the top of the left pane of the
Thunderbird window. E.g., you may see me@example.com there. Select
Settings, then put the alias in the Email Address field
and, if needed, set the Your Name field appropriately, then
click on OK. Once you have sent the email you needed to send
to the Acme Corporation you can change the settings back to those you
normally use.
[/network/email/clients/thunderbird]
permanent link
Sat, Jan 11, 2014 4:38 pm
Disk Management Under Windows 7 from a Regular Windows Account
If you are logged into a Windows 7 system as a regular user without
administrator privileges, you can still access the disk management
function without logging off and on again as administrator or switching
to the administrator account via the
Switch User feature. To
do so, take the following steps.
-
Click on the Start button.
-
Type
cmd and hit enter to open a command prompt window.
-
At the command prompt window, type
runas /user:administrator mmc. Note: if the system is part
of a Microsoft
Windows domain and you wish to use the domain administrator account,
put the domain name followed by a backslash after user: and
before administrator. E.g., runas
/user:mydomain\administrator mmc.
-
When prompted for the administrator password, enter it.
-
In the Console Root window that opens, click on File
and select compmgmt.
-
In the Computer Management window that opens, you
will then see Disk Management under Storage.
[/os/windows/win7]
permanent link
Tue, Jan 07, 2014 2:56 pm
Telemarketing or scammer call from 717-203-8889
At 2:12 PM, I received another annoying telemarketing/scammer credit card
call. When I answered the phone I heard a message about reducing
credit card interest rates. There was a mention that the call was from
"Cardmember Services". Since there was no mention of my credit union
nor bank, it was obvious that it was not a call from my
bank nor credit union. I hit "1" to speak to a representative so I could
ask that the calls be stopped. When I was finally connected to a person,
I asked her what company she represented in a friendly tone; the person
immediately hung up without answering, so I couldn't ask to be removed
from any calling list used.
I then used *69 to get the calling number, which was 7172038889. When
I called I heard the message "Please leave a message for. That mailbox
is full." There was no person or company identified after the word "for".
I've received many telemarketing calls where the caller is identified as
"Cardmember Services" and don't know how many telemarketing companies
or credit card scammers use that identification. If it was a telemarketing
number, there was not a way for me to get the actual name of the company.
As I usually do in such cases, I reported the calling number to the
U.S. Federal Trade Commission's National
Do Not Call Registry website, since my home phone number is in that
registry, thus telemarketers shouldn't be calling my number. Unfortunately,
many telemarketers ignore the list, apparently feeling that nothing will be
done to them if they ignore the list. Perhaps that is true; I don't know
how limited the FTC's resources may be for pursuing such companies. I can
only hope that if enough complaints are filed for a particular number that
the FTC will investigate and at least fine a few of them, though I'd like
to see such companies put out of business.
I think anyone who would answer such a call and provide a credit card
number to the caller is either a fool or extremely naive, since providing
credit card information to an unknown caller may provide an opportunity to
a scammer to use that information to use the credit card information for
nefarious purposes. But since I've frequently received such calls, apparently
such telemarketers/scammers find a fair number of people willing to do so.
[/phone]
permanent link
Fri, Jan 03, 2014 9:50 pm
Altering a browser's display of a webpage by zooming in and out
Many browsers, e.g., Internet Explorer, Firefox, and Safari, provide a
feature to zoom in and out, i.e., to magnify the display of a webpage to
make text and images larger or smaller through the use of
Ctrl-key
combinations.
Ctrl-+, i.e., the
Ctrl and
+ (plus)
keys hit simultaneously, will permit you to "zoom in" to enlarge the display
of text and images on a page. Hitting the
Ctrl and
- (minus)
keys simultaneously will reverse the process allowing you to zoom
back out, i.e., reduce the size of text and images. If you wish to return
to the default display, use
Ctrl-0, i.e., the
Ctrl
and zero keys struck simultaneously.
[/network/web/browser]
permanent link
Thu, Jan 02, 2014 7:30 pm
Juniper VPN software not working with Safari for Mac OS X
I haven't been able to use Safari on my MacBook Pro laptop running OS X
version 10.8.3, aka "
Mountain Lion, to start a VPN connection from home to the office
network for some time. When I attempt to establish the VPN connection,
by going to the website address that worked in the past from within
Safari 6.1, I am asked about running a Juniper Networks application.
Do you want to run this application?
Name: NCAppController
Publisher: Juniper Networks, Inc.
When I run it, a "Setup Control - Warning" message then appears
containing the following information:
Do you want to download, install, and/or execute software
from the following server?
Product Name: Network Connect
Software Name: NetworkConnect.app
When I click on "Yes", I see a "[Network Connect] Error" window
open stating "An error occurred while extracting one of the Network
components." The only option available is "OK" and the VPN connection
is not established.
According to
Connections to Juniper Network Connect VPN failing in Safari 6.1 and Safari
7, this problem also occurs with Safari 7 on OS X 10.8 (Mountain Lion).
The author of that article states:
Based on what I’m seeing, it looks like Safari 6.1 and Safari 7
introduced a new sandbox for browser plug-ins, replacing the previous
Java whitelist. At this time, it does not appear that Juniper’s
software is able to work with this sandbox.
I can establish the VPN connection by going to the Applications
directory in the Finder and double-click on Network
Connect, which starts the Network Connect 7.4.0 application,
then put in my username and password for the VPN and establish a
connection by that means without a problem.
[/os/os-x]
permanent link
Thu, Jan 02, 2014 11:40 am
Choosing a country for the Tor exit node
If you use the
Tor Browser Bundle
for web browsing, you may sometimes see "This service is not available in
your location" or similar messages when you attempt to use some online
services when a service is not available to residents of some countries, if
the exit node, i.e., the last hop in the Tor network, for your browser
session happens to be in a country for which the oline service is
unavailable. You can see the location of the exit node, i.e., the IP address
that websites see for your location when you visit them by visiting
WhatIsMyIP.com or similar websites
that provide geolocation information.
If you wish to specify an exit node in a particular country, you
can use the country code
for the country established by the
International Organization for Standardizaton. Two characters are used
to represent the country code in an online address, e.g. us for
the United States, dk for Denmark, gb for
Great Britain, etc. You can find the complete list of country codes
at
ISO 3166-1-alpha-2 code. The country code to be used for the exit
note must be placed in the
torrc
configuration file used by the Tor browser bundle. Look
for the torrc file in the Data/Tor directory
beneath the directory in which you installed the Tor Browser Bundle. You
can edit it with a text editor, such as Notepad on a Microsoft Windows
system. Put the following line at the end of the file where cc
represents the country code:
ExitNodes {cc}
E.g., for a United States exit node, you would use:
ExitNodes {us}
To confirm the exit node location, restart the Tor browser, if
it is running, and visit a site such as
WhatIsMyIp. Note: if there is a problem accessing an exit node in
the selected country or if you entered an invalid country code, you may find
that you don't get past the "Connecting to the Tor network" window
when you start the Tor browser. In that case, you may need to select
a different country code. Also, some online services may block access
from all known Tor exit nodes, since some people use Tor for malicious
purposes rather than simply for online privacy. E.g., Wikipedia does not
allow editing of articles when an editor is accessing Wikipedia via the
Tor network.
Also note that the Tor Project does not recommend specifying
an exit node. At
Tor FAQ: Can I control which nodes (or country) are used for entry/exit?
you will find:
We recommend you do not use these — they are intended for testing and
may disappear in future versions. You get the best security that Tor can
provide when you leave the route selection to Tor; overriding the entry /
exit nodes can mess up your anonymity in ways we don't understand.
But that option is available, if you wish to use it, at least as of
version 3.5 of the Tor Browser Bundle.
[/network/web/browser/tor]
permanent link
Wed, Jan 01, 2014 3:45 pm
Tor reports Firefox is already running
If you install the
Tor browser
bundle for online privacy and see a "Close Firefox" window appear
when you attempt to start the Tor browser with the message below, then you
may need to change the location where you placed the Tor browser bundle:
Firefox is already running, but it is not responding. To open a new window,
you must first close the existing Firefox process, or restart your system.
This message can appear even when the Firefox browser provided with the
Tor browser bundle isn't running as you can see by using the Windows Task
Manager to check for running processes, if the the software was placed
under the C:\Program Files (x86) directory, even if you run
the software from an account with administrator privileges. The
software apparently needs to write to files in the directory where it
has been installed, but can't do so. If you install it to the Desktop
or under the Documents directory for the account from which you will be
running it, you won't see the message.
[/network/web/browser/tor]
permanent link

Privacy Policy
Contact











































